* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Overview of Business Processes
Survey
Document related concepts
Transcript
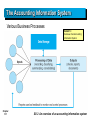
Prepared by Coby Harmon University of California, Santa Barbara Westmont College Chapter 1-1 Introduction to AIS Chapter 1-2 Accounting Information Systems, 2nd Edition Study Objectives 1. An overview of business processes 2. An overview of an accounting information system 3. The business process linkage throughout the supply chain 4. The IT enablement of business processes 5. Basic computer and IT concepts 6. Examples of IT enablement 7. The internal control structure of organizations 8. The importance of accounting information systems to accountants 9. Chapter 1-3 The relation of ethics to accounting information systems Overview of Business Processes Accounting Information System must identify the Chapter 1-4 ► Transactions to record, ► Capture all details, ► Properly process into correct accounts, and ► Provide reports externally and internally. SO 1 An overview of business processes Overview of Business Processes Business Process - a sequence of work steps performed in order to produce a desired result. Examples: Chapter 1-5 ► Completing a sale ► Purchasing raw materials ► Paying employees ► Paying vendors SO 1 An overview of business processes Overview of Business Processes Four general types of business processes: 1. Revenue Processes (Chapters 8) a. Sales b. Sales return c. Cash collection Chapter 1-6 SO 1 An overview of business processes Overview of Business Processes Four general types of business processes: 2. Expenditure Processes (Chapters 9 and 10) a. Purchase b. Purchase return c. Cash disbursement d. Payroll e. Fixed asset Chapter 1-7 SO 1 An overview of business processes Overview of Business Processes Four general types of business processes: 3. Conversion Processes (Chapter 11) a. Planning b. Resource management c. Logistics 4. Administrative Processes (Chapter 12) a. Capital b. Investment c. General ledger Chapter 1-8 SO 1 An overview of business processes Overview of Business Processes Internal controls are the set of procedures and policies adopted to: 1. safeguard assets, 2. check accuracy and reliability of data, 3. promote operational efficiency, and 4. encourage adherence to prescribed managerial practices. Chapter 1-9 SO 1 An overview of business processes Overview of Business Processes Review Question When a customer returns goods that were purchased, the business process to accept the return would most likely be a(n) a. administrative process b. conversion process c. expenditure process d. revenue process Chapter 1-10 Advance slide in presentation mode to reveal answer. 1. Revenue Processes a. Sales b. Sales return c. Cash collection SO 1 An overview of business processes The Accounting Information System Various Business Processes Exhibit 1-1 Overview of an Accounting Information System Chapter 1-11 SO 2 An overview of an accounting information system The Accounting Information System Review Question Which of the following is least likely to be an output of the accounting information system? a. a check b. a report c. an invoice d. a bar code Chapter 1-12 A bar code is usually an input to the accounting information system. SO 2 An overview of an accounting information system Process Throughout the Supply Chain Supply Chain - processes and information flows that involve the movement of materials, funds, and related information through the full logistics process, from the acquisition of raw materials to the delivery of finished products to the end user. The supply chain includes all: Chapter 1-13 ► Vendors ► Customers ► Service providers ► Intermediaries SO 3 The business process linkage throughout the supply chain Process Throughout the Supply Chain Supply Chain Management - the organization and control of all materials, funds, and related information in the logistics process, from the acquisition of raw materials to the delivery of finished products to the end user (customer). Chapter 1-14 SO 3 The business process linkage throughout the supply chain Process Throughout the Supply Chain A simplified Supply Chain for McDonald’s Chapter 1-15 Exhibit 1-2 A Simplified Supply Chain for McDonald’s SO 3 The business process linkage throughout the supply chain The Real World An organization such as McDonald’s must have many different suppliers of the same product because of the need for fresh ingredients. For example, the regional bakery in the next exhibit provides buns for McDonald’s in a five-state area. As you have traveled, you may have noticed that your Big Mac is always the same, no matter where you go. Even the buns are exactly the same in each town and city. McDonald’s plans for this uniformity in buns and must have many suppliers throughout the world that can make and deliver a consistent quality bun. East Balt Inc. is one of the large bakeries that supplies McDonald’s with buns. East Balt bakeries make these buns according to strict standards of size, shape, color, height, and seed coverage. To maintain freshness, the buns have to be baked in regional locations. It would be much too difficult to have one central location bake all buns for McDonald’s. Therefore, McDonald’s must have many different suppliers of buns throughout the world. Chapter 1-16 SO 3 The business process linkage throughout the supply chain Process Throughout the Supply Chain Review Question Which of the following is not true of the supply chain? a. The supply chain includes vendors. b. The supply chain excludes customers. c. The supply chain includes information flows. d. The supply chain includes secondary suppliers. Chapter 1-17 SO 3 The business process linkage throughout the supply chain IT Enablement of Business Processes Information Technology - Computers, ancillary equipment, software, services, and related resources as applied to support business processes. IT Enablement - Using IT systems to enhance efficiency and effectiveness of internal or supply chain processes. Chapter 1-18 SO 4 The IT enablement of business processes IT Enablement of Processes and the AIS IT usage accomplishes one or more of the following objectives: 1. Increased efficiency of business processes 2. Reduced cost of business processes 3. Increased accuracy of the data related to business processes Business Process Reengineering (BPR) is the purposeful and organized changing of business processes to make them more efficient. Chapter 1-19 SO 4 The IT enablement of business processes Process Throughout the Supply Chain Review Question Which of the following is not an objective of IT enablement? a. increased accuracy of data b. reduced cost c. reduced security problems d. increased efficiency Chapter 1-20 SO 4 The IT enablement of business processes Basic Computer and IT Concepts Basic Computer Data Structures Data hierarchy: 1. Bit, or binary digit 2. Byte 3. Field 4. Record 5. File 6. Database ► Smallest unit ► Values = zero or one ► One character ► Eight bits ► One item within record ► Example - last name ► Set of related fields ► Example – employee #, name, pay rate, etc. ► Set of related records ► Entire collection of files Chapter 1-21 SO 5 Basic computer and IT concepts Process Throughout the Supply Chain Review Question The correct order of the computer data hierarchy is a. byte, bit, record, field, file, database b. bit, byte, record, field, file, database c. bit, byte, field, record, file, database d. bit, byte, field, record, database, file Chapter 1-22 SO 5 Basic computer and IT concepts Basic Computer and IT Concepts Relational Database Chapter 1-23 Example - relationship in data of a customer having more than one order. Master File Example - payroll master file maintains the relatively permanent data to process payroll transactions. Transaction File Example - transaction file is processed against the master file, and year-to-date balances are updated in the master file. SO 5 Basic computer and IT concepts Basic Computer and IT Concepts File Access and Processing Modes ► Sequential access ► Random access ► Indexed Sequential Access Method (ISAM) ► Batch processing ► Online processing ► Real-time processing Chapter 1-24 SO 5 Basic computer and IT concepts Basic Computer and IT Concepts Data Warehouse and Data Mining ► Data warehouse ► Operational database ► Data mining Chapter 1-25 SO 5 Basic computer and IT concepts Process Throughout the Supply Chain Review Question The process of searching for identifiable patterns in data is called a. Sequential processing b. data warehousing c. data mining d. real-time processing Chapter 1-26 SO 5 Basic computer and IT concepts Basic Computer and IT Concepts Networks and the Internet Network (two or more computers linked together) Types important to accounting: ► Local Area Network (LAN) ► Internet ► Intranet ► Extranet Chapter 1-27 SO 5 Basic computer and IT concepts The Real World The American Institute of Certified Public Accountants recently released the results of its 2012 Top Technology Initiatives Survey. The survey asked respondents to rank their organization’s top IT goals for the coming year. The top five responses were: 1. Securing the IT environment 2. Managing and retaining data 3. Managing risks and compliance 4. Ensuring privacy 5. Leveraging new technologies (such as cloud computing and mobile devices) These findings clearly indicate that the ability to access key information is a top priority for accountants. However, changing technologies tend to cause accountants to rethink the way they work. The more that can be learned about the capabilities of emerging technologies, the more likely it is that they will be appropriately integrated into the IT environment to produce an improved result. Complete survey results are available at aicpa.org/toptech. Chapter 1-28 Examples of IT Enablement E-Business Encompasses all forms of: ► Online electronic trading ► Consumer-based e-commerce ► Business-to-business transactions ► Internal use of IT Examples, buying: a book at Amazon.com clothes at Landsend.com Chapter 1-29 SO 6 Examples of IT enablement Examples of IT Enablement Electronic Data Interchange (EDI) The intercompany, computer-to-computer transfer of business documents in a standard business format. Example: Transmit purchase orders, invoices, and payments electronically between trading partners. Chapter 1-30 SO 6 Examples of IT enablement Examples of IT Enablement Point of Sale System A system of hardware and software that captures retail sales transactions by standard bar coding. Example: Customer checks out through the cash register, bar codes are scanned on the items purchased, prices are determined by access to inventory and price list data, sales revenue is recorded, and inventory values are updated. Chapter 1-31 SO 6 Examples of IT enablement Examples of IT Enablement Automated Matching A computer system in which the software matches an invoice to its related purchase order and receiving report. Example: Ford Motor Company described in text illustrated an automated matching system. Chapter 1-32 SO 6 Examples of IT enablement Examples of IT Enablement Evaluated Receipt Settlement (ERS) An invoice-less system in which computer software completes an invoice-less match that is a comparison of the purchase order with the goods received. E-Payables and Electronic Invoice Presentment and Payment (EIPP) Web-enabled receipt and payment of vendor invoices. Chapter 1-33 SO 6 Examples of IT enablement Examples of IT Enablement Enterprise Resource Planning Systems (ERP) Multi-module software system designed to manage all aspects of an enterprise. Usually broken down into modules such as Chapter 1-34 ► financials, ► inventory management, ► sales, ► manufacturing, and ► purchasing, ► human resources. SO 6 Examples of IT enablement Process Throughout the Supply Chain Review Question An IT enabled system for purchasing that is an “invoiceless” system is called a(n) a. automated matching system b. evaluated receipt settlement c. e-payables d. point of sale system Chapter 1-35 SO 6 Examples of IT enablement Internal Control Structure of Organizations Risks that impact financial standing: 1. Assets will be stolen or misused 2. Errors in accounting data or information 3. Fraudulent activity 4. Risks inherent in IT systems, such as a. Erroneous input of data d. Erroneous input of data b. Erroneous processing of e. Hardware or software failure data f. Natural disasters c. Chapter 1-36 Computer fraud SO 7 The internal control structure of organizations Internal Control Structure of Organizations Enterprise Risk Management (ERM) ERM is defined as . . . a process, effected by an entity’s board of directors, management and other personnel, applied in strategy setting and across the enterprise, designed to identify potential events that may affect the entity, and manage risk to be within its risk appetite, to provide reasonable assurance regarding the achievement of entity objectives. Chapter 1-37 SO 7 The internal control structure of organizations Internal Control Structure of Organizations Enterprise Risk Management (ERM) Requires management set policies and procedures related to: Chapter 1-38 ► Internal Environment ► Risk Response ► Objective Setting ► Control Activities ► Event Identification ► Information and Communication ► Risk Assessment ► Monitoring SO 7 The internal control structure of organizations Internal Control Structure of Organizations Enterprise Risk Management (ERM) Management should ensure the following types of control structures exist: 1. Code of Ethics (Chapter 3) 2. COSO Accounting Internal Control Structure (Chapter 3) 3. IT Controls (Chapter 4) 4. Corporate Governance (Chapter 5) 5. IT Governance (Chapter 6) Chapter 1-39 SO 7 The internal control structure of organizations Internal Control Structure of Organizations Review Question The COSO report written for the purpose of assisting managers in the challenge of managing risk in their organizations is entitled a. “Internal Controls—Integrated Framework” b. “Enterprise Risk Management—Integrated Framework” c. “Corporate Governance” d. “IT Governance” Chapter 1-40 Advance slide in presentation mode to reveal answer. SO 7 The internal control structure of organizations The Real World On April 20, 2010, an explosion aboard the Deep Water Horizon drilling platform forced millions of gallons of oil to spill into the Gulf of Mexico, wreaking havoc on marine life and upsetting the coastal economies. This event and the related problems have been disastrous for BP plc, the company most frequently blamed for this tragedy. This example illustrates how critical it is for companies to manage risks. Risks lie in nearly every aspect of every business, and the task of identifying and mitigating them is a daily challenge. Certainly, any oil company would include an explosion, oil spill or oil leak to be among its most serious risks. In the case of BP and the other responsible companies, there were evidently breakdowns in the monitoring of controls surrounding this location. Although many people are familiar with the BP oil spill, most have probably never considered the accounting implications of this disaster. Yet years after its occurrence, BP was still struggling to account for the damages owed for environmental clean-up and legal claims, and its audit firm was still using cautionary language in the audit opinion accompanying BP’s financial statements. Chapter 1-41 Importance of AIS to Accountants Accountants may be ► Users of the AIS, ► Part of the design or implementation team of an AIS, and/or ► Auditors of an AIS. Chapter 1-42 SO 8 The importance of accounting information systems to accountants Importance of AIS to Accountants Review Question Accountants have some form of use of the AIS in all but which role? a. user b. programmer c. auditor d. designer Chapter 1-43 SO 8 The importance of accounting information systems to accountants Relation of Ethics to AIS Examples of potential unethical behaviors: ► Fraudulent financial reporting ► Revenue inflation ► Expense account fraud ► Inflating hours worked for payroll purposes ► Computer fraud ► Hacking ► Browsing confidential data Chapter 1-44 SO 9 The relation of ethics to accounting information systems Ethics and the AIS Review Question Which of the following is not true of unethical behavior? a. The only category of unethical behavior for accountants is inflating revenue. b. Accountants are often pressured to help commit or cover up unethical behavior. c. Hacking is an unethical behavior that accountants should be concerned about. d. An accounting information system can be used to cover up unethical behavior. Chapter 1-45 SO 9 The relation of ethics to accounting information systems Copyright Copyright © 2013 John Wiley & Sons, Inc. All rights reserved. Reproduction or translation of this work beyond that permitted in Section 117 of the 1976 United States Copyright Act without the express written permission of the copyright owner is unlawful. Request for further information should be addressed to the Permissions Department, John Wiley & Sons, Inc. The purchaser may make back-up copies for his/her own use only and not for distribution or resale. The Publisher assumes no responsibility for errors, omissions, or damages, caused by the use of these programs or from the use of the information contained herein. Chapter 1-46