* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Chapter 12
Piggybacking (Internet access) wikipedia , lookup
Distributed firewall wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Distributed operating system wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Computer network wikipedia , lookup
Network tap wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
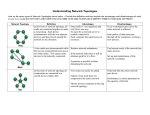
Chapter 12 Communication Controls IS Auditor Role • Collect evidence to ascertain an entities ability to: – – – – Safeguard assets Provide data integrity Efficiency of systems Effectiveness of systems Communication Subsystem Exposures 1) Transmission Impairments a) Attenuation--weakening of a signal b) Delay Distortion--signal transmitted through bounded media c) Noise--random electric signals 2) Component Failure – hardware, software, transmission media 3) Subversive Threats Subversive Threats Active Attack Types Intruders can: • • • • • • • Insert a message Delete a message Modify the contents of a message Alter the order of messages Duplicate messages Deny message services Establish spurious associations Types of Transmission Media Physical Component Controls • Transmission Media – bounded (or guided), unbounded • Communication Lines (public lines vs private lines) • Modems (modulator/demodualtor) Next slide • Port-Protection Devices (mitigate exposures to dial up access) Three Functions of Modem • Increase speed by multiplexing • Perform equalization for line errors and adjust for better line characteristics • Variable speed modem will compensate for various levels of noise • Port-Protection Devices • • • • Force call to only authorized number Voice/ data switching Request password Audit trail of successful/unsuccessful attempts Multiplexors and Concentrators • Both allow the bandwidth or capacity of a communication line to be used more effectively • Multiplexors – frequency-division multiplexing – time-division multiplexing • Concentrators – message switching (entire message waits for clear comm. Path) – packet switching (a message is broken into several small packets) – line switching (circuit switching to find available line) Multiplexing Techniques Line Error Controls (to avoid distortion, noise, and attenuation) • Error Detection – loop checking involves the receiver sending the message back to the sender – parity checking involves adding an extra bit to a string of bits – cyclic redundancy checking involves the block of data to be transmitted is treated as a binary number Line Error Controls • Error Correction – Forward error correcting codes enables line errors to be corrected at the receiving station – Retransmissions of data in error (backward error correction), the sender sends the data again if the receiver indicates the data has been received in error Flow Controls • Stop-and-wait flow control--the sender will not transmit another frame until it receives an acknowledgment from the receiver. • Sliding-window flow control--both sender & receiver hold multiple frames of data to overlap transmission and processing of data. Topological Controls • Local Area Network Topologies – privately owned – provide high-speed communication – confined to limited geographic areas • Types of Topologies – – – – bus topology tree topology ring topology star topology Bus Topology • Nodes in the network are connected in parallel to a single communication line • Types of bus – broadband bus (uses analog signaling) – baseband bus (uses digital signaling) Bus Network Topology Tree Topology • Nodes in the network are connected to a branching communication line that has no closed loops • Use analog signaling to broadcast messages in the direction of the root of the tree. Tree Topology Ring Topology • Nodes in the network are connected via repeaters to a communication line that is configured as a closed loop • Often data is transmitted only in one direction on the ring • Point-to-point topology--each node is connected directly to another node Ring Network Topology Star Topology • Nodes in the network are connected in a point-to-point configuration to a central hub • Hub can route messages from one node to another or a subset of nodes Star Network Topology Wide Area Network Topologies • Characteristics: – Often encompass components that are owned by other parties – Provide relatively low-speed communication among nodes – Span large geographic area • Conceptually every node in the network can have a point-to-point connection with every other node Mesh Network Topology Channel Access Controls • Polling Methods – Centralized polling (one node keep polling) – Distributed polling (token passing) • Contention Methods – Carrier sense multiple access with collision detection (CSMA/CD) – each node compete with other nodes but differences will be resolved Centralized Polling Models Distributed Polling Model Link Encryption • Protects data traversing a communication channel connecting two nodes in a network • Cryptographic key might be common to all nodes in the network • Reduces expected losses from traffic analysis Link Encryption End-to-End Encryption • Protects the integrity of data passing between a send and a receiver, independently of the nodes of the data traverses • The sender encrypts data before it is given to the network for transmission to the receiver Other Subversive Threat Controls See Table 12-2 • Stream Ciphers • Error Propagation Codes • Message Authentication Codes • Message Sequence Numbers • Request-Response Mechanisms Controls over Subversive Threats Internetworking Controls • Internetworking is the process of connecting two or more communication networks together to allow the users of one network to communicate with the users of other networks. • Three types of devices are used – Bridge (e.g. Bus), Router (e.g., Bus and Ring), Gateway (e.g., Bus, Ring, MS NT, Novel) Communication Architectures & Controls • Open-systems interconnection (OSI) • IBM’s system network architecture (SNA) • Transmission control protocol/internet protocol (TCP/IP) Transmission of Data with OSI Accounting Audit Trail • Must allow a message to be traced through each node in a network • Examples – unique identifier of the source node – unique identifier of the person authorizing dispatch of the message – time and date of dispatch Operations Audit Trail • The performance and the integrity of the network depend on the availability of comprehensive operations audit trail data. • Examples: – number of messages that have traversed each link – number of messages that have traversed each node – Queue lengths at each node