* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download A Digital Design Flow for Secure Integrated Circuits
Control system wikipedia , lookup
Power engineering wikipedia , lookup
Opto-isolator wikipedia , lookup
Switched-mode power supply wikipedia , lookup
Distribution management system wikipedia , lookup
Field-programmable gate array wikipedia , lookup
Transmission line loudspeaker wikipedia , lookup
Integrated circuit wikipedia , lookup
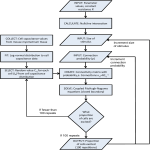
Written By: Kris Tiri and Ingrid Verbauwhede Presented By: William Whitehouse Purpose Wave Dynamic Differential Logic Differential Pair Routing Proposed Design Flow Experimental Results Comments Small integrated circuits are vulnerable to side-channel attacks (SCA). The authors present a digital VLSI design flow to create secure power-analysis-attack-resistant ICs. The proposed design flow uses a technique to balance the power consumption of the logic gates. It is independent of the cryptographic algorithm or arithmetic implemented. Wave Dynamic Differential Logic (WDDL) was chosen for its constant power consumption WDDL Library contains 37 of 53 basic logic functions WDDL AND-OR-INVERT example Demonstration of the output voltage for a WDDL gate: Load capacitances of differential outputs must be matched to achieve constant power consumption Load capacitance is made of: ◦ Intrinsic output capacitance ◦ Interconnect capacitance ◦ Intrinsic input capacitance With the shrinking of the channel length of the transistors the interconnect capacitance becomes the dominant capacitance The WDDL true and false output interconnects are routed in parallel such that they are: ◦ on adjacent tracks of the routing grid ◦ on the same layers ◦ the same length Interconnect must have the same parasitic effects (resistance and capacitance) Interconnects must be routed to control crosstalk To add the differential pair routing to the secure design flow the authors split the routing into two steps: ◦ Fat Wire Routing ◦ Interconnect Decomposition This figure illustrates the interconnect decomposition: Variation of the input capacitance of true/false WDDL gates is within 10% Variation between true/false interconnect capacitance of differential pair routing is within 20% Variation between true/false interconnect capacitance of regular routing of true/false gates is 50% The following is the authors’ proposed secure digital design flow: New stages include Cell Substitution and Interconnect Decomposition: Subset of DES algorithm Secure Reference Size (um2) 12880 3782 Mean Energy Consumption (pJ) 27.1 4.6 Normalized Energy Deviation 6.6% 60% Normalized Standard Deviation 0.9% 12% A differential power analysis (DPA) attack was performed on the two designs. Secure and Insecure AES Core were design and fabricated on the same die: Good case for use of differential gates Designs SCA resistant ICs Easy to add into digital design flow and not much overhead Independent of cryptographic algorithm Larger area and power consumption Much Lower throughput Only use WDDL gates and differential pair routing on some blocks of the design The WDDL library only has 70% of basic logic functions in a standard cell library If you have any questions please email me at: [email protected]