* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download socks - OpenLoop.com
Computer network wikipedia , lookup
Airborne Networking wikipedia , lookup
Server Message Block wikipedia , lookup
Dynamic Host Configuration Protocol wikipedia , lookup
Wireless security wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Extensible Authentication Protocol wikipedia , lookup
Deep packet inspection wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Remote Desktop Services wikipedia , lookup
Internet protocol suite wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Hypertext Transfer Protocol wikipedia , lookup
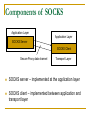
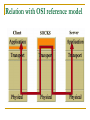
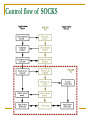
SOCKS By BITSnBYTES (Bhargavi, Maya, Priya, Rajini and Shruti) Outline Definition History Major components Working Features Functions Applications Need for protocol Widespread use of firewalls Need to provide a general framework for sophisticated application layer protocols to transparently and securely traverse a firewall with strong authentication capabilities Need to provide a framework for client-server applications in both TCP and UDP domains to conveniently and securely use the services of a network firewall What is SOCKS? Acronym for SOCKet Secure Networking proxy protocol for TCP/IP based network applications Intermediate layer between application layer and transport layer History Originally developed by David Koblas in 1992 Protocol extended to version 4 by Ying-Da Lee of NEC Designed to allow clients to communicate with Internet servers through firewalls Two major versions of SOCKS – SOCKS V4 SOCKS V5 Components of SOCKS Application Layer Application Layer SOCKS Server SOCKS Client Secure Proxy data channel Transport Layer SOCKS server – implemented at the application layer SOCKS client – implemented between application and transport layer How does it work? Establishes a secure proxy data channel between two computers in a client/server environment SOCKS server handles requests from clients inside a network's firewall and allows/rejects connection requests, based on the requested Internet destination or user identification Once a connection and a subsequent "bind" request have been set up, the flow of information exchange follows the usual protocol Client's perspective - SOCKS is transparent Server's perspective - SOCKS is a client How does it work? SOCKS is typically implemented on proxy servers SOCKS uses sockets to represent and keep track of individual connections Client side of SOCKS is built into Web browsers Server side can be added to a proxy server The SOCKS server – authenticates and authorizes requests establishes a proxy connection relays data between hosts Relation with OSI reference model Purpose of SOCKS Enables Hosts on one side of the SOCKS server to gain access to the other side of the SOCKS server without requiring direct IP-reachability Clients behind a firewall wanting to access exterior servers connect to a SOCKS proxy server which controls the eligibility of the client to access the external server and passes the request on to the server. Major Functions The SOCKS protocol performs four functions: Making connection requests Setting up proxy circuits Relaying application data Performing user authentication (optional) Two versions of SOCKS SOCKSv4 Makes connection request Sets up proxy server Relays application data SOCKSv5 Adds authentication to V4 - Username/Password (RFC 1929) - GSS-API (RFC 1961) Authentication Method Negotiation Address Resolution Proxy UDP proxy Control flow of SOCKS Features Allows for transparent network access across multiple proxy servers Provides a flexible framework for developing secure communications by easily integrating other security technologies Rapid deployment of new network applications Simple network security policy management Benefits Single communication protocol to authenticate users and establish communication channels Universal – works with several internet protocols Application-Independent proxy Can be used with either UDP or TCP based protocols Bi-directional proxy support Benefits (continued..) Easy deployment of authentication and encryption methods Firewall tunneling service - allows many machines behind a firewall to access the Internet without actually being on the Internet themselves Drawbacks SOCKS v4 does not support UDP and authentication The SOCKSv5 protocol does not support SOCKSv4 protocol SOCKS implementations do not support data encryption (except for some commercial software) making data transfers vulnerable to interception Applications Most common use - Network firewall Authorized data relay between Hosts Supported as a proxy configuration option in popular Web browsers and instant messaging programs Found in some VPN implementations Emerging as one of the best ways to secure multimedia applications across the Internet Summary SOCKS is easy to deploy and manage SOCKS is transparent to the user, while providing multiple layers of security Allows client-server applications to transparently use the services of a network firewall without requiring direct IPrechability References RFC 1928 - base SOCKS v5 specification RFC 1929 , RFC 1961 - additional details http://www.socks.permeo.com/AboutSOCKS/SOCKSOverview.asp http://whatis.techtarget.com/definition/0,,sid9_gci213023,00.html http://www.socks.permeo.com/TechnicalResources/SOCKSFAQ/SO CKSGeneralFAQ/index.asp The SOCKS reference architecture and client are owned by Permeo Technologies, spin-off from NEC. NEC Corporation has promoted SOCKS. A SOCKSv4 implementation is available through anonymous ftp from ftp://ftp.nec.com:/pub/socks/ SOCKV5 Reference implementation by Permeo. Questions?