* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download DCN-7-Network_Security
Computer and network surveillance wikipedia , lookup
Next-Generation Secure Computing Base wikipedia , lookup
Information security wikipedia , lookup
Airport security wikipedia , lookup
One-time pad wikipedia , lookup
Quantum key distribution wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Security and safety features new to Windows Vista wikipedia , lookup
Digital signature wikipedia , lookup
Public-key cryptography wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Web of trust wikipedia , lookup
Wireless security wikipedia , lookup
Cryptanalysis wikipedia , lookup
Unix security wikipedia , lookup
Certificate authority wikipedia , lookup
Mobile security wikipedia , lookup
Computer security wikipedia , lookup
Diffie–Hellman key exchange wikipedia , lookup
Cybercrime countermeasures wikipedia , lookup
Security-focused operating system wikipedia , lookup
Cryptography wikipedia , lookup
Distributed firewall wikipedia , lookup
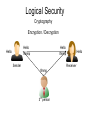
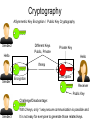
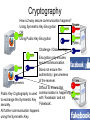
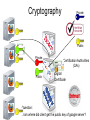
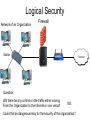
Security •Security: –Security means, •Protection against, –Some kind of Threat (Danger). Security •Security: –Scenario: Few years ago: •It was only about a Computer / PC security which was obtained by, –Using physical controls over access to computers. •Tools to secure computers were: –Alarmed Doors and Windows. –Security Guards. –Security Badges to admit people to sensitive areas. –Surveillance cameras. •Mainly dealing with, –Physical Security. –Scenario: Today: •It’s not about a Computer/PC security but, –All about Computer Network Security. •Physical security is just one aspect of security and, •Along with Physical security, one more aspect of security needs to be considered: –Logical Security Network Security •Network Security: –2 general types of security: •Physical Security: –Protection against physical threats/dangers such as: »Unauthorized Person such as Thief etc. »Unauthorized Device such as CD, Pen Drive etc. •Logical Security: –Protection against logical/software/electronic threats/dangers such as: »Viruses, Worms, Spywares etc. –Note: •Physical security is the first step to any kind of security because, –If a PC is not ‘Physically’ secure, it can never be secured ‘Logically’. Network Security •Physical Security: –Measures to control Physical Access to Networks and improve Physical Security: •Basic measures: –Locked Rooms, Security Alarms, CCTV Cameras, Security Badges for Authorized Persons. •Advanced measures: –Writing pads that detect the form and pressure of a person writing a signature. –Biometric Devices such as: »Fingerprint Scanner, Face Recognition, Eye/Retina Scanner, Palm Scanner. Network Security •Physical Security: –Apart from the normal physical security such as guards, surveillance systems, •Many companies maintain backup copies of server contents at a remote location. •In case of a disaster, –The operations can be switched over in a matter of seconds to the backup location. Network Security •Logical Security: –Need: •Internet/Network was always designed to be, –Redundant because, »Packets travel through different uncontrolled paths, •And was never designed to be, –Secure. –Hence ‘Logical Security’ is something which is, •Not a inherent (inbuilt) part of Network. Logical Security •Measures for Logical Security: –IDs and Passwords: •Provide authentication credentials to every user of the system in the form of: –IDs and Passwords •Even after successful login, –Allow access to only certain required applications by giving, »Selected ‘Rights/Permissions’ to the users. •Apply ‘Time-of-Day’ restrictions to users and applications so that, –Available on weekdays but offline on weekends. Logical Security •IDs and Passwords: –Tips to Select & Protect IDs and Passwords: •Select a password which is, –At least 8 characters long and, »Including all types of symbols such as lowercase, uppercase, numbers and special characters. •Password should be selected in such a way so that it is, –Not easily guessable/identifiable such as, »Name of spouse, children, phone number, as a password. •Change the passwords, –Periodically or at regular intervals. •Log (Store) and check all the unsuccessful login attempts and, –Block the ID if unsuccessful login attempts increase beyond a certain threshold (level) because, –A pattern of attempted but unsuccessful logins might signal that an unauthorized user is trying to access the network. Logical Security Cryptography Encryption / Decryption Hello Ifmmp Hello Hello Ifmmp Sender Hello Receiver Ifmmp 3rd person Encryption (Example) Key: VIOLIN Algorithm: SENDER Transfer One Lakh Rupees To Account 756 Encryption 6 1 5 3 2 4 V I T r e r L R u T c o 7 5 O L I a n s O n a k h p e e o A u n t 6 N f e RECEIVER Transfer One Lakh Rupees To Account 756 s c Decryption rrLuTo5snheAt nOke n fe sc a apou6Te R c7 Logical Security •Measures for Logical Security: –Encryption: •Coding / Locking of information by using: –A mathematically based program (Algorithm) AND –A secret key, »To produce a string of characters that is, »Unintelligible (Not understandable). •Similar to, –Scrambling that is done on the premium cable channels. –If the cable user pays an extra fee, »The cable company unscrambles the signal for that user by, »Sending over the KEY. Logical Security •Measures for Logical Security: –Cryptography: •Science that studies encryption / decryption. •Comes from 2 Greek words: –krypto: secret –grapho: writing Cryptography Symmetric Key Encryption / Private Key Cryptography Plaintext Ciphertext Hello Hello Ifmmp Sender Encryption Same Keys & Private Decryption Receiver Advantage: Anyone can easily generate a Symmetric Key. 2-way secure communication is possible using a single Symmetric Key. Challenge/Disadvantage: Difficult to exchange ‘KEY’ itself securely at the first place. Cryptography ASymmetric Key Encryption / Public Key Cryptography Sender2 Different Keys Public, Private Hello Private Key Hello Ifmmp Sender1 Encryption Decryption Receiver Public Key Challenge/Disadvantage: Sender3 With 2 keys, only 1 way secure communication is possible and It is not easy for everyone to generate those related keys. Logical Security •Cryptography: –Symmetric/Private Key Cryptography: •Uses a single key for, –Encryption and Decryption, which must be kept, –Private (Secret) between the Sender and the Receiver. •Challenge/Disadvantage: –Difficult to share the Private Key securely at the first place. •Examples: –DES: Data Encryption Standard. »56 bit encryption key. »Could be broken by a fast computer in 6 minutes. –3DES: Triple DES. »Key Length: 112 bits. –AES: Advanced Encryption Standard. »Key Length: 256 bytes = 2048 bits. »Takes 150 trillion years to break the key. –Blowfish, IDEA (International Data Encryption Algorithm) etc. Logical Security •Cryptography: –Asymmetric/Public Key Cryptography: •Uses 2 different (mathematically related) keys for, –Encryption and Decryption where, »Encryption is done using Receiver’s Public Key and, »Decryption is done using Receiver’s Private Key. •Data encrypted using receiver’s Public Key can only be decrypted using, –Receiver’s Private Key and cannot be decrypted using, –The same Public Key. •Examples: –RSA: Ron Rivest, Adi Shamir, Leonard Adleman. »Key Length: 1024 bit •For more detailed information, click here. Cryptography How a 2-way secure communication happens? Private Using Symmetric Key Encryption OR Using Public Key Encryption Public Challenge / Disadvantage: Encryption only ensures secure communication. Symmetric Does not ensure the authenticity / genuineness of the receiver. Private Difficult to ensure that Public Key Cryptography is used communication is happening Public to exchange the Symmetric Key with ‘Facebook’ and not ‘Fakebook’. securely. All further communication happens using the Symmetric Key. Cryptography ASymmetric Key Encryption / Public Key Cryptography Digital Signature Keys Private Student1 Public HOD Private Student2 Faculty Public Encryption: Done using the private key. Student3 Decryption: Done using the public key. Cryptography Private Public Private Public Certification Authorities (CAs) Digital Certificate Question: From where did client get the public key of google server? Cryptography 1. Clients sends a request. SSL (HTTPS) Communication 2. Server sends a response in the form of its Digital Certificate issued by some Certification Authority (CA). Digital Certificate is encrypted by the Private Key of CA. 3. Client decrypts the Digital Certificate using the preloaded Public Key of CA and extracts information such as Name of Server, Address of Server, Public Key of Server, Expiry Date of Certificate etc. 4. Client generates a unique Symmetric Key and sends it to the Server by encrypting it using Public Key of Server. 5. Server decrypts the Symmetric Key using the Private Key of Server. 6. Then communication happens between Client and Server using the Symmetric Key. SSL (HTTPS) Communication SSL (HTTPS) Communication Logical Security •Asymmetric/Public Key Cryptography: –Digital Signature: •A method for, –Showing the authenticity (genuineness) of a message or document. •A valid digital signature gives a receiver a reason to believe that, –Authentication: »Message was created by a known sender. –Non-Repudiation: »Sender cannot deny having sent the message. –Integrity: »Message was not altered in transit. •Commonly used for, –Software distribution, Financial transactions etc. Logical Security •Digital Certificates / Digital ID: –A functionality that: •Verifies that a sender (Web site) is who or what it claims to be. –Serves the same function as a: »Driving license »Passport –Although it does not say one thing: •About the usefulness or quality of the downloaded program. –Only supplies a level of assurance that the software is genuine. Logical Security •Digital Certificates: –Issued to organizations or individuals by an agency called: •Certification authority (CA). –Examples: »Thawte »VeriSign »Entrust »Equifax Secure –Entities must supply appropriate proof of identity when applying for digital certificates. •Once the CA is satisfied, it issues the certificate. Logical Security •Digital Certificates: –Includes following elements: •Certificate owner’s identifying information such as name, organization, address. •Certificate owner’s public key. •Dates between which the certificate is valid. •Serial number of the certificate. •Name of the certificate issuer (Certification Authority). Logical Security Network of an Organization Firewall Switch Question: Will there be any control on the traffic either moving From the Organization to the Internet or vice versa? NO. Could this be dangerous/risky for the security of the organization? Logical Security •Firewall: –Entity which is placed at the, •Entry/Exit point of the networks to, –Provide a defense between, »A network and the Internet and, –Control the data traffic moving through it. –Acts as a, •Filter which can distinguish/identify, –Good from the Bad, –Allowed from Denied, •According to the, –Rules/Configurations/Policies set in a Firewall. –Similar to, •Scanning machine kept at the Malls / Airports. •Ozone layer of the atmosphere. Firewall •Characteristics of a Firewall: –1) All traffic from inside to outside and from outside to inside the network, •Must pass through the firewall. –2) A firewall should obstruct/block/stop, •All the unauthorized traffic. –3) A firewall should not obstruct/block/stop, •Any legitimate users. Firewall •Characteristics of a Firewall: –4) The firewall itself should be immune to penetration. •Firewalls should not have any unnecessary software installed. –Should be used only as a firewall and not as a general-purpose computing machine. »Only essential OS and firewall-specific protection software should remain on the computer. –Having fewer software programs on the system means: »Less chances of security breaches. •Access to a firewall should only be restricted to: –Physical Access (Not remote access) Firewall •Types of Firewalls: –Classified into following categories: •Application-level Firewall. •Packet-level Firewall. Firewall •Types of Firewalls: –Application-level Firewall: •Filter traffic based on the application requested. –Allow/Deny access to specific applications such as, »FTP, HTTP etc. •Example of Application-level policy: –Allows Incoming FTP requests but Blocks Outgoing FTP requests. –Allows Incoming HTTP requests but Blocks Outgoing HTTP requests. Firewall •Types of Firewalls: –Packet-level Firewall: •Works as IP level filter. •Examines/Checks the source and destination addresses and ports of incoming packets and, –Allows or denies entrance to the packets based on a set of rules. •Example: –Allow IP address 192.168.1.1 to go through but disallow IP address 192.168.10.10. Logical Security Firewall Home User Can a home user afford a dedicated machine for a Firewall? NO. Software Firewall: Windows Firewall, Norton Internet Security etc. Network Security •References: –http://content.hccfl.edu/pollock/AUnixSec/P ublicKeyDemo.htm –http://www.youtube.com/watch?v=Ao5pMF e9fHU