* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Secure Electronic Transactions
Survey
Document related concepts
Transcript
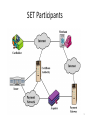
Secure Electronic Transaction Q. What type of transaction are supported by secure Electronic transactions ? Describe any three in details Q. What are various Electronic commerce components ? Q. What is SET ? i. Explain key-features and participants ii. Briefly describe the sequence of events that are required for transaction. Secure Electronic Transactions • An open encryption and security specification. • Protect credit card transaction on the Internet. • Companies involved in developing : – MasterCard, Visa, IBM, Microsoft, Netscape, RSA, Terisa and Verisign • Not itself a payment system. • Set of security protocols and formats. • which enables user to use existing credit card payment infrastructure on an open network. 2 SET Services 3 Services: • Provides a secure communication channel in a transaction. • Provides trust by the use of X.509v3 digital certificates. • Ensures privacy, i.e. Information is only available when are where needed. 3 SET Overview • Business requirements for secure payment processing with credit cards over Internet and other network: – Provide confidentiality of payment and ordering information : assures cardholders that this information is safe and accessible to intended recipient; reduces risk of fraud. – Ensures the integrity of all transmitted data : no modification of data during transmission ; Digital signature are used. – Provide authentication that a cardholder is a legitimate user of credit card account : linking cardholder with specific account number reduces incedence of fraudand overall cost of payment processing ; Digital signature and certificates are used to verify that cardholder is legitimate user of a valid account. 4 SET Overview – Provide authentication that a merchant can accept credit card transactions through its relationship with a financial institution : Provide ability to cardholders to identify merchants ; digital signatures and certificates are used. – Ensure the use of best security practices and system design techiques to protect all legitimate parties in an electornic commerce transaction : Set is well tested specification based on highly secure cryptographic algo and protocols. – Create a protocol that neither depends on transport security mechanism nor prevents their use: securly operates over a ”raw” TCP/IP stack; It does not interfere other security mechanism, such as IPSec and SSL/TLS. 5 SET Overview – Facilitate and encourage interoperatability among S/W and Network providers : SET protocols and formats are independent of H/W platforms, OS and web Software. 6 SET Overview • For meeting requirements, SET consist of various Key Features: – Confidentiality of information : DES is used for providing confidentiality, main aspect that it prevents merchant from learning credit cardholder’s card number – Integrity of data : Payment information sent from cardholder to merchant includes order information, personal data, payment instruction. SET guarantees that contents not get altered in transit • use RSA digital signature and SHA for message integrity. • Sometime uses HMAC also. 7 SET Overview – Cardholder account authentication : Enables merchant to verify authenticity of cardholder and also to verify the valid card number, uses X.509 digital certificate with RSA signature. – Merchant authentication : Also allows cardholder to verify the merchant by looking towards the relationship with the financial institution to accept payment cards, again uses X.509 digital certificates with RSA signatures. 8 SET Participants 9 Sequence of events for transactions 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. The customer opens an account. The customer receives a certificate. Merchants have their own certificates. The customer places an order. The merchant is verified. The order and payment are sent. The merchant request payment authorization. The merchant confirm the order. The merchant provides the goods or service. The merchant requests payments. 10 Dual Signature • Purpose of the dual signature is to link two messages that are intended for two different recipients. • If customer wants to send order information (OI) to Merchant and Payment Information (PI) to bank. • Merchant does not need to know customer’s credit card number, and the bank does not need to know the details of the customer order. • customer is provided with extra protection in terms of privacy. • By keeping these two items separate. • Link is needed here to prove that this payment is intended for this order and not for some other goods or services. Dual Signature • Consider the customer send two messages: • A signed OI and signed PI. • Define ur own. • Dual Signature DS EKRc [ H ( H ( PI ) || H(OI))] 13 Payment processing Cardholder sends Purchase Request 14 Payment processing Merchant Verifies Customer Purchase Request 15 Payment processing • Payment Authorization: – Authorization Request – Authorization Response • Payment Capture: – Capture Request – Capture Response 16