* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Introduction to Networking
Computer security wikipedia , lookup
Net neutrality law wikipedia , lookup
Wireless security wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Distributed firewall wikipedia , lookup
Deep packet inspection wikipedia , lookup
Internet protocol suite wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Computer network wikipedia , lookup
Network tap wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
UniPro protocol stack wikipedia , lookup
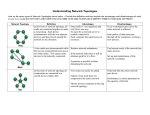
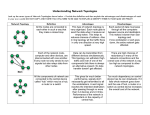
Unit III Data Communication and Networks (ITM) Ashima Wadhwa Assistant Professor (giBS) Overview of Networks Network – two or more computers linked together so they can communicate, share resources and exchange information Networks allow users to: ◦ ◦ ◦ ◦ ◦ ◦ Access shared programs and data Transfer data from one computer to another Share peripheral devices such as printers Share storage devices to store data for backup Use e-mail to communicate with one another Access the Internet Networking Computer network A collection of computing devices that are connected in various ways in order to communicate and share resources Usually, the connections between computers in a network are made using physical wires or cables However, some connections are wireless, using radio waves or infrared signals 153 Networking The generic term node or host refers to any device on a network Data transfer rate The speed with which data is moved from one place on a network to another Data transfer rate is a key issue in computer networks 154 Networking Computer networks have opened up an entire frontier in the world of computing called the client/server model 155 Advantages: › Enable people to work together › Reduce costs from sharing networked hardware and software › Increase productivity by sharing data › Provide access to a wide range of services and specialized peripheral devices Disadvantages › Unavailable resources when network malfunctions › More vulnerable to unauthorized access than stand alone computers › Susceptible to an increased number of worms, Trojan horses, and blended threats Types of Networks LAN WAN Local Area Network (LAN) Network of computers located in a single location, like a home, school, or office building Can share connection with other LANS and with the internet Characteristics of a LAN? Local area network Relatively limited in size Computers connected in small areas Same office True peer-to-peer Can support limited number of nodes Wide Area Network (WAN) Network over a large area like a city, a country, or multiple countries ◦ Connects multiple LANs together Generally utilizes different and much more expensive networking equipment than LANs The internet is the most popular WAN Types of Computer Networks : Wired and Wireless Networks Client / Server And Peer to Peer Networks Wired Network A wired network uses cables to connect network devices Wired networks are fast, secure, and simple to configure Devices tethered to cables have limited mobility Wireless Networking A network is considered wireless when data is transmitted from one device to another without cables or wires Tend to be slower than wired networks Have more security issues Common wireless terms: › Wi-Fi - common standard technology for building home networks and other LANs › Hotspots – many businesses use Wi-Fi technology to allow the public an access point to a wireless network › Bluetooth – allows handhelds, cell phones, and other peripherals to communicate over short ranges Client/Server Network work devices can function as clients or servers Server - computer that performs administration or coordination functions within a network Types: (1)application server, (2) file server, (3) print server Client – regular workstation that performs applications Client / Server Networks Clients ◦ Computers that request or order information from a server ◦ Usually desktop computers with their own local storage and processing power ◦ Thin client – network computer with no local storage Servers ◦ Computers that work behind the scenes to provide (serve) the resources requested by the clients ◦ Two types Non-dedicated – provides many different services to its client computers such as file retrieval, printing, and emailing Dedicated – provides only one type of resource to its clients, such as printing Client/Server Network Peer-to-Peer Network A network of personal computers, each of which acts as both client and sever, so that each can exchange files directly with every other computer on the network Each computer can access any of the others, although access can be restricted to those files that a computer's user chooses to make available Less expensive than client/server networks but less efficient when large amounts of data need to be exchanged Peer-to-peer Topology A Network Topology is the way computer systems or network equipment connected to each other. Topologies may define both physical and logical aspect of the network. Both logical and physical topologies could be same or different in a same network. Topology Common types: ◦ ◦ ◦ ◦ ◦ ◦ Star Ring Bus Tree Mesh(Fully Connected) Hybrid Star Topology All the cables run from the computers to a central location, where they are all connected by a device called a hub. Each computer on a star network communicates with a central hub that resends the message either to all the computers or only to the destination computers. Advantages of Star topology ▸ Due to its centralized nature, the topology offers simplicity of operation. ▸ It also achieves isolation of each device in the network. ▸ Adding or removing network nodes is easy, and can be done without affecting the entire network. ▸ Due to the centralized nature, it is easy to detect faults in the network devices. ▸ As the analysis of traffic is easy, the topology poses lesser security risk. ▸ Data packets do not have to pass through many nodes, like in the case of a ring network. Thus, with the use of a high-capacity central hub, traffic load can be handled at fairly decent speeds. Disadvantages of Star Topology ▸ Network operation depends on the functioning of the central hub. Hence, central hub failure leads to failure of the entire network. ▸ Also, the number of nodes that can be added, depends on the capacity of the central hub. ▸ The setup cost is quite high. Ring Topology Every device has exactly two neighbors for communication purposes All messages travel through a ring in the same direction (either "clockwise" or "counterclockwise“) Advantages of Ring topology ▸ The data being transmitted between two nodes passes through all the intermediate nodes. A central server is not required for the management of this topology. ▸ The traffic is unidirectional and the data transmission is high-speed. ▸ In comparison to a bus, a ring is better at handling load. ▸ The adding or removing of network nodes is easy, as the process requires changing only two connections. ▸ The configuration makes it easy to identify faults in network nodes. ▸ In this topology, each node has the opportunity to transmit data. Thus, it is a very organized network topology. ▸ It is less costly than a star topology. Disadvantages of Ring Topology ▸ The failure of a single node in the network can cause the entire network to fail. ▸ The movement or changes made to network nodes affect the entire network's performance. ▸ Data sent from one node to another has to pass through all the intermediate nodes. This makes the transmission slower in comparison to that in a star topology. The transmission speed drops with an increase in the number of nodes. ▸ There is heavy dependency on the wire connecting the network nodes in the ring. Bus Topology A common backbone (a single cable) to connects all devices and devices attach, or tap into, the cable with an interface connector Devices wanting to communicate with other devices on the network send a broadcast message onto the wire that all other devices see, but only the intended recipient actually accepts and processes the message Advantages of Bus topology ▸ It is easy to set up, handle, and implement. ▸ It is best-suited for small networks. ▸ It costs very less. Disadvantages of Bus Topology ▸ The cable length is limited. This limits the number of network nodes that can be connected. ▸ This network topology can perform well only for a limited number of nodes. When the number of devices connected to the bus increases, the efficiency decreases. ▸ It is suitable for networks with low traffic. High traffic increases load on the bus, and the network efficiency drops. ▸ It is heavily dependent on the central bus. A fault in the bus leads to network failure. ▸ It is not easy to isolate faults in the network nodes. ▸ Each device on the network "sees" all the data being transmitted, thus posing a security risk. Tree Topology Tree Topology integrates the characteristics of Star and Bus Topology. Advantages of Tree topology ▸ The tree topology is useful in cases where a star or bus cannot be implemented individually. It is most-suited in networking multiple departments of a university or corporation, where each unit (star segment) functions separately, and is also connected with the main node (root node). ▸ The advantages of centralization that are achieved in a star topology are inherited by the individual star segments in a tree network. ▸ Each star segment gets a dedicated link from the central bus. Thus, failing of one segment does not affect the rest of the network. ▸ Fault identification is easy. ▸ The network can be expanded by the addition of secondary nodes. Thus, scalability is achieved. Disadvantages of Tree Topology ▸ As multiple segments are connected to a central bus, the network depends heavily on the bus. Its failure affects the entire network. ▸ Owing to its size and complexity, maintenance is not easy and costs are high. Also, configuration is difficult in comparison to that in other topologies. ▸ Though it is scalable, the number of nodes that can be added depends on the capacity of the central bus and on the cable type. Mesh Topology In a mesh network topology, each of the network node, computer and other devices, are interconnected with one another. Advantages of Mesh topology 1) Data can be transmitted from different devices simultaneously. This topology can withstand high traffic. 2) Even if one of the components fails there is always an alternative present. So data transfer doesn’t get affected. 3) Expansion and modification in topology can be done without disrupting other nodes. Disadvantages of Mesh topology 1) There are high chances of redundancy in many of the network connections. 2) Overall cost of this network is way too high as compared to other network topologies. 3) Set-up and maintenance of this topology is very difficult. Even administration of the network is tough. Hybrid Topology Combination of any two or more network topologies › A hybrid topology always accrues when two different basic network topologies are connected Advantages of Hybrid topology One of the prominent advantages of this topology is its flexibility. The topology is designed, so that it can be implemented for a number of different network environment. As compared to most other topologies, this topology is reliable. It has better fault tolerance. Any type of topology can be combined with another without making any changes to the existing topology Disadvantages of Hybrid Topology Since different topologies come together in a hybrid topology, managing the topology becomes difficult. It is also very expensive to maintain. Installation and configuration of the topology is difficult. Communication Main purpose of communication is to transfer information from a source to a recipient via a channel or medium. Basic block diagram of a communication system: Source Transmitter Channel Receiver Recipient Brief Description Source: analog or digital Transmitter: transducer, amplifier, modulator, oscillator, power amp., antenna Channel: e.g. cable, optical fibre, free space Receiver: antenna, amplifier, demodulator, oscillator, power amplifier, transducer Recipient: e.g. person, (loud) speaker, computer Data Communication Channels or Data Transmission Modes : Simplex Half Duplex Full Duplex Data Communication Channels or Data Transmission Modes Simplex ◦ Data in a simplex channel is always one way. Simplex channels are not often used because it is not possible to send back error or control signals to the transmit end. An example of a simplex channel in a computer system is the interface between the keyboard and the computer, in that key codes need only be sent one way from the keyboard to the computer system. Half Duplex ◦ A half duplex channel can send and receive, but not at the same time. Its like a one-lane bridge where two way traffic must give way in order to cross. Only one end transmits at a time, the other end receives. Full Duplex ◦ Data can travel in both directions simultaneously. There is no need to switch from transmit to receive mode like in half duplex. Its like a two lane bridge on a two-lane highway. Analog and digital signals are used to transmit information, usually through electric signals. In both these technologies, the information, such as any audio or video, is transformed into electric signals. The difference between analog and digital technologies is that in analog technology, information is translated into electric pulses of varying amplitude. In digital technology, translation of information is into binary format (zero or one) where each bit is representative of two distinct amplitudes. Comparison chart Analog Analog signal is a continuous signal which represents physical measurements. Denoted by sine waves Uses continuous range of values to represent information Digital Digital signals are discrete time signals generated by digital modulation. Denoted by square waves Protocols Network Protocol Defines rules and conventions for communication between network devices Protocols for computer networking all generally use packet switching techniques to send and receive messages in the form of packets Network protocols include mechanisms for: › Devices to identify and make connections with each other › Formatting rules that specify how data is packaged into messages sent and received › Message acknowledgement › Data compression designed for reliable and/or highperformance network communication Hundreds of different computer network protocols have been developed each designed for specific purposes and environments What is OSI? Developed by the International Organization for Standardization (ISO) in 1984 The primary architectural model for intercomputer communications. A conceptual model composed of seven layers, each specifying particular network functions. Describes how information from a software application in one computer moves through a network medium to a software application in another computer. OSI Lower Layers/OSI Upper Layers Physical 2. Data Link 3. Network 1. Transport 2. Session 3. Presentation 4. Application 1. OSI Physical Layer Responsible for transmission of bits Always implemented through hardware Encompasses mechanical, electrical, and functional interfaces Transmission technique: determines whether the encoded bits will be transmitted by baseband (digital) or broadband (analog) signaling. OSI Data Link Layer Link establishment and termination: establishes and terminates the logical link between two nodes. Frame traffic control: tells the transmitting node to "back-off" when no frame buffers are available. Frame sequencing: transmits/receives frames sequentially. Frame acknowledgment: provides/expects frame acknowledgments. Detects and recovers from errors that occur in the physical layer by retransmitting nonacknowledged frames and handling duplicate frame receipt. Frame delimiting: creates and recognizes frame boundaries. Frame error checking: checks received frames for integrity. Media access management: determines when the node "has the right" to use the physical medium. OSI Network Layer Routing: routes frames among networks. Subnet traffic control: routers (network layer intermediate systems) can instruct a sending station to "throttle back" its frame transmission when the router's buffer fills up. Frame fragmentation: if it determines that a downstream router's maximum transmission unit (MTU) size is less than the frame size, a router can fragment a frame for transmission and re-assembly at the destination station. Logical-physical address mapping: translates logical addresses, or names, into physical addresses. Subnet usage accounting: has accounting functions to keep track of frames forwarded by subnet intermediate systems, to produce billing information. OSI Transport Layer Message segmentation: accepts a message from the (session) layer above it, splits the message into smaller units (if not already small enough), and passes the smaller units down to the network layer. The transport layer at the destination station reassembles the message. Message acknowledgment: provides reliable end-toend message delivery with acknowledgments. Message traffic control: tells the transmitting station to "back-off" when no message buffers are available. Session multiplexing: multiplexes several message streams, or sessions onto one logical link and keeps track of which messages belong to which sessions (see session layer). OSI Session Layer Session establishment, maintenance and termination: allows two application processes on different machines to establish, use and terminate a connection, called a session. Session support: performs the functions that allow these processes to communicate over the network, performing security, name recognition, logging, and so on. OSI Presentation Layer Character code translation: for example, ASCII to EBCDIC. Data conversion: bit order, CR-CR/LF, integer-floating point, and so on. Data compression: reduces the number of bits that need to be transmitted on the network. Data encryption: encrypt data for security purposes. For example, password encryption. OSI Application Layer Resource sharing and device redirection Remote file access Remote printer access Inter-process communication Network management Directory services Electronic messaging (such as mail) Network virtual terminals TCP/IP Transmission control Protocol/Internet Protocol Developed by DARPA No official protocol standard Can identify five layers ◦ ◦ ◦ ◦ ◦ Application Host-to-Host (transport) Internet Network Access Physical An OSI View of TCP/IP TCP\IP Model OSI Model Application (http, telnet, snmp, smtp, nfs, ftp) Transport (TCP, UDP) Internet (IPv4/IPv6) Network Access Physical layer (HDLC) Sender Application Layer Transport Layer Network Layer Data Link Layer Physical Layer HTTP Request TCP HTTP Request IP TCP HTTP Ethernet IP Receiver Application Layer Transport Layer Request TCP HTTP Request Network Layer Data Link Layer Physical Layer HTTP Request TCP HTTP Request IP TCP HTTP Ethernet IP Request TCP HTTP Request TCP/IP Network Access Layer Exchange of data between end system and network Address of host and destination Prioritization of transmission Software at this layer depends on network TCP/IP Internet Layer An Internet is an interconnection of two or more networks Internet layer handles tasks similar to network access layer, but between networks rather than between nodes on a network Uses IP for addressing and routing across networks Implemented in workstations and routers TCP/IP Transport Layer Also called host-to-host layer Reliable exchange of data between applications Uses TCP protocols for transmission TCP/IP Application Layer Logic needed to support variety of applications Separate module supports each type of application (e.g. file transfer) ◦ ◦ ◦ ◦ ◦ FTP HTTP Telnet News SMTP *TCP/IP Application Presentation Session Transport TELNET FTP SMTP DNS SNMP DHCP RIP RTP RTCP Transmission Control Protocol User Datagram Protocol OSPF ICMP IGMP Internet Protocol Network ARP Data link Physical Ethernet Token Bus Token Ring FDDI Overview of the Internet Internet – a vast network of LANs and WANs that electronically connects millions of people worldwide The Internet was formed in 1969 by ARPA, whose network, ARPANET, featured multiple servers and connections The World Wide Web World Wide Web – a set of software programs that enables users to access resources on the Internet via hypertext documents, or Web pages Web page – a document created in HTML containing hypertext links that, when clicked, enable users to access a different location or document Web site – a collection of related Web pages Web browser – a software application that enables users to easily access, view and navigate Web pages on the Internet How the Internet Works Network protocols and packets: ◦ Protocol – an agreed-upon format for transmitting data between two devices ◦ Packet – a fixed piece of information sent across a network Every computer connected to the Internet uses Transmission Control Protocol/Internet Protocol (TCP/IP) ◦ TCP/IP – software that makes Internet communication possible How the Internet Works (cont’d) Computers access information from the Internet as follows: ◦ You request data from an Internet server ◦ The request is divided into packets ◦ The packets are routed from your LAN to the Internet backbone ◦ The packets are routed from the Internet backbone to the destination server ◦ The destination server sends the requested information using the same process Connecting to the Internet Six elements are required to connect to the Internet: ◦ ◦ ◦ ◦ ◦ Computer Operating system TCP/IP Client software Internet connection (dial-up or direct through an ISP) ◦ Internet address Internet Service Providers (ISPs) Internet Service Provider (ISP) – an organization that provides access to the Internet ◦ Most ISPs charge a flat monthly rate ◦ There are some basic-service ISPs that offer Internet connectivity for free ◦ ISPs offer dial-up or direct Internet connections Internet Protocols Internet Protocol version 4 (IPv4) – supports 32-bit dotted quad IP address format ◦ Most widely used version of IP ◦ Approximately 4 billion possible IP addresses Internet Protocol version 6 (IPv6) – supports 128-bit hexadecimal address format ◦ Also known as Internet Protocol Next Generation (IPng) ◦ Will replace IPv4 in the future ◦ Approximately 4 trillion possible IP addresses Internet Protocols (cont’d) Hypertext Transfer Protocol (HTTP) – used to transfer Web pages from a Web server to a Web client (Web browser) Hypertext Transfer Protocol Secure (HTTPS) – used to access a secure Web server File Transfer Protocol (FTP) – used to transfer files between computers on the Internet Electronic mail (e-mail) protocols: ◦ Simple Mail Transfer Protocol (SMTP) – used to transfer e-mail messages to others with an outgoing mail server Domain Name System (DNS) Domain Name System (DNS) – resolves IP addresses into easily recognizable names For example: ◦ 64.128.206.9 = www.CIW-certified.com Domain name and IP address refer to the same Web server Typical Domain Name www.CIW-certified.com Server (host) name Registered company domain name Domain category (top-level domain) Top-Level Domains com — commercial or company sites edu — educational institutions, typically universities org — organizations; originally clubs, associations and nonprofit groups; currently, various types of organizations mil — U.S. military gov — U.S. civilian government net — network sites, including ISPs int — international organizations (rarely used) Applications /Services Operations Of Internet Download programs and files E-Mail Voice and Video Conferencing E-Commerce File Sharing Information browsing Search the web addresses for access through search engine Chatting and many more… Disadvantages of Internet Theft of personal information such as name, address, credit card number etc. Virus threats nothing but a program which disrupts the normal functioning of your system. Spamming refers to receiving unwanted e-mails in bulk, which provide no purpose and needlessly obstruct the entire system. Pornography This is perhaps the biggest threat related to children’s healthy mental life.A very serious issue concerning the Internet. Though, internet can also create havoc, destruction and its misuse can be very fatal, the advantages of it outweigh its disadvantages. What is Intranet ? Internal company network that uses Internet standards (HTML, HTTP & TCP/IP protocols) & software. Accessed only by authorized persons, especially members or employees of the organization Applications of Intranet Sharing of company policies/rules & regulations Access employee database Distribution of circulars/Office Orders Access product & customer data Sharing of information of common interest Launching of personal/departmental home pages Submission of reports Corporate telephone directories Disadvantages Management problem Security problem A company may not have person to update their Intranet on a routine basis Fear of sharing information and the loss of control Limited bandwidth for the business Unauthorized access Abuse of access Denial of service Productivity problem Information overload lowers productivity True purpose of the Intranet is unknown to many employees/departments Hidden or unknown complexity and costs What is Extranet ? Extranet is an Intranet for outside authorized users using same internet technology. Inter-organizational information system. enable outsiders to work together with company’s employees. open to selected suppliers, customers & other business partners Benefits of Extranet Improved quality. lower travel costs. lower administrative & other overhead costs. reduction in paperwork. delivery of accurate information on time. improved customer service. better communication. overall improvement in business effectiveness. Disadvantages The suppliers & customer who don’t have technical knowledge feel problem. Faceless contact. Information can be misused by other competitors. Fraud may be possible. Technical Employees are required. Communication Media • • • Cables coaxial twisted-pair fiber optic • • • Wireless Media Infrared Narrowband radio Microwave Cables pp. Cable is used to connect network devices. There are many types of networking cable in use today. Different types of cable have particular strengths and weaknesses, most notably in the speed at which they can transfer information. 111-116 Cables The vast majority of networks are connected by some sort of cabling. The cables are the network transmission media that carry signals between computers. Three major groups of cabling connect the majority of networks: • coaxial • twisted-pair • fiber optic pp. 111-116 Coaxial cable Coaxial cable consists of a core of copper wire surrounded by insulation, a braided metal shielding, and an outer cover. pp. 111-116 shielding A layer of covering that grounds a cable and protects it from electric noise and crosstalk. Twisted-Pair Cable The twisting of the twisted-pair cable wire cancels out crosstalk from adjacent pairs of cable. The higher the number of twists per foot of cable, the more effectively it cancels out crosstalk. The total number of pairs in a cable varies, depending on the purpose of the cable. pp. 111-116 twisted-pair cable A type of cable that consists of two insulated strands of copper wire twisted around each other. Twisted Pair Cable pp. Fiber Optic Cable In a fiber optic cable, pulses of light travel down extremely thin tubes of glass or plastic to transmit data. The signal—a light pulse—can be transmitted over many miles very quickly. 111-116 fiber optic cable A type of cable made up of extremely thin tubes of glass or plastic that allow pulses of light to travel through it to transmit data. Wireless Media •Infrared •Narrowband radio •Microwave pp. 125-128 Infrared Light There are four types of infrared networks: • line-of-sight • scatter infrared • reflective • broadband optical telepoint infrared A type of light beam used in wireless networks to transmit the data between devices. pp. 125-128 Narrowband Radio Narrowband radio is similar to broadcasting from a radio station. The broadcast range is 3,000 meters (9,842 feet), and does not require line-ofsight focusing. However, because the signal is high frequency, it is subject to attenuation from steel and load-bearing walls. narrowband radio A high-frequency transmission similar to broadcasting from a radio station. The user tunes both the transmitter and the receiver to a certain frequency. pp. 125-128 pp. Microwave Microwave systems can be used for the following: • satellite-to-ground links • between two buildings • across large, flat, and open areas, such as bodies of water or deserts microwave Part of the electromagnetic spectrum, and a form of radiation that can be used for short- and long-distance communications systems. 125-128 Microwave Technology pp. 125-128 A microwave system can be used to transmit data from building to building. Network hardware Cables Wireless Media Hubs Repeaters Bridges and Switches Routers Gateways Modems Hubs The hub is a central hardware component for many LANs. Hubs operate at the Physical Layer in the OSI model. Hubs contain multiple ports, and can connect to other hubs to expand the network. pp. 104-109 Repeaters Repeaters operate at the Physical Layer of the OSI model. Essentially, repeaters allow smaller LANs to grow into larger LANs by moving transmissions from one network segment to another. pp. repeater A device that can be used to connect two cables and that boosts the signal before sending it along. segment A section of the network that includes the cable and nodes that are connected to a device, such as a repeater, hub, or bridge. 104-109 Bridges and Switches Bridges can be used to connect dissimilar network segments that use different methods of transferring data. In today’s networks, it is uncommon to find bridges because switches provide “multibridge” capability. bridge A device used to connect two network segments together. switch A multiport bridge that allows several segments of a network to communicate with one another. pp. 104-109 Bridges and Switches An important function of bridges and switches is to minimize collision of data packets by creating collision domains. Bridges and switches prevent the passing of collisions from one network segment to another. pp. 104-109 pp. Routers Bridges are clever devices, but they are not as smart as routers. Brides forward data from one network segment to another, routers: • forward packets from one network to another and , • determine the best route to use to deliver the data router A network device used to connect networks of different types and that forwards packets from one network to another, even those separated by great distances. A router determines the best route to use to deliver the data. 104-109 pp. Gateways Gateways enable dissimilar networks to communicate. Gateways operate at higher levels in the OSI model such as the Application, Presentation, and Session layers. In some cases, they operate at all seven layers. gateway A dedicated network computer whose job is to convert data packets from one network protocol to another. Enables dissimilar networks to communicate. 104-109 Modems • • A modem is a computerto-computer communication device that converts digital signals from the computer to analog signals for the telephone lines. The word “modem” comes from the two operations it handles: modulation demodulation modulation The process on changing the digital signal to an analog signal on the sending computer. demodulation The process of converting the analog signal back to a digital signal on the receiving computer. Queries?? Queries?