* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download ad hoc wireless networks
Distributed operating system wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Distributed firewall wikipedia , lookup
Policies promoting wireless broadband in the United States wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Internet protocol suite wikipedia , lookup
Deep packet inspection wikipedia , lookup
Computer network wikipedia , lookup
Network tap wikipedia , lookup
Wireless security wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Airborne Networking wikipedia , lookup
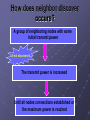
AD HOC WIRELESS NETWORKS BY: Radwa Bayoumy OUTLINE Introduction Application Design Principles and Challenges Protocol Layers Cross-Layer Design Network Capacity Limits Energy-Constrained Networks Introduction: An ad-hoc (or "spontaneous") network is a local area wireless or temporary plugin connections. In Latin, ad hoc literally means "for this," further meaning "for this purpose only," Applications An ad-hoc network has been applied to future office or home networks in which new devices can be quickly added, using, for example, Bluetooth technology in which devices communicate with the computer and perhaps other devices using wireless transmission. Examples of applications Data Networks Home Networks Device Networks Sensor Networks Distributed Control Systems Data Networks These types of networks support data exchange between laptops, palmtops, personal digital assistance (PDA), and other information devices. According to the area being covered, the category of the network is being identified weather it’s LANs, MANs, and WANs. Although the wireless LANs has a good performance at low cost, the ad hoc have some advantages over it. Only one access point is needed for communication with an already wired network and in certain cases no access point is needed. It’s inefficient if a node had to go through an access point or a base station to exchange information for example: between two PDAs right next to each other. In wireless MANs the multihop routing is a necessary as they cover a large area. For the high mobility users (example: military programs) it’ complicated to communicate with the lake of centralized network control. The ad hoc network had offered the solution for such case with a limited success. In Wireless WANs it’s used where network infra structure cannot be developed and network that must be build up and torn out quickly as in military application. Home Networks All the house electronics equipment can be linked together by the help of the ad hoc network. Such a network could enable a smart room from the light adjustment to the fire alarm that is connected to the fire department. These types of application are mostly used by the people with certain disabilities. Device Networks Short range wireless connection between devices is supported by device Networks. Usually such connection is wired. Devices as cell phones, modems, headsets, PDAs, computers, printers, projectors, network access point, the main technology drivers for a network between them can be one at low cost, low power radio with network capabilities such as Bluetooth, Zigbee, and UWB. Sensor Networks These networks consist of small nodes with sensing, computation, and wireless network. Sensor array can be deployed and used for remote sensing in nuclear power plants, mines, and military applications. Distributed control systems Distributed Control applications, with remote plants, sensors, and actuator linked together by wireless communication channel are enable by ad hoc wireless networks. The ad hoc wireless networks can be used to support coordinated control of multiple vehicles in an automated highway system. Design Principles and Challenges The most design principles and challenges of an ad hoc network come from the fact of its lack of infrastructure. For wireless networks there is no peer to peer communication. On the other side ad hoc wireless network has peer to peer communication, networking and control functions that are distributed among all nodes, and routing that can exploit intermediate nodes are relays. Ad hoc wireless networks may create structure to improve network performance, although it’s not a fundamental design requirement of the network. Ad hoc wireless networks can form a backbone infrastructure from a subset of nodes in a network or some nodes may be chosen to perform as base stations for neighboring nodes. If a node in this backbone subset leaves the network, the backbone can be reconfigured. One of the biggest challenges in ad hoc wireless networks design is energy constrain. These constrains arise in wireless network nodes power by batteries that cannot be recharged. Therefore energy consumption must be optimized over all aspects of the network design. Protocol Layer A protocol is a set of rules that govern the operation of functional units to achieve communication. There is an international standard called OSI (open system interconnection) model that was developed as a framework for protocol layer in data networks. From this standard model, different models were derived as the TCO (transport control protocol) and IP (internet protocol). The TCP and IP protocol consist of five layer model. Application Transport Network Access Physical Physical Layer Design The Physical Layer which is also referred to as the link layer, deals primarily with transmitting bits over a point-to-point wireless link In ad hoc networks bits are pocketsize for transmission. The link packets error rate (PER) is determined by physical layer along with the channel and interference conditions. A multiple antennas can be used with ad hoc wireless network. In fact it can increase the data rate on the link, by providing diversity to fading so that average BER is reduced leading to a fewer retransmission. It also can provide directionality to reduce fading and the interference of signal causes to anther. furthermore multiplexing will increase the link rate, which reduces overcrowding and delay in the link and benefits all multiple routes using that link. Considering the transmitted power of all nodes in the network, it must be optimized with respect to all layers that it impacts. As increasing transmit power at the physical layer reduce PER and that decrease the retransmission required at the access layer, but a high transmit power from one node of the network can cause significant interference to the other nodes. Therefore SINR drives the performance in an ad hoc wireless. The transmit power coupled with adaptive modulation and coding for a given node defines it’s “local neighborhood”- the collection of nodes that it can reach in a single hop - and defines the context in which access, routing, and other higher layer protocols operate. Access Layer Design Access layer is the layer that controls how different users share the available spectrum and ensures successful reception of packets transmitted over this shared spectrum. There are two types of access either multiple access or random access. Multiple access divides the signaling dimensions into dedicated channel. The common used methods of multiplexing are TDMA, FDMA, and CDMA. In random access, channels are assigned to achieve user dynamically, and in multihop networks these protocols must content with hidden and expose terminals. The power control across the network is also a part of the access layer functions. The main role of power control is to insure that SINR targets can be met on all links in the network. Assume an ad hoc wireless network with K nodes and N links between different transmitterreceiver pairs of these nodes. The SINR link K is given by ij Gij Pi j k i Gkj Pk T The access layer is also responsible for retransmitting of packet received in error over the wireless link. The data packets have an error detection code that is used by the receiver to determine if one or more bits in the packets were corrupted and cannot be corrected. For such packet: the receiver will discard the corrupted packets and inform the transmitter by a feedback that the packet must be retransmitted. or The access layer can save it and use a form of diversity to combine the corrupted packet with the retransmission packets for a higher probability of correct packet reception. or An alternative retransmitting the original packets in its entirety the transmitter can just send some additional coded bits to provide a stronger error correction capability for the original packets to correct for its corrupted bits. Network Layer Function Neighbor discovery Routing Dynamic Resource Allocation How does neighbor discover occurs? A group of neighboring nodes with some initial transmit power If not discovered The transmit power is increased Until all nodes connections established or the maximum power is reached Routing Flooding Routing Proactive Routing Reactive Routing Flooding A packet is broadcast to all nodes within receiving range Nodes also broadcast the packet Forward continues until the packet reaches it destination Advantages of Flooding Highly flexible to changing network topologies Requires little routing overhead Disadvantages of Flooding Wasting Bandwidth Battery power of transmitting nodes Centralization approach information about channel conditions and network topology forwarded to a centralized location that computes the routing tables for all nodes in the network Advantages minimum average delay minimum number of hops minimum network congestion. Disadvantages cannot adapt to fast change in the channel condition and network topology requires much over head for periodically collecting local node information Reactive routing source node initiates a route-discovery process when it has data to send It will determine if one or more route are available to the destination. Advantages can be obtained with relatively little overhead Disadvantages significant initial delay Advantages can be obtained with relatively little overhead Disadvantages significant initial delay Resource Allocation and flow Control Identify the route a packet should follow from a source to its destination How are Routing, resource allocation & flow control related? Routing based on minimum delay Delay is a function of the link data rate or capacity The higher the capacity, the more data that can flow with min. delay The link capacity depends on the resources allocated to the link Fij Dij = Cij- Fij •Fij traffic flow •Dij delay on a link •Cij capacity Link Utilization Formula Fij Dij = Cij Transport layer Transport Layer Functions:(end to end functions) Error recovery Retransmission Reordering Flow control Application Layer Functions: Generates the data to be sent over the network Processes the corresponding data received over the network Provides compression of the application data along with error correction and cover up MDC Multiple description coding A form of compression Multiple descriptions of the data are generated The original data can be reconstructed from any of these descriptions with some loss Cross Layer Design The layering approach to wireless network design, where each layer of the protocol stack is unaware to the design and operation of other layers, has not worked well in general Cross-layer design clearly requires: information exchange between layers, adaptively to this information at each layer, diversity built into each layer interaction between layers Ease of modifying the functionality of one of the layers May need to generate a new protocol stack each time a small change is modified Long term survivability of such architectures? Network Capacity Limits Capacity is the set of maximum data rates possible between all nodes. The capacity region has dimension of K(K − 1) For a large K, the per-node rate is 1/√K logK , and the throughput is √K/logK Energy-Constrained Networks Batteries in nodes and devices: Nodes are powered by batteries with a limited life time Devices with rechargeable batteries must conserve energy to max. time between recharges Some devices can not be recharges Some operate solely form the environment Energy constraints associated with node operation: Hardware operation Transmit power Signal Processing Design consideration with energy constrained nodes: Modulation & Coding MIMO and Cooperative MIMO Access, Routing, & Sleeping Cross Layer Design under Energy Constraints Capacity Per Unit Energy Modulation & coding are based on: Required transmit power Data rate BER Complexity Modulation The design choice should be based on the total energy consumption Circuit energy consumption increases with transmition time Decrease transmition time & putting nodes to sleep Example between M-ary Modulation and binary modulation Coding Reduces the required transmit energy per bit for a given BER target Some coding schemes encode bits into a codeword that is longer than the original bit sequence: Such as: block codes Convolution codes continue The total transmit energy required for the codeword to be sent , a longer transmission time consumes more circuit energy, and band width expansion MQAM is more efficient then MFSK MIMO Multiple Inputs Multiple outputs Functions: Multiplexing gain: Provides a higher data rate Diversity gain: Provides a lower BER in fading Continue Provide energy savings over a single antenna system for most transmition distances Why? The reason is that MIMO systems can support a higher data rate for a given energy per bit. So, it transmits the bits quicker and then it shuts down Cooperative MIMO Small nodes that can not support multiple antennas they are grouped together to form a transmitter while others form a receiver Distance between the nodes is small so the energy associated is small Cooperative MINO Access How to be more energy efficient? Minimizing collision Optimizing transmit power Routing Routing is affected by energy consumption distributed across all node Routing optimization to minimize end to end consumption How By applying the Standard optimization procedure Sleep Nodes consume power even in stand by mode How to solve? By scheduling sleep periods for nodes Each node to only listen during a certain period of time