* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download BSCI Module 2 Lesson 1
Survey
Document related concepts
Transcript
Configuring EIGRP
BSCI Module 2-1 – Introduction to EIGRP
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
1
Objectives
This module will cover topics which allow students to
meet the following objectives:
Describe the key capabilities that distinguish EIGRP from other
routing protocols
Identify the four key technologies employed by EIGRP
Describe how EIGRP operates
Describe the five components of the metric used by EIGRP
Calculate the EIGRP metric for a range of pathways between
routers
Explain how IGRP routes are integrated into EIGRP routes and
vice-versa
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
2
Purpose of this Lesson
Coverage of topics new to the “EIGRP” module of BSCI.
What’s new in this module?
EIGRP metric calculations for pathway ranges between routers.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
3
EIGRP Features
There are several key differences with EIGRP from
other routing protocols which are explored in this
module.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
4
EIGRP Key Technologies
Neighbor discover/recovery
Reliable Transport Protocol (RTP)
DUAL finite-state machine
Protocol-dependent modules (PDMs)
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
5
The Diffusing Update Algorithm (DUAL)
How does EIGRP determine
which routes are loop-free?
Each of A’s neighbors is
reporting reachability to E:
B with a cost of 10
C with a cost of 10
D with a cost of 30
These three costs are
called the reported
distance (RD); the
distance each neighbor is
reporting to a given
destination
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
6
The Diffusing Update Algorithm (DUAL)
At A, the total cost to reach E is:
20 through B
25 through C
45 through D
The best of these three
paths is the path through
B, with a cost of 20
This is the feasible distance (FD)
The route with the best FD is
known as the “Successor”
All next best routes are known as
“Feasible Successors”
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
7
The Diffusing Update Algorithm (DUAL)
A uses the FD and the RD
to determine which paths
are loop-free
The best path (FD) is used
as a benchmark; all paths
with RDs lower than the FD
cannot contain loops
The algorithm may mark
some loop-free paths as
loops
However, it is guaranteed
never to mark a looped path
as loop-free
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
8
The Diffusing Update Algorithm (DUAL)
At A:
The path through B is the
best path (FD), at 20
C can reach E with a cost
of 10; 10 (RD) is less than
20 (FD), so this path is
loop-free.
D can reach E with a
cost of 30; 30 (RD) is
not less than 20 (FD),
so EIGRP assumes
this path is a loop.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
9
EIGRP Topology Table
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
10
EIGRP Neighbor Status
RTRA#show ip eigrp neighbors
IP-EIGRP neighbors for process 1
H
Address
Interface Hold Uptime SRTT
(sec)
(ms)
2
10.1.1.1 Et0
12
6d16h
20
1
10.1.4.3 Et1
13
2w2d
87
0
10.1.4.2 Et1
10
2w2d
85
RTO
Q
Cnt
200 0
522 0
510 0
Seq
Num
233
452
3
Seconds Remaining Before Declaring Neighbor Down
How Long Since the Last Time Neighbor Was Discovered
How Long It Takes for This Neighbor To Respond To Reliable Packets
How Long to Wait Before Retransmitting If No Acknowledgement
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
11
EIGRP IP Routing Table
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
12
Example: EIGRP Tables
Router C’s tables:
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
13
EIGRP Packets
Hello: Establish neighbor relationships.
Update: Send routing updates
Query: Ask neighbors about routing information
Reply: Respond to query about routing information
ACK: Acknowledge a reliable packet
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
14
Initial Route Discovery
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
15
EIGRP Metric
Same metric components as IGRP:
Bandwidth
Delay
Reliability
Loading
MTU
EIGRP metric is IGRP metric multiplied by 256
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
16
EIGRP Metric Calculation
By default, EIGRP metric:
Metric = bandwidth (slowest link only) + delay (sum of delays)
Delay = sum of the delays in the path, in tens of
microseconds, multiplied by 256.
Bandwidth = [(10^7) / (minimum bandwidth link along
the path, in kilobits per second)] * 256
Formula with default K values (K1 = 1, K2 = 0, K3 = 1,
K4 = 0, K5 = 0):
Metric = [K1 * BW + ((K2 * BW) / (256 – load)) + K3 * delay]
If K5 not equal to 0:
Metric = Metric * [K5 / (reliability + K4)]
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
17
EIGRP Metrics Calculation Example
ABCD
Least bandwidth 64 kbps
Total delay 6,000
AXYZD
Least bandwidth 256 kbps
Total delay 8,000
Delay is the sum of all the delays of the links along the paths:
Delay = [delay in tens of microseconds] x 256
BW is the lowest bandwidth of the links along the paths:
BW = [10,000,000 / (bandwidth in kbps)] x 256
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
18
EIGRP Metrics Are Backward-Compatible
with IGRP
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
19
Summary
EIGRP capabilities include fast convergence and support for
VLSM, partial updates, and multiple network layer protocols.
EIGRP key technologies are: neighbor discovery/recovery, RTP,
DUAL finite-state machine, and protocol-dependent modules.
EIGRP uses three tables: neighbor table, topology table, and
routing table. The routing table contains the best route to each
destination, called the successor route. A feasible successor route
is a backup route to a destination; it is kept in the topology table.
EIGRP uses the same metric components as IGRP: delay,
bandwidth, reliability, load, and MTU.
By default, EIGRP metric = bandwidth (slowest link) + delay (sum
of delays).
EIGRP metrics are backward-compatible with IGRP; the EIGRPequivalent metric is the IGRP metric multiplied by 256.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
20
Self Check
What is a reported distance?
What is a feasible distance?
EIGRP uses three tables: name the three tables: __________,
____________, _____________. Which of the tables contains the
best route or successor route to each destination?
EIGRP uses what metrics? __________, _________, _________,
__________, ___________
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
21
Resources
http://www.cisco.com/en/US/tech/tk365/technologies_tech_note09
186a008009405c.shtml
http://www.cisco.com/en/US/tech/tk365/technologies_tech_note09
186a0080093f07.shtml
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
22
Q and A
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
23
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
24
Configuring EIGRP
BSCI Module 2-2 – Implementing and Verifying EIGRP
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
25
Objectives
Upon completing this lesson, you will be able to
describe how to implement EIGRP routing. This ability
includes being able to meet these objectives:
Describe the commands used in a basic EIGRP configuration
task
Explain how to configure a router to use wildcard masks to
select the interfaces and networks that will participate in EIGRP
routing
Configure the gateway of last resort or default route
Verify that the router recognizes EIGRP neighbors and routes
Verify EIGRP operations
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
26
Purpose of this Lesson
Coverage of topics new to the “EIGRP” module of BSCI.
What’s new in this module?
Describe the commands used in a basic EIGRP configuration task
Explain how to configure a router to use wildcard masks to select
the interfaces and networks that will participate in EIGRP routing
Configure the gateway of last resort or default route.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
27
Configuring EIGRP
Router(config)#
router eigrp autonomous-system-number
Defines EIGRP as the IP routing protocol.
All routers in the internetwork that must exchange EIGRP
routing updates must have the same autonomous system
number.
Router(config-router)#
network network-number [wildcard-mask]
Identifies attached networks participating in EIGRP.
The wildcard-mask is an inverse mask used to
determine how to interpret the address. The mask has
wildcard bits, where 0 is a match and 1 is “don’t care.”
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
28
Configuring EIGRP (Cont.)
Router(config-if)#
bandwidth kilobits
Defines the interface’s bandwidth for the purposes of
sending routing update traffic.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
29
Configuring EIGRP for IP
Network 192.168.1.0 is not configured on router A,
because it is not directly connected to router A.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
30
Configuring EIGRP with IP (cont.)
Classful configuration example:
What’s wrong with this?
routerA(config)#router eigrp 109
routerA(config-router)#network 10.1.0.0
routerA(config-router)#network 10.4.0.0
routerA(config-router)#network 172.16.7.0
routerA(config-router)#network 172.16.2.0
Classless configuration example:
routerA(config)#router eigrp 109
routerA(config-router)#network 10.1.0.0 0.0.255.255
routerA(config-router)#network 10.4.0.0 0.0.255.255
routerA(config-router)#network 172.16.2.0 0.0.0.255
routerA(config-router)#network 172.16.7.0 0.0.0.255
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
31
Using the Wildcard Mask in EIGRP
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
32
Using and Configuring the ip default-network
command for EIGRP
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
33
Example R1 EIGRP Configuration
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
34
R2 EIGRP Configuration
<output omitted>
interface FastEthernet0/0
ip address 172.17.2.2 255.255.255.0
<output omitted>
interface Serial0/0/1
bandwidth 64
ip address 192.168.1.102 255.255.255.224
<output omitted>
router eigrp 100
network 172.17.2.0 0.0.0.255
network 192.168.1.0
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
35
EIGRP Manual Summarization
Automatic summarization of routes at the major classful
boundary is a characteristic of distance vector
operations.
With EIGRP you can disable automatic summarization
and create one or more summary routes within the
network on any bit boundary as long as a more specific
route exists in the routing table.
When a more specific route no longer exists the summary
route is removed from the routing table.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
36
EIGRP Summarization
In the routing table, summary routes are automatically
assigned to interface null0 to prevent routing loops.
This is also true for manual summarization
If the summarizing router receives a packet for a
destination that is included in the summary route but is
unknown by the router, the router will send it to the null
interface – drops the packet.
For manual summarization to be effective, blocks of
contiguous addresses (subnets) must come together at a
common router so that the router can advertise a single
summary route.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
37
Configuring Summary Routes
Summary routes are manually configured at the
interface.
if)# ip summary-address eigrp [as number] [network] [subnet mask]
Remember, these are summary addresses that your
router is summarizing
Summary addresses also cut down on the number of
eigrp queries.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
38
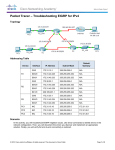
Verifying EIGRP: show ip eigrp neighbors
R1#show ip eigrp neighbors
IP-EIGRP neighbors for process 100
H
Address
Interface
Hold Uptime
SRTT
(sec)
(ms)
0
192.168.1.102 Se0/0/1
10
00:07:22
10
R1#
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
RTO
Q Seq
Cnt Num
2280 0 5
39
Verifying EIGRP: show ip route
eigrp
R1#show ip route eigrp
D
172.17.0.0/16 [90/40514560] via 192.168.1.102, 00:07:01, Serial0/0/1
172.16.0.0/16 is variably subnetted, 2 subnets, 2 masks
D
172.16.0.0/16 is a summary, 00:05:13, Null0
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
D
192.168.1.0/24 is a summary, 00:05:13, Null0
R1#show ip route
<output omitted>
Gateway of last resort is not set
D
172.17.0.0/16 [90/40514560] via 192.168.1.102, 00:06:55, Serial0/0/1
172.16.0.0/16 is variably subnetted, 2 subnets, 2 masks
D
172.16.0.0/16 is a summary, 00:05:07, Null0
C
172.16.1.0/24 is directly connected, FastEthernet0/0
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C
192.168.1.96/27 is directly connected, Serial0/0/1
D
192.168.1.0/24 is a summary, 00:05:07, Null0
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
40
Verifying EIGRP: show ip protocols
R1#show ip protocols
Routing Protocol is "eigrp 100"
Outgoing update filter list for all interfaces is not set
Incoming update filter list for all interfaces is not set
Default networks flagged in outgoing updates
Default networks accepted from incoming updates
EIGRP metric weight K1=1, K2=0, K3=1, K4=0, K5=0
EIGRP maximum hopcount 100
EIGRP maximum metric variance 1
Redistributing: eigrp 100
EIGRP NSF-aware route hold timer is 240s
<output omitted>
Maximum path: 4
Routing for Networks:
172.16.1.0/24
192.168.1.0
Routing Information Sources:
Gateway
Distance
Last Update
(this router)
90
00:09:38
Gateway
Distance
Last Update
192.168.1.102
90
00:09:40
Distance: internal 90 external 170
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
41
Verifying EIGRP: show ip eigrp
interfaces
R1#show ip eigrp interfaces
IP-EIGRP interfaces for process 100
Xmit Queue
Interface
Peers Un/Reliable
Fa0/0
0
0/0
Se0/0/1
1
0/0
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
Mean
SRTT
0
10
Pacing Time
Un/Reliable
0/10
10/380
Multicast
Flow Timer
0
424
Pending
Routes
0
0
42
Verifying EIGRP: show ip eigrp
topology
R1#show ip eigrp topology
IP-EIGRP Topology Table for AS(100)/ID(192.168.1.101)
Codes: P - Passive, A - Active, U - Update, Q - Query, R - Reply,
r - reply Status, s - sia Status
P 192.168.1.96/27, 1 successors, FD is 40512000
via Connected, Serial0/0/1
P 192.168.1.0/24, 1 successors, FD is 40512000
via Summary (40512000/0), Null0
P 172.16.0.0/16, 1 successors, FD is 28160
via Summary (28160/0), Null0
P 172.16.1.0/24, 1 successors, FD is 28160
via Connected, FastEthernet0/0
P 172.17.0.0/16, 1 successors, FD is 40514560
via 192.168.1.102 (40514560/28160), Serial0/0/1
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
43
Verifying EIGRP: show ip eigrp
traffic
R1#show ip eigrp traffic
IP-EIGRP Traffic Statistics for AS 100
Hellos sent/received: 429/192
Updates sent/received: 4/4
Queries sent/received: 1/0
Replies sent/received: 0/1
Acks sent/received: 4/3
Input queue high water mark 1, 0 drops
SIA-Queries sent/received: 0/0
SIA-Replies sent/received: 0/0
Hello Process ID: 113
PDM Process ID: 73
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
44
Summary
The configuration commands for basic EIGRP include:
router eigrp autonomous-system
network network-number [wildcard-mask]
bandwidth kilobits
The optional wildcard-mask parameter in the network
command is an inverse mask used to determine how to
interpret the network-number. A wildcard bit of 0 is a
match and of 1 is “don’t care”.
Create and advertise a default route in an EIGRP
autonomous system with the ip default-network
network-number command.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
45
Summary (cont.)
Use the show ip eigrp neighbors command to
verify that the router recognizes its neighbors. Use the
show ip route eigrp command to verify that the
router recognizes routes from its neighbors.
Use the show ip protocols, show ip eigrp
interfaces, show ip eigrp neighbors, show
ip eigrp topology, and show ip eigrp
traffic commands to verify EIGRP operations.
.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
46
Activity
Create a simple network using EIGRP as your routing
protocol. These steps were discussed at the beginning
of this module.
Verify your connections by running the show
commands discussed in the module:
show ip protocols, show ip eigrp interfaces, show
ip eigrp neighbors, show ip eigrp topology, and
show ip eigrp traffic
Reflection: Are your routes displayed correctly in the
routing table and identified as both directly connected
or EIGRP?
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
47
Self Check
Which show command verifies the router can recognize
its neighbors?
Show ip route eigrp has what function?
What command establishes EIGRP as the routing
protocol?
Identify the command to create and advertise a default
route in an EIGRP autonomous system.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
48
Resources
http://www.cisco.com/en/US/tech/tk365/technologies_te
ch_note09186a008009405c.shtml
http://www.cisco.com/en/US/products/sw/iosswrel/ps18
28/products_command_reference_chapter09186a0080
0ca5a9.html
http://www.cisco.com/en/US/tech/tk365/technologies_te
ch_note09186a0080093f07.shtml
.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
49
Q and A
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
50
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
51
Configuring EIGRP
BSCI Module 2-4 – Configuring EIGRP Authentication
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
52
Objectives
Upon completing this lesson, you will be able to implement
authentication in an EIGRP network. This ability includes
being able to meet these objectives:
Describe router authentication
Describe the MD5 authentication used in EIGRP
Configure MD5 authentication
Troubleshoot MD5 authentication
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
53
Purpose of this Lesson
Coverage of topics new to the “EIGRP” module of BSCI.
What’s new in this module?
EIGRP Message Digest 5 (MD5) authentication and how to
configure and troubleshoot it.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
54
Router Authentication
Many routing protocols support authentication such that
a router authenticates the source of each routing
update packet that it receives.
Simple password authentication is supported by:
IS-IS
OSPF
RIPv2
MD5 authentication is supported by:
OSPF
RIPv2
BGP
EIGRP
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
55
Simple Password vs. MD5 Authentication
Simple password authentication:
Router sends packet and key.
Neighbor checks if received key matches its key.
Not secure.
MD5 authentication
Configure a “key” (password) and key-id; router generates a
message digest, or hash, of the key, key-id and message.
Message digest is sent with packet; key is not sent.
Secure.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
56
EIGRP MD5 Authentication
EIGRP supports MD5 authentication.
Router generates and checks every EIGRP packet.
Router authenticates the source of each routing update
packet that it receives.
Configure a “key” (password) and key-id; each
participating neighbor must have same key configured.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
57
MD5 Authentication
EIGRP MD5 authentication:
Router generates a message digest, or hash, of the key, key-id,
and message.
EIGRP allows keys to be managed using key chains.
Specify key-id (number, key, and lifetime of key).
First valid activated key, in order of key numbers, is used.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
58
Configuring EIGRP MD5 Authentication
(cont.)
Router(config)#
key chain name-of-chain
Enters configuration mode for the key-chain
Router(config-keychain)#
key key-id
Identifies key and enters configuration mode for the keyid
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
59
Configuring EIGRP MD5 Authentication
(cont.)
Router(config-keychain-key)#
key-string text
Identifies key string (password)
Router(config-keychain-key)#
accept-lifetime start-time {infinite | end-time | duration
seconds}
Optional: specifies when key will be accepted for received
packets
Router(config-keychain-key)#
send-lifetime start-time {infinite | end-time | duration
seconds}
Optional: specifies when key can be used for sending
packets
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
60
Configuring EIGRP MD5 Authentication
Router(config-if)#
ip authentication mode eigrp autonomous-system md5
Specifies MD5 authentication for EIGRP packets
Router(config-if)#
ip authentication key-chain eigrp autonomous-system
name-of-chain
Enables authentication of EIGRP packets using key in the
key-chain
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
61
Example MD5 Authentication
Configuration
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
62
R1 Configuration for MD5 Authentication
<output omitted>
key chain R1chain
key 1
key-string firstkey
accept-lifetime 04:00:00 Jan 1 2006 infinite
send-lifetime 04:00:00 Jan 1 2006 04:01:00 Jan 1 2006
key 2
key-string secondkey
accept-lifetime 04:00:00 Jan 1 2006 infinite
send-lifetime 04:00:00 Jan 1 2006 infinite
<output omitted>
interface FastEthernet0/0
ip address 172.16.1.1 255.255.255.0
!
interface Serial0/0/1
bandwidth 64
ip address 192.168.1.101 255.255.255.224
ip authentication mode eigrp 100 md5
ip authentication key-chain eigrp 100 R1chain
!
router eigrp 100
network 172.16.1.0 0.0.0.255
network 192.168.1.0
auto-summary
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
63
R2 Configuration for MD5 Authentication
<output omitted>
key chain R2chain
key 1
key-string firstkey
accept-lifetime 04:00:00 Jan 1 2006 infinite
send-lifetime 04:00:00 Jan 1 2006 infinite
key 2
key-string secondkey
accept-lifetime 04:00:00 Jan 1 2006 infinite
send-lifetime 04:00:00 Jan 1 2006 infinite
<output omitted>
interface FastEthernet0/0
ip address 172.17.2.2 255.255.255.0
!
interface Serial0/0/1
bandwidth 64
ip address 192.168.1.102 255.255.255.224
ip authentication mode eigrp 100 md5
ip authentication key-chain eigrp 100 R2chain
!
router eigrp 100
network 172.17.2.0 0.0.0.255
network 192.168.1.0
auto-summary
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
64
Verifying MD5 Authentication
R1#
*Jan 21 16:23:30.517: %DUAL-5-NBRCHANGE: IP-EIGRP(0) 100: Neighbor
192.168.1.102 (Serial0/0/1) is up: new adjacency
R1#show ip eigrp neighbors
IP-EIGRP neighbors for process 100
H
Address
Interface
Hold
0
192.168.1.102
Se0/0/1
12
Uptime
SRTT
00:03:10 17
RTO Q Seq
2280 0 14
R1#show ip route
<output omitted>
Gateway of last resort is not set
D
172.17.0.0/16 [90/40514560] via 192.168.1.102, 00:02:22, Serial0/0/1
172.16.0.0/16 is variably subnetted, 2 subnets, 2 masks
D
172.16.0.0/16 is a summary, 00:31:31, Null0
C
172.16.1.0/24 is directly connected, FastEthernet0/0
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C
192.168.1.96/27 is directly connected, Serial0/0/1
D
192.168.1.0/24 is a summary, 00:31:31, Null0
R1#ping 172.17.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.17.2.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 12/15/16 ms
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
65
Troubleshooting MD5 Authentication
R1#debug eigrp packets
EIGRP Packets debugging is on
(UPDATE, REQUEST, QUERY, REPLY, HELLO, IPXSAP, PROBE, ACK, STUB, SIAQUERY,
SIAREPLY)
*Jan 21 16:38:51.745: EIGRP: received packet with MD5 authentication, key id = 1
*Jan 21 16:38:51.745: EIGRP: Received HELLO on Serial0/0/1 nbr 192.168.1.102
*Jan 21 16:38:51.745:
AS 100, Flags 0x0, Seq 0/0 idbQ 0/0 iidbQ un/rely 0/0 pe
erQ un/rely 0/0
R2#debug eigrp packets
EIGRP Packets debugging is on
(UPDATE, REQUEST, QUERY, REPLY, HELLO, IPXSAP, PROBE, ACK, STUB, SIAQUERY,
SIAREPLY)
R2#
*Jan 21 16:38:38.321: EIGRP: received packet with MD5 authentication, key id = 2
*Jan 21 16:38:38.321: EIGRP: Received HELLO on Serial0/0/1 nbr 192.168.1.101
*Jan 21 16:38:38.321:
AS 100, Flags 0x0, Seq 0/0 idbQ 0/0 iidbQ un/rely 0/0 pe
erQ un/rely 0/0
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
66
Summary
There are two types of router authentication: simple
password and MD5.
When EIGRP authentication is configured, the router
generates and checks every EIGRP packet and
authenticates the source of each routing update packet
that it receives. EIGRP supports MD5 authentication.
To configure MD5 authentication, use the ip
authentication mode eigrp and ip
authentication key-chain interface commands.
The key chain must also be configured, starting with the
key chain command.
Use debug eigrp packets to verify and
troubleshoot MD5 authentication.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
67
Activity
Using the network created in module 2 using EIGRP as
your routing protocol, follow the steps in this module to
add security to EIGRP.
Be sure to verify your connections by running the show
commands discussed in the module both before and
after you implement security.
show ip protocols, show ip eigrp interfaces, show
ip eigrp neighbors, show ip eigrp topology, and
show ip eigrp traffic
NOTE: before adding any security, you should always
verify your connection first to avoid additional
troubleshooting later.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
68
Self Check
Name the two types of router authentication:
_______________ and __________________
Which two commands are used to configure MD5
authentication, _____________________ and
__________________
What debug command will verify and troubleshoot MD5
authentication?
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
69
Resources
http://www.cisco.com/en/US/tech/tk365/technologies_te
ch_note09186a008009405c.shtml
http://www.cisco.com/en/US/products/sw/iosswrel/ps18
28/products_command_reference_chapter09186a0080
0ca5a9.html
http://www.cisco.com/en/US/tech/tk365/technologies_te
ch_note09186a0080093f07.shtml
.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
70
Q and A
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
71
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
72
Configuring EIGRP
BSCI Module 2-5 – Configuring EIGRP in an Enterprise Network
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
73
Objectives
Upon completing this lesson, you will be able to describe,
recognize, and correct common EIGRP issues and
problems. This ability includes being able to meet these
objectives:
Explain factors affecting scalability in large internetworks
Explain how EIGRP uses queries to update its routing
tables in the event a route is lost and there is no feasible
successor
Explain how to mark the spokes of large network as stubs
to reduce EIGRP queries and thus improve network
scaling
Explain why SIA connections occur
Explain how to minimize active routes
Describe how graceful shut down prevents loss of
packets when routers go down
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
74
Purpose of this Lesson
Coverage of topics new to the “EIGRP” module of BSCI.
What’s new in this module?
Configuring EIGRP in large scale (enterprise) networks
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
75
Factors That Influence EIGRP Scalability
Quantity of routing information exchanged between
peers: without proper route summarization, this can be
excessive.
Number of routers that must be involved when a
topology change occurs.
Depth of topology: the number of hops that information
must travel to reach all routers.
Number of alternate paths through the network.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
76
EIGRP Query Process
Queries are sent when a route is lost and no feasible
successor is available.
The lost route is now in “active” state.
Queries are sent to all neighboring routers on all
interfaces except the interface to the successor.
If the neighbors do not have their lost-route information,
queries are sent to their neighbors.
If a router has an alternate route, it answers the query;
this stops the query from spreading in that branch of
the network.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
77
Updates and Queries in Hub-and-Spoke
Topology
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
78
EIGRP Stub
The EIGRP Stub Routing feature
Improves network stability
Reduces resource utilization and
Simplifies remote router (spoke) configuration
Stub routing is commonly used in hub-and-spoke topology
Stub router sends a special peer information packet to all
neighboring routers to report its status as a stub router
Any neighbor that receives a packet informing it of the
stub status does not query the stub router for any routes
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
79
If A loses its connection
to 10.1.1.0/24, it must
build and transmit five
queries: one query to
each remote, and one
query to B
10.1.1.0/24
Stub Review
A
B
Each of the remote sites
will also build a query
towards B
B receives five queries
which it must process
and answer
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
80
If these spokes are
remotes sites, they
typically have two
connections for
redundancy, not so they
can transit traffic between
A and B
A should never use the
spokes as a path to
anything reachable
through B, so there’s no
reason to learn about, or
query for, routes through
these spokes
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
10.1.1.0/24
Stub Review
A
B
These Are Not
Designed to
Transit Traffic
81
To signal A and B that the paths
through the spokes should not
be used for transit traffic, the
spoke routers can be
configured as stubs
10.1.1.0/24
Stub Review
A
B
router#config t#
router(config)#router eigrp 100
router(config-router)#eigrp stub
router(config-router)#
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
82
Marking the spokes as
stubs allows them to signal
A and B that they are not
transit paths
A will not query stubs,
reducing the total number
of queries in this example
to one
10.1.1.0/24
Stub Review
A
B
Marking the remotes as
stubs also reduces the
complexity of this topology;
B now believes it only has
one path to 10.1.1.0/24,
rather than five
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
83
Configuring EIGRP Stub
Router(config-router)#
eigrp stub [receive-only|connected|static|summary]
receive-only: Prevents the stub from sending any
type of route.
connected: Permits stub to send connected routes
(may still need to redistribute).
static: Permits stub to send static routes (must still
redistribute).
summary: Permits stub to send summary routes.
Default is connected and summary.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
84
Example: EIGRP stub Parameters
If stub connected is
configured:
B will advertise 10.1.2.0/24
to A.
B will not advertise
10.1.2.0/23, 10.1.3.0/23, or
10.1.4.0/24.
If stub summary is
configured:
B will advertise 10.1.2.0/23
to A.
B will not advertise
10.1.2.0/24, 10.1.3.0/24, or
10.1.4.0/24.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
85
Example: EIGRP stub Parameters (Cont.)
If stub static is
configured:
B will advertise 10.1.4.0/24
to A.
B will not advertise
10.1.2.0/24, 10.1.2.0/23, or
10.1.3.0/24.
If stub receive-only
is configured:
B won’t advertise anything to
A, so A needs to have a
static route to the networks
behind B to reach them.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
86
EIGRP Query Process Stuck-in-Active
The router has to get all the replies from the neighbors
with an outstanding query before the router calculates
the successor information.
If any neighbor fails to reply to the query within three minutes,
by default, the route is SIA, and the router resets the neighbor
relationship with the neighbor that fails to reply.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
87
Active Process Enhancement
BSCI 2 - 1
Before
After
Router A resets relationship to
router B when the normal active
timer expires. However, the
problem is the link between router
B and C.
Router A sends an SIA-Query at
half of the normal active timer.
Router B acknowledges the
query there by keeping the
relationship up.
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
88
Graceful Shutdown
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
89
Summary
Factors that affect network scalability include:
.Amount of information exchanged between neighbors
Number of routers
Depth of the topology
Number of alternate paths through the network
When a route is lost and no feasible successor is
available, queries are sent to all neighboring routers on all
interfaces.
The eigrp stub command is used to enable the stub
routing feature, which improves network stability, reduces
resource utilization, and simplifies stub router
configuration.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
90
Summary (Cont.)
Once a route goes active and the query sequence is
initiated, it can only come out of the active state and
transition to passive state when it receives a reply for
every generated query. If the router does not receive a
reply to all the outstanding queries within 3 minutes (the
default time), the route goes to the SIA state.
The active process enhancement feature enables an
EIGRP router to monitor the progression of the search
for a successor route so that neighbor relationships are
not reset unnecessarily.
With graceful shutdown, a goodbye message is
broadcast when an EIGRP routing process is shut
down, to inform adjacent peers about the impending
topology change.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
91
Activity
Using the network created in module 4 using EIGRP as
your routing protocol, follow the steps in this module to
add a stub to EIGRP. Be sure you are running debug
eigrp to watch communication of your links.
You can also verify your connections by running the
show commands discussed in the previous module
once you have added your stub route.
show ip protocols, show ip eigrp interfaces, show
ip eigrp neighbors, show ip eigrp topology, and
show ip eigrp traffic
With debugging still running, shut down your stub
connection and observe the communication on your
debug output.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
92
Self Check
What factors affect the scalability of a network:
What command is used to enable the stub routing
feature?
What is the purpose of enabling EIGRP stub routing?
When routes are lost and no feasible successor can be
found, how does EIGRP reestablish its connection?
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
93
Resources
http://www.cisco.com/en/US/tech/tk365/technologies_te
ch_note09186a008009405c.shtml
http://www.cisco.com/en/US/products/sw/iosswrel/ps18
28/products_command_reference_chapter09186a0080
0ca5a9.html
http://www.cisco.com/en/US/tech/tk365/technologies_te
ch_note09186a0080093f07.shtml
http://www.cisco.com/en/US/products/sw/iosswrel/ps51
87/products_command_reference_chapter09186a0080
17d003.html
.
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
94
Q and A
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
95
BSCI 2 - 1
© 2006 Cisco Systems, Inc. All rights reserved.
Cisco Confidential
96