* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Layer 5
Wake-on-LAN wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
Distributed firewall wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Network tap wikipedia , lookup
IEEE 802.11 wikipedia , lookup
Computer network wikipedia , lookup
Airborne Networking wikipedia , lookup
Deep packet inspection wikipedia , lookup
Internet protocol suite wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
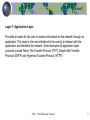
Lecture 5 Information Systems Spring 2011 Convener: Houman Younessi 1-860-548-7880 [email protected] ISM - © 2010 Houman Younessi 1 Lecture 5 Islands of Information/Automation Need for inter-communication ISM - © 2010 Houman Younessi 2 Lecture 5 Network: A collection of links arranged so that messages may be passed from one part to another usually over multiple links. Data Communication Networks Tele-Communication Networks ISM - © 2010 Houman Younessi 3 Lecture 5 Network Protocols The Open Systems Interconnection Reference Model (OSI Model or OSI Reference Model for short) is a layered, abstract description for communications and computer network protocol design. ISM - © 2010 Houman Younessi 4 Lecture 5 Layer 1: Physical Layer Defines all the electrical and physical specifications for devices including layout of pins, voltages, and cable specifications. Hubs, repeaters, network adapters and Host Bus Adapters (HBAs used in Storage Area Networks) are physical-layer devices. Ethernet incorporates both this layer and the data-link layer (Layer 2). The same applies to other local-area networks, such as Token ring, FDDI, and IEEE 802.11. The major functions and services performed by the physical layer are: • Establish/terminate a connection • Contention resolution and flow control • Modulation, or conversion between the representation of digital data in user equipment and the corresponding signals transmitted over a communications channel. These are signals operating over the physical cabling—copper and fiber optic, for example—or over a radio link. ISM - © 2010 Houman Younessi 5 Lecture 5 Layer 2: Data Link Layer Transfers data between network entities and to detect and possibly correct errors that may occur in the Physical layer. The addressing scheme is physical which means that the addresses are hard-coded into the network cards at the time of manufacture. The addressing scheme is flat. Examples are Ethernet, HDLC and ADCCP for point-to-point or packet-switched networks and Aloha for local area networks. On IEEE 802 local area networks, and some non-IEEE 802 networks such as FDDI, this layer may be split into a Media Access Control (MAC) layer and the IEEE 802.2 Logical Link Control (LLC) layer. This is the layer at which the bridges and switches operate. Connectivity is provided only among locally attached network nodes. ISM - © 2010 Houman Younessi 6 Lecture 5 Layer 3: Network Layer Provides the functional and procedural means of transferring variable length data sequences from a source to a destination via one or more networks while maintaining the quality of service requested by the Transport layer. The Network layer performs network routing, flow control, segmentation/de-segmentation, and error control functions. Routers operate at this layer—sending data throughout the extended network and making the Internet possible (there also exist layer 3 (or IP) switches). This is a logical addressing scheme – values are chosen by the network engineer. The addressing scheme is hierarchical. The best known example of a layer 3 protocol is the Internet Protocol (IP). ISM - © 2010 Houman Younessi 7 Lecture 5 Layer 4: Transport Layer Provides transparent transfer of data between end users, thus relieving the upper layers from any concern while providing reliable and cost-effective data transfer. The transport layer controls the reliability of a given link. Some protocols are state and connection oriented. This means that the transport layer can keep track of the packets and retransmit those that fail. The best known example of a layer 4 protocol is the Transmission Control Protocol (TCP). It is the layer that converts messages into TCP, User Datagram Protocol (UDP), Stream Control Transmission Protocol (SCTP), etc. packets. ISM - © 2010 Houman Younessi 8 Lecture 5 Layer 5: Session Layer Controls the dialogues (sessions) between computers. It establishes, manages and terminates the connections between the local and remote application. It provides for either duplex or half-duplex operation and establishes checkpointing, adjournment, termination, and restart procedures. The OSI model made this layer responsible for "graceful close" of sessions, which is a property of TCP, and also for session check-pointing and recovery, which is not usually used in the Internet protocol suite. ISM - © 2010 Houman Younessi 9 Lecture 5 Layer 6: Presentation Layer Transforms data to provide a standard interface for the Application layer. MIME encoding, data compression, data encryption and similar manipulation of the presentation is done at this layer to present the data as a service or protocol developer sees fit. Examples: converting an EBCDIC-coded text file to an ASCII-coded file, or serializing objects and other data structures into and out of XML. ISM - © 2010 Houman Younessi 10 Lecture 5 Layer 7: Application Layer Provides a means for the user to access information on the network through an application. This layer is the main interface for the user(s) to interact with the application and therefore the network. Some examples of application layer protocols include Telnet, File Transfer Protocol (FTP), Simple Mail Transfer Protocol (SMTP) and Hypertext Transfer Protocol (HTTP). ISM - © 2010 Houman Younessi 11 Lecture 5 ISM - © 2010 Houman Younessi 12 Lecture 5 Towards a Real-time Infra-structure: Better Data – Better Decisions Improved Process Visibility Improved Process Efficiency Sense-and-respond (respond to actual demand rather than forecasted demand) But for this to take place, we need to integrate more than just the production. ISM - © 2010 Houman Younessi 13