* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Congruences
Survey
Document related concepts
Transcript
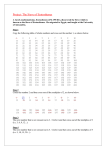
A View of Modern Factorization “For partial completion of the requirements for CMSC 485” Blaine Holcomb Mentor: Dr. Taylor The College of NJ Due: May 10th 2002 Introduction When speaking of improving security of computer networks, RSA encryption inevitably comes up in the discussion. However, very few people know more than that it is based off the multiplication of primes. During the course of the semester, I wanted to explore the two main focuses of RSA Encryption: Primes and Factorization. The first section of the semester was dedicated to understand some basic number theory, including, but not limited to, Euclid’s Proof of Infinite Primes, Sieve of Eratosthenes, Mersenne Primes, Fermat’s Factorization Method (Difference of Squares) and Euler’s Factorization Method. The second half of the semester was to seek some understanding of some of the more modern approaches to factorization such as the Quadratic Sieve. A Little History In 1970, it was barely possible to factor a 20-digit number. By 1990, with the use of the quadratic sieve factoring algorithm, the record factored number was 116 digits long. In 1994, the quadratic sieve managed to break the 129-digit RSA challenge number, which had been estimated, in 1976, to be safe for 40 quadrillion years. The quadratic sieve was replaced by Pollard’s number field sieve in 1996, which managed to factor a 130-digit RSA challenge number. The number field sieve managed to factor the number in about 15% of the time that the quadratic sieve would have taken. This little bit of history shows the ability to factor huge numbers was not solely the result of advancements in computer technology, but instead was heavily based on the growth of mathematical algorithms. These advances began with a mathematician named Carl Friedrich Gauss. Congruences Congruences were the brainchild of the prominent mathematician, Carl Friedrich Gauss. The variables a and b are said to be congruent when their difference is divisible by another integer n. This is expressed as: a ≡ b (mod n) which is equivalent to saying (a-b) mod n = 0 . When a and b are not congruent, they are considered incongruent, which can be expressed as a !≡ b (mod n). Obviously, there is a great deal more information about congruences, however, the basic understanding will be enough information to understand the remainder of the paper. Kraitchik In the 1920’s, Maurice Kraitchik improved Fermat’s difference of squares technique for factorization (x^2 – y^2), which set the basis of most modern factorization algorithms. Kraitchik determined that instead of looking for a difference of squares equal to n, it would be enough to find a difference of squares, which is equal to a multiple of n. This can be restated as x^2 ≡ y^2 (mod n). This congruence can have two different types of solutions: “interesting” solutions and “uninteresting” solutions. An uninteresting solution is a solution where x ≡ ±y (mod n), where as an interesting solution x !≡ ±y (mod n). What makes an interesting solution interesting and an uninteresting solution uninteresting? This can be understood by breaking down x^2 – y^2 into two factors (x-y)(x+y). In the case of an uninteresting, one of the two factors is a multiple of the number trying to be factored, n. This can be shown as (a*n)(b) = ab*n, where a and b are integers and ab*n is the value of x^2 ≡ y^2 (mod n). In this uninteresting solution, the number n has not been “broken” into two factors. In the case of an interesting solution, the factorization ends up as a*b = c*n, or in other words, broken into two factors. Another way of showing this would be (a1*f1)(b1*f2) = (a1*b1)(f1*f2) = c*n where f1 and f2 are the factors of n. Now, more importantly, how can the factors be “pulled out” once an interesting solution has been found? The answer to this can be found in Euclid’s Greatest Common Divisor algorithm. Applying this algorithm to either x-y or x+y in an interesting solution, will yield a factor. Euclid’s algorithm works by repeatedly dividing the remainder into divisor of the previous function until the remainder is zero or one. If the remainder is zero, then the greatest common divisor has been found and if the remainder is one, then the numbers are relatively prime. Where x and y are the numbers being examined, r# is the remainder, and a,b,… is the multiple of the remainder, the process works as follows: x = a*y + r1 y = b*r1 + r2 … r(f-1) = z*r(f) Kraitchik Example Now, to better understand this theory, an example of the problem must be approached. For argument’s sake, the number 1261 will be used. The ceiling of the square root of this value is 36. Using Fermat’s method (N-x^2=y^2), the following is obtained: 36^2 - 1261 = 35 = 5*7 37^2 - 1261 = 108 = 2*53 38^2 - 1261 = 183 = 3*61 39^2 - 1261 = 260 = 2^2*5*13 40^2 - 1261 = 339 = 3*113 41^2 - 1261 = 420 = 2^2*3*5*7 42^2 - 1261 = 503 43^2 - 1261 = 588 = 2^2*3*7^2 44^2 - 1261 = 675 = 3^3*5^2 45^2 - 1261 = 764 = 2^2*191 46^2 - 1261 = 855 = 3^2*5*19 47^2 - 1261 = 948 = 2^2*3*79 48^2 - 1261 = 1043 = 7*149 49^2 - 1261 = 1140 = 2^2*3*5*19 At this point, Kraitchik’s method found a solution by combining several of the above results. The first combination, which that is found is when x^2 =( 36^2*41^2*43^2), since the multiplication of the results is a square (y^2 = 2^4*3^2*5^2*7^4). Therefore, in the above solution x = (36*41*43) and y = (2^2*3*5*7^2) yielding (63468-2940) (63468+2940). However, when (63468-2940) mod 1261 is tested the result is zero and therefore the result is uninteresting. The next combination that is found is when x = 36*41*44 and y = 2*3^2*5^2*7 which is also uninteresting. Luckily, the following combination, x = (44*46*49) and y = (2*3^3*5^2*19) is interesting. (Note: If the powers of all numbers are even, then a square has been found). Since an interesting combination has been found, it is time to apply Euclid’s algorithm to x+y (99176+25650=124826): 124826 = 1261*98 + 1248 1261 = 1248*1 + 13 1248 = 13*96 + 0 Through this the factor, 13, has been pulled out. By dividing the number 1261 by 13, the other factor, 97, is obtained. The Quadratic Sieve The Kraitchik method searches for combinations to produce a square by incrementing from the ceiling of the square root until an interesting combination is found. The quadratic sieve aimed at finding a more efficient method of searching for these combinations by using a modified version of the Sieve of Eratosthenes. The Sieve of Eratosthenes searches for new primes by crossing off all multiples of primes below the square root of the upper bound of the search. Instead of crossing off the numbers, the quadratic sieve uses the search to find numbers, which fall in a range of primes. The Quadratic Sieve would search for results, which were completely factorable by all primes underneath a certain value (a combination with primes under a certain value is called YSmooth, where y is the largest prime) by using division, instead of simply crossing off the values. However, it must be noted, that the larger the number being factored, the harder it becomes to find values under a low y-smooth range. Conclusion Obviously, the Quadratic Sieve is not the end-all of factorization methods. In fact, the advent of the Numeric Sieve toppled the Quadratic Sieve’s record. However, it is doubtful that the Numeric Sieve is the best method of factorization either. The next algorithm may make 1024-bit encryption obsolete long before the time computer processors are expected to make it useless. The power of the algorithm lies in the inability to solve the problem, however, as mathematics advances the encryption methods must also evolve. Bibliography Ore, Oystein. Number Theory and Its History. Toronto: General Publishing Company, 1988. Pomerance, Carl. “A Tale of Two Sieves.” Notices of the AMS. December 1996. Dr. Clifford. The College of New Jersey.