* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Document
Asynchronous Transfer Mode wikipedia , lookup
Deep packet inspection wikipedia , lookup
Registered jack wikipedia , lookup
Wireless security wikipedia , lookup
Passive optical network wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Network tap wikipedia , lookup
Computer network wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Airborne Networking wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Point-to-Point Protocol over Ethernet wikipedia , lookup
Power over Ethernet wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
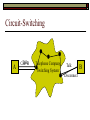
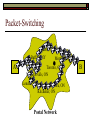
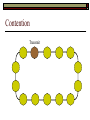
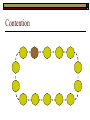
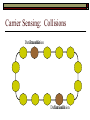
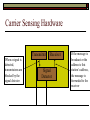
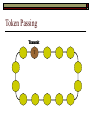
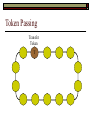
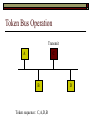
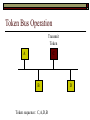
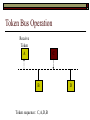
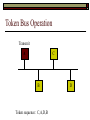
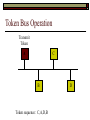
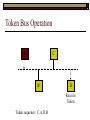
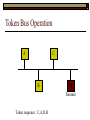
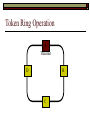
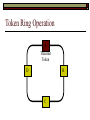
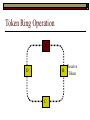
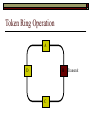
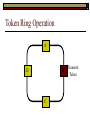
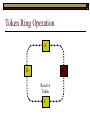
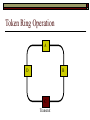
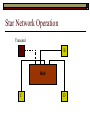
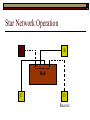
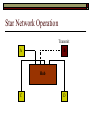
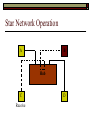
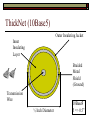
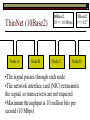
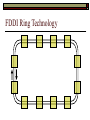
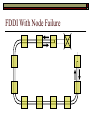
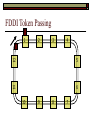
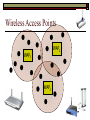
Data Link Layer Issues Dealing with Different Types of Networks Types of Networks Network hardware can be categorized into: Circuit-switched (e.g. telephone) Prior to communication, the hardware establishes a dedicated end-to-end connection Since there is a dedicated connection, a continuous stream of bytes can be sent Frequency or time-division multiplexing can be used to share links in such a network Packet-switched (e.g. Ethernet, ATM) Data is divided into packets of limited size, and each is forwarded through the network to the destination This can be done by routers or switches Types of Networks Disadvantages Circuit-switched A dedicated connection that has no transmission means wasted bandwidth A connection is time consuming if short, infrequent, or sporadic communication is to occur Packet-switched Forwarding each packet means that each router must decide the next hop for every packet (even for the same destination) Routers are typically network slowdowns due to the amount of processing, as well as input/output buffering Types of Networks Circuit-switching is used in a telephone conversation A connection to the receiver is established by the sender (the caller) The telephone company reserves a certain bandwidth (64 Kbps for voice communication) for this call If the bandwidth is not used by the callers, it is wasted Packet-switching is similar to the postal service Each message (envelope) is addressed to the recipient individually, and the postal service delivers each message to the recipient The postal service may deliver these envelopes through different cities and methods of transport (airplane, truck, …) It can be said that these messages can be delivered using different routes Circuit-Switching A TalkB Call: Telephone Company Switching System Talk Disconnect B Circuit-Switching A Telephone Company Switching System B Packet-Switching A Quebec, QC Buffalo, NY Montreal, QC Windsor, ON Toronto, ON Niagara Falls, ON London, ON Ottawa, ON Kitchener, ON Postal Network B Types of Packet-Switching Virtual circuit-switching A ‘virtual circuit’ is created between source and destination This VC is used for all subsequent sending of packets Datagram Each packet is routed individually Virtual Circuit Packet-Switching Advantages After the first message, routing is faster Because a connection is created, the connection identifier can be used (alone) to address packets A route must only be determined once, for the first message Once the route has been determined, the path used by the router is reused for all messages As a result, routing tables are much smaller (and can be searched more quickly) Typically, such as with ATM cells, this can reduce the size of a cell/packet’s header Messages do not arrive out of order As a result, receivers do not need to reorder the cells Virtual Circuit Packet-Switching Disadvantages Connections take some time to create Infrequent messaging is not suitable for connection-based messaging Routers/switches must intercommunicate in order to create the connection The connection may be lost after a timeout, and will have to be recreated again and again The time delay for creating the connection may outweigh the speed benefits of using connection-based transport Routing tables will be dynamic, and routing algorithms are more complex Datagram Packet-Switching Advantages Connections need not be created Infrequent messaging is perfect for connectionless messaging Connectionless messaging can be resumed after any amount of delay, any number of times, without any delays due to the resumption of communication Routing each message separately allows for load balancing Some messages may be sent through one route, but when that route becomes saturated, messages may then be sent through a different route in order to achieve the most optimal communication possible Datagram Packet-Switching Disadvantages Each message takes a certain amount of time to transmit (including transmission, routing, reception, etc.) Nodes communicating large amounts of information in a short time will: Use a lot of bandwidth for things such as header information Waste a lot of time routing messages to the same destination Messages may arrive out of order Messages must be reordered by the recipient Multiple Access Strategies Schemes for Sharing a Communication Medium Multiple Access Most networks are shared medium This means that a single medium (e.g. radio frequency) is shared by all of a network’s hosts We need a scheme to allow the hosts to share the medium, without collisions Collisions occur when two (or more) messages are transmitted at the same time The result is constructive and destructive interference in the carrier wave This causes the messages to be combined and scrambled Contention In contention networks, any node that has a packet to send, merely sends the packet It is clear that this type of network frequently experiences collisions The more nodes trying to communicate, the higher the chance of collisions Thus, contention networks are severely limited in the number of hosts possible Contention Transmit Contention Contention Transmit Contention Contention: Collisions Transmit Transmit Contention: Collisions Scrambled Signal Contention No collision avoidance is present Messages are just sent When collisions occur, the messages are simply resent after some random (or pseudo-random) amount of time Collisions can occur anytime Carrier Sensing Test the medium for a signal Carrier Sensing Test the medium for a signal: Available Transmit Carrier Sensing Test the medium for a signal Carrier Sensing Test the medium for a signal: In use Carrier Sensing Transmission Complete Carrier Sensing Test the medium for a signal Carrier Sensing Test the medium for a signal: Available Carrier Sensing: Collisions Test the medium for a signal: Available Test the medium for a signal: Available Carrier Sensing: Collisions Transmit Transmit Carrier Sensing: Collisions Scrambled data Carrier Sensing: Collisions Detect Transmit collision Detect Transmit collision Carrier Sensing (CSMA) 1 To reduce the number of collisions, the medium is tested for a signal before each transmission Collisions can still occur (although less often) If a signal exists, the node waits Signal testing can be anything from detection of an electrical signal, to testing for photons 1 If a node tests for a signal before a transmission from another node, and transmits after, a collision occurs CSMA/CA is short for: Carrier Sense Multiple Access with Collision Avoidance Carrier Sensing Hardware Transmitter When a signal is detected, transmissions are blocked by the signal detector Receiver Signal Detector If the message is broadcast or the address is this station’s address, the message is forwarded to the receiver CSMA/CA CSMA/CA networks (such as wireless 802.11g) also use carrier sensing and collision detect However, detecting collisions in wireless networks is significantly more complicated Also, after detecting carrier and determining there is no signal, a CSMA/CA network transmits a ‘Do not broadcast’ message If this message is sent without a collision, the host can assume it is safe to transmit Carrier Sensing Networks Advantages No tokens Simple hardware No need for token transmission Disadvantages Collisions Wasted bandwidth for re-transmits Require complicated re-collision avoidance schemes Token Passing Transmit T Token Passing Transfer Token T Token Passing T Token Passing Transmit T Token Passing A small packet (the token) is passed from node to node When a node has the token, it has sole use of the network medium There are no collisions The nodes must have the token in order to transmit The network hardware ensures that there is only one token at any given time Token-Based Networks Advantages No collisions, so no bandwidth is wasted by collisions and re-transmits No need for re-collision avoidance schemes Disadvantages Token transmission uses bandwidth More complicated hardware Hardware must be built to use tokens, dynamically determine token sequence, etc. Local Area Networks Networks which span a small geographic area They typically represent high bandwidth, short delays, few errors They commonly support features such as broadcasting, multicasting They are typically limited to hundreds of network nodes (maximum) Typical Local Area Networks A collection of computers in the same room e.g. The basement of the computer centre All computers within an office building e.g. The computers in the offices of the professors and staff in Lambton tower Local Area Network Topologies Structures of LANs Token Bus Networks The token is passed in a specific sequence Nodes must know the address if the next node in the sequence The token sequence is not necessarily in the same order as the physical order of nodes on the communication medium When a node has completed transmission, it forwards the token, addressed to the next node in the token sequence The token sequence forms a ‘logical ring’ Common Token Bus Networks IEEE 802.4 networks Nodes are share a communication medium similar to that of Ethernet (IEEE 802.3) Coaxial cable connection Token Bus Operation Transmit A C B Token sequence: C,A,D,B D Token Bus Operation Transmit Token A C B Token sequence: C,A,D,B D Token Bus Operation Receive Token A C B Token sequence: C,A,D,B D Token Bus Operation Transmit A C B Token sequence: C,A,D,B D Token Bus Operation Transmit Token A C B Token sequence: C,A,D,B D Token Bus Operation A C B D Receive Token Token sequence: C,A,D,B Token Bus Operation A C B D Transmit Token sequence: C,A,D,B Token Ring Networks The token is passed to each node, in the physical order on the network The physical medium must be a closed loop to meet this network category So the token can keep going around the network Common Token Ring Networks IEEE 802.5 networks FDDI networks (fibre distributed data interface) Nodes are share a coaxial communication medium similar to that of Ethernet (IEEE 802.3) Nodes use 2 fibre optic rings as the communication medium CDDI networks (copper dist. data interface) Based on FDDI technology, but uses copper wiring similar to 802.4 However, CDDI uses 2 rings like FDDI Token Ring Operation A Transmit D B C Token Ring Operation A Transmit Token D B C Token Ring Operation A D B C Receive Token Token Ring Operation A D B C Transmit Token Ring Operation A D B C Transmit Token Token Ring Operation A D B Receive Token C Token Ring Operation A D B C Transmit Bus and Ring Networks Advantages Less wiring is necessary Disadvantages Node failure can mean partial (or complete) LAN failure This can mean locating network problems is also more difficult Star Topology Star networks send all messages through a central hub Each node on the network is wired separately to the hub Star networks are not a shared bus technology, but a private bus technology However, nodes still share the hub Common Star Networks Twisted pair Ethernet (logical star): All nodes connect to a central hub (an Ethernet hub) via Cat5 cables The hub forwards messages to all wires, and the destination node keeps the message Other nodes ignore the message An Ethernet switch (similar to an ATM switch) forwards only in the one correct direction (or not, if appropriate) Star Network Operation Transmit A B Hub C D Star Network Operation A B Hub C D Receive Star Network Operation Transmit A B Hub C D Star Network Operation A B Hub C Receive D Twisted Pair Ethernet Physically, all Ethernet types are bus networks However, the actual layout of the cables in twisted pair Ethernet forms a star topology Twisted pair is called a logical star topology, while still a physical bus topology Twisted Pair Ethernet as a Bus Short Shared Bus A B C D G H Hub E F Long Private Lines Traditional Ethernet as a Bus Long Shared Bus A B C D E F G H Short Private Lines Star Topology Advantages Simple installation and wiring Node failures do not affect the rest of the system Disadvantages All traffic passes through same hub, so network bandwidth is limited by hub speed This can be reduced with buffers inside hubs which store messages that come in when the hub is busy Hub failure = LAN failure More wiring Duplication of messages LAN Service Models In general, most LANs implement (in some sense) the OSI reference model The IEEE committee on LAN technology (IEEE 802) chose to subdivide the Data Link Layer into 2 sub-layers: 1. MAC (Medium Access Control): Deals with issues specific to each type of LAN 2. Such as token passing, collision detection, error detection, etc. LLC (Logical Link Control): Deals with issues common to all LAN types Such as data transmission, etc. Data Link Addressing The data link layer is represents the network Addressing, then, is specific to the network hardware e.g. Ethernet MAC addresses are typically used for this purpose These addresses are not used in routing They are only used on a single network Thus, they are used for hop to hop delivery End-to-end delivery is the domain of the Network layer MAC Addresses Officially the IEEE 802 committee standardized addresses to be 16bit, 48bit, and even 60bit 48bit addresses (in use by most LANs covered by the 802 committee) allow for globally unique identifiers (GUIDs) to be assigned to each network card by the manufacturer As a result, each NIC can be uniquely identified on any network These are called MAC addresses, due to the Data Link sub-layer that deals with them e.g. 8D-F0-A6-75-9C-13 Data Link Flow Control Flow control is limiting the packet rate so that both the source or destination can keep up At the data link layer, source and destination are on the same LAN Thus, limiting the packet rate is relatively easy Data Link Reliability Reliability: Best effort: The network takes no steps to ensure packets arrive Reliable: The network uses acknowledgements to ensure packets arrive The majority of packets should be received without problems When packets are lost (for whatever reason), they are handled appropriately Error handling: Corrupt packets should be re-sent Reliability at the Data Link layer is usually unnecessary, since the Transport layer will typically be able to do it more efficiently Error Control Error control is achieved using one of the following methods: Checksum: An n-bit sum is taken of the binary stream In other words, a checksum counts the ones What if one 0 became a 1 and a 1 became a 0?? Cyclical redundancy check: Should generate different CRC values, despite the same number of 0s and 1s Ethernet An Early Incarnation of LANs What Started It All Robert Metcalfe (from Xerox PARC) Ethernet History In 1973, Xerox PARC developed a packet-switched LAN, called Ethernet In 1978, IEEE created a standard (802.3) based on the research of Xerox, Intel, and DEC IEEE: Institute of Electrical and Electronics Engineers 802.3 Ethernet uses a coaxial cable to connect nodes (called 10Base5 or ThickNet) Since then, several new forms of Ethernet have evolved ThickNet (10Base5) Outer Insulating Jacket Inner Insulating Layer Braided Metal Shield (Ground) Transmission Wire ½ Inch Diameter 10Base5 5 => 0.5” ThickNet (10Base5) 10Base5 10 => 10 Mbps •Each network node uses a transceiver •A transceiver ‘taps’ into the wire through holes •Maximum throughput is 10 million bits per second (10 Mbps) Transceiver ThinNet (10Base2) Create as an inexpensive alternative to ThickNet (or 10Base2) Called thin-wire Ethernet, because it uses a thin cable with less shielding Less shielding means more interference, so cable placement is important 10Base2 does not use transceivers, which are expensive, which further reduces cost ThinNet (10Base2) Node A Node B 10Base2 10 => 10 Mbps Node C 10Base2 2 => 0.2” Node D •The signal passes through each node •The network interface card (NIC) retransmits the signal, so transceivers are not required •Maximum throughput is 10 million bits per second (10 Mbps) Twisted Pair Ethernet (10BaseT) Uses 4 pairs of twisted wires inside an unshielded cable The twisting of the wires reduces interference The absence of shielding makes the cable flexible and inexpensive The cable is capable of 10Mbps Twisted Pair Ethernet Connectors on twisted pair Ethernet (RJ45) look similar to telephone wire connectors (RJ11) This kind of Ethernet uses unshielded twisted pair (UTP) UTP cable has various categories: Cat3: Can only be used for 10BaseT Cat5: Can be used for 10BaseT, 100BaseT Cat5e, Cat6: Can be used for up to 1000BaseT ThinNet Ethernet 011100110 011100110 Twisted Pair Ethernet accept message 011100110 ignore ignore ignore 10 Mbps Ethernet Overview 10Base2 and 10Base5 both used coaxial cable which joined each node in a line 10BaseT uses UTP cabling, where each node is directly connected with the hub The hub receives messages and forwards them to all nodes The one that is connected to the recipient node Fast Ethernet Using the same Cat5 cabling used for 10BaseT, an Ethernet-based LAN that operates at 100 Mbps (100BaseT) is possible Standard: IEEE 802.3u While using the same cable, network hubs and network interface cards (NICs) must be upgraded to transmit messages at 100 Mbps Fast Ethernet While very few computers can handle 100 Mbps throughput (bus speeds of computers are often slower than this), multiple computers can share this bandwidth 10/100 Ethernet (or 10/100 switched Ethernet) allows you to use the same NICs and hubs for both 10BaseT and 100BaseT If a NIC and hub can both handle 100BaseT, that speed is used, otherwise 10BaseT is used 10/100 Ethernet allows you to slowly upgrade your network with minimal downtime Gigabit Ethernet Gigabit Ethernet allows for 1000 Mbps throughput Gigabit Ethernet (Gig-E) can use Cat5 cabling (1000BaseT) or shielded Cat5E cabling (1000BaseTX) Standard: IEEE 802.3ab Gig-E pushes the limits of the speed capable with Cat5 cabling, due to interference with the electrical signal, Cat5E cabling results in better performance Gigabit Ethernet is so fast, that it is sometimes used as a backbone for a Wide Area Network (WAN) instead of more expensive optical networks e.g. One of the backbones of the network here at the U Ethernet Future Another form of Gigabit Ethernet which uses fibre optic cabling has been proposed (802.3z) Using multimode (multiple channel – 1000BaseSX), or single mode (1000BaseLH, 1000BaseZX) Research groups are in the process of developing 10 Gigabit Ethernet (802.3ae) This research is managed by the 10 Gigabit Ethernet Alliance http://www.10gea.org LAN Service Models LLC (Logical Link Control), for LANs, can be one of two types: Type 1: A straight datagram scheme The packet is delivered using best-effort service No acknowledgements are used to ensure packet arrival Type 2: A reliable scheme Packets are numbered Packets are acknowledged as they are received IEEE 802 Committees Five 802 committees were developed to research various technologies associated with LANs: 802.1: Issues common to all LANs 802.2: Issues related to the LLC sub-layer e.g. reliability schemes, packet transmission 802.3: Issues related to CSMA/CD category LANs e.g. addressing, management, bridges e.g. Ethernet 802.4: Issues related to token bus category LANs 802.5: Issues related to token ring category LANs LAN Addresses The 48 bit addresses (often called MAC addresses) are the ones used by Ethernet LANs e.g. 02-60-8C-08-E1-0C All Ethernet cards contain a globally unique MAC address Ethernet Overview Ethernet is not a reliable service Most Ethernet networks use broadcasting to achieve messaging There are no acknowledgements for packet receipt Ethernet uses best-effort delivery Each message is received by each node Ethernet is one network in a category of networks known as shared bus networks Each node shares a single communication medium Ethernet Overview Ethernet is a carrier-sensing network Carrier-sensing networks use distributed access control methods Each station determines whether it can access the communication medium Each station senses whether or not the transmission medium (wire) is charged If not, an attempt at transmission is made If so, the node will wait and sense again Ethernet Overview Sometimes, more than one station will attempt to transmit at roughly the same time This is called a collision Due to the finite speed of electrons traversing a wire Or due to the finite speed of photons moving through glass 70% of the speed of light The speed of light The two (or more) messages collide or interfere with one another, creating scrambled data packets Collision Detection in Ethernet When scrambled messages are read by the transmitting stations, it is determined to be a collision Both (or all) of the stations involved will detect the collision This type of network is known as CSMA/CD Carrier-sensing, multiple access with collision detection Each station must retransmit their packets Collision Avoidance in Ethernet After a collision occurs, if both stations tried to transmit after the same period of time, another collision would occur To combat this, Ethernet uses a binary exponential back-off policy Each subsequent collision would cause the station to wait double the amount of time before reattempting transmission Ethernet Packets (Frames) Size: 64 octets – 1518 octets An octet is another term for an 8-bit byte The frame contains more than just data The source and destination addresses An identifier, signifying that the frame is in fact an Ethernet frame A Cyclical Redundancy Check (CRC) to ensure data integrity upon arrival Ethernet Frames 8 octets Preamble 6 octets Dest Address 6 octets Source Address 2 octets Frame Type 46-1500 Data 4 octets CRC Sequence of 01010101 used to synchronize the receiving station The MAC address of the destination node The MAC address of the sender node The identifier used to identify the frame as an Ethernet frame The data to be sent to the destination A cyclical redundancy check (CRC) used to determine if data has been corrupted Ethernet Distance Limitations Coaxial Ethernet cables have a maximum length Due to signal deterioration This length could be extended using repeaters Machines that read signals through a port and recreate them (at full strength) out another port The use of more than 2 repeaters between any 2 stations would interfere with times used in CSMA/CD schemes As a result, a maximum of 2 repeaters can be placed between any 2 nodes Ethernet Distance Limitations Ethernet LAN sizes could also be increased by using Bridges to connect separate LANs into a single LAN Bridges filter out erroneous frames, as well as line noise Some bridges (adaptive bridges) are even intelligent enough to know when a frame must be forwarded or not e.g. If the destination node is not on the other side of a Bridge, the frame need not be forwarded FDDI Fiber Distributed Data Interconnect FDDI Use optical fibre cabling as a shared communication medium Optical fibre cables are made of glass Because they are so thin, they are fairly flexible Capable of 100 Mbps Light is used to transmit data Light is not susceptible to electrical interference Optical cabling can span longer distances Optical cabling does not need to be shielded near devices which generate electromagnetic interference Light waves (photons) travel faster than electrons FDDI Is a token-ring category network A token is passed from station to station When a station receives the token, it may transmit data If a station has no data, it allows the token to pass to the next station FDDI uses 2 rings of cabling, moving in opposite directions The second ring is used to allow twice the flow of data The purpose of the second ring is to allow data to reach its destination, even when one station has failed (and cannot forward messages) FDDI Ring Technology FDDI With Node Failure FDDI Token Passing S:12 D:07 T 12 1 S:12 D:07 S:12 D:07 2 S:12 D:07 S:12 D:07 3 S:12 D:07 S:12 D:07 4 S:12 D:07 S:12 D:07 5 S:12 D:07 S:12 D:07 11 10 9 8 S:12 D:07 6 7 S:12 D:07 S:12 D:07 FDDI Token Passing T T 1 2 3 4 12 5 11 6 10 9 8 7 FDDI Frames octets: 2+ 1 1 2 or 6 2 or 6 0-30 0-4500 4 0.5 1.5+ Preamble Start Delimiter Frame Control Dest Address Source Address Routing Info Data FCS End Delimiter Frame Status Data Used to Synchronize Stations Indicates Start of Frame Identifies the Type of Frame Address of the Destination Node Address of the Source Node Routing Information Frame Data Frame Check Sequence Indicates End of Frame Status of Frame Wireless Networks Radio-Based LANs Wireless LANs Contrary to one’s initial guess, wireless LANs are very similar to ‘wired’ LANs Wireless LANs are a shared media network, just like Ethernet However, in a wireless LAN, the shared medium is not the air, but something called a base station or wireless access point Wireless LANs (WLANs) The wireless access point, which is similar to a hub, is the shared medium Despite the fact that radio waves using the same frequency will cause mutual interference, the air is not generally considered a shared medium Technically speaking, twisted pair Ethernet is similar to WLANs The cables themselves are just point-to-point connectors and are not shared The hub/switch, however, is shared Wireless LANs (WLAN) Wireless Access Point (WAP): A base station that coordinates transmission between one or more wireless hosts Analogous to a cell tower in a mobile phone network Wireless hosts must be a certain distance away from a WAP to participate on a WLAN The communicable area of all of the WAPs in a WLAN, define the coverage area for the WLAN Some WLANs do without a WAP, but pass messages directly to one another These are typically small (2-3 hosts) networks, and are called ad hoc networks 802.11 Operation 802.11 networks (such as 802.11g) use CSMA/CA multiple access scheme Hosts try to detect carrier before sending (CS) This is not adequate, since there could be hidden hosts These are hosts out of range of this host, but in range of the same base station: 802.11 Operation To avoid collisions with hidden hosts: The host will send a ‘request to send’ (RTS) frame before transmitting The base station will respond with a ‘clear to send’ (CTS) frame if the channel is clear Once a base station sends a CTS, it will reject any further RTS requests until the data is received by the host who sent the first RTS This is called collision avoidance (CA) Frames are acknowledged at the data link layer in 802.11 networks 802.11 Frame Format Frame Control (2 octets) Source Address (6) Destination Address (6) Receiving Station Address (6) Sequence Control (2) Transmitting Station Address (6) Data (0-2312) Frame Check Sequence (2) Flags MAC Address of sending host MAC Address of receiving host MAC Address of sender base station Fragment number, sequence number MAC Address of receiver base station Frame data CRC for frame header and data 802.11 Frame Header: Frame Control Protocol Version (2 bits) Type (2) Subtype (4) To AP (1) From AP (1) More Fragments (1) Retry (1) Power Management (1) More Data (1) WEP (1) Order (1) Flags Management, control or data frame Type of management or control frame Sent to an access point? Sent by an access point? Are there more fragments from this frame? Is this a retransmission of a previous frame? Power state of sender after transmission Is there more data to come? Has WEP encryption been applied to frame? Are the packets strictly ordered? Wireless Access Points WAP2 WAP1 WAP3 Ad Hoc Networks In ad hoc networks, stations directly transmit to one another Hosts are responsible for routing, addressing, name translation, security, etc. Two ad hoc networks using the same frequency, within range of one another will cause conflicts Thus, different frequencies should be used Handoffs in WAPs For WLANs with WAPs, roaming hosts must be considered If a host moves into the range of another WAP, then out of range of their current WAP, a handoff takes place A handoff is when one WAP gives the responsibility for a particular host to one of its neighbouring WAPs The two WAPs must communicate for this to happen, and thus neighbouring WAPs must be within each other’s transmission range Wireless LAN Standards Some of the main standardized WLANs: 802.11a, 802.11g: 54Mbps, comparable with 100BaseT Ethernet, under 100M range 802.11b: 11Mbps, comparable to 10BaseT Ethernet, under 100M range These technologies are intended for LANs within the same small to medium-sized building BlueTooth/802.15: 721 kbps, under 10M range This technology is intended for communicate within one room or vehicle