* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Document
SIP extensions for the IP Multimedia Subsystem wikipedia , lookup
Point-to-Point Protocol over Ethernet wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Distributed firewall wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Network tap wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
TCP congestion control wikipedia , lookup
Airborne Networking wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
Dynamic Host Configuration Protocol wikipedia , lookup
Computer network wikipedia , lookup
Deep packet inspection wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Routing in delay-tolerant networking wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Internet protocol suite wikipedia , lookup
UniPro protocol stack wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
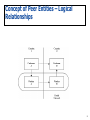
TCOM 509: TCP/IP - Internet Protocols Instructor: Scott T. Tran * Obtained permission to use Raj Jain’s technical material Course Objectives Understand concept of datagram processing and delivery (layering and encapsulation) Understand the client-server model as applied to networking Understand IP Addressing and Subnet Masking Schemes (CIDR/VLSM) Understand IP routing (RIP, OSPF, IS-IS) Understand service (e.g., application) addressing and access to services across an IP network Understand TCP performance parameters and metrics Advanced topics (IP Multicast, IP Tunneling, NAT, DHCP, IP Security, etc…) 2 On-Line Course Info Look week at the website at least once per http://osf1.gmu.edu/~stran4 3 IP Header 4 UDP Header 5 TCP Header 6 Communications Between LAN Hosts (TCP/IP) Via Wide Area Networks (IP) 7 Chapter 1: Introduction Concept of Peer Entities – Logical Relationships 9 Protocols A protocol is a set of rules and formats that govern the communication between communicating peers set of valid messages meaning of each message A protocol is necessary for any function that requires cooperation between peers 10 What does a protocol tell us? Syntax of a message what fields does it contain? in what format? Semantics of a message what does a message mean? for example, not-OK message means receiver got a corrupted file Actions to take on receipt of a message for example, on receiving not-OK message, retransmit the entire file 11 The Internet Standards-based – the TCP/IP protocol suite An Open System – not linked to a single vendor US Gov’t research resulted in quite and extensible set of protocols Best spent tax money I know of Evolution from gov’t-orientation to researchorientation to business-orientation Why is it so good? Why did it beat out “OSI Networking”? Let’s start in on the details… 12 Getting Data from Here to There IP is a form of packet switching Data is broken up into discrete chucks and then sent toward destination Each packet has to find its own route to the destination. There is no predetermined path; the decision as to which node to hop to in the next step is taken only when a node is reached. Each packet finds its way using the information it carries, such as the source and destination IP addresses. Network resources (routers, links) are shared between different data streams - multiplexing The phone network: circuit switching Sender calls receiver and establishes a logical connection The connection is maintained for the duration of the data flow Two distinct paradigms Both have value The TCP part of TCP/IP provides a logical connection, when necessary 13 Motivation behind OSI Model Is a conceptual, reference model. Is the primary architectural model for inter-computer communications. Is the only common language spoken by different manufacturers. Mastery of the OSI model is mandatory 14 Motivation behind OSI Model The goal of an OSI layer is to communicate with its peer layer on another host. 7 6 5 4 3 2 1 Application Presentation Session Transport Network Data Link Physical 7 6 5 4 3 2 1 Application Presentation Session Transport Network Data Link Physical The information exchanged is called a Protocol Data Unit (PDU). 7 6 5 4 3 2 1 Application Presentation Session Transport Network Data Link Physical Messages Messages Messages Segments Packets or Datagrams Frames Bits 15 Communication between OSI Layers 7 6 5 4 3 2 1 Application Presentation Session Transport Network Data Link Physical 7 6 5 4 3 2 1 Application Presentation Session Transport Network Data Link Physical 16 Motivation behind OSI Model – Protocol Functionality Fragmentation and Reassembly Breaking up data into pre-defined sized blocks Encapsulation Adding control info to data (address, error detection code, etc…) Connection Control Providing connection establishment, data transfer, connection termination Flow Control Throttling of data rate exchanged between source and destination Error Control Error detection Synchronization Timeouts, Send state, Receive state. Etc… Sequencing Numbering of data blocks (applicable only for connection-oriented mode) Addressing Has local and global significance, Used for routing purposes in IP Multiplexing Allowing multiple logical connections to use one physical connections Mapping of connections from one protocol layer to another Transmission Services Security, Priority, Grade of Service 17 The OSI Reference Model 18 Why seven layers? Need a top and a bottom -- 2 Need to hide physical link, so need datalink -- 3 Need both end-to-end and hop-by-hop actions; so need at least the transport (TCP) and network (IP) layers -- 5 Session and presentation layers are not so important, and are often ignored So, we need at least 5, and 7 seems to be excessive Note that we can place functions in different layers 19 Physical layer Moves bits between physically connected endsystems Standard prescribes Postal network coding scheme to represent a bit shapes and sizes of connectors bit-level synchronization Supported transmission: electric voltages, radio frequencies, pulses of infrared or ordinary light technology for moving letters from one point to another (trains, planes, vans, bicycles, ships…) Internet technology to move bits on a wire, wireless link, satellite channel etc. 20 Datalink layer Introduces the notion of a frame Idle markers tell us that a link is not carrying a frame Begin and end markers delimit a frame On a broadcast link (such as Ethernet) set of bits that belong together end-system must receive only bits meant for it need datalink-layer address also need to decide who gets to speak next these functions are provided by Medium Access sublayer (MAC) Some data links also retransmit corrupted packets and pace the rate at which frames are placed on a link part of logical link control sublayer layered over MAC sublayer 21 Datalink layer (contd.) Datalink layer protocols are the first layer of software Very dependent on underlying physical link properties Usually bundle both physical and datalink layer on host adaptor card Postal service example: Ethernet mail bag ‘frames’ letters Internet a variety of datalink layer protocols most common is Ethernet others are FDDI, SONET, HDLC 22 Network layer Logically concatenates a set of links to form the abstraction of an end-to-end link Allows an end-system to communicate with any other end-system by computing a route between them Hides idiosyncrasies of datalink layer Provides unique network-wide addresses Found both in end-systems and in intermediate systems At end-systems primarily hide details of datalink layer segmentation and reassembly error detection 23 Network layer (contd.) At intermediate systems participates in routing protocol to create routing tables responsible for forwarding packets scheduling the transmission order of packets choosing which packets to drop 24 Two types of network layers In datagram (connection-less) networks provides both routing and data forwarding Ex: Internet using IP protocol In connection-oriented networks we distinguish between data plane and control plane data plane only forwards and schedules data (touches every byte) control plane responsible for routing, call-establishment, callteardown (doesn’t touch data bytes) Ex: TCP protocol running over IP 25 Network layer Postal network set up internal routing tables forward letters from source to destination static routing multiple qualities of service Internet network layer is provided by Internet Protocol found in all end-systems and intermediate systems segmentation and reassembly packet-forwarding, routing, scheduling unique IP addresses can be layered over anything, but only best-effort service 26 Transport layer - TCP Network provides a ‘raw’ end-to-end service Transport layer creates the abstraction of an error-controlled, flow-controlled and multiplexed end-to-end link Error control message will reach destination despite packet loss, corruption and duplication retransmit lost packets; detect, discard, and retransmit corrupted packets; detect and discard duplicated packets Flow control match transmission rat to rate currently sustainable on the path to destination, and at the destination itself 27 Transport Layer - TCP 28 Transport Layer (TCP) – Relationships with Other Layers Below Process-to-process delivery 29 Transport Layer Addressing Addresses •Data link layer MAC address •Network layer IP address •Transport layer Port number (choose among multiple processes running on destination host) 30 Transport layer (contd.) Multiplexes multiple applications to the same end-to-end connection adds an application-specific identifier (port number) so that receiving end-system can hand in incoming packet to the correct application Some transport layers provide fewer services e.g. simple error detection, no flow control, and no retransmission lightweight transport layer 31 Transport layer (contd.) Postal system doesn’t have a transport layer implemented, if at all, by customers detect lost letters (how?) and retransmit them Internet two popular protocols are TCP and UDP TCP provides error control, flow control, multiplexing UDP provides only multiplexing 32 Session layer Not common Provides full-duplex service, expedited data delivery, and session synchronization Duplex Expedited data delivery if transport layer is simplex, concatenates two transport endpoints together allows some messages to skip ahead in end-system queues, by using a separate low-delay transport layer endpoint Synchronization allows users to place marks in data stream and to roll back to a pre-specified mark 33 Example Postal network suppose a company has separate shipping and receiving clerks chief clerk can manage both to provide abstraction of a duplex service chief clerk may also send some messages using a courier (expedited service) chief clerk can arrange to have a set of messages either delivered all at once, or not at all Internet doesn’t have a standard session layer 34 Presentation layer Unlike other layers which deal with headers, presentation layer touches the application data Hides data representation differences between applications Can also encrypt data Usually ad hoc Postal network e.g. endian-ness translator translates contents before giving it to chief clerk Internet no standard presentation layer only defines network byte order for 2- and 4-byte integers 35 Application layer The set of applications that use the network Doesn’t provide services to any other layer Postal network the person who uses the postal system suppose manager wants to send a set of recall letters translator translates letters going abroad chief clerk sends some priority mail, and some by regular mail mail clerk sends a message, retransmits if not acked postal system computes a route and forwards the letters datalink layer: letters carried by planes, trains, automobiles physical layer: the letter itself 36 OSI Reference Model vs. TCP/IP Protocol Stack OSI TCP / IP Application (Layer7) Presentation (Layer6) Application Session (Layer 5) Transport (Layer 4) Transport Network (Layer 3) Internet Data Link (Layer 2) Physical (Layer 1) Subnet 37 Layering and Encapsulation 38 Why Layering Required For Networking? A system that is too complex to comprehend in its entirety. A system that is difficult to maintain. A system whose least stable elements are not isolated. A system whose most reusable elements are difficult to identify. A system that is to be built by different teams, possibly with different skills. 39 Why Need Encapsulation? Preserve content of layers which is private but allow interfacing between them Allows management of complexity and change within layers 40 41 42 What is a Router? A specialized computer Interconnects multiple physical networks Allows construction of a LOGICAL network topology that is independent from the PHYSICAL networks Notation Show-and-tell 43 How does a router's forwarding logic differ from a bridge's forwarding logic? 1. Packet Filtering: A router examines only those data packets specifically addressed to it, as opposed to a bridge, which reads the destination address of every data packet on the LAN to which it is attached. 2. Route Determination: A bridge checks the frame's data-link protocol for source as well as destination address. It then checks its table of known local nodes. The destination address is compared with the contents of the known local nodes in order to determine whether the frame should be allowed to cross the bridge or not whether the destination is local or not). The bridge does not determine the path; it merely allows or disallows the packet to cross. Destination routes must be obtained through other network devices, such as the originating workstation for source routing bridges. Bridges are thus sometimes known as "forward if not local" devices. Routers actually maintain dynamic tables of "best routes", which depend on network conditions. Based the latest traffic conditions, the router chooses the best path for the data packet to reach its destination, and sends the data packet on its way. After reading the network layer destination address and the protocol of the network layer data, the router consults its routing tables in order to determine the best path on which to forward this data packet. Having found the best path, the router has the ability to repackage the data packet as required for the chosen delivery route. For example, if the packet were to be sent out over an X.25 packetswitched network, the router would encapsulate the packet in an X.25-compliant envelope. 3. Routing Logic: A bridge reads the destination address of each data frame on a LAN, decides whether the address is local or remote (on the other side of the bridge), and only allows those data frames with non-local destination addresses to cross the bridge. A router is more discriminating. The router first confirms the existence of the destination address as well as the latest information on available network paths to reach that destination. Unlike a bridge, which merely allows access to the internetwork (forward-if-not-local logic), a router specifically addresses the data packet to a distant router. However, before a router actually releases a data packet on to the internetwork, is confirms the existence of the destination address to which the data packet is bound. Only once the router is satisfies with the viability of the destination address as well as with the quality of the intended path, will it release the packaged packet. The router's meticulous processing is known as "forward if proven remote" logic. 44 TCP/IP Protocol Suite Layers 45 TCP/IP Layering 46 Multiplexing and Demultiplexing 47 The Client-Server Model Two hosts interact in a predefined manner One side is the client – it wants information One side is the server – it provides the information EX: WWW – web browser is the client, website is the server A host is not “locked down” to be only a client or only a server Multiple client and server programs can be running on a single host at the same time 48 Client/Server on the same LAN 49 Client/Server on two different LANs 50 Service Addresses: Port Numbering Port numbers are “Layer 4” addresses (TCP or UDP in the TCP/IP suite) They allow multiple services on a single host to have unique addresses E.g., one host can be running servers for FTP, HTTP, and telnet Each service listens on it’s own port The combination of IP address plus TCP/UDP can uniquely identify a connection (a “socket”) 51 How Do You Get a Port Number? Standards and Standards Processes The Internet Engineering Task Force (IETF) most directly controls the development of standards for the TCP/IP protocol suite Those standards are called Requests for Comment (RFCs) Relatively collegial process Different from IEEE, ITU, ANSI, etc. http://www.ietf.org http://www.rfc-editor.org See section 1.11, pp. 14-15 Some of these RFCs have been updated 52 IP Protocol and Its Associated Upper Layer: IP Protocol Numbers http://www.iana.org/assignments/protocol-numbers unix-host% more /etc/protocols # # Internet protocols # # $FreeBSD: src/etc/protocols,v 1.13.2.1 2000/09/24 11:26:39 asmodai Exp $ # from: @(#)protocols 5.1 (Berkeley) 4/17/89 # # See also http://www.isi.edu/in-notes/iana/assignments/protocol-numbers # ip 0 IP # internet protocol, pseudo protocol number #hopopt 0 HOPOPT # hop-by-hop options for ipv6 icmp 1 ICMP # internet control message protocol igmp 2 IGMP # internet group management protocol ggp 3 GGP # gateway-gateway protocol ipencap 4 IP-ENCAP # IP encapsulated in IP (officially ``IP'') st2 5 ST2 # ST2 datagram mode (RFC 1819) tcp 6 TCP # transmission control protocol cbt 7 CBT # CBT, Tony Ballardie <[email protected]> egp 8 EGP # exterior gateway protocol igp 9 IGP # any private interior gateway (Cisco: for IGRP) <snip> udp 17 UDP # user datagram protocol ipv6 41 IPV6 # ipv6 sdrp 42 SDRP # Source Demand Routing Protocol ipv6-route 43 IPV6-ROUTE # routing header for ipv6 ipv6-frag 44 IPV6-FRAG # fragment header for ipv6 idrp 45 IDRP # Inter-Domain Routing Protocol rsvp 46 RSVP # Resource ReSerVation Protocol gre 47 GRE # Generic Routing Encapsulation <etc.> 53 Chapter 2: Link Layer Ethernet Encapsulations – 2 Types 55 Loopback Interfaces Special logical IP address (127.0.0.1) Any IP traffic sent to loopback interface must not appear on any network Used to allow a client and a server on the same host to communicate with each other using TCP/IP 56 Maximum Transmission Unit (MTU) 57 Chapter 3: IP: Internet Protocol IP Header 59 60 61 62 IP Fragmentation & Reassembly network links have MTU (max.transfer size) - largest possible link-level frame. different link types, different MTUs large IP datagram divided (“fragmented”) within net one datagram becomes several datagrams “reassembled” only at final destination IP header bits used to identify, order related fragments fragmentation: in: one large datagram out: 3 smaller datagrams reassembly 63 IP Fragmentation and Reassembly IP header has identification (x), flag, and fragmentation fields Example: 4000byte d’gram (20byte header + 3980 IP payload). MTU = 1500bytes Frag 1: 1480bytes + 20byte header Frag 2: 1480bytes + 20byte header Frag 3: 3980-2*1480 bytes + 20byte header length ID fragflag offset =4000 =x =0 =0 One large datagram becomes several smaller datagrams length ID fragflag offset =1500 =x =1 =0 length ID fragflag offset =1500 =x =1 =1480 length ID fragflag offset =1040 =x =0 =2960 64 IP Fragmentation processing at a Router Fragmentation is performed when packet size is larger than MTU size of the outgoing interface To fragment/segment a long internet packet, an Intermediate System using the Internet Protocol (for example, a router), creates two new IP packets and copies the contents of the IP header fields from the long packet into BOTH new IP headers. The data of the long packet is divided into two portions on a 8 byte (64 bit) boundary. All packets which have a more fragments (MF) flag set, must have an integral multiple of 8 bytes, but those that do not have this flag set need not do. If we call the number of 8 byte blocks in the first portion NFB (for Number of Fragment Blocks). The first portion of the data is placed in the first new IP packet, and the total length field is set to the length of the FIRST IP packet. The more-fragments flag (MF) is set to one. The second portion of the data is placed in the second new IP packet, and the total length field is set to the length of the SECOND packet. The more-fragments flag (MF) carries the same value as the long packet. The fragment offset field of the second new IP is set to the value of that field in the long IP packet plus the NFB. 65 IP Addresses in TCP/IP Model Addresses provide UNIQUENESS Different from other types of address Layer 1 – physical address: hardware manufacturer assigns, hardly ever changes; MAC addresses Layer 2 – logical address: you assign, and reassign as changes are made in the network; IP addresses Layer 3 – “service” address: standards bodies assign, software manufacturers must abide by them for interoperability; TCP/UDP addresses Why 32 bits for IP? 2^32 = 4+ billion – enough addresses (???) 66 Addressing, Numbering, and Notation Computers care about BINARY Humans care about DECIMAL IP addresses are truly 32-bit unsigned integers, represented in dotted-decimal (a.k.a. dotted-quad) for our convenience Electrical Engineers care about HEXADECIMAL On/off, hi/low, signal/no signal, etc. Neither computer nor human? Compact representation of binary info Often used for Layer 2 (hardware) addresses YOU need to care about ALL 3 Discuss some examples here… 67 Bit Positions and Their Values 68 IP Address Classes 69 IP Address Class Ranges 70 Address Class Characteristics Class Network Bits Host Bits Total Networks Total Addresses A 8 24 127 16,777,216 B 16 16 16,384 65,536 C 24 8 2,097,152 256 71 IP addressing: the last word... Q: How does an ISP get block of addresses? A: ICANN: Internet Corporation for Assigned Names and Numbers (guidelines in RFC 2050) allocates addresses manages DNS assigns domain names, resolves disputes 72 Subnetting To divide the standard classful host-number field into two parts - the subnet-number and the host-number on that subnet. Motivation: Efficient use of available network addresses Flexibility in planning network growth and design Capability to contain broadcast traffic (ARP, RARP, etc…) Subnets under local administrative control Mechanism: Define/assign a subnet mask for addresses in a network that has been subnetted Subnet mask tells router which octets of an IP address to pay attention to when comparing the destination address of a packet to its routing table entries A subnet mask identifies the subnet field of network addresses Correct routing requires that all subnets of a network be physically contiguous. In other words, the network must be set up such that it does not require traffic between any two subnets to cross another network Most implementations require that all subnets of a network have the same number of subnet bits. Example 73 Arrangement of Subnets 74 How To Calculate Subnet Address with a Given Subnet Mask Resulting subnet address is 171.16.1.0 75 Example Subnet Masks 76 Using Subnet Masks 77 Supernetting – CIDR and VLSM Motivation: Address issues with current IP Address Depletion Subnetting allows you to take a (classful) block of addresses and break it up into usable portions Subnetting >>> Segregation Supernetting allows you to implement classless addressing scheme and combine address blocks for the purposes of efficiency in routing updates Supernetting >>> Aggregation Rationale: More flexible use of IP addresses and reduces entries in the routing table Two ways to implement Supernetting Organizations need Variable Length Subnet Mask (VLSM) to provide flexibility and address efficiency The Internet needs Classless Interdomain Routing (CIDR) for scalability 78 Requirements for Deploying CIDR or VLSM The successful deployment of VLSM has three prerequisites: The routing protocols must carry extended network prefix information with each route advertisement. All routers must implement a consistent forwarding algorithm based on the “longest match.” For route aggregation to occur, addresses must be assigned so that they have topological significance 79 Comparing CIDR to VLSM CIDR and VLSM both allow a portion of the IP address space to be recursively divided into subsequently smaller pieces. The difference is that with VLSM, the recursion is performed on the address space previously assigned to an organization and is invisible to the global Internet. CIDR, on the other hand, permits the recursive allocation of an address block by an Internet Registry to a highlevel ISP, a mid-level ISP, a low level ISP, and a private organization’s network. 80 Classless Interdomain Routing (CIDR) With subnet addressing, we can have higher flexibility within a domain/AS However, the rigidity of classful IP addresses is still very inflexible (e.g. HostIDs in a domain is limited to 256, 66048, 16908288) CIDR – use arbitrary prefix length of Network ID E.g. 205.100.0.0/22 means that network ID length is 22 bits, i.e. netmask is 255.255.252.0 Also allows RECURSION allocation of an address block provided by the Internet Registry to a high-level ISP, to a mid-level ISP, to a low-level ISP, and finally to a private organization’s network 81 Classless Interdomain Routing (CIDR) Changes to routing table Each entry must specify a 32-bit mask together with the 32-bit IP address Use longest prefix match to find a suitable entry E.g. a packet with destination IP addr: 205.100.1.2, and the routing has two entries as 205.100.0.0/22 and 205.100.0.0/20. Both entries match the destination IP addr, which one should be chosen? Ans: Choose the one with longest matched bits 205.100.0.0/22 = 11001101.01100100.00000000.00000000 205.100.0.0/20 = 11001101.01100100.00000000.00000000 205.100.1.2 = Longest match 11001101.01100100.00000001.00000010 82 Classless Interdomain Routing (CIDR) Advantages: An organization can “buy” the number of IPs according to its needs (not confined to 256, 66048, 16908288) Reduce routing table size significantly as multiple “continuous” networks following the same route can be combined to form a single routing entry E.g. original 4 entries for destinations as 137.188.0.0, 137.189.0.0, 137.190.0.0,137.191.0.0 Now, we can combine them into one entry of 137.188.0.0/14 83 An Example of How CIDR Is Used CIDR Reduces the Size of Internet Routing Tables 84 CIDR: Partitioning of IP addresses Q: How does network get network part of IP addr? A: gets allocated portion of its provider ISP’s address space ISP's block 11001000 00010111 00010000 00000000 (allocated to ISP). It is divided into 8 equal sized blocks. Organization 0 11001000 00010111 00010000 00000000 Organization 1 11001000 00010111 00010010 00000000 Organization 2 11001000 00010111 00010100 00000000 ... ….. …. 200.23.16.0/23 200.23.18.0/23 200.23.20.0/23 …. Organization 7 200.23.30.0/23 11001000 00010111 00011110 00000000 200.23.16.0/20 85 CIDR Hierarchical addressing: route aggregation Hierarchical addressing allows efficient advertisement of routing information: “Fly-by-night-ISP requests that all datagrams whose first 20 address bits match 200.23.16.0/20. The world doesn’t know that within this there are 8 other orgs. each with their own networks. Organization 0 200.23.16.0/23 Organization 1 200.23.18.0/23 Organization 2 200.23.20.0/23 Organization 7 . . . . . . Fly-By-Night-ISP “Send me anything with addresses beginning 200.23.16.0/20” Internet 200.23.30.0/23 ISPs-R-Us “Send me anything with addresses beginning 199.31.0.0/16” 86 Hierarchical addressing: more specific routes Suppose Org. 1 dislikes Fly-by-night-ISP’s service and wants to move to ISPs-R-Us? Org.1 keeps its addresses in 200.23.18.0/23 but now ISPs-R-Us advertises 200.23.18.0/23. When other routers see 200.23.16.0/20 & 200.23.18.0/23 and want to route to 200.23.18.0/23 They will use the longest prefix matching rule and send to ISPs-R-Us Organization 0 200.23.16.0/23 Organization 2 200.23.20.0/23 Organization 7 . . . . . . Fly-By-Night-ISP “Send me anything with addresses beginning 200.23.16.0/20” Internet 200.23.30.0/23 ISPs-R-Us Organization 1 200.23.18.0/23 “Send me anything with addresses beginning 199.31.0.0/16 or 200.23.18.0/23” 87 Supernetting – VLSM In 1987, RFC 1009 specified how a subnetted network could use more than one subnet mask. When an IP network is assigned more than one subnet mask, it is considered a network with (VLSM) since the extended network prefixes have different lengths. Allows RECURSIVE division of a network prefix (subnets of subnets) Allows detailed structure of routing info for one subnet group to be hidden from routers in another subnet group VLSM is different than CIDR because the recursion is performed on the address space previously assigned to an org. and is INVISIBLE to the global Internet 88 VLSM Design Considerations When developing a VLSM design, the network designer must recursively ask the same set of questions as for a traditional subnet design. The same set of design decisions must be made at each level of the hierarchy: 1 How many total subnets does this level need today? 2 How many total subnets will this level need in the future? 3 How many hosts are on this level’s largest subnet today? 4 How many hosts will be on this level’s largest subnet be in the future? 89 An Example of How VLSM Is Used Recursive Division Detailed Structure Of Recursion is hidden VLSM Permits Route Aggregation - Reducing Routing Table Size 90 IP Design Considerations Addressing (Impact of Subnetting) Routing (Topology dependent) Fragmentation and reassembly (MTU size for different layers) Datagram lifetime (impact of TTL setting) Error control (Related to MTU size) Flow control (limited via ICMP) 91 IP Futures In addition to Stevens’ observations: IP version 6 IPSec MPLS IP Multicast These aren’t really futures anymore; they’re here today Think about what you’d like to cover in last week Time permitting I’m leaning toward IPSec 92 IPv4 addressing - Summary There are three types of IPv4 addressing environments. Original Classful. Classful and subnet mask (RFC 950). Classless. An internetwork can be a mix of several environments. 93 Chapter 4: ARP: Address Resolution Protocol To ARP or Not to ARP? That is the question. TCP/IP Layering 95 Multiplexing and Demultiplexing 96 TCP/IP suite: ARP Maps IPv4 addresses to MAC addresses. An ARP request is a local broadcast. ARP broadcasts are not propagated through routers. Entries in the ARP table are deleted when a timeout expires. Several scenarios exist: You know the IP address to send to and you need the corresponding MAC address (ARP) You know your MAC address and you need to know your IP address (RARP) You’re hiding physical networks (Proxy ARP) You need to verify that your IP address isn’t being used by another host (Gratuitous ARP) 97 98 Packet Delivery on a single LAN 99 Use of ARP - Packet Delivery across multiple LANs 100 The Purpose of ARP 101 An Example: ARP with TFTP 102 ARP Frame Format 103 ARP Notes ARP generally only occurs on a single physical network ARP request is a layer 2 broadcast, and routers block these broadcasts by default ARP is designed to work for protocols other than IP A generic solution Some other protocols (e.g., IPX) were designed such that they don’t need ARP 104 More ARP Notes Dynamic nature of ARP is very flexible MAC addresses tend to stay the same, but IP addresses can change (e.g., DHCP, change in logical structure of IP network) Sometimes MAC addresses can change (e.g., change a broken NIC, administratively change MAC address) ARP allows for dynamic (re-)mapping What happens if you ARP every time? Lots of overhead Use a cache mechanism with timeouts 105 Notes on Proxy ARP Also known as “promiscuous ARP” Accommodates older TCP/IP stacks. A technique by which a router replies to an Address Resolution Protocol (ARP) request from a host on behalf of the ARP target host. Proxy ARP (Address Resolution Protocol) is a technique by which a network host answers to the ARP queries for the network address that it does not have configured on the receiving interface. Proxying ARP requests on behalf of another host effectively directs all LAN traffic destined for that host to the proxying host/router. The "captured" traffic is then typically routed to the destination host via another interface or via a tunnel. When you see same MAC address in ARP cache for 2 different IP addresses, that’s a hint that Proxy ARP is being used Proxy ARP can create DoS attacks on networks if misconfigured. For example a misconfigured router with proxy ARP has the ability to receive packets destined for other hosts (as it gives its own MAC address in response to ARP requests for other hosts/routers), but may not have the ability to correctly forward these packets on to their final destination, thus blackholing the traffic. 106 Uses of Gratuitous ARP When a computer starts, a packet is broadcast on the network containing the computer's TCP/IP address to prevent the use of duplicate addresses on the same network When a computer starts and its Ethernet hardware address has changed due to interface card replacement, a packet is broadcast to other host to signal an update to the IP-to-MAC address mapping 107 Issues With ARP Weak Security a bogus host can issue a gratuitous ARP and change cache entries on other router’s cache table a bogus host can send replies giving its own hardware address (instead of the target) – re-directing traffic Broadcasting excessive CPU can be expensive use of bandwidth costs 108 Chapter 5: RARP: Reverse Address Resolution Protocol What is RARP For? A workstation without a hard drive (e.g., diskless workstation, X-terminal, “thin client”) may have no means to “remember” an IP address However, it will have a NIC that has a MAC address burned-in on an EEPROM RARP allows this host to broadcast and request it’s IP address A RARP Server must be configured on the local subnet to assign this particular MAC address with a unique IP address 110 Issues with RARP More difficult to implement than ARP ARP is needed for basic IP communications and requires no configuration (mostly) RARP config normally resides in a static text file Coordination between multiple RARP servers requires that those text files are always in sync Improvements over RARP BOOTP DHCP – most commonly used today 111 TCP/IP suite: DHCP vs. RARP RARP is based on a table that needs to be configured in the RARP server. Static, one-to-one address mapping: The same MAC address will always acquire the same IP address. RARP does provide IP addresses to devices, but there is no much gain in administrative overhead. 112 TCP/IP suite: DHCP vs. RARP RARP is obsolete and almost never seen. DHCP is implemented in many devices such as Windows NT servers, Novell servers, Cisco routers, NAT boxes… Although there are plans for DHCPv6, IPv6 has some auto-configuration mechanisms that will probably make DHCP obsolete in the long run. 113 TCP/IP suite: DHCP This reservation mechanism provides a functionality similar to RARP: the IP address is obtained from the server and is always the same. A typical IP set is a combination of static, reservations, and dynamic DHCP addresses. 114 TCP/IP suite: DHCP DHCP is an evolution of BOOTP Provides the same basic functionality as RARP, but the underlying mechanism is not the same. Can provide additional functionality such as the address of the WINS server or the node-type. 115 TCP/IP suite: DHCP vs. RARP Unless a reservation is made, there is no guarantee that a device will obtain the same IP address each time. Servers are typically configured with static IP addresses. DHCP does take some of the administrative burden out (for workstations). 116 DHCP: Dynamic Host Configuration Protocol Goal: allow host to dynamically obtain its IP address from network server when it joins network Can renew its lease on address in use Allows reuse of addresses (only hold address while connected an “on” Support for mobile users who want to join network DHCP overview: host broadcasts “DHCP discover” msg DHCP server responds with “DHCP offer” msg host requests IP address: “DHCP request” msg DHCP server sends address: “DHCP ack” msg 117 DHCP client-server scenario A B 223.1.2.1 DHCP server 223.1.1.1 223.1.1.2 223.1.1.4 223.1.2.9 223.1.2.2 223.1.1.3 223.1.3.1 223.1.3.27 223.1.3.2 E arriving DHCP client needs address in this network 118 TCP/IP suite: DHCP vs. RARP There are some circumstances where the use of DHCP would be nice, but the devices needs a fixed IP address. Example: Print Servers. The DHCP solution is called reservation. The MAC address of the device is configured in the DHCP server. 119 Chapter 6: ICMP: Internet Control Message Protocol Where ICMP in The TCP/IP Layering 121 What is ICMP? Every protocol suite needs mechanisms for control and error messaging Phone network to end user: dial tone, ringing tone, etc. (note: in-band) Phone network between switches: SS7 network for call management (note: out-ofband) ICMP is the set of messages that handle basic control and error messaging for the TCP/IP protocol suite 122 ICMP Message Types 123 Key ICMP Uses Time Stamp Ping Traceroute Source Quench Indication that flow control needs to be activated at the source MTU size determination ICMP Destination Unreachability Can be used to detect malicious port scanning activity 124 125 ICMP Message Transport in IP 126 ICMP Message Format 127 ICMP Timestamp 128 Round Trip Time (RTT) Concept 129 Chapter 7: ping What is ping? Uses ICMP Echo Request and Reply Tests reachability – make sure that the network connection is in tact Don’t use it for fine-grained measurements of network performance 131 ICMP packets used for ping 132 133 Ping output 134 Ping with IP Options: Record Route 135 ping with Record Route 136 ICMP Source Quench When to send an ICMP Source Quench What to do when an ICMP Source Quench is received Standards says: when a packet is dropped inside a router due to depleted buffer space Real life: when ½ of the buffer space is used up Implementation dependent Ex: Reset the window size to 0 for n number of ACKS have been received Security Concern: Source Quench messages are used by attackers in ICMP flood attacks 137 MTU Size Determination 138 ICMP Destination Unreachability 16 different categories of Destination Unreachable ICMP messages Ex: ‘port unreachable’ (type 3, code 3) where a local host requests information from a remote host using TCP or UDP, and the remote host doesn’t have an application listening on the required port. The remote host replies with the type 3, code 3, ICMP messages declaring the problem Security Concern: These messages outbound will enable an attacker the ability to easily map network topology 139 ICMP Port Unreachable – Example msg 140 ICMP Port Unreachable - Format 141 Chapter 8: traceroute IP Routing Processes The IP routing processes on all nodes involved in the delivery of an IP packet includes: the sending host, the intermediate routers, and the destination host. IP on the Sending Host When a packet is sent by a sending host, the packet is handed from an upper layer protocol (TCP, UDP, or ICMP) to IP. IP on the sending host does the following: Sets the Time-to-Live (TTL) value to either a default or application-specified value. IP checks its routing table for the best route to the destination IP address. If no route is found, IP indicates a routing error to the upper layer protocol (TCP, UDP, or ICMP). Based on the most specific route, IP determines the forwarding IP address and the interface to be used for forwarding the packet. IP hands the packet, the forwarding IP address, and the interface to Address Resolution Protocol (ARP), and then ARP resolves the forwarding IP address to its media access control (MAC) address and forwards the packet. IP on the Router - When a packet is received at a router, the packet is passed to IP. IP on the router does the following: IP verifies the IP header checksum. If the IP header checksum fails, the IP packet is discarded without notification to the user. This is known as a silent discard . IP verifies whether the destination IP address in the IP datagram corresponds to an IP address assigned to a router interface. If so, the router processes the IP datagram as the destination host (see step 3 in the following "IP on the Destination Host" section). If the destination IP address is not the router, IP decreases the time-to-live (TTL) by 1. If the TTL is 0, the router discards the packet and sends an ICMP Time Expired-TTL Expired message to the sender. If the TTL is 1 or greater, IP updates the TTL field and calculates a new IP header checksum. IP checks its routing table for the best route to the destination IP address in the IP datagram. If no route is found, the router discards the packet and sends an ICMP Destination Unreachable-Network Unreachable message to the sender. Based on the best route found, IP determines the forwarding IP address and the interface to be used for forwarding the packet. IP hands the packet, the forwarding IP address, and the interface to ARP, and then ARP forwards the packet to the appropriate MAC address. This entire process is repeated at each router in the path between the source and destination host. IP on the Destination Host - When a packet is received at the destination host, it is passed up to IP. IP on the destination host does the following: IP verifies the IP header checksum. If the IP header checksum fails, the IP packet is silently discarded. IP verifies that the destination IP address in the IP datagram corresponds to an IP address assigned to the host. If the destination IP address is not assigned to the host, the IP packet is silently discarded. Based on the IP protocol field, IP passes the IP datagram without the IP header to the appropriate upper-level protocol. If the protocol does not exist, ICMP sends a Destination Unreachable-Protocol Unreachable message back to the sender. For TCP and UDP packets, the destination port is checked and the TCP segment or UDP header is processed. If no application exists for the UDP port number, ICMP sends a Destination Unreachable-Port Unreachable message back to the sender. If no application exists for the TCP port number, TCP sends a Connection Reset segment back to the sender. 143 What is traceroute? A program ported to just about anything with a TCP/IP stack Shows the path packets take across the network Takes advantage of the ICMP “time exceeded” message “tracert” in Windows products 144 How Traceroute Works Traceroute creates an UDP packet with the time to live (TTL) in the IP Header set to 1 and addresses the packets set to the destination computer's IP address Traceroute process waits for a response. This response will be: An ICMP Time Exceeded message - this means the host responding is not the destination. An ICMP Port Unreachable - this means the UDP layer at the destination host responding doesn't not recognize the UDP port info in the received UDP packet. The computer on which the messages die because the time to live expired (somewhere between the Source and Destination hosts ) sends back ICMP Time Exceeded (ICMP Type '11') responses. These messages indicate to the soure that the traceroute messages have not yet reached the destination host The source increments the TTL in the IP Header by one, then repeats steps the previous six steps (creates 3 packets, sets the Time to Live to the next highest number, starts a timer, transmits the packets, waits for a response). This process is repeated until the packets reach the destination computer which the source host is tracing the route to. When the ICMP message reaches the destination computer, the UDP layer will get to process it and will find out that the UDP port specified is invalid which will trigger an ICMP Port Unreachable message back to the source host. The Port Unreachable error message indicates to traceroute that the destination has been reached. 145 ICMP time exceeded message 146 How to read traceroute output 147 148