* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Document
IEEE 802.1aq wikipedia , lookup
Computer security wikipedia , lookup
Power over Ethernet wikipedia , lookup
Distributed firewall wikipedia , lookup
Deep packet inspection wikipedia , lookup
Wireless security wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Wake-on-LAN wikipedia , lookup
IEEE 802.11 wikipedia , lookup
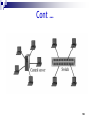
Internet protocol suite wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Network tap wikipedia , lookup
Computer network wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Airborne Networking wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
CIT 742: Network Administration and Security Mohammed A. Saleh http://ifm.ac.tz/staff/msaleh/CIT742.html 1 Important Information Lecturer name: Mr. Mohammed A. S. Find out about my contact details from my personal website http://ifm.ac.tz/staff/msaleh For any questions regarding the course, you can write me an email at any time. Will try to be prompt for response. If you need to see me in my office please book an appointment by writing me an email [email protected] All notes will be uploaded on the CIT 742 web page, http://ifm.ac.tz/staff/msaleh/CIT742.html A hardcopy will be submitted to the class representative 2 Basic Rules Try to attend ALL lectures Sign against your name on the register Try not to be late, if you have to be late, come in quietly. If you miss a class find out what was covered Material covered in lectures is examinable The course notes are not meant to be exhaustive, read the recommended books; Read critically, point out any errors in the lecture notes. 3 Required Readings Author Year Title Publisher Hermachandran L. 2003 Computer Communications Network Charulatha Tanenbaum A. S. 2005 Computer Networks Prentice-Hall Galo M. A. 2002 Computer Communications and Networking Technologies Pacific Grove Rowe S and Schuch 2005 Computer Networking Pearson 4 Recommended Readings Author Year Title Publisher Kurose J. F 2001 Computer Networking a top down approach Pearson Halsall 2005 Computer Networking and Internet McGraw-Hill Madhulika J. 2002 Computer Networks BPB 5 Method of Assessment Student will be assessed through CA (coursework) Two compulsory tests – Dates will be announced soon! Tutorials and Assignments – Must attend tutorials! Final examinations Coursework carries 40% Final Exams carries 60% 6 Introduction High computer sales are accounted for by both private and business markets. Where a business has more than one computer, they are in practice always connected together in a local area network These networks mat be advanced therefore are more or less costly Question: Why should so much money (and time) be spent in designing local area networks? Question: What can you do with a freestanding PC? 7 Terminologies Local Area Network (LAN) 1. 2. 3. 4. 5. Set of physically interconnected computers and computer equipment within a limited area A LAN may be connected to other LANs Components that make up the LAN Workstations Servers Cabling Interconnected components (switches and hubs) Other resources – printers and cd roms 8 Cont … 9 LANs, Ethernet and Internet Development of LANs were accelerated by the development of the Internet and Ethernet Ethernet developed further into newer versions, Fast Ethernet and the Gigabit Ethernet Question: So where did the Internet originate from? Originated in the American Department of Defense They developed the ARPA project (Advanced Research Project Agency) ARPAnet, and was the first-ever Internet It had interconnected networks that used the TCP/IP protocol, which is still used in today’s Internet 10 Classification of LANs Local Area Networks A network that is restricted to a single geographical location. Encompasses a relatively small area such as an office building or school The function of the LAN is to interconnect workstation computers for the purposes of sharing files and resources. It is typically high speed and cheaper to set up than a WAN 11 Cont … 12 Cont … Major Characteristics of LANs Every computer has the potential to communicate with any other computers of the network High degree of interconnection between computers Easy physical connection of computers in a network Inexpensive medium of data transmission High data transmission rate Advantages The reliability of network is high because the failure of one computer in the network does not effect the functioning for other computers. 13 Cont … Addition of new computer to network is easy. High rate of data transmission is possible. Peripheral devices like magnetic disk and printer can be shared by other computers. Disadvantages If the communication line fails, the entire network system breaks down. 14 Cont … Use of LAN Followings are the major areas where LAN is normally used: 1. File transfers and Access 2. Word and text processing 3. Electronic message handling 4. Remote database access 5. Personal computing 6. Digital voice transmission and storage 15 Cont … Wide Area Networks (WANs) It is used to describe a computer network spanning a regional, national or global area. For example, for a large company the head quarters might be at Dar Es Salaam and regional branches at Dodoma, Arusha, Mwanza and Morogoro They are built so that users from one location can communicate with users from another location WANs are slower than LANs Often require additional and costly hardware Routers Dedicated leased line Complicated implementation procedures 16 Example of WAN Wide Area Network 17 Cont … 1. Major characteristics of WAN Communication Facility 2. Remote Data Entry 3. Video conferencing Updating data remotely Centralised Information: Centralised data storage 18 Difference between LAN and WAN 1. 2. 3. Coverage: LAN is restricted to limited geographical area of few kilometers. But WAN covers great distance and operate nationwide or even worldwide. Connectivity: In LAN, the computer terminals and peripheral devices are connected with wires and coaxial cables. In WAN there is no physical connection. Communication is done through telephone lines and satellite links. Cost: Cost of data transmission in LAN is less because the transmission medium is owned by a single organisation. In case of WAN the cost of data transmission is very high because the transmission medium used are hired, either telephone lines or satellite links. 19 Cont … 4. 5. Speed: The speed of data transmission is much higher in LAN than in WAN. The transmission speed in LAN varies from 0.1 to 100 megabits per second. In case of WAN the speed ranges from 1800 to 9600 bits per second (bps). Transmission Errors: Few data transmission errors occur in LAN compared to WAN. It is because in LAN the distance covered is negligible. 20 Cont … Metropolitan Area Networks (MANs) A network that usually spans across the city or a large campus Interconnects several local area networks It uses a high-speed cable for the interconnections between different LANs It might be owned or operated by a single organization Its geographical scope falls between a WAN and a LAN MANs provides internet connectivity for LANs in the same metropolitan area 21 Cont … 22 Life Cycle of LANs Why would an organization decide to have a LAN? Always have a Business Case Reason to spend money Without a BC a LAN may be purchased for the wrong reasons 23 Cont … 24 Cont … 1. Analysis Finding out what the problem is (preliminary study) and defining it in a specification of requirements what should be evaluated are different network operating systems, mail systems, and other applications choice of hardware components should also be evaluated. The phase is generally aimed at establishing what the system should do, not how it should do it. Other requirements should include response times, functionality, security, training, hardware, and life expectancy. 25 Cont … 2. Design Determine how the requirements of the specification are to be met Breaking down complex projects into more manageable subprojects. An extremely important aspect of the documentation of the network It must include all the drawings showing the location of hardware and cables An overview of the software to be installed on all the machines must also be prepared here. 26 Cont … 3. Implementation This phase involves the physical installation of the local area network Cables are run, software is installed, and computers and other hardware are put in place Other important aspects of this phase are user training and starting new routines Changes may be major hence making it a long process 27 Cont … 4. Integration and System Testing The system must be tested This is a major and comprehensive task Testing must be given high priority to enhance security To ensure that the network meets the requirements set out in the specification To ensure that the network is stable Level of data authorization To tight up security penetration is absolutely necessary 28 Cont … 5. Operation and Maintenance Faults may emerge Serious consequences if there is unauthorized access Always focus on balancing security and functionality 29 OSI Reference Model OSI stands for Open Systems Interconnection, and is a model for data communication It was created by IS0 -the International Standardization Organization, and defines seven layers 30 Cont … •Application •Presentation •Session •Transport •Network •Data Link •Physical •All •Away •People •Pizza •Seem •Sausage •To •Throw •Need •Not •Data •Do •Processing •Please Easy way to remember the 7 layers of the OSI model 31 Cheat Sheet 32 Cont … The different layers of this model have different communication tasks The OSI model is a description of how communication takes place 33 Layers 1. Physical Layer It carries the signals between the parties through a medium conducting media such as pairs of wires, coaxial cable, optical fiber, or radiating media such as radio or satellite links Depending on the medium the signals can be electrical signals, light signals or radio waves The task on this layer is therefore to carry bits on the chosen medium. It also defines other physical characteristics of the network i.e. identifies which physical topology is to be used. 34 Cont … 2. Data Link Layer It administers the use of the physical layer, in terms of channel access. It gathers the bits into blocks of frames, this is the protocol data unit at layer 2 It offers flow control and applies error control and corrections It is also responsible for hardware addressing of frames It is subdivided into two main sub-layers: MAC layer: The MAC address is defined at this layer. The MAC address is the physical or hardware address burned into each NIC. LLC layer The LLC layer is responsible for the error and flowcontrol mechanisms of the data-link layer 35 Cont … 3. Network Layer With the two previous layers, these problems have been solved Conveying signals between the sender and receiver Flow control Freedom of errors We start interconnecting devices to form a network and interconnect network to other networks, more problems arise Imagine you are connecting to a web server, which is far away, there is no direct line from your PC to the server 36 Cont … 37 Cont … The network layer is responsible for carrying data through a network Two things are needed: Every device connected to the network must have a network address The routers that connect the network together must have tables that link the physical lines with possible addresses. It uses network addresses and internal tables to decide the route that the data should take through the network to reach the address of the receiver this is known as routing The data on this level is referred to as packets or datagrams 38 Cont … 4. Chosen routes may either be dedicated routes or not. A dedicated route is known as connection-oriented network, while a route that is not set up is referred to as connectionless network. Transport Layer Known as end-to-end protocol establishes a connection between the endpoints Flow control and error control mechanisms are also performed in layer 4 Error control for the arriving packets It is also responsible for sequence control, making sure that packets are delivered in the correct sequence 39 Cont … 5. 6. Session Layer This layer is used to establish, monitor, and terminate sessions between the end points. The most important task here is the ability to synchronize the communicating parties. It does this by establishing, maintaining, and breaking sessions. Presentation Layer This layer ensures that the data is displayed correctly on the equipment to which it is sent. Functions such as character conversion, display control, encryption, compression, and so on are performed here. 40 Cont … Some common data formats handled presentation layer include the following: by the Graphics files JPEG, TIFF, GIF. Text and data: translate data into different formats such as American Standard Code for Information Interchange (ASCII) and the Extended Binary Coded Decimal Interchange Code (EBCDIC). Sound/video MPEGs, QuickTime video, and MIDI files 41 Cont … 7. Application Layer The function of the application layer is to take requests and data from the users and pass them to the lower layers of the OSI model Incoming information is passed to the application layer, which then displays the information to the users The most common misconception about the application layer is that it represents applications that are used on a system such as a Web browser, word processor, or a spread sheet It defines the processes that enable applications to use network services, like web, email, file transfer, terminal emulation programs 42 TCP/IP Model When the ARPAnet was invented, it resulted to the following: Protocols used on the internet are known as the TCP/IP suite The IP protocol became the standard for the network the network came to be known as the Internet Includes all standards. protocols that are recommended network The layering changed to have only four layers, now referred to as the TCP/IP model. Simpler than the OSI model 43 TCP/IP Model 44 TCP/IP Protocol Suite 45 PDUs and Encapsulation Every layer also has a protocol (a set of rules)for the exchange of data units. 46 Cont … Note that the rules operate horizontally, between peer layers, while the data is sent vertically between the layers until it reaches the transport medium An application protocol defines a set of possible protocol data units in order to send data or commands between a client and a server The protocol of the application now specifies in detail what this PDU must look like. 47 Cont … On transmission from client to server, this A-PDU is handed down to the layer below -in this case TCP 48 Cont … Note that the application has put a header on the PDU The TCP layer now regards the A-PDU as data to be transported This header says something about the nature of the content of the PDU, which the receiving side needs to know for correct processing. The transport layer adds its own header to manage the transport service The same procedure is repeated with the network layer, where the T-PDU is encapsulated in a network IP datagram, or N-PDU. The IP datagram (the N-PDU) is encapsulated in an Ethernet frame (LPDU),and the network card sends this frame out on to the medium. 49 Cont … At the receiving computer, the reverse process takes place: every layer recovers its PDU by unpacking the data field from underlying layer 50 Exercises 1. 2. 3. List the five phases of the waterfall model. Relate each of the phases to the installation of a local area network. Outline the main advantages –and disadvantages-of installing a local area network in an organization. 51 Topologies It referrers to the design of LANs The way LANS are physically set up. Common topologies are bus, star and ring 1. Bus topology Nodes are connected via a long cable. All the nodes are connected to the same cable, at different positions. 52 Cont … An example of this design is a telephone network. Problems: Capacity problem the fact that several different units are sharing a common medium(the telephone cable)leads to conflicts between the units Since only one unit at a time can use the cable, capacity could become a problem It is defined as collisions The access method used is CSMA/CD Security problems All the nodes that are connected to a bus will be able to hear all communication that is being carried on the cable Access to the cable gives access to all the information being carried on this part of the network. 53 Cont … The bus topology is a typical example of a shared network. Therefore an Ethernet network is a classical example of a shared network. How can a message reach the appropriate receiver in a network with several stations, when every node is able to read the message? 54 Cont … 2. Ring Topology Commonly used method in local area networks. Technology used is Token Ring 55 Cont … Data will be sent from one station to another in a welldefined order It will need to go through several other "neighbours" to reach its destination. Any node that needs to transmit will have a ‘token’, which circulates on the ring The ring topology does not look like a ring, but the design is just logical A hub will normally take care of the connection, Such a special hub is called a Multistation Access Unit (MAU) 56 Cont … 57 Cont … 3. Star Topology Communicate in full through a central node in the network. Modern network connect nodes to a switch The switch becomes the central unit managing traffic between the other connected units A switch only sends data to the port for which it is designated Modem network cabling is in practice only carried out with structured cabling everything is put in a star structure 58 Cont … 59 Access Methods Different topologies can be used for LANs Some of these assume that several users will be using the same medium Common access methods are: Carrier Sense (CSMA/CD) Token passing Multiple Access with Collision Detection 60 Contest CSMA/CD A distributed principle which is used in Ethernet – bus/ tree topology It stands for Carrier Sense Multiple Access/Collision Detection “Carrier Sense” Means that a device that wishes to send on the medium senses whether there are other devices sending a carrier at the same time If the medium is in use, the station does not send, but waits until the medium is free When the medium becomes free it will start its frame on the medium 61 62 Cont … “Collisions Detect” In the event of a collision the parties stop sending and try again after a random wait In this way, many users can use the same medium (Multiple Access). 63 Token Passing The principle of token passing can be used on both ring and bus networks It uses the principle of a token to transmit frames across the network Tokens circulate between the participants if the network is a ring If the network is a bus, the tokens "circulate” in a particular sequence Think of the baton in a relay race Only the one who "is holding” the token at a given instant can use the medium This ensures that only one recipient uses the medium at a time. 64 Cont … Principle advantages over CSMA/CD CSMA/CD decreases in efficiency whenever there is a high load on the network, whereas token passing is always efficient (the medium can be exploited fully) The efficiency of CSMA/CD declines sharply when there are many collisions and the frames have to be re-sent Token passing offers the ability to prioritize traffic It can also guarantee a maximum waiting time before a station can send 65 LAN Standards The Institute of Electrical and Electronic Engineers (IEEE) developed a series of networking standards. to ensure that networking technologies developed by respective manufacturers are compatible. cabling, networking devices, and protocols are all interchangeable when designed under the banner of a specific IEEE standard. Each of these IEEE specifications outlines specific characteristics for LAN networking including: Speed Topology Cabling and Access method 66 67 802.2 IEEE Standard Referred to as the Logical Link Control (LLC) Manages data flow control and error control for the other IEEE LAN standards. Data flow control regulates how much data can be transmitted in a certain amount of time Error control refers to the recognition and notification of damaged data. 68 802.3 IEEE Standard Defines the characteristics for Ethernet networks. Ethernet networking is by far the most widely implemented form of local area networking . Since the development of the original 802.3 standards, there have also been several additions that have been assigned new designators. These standards are often referred to as the 802.3x standards Some of the newer standards include: 802.3u for Fast Ethernet 802.3z for Gigabit Ethernet 802.3ae for 10-Gigabit Ethernet 69 Features of IEEE 802.3 Speed The original IEEE 802.3 standard specified a network transfer rate of 10Mbps Modifications to the standard led to: Fast Ethernet (802.3u), which can transmit network data up to 100Mbps and higher. Gigabit Ethernet (802.3z), which can transmit at speeds up to 1000Mbps. 802.3ae is a very fast 803.3 standard. Known as 10-Gigabit Ethernet, it offers speeds 10 times that of Gigabit Ethernet. Topology The original Ethernet networks used a bus or star topology IEEE 802.3u and 802.3z use the star topology. 70 Cont … Media Refers to the physical cabling used to transmit the signal around the network The original 802.3 specifications identified coaxial and twisted pair cabling to be used The more modern standards specify twisted pair and fiber-optic cable 802.3ae currently only supports fiber media. Access method The access method refers to the way that the network media is accessed Ethernet networks use a system called Carrier Sense Multiple Access with Collision Detection (CSMA/CD). 71 802.5 IEEE Standard This standard specifies the characteristics for Token Ring networks. Developed by IBM in the mid 80’s replaced by the Ethernet networks. It is unlikely that you will encounter a ring network in your travels and even more unlikely that you will be implementing a ring network as a new installation. 72 Features of IEEE 802.5 Speed Topology Token Ring networks use a logical ring topology and most often a physical star Media The 802.5 Token Ring specifies network speeds of 4 and 16Mbps. Token Ring networks use unshielded twisted pair cabling or shielded twisted pair. Access Method specifies an access method known as token passing On a Token Ring network, only one computer at a time can transmit data 73 Fiber Distributed Data Interface The American National Standards Institute (ANSI) developed the Fiber Distributed Data Interface (FDDI) standard It was developed to meet the growing need for a reliable and fast networking system to accommodate distributed applications. FDDI uses a ring network design unlike the traditional 802.5 standard, FDDI uses a dual ring technology for fault tolerance Because of the dual ring design, FDDI is not susceptible to a single cable failure like the regular 802.5 IEEE standard 74 Features of IEEE FDDI Speed Topology FDDI uses a dual ring topology for fault-tolerant reasons. Media FDDI transmits data at 100Mbps and higher. FDDI uses fiber-optic cable that enables data transmissions that exceed two kilometer Access Method Similar to 802.5, FDDI uses a token-passing access method. 75 IEEE 802.11 Standard Specify the characteristics of wireless LAN Ethernet networks There are four common wireless standards: 802.11, 802.11a, 802.11b and 802.11g Each of these wireless standards characteristics identifies several Features of 802.11 Speed Media measured in Mbps and vary between network standards. use radio frequency (RF) as a transmission media Topology wireless standards can be implemented in an ad-hoc or 76 infrastructure topology IEEE 802.11 Standard Access Methods Uses Carrier Sense Multiple Access/Collision Avoidance (CSMA/CA). Variation on the CSMA/CD access method CSMA/CA access method uses a "listen before talking" strategy Any system wanting to transmit data must first verify that the channel is clear before transmitting, thereby avoiding potential collisions. Range Wireless standards each specify a transmission range It is influenced by many factors such as obstacles or weather. 77 Cont … IEEE 802.11offered 1 or 2Mbps transmission speeds 802.11a specified speeds of up to 54Mbps IEEE 802.11b The 802.11b standard provides for a maximum transmission speed of 11Mbps 78 Questions