* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download System Virtualization 1
Survey
Document related concepts
Transcript
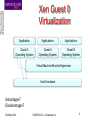
COMP25212 VIRTUALIZATION 2 Sergio Davies [email protected] Feb/Mar 2014 COMP25212 – Virtualization 2 Learning objectives – To understand the implementation choices and details of System Virtualization Feb/Mar 2014 COMP25212 – Virtualization 2 2 Aims and Definitions Application Applications Applications Operating System Guest A Operating System Guest B Operating System Hardware Virtual Machine Monitor/Hypervisor Host Hardware Unvirtualized Virtualized Host: Guest: Feb/Mar 2014 COMP25212 – Virtualization 2 3 Hosted Virtualization Application Applications Applications Guest A Operating System Guest B Operating System Virtual Machine Monitor/Hypervisor Host Operating System Host Hardware Advantages? Disadvantages? Feb/Mar 2014 COMP25212 – Virtualization 2 4 Xen Guest 0 Virtualization Application Applications Applications Guest 0 Operating System Guest A Operating System Guest B Operating System Virtual Machine Monitor/Hypervisor Host Hardware Advantages? Disadvantages? Feb/Mar 2014 COMP25212 – Virtualization 2 5 Revision: OS Protection/Privilege • OS handles physical resources: – Privileged Application Operating System • Application isolated from resources: Hardware – Non-privileged Unvirtualized Feb/Mar 2014 COMP25212 – Virtualization 2 6 Virtualization: Protection/Privilege • VMM handles physical resources: – Privileged • Guest OS isolated from resources Applications Applications Guest A Operating System Guest B Operating System Virtual Machine Monitor/Hypervisor Host Hardware – non- (less-) privileged Virtualized VMM gets control on every guest OS access to physical resource Feb/Mar 2014 COMP25212 – Virtualization 2 7 What Physical Resources are Guarded? • Timers • CPU registers: – Interrupt Enable – Page Table Base • Device Control Registers – Programmed I/O? – Interrupt I/O? – DMA I/O? • Interrupts (may be for different Guest?) • Memory Mapping (page tables) Feb/Mar 2014 COMP25212 – Virtualization 2 8 How does Guest Cause VMM Entry? • VMM designers are (a bit) lucky: – Many Guest accesses to physical resources cause trap in non-privileged mode – So, running the OS in non-privileged mode suffices • BUT some instructions behave differently (without trapping) in privileged and nonprivileged mode (e.g. Intel “Store into Flags”) Feb/Mar 2014 COMP25212 – Virtualization 2 9 Memory Accessing in Virtualization Virtual Address OS Page Tables (+ TLBs for efficiency) Physical Address Unvirtualized Virtual Address OS Page Tables VMMPage Tables Physical Address TLBs ?? Virtualized Feb/Mar 2014 COMP25212 – Virtualization 2 10 Interfacing Guest OS and VMM • Three solutions today: a) Software (static) b) Software (dynamic) c) Hardware (dynamic) Feb/Mar 2014 COMP25212 – Virtualization 2 11 ParaVirtualization Modify Guest OS to be Virtualization-aware: a) call VMM for all privileged operations b) cooperate with VMM over shared page tables c) call VMM for input-output Advantages? Disadvantages? Feb/Mar 2014 COMP25212 – Virtualization 2 12 Detect and Fix Interfaces in VMM • Detection: – Write-protect Guest OS page tables – Code-scan (Dynamic Binary Translation?) Guest OS for unsafe instructions – plant traps • Fixing: – Use write-error trap to detect guest page-table writes – Provide “shadow page tables” for hardware TLBs – Use “illegal instruction” and “trap” traps Feb/Mar 2014 COMP25212 – Virtualization 2 13 Detect and Fix Interfaces in Hardware • Requirement: – VMM runs more-privileged than Guest OS • Hardware provides Application/OS and VMM modes • When Virtualization is active, all OS accesses to physical resources trap to VMM Advantages? Disadvantages? Feb/Mar 2014 COMP25212 – Virtualization 2 14