* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Categories of I/O Devices - NYU Stern School of Business
Server Message Block wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Bus (computing) wikipedia , lookup
Dynamic Host Configuration Protocol wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Hypertext Transfer Protocol wikipedia , lookup
Real-Time Messaging Protocol wikipedia , lookup
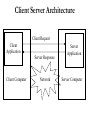
Categories of I/O Devices • Human readable – – – – – – • Machine readable Communication with the user Printers Video display terminals Display Keyboard Mouse – Communication with electronic equipment – Disk drives – Sensors – Controllers/Actors • Communication – Communication with remote devices – Digital line drivers – Modems Differences in I/O Devices • Complexity of control • Unit of transfer – Data may be transferred as a stream of bytes for a terminal or in larger blocks for a disk • Data representation – Encoding schemes • Error conditions – Devices respond to errors differently Differences in I/O Devices • Programmed I/O – Process is busy-waiting for the operation to complete • Interrupt-driven I/O – I/O command is issued – Processor continues executing instructions – I/O module sends an interrupt when done • Data Rate – Human input can be very slow – Machine communication should be fast Differences: Data Rate Operating System Design Issues • Efficiency – Most I/O devices extremely slow compared to main memory – Use of multiprogramming allows for some processes to be waiting on I/O while another process executes – I/O cannot keep up with processor speed – Swapping is used to bring in additional Ready processes which is an I/O operation Operating System Design Issues • Generality – Desirable to handle all I/O devices in a uniform manner – Hide most of the details of device I/O in lowerlevel routines so that processes and upper levels see devices in general terms such as read, write, open, close, lock, unlock Data Transfer Scheme • Block-oriented – Information is stored in fixed sized blocks – Transfers are made a block at a time – Used for disks and tapes • Stream-oriented – Transfer information as a stream of bytes – Used for terminals, printers, communication ports, mouse, and most other devices that are not secondary storage I/O Buffering • Reasons for buffering – Processes must wait for I/O to complete before proceeding (you can’t do anything useful anyway) • Adjust speed differences between information source and use • Example: Printer buffer – You don’t want your computer to sit and wait in order to transfer data until there is no other job ahead in the queue and the data could go directly to printer – Instead printer buffers data Techniques for Performing I/O • Direct Memory Access (DMA) – DMA module controls exchange of data between main memory and the I/O device – Processor interrupted only after entire block has been transferred • CPU independent, CPU can do something else while I/O data transfer to memory happens Direct Memory Access • Takes control of the system form the CPU to transfer data to and from memory over the system bus • Cycle stealing is used to transfer data on the system bus • The instruction cycle is suspended so data can be transferred • The CPU pauses one bus cycle • No interrupts occur, no process swapping – Do not save context Communication Inputs • I/O = Input + Output • Output: CPU initiated • Input: Initiated by device – Creates an interrupt to inform CPU of input – Typical Example: Communication in Client Server environment Examples of Client Server • Application-level protocols provide high-level services – – – – – DNS Electronic mail TELNET: Remote login FTP HTTP World Wide Web • All of these applications use client-server architecture Client Server Architecture Client Request Client Application Server Response Client Computer Network Server Application Server Computer Client Server Paradigm • Server application is ``listener'' – Waits for incoming message – Performs service – Returns results • Client application establishes connection – Sends message to server – Waits for return message Issues • • • • • Identification of Server computer Identification of Client computer Identification of Server Application Identification of Client Application How do you ensure that both application “understand” each other? – Answer: IP address, Port number , TCP Client • • • • • • • • Arbitrary application program Becomes client when network service is needed Also performs other computations Invoked directly by user Runs locally on user's computer Initiates contact with server Can access multiple services (one at a time) Does not require special hardware or sophisticated operating system Server • Special purpose application dedicated to providing network service • Starts at system initialization time • Runs on a remote computer (usually centralized, shared computer) • Waits for service requests from clients; loops to wait for next request • Will accept requests from arbitrary clients; provides one service to each client • Requires powerful hardware and sophisticated operating system Server Class Computer • Shared, centralized computers that run many server applications called ``servers'' • More precisely, the applications are the ``servers'' and the computer is a ``server-class computer'' • Servers can run on very simple computers... Message exchange • Typically, client and server exchange messages: • Client sends request, perhaps with data • Server send response, perhaps with data • Client may send multiple requests; server sends multiple responses • Server may send multiple response - imagine video feed Message Protocols TCP • Standards for messages that ensure that the server can understand the client independent of implementation Multi Server and Client • Multiple clients share same server • One server class computer runs multiple server applications and types (eureka) • Listener organizes Service Identification • Each service gets a unique identifier; both client and server use that identifier • Server registers with local protocol software under the identifier • Client contacts protocol software for session under that identifier • Example - TCP uses protocol port numbers as identifiers • Server registers under port number for service • Client requests session with port number for service • How does client knows the port number on the server computer? Multiple servers for one service • Responding to a client request may require significant time • Other clients must wait while earlier requests are satisfied • Multiple servers can handle requests concurrently, completing shorter requests without waiting for longer requests Master-slave servers • One way to run concurrent servers is to dynamically create server processes for each client • Master server accepts incoming requests and starts slave server for each client • Slave handles subsequent requests from its client • Master server then waits for next request Examples of server running on eureka • Ps –u root – – – – Mountd In.telnetd Inetd Listen: • Program that does the listening for all server and starts a new serving program Review Interrupts • External devices (network card) creates interrupts that are first dealt with by an interrupt controller (IC) • IC sends highest priority interrupt to CPU and puts into the interrupt register the PC associated with the code that can deal with this type of interrupt – Listener decides what to do • Start new server • Start running server who was the recipient of incoming message Selecting from multiple servers • How do incoming messages get delivered to the correct server? • Each transport session has two unique identifiers • (IP address, port number) on server • (IP address, port number) on client • No two clients on one computer can use same source port • Thus, client endpoints are unique, and server computer protocol software can deliver messages to correct server process