* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Document
Survey
Document related concepts
TV Everywhere wikipedia , lookup
Computer network wikipedia , lookup
Deep packet inspection wikipedia , lookup
Extensible Authentication Protocol wikipedia , lookup
Wireless USB wikipedia , lookup
Internet protocol suite wikipedia , lookup
SIP extensions for the IP Multimedia Subsystem wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Remote Desktop Services wikipedia , lookup
Policies promoting wireless broadband in the United States wikipedia , lookup
Wireless security wikipedia , lookup
Transcript
Wireless Application
Protocol
Outline
Mobile applications
How are mobile/wireless environments different?
What is WAP?
WAP Architecture
WAE (WML/WMLScript)
WTA Framework
WAP Push Services
WAP Protocol Stack
Hype v/s Reality
References and Resources
Mobile Applications - 1
Vehicles
transmission of news, road condition etc
ad-hoc network with near vehicles to prevent accidents
Emergencies
early transmission of patient data to the hospital
ad-hoc network in case of earthquakes, cyclones
military ...
Traveling salesmen
direct access to central customer files
consistent databases for all agents
mobile office
Mobile Applications - 2
Web access
outdoor Internet access
intelligent travel guide with up-to-date location dependent information
Information services
push: stock quotes; pull: nearest cash ATM
Disconnected operations
file-system caching for off-line work
mobile agents, e.g., shopping
Entertainment
games, etc
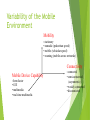
Variability of the Mobile
Environment
Mobility
• stationary
• nomadic (pedestrian speed)
• mobile (vehicular speed)
• roaming (mobile across networks)
Connectivity
Mobile Device Capability
• form
factor
• GUI
• multimedia
• real-time multimedia
• connected
• semi-connected
(asymmetric)
• weakly connected
• disconnected
World Wide Web and Mobility
HTTP/HTML have not been designed for mobile applications/devices
HTTP 1.0 characteristics
designed for large bandwidth, low delay
stateless, client/server, request/response communication
connection oriented, one connection per request
TCP 3-way handshake, DNS lookup overheads
big protocol headers, uncompressed content transfer
primitive caching (often disabled, dynamic objects)
security problems (using SSL/TLS with proxies)
HTML characteristics
designed for computers with “high” performance, color high-resolution
display, mouse, hard disk
typically, web pages optimized for design, not for communication; ignore
end-system characteristics
System Support for Mobile
Enhanced browsers
WWW
client-aware support for mobility
Proxies
Client proxy: pre-fetching, caching, off-line use
Network proxy: adaptive content transformation for connections
Client and network proxy
Enhanced servers
server-aware support for mobility
serve the content in multiple ways, depending on client capabilities
New protocols/languages
WAP/WML
Wireless Application Protocol (WAP)
Empowers mobile users with wireless devices to easily access and
interact with information and services.
A “standard” created by wireless and Internet companies to
enable Internet access from a cellular phone
wapforum.org:
co-founded by Ericsson, Motorola, Nokia, Phone.com
450 members in 2000, comprise of Handset manufacturers, Wireless
service providers, ISPs, Software companies in the wireless industry
Goals
deliver Internet services to mobile devices
enable applications to scale across a variety of transport options
and device types
independence from wireless network standards
GSM, CDMA IS-95, TDMA IS-136, 3G systems (UMTS, W-CDMA)
WAP: Main Features
Browser
Markup language
“Wap/Origin server”, similar to existing web servers
Protocol layers
Transition from wireless to wired world
Server
Similar to Javascript, adapted to mobile devices
Gateway
Similar to HTML, adapted to mobile devices
Script language
“Micro browser”, similar to existing web browsers
Transport layer, security layer, session layer etc.
Telephony application interface
Access to telephony functions
Internet Model
HTML
HTTP
TLS/SSL
TCP/IP
WAP Architecture
Web Server
WAP Gateway
WML
WML Encoder
WMLScript
WSP/WTP
WMLScript
Compiler
HTTP
CGI
Scripts
etc.
WTAI
Protocol Adapters
Content
WML Decks
with WML-Script
Client
Etc.
Source: WAP Forum
WAP Application Server
Client
WML
WMLScript
WTAI
WML Encoder
WSP/WTP
WMLScript
Compiler
Protocol Adapters
Application
Logic
Content
WML Decks
with WML-Script
WAP Application Server
Etc.
Source: WAP Forum
WAP Architecture
Another look
Key Components
•
•
•
•
•
•
•
Origin/Web Server
WAP Gateway/Proxy
WAP Protocol Stack
Micro Browser
WML/WML Script
Transcoders
WTA
Source: WAP Forum
WAP: Network Elements
fixed network
Internet
HTML
wireless network
WML
HTML
filter
WAP
proxy
Binary WML
WML
HTML
web
server
HTML
filter/
WAP
proxy
WTA
server
Binary WML
Binary WML
PSTN
Binary WML: binary file format for clients
Source: Schiller
WAP Specifies
Wireless Application Environment
WML Microbrowser
WMLScript Virtual Machine
WMLScript Standard Library
Wireless Telephony Application Interface (WTAI)
WAP content types
Wireless Protocol Stack
Wireless Session Protocol (WSP)
Wireless Transport Layer Security (WTLS)
Wireless Transaction Protocol (WTP)
Wireless Datagram Protocol (WDP)
Wireless network interface definitions
WAP Stack
MicroBrowser (WML,
WMLScript, WTA, WTAI)
Runs on top of WDP
Provided lightweight X-oriented service
• Unreliable 1-way request
• Reliable 1-way/2-way req./response
Lightweight SSL
Uses WIM/PKI-Cards
Datagram service on different
bearers
Convergence between bearer
services
Different Wireless Tech.
Source: WAP Forum
WAP Stack
WAE (Wireless Application Environment):
Architecture: application model, browser, gateway, server
WML: XML-Syntax, based on card stacks, variables, ...
WTA: telephone services, such as call control, phone book etc.
WSP (Wireless Session Protocol):
Provides HTTP 1.1 functionality
Supports session management, security, etc.
WTP (Wireless Transaction Protocol):
Provides reliable message transfer mechanisms
Based on ideas from TCP/RPC
WTLS (Wireless Transport Layer Security):
Provides data integrity, privacy, authentication functions
Based on ideas from TLS/SSL
WDP (Wireless Datagram Protocol):
Provides transport layer functions
Based on ideas from UDP
Content encoding, optimized for low-bandwidth channels, simple devices
Why is HTTP/HTML not
enough?
Big pipe - small pipe syndrome
Internet
HTTP/HTML
<HTML>
<HEAD>
<TITLE>NNN Interactive</TITLE>
<META HTTP-EQUIV="Refresh" CONTENT="1800,
URL=/index.html">
</HEAD>
<BODY BGCOLOR="#FFFFFF"
BACKGROUND="/images/9607/bgbar5.gif" LINK="#0A3990"
ALINK="#FF0000" VLINK="#FF0000" TEXT="000000"
ONLOAD="if(parent.frames.length!=0)top.location='ht
tp://nnn.com';">
<A NAME="#top"></A>
<TABLE WIDTH=599 BORDER="0">
<TR ALIGN=LEFT>
<TD WIDTH=117 VALIGN=TOP ALIGN=LEFT>
<HTML>
<HEAD>
<TITLE
>NNN
Intera
ctive<
/TITLE
>
<META
HTTPEQUIV=
"Refre
sh"
CONTEN
T="180
0,
URL=/i
ndex.h
tml">
Wireless network
<WML>
<CARD>
<DO TYPE="ACCEPT">
<GO URL="/submit?Name=$N"/>
</DO>
Enter name:
<INPUT TYPE="TEXT" KEY="N"/>
</CARD>
</WML>
WAP
Content encoding
010011
010011
110110
010011
011011
011101
010010
011010
Source: WAP Forum
WAP: “Killer” Applications
Location-based services
Enterprise solutions
Schedules and rescheduling, Reservations
Gaming and Entertainment
Banking, Bill-paying, Stock trading, Funds transfers
Travel services
Email access, Database access, “global” intranet access
Information updates “pushed” to WAP devices
Financial services
Real-time traffic reporting, Event/restaurant recommendation
Online, real-time, multi-player games
Downloadable horoscopes, cartoons, quotes, advice
M-Commerce
Shopping on the go
Instant comparison shopping
Location-based special offers and sales
Wireless Application Environment (WAE)
Goals
device and network independent application environment
for low-bandwidth, wireless devices
considerations of slow links, limited memory, low computing power, small
display, simple user interface (compared to desktops)
integrated Internet/WWW programming model
high interoperability
WAE Components
Architecture
User Agents
WML/WTA/Others
content formats: vCard, vCalendar, Wireless Bitmap, WML, ...
WML
procedural, loops, conditions, ... (similar to JavaScript)
WTA
XML-Syntax, based on card stacks, variables, ...
WMLScript
Application model, Microbrowser, Gateway, Server
telephone services, such as call control, text messages, phone book, ...
(accessible from WML/WMLScript)
Proxy (Method/Push)
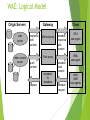
WAE: Logical Model
Origin Servers
web
server
other content
server
Client
Gateway
response
with
content
Method proxy
encoded
response
with
content
Push proxy
push
content
encoders
&
decoders
request
encoded
push
content
encoded
request
WTA
user agent
WML
user agent
other
WAE
user agents
WAP Microbrowser
Optimized for wireless devices
Minimal RAM, ROM, Display, CPU and keys
Provides consistent service UI across devices
Provides Internet compatibility
Enables wide array of available content and applications
WML: Wireless Markup
Tag-based browsing language:
Language
Screen management (text, images)
Data input (text, selection lists, etc.)
Hyperlinks & navigation support
Takes into account limited display,
navigation capabilities of devices
XML-based language
describes only intent of interaction in
an abstract manner
presentation depends upon device
capabilities
Cards and Decks
document consists of many cards
User interactions are split into cards
Explicit navigation between cards
cards are grouped to decks
deck is similar to HTML page, unit of
content transmission
Events, variables and state mgmt
Content (XML)
XSL Processor
WML Stylesheet
WML Browsers
HTML StyleSheet
HTTP Browser
WML
The basic unit is a card. Cards are grouped together into Decks Document ~ Deck (unit of transfer)
All decks must contain
Document prologue
XML & document type declaration
<WML> element
Must contain one or more cards
WML File Structure
<?xml version="1.0"?>
<!DOCTYPE WML PUBLIC "-//WAPFORUM//DTD WML 1.0//EN"
"http://www.wapforum.org/DTD/wml.xml">
<WML>
...
</WML>
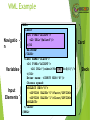
WML Example
Navigatio
n
Variables
Input
Elements
<WML>
<CARD>
<DO TYPE=“ACCEPT”>
<GO URL=“#eCard”/>
</DO
Welcome!
</CARD>
<CARD NAME=“eCard”>
<DO TYPE=“ACCEPT”>
<GO URL=“/submit?N=$(N)&S=$(S)”/>
</DO>
Enter name: <INPUT KEY=“N”/>
Choose speed:
<SELECT KEY=“S”>
<OPTION VALUE=“0”>Fast</OPTION>
<OPTION VALUE=“1”>Slow</OPTION>
<SELECT>
</CARD>
</WML>
Card
Deck
A Deck of Cards
<WML>
<CARD>
<DO TYPE="ACCEPT" LABEL="Next">
<GO URL="#card2"/>
</DO>
Acme Inc.<BR/>Directory
</CARD>
<CARD NAME="card2">
<DO TYPE="ACCEPT">
<GO URL="?send=$type"/>
</DO>
Services
<SELECT KEY="type">
<OPTION VALUE="em">Email</OPTION>
<OPTION VALUE="ph">Phone</OPTION>
<OPTION VALUE="fx">Fax</OPTION>
</SELECT>
</CARD>
</WML>
Acme Inc.
Directory
_____________
Next
Services
1>Email
2 Phone
____________
OK
Source: WAP Forum
The DO Element
Binds a task to a user action
Action type:
ACCEPT, OPTIONS, HELP
PREV, DELETE, RESET
Label:
Text string or image (optional)
Task:
GO
PREV, REFRESH, NOOP
Destination:
URL
Post data:
if METHOD=POST
<DO TYPE="ACCEPT" LABEL="Next">
<GO URL="http://www.mysite.com/myapp.wml"/>
</DO>
Source: WAP Forum
Anchored Links
Bind a task to the ACCEPT action,
when cursor points to a link
TITLE= sets the label string (default = “Link”)
Links are not allowed in select list options
<CARD>
Please visit our
<A TITLE="Visit">
<GO URL="home.wml"/>home page</A>
for details.
</CARD>
Please visit
our home
page for
____________
Visit
Source: WAP Forum
The TEMPLATE Element
Defines actions & events for all cards in a deck
<WML>
<TEMPLATE>
<DO TYPE="OPTIONS" LABEL="Main">
<GO URL="main_menu.wml"/>
</DO>
</TEMPLATE>
<CARD NAME="msg1">
<DO TYPE="ACCEPT" LABEL="Next">
<GO URL="#msg2"/>
</DO>
First story
</CARD>
<CARD NAME="msg2">
Second story
</CARD>
</WML>
First story
…
_____________
Next
Main
Second story
...
_____________
OK
Main
Source: WAP Forum
Handling User Input
Select lists
Input fields
Choose from a list of options
Enter a string of text or numbers
KEY variables
Set by SELECT and INPUT elements
How user input is passed to other cards and the
application server
Source: WAP Forum
The SELECT Element
Display a list of options
Each option may set the KEY variable and/or bind a task to
the ACCEPT key
TITLE= dynamically sets the label string
MULTIPLE=“TRUE”: Allows user to pick multiple items
<CARD>
<DO TYPE="ACCEPT" LABEL="View">
<GO URL="getcity.cgi?location=$city"/>
</DO>
Forecast
<SELECT KEY="city">
<OPTION VALUE="ber">Berlin</OPTION>
<OPTION VALUE="rom">Rome</OPTION>
<OPTION TITLE="Find" ONCLICK="find.cgi">New
</SELECT>
</CARD>
Forecast
1 Berlin
2 Rome
3>New City
____________
Find
City</OPTION>
Source: WAP Forum
The INPUT Element
Prompts user to enter a string of text
DEFAULT=key_value; Default KEY variable (displayed to user)
FORMAT=format_specifier; If omitted, free-form entry is allowed
EMPTYOK="TRUE“; Browser will accept null input
TYPE="PASSWORD“; Special entry mode handled by the browser
MAXLENGTH=number; Maximum number of allowed characters
<CARD>
<DO TYPE="ACCEPT">
<GO URL="?get=person"
METHOD="POST" POSTDATA="userid=$ssn"/>
</DO>
Soc Security:
<INPUT KEY="ssn" FORMAT="NNN\-NN\-NNNN"/>
</CARD>
Soc. Security:
287-33- _
____________
NUM
Soc. Security:
287-33- 7629
____________
OK
Source: WAP Forum
WML Content Formats
Common interchange formats, for interoperability
Formats:
Newly defined formats:
WML text and tokenized format
WMLScript text and bytecode format
WBMP image format
Binary format for size reduction
Business cards: IMC vCard standard
Calendar: IMC vCalendar standard
Images: WBMP (Wireless BitMaP)
Compiled WML, WMLScript
Bytecodes/tokens for common values and operators
Compressed headers
Data compression (e.g. images)
General-purpose transport compression can still be applied
Displaying Images
Insert app images or local icons within display text
1-bit BMP format
Images are ignored by non-bitmapped devices
Check HTTP_ACCEPT for “image/bmp”
<CARD>
<DO TYPE="ACCEPT">
<GO URL="#c2"/>
</DO>
Continue <IMG LOCALSRC="righthand"
ALT="forward..."/>
</CARD>
<CARD NAME="c2">
<IMG SRC="../images/logo.wbmp"
ALT="Unwired Planet"/>
<BR/>Welcome!
</CARD>
Source: WAP Forum
WML (other features)
Setting card styles to create forms
Using variables to cache user data
Using card intrinsic events to trigger transparent tasks
Using timers
Securing WML decks
Bookmarking decks
WMLScript
Complement to WML
Provides general scripting capabilities
local user interaction, validity check of user input
access to device facilities (phone call, address book etc.)
extensions to the device software
configure device, download new functionality after deployment
Bytecode-based virtual machine
Procedural logic, loops, conditionals, etc.
Optimized for small-memory, small-cpu devices
Features
Derived from JavaScript™
Stack-oriented design, ROM-able
Designed for simple, low-impact implementation
WMLScript compiler resides in the network
WMLScript Libraries
Lang - VM constants, general-purpose math
functionality, etc.
String - string processing functions
URL - URL processing
Browser - WML browser interface
Dialog - simple user interface
Float - floating point functions
WMLScript Example
Functions
Variables
Programming
Constructs
function currencyConvertor(currency, exchRate) {
return currency*exchangeRate;
}
function myDay(sunShines) {
var myDay;
if (sunShines) {
myDay = “Good”;
} else {
myDay = “Not so good”;
};
return myDay;
}
Source: WAP Forum
Wireless Telephony
Application
(WTA)
Collection of telephony
specific extensions
designed primarily for network operators
Example
calling a number (WML)
wtai://wp/mc;07216086415
calling a number (WMLScript)
WTAPublic.makeCall("07216086415");
Implementation
Extension of basic WAE application model
Extensions added to standard WML/WMLScript browser
Exposes additional API (WTAI)
WTA Features
Extension of basic WAE application model
WTAI includes:
network model for interaction
client requests to server
event signaling: server can push content to the client
event handling
table indicating how to react on certain events from the network
client may now be able to handle unknown events
telephony functions
some application on the client may access telephony functions
Call control
Network text messaging
Phone book interface
Event processing
Security model: segregation
Separate WTA browser
Separate WTA port
WTA Example (WML)
Placing an outgoing call with WTAI:
WTAI Call
Input Element
<WML>
<CARD>
<DO TYPE=“ACCEPT”>
<GO URL=“wtai:cc/mc;$(N)”/>
</DO>
Enter phone number:
<INPUT TYPE=“TEXT” KEY=“N”/>
</CARD>
</WML>
Source: WAP Forum
WTA Example (WMLScript)
Placing an outgoing call with WTAI:
WTAI Call
function checkNumber(N) {
if (Lang.isInt(N))
WTAI.makeCall(N);
else
Dialog.alert(“Bad phone number”);
}
Source: WAP Forum
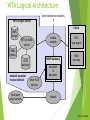
WTA Logical Architecture
other telephone networks
WTA Origin Server
Client
WML
Scripts
WTA & WML
server
mobile
network
WTA
user agent
WAP Gateway
WAE
services
WML
decks
WTA
services
network operator
trusted domain
third party
origin servers
encoders
&
decoders
other WTA
servers
firewall
Source: Schiller
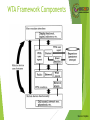
WTA Framework Components
Source: Heijden
WTA User Agent
WTA User Agent
WML User agent with extended functionality
can access mobile device’s telephony functions through WTAI
can store WTA service content persistently in a repository
handles events originating in the mobile network
WTA User Agent Context
Abstraction of execution space
Holds current parameters, navigation history, state of user agent
Similar to activation record in a process address space
Uses connection-mode and connectionless services offered by WSP
Specific, secure WDP ports on the WAP gateway
WTA Events and Repository
WTA Events
Network notifies device of event (such as incoming call)
WTA events map to device’s native events
WTA services are aware of and able to act on these events
example: incoming call indication, call cleared, call connected
WTA Repository
local store for content related to WTA services (minimize network traffic)
Channels: define the service
content format defining a WTA service stored in repository
XML document specifying eventid, title, abstract, and resources that
implement a service
Resources: execution scripts for a service
could be WML decks, WML Scripts, WBMP images..
downloaded from WTA server and stored in repository before service
is referenced
Server can also initiate download of a channel
WTA Channels and Resources
Source: Heijden
WTA Interface (public)
WTA Interface
generic, high-level interface to mobile’s telephony functions
setting up phone calls, reading and writing entries in phonebook..
Public WTAI
for third party WML content providers
restricted set of telephony functions available to any WAE User Agent
library functions
make call: allows application to setup call to a valid tel number
send DTMF tones: send DTMF tones through the setup call
user notified to grant permission for service execution
cannot be triggered by network events
example: Yellow pages service with “make call” feature
WTA Interface (network)
Network Common WTAI
WTA service provider is in operator’s domain
all WTAI features are accessible, including the interface to WTA events
library functions
Voice-call control: setup call, accept, release, send DTMF tones
Network text: send text, read text, remove text (SMS)
Phonebook: write, read, remove phonebook entry
Call logs: last dialed numbers, missed calls, received calls
Miscellaneous: terminate WTA user agent, protect context
user can give blanket permission to invoke a function
example: Voice mail service
Network Specific WTAI
specific to type of bearer network
example:
GSM: call reject, call hold, call transfer, join multiparty, send USSD
WTA Event Handling
Event occurrence
WTA user agent could be executing and expecting the event
WTA user agent could be executing and a different event occurs
No service is executing
Event handling
channel for each event defines the content to be processed upon
reception of that event
Event binding
association of an event with the corresponding handler (channel)
Global binding:
channel corresponding to the event is stored in the repository
event causes execution of resources defined by the channel
example: voice mail service
Temporary binding:
resources to be executed are defined by the already executing
service
example: yellow pages lookup and call establishment
Event Handling (no service in
execution)
Source: Heijden
Event Handling (service
already execution)
1: Temporary binding exists
2. No temporary binding and context is protected
3: No temporary binding and context is not protected
Source: Heijden
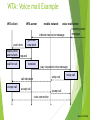
WTA: Voice mail Example
WTA client
WTA server
mobile network
voice mail server
incoming voice
message
indicate new voice message
push deck
display deck;
user selects
wait for call
accept call
generate
new deck
request
translate
play requested voice message
call indication
setup call
accept call
accept call
setup call
voice connection
Source: Schiller
WTA Application: Example (using WML)
<WML>
<CARD>
<DO TYPE="ACCEPT" TASK="GO" URL="#voteChamp"/>
Please vote for your champion!
</CARD>
<CARD NAME="voteChamp">
<DO TYPE="ACCEPT" TASK="GO"
URL="wtai://cc/sc;$voteNo;1"/>
Please choose:
<SELECT KEY="voteNo">
<OPTION VALUE="6086415">Mickey</OPTION>
<OPTION VALUE="6086416">Donald</OPTION>
<OPTION VALUE="6086417">Pluto</OPTION>
</SELECT>
</CARD>
</WML>
Source: Schiller
WTA: Example with WML and WMLScript
function voteCall(Nr) {
var j = WTACallControl.setup(Nr,1);
if (j>=0) {
WMLBrowser.setVar("Message", "Called");
WMLBrowser.setVar("No", Nr);
}
else {
WMLBrowser.setVar("Message", "Error!");
WMLBrowser.setVar("No", j);
}
WMLBrowser.go("showResult");
}
Source: Schiller
WTA: Example with WML and WMLScript
<WML>
<CARD>
<DO TYPE="ACCEPT" TASK="GO" URL="#voteChamp"/>
Please vote for your champion!
</CARD>
<CARD NAME="voteChamp">
<DO TYPE="ACCEPT" TASK="GO" URL="/script#voteCall($voteNo)"/>
Please choose:
<SELECT KEY="voteNo">
<OPTION VALUE="6086415">Mickey</OPTION>
<OPTION VALUE="6086416">Donald</OPTION>
<OPTION VALUE="6086417">Pluto</OPTION>
</SELECT>
</CARD>
<CARD NAME="showResult">
Status of your call: $Message $No
</CARD>
</WML>
Source: Schiller
WAP Push Services
Web push
Scheduled pull by client (browser)
no real-time alerting/response
example: stock quotes
Wireless push
accomplished by using the network itself
example: SMS
limited to simple text, cannot be used as starting point for service
example: Active Channels
example: if SMS contains news, user cannot request specific news item
WAP push
Network supported push of WML content
example: Alerts or service indications
Pre-caching of data (channels/resources)
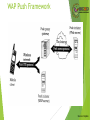
WAP Push Framework
Source: Heijden
Push Access Protocol
Based on request/response model
Push initiator is the client
Push proxy is the server
Initiator uses HTTP POST to send push message to proxy
Initiator sends control information as an XML document, and content
for mobile (as WML)
Proxy sends XML entity in response indicating submission status
Initiator can
cancel previous push
query status of push
query status/capabilities of device
Push Proxy Gateway
WAP stack (communication with mobile device)
TCP/IP stack (communication with Internet push initiator)
Proxy layer does
control information parsing
content transformation
session management
client capabilities
store and forward
prioritization
address resolution
management function
Over the Air (OTA) Protocol
Extends WSP with push-specific functionality
Application ID uniquely identifies a particular application in
the client (referenced as a URI)
Connection-oriented mode
Connectionless mode
client informs proxy of application IDs in a session
well known ports, one for secure and other for non-secure
push
Session Initiation Application (SIA)
unconfirmed push from proxy to client
request to create a session for a specific user agent and bearer
WAE Summary
WML
WMLScript
analogous to JavaScript
features of compiler in the network
WTA
analogous to HTML (optimized for wireless)
event based, microbrowser user agent
WTAI: different access rights for different applications/agents
WTA User Agent (analogy with operating systems)
Context – Activation Record
Channel – Interrupt Handler
Resource – Shared routines invoked by interrupt handlers
Repository – Library of interrupt handlers
feature of dynamically pushing the interrupt handler before the event
Push
no analogy in Internet
WAP Gateway Summary
Encoders
Filters
translate between binary (WML) and text (HTML/WML)
transcoding between WML (wireless) and HTML (wired)
Method Proxy
similar to standard proxy services
WAP stack on wireless interface and TCP/IP stack on Internet interface
Push Proxy
Push Access Protocol with Internet Push Initiator (Web Server)
Over the Air Protocol with mobile device (and WAP Push Initiator)
Performs necessary filtering, translation etc.
WAP Servers Summary
Origin Server
Web server with HTML/WML contents
Runs TCP/IP stack, needs PAP protocol for push, no end-to-end security
WAP Server
Serves WML content
Runs WAP stack, uses OTA protocol for push, end-to-end security possible
WTA Server
Specialized for telephony applications (runs WAP stack, uses push
extensively)
Client initiated (make call “hyperlink” from a Yellow pages service)
Server intiated (incoming call from a Voice mail service)
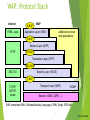
WAP: Protocol Stack
Internet
HTML, Java
A-SAP
WAP
Application Layer (WAE)
S-SAP
additional services
and applications
Session Layer (WSP)
HTTP
TR-SAP
Transaction Layer (WTP)
SEC-SAP
SSL/TLS
Security Layer (WTLS)
T-SAP
TCP/IP,
UDP/IP,
media
Transport Layer (WDP)
WCMP
Bearers (GSM, CDPD, ...)
WAE comprises WML (Wireless Markup Language), WML Script, WTAI etc.
Source: Schiller
WDP: Wireless Datagram
Goals
Protocol
create a worldwide interoperable transport system by adapting WDP
to the different underlying technologies
transmission services, such as SMS in GSM might change, new services
can replace the old ones
WDP
Transport layer protocol within the WAP architecture
uses the Service Primitive
T-UnitData.req .ind
uses transport mechanisms of different bearer technologies
offers a common interface for higher layer protocols
allows for transparent communication despite different technologies
addressing uses port numbers
WDP over IP is UDP/IP
WDP: Service Primitives
T-SAP
T-DUnitdata.req
(DA, DP, SA, SP, UD)
T-SAP
T-DUnitdata.ind
(SA, SP, UD)
T-DUnitdata.req
(DA, DP, SA, SP, UD)
T-DError.ind
(EC)
SAP: Service Access Point
DA: Destination Address
DP: Destination Port
SA: Source Address
SP: Source Port
UD: User Data
EC: Error Code
Source: Schiller
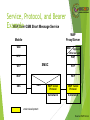
Service, Protocol, and Bearer
Example
WAP Over GSM Circuit-Switched
WAP
Proxy/Server
Mobile
WAE
WSP
IWF
ISP/RAS
WAE
Apps on
Other Servers
WSP
WTP
WTP
UDP
UDP
IP
PPP
CSD-RF
IP
IP
PSTN Subnetwork
Circuit
Subnetwork
PPP
CSDRF
PSTN
Circuit
RAS - Remote Access Server
IWF - InterWorking Function
Source: WAP Forum
Service, Protocol, and Bearer
WAP Over GSM Short Message Service
Example
WAP
Proxy/Server
Mobile
WAE
WAE Apps on
other servers
WSP
WSP
SMSC
WTP
WDP
SMS
WTP
WDP
SMS
WDP Tunnel
Protocol
WDP Tunnel
Protocol
Subnetwork
Subnetwork
under development
Source: WAP Forum
WTLS:Wireless Transport
Goals Security
Layer
Provide mechanisms for secure transfer of content, for applications
needing privacy, identification, message integrity and non-repudiation
Provide support for protection against denial-of-service attacks
WTLS
is based on the TLS/SSL (Transport Layer Security) protocol
optimized for low-bandwidth communication channels
provides
privacy (encryption)
data integrity (MACs)
authentication (public-key and symmetric)
Employs special adapted mechanisms for wireless usage
Long lived secure sessions
Optimised handshake procedures
Provides simple data reliability for operation over datagram
bearers
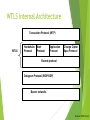
WTLS Internal Architecture
Transaction Protocol (WTP)
WTLS
Handshake
Protocol
Alert
Protocol
Application
Protocol
Change Cipher
Spec Protocol
Record Protocol
Record protocol
Datagram Protocol (WDP/UDP)
Bearer networks
Source: WAP Forum
WTLS: Secure session, Full handshake
originator
SEC-SAP
SEC-Create.req
(SA, SP, DA, DP, KES, CS, CM)
peer
SEC-SAP
SEC-Create.ind
(SA, SP, DA, DP, KES, CS, CM)
SEC-Create.res
(SNM, KR, SID, KES‘, CS‘, CM‘)
SEC-Create.cnf
(SNM, KR, SID, KES‘, CS‘, CM‘)
SEC-Exchange.ind
SEC-Exchange.res
(CC)
SEC-Commit.req
SEC-Commit.cnf
SEC-Exchange.req
KES: Key Exchange Suite
CS: Cipher Suite
CM: Compression Mode
SNM: Sequence Number Mode
SEC-Exchange.cnf
(CC)
SEC-Commit.ind
KR: Key Refresh Cycle
SID: Session Identifier
CC: Client Certificate
Source: Schiller
WTLS: Transferring Datagrams
sender
SEC-SAP
SEC-Unitdata.req
(SA, SP, DA, DP, UD)
receiver
SEC-SAP
SEC-Unitdata.ind
(SA, SP, DA, DP, UD)
Source: Schiller
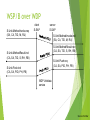
WTP: Wireless Transaction Protocol
Goals
different transaction services that enable applications to select reliability,
efficiency levels
low memory requirements, suited to simple devices (< 10kbyte )
efficiency for wireless transmission
WTP
supports peer-to-peer, client/server and multicast applications
efficient for wireless transmission
support for different communication scenarios
class 0: unreliable message transfer
unconfirmed Invoke message with no Result message
a datagram that can be sent within the context of an existing Session
class 1: reliable message transfer without result message
confirmed Invoke message with no Result message
used for data push, where no response from the destination is expected
class 2: reliable message transfer with exactly one reliable result message
confirmed Invoke message with one confirmed Result message
a single request produces a single reply
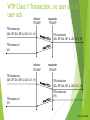
WTP Services and Protocols
WTP (Transaction)
provides reliable data transfer based on request/reply paradigm
no explicit connection setup or tear down
optimized setup (data carried in first packet of protocol exchange)
seeks to reduce 3-way handshake on initial request
supports
header compression
segmentation /re-assembly
retransmission of lost packets
selective-retransmission
port number addressing (UDP ports numbers)
flow control
message oriented (not stream)
supports an Abort function for outstanding requests
supports concatenation of PDUs
supports User acknowledgement or Stack acknowledgement option
acks may be forced from the WTP user (upper layer)
default is stack ack
WTP Class 0 Transaction
initiator
TR-SAP
TR-Invoke.req
(SA, SP, DA, DP, A, UD, C=0, H)
responder
TR-SAP
TR-Invoke.ind
(SA, SP, DA, DP, A, UD, C=0, H‘)
A: Acknowledgement Type
(WTP/User)
C: Class (0,1,2)
H: Handle (socket alias)
Source: Schiller
WTP Class 1 Transaction, no user ack &
user ack
initiator
responder
TR-SAP
TR-Invoke.req
(SA, SP, DA, DP, A, UD, C=1, H)
TR-SAP
TR-Invoke.ind
(SA, SP, DA, DP, A, UD, C=1, H‘)
TR-Invoke.cnf
(H)
initiator
TR-SAP
TR-Invoke.req
(SA, SP, DA, DP, A, UD, C=1, H)
TR-Invoke.cnf
(H)
responder
TR-SAP
TR-Invoke.ind
(SA, SP, DA, DP, A, UD, C=1, H‘)
TR-Invoke.res
(H‘)
Source: Schiller
WTP Class 2 Transaction, no
initiator
user ack, no TR-SAP
hold onresponder
TR-SAP
TR-Invoke.req
(SA, SP, DA, DP, A, UD, C=2, H)
TR-Invoke.cnf
(H)
TR-Invoke.ind
(SA, SP, DA, DP, A, UD, C=2, H‘)
TR-Result.req
(UD*, H‘)
TR-Result.ind
(UD*, H)
TR-Result.res
(H)
TR-Result.cnf
(H‘)
Source: Schiller
WTP Class 2 Transaction, user
initiator
responder
ack
TR-SAP
TR-SAP
TR-Invoke.req
(SA, SP, DA, DP, A, UD, C=2, H)
TR-Invoke.cnf
(H)
TR-Result.ind
(UD*, H)
TR-Result.res
(H)
TR-Invoke.ind
(SA, SP, DA, DP, A, UD, C=2, H‘)
TR-Invoke.res
(H‘)
TR-Result.req
(UD*, H‘)
TR-Result.cnf
(H‘)
Source: Schiller
WTP Class 2 Transaction, hold
on, no user ack
initiator
responder
TR-SAP
TR-Invoke.req
(SA, SP, DA, DP, A, UD, C=2, H)
TR-Invoke.cnf
(H)
TR-SAP
TR-Invoke.ind
(SA, SP, DA, DP, A, UD, C=2, H‘)
TR-Result.req
(UD*, H‘)
TR-Result.ind
(UD*, H)
TR-Result.res
(H)
TR-Result.cnf
(H‘)
Source: Schiller
WSP - Wireless Session Protocol
Goals
HTTP 1.1 functionality
Request/reply, content type negotiation, ...
support of client/server transactions, push technology
key management, authentication, Internet security services
WSP Services
provides shared state between client and server, optimizes content transfer
session management (establish, release, suspend, resume)
efficient capability negotiation
content encoding
push
WSP/B (Browsing)
HTTP/1.1 functionality - but binary encoded
exchange of session headers
push and pull data transfer
asynchronous requests
WSP Overview
Header Encoding
compact binary encoding of headers, content type identifiers and
other well-known textual or structured values
reduces the data actually sent over the network
Capabilities (are defined for):
message size, client and server
protocol options: Confirmed Push Facility, Push Facility, Session
Suspend Facility, Acknowledgement headers
maximum outstanding requests
extended methods
header code pages
Suspend and Resume
server knows when client can accept a push
multi-bearer devices
dynamic addressing
allows the release of underlying bearer resources
WSP Sessions
Session Context and Push
push can take advantage of session headers
server knows when client can accept a push
Connection-mode
long-lived communication, benefits of the session state,
reliability
Connectionless-mode
stateless applications, no session creation overhead, no
reliability overhead
WSP/B session establishment
client
S-SAP
server
S-SAP
S-Connect.req
(SA, CA, CH, RC)
S-Connect.ind
(SA, CA, CH, RC)
S-Connect.res
(SH, NC)
S-Connect.cnf
(SH, NC)
WTP Class 2
transaction
CH: Client Header
RC: Requested Capabilities
SH: Server Header
NC: Negotiated Capabilities
Source: Schiller
WSP/B session suspend/resume
client
S-SAP
server
S-SAP
S-Suspend.req
S-Suspend.ind
(R)
S-Suspend.ind
(R)
S-Resume.req
(SA, CA)
WTP Class 0
transaction
~
~
R: Reason for disconnection
S-Resume.ind
(SA, CA)
S-Resume.res
S-Resume.cnf
WTP Class 2
transaction
Source: Schiller
WSP/B session termination
client
S-SAP
server
S-SAP
S-Disconnect.req
(R)
S-Disconnect.ind
(R)
S-Disconnect.ind
(R)
WTP Class 0
transaction
Source: Schiller
WSP/B method invoke
client
S-SAP
server
S-SAP
S-MethodInvoke.req
(CTID, M, RU)
S-MethodInvoke.ind
(STID, M, RU)
S-MethodInvoke.res
(STID)
S-MethodInvoke.cnf
(CTID)
S-MethodResult.req
(STID, S, RH, RB)
S-MethodResult.ind
(CTID, S, RH, RB)
S-MethodResult.res
(CTID)
S-MethodResult.cnf
(STID)
CTID: Client Transaction ID
WTP Class 2
transaction
M: Method Invoked
RU: Request URI
STID: Server Transaction ID
S: Response Status
RH: Response Header
RB: Response BodySource: Schiller
WSP/B over WTP - method
client
initiator
responder
server
S-SAP
TR-SAP
TR-SAP
S-SAP
invocation
S-MethodInvoke.req TR-Invoke.req
TR-Invoke.ind S-MethodInvoke.ind
TR-Invoke.res S-MethodInvoke.res
S-MethodInvoke.cnf TR-Invoke.cnf
TR-Result.req S-MethodResult.req
S-MethodResult.ind
TR-Result.ind
S-MethodResult.res
TR-Result.res
TR-Result.cnf S-MethodResult.cnf
Source: Schiller
WSP/B over WTP - asynchronous,
unordered requests
client
server
S-SAP
S-SAP
S-MethodInvoke_1.req
S-MethodInvoke_2.req
S-MethodInvoke_2.ind
S-MethodInvoke_1.ind
S-MethodInvoke_3.req
S-MethodResult_1.ind
S-MethodResult_3.ind
S-MethodResult_1.req
S-MethodInvoke_3.ind
S-MethodResult_3.req
S-MethodResult_2.req
S-MethodInvoke_4.req
S-MethodInvoke_4.ind
S-MethodResult_4.ind
S-MethodResult_4.req
S-MethodResult_2.ind
Source: Schiller
WSP/B - confirmed/non-confirmed push
client
S-SAP
S-Push.ind
(PH, PB)
server
S-SAP
S-Push.req
(PH, PB)
WTP Class 0
transaction
PH: Push Header
PB: Push Body
SPID: Server Push ID
client
S-SAP
S-ConfirmedPush.ind
(CPID, PH, PB)
server
CPID: Client Push ID
S-SAP
S-ConfirmedPush.req
(SPID, PH, PB)
S-ConfirmedPush.res
(CPID)
S-ConfirmedPush.cnf
(SPID)
WTP Class 1
transaction
Source: Schiller
WSP/B over WDP
S-Unit-MethodInvoke.req
(SA, CA, TID, M, RU)
client
S-SAP
server
S-SAP
S-Unit-MethodInvoke.ind
(SA, CA, TID, M, RU)
S-Unit-MethodResult.req
(CA, SA, TID, S, RH, RB)
S-Unit-MethodResult.ind
(CA, SA, TID, S, RH, RB)
S-Unit-Push.req
(CA, SA, PID, PH, PB)
S-Unit-Push.ind
(CA, SA, PID, PH, PB)
WDP Unitdata
service
Source: Schiller
WAP Stack Summary
WDP
WTLS
functionality similar to UDP in IP networks
functionality similar to SSL/TLS (optimized for wireless)
WTP
Class 0: analogous to UDP
Class 1: analogous to TCP (without connection setup overheads)
Class 2: analogous to RPC (optimized for wireless)
features of “user acknowledgement”, “hold on”
WSP
WSP/B: analogous to http 1.1 (add features of suspend/resume)
method: analogous to RPC/RMI
features of asynchronous invocations, push (confirmed/unconfirmed)
WAP: Ongoing Work
WDP
Tunnel to support WAP where no (end-to-end) IP bearer available
WTLS
support for end-to-end security (extending WTLS endpoint beyond WAP
Gateway)
interoperable between WAP and Internet (public key infrastructure)
integrating Smart Cards for security functions
WTP
efficient transport over wireless links (wireless TCP)
bearer selection/switching
quality of service definitions
WSP
quality of service parameters
multicast data, multimedia support
WAE
User agent profiles: personalize for device characteristics, preferences etc
Push architecture, asynchronous applications
Billing
WAP: Hype vs Reality
Low-bandwidth wireless links
tcp/ip over wireless can also address these problems
encoding in http can also reduce data transfer on wireless links
Limited device capabilities
Microbrowser is appropriate to address this problem
WTAI features are not present in tcp/ip domain
Challenges in WAP
adapting to applications rich in content and interaction
service guarantees
interface design and usability
Other approaches for WWW access through mobiles
i-Mode (from NTT DoCoMo)
WAP is a TRAP (http://www.freeprotocols.org/wapTrap)
References and Resources
Books
Official Website (specifications)
www.palopt.com.au/wap
www.wap.net
Major players
www.wapforum.org
Technical/Developer Info and tools
Mobile communications: Jochen Schiller, Addison Wesley 2000
Understanding WAP:
www.nokia.com/wap
www.ericsson.se/wap
phone.com
OpenSource effort
www.wapgateway.org (Kannel WAP gateway project)
Thank You
This presentation is available online from
http://www.it.iitb.ernet.in/~sri/talks
Sridhar Iyer
KR School of Information Technology
IIT Bombay
WiFi
Is for “Wireless Fidelity”
Or
IEEE 802.11 Standard
WiFi
101
What is the goal of 802.11 standard ?
To develop a Medium Access Control (MAC)
and Physical Layer (PHY) specification for
wireless connectivity for fixed, portable and
moving stations within a local area.
WiFi
102
802.11 sub-standards(amendments ) ….
802.11
802.11b
802.11a
802.11g
802.11i
802.11e
802.11h
802.11h
MAC (Media Access Control)
PHY 2.4 GHz (max 11 Mbps)
PHY 5.0 GHz (max 54 Mbps)
PHY 2.0 GHz (max 54 Mbps)
Security
QoS, Multimedia
European regulations for 5GHz
Japan regulations for 5GHz
ratified 1999
ratified 1999
ratified 1999
ratified 2003
draft number XXX
draft number XXX
draft number XXX
draft number XXX
WiFi
103
Do I need any license to use 802.11 device ?
No , 2.4 GHz and 5.0 GHz are public
available frequency !!!
WiFi
104
Context with OSI layers
WiFi
105
Logical Link Control Services
WiFi
106
Standard 802.11 frame format
WiFi
107
Frames types and subtypes
Three types of frames:
Control
(ACK,RTS,CTS ,Power Save …)
Management
(Beacon,Probe Request ,Probe Response,
Association request , Association response …)
Data
(Data, Null Data, Data_CF_Ack , ….)
WiFi
108
802.11 MAC – Configuration summary – Infrastructure model
Infrastructure Model includes:
(most common)
BSS2
• Stations (STA)
– any wireless device
• Access Point (AP)
– connects BSS to DS
– controls access by STA’s
ESS1
• Basic Service Set (BSS)
– a region controlled by an AP
– mobility is supported within a
single BSS
• Extended Service Set (ESS)
– a set of BSS’s forming a virtual
BSS
– mobility is supported between
BSS’s in an ESS
• Distribution Service (DS)
– connection between BSS’s
AP2
AP3
DS
AP1
STA3
STA1
BSS3
BSS1
STA2
WiFi
109
The 802.11 MAC supports infrastructure
and ad hoc network models
Ad Hoc Model includes:
• Stations (STA)
– any wireless device
– act as distributed AP
STA1
• Independent Basic Service Set (IBSS)
– BSS forming a self contained
network
– no AP and no connection to the DS
STA3
STA2
IBSS
WiFi
110
Two types of access to air
DCF (distributed coordination function )
means everybody can speak and try
to get air : 100% on the market
PCF (point coordination function)
means ONE point coordinator (BOSS)
who will allowed you to speak
(like in bluetooth)
WiFi
111
Summary of required features and
difficulties vs 802.11 features
Features
High speed operation (PHY only)
Fair access (DCF, PCF)
Time-bounded access (PCF)
Flexible configuration (BSS, IBSS)
Security (WEP)
Mobility support (ESS)
Low power (PS)
Difficulties
Hidden terminals (RTS/CTS)
Capture (CSMA/CA, ACK)
Noise and interference (ACK, frag)
Limited spectrum (licencing, PHYs)
WiFi
112
The 802.11 MAC basic Distributed Coordination Function (DCF) access scheme
uses a CSMA/CA based protocol
If the STA detects the medium is busy when attempting to send a packet
then:
An STA may transmit a packet after sensing the medium is idle for an Inter
Frame Space (IFS) period
the STA starts a random back-off timer
the randomisation parameters depend on previous transmission
successes/failures
the back-off timer runs once the medium has been idle for an IFS period
the back-off timer suspends when the medium is busy and does not restart
until medium is idle for an IFS period
The STA may transmit when the back-off timer expires
The state (busy or idle) of the medium is determined using:
physical carrier sense
virtual carrier sense, based on reservations in received packets. These
reservations set the NAV timer. The medium is considered busy until the
NAV timer expires
WiFi
113
The 802.11 MAC basic Distributed Coordination Function (DCF) access scheme
uses a CSMA/CA based protocol
Medium busy
IFS
Contention
window
Send frame
IFS
Busy
Frame
Defer access
while busy
and for an IFS
period
WiFi
Decrement backoff when medium
idle for at least
IFS period
114
Acknowledgment
WiFi
115
Security
WEP ( wired equivalent privacy) 64/128 bits
Using RC4 algorithm, almost permanent key, very week
security, able to crack by collecting statistic
Current security level for 99.9% products on the market.
TKIP (temporal key integrity protocol )
Used RC4 algorithm with with a 128-bit "temporal key"
but changes temporal keys every 10,000 packets and key dependes
on address and sequence number.
Will be required to obtain WiFi certification from 09/01/03
AES (Advanced Encryption Standard )
New, much more stronger encryption, protect against hacker frames in
insertion. Need hardware accelerator. Optional feature.
WiFi
116
Why do we need 11A/11B/11G ?
11B: 2.4 GHz , CCK modulation
Rates from 1 to 11Mbps , on market from 1999
11A: 5.0 GHz , OFDM modulation
Rates from 6 to 56 Mbps , on market from 2002
11G: 2.4 GHz, CCK+OFDM modulation
Rates from 6 to 56 Mbps, on market from 2003 and …
most popular today !!!
Advantages of 2.4 GHz PHY:
Low frequency, better wall penetration, less sensitive to multipath
3 not-overlapped channels
Advantages of 5.0 GHz PHY:
Less devices on the market (no microwave, no blue tooth …)
8 not-overlapped channels
Range: almost the same …
WiFi
117
802.11 a/b/g performance
11A/G max throughput ~22 Mbps , not 54 Mbps (!!!)
11B max throughput ~6 Mbps
WiFi
118
Wlan market Scenarios
WiFi
119
IEEE 802.16 for MAN==Metropolitan Area Network
New alternative to DSL/Cable modems
IEEE 802.16 Progress
Work on 802.16 started in July 1999. Four years into its mission, the IEEE 802.16 Working
Group on Broadband Wireless Access has delivered a base and three follow-on standards.
IEEE 802.16 (“Air Interface for Fixed Broadband Wireless Access Systems”) was approved
in December 2001. This standard is for wireless MANs operating at frequencies between
10 and 66 GHz.
IEEE 802.16.2, published in 2001, specifies a “recommended practice” to address the
operation of multiple, different broadband systems in the 10-66 GHz frequency range.
In January of this year, the IEEE approved an amendment to 802.16, called 802.16a, which
adds to the original standard operation in licensed and unlicensed frequency bands from 211 GHz.
802.16c, which was approved in December 2002, is aimed at improving interoperability by
specifying system profiles in the 10-66 GHz range.
WiFi
120
802.11/802.16
WiFi
121
WiFi
122
WiFi
123
WiFi
124
What is WIMAX ?
WiMAX is an IP based, wireless broadband
access technology that provides performance
similar to 802.11/Wi-Fi networks with the
coverage and QOS (quality of service) of
cellular networks. WiMAX is also an acronym
meaning "Worldwide Interoperability for
Microwave Access (WiMAX).
What is WIMAX ?
WiMAX (Worldwide Interoperability for
Microwave Access) is a telecommunications
protocol that provides fixed and mobile Internet
access. The current WiMAX revision provides
up to 40 Mbit/s with the IEEE 802.16m update
expected to offer up to 1 Gbit/s fixed speeds.
What is WIMAX ?
The name "WiMAX" was created by the
WiMAX Forum, which was formed in June
2001 to promote conformity and
interoperability of the standard. The forum
describes WiMAX as "a standards-based
technology enabling the delivery of last mile
wireless broadband access as an alternative
to cable and DSL".
What is last mile operation ?
The "last mile" or "last kilometer" is the
final leg of delivering connectivity from a
communications provider to a customer. The
phrase is therefore often used by the
telecommunications and cable television
industries. The actual distance of this leg
may be considerably more than a mile,
especially in rural areas.
What is last mile operation ?
It is typically seen as an expensive challenge
because "fanning out" wires and cables is a
considerable physical undertaking. Because
the last mile of a network to the user is also
the first mile from the user to the world, the
term "first mile" is sometimes used.
Last mile
To solve the problem of providing enhanced
services over the last mile, some firms have
been mixing networks for decades. One
example is Fixed Wireless Access, where a
wireless network is used instead of wires to
connect a stationary terminal to the wireline
network.
What is Wimax ?
WiMAX is a wireless digital communications
system, also known as IEEE 802.16, that is
intended for wireless "metropolitan area
networks". WiMAX can provide broadband
wireless access (BWA) up to 30 miles (50 km) for
fixed stations, and 3 - 10 miles (5 - 15 km) for
mobile stations. In contrast, the WiFi/802.11
wireless local area network standard is limited in
most cases to only 100 - 300 feet (30 - 100m).
Integration with an IP-based network
Integration with an IP-based network
The WiMAX Forum has proposed an
architecture that defines how a WiMAX
network can be connected with an IP based
core network, which is typically chosen by
operators that serve as Internet Service
Providers (ISP); Nevertheless the WiMAX BS
provide seamless integration capabilities with
other types of architectures as with packet
switched Mobile Networks.
Integration with an IP-based network
The WiMAX forum proposal defines a number of components, plus
some of the interconnections (or reference points) between these,
labeled R1 to R5 and R8:
SS/MS: the Subscriber Station/Mobile Station
ASN: the Access Service Network[19]
BS: Base station, part of the ASN
ASN-GW: the ASN Gateway, part of the ASN
CSN: the Connectivity Service Network
HA: Home Agent, part of the CSN
AAA: Authentication, Authorization and Accounting Server, part of
the CSN
NAP: a Network Access Provider
NSP: a Network Service Provider
Integration with an IP-based network
It is important to note that the functional
architecture can be designed into various
hardware configurations rather than fixed
configurations. For example, the architecture is
flexible enough to allow remote/mobile stations
of varying scale and functionality and Base
Stations of varying size - e.g. femto, pico, and
mini BS as well as macros.
WiMAX installation
There are numerous devices on the market that
provide connectivity to a WiMAX network. These are
known as the "subscriber unit" (SU).
There is an increasing focus on portable units. This
includes handsets (similar to cellular smartphones);
PC peripherals (PC Cards or USB dongles); and
embedded devices in laptops, which are now
available for Wi-Fi services.
WiMAX installation
In addition, there is much emphasis by
operators on consumer electronics devices
such as Gaming consoles, MP3 players and
similar devices. It is notable that WiMAX is
more similar to Wi-Fi than to 3G cellular
technologies.
WiMAX installation
The WiMAX Forum website provides a list of
certified devices. However, this is not a
complete list of devices available as certified
modules are embedded into laptops, MIDs
(Mobile Internet devices), and other private
labeled devices.
WiMAX installation: Gateways
WiMAX gateway devices are available as
both indoor and outdoor versions from
several manufacturers. Many of the WiMAX
gateways that are offered by manufactures
such as Airspan, ZyXEL, Huawei, Motorola,
and Greenpacket are stand-alone self-install
indoor units. Such devices typically sit near
the customer's window with the best WiMAX
signal, and provide:
WiMAX installation: Gateways
An integrated Wi-Fi access point to provide the
WiMAX Internet connectivity to multiple
devices throughout the home or business.
Ethernet ports should you wish to connect
directly to your computer or DVR instead.
One or two PSTN telephone jacks to connect
your land-line phone and take advantage of
VoIP.
WiMAX installation: Gateways
Indoor gateways are convenient, but radio losses mean
that the subscriber may need to be significantly closer to
the WiMAX base station than with professionallyinstalled external units.
Outdoor units are roughly the size of a laptop PC, and
their installation is comparable to the installation of a
residential satellite dish. A higher-gain directional
outdoor unit will generally result in greatly increased
range and throughput but with the obvious loss of
practical mobility of the unit.
WiMAX installation: Dongles
There are a variety of USB dongles on the
market which provide connectivity to a
WiMAX network. Generally these devices are
connected to a notebook or netbook whilst
on the go. Dongles typically have
omnidirectional antennae which are of lowergain compared to other devices, as such
these devices are best used in areas of good
coverage.
WiMAX installation: Mobile phones
HTC announced the first WiMAX enabled
mobile phone, the Max 4G, on Nov 12th
2008.[12] The device was only available to
certain markets in Russia on the Yota
network.
WiMAX installation: Mobile phones
HTC and Sprint Nextel released the second WiMAX
enabled mobile phone, the EVO 4G, March 23, 2010
at the CTIA conference in Las Vegas. The device,
made available on June 4, 2010,[13] is capable of
both EV-DO(3G) and WiMAX(4G) as well as
simultaneous data & voice sessions. The device also
has a front-facing camera enabling the use of video
conversations.[14] A number of WiMAX Mobiles are
expected to hit the US market in 2011.
WiMAX installation: MAC (data link)
layer
The WiMAX MAC uses a scheduling algorithm
for which the subscriber station needs to
compete only once for initial entry into the
network. After network entry is allowed, the
subscriber station is allocated an access slot
by the base station. The time slot can enlarge
and contract, but remains assigned to the
subscriber station, which means that other
subscribers cannot use it.
WiMAX installation: MAC (data link)
layer
In addition to being stable under overload and
over-subscription, the scheduling algorithm can
also be more bandwidth efficient. The
scheduling algorithm also allows the base
station to control Quality of service (QoS)
parameters by balancing the time-slot
assignments among the application needs of
the subscriber station.
WiMAX Performance
As a standard intended to satisfy needs of
next-generation data networks (4G), WiMAX
is distinguished by its dynamic burst
algorithm modulation adaptive to the physical
environment the RF signal travels through.
Modulation is chosen to be more spectrally
efficient (more bits per OFDM/SOFDMA
symbol).
WiMAX Performance
That is, when the bursts have a high signal
strength and a high carrier to noise plus
interference ratio (CINR), they can be more
easily decoded using digital signal
processing (DSP).
WiMAX Performance
In contrast, operating in less favorable
environments for RF communication, the
system automatically steps down to a more
robust mode (burst profile) which means fewer
bits per OFDM/SOFDMA symbol; with the
advantage that power per bit is higher and
therefore simpler accurate signal processing
can be performed.
WiMAX vs. LTE
The more recent Long Term Evolution (LTE)
standard is a similar term describing a parallel
technology to WiMAX that is being developed
by vendors and carriers as a counterpoint to
WiMAX.
An example of Wireless competition
Korea launched Wimax at 2nd quarter of 2006
and then launched HSPA one quarter after
launched Wimax. At the end of 2008 there were
8.4 million HSPA subscribers and 350,000
Wimax subscribers in Korea. Almost all of
HSPA subscribers come from 2G and 3G users
who have been tempted to upgrade to new
devices by high subsidies, whereas Wimax
subscribers almost all are newcomers.
An example of wireless competition
Deployment of Wimax is still limited (spotted),
whereas there are well over 100 countries
where HSPA networks are deployed, and even
where there is no HSPA coverage there is
backward compatibility (using HSPA devices)
to pre-existing networks (GSM and WCDMA)
with a roaming infrastructure already in place
WiMAX statistics
As of October 2010, the WiMAX Forum
claims there are over 592 WiMAX (fixed and
mobile) networks deployed in over 148
countries.
Yota is the largest WiMAX network operator
in the world, but has announced that it will
move new network deployments to LTE and,
subsequently, change its existing networks
as well.
What is HSPA ?
High Speed Packet Access (HSPA) is an
amalgamation of two mobile telephony
protocols, High Speed Downlink Packet Access
(HSDPA) and High Speed Uplink Packet
Access (HSUPA), that extends and improves
the performance of existing WCDMA protocols.
A further standard, Evolved HSPA (also known
as HSPA+), was released late in 2008 with
subsequent adoption worldwide beginning in
2010.
WiMAX competitors
Within the marketplace, WiMAX's main
competition comes from existing, widely
deployed wireless systems such as UMTS,
CDMA2000, existing Wi-Fi and mesh
networking.
WiMAX competitors
Speed vs. Mobility of wireless systems: Wi-Fi, HSPA, UMTS, GSM
The future of wireless networks
In the future, competition will be from the
evolution of the major cellular standards to socalled 4G, high-bandwidth, low-latency, all-IP
networks with voice services built on top. The
worldwide move to 4G for GSM/UMTS and
AMPS/TIA (including CDMA2000) is the
3GPP Long Term Evolution effort.