* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download PPT
Computer security wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Airborne Networking wikipedia , lookup
Computer network wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Bus (computing) wikipedia , lookup
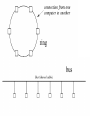
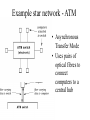
LAN technologies and network topology LANs and shared media Locality of reference Star, bus and ring topologies Medium access control protocols Mesh networks • Early local networks used dedicated links between each pair of computers • Some useful properties – hardware and frame details can be tailored for each link – easy to enforce security and privacy Disadvantages of meshes • Poor scalability Links between rooms/buildings • Many links would follow the same physical path Shared Communication Channels • • • • • Shared LANs invented in the 1960s Rely on computers sharing a single medium Computers coordinate their access Low cost But not suitable for wide area communication delays inhibit coordination Locality of reference • LANs now connect more computers than any other form of network • The reason LANs are so popular is due to the principle of locality of reference – physical locality of reference - computers more likely to communicate with those nearby – temporal locality of reference - computer is more likely to communicate with the same computers repeatedly LAN topologies • LANs may be categorised according to topology star ring bus Pros and cons • Star is more robust but hub may be a bottleneck • Ring enables easy coordination but is sensitive to a cable being cut • Bus requires less wiring but is also sensitive to a cable being cut Example bus network: Ethernet • Single coaxial cable - the ether - to which computers connect • IEEE standard specifies details – – – – data rates maximum length and minimum separation frame formats electrical and physical details Conceptual flow of Ethernet data • Transmitter has exclusive use of the medium Ethernet coordination • The computers can detect when a signal is on the Ether - carrier sense • Can only transmit when the Ether is free carrier sense with multiple access (CSMA) • Prevents a computer interrupting an ongoing transmission Collision detection • Collisions can occur if computers decide to transmit at the same time • Each computer also senses for garbled transmission - a collision • Ethernet mechanism is called - carrier sense multiple access with collision detect CSMA/CD • Example of a medium access control (MAC) protocol Collision recovery • Computers must wait after collision before retransmission • Choose random delay up to specified max • Double the delay for each subsequent collision - binary exponential backoff • Difference between bandwidth and throughput Throughput vs. offered traffic • More offered traffic results in more collisions, more backing-off and eventually congestion and reduced throughput What to do if the medium is busy? • Non persistent CSMA (deferential) – if medium is idle, transmit – if busy, wait a random time then try again • 1-persistent CSMA (selfish) – if idle, transmit – if busy, listen until idle then transmit • p-persistent (compromise) – if idle transmit with probability p and delay one time unit with probability (1-p) Example bus network LocalTalk • LAN technology for Apple computers • MAC protocol is CSMA/CA (collision avoidance) • Each computer first sends a small message to reserve the bus Wireless LANs and CSMA/CA • Collision detection does not work because a transmission from one computer may only be received by its immediate neighbours • Solution is collision avoidance – sender sends small request message to receiver – receiver responds with a ‘clear to send’ message that received by all adjacent computers Example ring network IBM Token Ring • MAC protocol based on token passing • Computer must wait for permission before transmitting • Computer controls the ring until finished • Data flows right round the ring – receiver makes a copy – transmitter checks for errors and then removes • Special message called the token grants permission (needs bit stuffing) • Computer grabs token, removes it, sends one frame, checks for errors then replaces it Example ring network - FDDI • Overcomes token ring susceptibility to failure through two counter-rotating cables Example star network - ATM • Asynchronous Transfer Mode • Uses pairs of optical fibres to connect computers to a central hub Summary • • • • Locality of reference Shared medium Star, bus and ring topologies Medium access control protocols