* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Example #3 – Application Analysis
Zero-configuration networking wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Distributed firewall wikipedia , lookup
Computer network wikipedia , lookup
Deep packet inspection wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
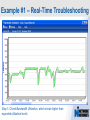
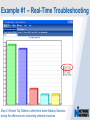
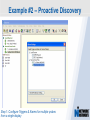
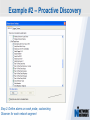
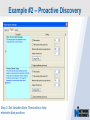
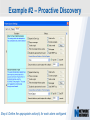
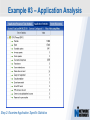
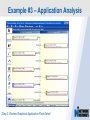
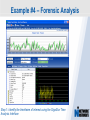
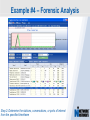
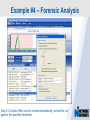
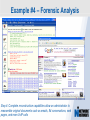
Network Instruments Troubleshooting Techniques Key Elements What to look for in network monitoring solutions… Real Time Statistics Long Term Trending Single Point of Visibility Into Multiple Segments SNMP Management Console Proactive Problem Notification Distributed Network Analysis Capacity Planning, Baselining Networks Triggers and Alarms Visual Network Traffic Flow Standards Based Management for Networks and Devices Application Analysis Troubleshooting & Problem Identification Example #1 – Real-Time Troubleshooting Situation: A large Law firm has been experiencing network slowdowns during peak usage times. Solution: Determine who or what is causing heightened levels of network activity at peak times. Example #1 – Real-Time Troubleshooting Step 1: Check Bandwidth Utilization, which shows higher than expected utilization levels Example #1 – Real-Time Troubleshooting Step 2: Review Top Talkers to determine active Backup Sessions during the afternoon are consuming network resources Example #1 – Recap Situation: A large Law firm has been experiencing network slowdowns during peak usage times late in the afternoon. Solution: Determine who or what is causing heightened levels of network activity at peak times. Result: By reviewing Observer’s Real-Time Statistics, network administrators were able to quickly determined that backups were running during work hours and promptly reconfigured the backup schedule. Observer provides real-time identification of network issues for faster troubleshooting. Example #2 – Proactive Discovery Situation: Network Operations for a large Community College is concerned with Peer to Peer client usage and virus activity on their wired and wireless networks. Solution: Monitor both the Wired and Wireless environment with Observer’s Triggers and Alarms. Example #2 – Proactive Discovery Step 1: Configure Triggers & Alarms for multiple probes from a single display Example #2 – Proactive Discovery Step 2: Define alarms on each probe, customizing Observer for each network segment Example #2 – Proactive Discovery Step 3: Set Variable Alarm Thresholds to help eliminate false positives Example #2 – Proactive Discovery Step 4: Define the appropriate action(s) for each alarm configured Example #2 – Recap Situation: Network Operations for a large Community College is concerned with Peer to Peer client usage and virus activity on their wired and wireless networks. Solution: Monitor both the Wired and Wireless environment with Observer’s Triggers and Alarms. Result: Using Observer’s Proactive Network Monitoring tools, the network operations team quickly identified a virus outbreak and prohibited illegal usage. Observer provides proactive discovery and notification of rogue elements. Example #3 – Application Analysis Situation: An large accounting firm has the need to track and identify application metrics, such as response time, as well as troubleshoot application connections. Solution: Application Analysis, paired with Connection Dynamics, offers an in-depth view of application response time, statistics, and conversation flows. Example #3 – Application Analysis Step 1: Monitor Application Level Response Time Example #3 – Application Analysis Step 2: Examine Application Specific Statistics Example #3 – Application Analysis Step 3: Review Graphical Application Flow Detail Example #3 – Application Analysis Situation: An large accounting firm has the need to track and identify application metrics, such as response time, as well as troubleshoot application connections. Solution: Application Analysis, paired with Connection Dynamics, offers an in-depth view of application response time, statistics, and conversation flows. Result: Isolate and identify application delay on the network, to put the responsibility on the proper group, and offer faster problem resolution for users. Observer allows you the ability to quickly differentiate between Network and Application Performance Example #4 – Forensic Analysis Situation: A major retail company has been tasked with researching the violations of their acceptable use policies by a former employee. Solution: The GigaStor appliance, featuring a time-based navigation interface, allows for complete write-to-disk at Gigabit line speed, to ensure all necessary data is captured and stored Example #4 – Forensic Analysis Step 1: Identify the timeframe of interest using the GigaStor Time Analysis Interface Example #4 – Forensic Analysis Step 2: Determine the stations, conversations, or ports of interest from the specified timeframe Example #4 – Forensic Analysis Step 3: Complex filters can be created automatically, and will be run against the specified timeframe Example #4 – Forensic Analysis Step 4: Complete reconstruction capabilities allow an administrator to reassemble original documents such as emails, IM conversations, web pages, and even VoIP calls Example #4 – Forensic Analysis Situation: A major retail company has been tasked with researching the violations of their acceptable use policies by a former employee. Solution: The GigaStor appliance, featuring a time-based navigation interface, allows for complete write-to-disk at Gigabit line speed, to ensure all necessary data is captured and stored. Result: Proactive monitoring allows the organization to have relevant information available without the need to recreate an issue, or, in this case, not have the ability to verify a potential conflict with their acceptable use policy. From Hype to Adoption By 2009, there will be over 155 million business IP end points in operation Market researchers expect the number of VoIP users worldwide to increase from around five million in 2004 to 200 million subscribers in 2010 http://www.instat.com/r/nrep/2004/IN0401446NT.htm http://www.heise.de/english/newsticker/news/64129 VoIP service is expected to grow 18-fold – from $1.25 billion in 2004 to $23.4 billion in 2009 – representing total revenues of $62 billion to be spent on the technology over the five-year period. http://www.techweb.com/wire/networking/172900487 Enterprise Pricing Enterprise Pricing Expert Observer Includes VoIP $ 2,895 Observer Suite Includes VoIP $ 3,995 10/100/1000 Probe Appliance Includes VoIP $ 2,495 Gigabit Probe Appliance Includes VoIP $ 11,995 4 TB GigaStor Includes VoIP $ 35,000 8 TB GigaStor Includes VoIP $ 50,000 VoIP Analysis included at no additional charge Shipped with a 64-bit Core, with support for 32-bit systems Gigabit and WAN Appliances are all 64-bit systems Network Instruments continues to lead the analysis industry in performance and value