* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download OSI Reference Model - Long Island University
Asynchronous Transfer Mode wikipedia , lookup
Deep packet inspection wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Distributed firewall wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Internet protocol suite wikipedia , lookup
Computer network wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Network tap wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
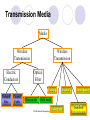
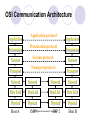
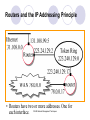
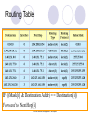
Network Elements and Services CS 695 Network Management Techniques Prof. P. T. Chung CS 695 Network Management Techniques Outline 1. Networking - Concepts 2. Internet Communication Protocols 3. Network Elements 4. Network Management Related Protocols CS 695 Network Management Techniques 1. Networking - Concepts Network Classifications Network Technologies Network Transmission Media Network Elements CS 695 Network Management Techniques Network Classifications Networks – Classified by Applications Data Communication Network Telecommunication Network Networks – Classified by Distance LAN (Local Area Network) MAN (Metropolitan Area Network) WAN (Wide Area Network) CS 695 Network Management Techniques Network Classifications (Conti) Networks – Classified by Switching Packet Switching Circuit Switching Networks – Classified by Transmission Media Wired Network Wireless Network CS 695 Network Management Techniques Bandwidth Network Technologies Gigabit Ethernet ATM Fast Ethernet FDDI MAN & SMDS Ethernet Token Ring Frame Relay ISDN (basic rate) LAN MAN CS 695 Network Management Techniques Distance WAN Transmission Media Media Wireline Transmission Electric Conductors Wireless Transmission Optical Fiber Radio Twisted Pair Coaxial Cable Mono-mode Infrared Laser Links Multi-mode Microwave CS 695 Network Management Techniques Satellite Transmission Network Elements LAN/Internet Elements: oRepeater oHub oBridge oSwitch oRouter oGateway WAN Elements: o Modem o Repeater o ADM (Add-Drop Multiplexer) o Cross-Connect o Switch o Multiplexer o Concentrator CS 695 Network Management Techniques OSI Communication Architecture Application Application protocol Application Presentation Presentation protocol Presentation Session Session protocol Session Transport Transport protocol Transport Network Network Network Network Data Link Data Link Data Link Data Link Physical Physical Physical Physical Host A CS 695 Network Management Techniques IMP 1 IMP 2 Host B 2. Internet Communication Protocols The TCP/IP Protocol Architecture TCP/IP Layers ( or TCP/IP Suite ) Application Layer Host-to-host, or transport layer Internet Layer Network Access Layer Physcical Layer CS 695 Network Management Techniques Internet Communication Protocol Application HTTP SMTP NNTP TELNET SNMP DNS TCP Transport Internet Network Access Data Link FTP ECHO NTP TIME BOOTP DHCP UDP RIP OSPF BGP ICMP IGMP IP ARP RARP SLIP PPP IP (Internet Protocol) Mainly provides multiple routes or Routing capabilities. Protocol Characteristics: Connectionless, Unreliable IP Addressing: Every host in TCP/IPnetwork has one 32-bit IP address. 140.131.76.1 CS 695 Network Management Techniques IP Address length:4 Bytes (32-Bit) IP address: Network Address Subnet Host Address) Network Subnet Host Host CS 695 Network Management Techniques IP Address Formats CS 695 Network Management Techniques CS 695 Network Management Techniques CS 695 Network Management Techniques Network Mask Set 1 for bits in Network Address and Subnet, and set 0 for other bits in IP address Class A 255.0.0.0 Class B 255.255.0.0 Class C 255.255.255.0 IP address Logical AND (Network Mask, IP Address) CS 695 Network Management Techniques Routers and the IP Addressing Principle • Routers have two or more addresses. One for each interface. CS 695 Network Management Techniques Routing Table IF ((Mask[i] & Destination Addr) = = Destination[i]) Forward to NextHop[i] CS 695 Network Management Techniques IP Forwarding Process CS 695 Network Management Techniques IF ((Mask[i] & Destination Addr) = = Destination[i]) Forward to NextHop[i] CS 695 Network Management Techniques Port Each host’s application layer (or processing layer) may have different application, service, or resource. Once a host received data from network, transport layer should have a mechanism to provide and distinquish network application service so that it could send data to correct processing program. Each upper-level communication application service or program maps to a unique TCP or UDP Port Number. CS 695 Network Management Techniques Common TCP/IP Application Services and Port Numbers TCP 21 23 25 53 79 80 110 119 123 FTP Telnet SMTP DNS Finger HTTP POP3 NNTP NTP UDP 53 67 69 161 162 DNS BOOTP TFTP SNMP SNMP-Trap Port: 1~1024,for Internets CS 695 Network Management Techniques 3. Network Elements Repeater Hub Bridge Switch Router Routing Switch Gateway CS 695 Network Management Techniques Repeater Operates at Layer 1, the physical layer. Connects two network segments into one large segment, or to expand an existing segment. Enhances data signals and thus can be used to extend maximum cabling distances. There is no network intelligence built into a simple repeater; it is used strictly for signal propagation. CS 695 Network Management Techniques Hub Operates at Layer 1, the physical layer. Simply a multiport repeater. Can be used to increase overall network size and number of nodes on a single segment. Can isolate faults within the subnet. Allows you to add stations to a segment without disrupting the entire network. CS 695 Network Management Techniques Bridge Operates at Layer 2, the data link layer. Allows networks with different physical signaling, but with compatible data link addressing schemes, to communicate. Helps reduce traffic on a backbone LAN by filtering any information coming from one segment to another that does not need to be forwarded through the backbone. A common use for a bridge is to allow users on an Ethernet LAN and a Token Ring LAN to communicate with each other. CS 695 Network Management Techniques Bridge Example Application Application Presentation Presentation Session Session Transport Bridge Network Transport Network Data Link Data Link Data Link Data Link Physical Physical Physical Physical CS 695 Network Management Techniques Switch Operates at Layer 2, the data link layer. Dispatches data to its destination, which it determines from the packet’s lower-layer media access control (MAC) address. Can limit traffic, and does not understand network protocols. CS 695 Network Management Techniques Router Operates at Layer 3, the network layer. Connects two networks with different technologies, and provides an intelligent means of transferring packets from one network to the other. Also forwards traffic among multiple hubs and bridges. CS 695 Network Management Techniques Router Example Application Application Presentation Presentation Session Session Transport Router Transport Network Network Network Network Data Link Data Link Data Link Data Link Physical Physical Physical CS 695 Network Management Techniques Physical Routing Switch Operates at Layer 3, the network layer. Combines the intelligence of a router with the efficiency of a switch, Routing data at higher speeds. CS 695 Network Management Techniques Gateway Operates at Layer 7, the application layer. Can encompass all seven of the OSI model layers. A computing system that can be programmed to do any number of intricate protocol conversions and negotiations, such as between IP and IPX. CS 695 Network Management Techniques CS 695 Network Management Techniques 4. Network Management related Protocols SNMPv1 SNMPv2C ICMP ARP/RARP DHCP CS 695 Network Management Techniques SNMPv1 (Simple Network Management Protocol version 1) The most common management protocol in use in data networks. Provides a means of obtaining information from, and sending information to, network devices. Based on the manager-agent model. Uses Management Information Bases (MIBs) to exchange information between the manager and the agent. Using the SNMP protocol, a manager can query and modify the status and configuration information on each managed device by making requests to the agent running on the managed device. All commands use the UDP/IP protocol, which means that communication between the manager and the agent is connectionless. SNMP operates at Layer 7, the application layer. CS 695 Network Management Techniques SNMPv2C (version 2) SNMPv2C includes the basic functions of SNMPv1. Adds new message types, standardized multi-protocol support, enhanced security, new MIB objects, and a way to co-exist with SNMPv1. SNMPv2C is useful for the retrieval of large amounts of management information using fewer network resources. CS 695 Network Management Techniques ICMP (Internet Control Message Protocol) ICMP is the part of IP that handles error and control messages. ICMP operates at Layer 3, the network layer. ICMP supports an echo function, which sends a packet on a round-trip between two hosts. Ping, which sends a signal to see if an interface is up and running, is based on ICMP echo. ICMP can also send an address mask request that returns the address of the subnet mask on the remote system. This feature is important for non-SNMP devices. CS 695 Network Management Techniques ARP/RARP (Address Resolution Protocol / Reverse ARP) ARP/RARP are used at Layer 2, the link layer, ARP is used to map an IP address to a MAC (or link level, or hardware) address. RARP is used to map a MAC address to an IP address. CS 695 Network Management Techniques DHCP (Dynamic Host Configuration Protocol) DHCP allows IP addresses to be allocated on a temporary basis (a lease). When the lease for an IP address expires, the address can be reused by a different node. This is useful in environments supporting mobile users who connect to the network with a laptop from many different places. This helps alleviate the problem of limited IP addresses and simplifies TCP/IP client configurations. CS 695 Network Management Techniques