* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download LAN BASICS
Deep packet inspection wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Policies promoting wireless broadband in the United States wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Internet protocol suite wikipedia , lookup
Power over Ethernet wikipedia , lookup
Low Pin Count wikipedia , lookup
Industry Standard Architecture wikipedia , lookup
Wireless security wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Computer network wikipedia , lookup
Bus (computing) wikipedia , lookup
Airborne Networking wikipedia , lookup
Zero-configuration networking wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Network tap wikipedia , lookup
Wake-on-LAN wikipedia , lookup
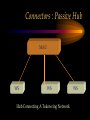
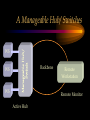
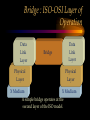
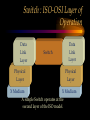
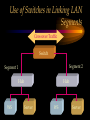
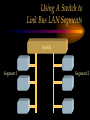
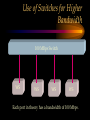
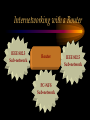
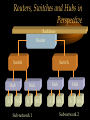
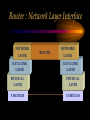
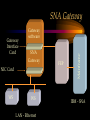
CHAPTER Network Hardware Chapter Objectives • Describe the important basic network hardware and the internetworking hardware • Discuss the desired characteristics of a server and a workstation • Present different switching technologies • Examine the routing process with the help of an example Introduction Module 1 (4-06) Network Hardware Categories • Local networking hardware • Internetworking hardware Local Networking Hardware • Network Interface Cards (NICs) • Cables • Connectors • Line drivers or repeaters • Hubs / Switches • Servers • Workstations Internetworking Hardware • Line drivers or repeaters • Transceivers • Bridges • Switches • Routers • Gateways Current Day Internetworking Devices • Mostly confined to the following: – Switches – Routers Folding of Devices into Switches • Show Diagram Folding of Devices into routers • Show Diagram Manageable Devices • Switches and routers in a large network can be managed from a remote console End of Module MODULE Network Interface Cards (NICs) NIC Basics • Technology used • Connectors used • Speed of the network • Interface technologies An Actual NIC Description • 100BaseTX, PCI card – – – – 100 = speed in Mbps Base =Ethernet TX = Twisted pair 32-bit = bus width; it may also be 64-bit wide – PCI = bus technology 10BaseT NIC • 10BaseT cards – – – – – Physical star and logical bus networks 10 Mbps speed Ethernet standard Twisted pair wiring RJ-45 Connectors 10Base2 NIC • 10base2 cards – – – – – Physical bus and logical bus networks 10 Mbps speed Ethernet standard Thin coaxial wiring BNC connectors 10Base5 NICs • 10Base5 – – – – – Physical bus and logical star networks 10 Mbps speed Ethernet standard Thick coaxial wiring AUI connectors are used • Note: 10BaseT, 10Base2 and 10Base5 are not used widely in practice anymore 100BaseTX NIC • 100BaseTX – 100 Mbps speed – Fast Ethernet standard – Twisted pair • Higher quality Category 5 wires are normally required to implement 100 mbps Ethernet networks 1000BaseT NICs • 1000BaseT – 1000 Mbps – Ethernet – Twisted-pair wire • Category 5e • 1000BaseF – 1000 Mbps – Ethernet – Optical fiber wire 1000BaseT NIC Source: 3Com Note the RJ-45 connection and the status lights on the card Gigabit Ethernet Fiber NIC Source: 3Com •Note the two connectors for the RX and TX connections •For use with PCI and PCI-X servers Gigabit Ethernet NIC Properties (Source: 3Com) • Tenfold throughput boost: accelerate Fast Ethernet server connections to 1000 Mbps • Fiber-optic cabling supports data security and faster throughput • Automatic link aggregation and fail-over allow multiple NIC connections to be installed • Advanced server features maximize availability, scalability, and fault tolerance Gigabit Ethernet NIC Properties (Source: 3Com) • 64-bit PCI and PCI-X support: faster transmissions with lower CPU utilization • Centralized, standards-compliant management lowers network administration time and total cost of ownership • TCP/UDP/IP checksum offloads reduce host CPU load for improved system performance • PCI Hot-Plug lets you remove/replace server NICs without taking the server offline Token Ring Cards • Token ring network cards • Earlier token ring cards – 4/1 Mbps • Later token ring cards – 16/4 Mbps • Newer token ring cards – Fast token ring networks – 100/16/4 Mbps PCI Bus Types for NICs • Width – Bus width is 32-bit or 64-bit • Bus frequency – 33 MHz – 66 MHz – 100 MHz etc. • Technology – PCI – PCI-X – PCI Express Source: Tomshardware: www6.tomshardware.com/howto/02q3/020904/diy-06.html Cable Connections for NICs • BNC barrel connector – Thin coaxial • RJ 45 – Twisted pair • Note the difference between RJ 11 and RJ-45 – RJ-11 is smaller and it is used in telephone connection – RJ-45 is larger and it is used in LAN connections Different Coax Connectors Coaxial Cable Connectors T connector Thin coaxial cable Terminator Network Interface Card BNC AUI and Combo Cable Connections for NICs • AUI Possibilities – Designed for a thick coaxial cable – Designed for a token ring network • Combo Cards – Consisting of different ports – BNC, RJ-45, AUI RJ-45 Connectors RJ-45 Port RJ-45 Connector Possible Combo Card Connections • Thin coaxial cables (BNC) • Twisted pair wires (RJ-45) • Phone connection (RJ11) • Thick coaxial cables (AUI) Wireless Network Interface Cards • IEEE 802.11b – 2.4 GHz, 11 Mbps • IEEE 802.11b+, IEEE 802.11g? – 2.4 GHz, up to 20% more throughput • IEEE 802.11a – 5.8 GHz, 54 Mbps • IEEE 802.11g • 2.4 GHz, 54 Mbps, 108 Mbps (Full duplex)? • IEEE 802.11n Example of Older 10Base2 Card BNC Source: Black Box Example of Older 10BaseT Card ISA RJ 45 Source: Black Box Example of Older Combo Card RJ 45 Combo Source: Black Box BNC D-Link Fast Ethernet Card (100BaseTX) D-Link 100BaseTX Specs (Source D-Link) • A manageable 10/100MB Dual Speed Ethernet PCI Network Interface Card with Wake-On-LAN (WOL) • Fully compliant with IEEE802.3 10Base-T, IEEE 802.3u 100Base-T specifications • Supports ACPI/WOL (Advanced Configuration Power Management Interface) feature, IP Multicast packet filtering, PXE (PreBoot execution Environment) Boot ROM, IEEE 802.1p, IEEE 802.1Q, and DMI (Desktop Management Interface). A Note on Remote Wake on LAN (Source: Intel) • A remote wake-up technology that enables you to remotely power systems "on" for offhours maintenance. A result of the Intel-IBM Advanced Manageability Alliance and part of the Wired for Management Baseline Specification, this technology helps save time on automated software installations, upgrades, disk backups and virus scans. Equally important, it increases end-user productivity by moving such planned disruptions to off-hours. Fast Ethernet PC Multi-Port Card NIC and modem connections Fast Ethernet Card Specs. The D-Link DMF-560TX is a 10/100Mb Dual Speed Ethernet PC Card with an integrated V.90/K56flex Data/Fax Modem. The DMF-560TX is targeted at notebook and laptop users that connect to a wide variety of datacommunications devices and services, and require access to faster technologies. Laptop users are able to seamlessly connect to both Ethernet and Fast Ethernet LANs, as well as send and receive faxes, connect to the Internet, and dial into a Remote Access Server or PC using this one PCMCIA PC Card solution. The DMF-560TX strictly adheres to the IEEE Ethernet standards and the ITU Data Communications and Modem standards in order to ensure maximum interoperability. The DMF-560TX attempts to connect at the highest speed supported by an ISP, LAN, host modem, or fax machine and automatically defaults to a lower speed until a stable connection can be created. Fast Ethernet Card Operational Specs. Modem Operating Protocols •V.90 (down-stream up to 56,000 bps) •K56flex (down-stream up to 56,000 bps) •V.34bis (up to 33,600 bps) •V.34 (2,400 to 28,800 bps) •V.32bis, V.32, V.22bis, V.23, V.22/Bell 212A, V.21/Bell 103 Error Correction Data Compression •V.42/V.42bis and MCP Class 2 to 5 Fax Compatibility •Group 3 send and receive •EIA Class 1 fax commands •V.17 (14,400 bps), V.29 (9600 bps), V.27ter (4800 bps), •V.21 (300bps) Token Ring Adapter (NIC) Note the connector type. Ethernet to Token Ring Bridge Wireless PC Card Adapter Wireless PC Card Specs D-LinkAir DWL-650 PC Card Type-II 11Mbps Wireless LAN Adapter The D-Link DWL-650 is an IEEE 802.11b compliant PC Card Type-II 11Mbps wireless LAN adapter. The DWL-650 will operate in 2.4 GHz Direct Sequence Spread Spectrum (DSSS) for wireless networks in the home or office environment. It is designed to operate in 3.3V or 5.0V DC slots. In addition, the DWL-650 uses a 64/128-bit WEP (Wired Equivalent Privacy) Encryption for a secure network connection. The D-Link DWL-650 can operate in either Ad-Hoc mode (Peer-to-Peer networking without access point) or Infrastructure mode (Peer-to-Peer networking using an access point). In Infrastructure mode, the DWL-650 can be connected to a broadband residential gateway or a DSL/Cable modem for high-speed wireless Internet access on the existing network. Wireless PC Card Specs The DWL-650 can transmit data at 11, 5.5, 2 or 1 Mbps per channel. The DWL-650 transmit rate values can be manually selected for Auto Select 1 or 2 Mbps, Fixed 1 Mbps, Fixed 11 Mbps, Fixed 2 Mbps, Fixed 5.5 Mbps and Fully Auto. The DWL-650 has full mobility and seamless roaming from cell to cell as well as across access points. The range of coverage per cell for indoor use is up to 328 feet and up to 984 feet per cell for outdoor use. The DWL-650 comes with an internal non-detachable diversity patch antenna and one built-in green LED indicator for power, network link and activity. The DWL-650 is compatible with Windows 98, Windows ME, Windows 2000, Windows XP. Wireless PCI Card Wireless PCI Card Specs The D-LinkAir DWL-520 is an IEEE 802.11b wireless PCI adapter. The DWL-520 provides an integrated PCI solution that will operate within the 2.4 GHz Direct Sequence Spread Spectrum (DSSS) for wireless networks in the home or office environment. Along with the advanced wireless technology that is incorporated into the DWL-520, wide range motherboard support is assured by compliance to the latest PCI 2.2 standard interface. The DWL-520 is the solution for users and network administrators looking for the convenience offered by a wireless connection. Wireless PCI Card Specs Cont. The D-Link DWL-520 can operate in either Ad-Hoc mode (Peer-toPeer networking without an access point) or Infrastructure mode (Peer-to-Peer networking using an access point). In Infrastructure mode, the DWL-520 can be connected to a wireless residential gateway with a broadband connection to enable wireless sharing of the High-speed Internet access. The DWL-520 can transmit data at rates of 11Mpbs, 5.5Mbps, 2Mps and 1 Mbps per channel. With its detachable antenna using a reverse SMA connector, the DWL-520 has an effective range of up to 230 feet for indoor use and up to 984 feet in an outdoor environment. In addition, the DWL-520 supports 64/128-bit WEP (Wired Equivalent Privacy) Encryption for network security. Wireless 5 GHz Wireless 5 GHz Specs •Next generation of wireless products with its highperformance D-LinkAir Pro series of 5GHz networking technology. Designed for indoor use, the D-LinkAir Pro DWL-A650 is a powerful notebook PC CardBus adapter that allows users to have mobile access to networks. It provides roaming capabilities from cell to cell and network to network. •At 54 Megabits per second (Mbps), the D-LinkAir Pro DWLA650 5GHz high speed wireless CardBus adapter delivers the fastest standards-based wireless technology in the industry. With IEEE 802.11a standard compliance, the D-LinkAir Pro DWL-A650 high-speed wireless adapter provides excellent network interoperability. Wireless 5 GHz Specs (Continued) • A proprietary “Turbo” mode allows the D-LinkAir Pro DWLA650 to operate at significantly greater data rates up to 72Mpbs. Eight non-overlapping channels create less interference, which supplies higher average cell throughput to clients. The DLinkAir Pro DWL-A650 employs enhanced 152-bit Wired Equivalent Privacy (WEP) and Dynamic Key Exchange to protect data from unauthorized access. • The D-LinkAir Pro DWL-A650 is easily installed into a laptop PC to provide connectivity directly to another wireless enabled device (ad-hoc mode) or through an 802.11a based access point (infrastructure mode). END OF MODULE MODULE NIC Resources NIC Resources • IRQ • I/O address • Base memory address, if provided • DMA, if provided IRQ • Must be unique for each device, unless it is steered – IRQ steering • An NIC requires an IRQ • IRQ is used to gain the attention of the CPU • There are a limited number of IRQs available on a computer IRQ Assignment (learnthat.com) IRQ Device 0 Timer 1 Keyboard 2 Wired to IRQ 9 3 COM 2 (COM 4) 4 COM 1 (COM 3) 5 Available (often LPT2, sound cards, or network cards) 6 Floppy Disk Controller 7 LPT1 8 Clock 9 Wired to IRQ 2 10 Unused 11 Unused 12 Mouse Port 13 Coprocessor 14 Hard Disk Controller 15 Unused I/O Address • Must be unique to each device • Each device of port must have an I/O address • The NIC must have an I/O Address as well Common I/O Address Assginemnt (learnthat.com) Address (Hex) 00-0F 20-21 40-43 1F0-1F8 200-20F 238-23B 278-27F 2E8-2EF 2F8-2FF 300-30F 330-33F 378-37F 3E8-3EF 3F0-3F7 3F8-3FF Device DMA Controller Interrupt Controller Timer Hard Disk Controller Joystick Controller Bus Mouse LPT2 COM4 Serial Port COM2 Serial Port Ethernet Card MIDI Port LPT1 Port COM3 Serial Port Floppy Disk Controller COM1 Serial Port I/O Address (www.techencylopedia.com ) • There is a 64K address space for I/O addresses, although typically less than 1K is used. Each board that uses an I/O address contains a few bytes of memory (16, 32, etc.) set to a default address range. One or more alternate addresses is also provided to resolve conflicts with other boards. These I/O spaces are a bunch of tiny memory banks scattered over different devices. As long as each one is set to a different address, the CPU can transmit signals to the appropriate boards without conflict. I/O Address Continued (www.techencylopedia.com ) • An I/O address operation takes place as follows. If a program needs to send a byte to the serial port, it issues an OUT instruction to the CPU with the address of that serial port. The CPU notifies the address bus to activate the I/O space, not regular memory, and the address bus signals the appropriate byte location on the board. The CPU then sends the data character over the data bus to that memory location. Base Memory Address • Must have a unique range for the NIC card • Some older cards did not require the base memory address to be specified DMA • Direct Memory Access • Channels are assigned for DMA • Not all the NIC cards have DMA • Newer PCI technologies used for expansion slots have made DMA somewhat obsolete DMA Use (Source learnthat.com) • In most PCs, there are 8 DMA Channels. • In most modern PCs, DMA shouldn't be used as it just slows it down. But, older PCs may use DMA. • Channels 4-7 are usually available, while Channel 0 is used to refresh DRAM, Channel 1 is used by a hard disk controller or sound card, and Channel 2 is usually used by the floppy disk controller. Resource Allocation on a NIC Examining the Network Resources Device Manager NIC Resources Properties END OF MODULE MODULE Network Connectors and Hubs Simple Connectors • T connectors – An interface between the NIC and the cables • Terminators – Used at both ends of a bus network T Connector Terminator Example of T-Connector and Terminator T Connector Source: Black Box Terminator Connectors : Hubs • Types – Passive hub – Active hub – Intelligent hub • Passive hubs – Simply provides the physical and the electrical connection for the network • Active hubs – A Multi-port device – Amplifies LAN signals • Manageable hubs – Has built-in manageability – Some are manageable hubs Connectors : Passive Hub MAU WS WS Hub Connecting A Token-ring Network WS A Manageable Hub/ Switches WS Backbone WS WS Remote Workstation Remote Monitor Active Hub LAN Management Software • Sophisticated • Monitor the network traffic through each of the ports • Becoming popular • Standardized protocol for remote management exists – SNMP (Simple Network Management Protocol) SNMP • A major protocol used in the management of networks • A number of LAN management software is based on the SNMP protocol SNMP Cont. (Source: Cisco) • The Simple Network Management Protocol (SNMP) is an application-layer protocol designed to facilitate the exchange of management information between network devices. • By using SNMP-transported data (such as packets per second and network error rates), network administrators can more easily manage network performance, find and solve network problems, and plan for network growth. • SNMP is a relatively simple protocol, yet its feature set is sufficiently powerful to handle the difficult problems presented in trying to manage today's heterogeneous networks. • Today, SNMP is the most popular protocol for managing diverse commercial internetworks as well as those used in universities and research organizations. SNMP Cont. • Like the Transmission Control Protocol (TCP), SNMP is an Internet protocol. • There are two versions of SNMP: Version 1 and Version 2. • Most of the changes introduced in Version 2 increase SNMP's security capabilities. Other changes increase interoperability by more rigorously defining the specifications for SNMP implementation. • SNMP's creators believe that after a relatively brief period of coexistence, SNMP Version 2 (SNMPv2) will largely replace SNMP Version 1 (SNMPv1). Web Research • Obtain additional information on the following LAN troubleshooting software – LAN Analyzer – LAN Sniffer Example of a Hub Used in Ring Network Source: Black Box Example of Hubs Used in the Star Network Stackable Hubs Source: Black Box END OF MODULE Web Research • Photonic switching – www.agilent.com/comms/photonicswitch – www.cnn.com/tech MODULE Server and Workstation Hardware Module Objectives • Give an overview of the different types of the server hardware • Discuss the desired characteristics of a server • Provide a specification for a workstation Servers • Types – Powerful micros – Servers – Super-servers – Mini and large computers are used as servers • In a client-server environment, the server also acts as an engine for database execution • In general, the server is used for the sharing of stored data and application Desired Characteristics of Server: Processor and Storage Requirement • Powerful processor – Latest Pentium Processor for example – Multiple processors, if necessary • Large storage space – Several gigabytes at a minimum – Actual requirement will vary with LAN size • Fast disk access speed – Less than 10 ms, for example • Versatile CD-ROM access (Towers) • Fault tolerance Processors • • • • Intel Pentium 4, 32-bit processors Intel Itanium 64-bit processors Special Xeon processors meant for servers Multiple processors – Symmetric Multi-Processing (SMP) • Other processors – Spark (Sun), AMD, Motorola, IBM’s own processors etc. Symmetric Multiprocessing (SMP) Source: Search390.com • SMP (symmetric multiprocessing) is the processing of programs by multiple processors that share a common operating system and memory. In symmetric (or "tightly coupled") multiprocessing, the processors share memory and the I/O bus or data path. A single copy of the operating system is in charge of all the processors. SMP, also known as a "shared everything" system, does not usually exceed 16 processors. Chip Set • Chip sets designed for servers to boost I/O operation Hard Disk Technologies • SCSI • ATA • Serial ATA (SATA) • Fiber channel storage • RAID Overview of Storage Technologies • SCSI, Small Computer Systems Interface, is widely used in mid- to high- performance workstations and servers. • SCSI offers faster transfer rates than ATA/IDE, the interface most commonly used in desktop PCs. • In general, ATA/IDE is considered easier to implement and less expensive than SCSI but does not offer as many features. – For example, SCSI can support up to 16 devices on a single bus (IDE offers two), generally offers faster throughput, uses less CPU horsepower during operation, and is therefore more efficient in demanding multiple initiator applications for multi-users and uses. This is significant because it allows the processor to perform more commands at one time making for greater efficiency. SCSI Standards S C SI Fast SCSI Ultra SCSI Wide Ultra SCSI Ultra2 SCSI Wide Ultra2 SCSI Ultra3 SCSI Data transfer rates max. Bus speed (MB/sec) 5 10 20 40 40 80 160 Maximum Data Bus width (bits) 8- 8-bit bit 8-bit 16-bit 8-bit 16-bit 16-bit Max. cable length (meters) 6 3 1.5 - 3 1.5 - 3 12 12 12 Max. device support 8 8 8-4 8-4 8 16 16 SCSI Terms (source: IBM) • The SCSI terms Fast, Ultra, or Ultra2 typically refer to data rate increases that move data faster on the bus, while the term Wide refers to adding more lanes to the bus, typically transferring 16 bits of data at one time rather than eight bits. Other differences between the standards include the maximum cable length and the number of devices that can exist on the same SCSI bus. Ultra 3 SCSI (source: IBM) •As one of the recent developments in SCSI, Ultra3 SCSI presents significant feature and benefit enhancements over Ultra2 SCSI products. Ultra3 SCSI products are designed to offer, at a minimum, the following features: Cyclic Redundancy Check (CRC) , domain validation , and double transition clocking , none of which are available in Ultra2 SCSI products. •These features are designed to improve speed, performance, and overall manageability of SCSI. Ultra 160 (source: IBM) • The subset of Ultra3 that includes the three features, Cyclic Redundancy Check (CRC) , domain validation , and double transition clocking , is commonly called Ultra160, for its speed 160MB per/sec. The main difference between Ultra3 and Ultra160 is that Ultra3 implementations may offer other features in addition to those listed above. ATA • The term ATA stands for Advanced Technology Attachment, for the standard bus interface on the original IBM AT computer. This interface also is called IDE, for Integrated Drive Electronics; ATA is the official ANSI (American National Standard Institute) standard designation. • Also known as Ultra DMA, ATA is generally the least expensive hard drive interface; many computer motherboards include ATA controllers and cable connectors that typically control the "C" drive that contains the operating system. However, ATA is a slightly slower drive interface, so it is used primarily in single user computer applications or low-end RAID systems. ATA Variations ATA/ ATA-2 Ultra-ATA/33 Ultra-ATA/66 Data transfer rates max. Bus speed (MB/sec) 8.3 16.6 33 66 Maximum Data Bus width (bits) 16-bit 16-bit 16-bit 16-bit Max. device support 2 2 2 2 Serial ATA (SATA) Fiber-Channel • Fiber Channel - Arbitrated Loop (FC-AL) is an exceptionally high-bandwidth industrystandard interface primarily targeted toward high-end servers and similar demanding applications. • FC-AL uses fiber optic cabling in a loop configuration to produce maximum transfer speeds of 100 MB/second and is designed to connect up to 127 devices as far as 10 kilometers apart, enabling data storage in remote, secure locations distant from the server. More on Fiber Channel • FC-AL devices can be dual ported, providing two simultaneous input/output sessions that doubles maximum throughput, and FC-AL enables "hot swapping," so you can add and remove hard drives without interrupting system operation, an important option in server environments. • FC-AL adapters tend to cost more than SCSI adapters. PCI BUS Technology • PCI is preferred – 32-bit and 64-bits • PCI-X – An extension to the PCI Bus interface • General PCI standards – PCI 1.0, 2.0 and 3.0 • PCI Express A Note on PCI-X 2.0 (Source PCISIG) • PCI-X 2.0 is an evolutionary, backward compatible technology that builds on the foundation of PCI and PCI-X while offering bandwidths 4 times higher than PCI-X without increasing pin-count. • These new, higher bandwidths are ideal for server-oriented adapter cards in the areas of Fibre Channel, RAID, networking, InfiniBand™ Architecture, SCSI, iSCSI, and other high-bandwidth technologies. PCI-X 2.0 Performance Advantage (Source PCISIG) • Doubles and Quadruples PCI-X bandwidth. • Enables 10Gb Ethernet, 10Gb Fiber Channel, InfiniBand™ Architecture, and other IO technologies. • Performance 32 times higher than the first generation of PCI. Desired Characteristics of Server: Bus and Memory Technologies • Better bus technology – PCI • Memory – In excess of 512 Mbytes – SDRAM or similar memory technology functioning at 10 nanoseconds or less – The 168-pin SDRAM is also known as the DIMM chips as opposed to the 72-pin SIMM chips – 182 DDR RAM – Rambus RAM Desired Characteristics of Server: Reliability • Good back-up facilities – Back-up tape • Uninterruptible Power Supply (UPS) Fault Tolerant Feature for Servers • RAID storage technology – A system based on multiple disk – Hot-swappable disks • Redundant power supply – Hot-swappable power supply Hot Pluggable and Hot Swappable • Hot Pluggable – When a card or a device is plugged into the computer (PCI), the computer will recognize the device automatically and install the device • An example is a NIC • Hot Swappable – A device that can be removed and replaced without having switch off the computer • An example is a hard drive Workstation • Most applications are executed at the workstation in the case of a file server • Therefore, it must be powerful in terms of the processor and the memory • As a rule of thumb, the workstation must be as powerful as it were to be used as a standalone unit to run the applications Workstation Processor and Memory • Powerful processor – Pentium class processor • Adequate memory – 32 Mbytes or more – DIMM preferred although fast EDO SIMM may also be used Workstation Storage and Compatibility • Sufficient storage – Storage in gigabytes – Important in a client-server environment – Front-end tools are stored on the workstation • Speed of storage – Ultra DMA or SCSI preferred – EIDE may also be used • Hardware components with appropriate drivers for the client operating system Reliability • Power surge protector • Uninterruptible Power Supply (UPS), for critical applications END OF MODULE MODULE Repeater An Overview of Repeaters • Used for extending the physical span of a network – An example is the extension of the distance between a hub and a node • Span is often limited by design considerations • 10base5 – The span is limited to 500 meters A Repeater Connection Expanding the Span of the Network Source: Black Box Another Example of Repeater Connection Extending the distance between the backbone and the nodes. Source: Black Box Current Day Use of Repeaters • Fiber optic repeaters are used for extending the distance between two nodes in a link or a network Operations of a Repeater Within the ISO OSI Model • Operates at the lower level of the ISO OSI model, namely layer 1 – Physical layer Physical Layer Medium Repeater Physical Layer Medium Other Devices Used for Extending the Span of a Network • Line Drivers • Short-Haul Modems Another Layer 1 Device • Hub – This is simply an electrical connecting device used in the configuration of a network • The topology in this case would be that of a star topology END OF MODULE MODULE Bridge An Overview of a Bridge • A device used for connecting two LANs operating usually under the same protocol – There are bridges that connect LAN segments operating under different protocols • Currently, the term bridge is loosely being used to describe different interconnecting devices – Used now for connecting LANs operating under different protocols as well Purpose of a Bridge • Facilitate the movement of data packet from one network segment to another • Not a sophisticated internetworking device • Bridge does not perform the routing of information to different segments of a network • Connects two network segments and not multiple network segments Bridge : ISO-OSI Layer of Operation Data Link Layer Data Link Layer Bridge Physical Layer Physical Layer X Medium X Medium A simple bridge operates at the second layer of the ISO model. Practical Bridge Implementations • Local Bridge • Remote Bridge Local and Remote Bridges • Local bridge – Connects two different LANs located locally • Remote bridge – Connects LAN segments that are geographically apart – An example is a device that provide dialup access to a LAN A Practical Bridge Example END OF MODULE MODULE Switch Switch Definition and Purpose • A switch is defined as a device that allows a LAN to be segmented – The segments will operate under the same protocol Difference Between a Switch and a Bridge • A switch focuses on segmenting a LAN • A bridge is concerned with linking two network segments that operate under different protocols Purpose of a Switch • Improve the network performance and reliability • Better manage the network in general Switch : ISO-OSI Layer of Operation Data Link Layer Data Link Layer Switch Physical Layer Physical Layer X Medium X Medium A simple Switch operates at the second layer of the ISO model. Layer 3 Switches • Some switches operate at Layer 3 of the ISO-OSI model • These switches perform routing as well Performance Improvement in Segmented Networks • Performance is improved especially in the case of a bus network • Multiple bus paths are now available for communication • Each segment can engage in simultaneous communication within itself • Easier to isolate a problem to a segment – Thus, better manage the entire network Network Reliability • When one segment does not function, the other segments can continue to function – Offers better reliability to at least part of the function Switches in Ethernet and Token Ring LANs • Switches were originally designed for segmenting Ethernet LANs – Used extensively in configuring large Ethernet bus LANs • Physically the network configured would still largely remain based on the star topology • Switches are now available for token ring networks as well Use of Switches in Linking LAN Segments Crossover Traffic Switch Segment 2 Segment 1 Hub WS Server Hub WS Server Using A Switch to Link Bus LAN Segments Switch Segment 1 Segment 2 Use of Switches in Internetworking • Because the typical inter-networking connection involves multiple segments, the use of a switch is more common than the use of a bridge Use of Switches for Higher Bandwidth 100 MBps Switch WS WS WS WS Each port in theory has a bandwidth of 100 Mbps. END OF MODULE MODULE Switching Technology Module Objectives • Explain the basic operation of a switch • List the switching technologies and describe their operation – Cut-through and store-and-forward technologies The Basic Operation of Switches Receiver’s Address Sender’s Address Data • A data packet is analyzed • Receiver’s addresses is checked • If it indicates the receiver to be in the same segment, the packet is dropped • If it indicates the receiver to be in a different segment, the packet is Switching Technologies • There are two major types of switching technologies – Cut-through – Store-and-forward Cut-Through Technology • Reads only part of the packet – The addresses header – Packet is forwarded accordingly • Bad packets are not filtered • Faster • Less error checking Store-and-Forward Technology • Entire packet is processed • Packets are filtered – Bad packets are filtered • Slower • More error checking Switching Technology Comparison Header Sender’s Add Cut-through Store-and-forward Receiver’s Add Data Switching Technology Operation at the ISO Layer • In each of the two cases of switching technologies no protocol conversion takes place • Forwarding and filtering are done at the MAC layer • A switch switches the traffic based on MAC address Web Research • Fiber channel • Clustering • Load Balancing END OF MODULE MODULE Routers The Purpose of a Router • Connect LANs operating under different protocols • The LANs connected are better known as sub-networks instead of network segments – The term segments is nevertheless used in practice – Each segment basically represents a subnet Router Characteristics • A router is a true internetworking device – Connects different sub-networks together • Establishes a logical path of communication between the sub-networks • Contributes to the modular construction of a network – Network itself is better managed – Network resources are better utilized Internetworking with a Router IEEE 802.3 Sub-network Router PC-NFS Sub-network IEEE 802.5 Sub-network Routers, Switches and Hubs in Perspective Backbone Router Switch Switch Hub S WS Hub S Sub-network 1 WS Hub WS S Hub WS WS S WS Sub-network 2 Difference Between Routers, Switches and Hubs • Hubs – Simply provides the mechanical and electrical connections between the nodes • Switches – – – – Examine the data packet for the destination address Do not alter the data packets Switches based on MAC address Basically a Layer 2 device • Routers – – – – Examine and alter the data packet format Perform protocol conversion Routes based on IP address Basically a Layer 3 device Router Requirements • Requires more processing power compared to switches and bridges • Operations fall within the network layer of the ISO-OSI communication model Router : Network Layer Interface NETWORK LAYER DATA LINK LAYER ROUTER NETWORK LAYER DATA LINK LAYER PHYSICAL LAYER PHYSICAL LAYER X MEDIUM X MEDIUM Layer 3 Layer 2 Layer 1 Switches Devices and Layers NETWORK LAYER Routers DATA LINK LAYER Switches PHYSICAL LAYER Hubs and Repeaters A Practical Router Example Router Router Router Router Router END OF MODULE MODULE Gateway Web Exercise • Build a small network consisting of 4 workstations and 1 server for a small business – Provide details of the hardware in terms of the types of hardware and the cost of the hardware • Connect the network to the Internet – Again provide the cost associated with the hardware required to make the connection • In both of the above cases, also provide a schematic diagram showing the network connections An Introduction to Gateways • Gateways are comprehensive internetworking devices • They can be computers themselves Gateways in the Past • Very popular • They were the only devices that could be used for internetworking • Computers of the past were not designed with network connections in mind – Interconnection of different computer systems has to be managed and driven by an advanced device such as a gateway The Present Scenario • Computers are now designed with due consideration given to network connections • Larger networks could today be configured using internetworking devices – Routers, switches, hubs etc. • Even, mainframes can be connected easily using the above internetworking devices • In the past, because of the different nature of the network (SNA), connecting a mainframe to a LAN often required a gateway (SAN Gateway) Use of Gateways at Present • Used in the rare occasion when neither of the internetworking devices could be used for connecting the sub-networks together • Example – Connection of a legacy mainframe system to a bus LAN Rule of Thump • Gateways are used for interconnecting vastly differing computing environments together SNA Gateway SNA Gateway NIC Card WS WS LAN - Ethernet FEP Mainframe Gateway Interface Card Gateway software IBM - SNA Gateway’s Functional Relationship to the ISO-OSI Model Application Application Presentation Presentation Session Session Transport Transport Network Network Data Link Data Link Physical Physical END OF MODULE END OF MODULE END OF CHAPTER