* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Corporate Overview - Network Instruments
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Computer network wikipedia , lookup
Deep packet inspection wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Wake-on-LAN wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Wireless security wikipedia , lookup
Network tap wikipedia , lookup
Airborne Networking wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
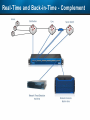
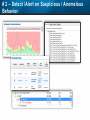
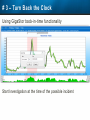
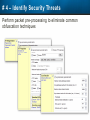
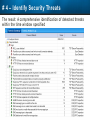
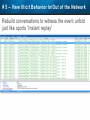
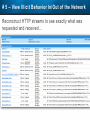
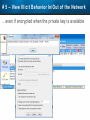
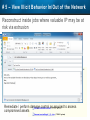
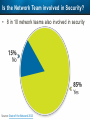
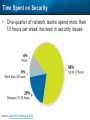
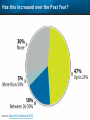
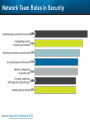
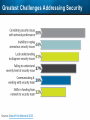
Observer Platform Network Security Forensics Agenda • Introduction o Today’s security challenges o Observer Platform network forensics benefits • Five Steps to Threat Resolution • Real-world customer example o Jack Henry & Associates • Investigating the packets demonstration o #1 – Identify a DDos o #2 – Botnet detection • Key Take-aways Security Challenges • IT threats continue to escalate in frequency, type, and malice o o • Negative financial and stakeholder implications are increasing o o • Revenue, profitability, and customer relations Long-term business survivability at risk Damage control and remediation urgency growing o o • Security perimeter breaches (must be) assumed a given “Inside jobs” are also on the rise What has been compromised? How do we validate “all clear”? Take-Away: Organizations need a retrospective, networkcentric method to backstop other security measures and identify and clean compromised IT assets Security Challenges – A Reality Today for the Network Team • Network Instruments 2015 State of the Network highlights: o o o o • 85% are involved with security investigations Engaged in multiple facets of security • 65% implementing preventative measures • 58% investigating attacks • 50% validating security tool configurations 50% indicated correlating security issues with network performance to be their top challenge 44% cited the inability to replay anomalous security issues Hacking and malware cause nearly 1/3 of all data loss events* * VERIS Community Database Our Benefits • Leverage Observer Platform performance monitoring functionality to bolster existing IT security measures o “ Two-for-one” deal (NPMD + security) • GigaStor offers back-in-time peace of mind o • Apex provides high-level views into possible errant behavior o • The “gold standard” in packet capture ensures every packet is captured No network conversations are missed Baseline graphs are a powerful means to visualize unusually activity Analyzer includes deep packet awareness • Integrated SNORT rule support for known malware • Sophisticated post-event filtering and pre-packet processing to quickly detect zero-day or other suspicious activity • Advanced alarming to alert on targeted conditions Real-Time and Back-in-Time - Complement Riverbed & NetScout • Don't offer Snort rule support • Cannot match our storage capacity • Drop packets as utilization rates increase • NetScout does offer Cyber Investigator o Dedicated hardened solution OBSERVER PLATFORM SECURITY FORENSICS Five Steps to Threat Resolution # 1 - Capture Everything on Your Network Never miss a single packet Monitor from the core to the edge # 2 – Detect /Alert on Suspicious / Anomalous Behavior # 3 – Turn Back the Clock Using GigaStor back-in-time functionality Start Investigation at the time of the possible incident # 4 – Identify Security Threats Leverage GigaStor forensics # 4 – Identify Security Threats Leverage GigaStor forensics # 4 – Identify Security Threats Perform packet pre-processing to eliminate common obfuscation techniques # 4 – Identify Security Threats Then apply advanced Analyzer filtering for zero-day events or Snort rules for known threats # 4 – Identify Security Threats The result: A comprehensive identification of detected threats within the time window specified # 5 – View Illicit Behavior In/Out of the Network Rebuild conversations to witness the event unfold just like sports “instant replay” # 5 – View Illicit Behavior In/Out of the Network Rebuild conversations to witness the event unfold just like sports “instant replay” # 5 – View Illicit Behavior In/Out of the Network Reconstruct HTTP streams to see exactly what was requested and received… # 5 – View Illicit Behavior In/Out of the Network …even if encrypted when the private key is available # 5 – View Illicit Behavior In/Out of the Network Reconstruct inside jobs where valuable IP may be at risk via extrusion Remediate / perform damage control as required to assess compromised assets CUSTOMER EXAMPLE JACK HENRY & ASSOCIATES About Jack Henry & Associates (JHA) • S&P 400 company with $1.2 Billion revenue (FY2014) • Support 11,300 financial service customers o Electronic payment solutions o Financial processing services o Business process automation • Three primary brands o Jack Henry Banking, Symitar, and ProfitStars JHA – Protecting Critical Customer Data • Already using Observer Platform to monitor network and app performance • Ongoing targeted attacks on IT resources • GigaStor to the rescue o Fortified existing security efforts by validating attempted breach into data center not successful • Having all the packets critical Solving the Customer’s Challenge • Late night call from the VP of Network Ops. o Oversees the security team • Significant expansion of GigaStor deployments o Now an integral part of ongoing security detection and remediation o Save every packet across seven DCs for two weeks • GigaStor data-at-rest adds more peace-of-mind Business Outcome – Additional Sales • Current (new) sales: o Observer Expert Consoles o Qty.2 – 10 Gb GigaStor-Expandable – 96 TB • Redundant on-shelf for rapid deployment if failure o Qty.2 – 10 Gb GigaStor-Expandable – 288 TB o Qty.1 – 10 Gb GigaStor – Expandable – 576 TB o Four years of maintenance • Future sales upside: o Qty.2 – 10 Gb GigaStor-Expandable – 288 TB o Qty.1 – 10 Gb GigaStor-Expandable – 96 TB o Qty.1 – 10 Gb GigaStor-Upgradeable – 16 TB INVESTIGATING IN THE PACKETS Key Takeaways • The number and severity of the IT security breaches continues to escalate • Network teams are playing an increasingly larger role in security investigations, preventive measures, and damage control • Having all the packets are critical for detecting breaches, identifying compromised assets, and validating cleanup Key Takeaways • Observer Platform offers tremendous value to network teams and security organizations to optimize IT resource health and performance o GigaStor data-at-rest adds even more value • GigaStor (easily) beats NetScout and Riverbed in high-speed packet capture, capacity, and integrated security functionality QUESTIONS? OPTIONAL SLIDES Is the Network Team involved in Security? • 8 in 10 network teams also involved in security Source: State of the Network 2015 Time Spent on Security • One-quarter of network teams spend more than 10 hours per week involved in security issues Source: State of the Network 2015 Has this Increased over the Past Year? Source: State of the Network 2015 Network Team Roles in Security Source: State of the Network 2015 Greatest Challenges Addressing Security Source: State of the Network 2015