* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download PPT Version
Survey
Document related concepts
Dynamic Host Configuration Protocol wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Wireless security wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Transcript
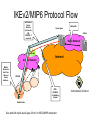
Overview of the Mobile IPv6 Bootstrapping Problem James Kempf DoCoMo Labs USA Thursday March 10, 2005 Outline • What needs to be dynamically configured? – Mobile IP WG calls dynamic configuration “bootstrapping” • What are the security problems and measures? • How is EAP being proposed as a solution? • Analysis of EAP Solution • Summary What Needs to be Dynamically Configured? Bootstrapping in the Mobile IPv6 Standard • Bootstrapping based on RFC 3775: – Topology-dependent dynamic home agent discovery – Authorized, dynamically autoconfigured home address with above – Preconfigured IKE preshared key to avoid host certificate provisioning Pre-provisioned information required on Mobile Node (best case): Home subnet prefix Home Agent/Mobile Node preshared key indexed by NAI on Home Agent for IKEv1 Phase 1 What’s Missing? • Topology-free dynamic Home Agent Address discovery • Authorized, dynamically configured home address with above • Credentials for IKE authorization of mobility service are AAA-like user/password credentials – Avoids host certificate provisioning and preconfigured preshared key Pre-provisioned information required on the Mobile Node: Topology-free host identifier (e.g. NAI) Some credentials for authorizing mobility service through EAPoIKEv2 What Needs to Be Configured? • Home Agent address? – Yes, required • Home Address? – Possibly, but that can be configured via IKEv2 too • IPsec SA? – No, that should be set up using IKE • Security credentials for IKE session? – Depends on the deployment scenario – Could be configured out of band or as part of the bootstrapping process – When EAP is used, security credentials for IKE (e.g. preshared key) are bootstrapped too What are the Security Problems and Measures? Home Agent/Mobile Node SA Establishment • Server to host data origin and integrity/replay protection – To protect a legitimate Mobile Node against rogue Home Agents • Host to server data origin and integrity/replay protection, and host mobility service authorization – To protect Home Agent from theft or disruption of mobility service by an attacker • Stateless Home Agent initial transaction – To avoid DoS state depletion attacks • This is covered by IKEv2 Home Address Discovery • Server to host data origin and integrity/replay protection – To protect a legitimate Mobile Node against rogue Home Agents handing out bogus addresses • Host to server data origin and integrity/replay protection – To protect Home Agents against unauthorized Mobile Nodes obtaining home addresses • This is covered by IKEv2 too IKE Security Credentials • Bidirectional data origin and integrity/replay protection – To avoid someone spoofing the credential • Bidirectional confidentiality protection – To avoid someone stealing the credential • This can’t be provided by IKE because it is used to secure IKE NonThreats • “Unauthorized” discovery of the Home Agent address – Even if the address is only sent to authorized users, there is no guarantee that an authorized user will not misuse it • Bogus Home Agent discovery – If the Mobile Node is given a bogus Home Agent address, it will not authenticate during IKEv2 transaction • Eavesdropping to find the Home Agent address while discovered – Home Agent address must be the destination address on Binding Update and so is always public • Attacks on the Mobile Node’s home address – The home address is typically published in the DNS anyway and therefore is public How is EAP being Proposed as a Solution? ref: draft-giaretta-mip6-authorization-eap-02.txt EAP Configuration Protocol Flow NAS sends credentials to local AAA Local AAA relays decision to NAS Internet Access! Home AAA replies with authentication and authorization decision and Master Key Home Agent Address, Credentials for Mobility ServiceAuthorization, and optional Home Address Included! Home Network AAA-L Border Router Access Network Master Key pushed to AP Internet AAA-H AR AP/NAS NAS authorizes Internet access Mobile Node now has Home Agent Address and preshared key (but not IPsec SAs)!. Terminal sends credentials to NAS Mobile Node Authorization Decision! Local AAA sends credentials to home AAA IKEv2/MIP6 Protocol Flow EAPoIKEv2 (Home Address returned in IKE CONFIG if required) EAPoAAA Home Agent AAA-H Home Network Border Router Access Network Mobile Node now has IPsec SAs and Home Address. Internet AR AP/NAS ESP + BU/BAck for Binding Update Mobile Node See draft-ietf-mipv6-ikev2-ipsec-00.txt for IKEv2/MIP6 interaction Authorization Decision! Analysis of EAP Solution Problems Solved by EAP* • Secure configuration of Home Agent address and home address via EAP method – Data origin and integrity/replay protection server to host – Also confidentiality and host to server authentication • Secure configuration of IKE credentials (e.g. preshared key) – Bidirectional confidentiality and data origin, integrity/replay protection – Mobility service authentication and authorization credentials are the same as for network access • Optimization of signaling to reduce protocol needed for Home Agent discovery and confine it to a time when configuration is being done anyway – Secondary effect *Assumes a secure, extensible EAP method! Problems Not Solved by EAP • Bootstrapping Home Agent address when the Home Network Service Provider and Mobility Service Provider are not the same – EAP bootstrapping depends on AAA-H to provide a Home Agent address • Bootstrapping mobility service authorization when the Access Service Authorizer and Mobility Service Authorizer are not the same – EAP bootstrapping uses network access credentials for mobility service authorization and Home Agent address discovery • Bootstrapping when EAP is not used for network access authentication and authorization Problems Created by EAP for Configuration • Management of Home Agent address, IKE session credentials, and potentially home address information in AAA-H – See draft-giaretta-mip6-aaa-ha-goals-00.txt for discussion of requirements/issues • Opens a “hole” in original design goal tightly confining EAP for configuration to network access keys only – Now, IP address information is configured also – What else will drive through that hole? Summary Summary • MIP6 bootstrapping requires configuration of Home Agent address from nontopological identity – Home address can be configured by IKEv2 – Optional configuration of credentials for IKE session if not preconfigured • EAP provides a mechanism for configuring all of the above – Only method that can securely provision IKE session credentials • Other methods provide mechanisms for configuring some of the above or in cases where EAP can’t be used The Question on Debate: Does EAP configuration provide enough benefit to expand the current deliberately narrow scope of applicability? Questions/Comments?