* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Security
Buffer overflow protection wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Wireless security wikipedia , lookup
Next-Generation Secure Computing Base wikipedia , lookup
Trusted Computing wikipedia , lookup
Authentication wikipedia , lookup
Password strength wikipedia , lookup
Electronic authentication wikipedia , lookup
Web of trust wikipedia , lookup
Computer security wikipedia , lookup
Antivirus software wikipedia , lookup
Security and safety features new to Windows Vista wikipedia , lookup
Cryptanalysis wikipedia , lookup
Security-focused operating system wikipedia , lookup
Cryptography wikipedia , lookup
Computer virus wikipedia , lookup
Post-quantum cryptography wikipedia , lookup
History of cryptography wikipedia , lookup
Mobile security wikipedia , lookup
Chapter 9
Security
9.1 The security environment
9.2 Basics of cryptography
9.3 User authentication
9.4 Attacks from inside the system
9.5 Attacks from outside the system
9.6 Protection mechanisms
9.7 Trusted systems
1
Security Environment
• Security refers to the overall security problem.
• Protection mechanisms refers to the specific
operating system mechanisms used to safeguard
information in the computer.
• Threats to computer systems:
– Data confidentiality is concerned with having
secret data remain secret.
– Data integrity means that unauthorized users
should not be able to modify any data without the
owner’s permission.
– System availability means that nobody can disturb
the system to have it unusable.
2
The Security Environment
Threats
• From a security perspective, computer systems
have three general goals.
Security goals and threats
3
Intruders
Common Categories
1. Casual prying by nontechnical users
2. Snooping by insiders
3. Determined attempt to make money
4. Commercial or military espionage
4
Accidental Data Loss
•
Valuable data can be lost by accident.
Common Causes:
1. Acts of God
-
fires, floods, wars
2. Hardware or software errors
-
CPU malfunction, bad disk, program bugs
3. Human errors
-
data entry, wrong tape mounted
5
Basics of Cryptography
• The purpose of cryptography is to take a
message or a file, called the plaintext, and
encrypt it into the ciphertext in such a way that
only authorized people know how to convert it
back to the plaintext.
• The secrecy depends on parameters to the
algorithms called keys.
6
Basics of Cryptography
Relationship between the plaintext and the ciphertext
7
Secret-Key Cryptography
• Substitute Cipher: each letter or group of letter is
replaced by another letter or group of letters
– Caesar cipher: rotate the letter (a D, b E, c F, z
C).
• Example: attack DWWDFN
– Monoalphabetic substitution
• Each letter replaced by different letter
Plaintext: ABCDEFGHIJKLMNOPQRSTUVWXYZ
Ciphertext: QWERTYUIOPASDFGHJKLZXCVBNM
• Disadvantage: It does not smooth out frequencies in the cipher text.
– Polyalphabatic cipher – use multiple cipher alphabets.
8
Secret-Key Cryptography
• Transposition cipher: reorder the letters, but don't
disguise them.
– select a key
MEGABUCK
74512836
plea se tr
ansfe ron
ehundred
afnsedtoelnhesurndpaeerr
Plain text cipher text
9
Transposition Ciphers
• A transposition cipher.
10
Secret-Key Cryptography
• Given the encryption key,
– easy to find decryption key
• Secret-key cryptography is called symmetric-key
cryptography because they used the same key for
encryption and decryption.
• The data encryption standard (DES):
– block cipher adopted by the US Government in Jan. 1977.
– encryption based on 56-bit key.
• The Advanced Encryption Standard (AES)
– In November 2001, Rijndael become US Government
Standard.
11
Public-Key Cryptography
• Public-key cryptography has the property:
– Distinct keys are used for encryption and
decryption.
– Given a well-chosen encryption key, it is virtually
impossible to discover the corresponding decryption
key.
• The encryption key can be made public and
only the private decryption key kept secret.
12
Public-Key Cryptography
• Public-key cryptography uses an encryption
algorithm E and a decryption algorithm D such
that deriving D is effectively impossible even
with a complete description of E. You can
encrypt without knowing how to decrypt.
• Requirements:
– D (E(P)) = P
– It is extremely difficult to deduce the decryption key
from the encryption key.
– E cannot be broken by a plaintext attack.
13
Public-Key Cryptography
• All users pick a public key/private key pair
– publish the public key
– private key not published
• Public key is the encryption key
– private key is the decryption key
14
Public-Key Cryptosystems: RSA
• RSA, named after its inventors Rivest, Shamir, and
Adlemean, a public-key cryptographic algorithm.
• The security of RSA comes from the fact that no
methods are known to efficiently find the prime
factors to large numbers.
• For example, 2100 can be written as 2100 = 2 x 2 x 3 x
5 x 5 x 7 making 2, 3, 5, and 7 the prime factors in
2100.
• In RSA, the private and public keys are constructed
from very large prime numbers. It turns out breaking
RSA is equivalent to finding those two prime numbers.
15
Public-Key Cryptography
• RSA (Rivest, Shamir, Adleman) Algorithm:
– choose 2 large primes, p and q > 10^100.
– compute n=pq and z=(p-1)(q-1).
– choose a number relatively prime to z (that is, such
that d has no common factors with z ) and call it d.
– find e such that e x d mod z = 1.
• Group P into blocks such that C=Pe (mod n) and
P=Cd(mod n) where 0 <= P < n
16
Public-Key Cryptography
• Example:
p=13 q=17 n = 13 x 17 = 221
z = (13 – 1) x (17 – 1) = 192.
let d=5 (prime to z)
e x d = 1 mod 192 = 1, 193, 385, ...
385 is divisible by d
e = 385/5 = 77
• Example:
p=3 q=11 n = 3 x 11 = 33
z = (3 – 1) x (11 – 1) = 20.
let d=7 (prime to z)
7 x e mod 20 = 1 e=3
C = P3 (mod 33), P = C7 (mod 33)
17
RSA
• An example of the RSA algorithm.
18
Pretty Good Privacy (PGP)
• Pretty Good Privacy (PGP) is a popular program used
•
•
•
•
to encrypt and decrypt e-mail over the Internet.
It can also be used to send an encrypted digital
signature that lets the receiver verify the sender's
identity and know that the message was not changed en
route.
Available both as freeware and in a low-cost
commercial version,
PGP is the most widely used privacy-ensuring program
by individuals and is also used by many corporations.
Developed by Philip R. Zimmermann in 1991, PGP has
become a de facto standard for e-mail security.
PGP can also be used to encrypt files being stored so
that they are unreadable by other users or intruders. .
19
One-Way Functions
• Function such that given formula for f(x)
– easy to evaluate y = f(x)
• But given y
– computationally infeasible to find x
• Example: Those functions used in publickey cryptography.
20
Digital Signatures
• Digital signatures make it possible to sign email
messages and other digital documents in such a way
that they cannot be repudiated by the sender later.
• Steps to use digital signatures:
– The sender runs the document through a one-way hashing
algorithm
– The sender applies his private key to the hash to get
D(hash). This is called the signature block.
– The receiver computes the hash of the document using MD5
or SHA and then applies the sender’s public key to the
signature block to get E(D(hash)). Compare these two.
21
Digital Signatures
(b)
• Computing a signature block
• What the receiver gets
22
Digital Signatures
• The most popular hashing functions used are:
– MD5 (Message Digest)
– SHA (Secure Hash Algorithm)
• The public key is usually published. To avoid
altering, message senders can attach a
certificate to the message, which contains:
– The user’s name
– The public key
– Digitally singed by a trusted third party
23
User Authentication
•
Basic Principles. Authentication must
identify:
1. Something the user knows
2. Something the user has
3. Something the user is
•
•
In the computer world, hacker is a term of
honor reserved for great programmers.
Crackers are those who try to break into
computer systems where they do not belong.
24
Authentication Using Passwords
• The most widely used form of authentication is
to require the user to type a login name and a
password.
• Selecting Good Passwords make it difficult for
a cracker to guess.
• In the following, which is the better practice?
25
Authentication Using Passwords
(a) A successful login
(b) Login rejected after name entered
(c) Login rejected after name and password typed
26
How crackers break in?
• Locate machines:
– War dialers dial telephone exchange (770-xxxx).
– Use ping to test if some computer is up and running.
• Guess password
• Become superuser.
• Install a packet sniffer, software that examines all
incoming and outgoing network packets.
• Real hackers refer to those who are just running
scripts they found on the Internet as script kiddies.
27
Authentication Using Passwords
• How a cracker broke into LBL
– a U.S. Dept. of Energy research lab
28
UNIX Password Security
• UNIX Password Security:
– The login program asks the user to type his name
and password.
– The login program then reads the password file
until it finds the line containing the user’s login
name. If the password matches, the login is
permitted.
• Improvement: Associate an n-bit random
number, called the salt, with each password.
29
Improving Password Security
• The password program might complaint:
– Passwords should be a minimum of seven
characters.
– Passwords should contain both upper and lower
case letters.
– Passwords should contain at least one digit or
special character.
– Passwords should not be dictionary words, people’s
names, etc.
• One-time passwords
• Challenge-response authentication
30
Authentication Using Passwords
,
,
,
,
Salt
Password
The use of salt to defeat precomputation of
encrypted passwords
31
Authentication Using a Physical
Object
• Information-bearing plastic cards come in two
varieties:
– Magnetic stripe cards
– Chip cards
• Stored value cards
• Smart cards
• Smart cards:
– Advantages:
• They do not need an online connection to a bank.
• Secure login authentication.
– Disadvantages:
• Fixed cryptographic protocol could be broken.
• Slower operation
32
Authentication Using a Physical Object
• Magnetic cards
– magnetic stripe cards
– chip cards: stored value cards, smart cards
33
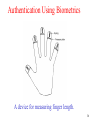
Authentication Using Biometrics
• Biometrics are physical characteristics of the
user that are hard to forge.
• A biometrics system has two parts:
– Enrollment – Biometrics is stored in a database or a
smart card.
– Identification – the user shows up and provides a
login name.
34
Authentication Using Biometrics
• Examples:
–
–
–
–
–
–
–
Finger length
Fingerprint
Retinal pattern analysis
Signature analysis
Voice recognition
Urinate sample
DNA analysis
35
Authentication Using Biometrics
A device for measuring finger length.
36
Countermeasures
•
•
•
•
•
Limiting times when someone can log in
Automatic callback at number prespecified
Limited number of login tries
A database of all logins
Simple login name/password as a trap
– security personnel notified when attacker bites
37
Operating System Security
Trojan Horses
• Free program made available to unsuspecting user
– Actually contains code to do harm
• Place altered version of utility program on victim's
computer
– trick user into running that program
38
Login Spoofing
(a) Correct login screen
(b) Phony login screen
39
Logic Bombs and Trap Doors
• A logic bomb is a piece of code written by
company programmer:
– potential to do harm
– OK as long as he/she enters password daily
– If programmer is fired, no password and bomb
explodes
• A trap door is the code inserted into the system
by a system programmer to bypass some normal
check.
– Solution: code reviews
40
Trap Doors
(a) Normal code.
(b) Code with a trapdoor inserted
41
Buffer Overflow
• Most systems are written in C. No C compiler
does array bounds checking.
• Overflow could point to an invalid address or
even an executable code.
• It is difficult to fix because there are so many
existing C programs around that do not check
for buffer overflow.
42
Buffer Overflow
• (a) Situation when main program is running
• (b) After program A called
• (c) Buffer overflow shown in gray
43
Generic Security Attacks
• To test a system’s security is to hire a group of experts,
known as tiger teams or penetration teams, to see if
they can break in.
• When designing a system, it should withstand typical
attacks:
–
–
–
–
–
–
–
Request memory, disk space, tapes and just read
Try illegal system calls
Start a login and hit DEL, RUBOUT, or BREAK
Try modifying complex OS structures
Try to do specified DO NOTs
Convince a system programmer to add a trap door
Beg administrator’s secretary to help a poor user who forgot
password
44
Famous Security Flaws
• UNIX
– lpr: remove the password file
– Force core dump on the password file
– Use some root related command such as mkdir
• TENEX for DEC-10 computers
– Carefully position a password to cause the page
fault for each character input
• OS/360
– During the password verification, wind the tape to
read the unauthorized file
45
Famous Security Flaws
(a)
(b)
(c)
The TENEX – password problem
46
Design Principles for Security
1.
2.
3.
4.
5.
System design should be public
Default should be no access
Check for current authority
Give each process least privilege possible
Protection mechanism should be
-
simple
uniform
in lowest layers of system
6. Scheme should be psychologically acceptable
• Keep the design simple
47
Network Security
• External threat
– code transmitted to target machine
– code executed there, doing damage
• Goals of virus writer
– quickly spreading virus
– difficult to detect
– hard to get rid of
• Virus is a program can reproduce itself
– By attaching its code to another program
– additionally, do harm
• Worms are programs which can self replicate
without attaching to other program.
48
Virus Damage Scenarios
• Blackmail (encrypt your files and ask for money)
• Denial of service as long as virus runs
main() {while (1) fork();}
• Permanently damage hardware (Overwrite BIOS)
• Target a competitor's computer
– do harm (reduce product quality)
– espionage (steal industrial secret)
• Intra-corporate dirty tricks
– sabotage another corporate officer's files (then get
promoted)
49
How Viruses Work
• Virus written in assembly language
• Inserted into another program
– use tool called a “dropper” to attach the
virus to another program.
• Virus dormant until program executed
– then infects other programs
– eventually executes its “payload”
– The payload may do nothing until a certain
date has passed.
50
How Viruses Work
• Seven kinds of virus based on what is
infected:
– Companion: prog.com, prog.exe
– Executable program
– Memory
– Boot sector
– Device driver
– Macro
– Source code
51
How Viruses Work
• Executable program viruses
– Overwriting viruses are viruses that
overwrite the executable program with
itself.
– Parasitic viruses are viruses attach
themselves to the program and do their dirty
work, but allow the program to function
normally afterward.
– Cavity viruses are viruses which hide itself
in the memory holes.
52
How Viruses Work
• Recursive
procedure
that finds
executable
files on a
UNIX
system
• Virus could
infect (or
attach virus
to) them all
53
How Viruses Work
•
•
•
•
An executable program
With a virus at the front
With the virus at the end
With a virus spread over free space within program
54
Viruses
• A memory-resident virus stays in memory
all the time.
• A virus that resides in the master boot record
or boot sector is called boot sector virus.
• A device virus is the virus that infects a
device drivers.
• A micro virus is a micro attached to the
document.
• A source code virus is the virus code
included in a program source code.
#include <virus.h>
55
How Viruses Work
•
•
•
After virus has captured interrupt, trap vectors
After OS has retaken printer interrupt vector
After virus has noticed loss of printer interrupt vector
and recaptured it
56
How Viruses Spread
• Virus placed where likely to be copied
• When copied
– infects programs on hard drive, floppy
– may try to spread over LAN
• Attach to innocent looking email
– when it runs, use mailing list to replicate
57
Antivirus and Anti-Antivirus Techniques
• A goat file is a program that does nothing but is
infected by a virus.
• Use goat file to create the profile of a virus and insert it
into the virus database.
• Virus scanners scan every executable file or some
specific types of files to locate the virus.
• The anitvirus program can detect file infection by
comparing the file length.
• A virus that mutates on each copy is called a
polymorphic virus.
• A piece of code that can mutate a sequence of machine
instructions without changing its functionality is called
mutation engine.
58
Antivirus and Anti-Antivirus Techniques
(a) A program
(b) Infected program
(c) Compressed infected program
(d) Encrypted virus
(e) Compressed virus with encrypted compression code
59
Antivirus and Anti-Antivirus Techniques
Examples of a polymorphic virus
All of these examples do the same thing
60
Antivirus and Anti-Antivirus Techniques
• Integrity checkers use the checksum to identify
an infected file.
• Behavioral checkers stay in memory and try to
catch virus.
• Virus avoidance: better safe than sorry.
–
–
–
–
–
good OS
install only shrink-wrapped software
use antivirus software
do not click on attachments to email
frequent backups
61
Antivirus and Anti-Antivirus Techniques
• The industry should do:
– Make simple operating system
– Forget active content
– There should be a way to selectively write protect
specified disk cylinders to prevent viruses from
infecting the programs on them.
– Flash ROM is a nice idea, but it should only be
modifiable when an external toggle switch has
been flipped.
• Recovery from virus attack
– halt computer, reboot from safe disk, run antivirus
62
The Internet Worm
• Nov. 2, 1988 a Cornell graduate student,
Robert Tappan Morris, released a worm
program into the Internet.
• Consisted of two programs
– bootstrap to upload worm
– the worm itself
• Worm first hid its existence.
• Next replicated itself on new machines
– Run a remote shell using the rsh command
– Overflow finger daemon to execute sh.
– Use sendmail to mail a copy of the bootstrap and
get it executed.
63
The Internet Worm
• Morris was caught when one of his friends
spoke with the New York Times computer
reporter, John Markoff, and tried to convince
Markoff that the incident was an accident.
• Morris was tried and convicted in federal
court. He was sentenced to a fine of $10,000,
3 years probation, and 400 hours of
community service.
• The CERT (Computer Emergency
Response Team) is established thereafter.
• What is Morris doing now?
64
Mobile Code
• Many Web pages contain small programs
called applets to be fetched and
executed.
• Agents are programs are shipped from
one machine to another for execution.
• A PostScript file is a file to be printed on
a PostScript printer.
65
Mobile Code
• Methods of dealing with applets and mobile
code:
– Sandboxing attempts to confine each applet to a
limited range of virtual addresses enforced at run
time.
– Interpretation makes applets run interpretively, for
example, in JVM (Java Virtual Machine).
– Code signing devices to accept applets from trusted
sources.
• Security was a part of the Java design.
66
Mobile Code Sandboxing
(a) Memory divided into 1-MB sandboxes
(b) One way of checking an instruction for validity
67
Mobile Code
• Applets can be interpreted by a Web browser
– Untrusted applet is confined in the sandbox.
– Local applets are trusted applets.
68
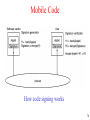
Code Signing
• How code signing works:
– The vendor computes a hash function of an applet to
get a 128-bit or 160-bit number, depending on
whether MD5 or SHA is used.
– It then signs the hash value by encrypting it with its
private key.
– When the applet is received, the browser computes
the hash functions and decrypts the accompanying
signature using the vendor’s public key.
69
Mobile Code
How code signing works
70
Java Security
•
•
Java programs are compiled to an intermediate
binary code called JVM byte code.
A type safe language
–
•
compiler rejects attempts to misuse variable
Checks include
1.
2.
3.
4.
5.
Attempts to forge pointers
Violation of access restrictions on private class members
Misuse of variables by type
Generation of stack over/underflows
Illegal conversion of variables to another type
71
Java Security
• Examples of specified protection with JDK 1.2
– Security policy (coding signing) applies to all local
and remote applets.
72
Protection Mechanisms
• Protection mechanisms are mechanisms used to
safeguard data.
– Policy: whose data are to be protected from whom
– Mechanism: how is the policy enforced in the system. (our
emphasis)
• Protection Domains
– object = computer resource, either hardware (CPU, printer,
etc.) or software (files, processes, etc.).
– right = an appropriate operation on an object. (read, write)
– protection domain = set of (object, rights) pairs.
• In some systems, protection is enforced by a program
called a reference monitor.
73
Protection Mechanisms
Protection Domains
Examples of three protection domains
74
Protection Mechanisms
• At every instance in time, each process runs in
some protection domain. (e.g. in UNIX the
domain of a process is defined by a user's id
(uid) and group id (gid))
– A system call causes a domain switch.
– e.g. when a process EXECs a file with the
SETUID of SETGID bit on, the process acquires a
new effecutive UID or GID with a different (UID,
GID) combination.
– For example, passwd
75
Protection Mechanisms
• How to keep track of which object belongs to
which domain?
– Protection Matrix: A large matrix with the rows
being domains and the columns being objects.
– Access Control List (ACL) - by column
– Capabilities - by row
76
Protection Domains
A protection matrix
77
Protection Domains
A protection matrix with domains as objects
78
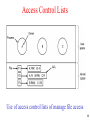
Access Control Lists
• Access Control List (ACL) is the technique to
associate with each object an ordered list containing
the domains that may access the object and their
rights:
– file11,r 2,rw NULL
file1: (Anne's UID, r), (Bob's UID, rw).
– e.g. UNIX provides 3 bits per file for:
owner owner's group
others
rwx
----– The owner can change the protection bits at any time suing
chmod - change mode.
79
Access Control Lists
Use of access control lists of manage file access
80
Access Control Lists
Two access control lists
81
Capabilities
• A capability list or C-list is a method to
associate a list of objects that may be
accessed and on which operations are
permitted with each process .
• Requests are sent to a type manager. The type
manager is given more rights than the
capability itself allows (e.g. to read an inode
to access a file - this is called rights
amplification).
82
Capabilities
• A Capabilities usually have generic rights:
1. Copy capability – create a new object with the
same capability.
2. Copy object – create a duplicate object with a
new capability.
3. remove capability – delete an entry from the Clist.
4. destroy object – permanently remove an object
and a capability.
83
Capabilities
Each process has a capability list
84
Capabilities
•
Cryptographically-protected capability
Server
•
Object
Rights
f(Objects, Rights, Check)
Generic Rights
1.
2.
3.
4.
Copy capability
Copy object
Remove capability
Destroy object
85
Trusted Systems
• Two questions are asked:
– Is it possible to build a secure computer system? Yes.
– If so, why is it not done?
• Current systems are not secure but users are unwilling
to throw them out.
• Building a secure system is to keep it simple. But users
want more features. More features mean more
complexity, more code, more bugs, and more security
errors.
• TCB (Trusted Computing Base) consisting of the
hardware and software necessary for enforcing all the
security rules.
86
Trusted Systems
Trusted Computing Base
A reference monitor
87
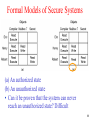
Formal Models of Secure Systems
(a) An authorized state
(b) An unauthorized state
• Can it be proven that the system can never
reach an unauthorized state? Difficult
88
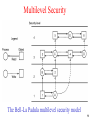
Multilevel Security
• The Bell-La Padula Model is designed for
handling military security.
• The Biba model is designed for the data
integrity.
• U.S. Department of Defense uses the Orange
Book to divide operating systems into seven
categories based on their security properties.
89
Multilevel Security
The Bell-La Padula multilevel security model
90
Multilevel Security
The Biba Model
• Principles to guarantee integrity of data
1. Simple integrity principle
•
process can write only objects at its security level or lower
2. The integrity * property
•
process can read only objects at its security level or higher
91
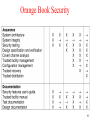
Orange Book Security
• Symbol X means new requirements
• Symbol -> requirements from next lower category
apply here also
92
Orange Book Security
93
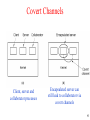
Covert Channels
• A covert channel is described as: "any
communication channel that can be exploited
by a process to transfer information in a
manner that violates the systems security
policy."
• Essentially, it is a method of communication
that is not part of an actual computer system
design, but can be used to transfer information
to users or system processes that normally
would not be allowed access to the
information.
94
Covert Channels
Client, server and
collaborator processes
Encapsulated server can
still leak to collaborator via
covert channels
95
Covert Channels
A covert channel using file locking
96
Covert Channels
• Pictures appear the same but information is hidden in
the image. It is called steganography.
• Picture on right has text of 5 Shakespeare plays
– encrypted, inserted into low order bits of color values
Zebras
Hamlet, Macbeth, Julius Caesar
Merchant of Venice, King Lear
97