* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Network Security Strategies
Wake-on-LAN wikipedia , lookup
Computer network wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Deep packet inspection wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Network tap wikipedia , lookup
Computer security wikipedia , lookup
Wireless security wikipedia , lookup
Airborne Networking wikipedia , lookup
Peer-to-peer wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
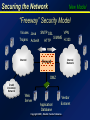
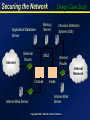
Securing the Borderless Network March 21, 2000 Ted Barlow Securing the Network Introduction The Internet has fundamentally changed the way networks are designed and secured Copyright 2000, Deloitte Touche Tohmatsu Securing the Network Old Model How things used to be . . . • single host environment • mainframe security systems Mainframe • hierarchical controls Controller • well-defined access paths • dumb terminals • centralized storage/processing of data Dumb Terminals Copyright 2000, Deloitte Touche Tohmatsu Dumb Terminals Securing the Network “New” Old Model “Fortress” Security Model Internet Firewall Protocols: SMTP FTP HTTP Copyright 2000, Deloitte Touche Tohmatsu Internal Network Securing the Network New Model “Freeway” Security Model Viruses Java SMTP SSL VPN S/MIME H.323 Trojans ActiveX HTTP Internet Internal Network Firewall DMZ Credit Validation Network Web Server Application/ Database Vendor Extranet Copyright 2000, Deloitte Touche Tohmatsu Securing the Network Risks What are the Risks? • Denial of Service • DDOS (Distributed Denial of Service Attacks) • Defacement • 3693 web server defacements in 1999 (www.attrition.org) • 130 government sites (.gov) • Loss of private data • CD Universe (~350,000 credit card numbers) • Breach of internal networks and systems Copyright 2000, Deloitte Touche Tohmatsu Securing the Network Design and Build How do you Build a Secure Internet Application Environment? • Incorporate security reviews early in the design process • Design with future strong authentication methods in mind • Design for explosive growth • Encrypt entire path from client to backup tapes for critical data • Establish security baselines and perform security hardening before going live on the Internet Copyright 2000, Deloitte Touche Tohmatsu Securing the Network Infrastructure Key Components of the Secure Network • Border routers • DMZ • Firewalls • Encrypted data paths • Intrusion Detection System (IDS) • Content Security (CVP) Copyright 2000, Deloitte Touche Tohmatsu Securing the Network Firewalls The Firewall/DMZ Environment • Begin with a secure screening router • Choose a firewall that is extensible, scalable • Packet filtering vs. application proxy firewalls • Firewall appliances and next generation firewalls • Network address translation (NAT) will improve DMZ security • Build firewall redundancy Copyright 2000, Deloitte Touche Tohmatsu Securing the Network Firewall Comparison Choosing the Right Firewall Solution PROS Packet Filters • Application Independent • High Performance • Scalable • Good Security • Fully Aware of Application ApplicationProxy Gateways Layer Stateful Inspection • Good Security • High Performance • Scalable • Fully Aware of Application Layer • Extensible CONS • Low Security • No Protection Above Network Layer • Poor Performance • Limited Application Support • Poor Scalability • More Expensive Copyright 2000, Deloitte Touche Tohmatsu Securing the Network IDS Is Intrusion Detection Necessary? • Definition – the ability to detect and defend against defined attack patterns • Host based & network based • Network IDS can be integrated with firewalls to automatically respond to attacks • Host based IDS can detect changes to operating system programs and configurations Copyright 2000, Deloitte Touche Tohmatsu Securing the Network Application/Database Server Internet Design Case Study Backup Server External Router Intrusion Detection System (IDS) DMZ Internal Router Internal Network Outside Internet Web Server Inside Intranet Web Server Copyright 2000, Deloitte Touche Tohmatsu Securing the Network Design Case Study Web Server App Server IDS Backup Server DMZ External Router DMZ Internet IDS Console CVP Server NAT IDS Internal Network NAT Internal Router Copyright 2000, Deloitte Touche Tohmatsu Securing the Network Maintenance How do you Maintain a Secure Internet Application Environment? • Keeping ahead of security exploits is a full time job • Actually review and report on firewall, IDS and system logs • Develop incidence response (IR) procedures and IR team • Periodically review and audit system and network security configurations Copyright 2000, Deloitte Touche Tohmatsu Securing the Network Future Developments What is coming in Network Security? • Better, cheaper authentication mechanisms • Open network security models • System, application level “firewalls” • Windows 2000 Copyright 2000, Deloitte Touche Tohmatsu Securing the Network Future Developments Windows 2000 Security • • • • • Kerberos Authentication Infrastructure Certificate Authority (CA) Security Configuration Editor IPSec Support Encrypting File System (EFS) Copyright 2000, Deloitte Touche Tohmatsu Securing the Network Future Developments Kerberos Authentication Windows 2000 supports several authentication models: Kerberos for internal authentication and X.509 certificates for external authentication. Kerberos can be configured to use private or public key authentication. Keys are managed by the Domain Controller (DC) in the Key Distribution Center (KDC). A User is granted a ticket or certificate which permits a session between the user and the server. Important security considerations: • The KDC MUST be physically secured • Susceptible to password dictionary attacks • Administrators still have complete access Copyright 2000, Deloitte Touche Tohmatsu Securing the Network Future Developments Certificate Authority (CA) This is a Public Key Certificate Server built into Windows 2000. The server manages the issuing, renewal, and cancellation of digital certificates. Digital certificates are used to initiate encrypted sessions such as Secure Sockets Layer (SSL) for secure web-based communications. Copyright 2000, Deloitte Touche Tohmatsu Securing the Network Future Developments Security Configuration Editor This is a Microsoft Management Console (MMC) tool that eases security administration. Allows administrators to create security baselines by defining templates with global security parameters, and then perform security analyses against the templates. Manages security policies, file system access control, and Registry permissions. Copyright 2000, Deloitte Touche Tohmatsu Securing the Network Future Developments Internet Protocol Security (IPSec) Defines security policies at the lowest possible layer: the network communication layer. Enables encryption and decryption of network packets before they leave the network interface card (NIC). Supports the use of public keys (RSA) or private keys (DES). Copyright 2000, Deloitte Touche Tohmatsu Securing the Network Future Developments Encrypting File System (EFS) Allows users to encrypt files and directories that only they (and administrators) can decrypt. EFS creates a separate 56-bit encryption key based on the Data Encryption Standard (DES) algorithm. The administrator’s key can unlock any encrypted file in the domain. This service is very fast and encryption/decryption occurs without the user noticing. Copyright 2000, Deloitte Touche Tohmatsu Securing the Network Summary Summary of Best Practices • If possible, create a separate trusted network (DMZ) • Choosing the right firewall solution is key • Application security is only as strong as system and network security • Design the infrastructure to facilitate monitoring and data backups • Intrusion Detection Systems – you can’t defend what you don’t detect Copyright 2000, Deloitte Touche Tohmatsu Securing the Network Questions? Contact: Ted Barlow [email protected] Thank You Copyright 2000, Deloitte Touche Tohmatsu