* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download CCNPv5 Module 5 Lesson 1
Survey
Document related concepts
Internet protocol suite wikipedia , lookup
Airborne Networking wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Wireless security wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Deep packet inspection wikipedia , lookup
Network tap wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Cisco Systems wikipedia , lookup
Computer security wikipedia , lookup
Transcript
Implementing Secure
Converged Wide
Area Networks
(ISCW)
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
1
Thinking Like a
Hacker
Lesson 1 – Module 5 – ‘Cisco Device Hardening’
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
2
Module Introduction (1)
The open nature of the Internet makes it increasingly important for
businesses to pay attention to the security of their networks. As
organisations move more of their business functions to the public
network, they need to take precautions to ensure that attackers do
not compromise their data, or that the data does not end up being
accessed by the wrong people.
Unauthorised network access by an outside hacker or disgruntled
employee can wreak havoc with proprietary data, negatively affect
company productivity, and stunt the ability to compete.
Unauthorised network access can also harm relationships with
customers and business partners who may question the ability of
companies to protect their confidential information, as well as lead
to potentially damaging and expensive legal actions.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
3
Module Introduction (2)
"If you know yourself but not your enemy, for
every victory gained you will also suffer a
defeat." Sun Tzu – The Art of War
Before learning how to defend against attack, you need to know
how a potential attacker operates. The theme of the first few
lessons in this module is therefore, “know thine enemy”.
This module will help you to understand how hackers
operate and what attack strategies they can employ.
Once you know the nature of the threat, you will be
better able to implement the full set of security features
contained in Cisco IOS software to provide security for
your network.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
4
Module Introduction (3)
The module describes the best practices for securing router
administrative access using mechanisms such as:
password security features,
failed login attempt handling, and
role-based command-line interface (CLI).
You will learn how to:
mitigate attacks using access lists;
how to design and implement a secure management system including
secure protocols such as Secure Shell (SSH), Simple Network
Management Protocol version 3 (SNMPv3), and authenticated Network
Time Protocol (NTP).
Also discussed are the most ubiquitous authentication,
authorisation, and accounting (AAA) protocols - RADIUS and
TACACS+, and explanations of the differences between them.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
5
Objectives
At the completion of this first lesson, you will be able to:
Describe the steps taken by a potential network hacker to gain
unauthorised access
Explain the detailed information that a hacker is looking to
learn, and how this may be used to compromise network
security
Describe the basic steps that need to be taken to mitigate
network attacks
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
6
Seven Steps to Hacking a Network
Seven steps for compromising targets and applications:
Step 1 — Perform footprint analysis (reconnaissance)
Step 2 — Detail the information
Step 3 — Manipulate users to gain access
Step 4 — Escalate privileges
Step 5 — Gather additional passwords and secrets
Step 6 — Install back doors
Step 7 — Leverage the compromised system
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
7
Hacking a Network
The goal of any hacker is to compromise the intended
target or application
Hackers begin with little or no information about the
intended target, but by the end of their analysis, they
will have accessed the network and will have begun to
compromise their target
Their approach is always careful and methodical—
never rushed and never reckless
The seven-step process outlined in the previous slide is
a good representation of the method that hackers use –
and a starting point for an analysis of how to defeat it
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
8
Footprint Analysis (Reconnaissance)
Web pages, phone books, company brochures,
subsidiaries, etc
Knowledge of acquisitions
nslookup command to reconcile domain names
against IP addresses of the company’s servers
and devices
Port scanning to find open ports and operating
systems installed on hosts
traceroute command to help build topology
WHOIS queries
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
9
How to Defeat Footprinting
Keep all sensitive data off-line (business plans,
formulas, and proprietary documents)
Minimise the amount of information on your public
website
Examine your own website for insecurities
Run a ping sweep on your network
Familiarise yourself with one or more of the five
Regional Internet Registries – such as ARIN for North
America – to determine network blocks.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
10
Detail the Information
Find your server applications and versions:
What are your web, FTP, and mail server versions?
Listen to TCP and UDP ports and send random data to each
Cross-reference information to vulnerability databases to look
for potential exploits
Exploit selected TCP ports, for example:
Windows NT, 2000, and XP file sharing using SMB protocol
which uses TCP port 445.
In Windows NT, SMB runs on top of NetBT using ports 137, 138
(UDP), and 139 (TCP).
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
11
Software Tools
Hackers can use some of the tools listed here. All of these tools
are readily available to download, and security staff should know
how these tools work.
Netcat: Netcat is a featured networking utility that reads and writes
data across network connections using the TCP/IP protocol.
Microsoft EPDump and Remote Procedure Call (RPC) Dump:
These tools provide information about Microsoft RPC services on a
server:
The Microsoft EPDump application shows what is running and waiting
on dynamically assigned ports.
The RPC Dump (rpcdump.exe) application is a command-line tool that
queries RPC endpoints for status and other information on RPC..
GetMAC: This application provides a quick way to find the MAC
(Ethernet) layer address and binding order for a computer running
Microsoft Windows 2000 locally or across a network..
Software development kits (SDKs): SDKs provide hackers with
the basic tools that they need to learn more about systems.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
12
Manipulate Users to Gain Access
Social engineering is a way to manipulate people inside
the network to provide the information needed to
access the network. A computer is not required!!
Social engineering by telephone
Dumpster diving
Reverse social engineering
Recommended reading: “The Art of Deception: Controlling the
Human Element of Security” Mitnik, KD and Simon, WL; Wiley;
New Ed edition (17 Oct 2003)
There is a great deal of anecdotal evidence that this is
one of the most successful techniques……
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
13
Password Cracking
Hackers use many tools and techniques to crack passwords:
Word lists
Brute force
Hybrids
The yellow Post-It stuck on the side of the monitor, or in top of desk drawer…..
Password cracking attacks any application or service that accepts
user authentication, including those listed here:
NetBIOS over TCP (TCP 139)
Direct host (TCP 445)
FTP (TCP 21)
Telnet (TCP 23)
SNMP (UDP 161)
PPTP (TCP 1723)
Terminal services (TCP 3389)
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
14
Escalate Privileges
After securing a password for a user account and
user-level privileges to a host, hackers attempt to
escalate their privileges.
The hacker will review all the information he or she
can see on the host:
Files containing user names and passwords
Registry keys containing application or user passwords
Any available documentation (for example, e-mail)
If the host cannot be seen by the hacker, the hacker
may launch a Trojan application such as W32/QAZ
to provide it.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
15
Gather Additional Passwords and Secrets
Hackers target:
The local security accounts manager database
The active directory of a domain controller
Hackers can use legitimate tools including pwdump
and lsadump applications.
Hackers gain administrative access to all computers by
cross-referencing user names and password
combinations
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
16
Install Back Doors and Port Redirectors
Back doors:
Back doors provide:
A way back into the system if the front door is locked
A way into the system that is not likely to be detected
Back doors may use reverse trafficking:
Example: Code Red
Port redirectors:
Port redirectors can help bypass port filters, routers, and
firewalls and may even be encrypted over an SSL tunnel to
evade intrusion detection devices.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
17
Leverage the Compromised System
Back doors and port redirectors let hackers attack other
systems in the network
Reverse trafficking lets hackers bypass security
mechanisms
Trojans let hackers execute commands undetected
Scanning and exploiting the network can be automated
The hacker remains behind the cover of a valid
administrator account
The whole seven-step process is repeated as the
hacker continues to penetrate the network
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
18
Best Practices to Defeat Hackers
Keep patches up to date
Shut down unnecessary services and ports
Use strong passwords and change them often
Control physical access to systems
Curtail unexpected and unnecessary input
Perform system backups and test them on a regular basis
Warn everybody about social engineering
Encrypt and password-protect sensitive data
Use appropriate security hardware and software
Develop a written security policy for the company
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
19
Implementing Secure
Converged Wide
Area Networks
(ISCW)
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
20
Mitigating Network
Attacks
Lesson 2 – Module 5 – ‘Cisco Device Hardening’
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
21
Module Introduction
The open nature of the Internet makes it increasingly important for
businesses to pay attention to the security of their networks. As
organisations move more of their business functions to the public
network, they need to take precautions to ensure that attackers do
not compromise their data, or that the data does not end up being
accessed by the wrong people.
Unauthorised network access by an outside hacker or disgruntled
employee can wreak havoc with proprietary data, negatively affect
company productivity, and stunt the ability to compete.
Unauthorised network access can also harm relationships with
customers and business partners who may question the ability of
companies to protect their confidential information, as well as lead
to potentially damaging and expensive legal actions.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
22
Objectives
At the completion of this second lesson, you will be
able to:
Describe some of the more common network attacks, and
explain what effect they have on the network
Explain how to mitigate the effects of these common attacks
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
23
Reconnaissance
Reconnaissance is the unauthorised discovery and mapping of
systems, services, or vulnerabilities.
Reconnaissance is also known as information gathering, and in
most cases, precedes an access or Denial of Service (DoS) attack.
The malicious intruder typically conducts a ping sweep of the
target network to determine which IP addresses are alive and then
determines which services or ports are active on the live IP
addresses.
The intruder then queries the ports to determine the type and
version of the application and operating system that is running on
the target host.
Reconnaissance attacks can consist of the following:
Packet sniffers
Port scans
Ping sweeps
Internet information queries
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
24
Attacks Based on Minimal Intelligence
Attacks that require little intelligence about the target network:
Reconnaissance
Access attacks
DoS and Distributed DoS (DDoS)
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
25
Attacks Based on Intelligence or Insider
Information
Attacks that typically require
more intelligence or insider
access:
Worms, viruses, and Trojan horses
Application layer attacks
Threats to management protocols
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
26
Packet Sniffing
A packet sniffer is a software application that uses a network
adapter card in promiscuous mode to capture all network packets
that are sent across a LAN
Packet sniffers can only work in the same collision domain as the
network being attacked
Promiscuous mode is a mode in which the network adapter card
sends all packets that are received on the physical network wire to
an application for processing
Some network applications distribute network packets in plaintext.
Because the network packets are not encrypted, the packets can
be processed and understood by any application that can pick
them off the network and process them
Because the specifications for network protocols, such as TCP/IP,
are widely published, a third party can easily interpret the network
packets and develop a packet sniffer. Numerous freeware and
shareware packet sniffers are available that do not require the user
to understand anything about the underlying protocols
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
27
Packet Sniffers
A packet sniffer is a software application that uses a network
adapter card in promiscuous mode to capture all network packets.
Packet sniffers:
Exploit information passed in plaintext. Protocols that pass
information in plaintext are Telnet, FTP, SNMP, POP, and
HTTP.
Must be on the same collision domain.
Can be used legitimately or can be designed specifically for
attack.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
28
Packet Sniffer Mitigation
The techniques and tools that can be used to mitigate packet
sniffer attacks include:
Authentication
Using strong authentication is a first option for defense against
packet sniffers.
Cryptography
If a communication channel is cryptographically secure, the only
data a packet sniffer detects is cipher text (a seemingly random
string of bits) and not the original message
Anti-sniffer tools
Antisniffer tools detect changes in the response time of hosts to
determine whether the hosts are processing more traffic than their
own traffic loads would indicate.
Switched infrastructure
A switched infrastructure obviously does not eliminate the threat of
packet sniffers but can greatly reduce the sniffers’ effectiveness.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
29
Port Scans and Ping Sweeps
As legitimate tools, port scan and ping sweep
applications run a series of tests against hosts and
devices to identify vulnerable services
The information is gathered by examining IP
addressing and port or banner data from both TCP and
UDP ports
Essentially, a port scan consists of sending a message
to each port, one port at a time. The kind of response
that the sender receives indicates whether the port is
used and can therefore be probed for weakness
A ping sweep, or ICMP sweep, is a basic network
scanning technique that determines which range of IP
addresses map to live hosts
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
30
Port Scans and Ping Sweeps
Port scans and
ping sweeps
attempt to identify:
All services
All hosts and
devices
The operating
systems
Vulnerabilities
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
31
Port Scan and Ping Sweep Mitigation
Port scanning and ping sweeping is not a crime and there is no way to
stop these scans and sweeps when a computer is connected to the
Internet
There are ways to prevent damage to the system
Ping sweeps can be stopped if ICMP echo and echo-reply are turned off
on edge routers
When these services are turned off, network diagnostic data is lost
Network-based IPS and host-based IPS (HIPS) can usually notify when a
reconnaissance attack is under way
ISPs compare incoming traffic to the intrusion detection system (IDS) or
the IPS signatures in the IPS database.
Signatures are characteristics of particular traffic patterns. A signature, such as
“several packets to different destination ports from the same source address
within a short period of time,” can be used to detect port scans
A stealth scan is more difficult to detect, and many intrusion detection and
prevention systems will not notice this scan taking place. Discovering
stealth scans requires kernel-level work
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
32
Port Scan and Ping Sweep Mitigation
Port scans and ping sweeps cannot be prevented without
compromising network capabilities.
However, damage can be mitigated using intrusion prevention
systems at network and host levels.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
33
Internet Information queries
DNS queries can reveal information such as who owns a particular
domain and what addresses have been assigned to that domain
Ping sweeps of addresses revealed by DNS queries can present a
picture of the live hosts in a particular environment
After such a list is generated, port scanning tools can cycle through all
well-known ports to provide a complete list of all services that are
running on the hosts that the ping sweep discovered. Hackers can
examine the characteristics of the applications that are running on the
hosts, which can lead to specific information that is useful when the
hacker attempts to compromise that service
IP address queries can reveal information such as who owns a
particular IP address or range of addresses and which domain is
associated with the addresses
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
34
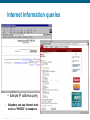
Internet Information queries
Sample IP address query
• Attackers can use Internet tools
such as “WHOIS” as weapons.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
35
Access Attacks and Mitigation
Access attacks exploit known vulnerabilities in authentication
services, FTP services, and web services to gain entry to web
accounts, confidential databases, and other sensitive information
for these reasons:
Retrieve data
Gain access
Escalate their access privileges
Access attacks can be performed in a number of different ways
Password attacks
Trust exploitation
Port redirection
Man-in-the-middle attacks
Buffer overflow
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
36
Password Attacks
Hackers implement
password attacks using
the following:
Brute-force attacks
Trojan horse programs
IP spoofing
Packet sniffers
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
37
Password Attacks
Password attacks can be implemented using several methods,
including brute-force attacks, Trojan horse programs, IP spoofing,
and packet sniffers.
One security risk is the fact that passwords can be stored as
plaintext. To overcome this risk, passwords should be encrypted.
On most systems, passwords are run through an encryption
algorithm to generate a one-way hash.
In granting authorisation, the hashes are calculated and compared
rather than using the plain password.
To use this encryption method, you supply an account and
password during the login process, and the algorithm generates a
one-way hash. This hash is compared to the hash stored on the
system. If they are the same, the system assumes that the proper
password was supplied.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
38
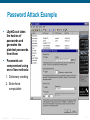
Password Attack Example
L0phtCrack takes
the hashes of
passwords and
generates the
plaintext passwords
from them
Passwords are
compromised using
one of two methods:
1. Dictionary cracking
2. Brute-force
computation
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
39
Password Attack Mitigation
Password attack mitigation techniques:
Do not allow users to use the same password on multiple
systems
Disable accounts after a certain number of unsuccessful login
attempts
Do not use plaintext passwords
For example “strong” passwords. (Use “mY8!Rthd8y” rather
than “mybirthday”)
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
40
Trust Exploitation
Trust exploitation refers to an individual taking advantage of a trust
relationship within a network.
An example of when trust exploitation takes place is when a
perimeter network is connected to a corporate network.
These network segments often contain DNS, SMTP, and HTTP
servers. Because these servers all reside on the same segment, a
compromise of one system can lead to the compromise of other
systems if those other systems also trust systems that are attached to
the same network.
Another example of trust exploitation is a Demilitarised Zone
(DMZ) host that has a trust relationship with an inside host that is
connected to the inside firewall interface. The inside host trusts the
DMZ host. When the DMZ host is compromised, the attacker can
leverage that trust relationship to attack the inside host.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
41
Trust Exploitation
A hacker leverages existing trust relationships.
Several trust models exist:
Windows:
Domains
Active directory
Linux and UNIX:
NIS
NIS+
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
42
Trust Exploitation
Trust exploitation-based attacks can be mitigated through tight
constraints on trust levels within a network
Systems that are inside a firewall should never absolutely trust
systems that are outside a firewall. Absolute trust should be limited to
specific protocols and, where possible, should be validated by
something other than an IP address
In the DMZ example, the hacker connected to the Internet has
already exploited some vulnerability of the DMZ host connected to
the DMZ interface of the firewall
The hacker’s next goal is to compromise the inside host that is
connected to the inside (trusted) interface of the firewall
To attack the inside host from the DMZ host, the hacker needs to find
the protocols that are permitted from the DMZ to the inside interface.
Once the protocols are known, the attacker searches for vulnerabilities
on the inside host. This attack can be stopped if the firewall allows only
minimum or no connectivity from the DMZ to the inside interface
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
43
Trust Exploitation Attack Mitigation
Trust levels within a network
are tightly restrained by
ensuring that systems inside a
firewall never absolutely trust
systems outside the firewall.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
44
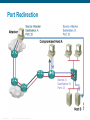
Port Redirection
A port redirection attack is a type of trust exploitation
attack that uses a compromised host to pass traffic
through a firewall that would otherwise have been
dropped.
Port redirection bypasses the firewall rule sets by
changing the normal source port for a type of network
traffic.
You can mitigate port redirection by using proper trust
models that are network-specific. Assuming a system is
under attack, an IPS can help detect a hacker and
prevent installation of such utilities on a host.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
45
Port Redirection
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
46
“Man-in-the-Middle” Attacks
Man-in-the-middle attacks have these purposes:
Theft of information
Hijacking of an ongoing session to gain access to your internal network
resources
Traffic analysis to obtain information about your network and network
users
DoS
Corruption of transmitted data
Introduction of new information into network sessions
An example of a man-in-the-middle attack is when someone
working for your ISP gains access to all network packets that
transfer between your network and any other network
Man-in-the-middle attacks can be mitigated by encrypting traffic in
a VPN tunnel. Encryption allows the hacker to see only cipher text
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
47
Man-in-the-Middle Attacks and their
Mitigation
A man-in-the-middle attack requires that the hacker has access
to network packets that come across a network
A man-in-the-middle attack is implemented using the following:
Network packet sniffers
Routing and transport protocols
Man-in-the-middle attacks can be effectively mitigated only
through the use of cryptographic encryption
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
48
DoS and DDoS Attacks and Mitigation
A DDoS attack and the simpler version of a DoS attack on a
server, send extremely large numbers of requests over a network
or the Internet
These many requests cause the target server to run well below
optimum speeds. Consequently, the attacked server becomes
unavailable for legitimate access and use
By overloading system resources, DoS and DDoS attacks crash
applications and processes by executing exploits or a combination
of exploits
DoS and DDoS attacks are the most publicised form of attack and are
among the most difficult to completely eliminate
The hacker community regards DoS attacks as trivial and
considers them unsophisticated because the attack requires so
little effort to execute
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
49
DoS and DDoS Attack Characteristics
A DoS attack damages or corrupts your computer
system or denies you and others access to your
networks, systems, or services
Distributed DoS technique performs simultanous
attacks from many distributed sources
DoS and DDoS attacks have these characteristics:
Generally not targeted to gain access or information
Require very little effort to execute
Difficult to eliminate, but their damage can be minimised
DoS and DDoS attacks can use IP spoofing
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
50
DDoS Attack Risks
DDoS attack risks include:
Downtime and productivity loss
Revenue loss from sales and support services
Lost customer loyalty
Theft of information
Extortion
Stock price manipulation
Malicious competition
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
51
DDoS Attack Example
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
52
DoS and DDoS Attack Mitigation
The threat of DoS and DDoS attacks can be reduced using:
Anti-spoof features on routers and firewalls
Proper configuration of anti-spoof features on your routers and firewalls can
reduce your risk of attack. These features include an appropriate filtering
with access lists, unicast reverse path forwarding that looks up the routing
table to identify spoofed packets, disabling of source route options, and
others.
Anti-DoS features on routers and firewalls
Proper configuration of anti-DoS features on routers and firewalls can help
limit the effectiveness of an attack. These features often involve limits on the
amount of half-open TCP connections that a system allows at any given
time.
Traffic rate limiting at the ISP level
An organization can implement traffic rate limiting with the organization’s
ISP
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
53
IP Spoofing in DoS and DDoS
IP spoofing occurs when a hacker inside or outside a
network impersonates the conversations of a trusted
computer.
IP spoofing can use either a trusted IP address in the
network or a trusted external IP address.
Uses for IP spoofing include:
Injecting malicious data or commands into an existing data
stream
Diverting all network packets to the hacker who can then reply
as a trusted user by changing the routing tables
IP spoofing may only be one step in a larger attack.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
54
IP Spoofing Attack Mitigation
The threat of IP spoofing can be reduced, but not
eliminated, using these measures:
Access control configuration
Encryption
RFC 3704 filtering
Additional authentication requirement that does not use
IP address-based authentication; examples are:
Cryptographic (recommended)
Strong, two-factor, one-time passwords
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
55
Network Attack
Using Intelligence
Lesson 3 – Module 5 – ‘Cisco Device Hardening’
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
56
Module Introduction
The open nature of the Internet makes it increasingly important for
businesses to pay attention to the security of their networks. As
organisations move more of their business functions to the public
network, they need to take precautions to ensure that attackers do
not compromise their data, or that the data does not end up being
accessed by the wrong people.
Unauthorised network access by an outside hacker or disgruntled
employee can wreak havoc with proprietary data, negatively affect
company productivity, and stunt the ability to compete.
Unauthorised network access can also harm relationships with
customers and business partners who may question the ability of
companies to protect their confidential information, as well as lead
to potentially damaging and expensive legal actions.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
57
Objectives
At the completion of this third lesson, you will be able
to:
Describe the difference between virus, trojan and worm
threats
Show how these threats are propagated
Explain techniques for dealing with these threats
Describe system software that can aid in defending and
mitigating against host machine attacks
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
58
End Station (Host) Vulnerabilities
Host machines are particularly vulnerable to attack if
not adequately protected. The main threats are:
Viruses
Trojan horse attacks
Worms
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
59
Viruses
A computer virus is a malicious computer program
(executable file) that can copy itself and infect a
computer without permission or knowledge of the
user. The original may modify the copies or the
copies may modify themselves, as occurs in a
metamorphic virus
A virus can only spread from one computer to another when its
host is taken to an uninfected computer, for instance by a user
sending it over a network as a file or as an email payload or
carrying it on a removable medium such as a ‘floppy’ disk, USB
disk (‘memory stick’), or CD / DVD
Some viruses are programmed to damage the computer by
damaging programs, deleting files, or reformatting the hard disk.
Others are not designed to do any damage, but simply replicate
themselves and perhaps make their presence known by presenting
text, video, or audio messages
Source: Wikepedia – Computer virus
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
60
Trojan Horse
A Trojan horse is a program that - unlike
a virus - contains or installs a malicious
program – the payload or 'trojan‘
Trojan horses may appear to be useful or interesting
programs, or at the very least harmless to an
unsuspecting user, but are actually harmful when
executed
There are two common types of Trojan horses
One is otherwise useful software that has been corrupted by a
hacker inserting malicious code that executes while the
program is used
The other type is a standalone program that masquerades as
something else, like a game or image file, in order to trick the
user into some misdirected complicity that is needed to carry
out the program's objectives
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
61
Worms
A computer worm is a self-replicating executable
computer program. It uses a network to send copies of
itself to other hosts (‘end-user’ machines on the
network) and it may do so without any user
intervention.
Unlike a virus, it does not need to attach itself to an
existing program. Worms always harm the network (if
only by consuming bandwidth), whereas viruses always
infect or corrupt files on a targeted computer.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
62
Malicious software containment
Viruses and Trojan horses can be contained by:
Effective use of antivirus software
Keeping up to date with the latest developments in these
methods of attacks
Keeping up to date with the latest antivirus software and
application versions
Implementing host-based intrusion prevention systems (for
example, Cisco Security Agent)
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
63
Worm Attack, Mitigation and Response
The anatomy of a worm attack has three parts:
The enabling vulnerability: A worm installs itself on a vulnerable
system
Propagation mechanism: After gaining access to devices, a
worm replicates and selects new targets
Payload: Once the worm infects the device, the attacker has
access to the host – often as a privileged user. Attackers
use a local exploit to escalate their privilege level to
administrator.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
64
Worm attack mitigation
Worm attack mitigation requires diligence on the part of system
and network administration staff.
Coordination between system administration, network engineering,
and security operations personnel is critical in responding
effectively to a worm incident.
Recommended steps for worm attack mitigation:
Containment: Contain the spread of the worm into your network and
within your network. Compartmentalise uninfected parts of your
network.
Inoculation: Start patching all systems and, if possible, scanning for
vulnerable systems.
Quarantine: Track down each infected machine inside your network.
Disconnect, remove, or block infected machines from the network.
Treatment: Clean and patch each infected system. Some worms may
require complete core system reinstallations to clean the system.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
65
Worm attack response
Six typical incident response methodologies to worms
are as follows:
1. Preparation: Acquire the resources to respond
2. Identification: Identify the worm
3. Classification: Classify the type of worm
4. Traceback: Trace the worm back to the attack’s origin
5. Reaction: Isolate and repair the affected systems
6. Post mortem: Document and analyse the process that you
used for future use
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
66
Application Layer Attacks and Mitigation
Application layer attacks have the following
characteristics:
They exploit well-known weaknesses, such as
those in protocols, that are intrinsic to an
application or system (for example, sendmail,
HTTP, and FTP)
They often use ports that are allowed through a
firewall (for example, TCP port 80 used in an
attack against a web server behind a firewall)
They can never be completely eliminated
because new vulnerabilities are always being
discovered
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
67
Netcat
Netcat is a tool that reads or writes data on any TCP/UDP
connections, relays TCP connections, and can act as a TCP/UDP
server.
#nc -h
connect to somewhere:
nc [-options] hostname port[s] [ports] ...
listen for inbound:
nc -l -p port [-options] [hostname] [port]
options:
-g gateway
source-routing hop point[s], up to 8
-G num
source-routing pointer: 4, 8, 12, ...
-i secs
delay interval for lines sent, ports scanned
-l
listen mode, for inbound connects
-n
numeric-only IP addresses, no DNS
-o file
hex dump of traffic
-p port
local port number
-r
randomize local and remote ports
-s addr
local source address
-u
UDP mode
-v
verbose [use twice to be more verbose]
port numbers can be individual or ranges: lo-hi [inclusive]
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
68
Netcat Example
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
69
Mitigation of Application Layer Attacks
Measures you can take to reduce risks include:
Read operating system and network log files or have the files
analysed by log analysis applications
Subscribe to mailing lists that publicise vulnerabilities
Keep all operating systems and applications current with the
latest patches
Use IDS/IPS that can scan for known attacks, monitor and log
attacks, and, in some cases, prevent attacks
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
70
Configuration Management protocols
Configuration management protocols include SSH, SSL and the
more insecure Telnet
Whichever is chosen for remote access to the managed device,
ACLs should be configured to allow only management servers to
connect to the device. All attempts from other IP addresses should
be denied and logged
Ideally use secure management protocols when configuring all
network devices. Protocols, such as Telnet and SNMPv2, must be
made secure by protecting the data with IPsec
The access lists should permit management access, such as SSH
or HTTPS, only from the legitimate management hosts
Also implement RFC 3704 filtering at the ingress router to reduce the
chance of an attacker from outside the network spoofing the addresses
of the management hosts
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
71
Management Protocols
These management protocols can be compromised:
SNMP: The community string information for simple
authentication is sent in plaintext.
syslog: Data is sent as plaintext between the managed device
and the management host.
TFTP: Data is sent as plaintext between the requesting host
and the TFTP server.
NTP: Many NTP servers on the Internet do not require any
authentication of peers.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
72
Management Protocol Best Practices
The following two slides summarise the best
practices to be followed when implementing a
secure management solution
Recommendations for the correct use of SNMP
tools include:
Configure SNMP with only read-only community strings
Set up access control on the device you want to manage
via SNMP to allow access by only the appropriate
management hosts
Use SNMP version 3. This version provides secure access
to devices through a combination of authenticating and
encrypting management packets over the network
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
73
Management Protocol Best Practices
Syslog: Encrypt syslog traffic within an IPsec tunnel.
Implement RFC 3704 filtering at the perimeter router when
allowing syslog access from devices outside a firewall.
Implement ACLs on the firewall to allow syslog data from only the
managed devices themselves to reach the management hosts.
TFTP: When possible, encrypt TFTP traffic within an IPsec tunnel
in order to reduce the chance of interception.
NTP: Implement your own master clock for private network
synchronisation.
Use NTP version 3 or above because these versions support a
cryptographic authentication mechanism between peers. NTP v3 is
currently supported by most vendors, including Cisco Systems.
The latest version 4 is not defined by any RFC and therefore not
widely supported.
Use ACLs that specify which network devices are allowed to
synchronise with other network devices.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
74
Determining Vulnerabilities and Threats
There are several tools and techniques that can be
used to find vulnerabilities in your network
Once any vulnerabilities have been identified, mitigation
steps can be considered and utilised as appropriate
Some common tools include:
Blue’s PortScanner
Wireshark (formerly Ethereal)
Microsoft Baseline Security Analyzer
Nmap
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
75
Blue’s Port Scanner
Blue’s Port Scanner is a fast
network scanner that can scan
over 300 ports per second on a
NT or Windows 2000 machine.
it comes with a Windows XP style interface, and offers TCP
and UDP scanning as well as a
Anti-Flood function
Blue’s
Port Scanner
http://www.securityconfig.com/software/specializedscanners/blues_port_scanner.html
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
76
Wireshark (Ethereal)
Wireshark is the world's
foremost network protocol
analyser, and is the
standard in many
industries. It is the
continuation of a project
that started in 1998.
Hundreds of developers
around the world have
contributed to it, and it is
still under active
development.
Wireshark
http://www.wireshark.org/about.html
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
77
Microsoft Baseline Security Analyzer
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
78
Nmap
Nmap ("Network Mapper") is a
free open source utility for network
exploration or security auditing.
It is designed to rapidly scan large
networks, although it works fine
against single hosts. Nmap uses
raw IP packets in novel ways to
determine what hosts are
available on the network, what
services (application name and
version) those hosts are offering,
what operating systems (and OS
versions) they are running, what
type of packet filters/firewalls are
in use, and dozens of other
characteristics.
Nmap runs on most types of
computers and both console and
graphical versions are available.
Nmap is free and open source
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
79
Disabling Unused
Cisco Router
Network Services
and Interfaces
Lesson 4 – Module 5 – ‘Cisco Device Hardening’
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
80
Module Introduction
The open nature of the Internet makes it increasingly important for
businesses to pay attention to the security of their networks. As
organisations move more of their business functions to the public
network, they need to take precautions to ensure that attackers do
not compromise their data, or that the data does not end up being
accessed by the wrong people.
Unauthorised network access by an outside hacker or disgruntled
employee can wreak havoc with proprietary data, negatively affect
company productivity, and stunt the ability to compete.
Unauthorised network access can also harm relationships with
customers and business partners who may question the ability of
companies to protect their confidential information, as well as lead
to potentially damaging and expensive legal actions.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
81
Vulnerable Router Services and Interfaces
Medium size and large networks typically use a firewall appliance
behind the perimeter router, which adds security features and
performs user authentication and more advanced packet filtering
Firewall installations also facilitate the creation of Demilitarized
Zones (DMZs), where the firewall ‘places’ hosts that are commonly
accessed from the Internet
Cisco IOS software offers an alternative to a firewall appliance by
incorporating many firewall features in the perimeter router.
Although this option does not provide the same performance and
security features that a Cisco PIX Security Appliance offers, a
router with an integrated firewall feature set can solve most smallto-medium business perimeter security requirements.
Cisco IOS routers run many services that create potential
vulnerabilities. To secure an enterprise network, all unneeded
router services and interfaces must be disabled.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
82
Vulnerable Router Services and Interfaces
Cisco IOS routers can be used as:
Edge devices
Firewalls
Internal routers
Routers have default services that create potential vulnerabilities (for
example, BOOTP, CDP, FTP, TFTP, NTP, Finger, SNMP, TCP/UDP minor
services, IP source routing, and proxy ARP
Vulnerabilities can be exploited regardless of where the routers are
placed.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
83
Vulnerable Router Services
Disable unnecessary services and interfaces (BOOTP, CDP,
FTP, TFTP, NTP, PAD, and TCP/UDP minor services)
Disable commonly configured management services (SNMP,
HTTP, and DNS)
Ensure path integrity (ICMP redirects and IP source routing)
Disable probes and scans (finger, ICMP unreachables, and
ICMP mask replies)
Ensure terminal access security (ident and TCP keepalives)
Disable gratuitous and proxy ARP
Disable IP directed broadcast
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
84
Unnecessary Services and Interfaces
Router Service
Default
Best Practice
BOOTP server
Enabled
Disable
Cisco Discovery Protocol (CDP)
Enabled
Disable if not required
Configuration auto-loading
Disabled
Disable if not required
Disable if not required.
FTP server
Disabled
Otherwise encrypt traffic within an
IPsec tunnel.
Disable if not required.
TFTP server
Disabled
Otherwise encrypt traffic within an
IPsec tunnel.
Disable if not required.
Network Time Protocol (NTP) service
Disabled
Otherwise configure NTPv3 and
control access between permitted
devices using ACLs.
Packet assembler and disassembler (PAD)
service
Enabled
Disable if not required
Enabled (pre
TCP and UDP minor services
11.3)
Disable if not required
Disabled (11.3+)
Maintenance Operation Protocol (MOP)
service
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
Enabled
Disable explicitly if not required
85
Commonly Configured Management Services
Management Service
Enabled by
Default
Best Practice
Simple Network Management Protocol (SNMP)
Enabled
Disable the service. Otherwise
configure SNMPv3.
Disable if not required.
ISCW-Mod5_L1
HTTP configuration and monitoring
Device dependent
Domain Name System (DNS)
Client Service –
Enabled
© 2007 Cisco Systems, Inc. All rights reserved.
Otherwise restrict access using
ACLs.
Disable if not required.
Otherwise explicitly configure the
DNS server address.
86
Path Integrity Mechanisms
ISCW-Mod5_L1
Path Integrity Mechanism
Enabled by
Default
Best Practice
ICMP redirects
Enabled
Disable the service
IP source routing
Enabled
Disable if not required.
© 2007 Cisco Systems, Inc. All rights reserved.
87
Probe and Scan Features
ISCW-Mod5_L1
Probe and Scan Feature
Enabled by
Default
Best Practice
Finger service
Enabled
Disable if not required.
ICMP unreachable notifications
Enabled
Disable explicitly on untrusted
interfaces.
ICMP mask reply
Disabled
Disable explicitly on untrusted
interfaces.
© 2007 Cisco Systems, Inc. All rights reserved.
88
Terminal Access Security
ISCW-Mod5_L1
Terminal Access Security
Enabled by
Default
Best Practice
IP identification service
Enabled
Disable
TCP Keepalives
Disabled
Enable
© 2007 Cisco Systems, Inc. All rights reserved.
89
ARP Service
ISCW-Mod5_L1
ARP Service
Enabled by
Default
Best Practice
Gratuitous ARP
Enabled
Disable if not required.
Proxy ARP
Enabled
Disable if not required.
© 2007 Cisco Systems, Inc. All rights reserved.
90
Router Hardening Considerations
Attackers can exploit unused router services and interfaces.
Administrators do not need to know how to exploit the services,
but they should know how to disable them.
It is tedious to disable the services individually.
An automated method is needed to speed up the hardening
process.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
91
Locking Down Routers with AutoSecure
The AutoSecure feature was released in Cisco IOS
Release 12.3 and later
AutoSecure is a single privileged EXEC program that
allows elimination of many potential security threats
quickly and easily. AutoSecure helps to make you
more efficient at securing Cisco routers
AutoSecure allows two modes of operation:
1. Interactive mode: Prompts to choose the way you want to
configure router services and other security-related features
2. Noninteractive mode: Configures security-related features
on your router based on a set of Cisco defaults
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
92
AutoSecure Functions
AutoSecure can selectively lock down:
Management plane services and functions:
Finger, PAD, UDP and TCP small servers, password encryption, TCP keepalives,
CDP, BOOTP, HTTP, source routing, gratuitous ARP, proxy ARP, ICMP
(redirects, mask-replies), directed broadcast, MOP, banner
Also provides password security and SSH access
Forwarding plane services and functions:
CEF, traffic filtering with ACLs
Firewall services and functions:
Cisco IOS Firewall inspection for common protocols
Login functions:
Password security
NTP protocol
SSH access
TCP Intercept services
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
93
AutoSecure Failure Rollback Feature
If AutoSecure fails to complete its operation, the
running configuration may be corrupt:
In Cisco IOS Release 12.3(8)T and later releases:
Pre-AutoSecure configuration snapshot is stored in the flash
under filename pre_autosec.cfg
Rollback reverts the router to the router’s pre-autosecure
configuration
Command: configure replace flash:pre_autosec.cfg
If the router is using software prior to Cisco IOS Release
12.3(8)T, the running configuration should be saved before
running AutoSecure.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
94
AutoSecure Process Overview
router#
auto secure [management | forwarding] [no-interact |
full] [ntp | login | ssh | firewall | tcp-intercept]
Cisco AutoSecure Interactive Steps:
Step 1 — Identify outside interfaces.
Step 2 — Secure the management plane.
Step 3 —
Step 4 —
Step 5 —
Step 6 —
ISCW-Mod5_L1
Create security banner.
Configure passwords, AAA, and SSH.
Secure the interface settings.
Secure the forwarding plane.
© 2007 Cisco Systems, Inc. All rights reserved.
95
Auto Secure Parameters
Parameter
Description
management
(Optional) Only the management plane will be secured.
forwarding
(Optional) Only the forwarding plane will be secured.
no-interact
(Optional) The user will not be prompted for any interactive
configurations. No interactive dialogue parameters will be configured,
including usernames or passwords.
full
(Optional) The user will be prompted for all interactive questions. This is
the default setting.
ntp
(Optional) Specifies the configuration of the Network Time Protocol (NTP)
feature in the AutoSecure command-line interface (CLI).
login
(Optional) Specifies the configuration of the Login feature in the
AutoSecure CLI.
ssh
(Optional) Specifies the configuration of the SSH feature in the
AutoSecure CLI.
firewall
(Optional) Specifies the configuration of the Firewall feature in the
AutoSecure CLI.
tcp-intercept
(Optional) Specifies the configuration of the TCP-Intercept feature in the
AutoSecure CLI.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
96
Step 1: Identify Outside Interfaces
Router#auto secure
--- AutoSecure Configuration --*** AutoSecure configuration enhances the security of the router but it
will not make router absolutely secure from all security attacks ***
All the configuration done as part of AutoSecure will be shown here. For
more details of why and how this configuration is useful, and any
possible side effects, please refer to Cisco documentation of
AutoSecure.
At any prompt you may enter '?' for help.
Use ctrl-c to abort this session at any prompt.
Gathering information about the router for AutoSecure
Is this router connected to internet? [no]: y
Enter the number of interfaces facing internet [1]: 1
Interface
IP-Address
OK? Method Status Protocol
Ethernet0/0
10.0.2.2
YES NVRAM up
up
Ethernet0/1
172.30.2.2
YES NVRAM up
up
Enter the interface name that is facing internet: Ethernet0/1
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
97
Step 2: Secure Management Plane
Services
Securing Management plane services..
Disabling service finger
Disabling service pad
Disabling udp & tcp small servers
Enabling service password encryption
Enabling service tcp-keepalives-in
Enabling service tcp-keepalives-out
Disabling the cdp protocol
Disabling the bootp server
Disabling the http server
Disabling the finger service
Disabling source routing
Disabling gratuitous arp
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
98
Step 3: Create Security Banner
Here is a sample Security Banner to be shown at every access to device.
Modify it to suit your enterprise requirements.
Authorised Access only
This system is the property of Woolloomooloo Pty Ltd.
UNAUTHORISED ACCESS TO THIS DEVICE IS PROHIBITED.
You must have explicit permission to access this
device. All activities performed on this device
are logged and violations of of this policy result
in disciplinary action.
Enter the security banner {Put the banner between
k and k, where k is any character}:
%This system is the property of Cisco Systems, Inc.
UNAUTHORIZED ACCESS TO THIS DEVICE IS PROHIBITED.%
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
99
Step 4: Passwords and AAA
Enable secret is either not configured or is same as enable password
Enter the new enable secret: Curium96
Configuration of local user database
Enter the username: student1
Enter the password: student1
Configuring aaa local authentication
Configuring console, Aux and vty lines for
local authentication, exec-timeout, transport
Securing device against Login Attacks
Configure the following parameters
Blocking Period when Login Attack detected: 300
Maximum Login failures with the device: 3
Maximum time period for crossing the failed login attempts: 60
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
100
Step 5: SSH and Interface-Specific
Services
Configure SSH server? [yes]: y
Enter the hostname: R2
Enter the domain-name: cisco.com
Configuring interface specific AutoSecure services
Disabling the following ip services on all interfaces:
no ip redirects
no ip proxy-arp
no ip unreachables
no ip directed-broadcast
no ip mask-reply
Disabling mop on Ethernet interfaces
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
101
Step 6: Forwarding Plane Verification
and Deployment
Securing Forwarding plane services..
Enabling CEF (This might impact the memory requirements for your
platform)
Enabling unicast rpf on all interfaces connected
to internet
Configure CBAC Firewall feature? [yes/no]: yes
This is the configuration generated:
no service finger
no service pad
no service udp-small-servers
no service tcp-small-servers
service password-encryption
.
.
Apply this configuration to running-config? [yes]: y
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
102
Auto Secure Configuration Example
(1 of 6)
no service finger
no service pad
no service udp-small-servers
no service tcp-small-servers
service password-encryption
service tcp-keepalives-in
service tcp-keepalives-out
no cdp run
no ip bootp server
no ip http server
no ip finger
no ip source-route
no ip gratuitous-arps
no ip identd
Disable global services.
Create banner.
banner #This system is the property of Cisco Systems, Inc.
Set minimum
UNAUTHORIZED ACCESS TO THIS DEVICE IS PROHIBITED.#
password length.
security passwords min-length 6
security authentication failure rate 10 log
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
Set the login failure
rate.
103
Auto Secure Configuration Example
(2 of 6)
enable secret 5 $1$6NpI$ClSvtL5Zs63fPpsQT5Dyq/
enable password 7 09674F04100916
aaa new-model
aaa authentication login local_auth local
line con 0
login authentication local_auth
exec-timeout 5 0
transport output telnet
line aux 0
login authentication local_auth
exec-timeout 10 0
transport output telnet
line vty 0 4
login authentication local_auth
transport input telnet
Enable secret password.
Enable local AAA.
Configure local authentication on
console, auxiliary and VTY lines
for telnet.
Block too many login
attempts.
login block-for 5 attempts 3 within 4
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
104
Auto Secure Configuration Example
(3 of 6)
Configure hostname and
domain name.
hostname LosAngeles
ip domain-name cisco.com
crypto key generate rsa general-keys modulus 1024
ip ssh time-out 60
ip ssh authentication-retries 2
line vty 0 4
transport input ssh telnet
service
service
logging
logging
service
logging
logging
ISCW-Mod5_L1
timestamps debug datetime msec localtime show-timezone
timestamps log datetime msec localtime show-timezone
facility local2
trap debugging
sequence-numbers
Configure logging
console critical
parameters.
buffered
© 2007 Cisco Systems, Inc. All rights reserved.
105
Auto Secure Configuration Example
(4 of 6)
interface FastEthernet0/0
no ip redirects
no ip proxy-arp
no ip unreachables
no ip directed-broadcast
no ip mask-reply
no mop enabled
interface Serial0/0
no ip redirects
no ip proxy-arp
no ip unreachables
no ip directed-broadcast
no ip mask-reply
interface FastEthernet0/1
no ip redirects
no ip proxy-arp
no ip unreachables
no ip directed-broadcast
no ip mask-reply
no mop enabled
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
Disable FE interface 0/0
services.
Disable serial port
services.
Disable FE interface 0/1
services.
106
Auto Secure Configuration Example
(5 of 6)
Enable CEF.
ip cef
Apply ACL to inside
interface Serial0/0
interface.
ip access-group autosec_complete_bogon in
exit
access-list 100 permit udp any any eq bootpc
interface Serial0/0
ip verify unicast source reachable-via rx allow-default 100
ip inspect
ip inspect
ip inspect
ip inspect
ip inspect
ip inspect
ip inspect
ip inspect
ip inspect
ip inspect
ip inspect
ip inspect
ip inspect
!
end
ISCW-Mod5_L1
audit-trail
dns-timeout 7
tcp idle-time 14400
udp idle-time 1800
name autosec_inspect
name autosec_inspect
name autosec_inspect
name autosec_inspect
name autosec_inspect
name autosec_inspect
name autosec_inspect
name autosec_inspect
name autosec_inspect
© 2007 Cisco Systems, Inc. All rights reserved.
Turn on the CBAC firewall
with common settings.
cuseeme timeout 3600
ftp timeout 3600
http timeout 3600
rcmd timeout 3600
realaudio timeout 3600
smtp timeout 3600
tftp timeout 30
udp timeout 15
tcp timeout 3600
107
Auto Secure Configuration Example
(6 of 6)
ip access-list extended autosec_firewall_acl
permit udp any any eq bootpc
deny ip any any
Apply CBAC inspect
list to outside
interface Serial0/0
ip inspect autosec_inspect interface.
out
ip access-group autosec_firewall_acl in
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
Apply ACL to
outside
interface.
108
Locking Down Routers with Cisco SDM
SDM simplifies router and security configuration through smart
wizards that help to quickly and easily deploy, configure, and
monitor a Cisco router without requiring knowledge of the CLI
SDM simplifies firewall and IOS software configuration without
requiring expertise about security or IOS software
SDM contains a Security Audit wizard that performs a
comprehensive router security audit
SDM uses security configurations recommended by Cisco
Technical Assistance Center (TAC) and the International Computer
Security Association (ICSA) as the basis for comparisons and
default settings
The Security Audit wizard assesses the vulnerability of the existing
router and provides quick compliance to best-practice security
policies
SDM can implement almost all of the configurations that
AutoSecure offers with the One-Step Lockdown feature
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
109
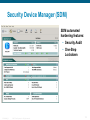
Security Device Manager (SDM)
SDM automated
hardening features:
• Security Audit
• One-Step
Lockdown
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
110
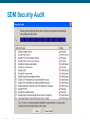
SDM Security Audit Overview
Security Audit compares router configuration against
recommended settings
Examples of the audit include:
Shut down unneeded servers
Disable unneeded services
Apply the firewall to the outside interfaces
Disable or harden SNMP
Shut down unused interfaces
Check password strength
Enforce the use of ACLs
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
111
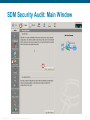
SDM Security Audit: Main Window
1.
2.
3.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
112
SDM Security Audit Wizard
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
113
SDM Security Audit Interface Configuration
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
114
SDM Security Audit
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
115
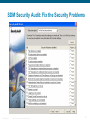
SDM Security Audit: Fix the Security Problems
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
116
SDM Security Audit: Summary
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
117
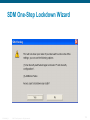
SDM One-Step Lockdown: Main Window
1.
2.
3.
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
118
SDM One-Step Lockdown Wizard
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
119
ISCW-Mod5_L1
© 2007 Cisco Systems, Inc. All rights reserved.
120




















































































































![Computer Networks [Opens in New Window]](http://s1.studyres.com/store/data/001432217_1-c782ef807e718d5ed80f4e9484b1006a-150x150.png)



