* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Chapter 1
Net neutrality law wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Airborne Networking wikipedia , lookup
Distributed firewall wikipedia , lookup
Network tap wikipedia , lookup
Computer network wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Deep packet inspection wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Internet protocol suite wikipedia , lookup
UniPro protocol stack wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
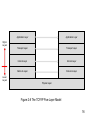
Building The Mobile Internet Internet Sessions A Common Scenario ? • You are cycling to University • Talking on your mobile • You pass many ‘cell-towers’ on the journey • Each time you move between cell-towers you lose the call. • You have to stop and make the call again • You think..’This is a really cool service’..? 2 A Common Scenario ?? • On long journeys you need to contact a new cell-phone provider and sign up for a temporary contract. • When you are on an international train and streaming a movie, it stops periodically and you have to contact a new company and arrange a new contract before continuing with the movie. • Then the movie starts over from the 3 beginning… Sessions • I don’t think this would be widely accepted • What users expect (even demand) is seamless real-time mobility. • This has become known as ‘Session-mobility’ • The Internet was not designed to enable the implementation of this kind of provision. 4 The Internet and the MobileInternet • Things get even more challenging when moving through differing types of access network. e.g. from Wi Fi to Cellular, or between different operators. • What we need is a ‘New Internet’ • A ‘Mobile-Internet’ 5 The Mobile-Internet • The Mobile-Internet must be a Pervasive IP-based network that can link fixed and mobile nodes, • Nodes, can have many characteristics and types 6 The Mobile Internet • • • • • • • • Nodes may be:Sensors; Servers; Stand-alone or Distributed; Battery-powered or Mains Powered; User initiated or Self Initiating Permanent or Temporary State-of-the-Art, or Legacy 7 The Internet: Review of Characteristics • Lets revisit the Internet and see if we can identify difficulties in making sessionmobility possible: 8 Network Routers Networks Network Network Network Hosts Network Figure 2-1: The Internet: A Network of Networks 9 Network Original data Packetized data Re-assembled original data Figure 2-2: Packet-switching: Dividing a data Source into Packets at the Sender, and Reassembling the Data-Source at the Receiver 10 Web e-Mail Telnet IP Ethernet Figure 2-3: DWDM WiFi IP Over Everything. Everything over IP 11 Bit 0 0 4 8 Net-id 12 16 20 24 28 32 Host-id Figure 2-4: IP Addresses consist of a net-id and a host-id part. 12 10.0.0.0 / 8 10.1.0.0 / 16 10.1.0.0 / 24 10.2.0.0 / 16 10.3.0.0 / 16 10.1.1.0 / 24 10.1.2.0 / 28 10.1.2.0 / 24 10.1.2.128 / 28 Figure 2-3 CIDR Subnetting 13 Bit 0 0 4 Version 8 IHL 12 16 20 24 Type of Service 28 32 Total Length 32 Identification Flags Fragment Offset 64 Time to Live Protocol 96 Header Checksum IPv4 Source Address 128 IPv4 Destination Address 160 Options Padding 192 Payload (variable length) The IPv4 Packet Format 14 Bit 0 32 64 0 4 Version 8 12 16 20 Traffic Class 24 28 32 Flow Label Next Header Payload Length Hop Limit IPv6 Source Address 128 192 IPv6 Destination Address 256 320 Payload (variable length) Figure 2-7 IPv6 Packet Format Documented in RFC 2460 Application Layer Application Layer Transport Layer Transport Layer Internet Layer Internet Layer Data Link Layer Data Link Layer Higher Layers Lower Layers Physical Layer Figure 2-8 The TCP/IP Five-Layer Model 16 Data Link Layer Internet Layer Transport Layer Application Layer Application data Figure 2-9 Data from Higher Layers Encapsulated Lower-layer Packets 17 Bit 0 0 4 8 12 16 20 24 Source Port 28 32 Destination Port 32 Length Checksum 64 Payload (variable length) Figure 2-10 UDP Datagram 18 Bit 0 0 4 8 12 16 20 24 Source Port 28 32 Destination Port 32 Sequence Number 64 Acknowledgment Number 96 128 160 Offset Reserved Checksum Flags Window Size Header Checksum Urgent Pointer Options (variable length 0-320 bits, depending on offset field) Payload (variable length) Figure 2-11 TCP Packet 19 “.” .com webex.com .net .nl linksys.com cisco.com host1.cisco.com host2.cisco.com 20 Building The Mobile Internet • Important Details; – Socket API – Network Address Translation 21 Network Address Translation • A cornerstone of Internet implementation is that every host should have a unique IP address. • Currently, this is not strictly the case; • Networks use Internal IP addressing; • Not exposed to the Internet 22 Network Address Translation • Perceived Benefits? • Security: IP address of specific user hidden! • Easier Network set-up with large address ranges ‘internal’ to the local network. • Reduces demand for Global IP addresses • (Won’t be needed with IPv6) 23 Network Address Translation • Disadvantages: • Internal and External IP addresses must be unique • Special range of IP addresses reserved for Internal use: • 10.0.0.0/8 • 172.16.0.0/12 • 192.168.0.0/16 24 • Translation Process required (NAT) NAT • Communication across the Internet requires interaction between globally unique IP addresses • A host with a locally-unique IP address communicating with a remote host, requires IP address translation at a host which has a globally-unique address. • The translation process (NAT) breaks the normal communication between Internet hosts. 25 Sockets • For an Application to connect to another Application on the Internet, requires an API. • The API must create connections to other hosts; • The most common abstraction is the Socket; • The API associates a socket-identifier with the IP address of a host, and a Port; 26 Sockets, Protocols and Ports Application 1 Application 2 Application 3 Application 4 Socket references TCP Sockets TCP Ports Sockets bound to ports 1 2 3 1 65535 2 3 65535 UDP TCP IP Sockets Protocols and Ports The Data Link Layer • The Data Link layer or Network Interface Layer takes IP packets and encapsulates them for transport over the physical layer; • Ethernet has become the dominant Layer 2 protocol in many networks; 28 Ethernet (IEEE802.3) • Ethernet (IEE 802.3) implements a unique MAC address to the physical interface card • The MAC address is unique, • Specified by the hardware manufacturer • Cannot be used for Interdomain routing 29 Address Resolution Protocol • To map an IP address to a hardware address requires an Address Resolution Protocol (ARP). • Typically a host receiving an IP address broadcasts a message to all the hosts to which it is connected asking for the mac address that the IP address is associated with. • The specific host responds with its MAC 30 address. ARP and Caching • In an effort to improve efficiency, host routers cache MAC-IP associations • If a host changes its IP address it could respond with its cached address rather than its new address. 31 Sessions and Mobility • A TCP communication is identified with the 5 tuple: – Local IP Address – Local Port – Remote IP Address – Remote Port – Socket Identifier 32 Sessions and Mobility • The entire structure was built on the implicit assumption that IP addresses were essentially fixed and that Hosts did not change location. • If a host moves they need a new IP address; • If a host gets a new IP address then the Socket ID for the communication must change 33 • Therefore the session breaks Sessions and Mobility • Another consequence of the TCP/IP inherent design is that an IP address in fact performs two functions; • It is a location-identifier • It is an end-point-identifier • In other words, an IP address identfies the specific host, and also its location in the network. • Not an issue until hosts start to move 34 around…! Strategies • Accept that application sessions will break; • Introduce an application layer ‘sessionpersistence’ mechanism • Keep the same IP address when moving; • Introduce a new Layer • Redesign the TCP/IP protocol stack to achieve separation of locators and endpoint identifiers 35 Accept that Application Sessions will Break • Easy option • For some situations session breaks don’t matter • Nomadic mobility: Fouus on seamless access to different networks • User can switch networks seamlessly • However, sessions will not necessarily ‘stay up’ 36 Introduce a ‘SessionPersistence’ mechanism in the Application Layer • Requires the Application to implement a session state; • Probably impractical • Maybe not desirable – Cookies in web browsers do this currently – Big security and privacy issues 37 Keep the same IP Address when Moving • The IP layer is an abstraction layer on top of the physical infrastructure, • When a host moves, it must chaange its IP address so that a source knows where to route its packets • This can be done to an extent by ‘tunneling’. • Make multiple physical layers look like one layer to the IP layer by encapsulating layer 38 2 packets in other layer 2 packets Introduce a New Layer • Consider implementing a session layer between the TCP layer and the Application Layer. • This is akin to revisiting the ISO-OSI Seven layer model which had a Session Layer above the TCP layer and under the Application layer. • Perhaps we used the wrong stack after all…? 39 Redesign TCP/IP to Separate Location ID and Host ID • A fairly fundamental approach • Separate entities to describe – A node – Its location • • • • Possible in theory Difficult to implement Maybe the only realistic way forward Explored in some detail later 40