* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Computer system structure overview
Survey
Document related concepts
Transcript
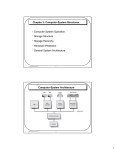
Computer System Structures Objectives To provide coverage of basic computer system organization How understanding the basic organization will help us in understanding the potential vulnerabilities in OS Lecture 2 1-1 What is a Computer System? Computer system divided into four components: Lecture 2 1-2 Computer System Organization Computer-system organization One or more CPUs, device controllers connect through common bus providing access to shared memory Concurrent execution of CPUs and devices competing for memory cycles Lecture 2 1-3 Computer Startup bootstrap program is loaded at power-up or reboot Typically stored in ROM or EPROM, generally known as firmware Initializes all aspects of system Loads operating system kernel and starts execution OS starts executing the first process “init” and waits for some events Lecture 2 1-4 Computer-System Operation After computer starts… I/O devices and the CPU can execute concurrently Each device controller is in charge of a particular device type Each device controller has a local buffer CPU moves data from/to main memory to/from local buffers But how would CPU know when the devices are ready? The occurrence of an event is signaled by an “interrupt” from either the hardware or software Lecture 2 1-5 Common Functions of Interrupts Modern Operating systems are interrupt-driven Occurrence of event from hardware side Interrupt (signal) sent to CPU through system bus Occurrence of event from software side Interrupt sent by executing a special operation (system call/monitor call) “Trap” – mostly software-generated interrupt caused by an error Lecture 2 1-6 Interrupt Architecture What happens when an interrupt is signaled… Interrupt architecture must save the address of the interrupted instruction CPU stops its “operation” Moves to the interrupt service routine address and executes On completion, CPU resumes the earlier operation Also remember: Incoming interrupts are disabled while another interrupt is being processed to prevent a lost interrupt Example: Operating system as different as MS-DOS and UNIX both follow the same interrupt principles Lecture 2 1-7 Interrupt Timeline - example Device controller informs CPU by triggering an interrupt e.g., CPU makes a read request I/O device controller starts the transfer from the device to local buffer Lecture 2 1-8 I/O interrupts There are two ways that the I/O operations are handled by OS Synchronous I/O After I/O starts, control returns to user program only upon I/O completion Special “Wait” instruction idles the CPU until the next interrupt Wait loop (contention for memory access) • Loop: jmp Loop At most one I/O request is outstanding at a time, no simultaneous I/O processing Lecture 2 1-9 I/O interrupts Asynchronous I/O After I/O starts, control returns to user program without waiting for I/O completion System call is then needed to request to the operating system to allow user to wait for I/O completion Asynchronous I/O is more complex Need to be able to keep track of many I/O requests Device-status table contains entry for each I/O device indicating its type, address, and state Operating system indexes into I/O device table to determine device status and to modify table entry to include interrupt Lecture 2 1-10 Device Status Table Device: keyboard Status: idle Device: laser printer Status: busy Request for laser printer address: 38546 Device: mouse Status: idle Device: disk unit 1 Status: idle Device: disk unit 2 Status: busy Request for disk unit 2 Request for disk unit 2 file: abc operation: read Address: xyz file: def operation: write Address: zyx Lecture 2 1-11 I/O interrupts Adv./disadv. of synchronous I/O and asynchronous I/O? Lecture 2 1-12 I/O Structure (contd.) Asynchronous I/O works well with slow I/O structure E.g., in a typical slow I/O, one character takes approx. 1 ms. (1000 micro sec.) Typical interrupt service routine takes 2 micro sec. per character to input character into a buffer Leaving 998 micro sec. out of 1000 micro sec. to do other CPU computations With high-speed I/O device, the above assumption not valid anymore I/O transfer at close to memory speed Asynchronous I/O will not be efficient any more… To solve this problem, Direct memory Access (DMA) is used for high speed I/O devices Lecture 2 1-13 Direct Memory Access Structure Used for high-speed I/O devices able to transmit information at close to memory speeds Device controller transfers blocks of data from buffer storage directly to main memory without CPU intervention Only one interrupt is generated per block, rather than the one interrupt per byte DMA still has “problem” of “stealing” memory cycles from the CPU Lecture 2 1-14 Storage Structure Main memory – only large storage media that the CPU can access directly Computer programs must be in main memory (RAM) The disk controller determines the logical interaction between the device and the computer Secondary storage – extension of main memory that provides large nonvolatile storage capacity Lecture 2 1-15 Storage Structure – Main Memory An example of Machine instructions with operators and operands for Motorola M68HC11 ORG $2000 Reserves space in memory for storing Main memory implemented in a semiconductor technology called dynamic random access memory (DRAM) Volatile storage device MEMSTO FCB $00 STRING FCC 'The final number is: ‘ MEMSTO1 FCB $00 MEMSTO2 FCB $00 STRING1 FCC ' in Hexadecimal.‘ FCB $04 START Interaction with main memory ORG $2030 Reserves memory for the program LDAA #10 Loads ten in decimal to accumulator A STAA MEMSTO ADDA MEMSTO STAA MEMSTO is achieved through series of load and store instructions Lecture 2 1-16 Secondary Storage Secondary storage – extension of main memory that provides large nonvolatile storage capacity Magnetic disks – most popular rigid metal or glass platters covered with magnetic recording material Disk surface is logically divided into circular tracks, which are subdivided into sectors Set of tracks in one arm position forms a cylinder Lecture 2 1-17 Magnetic Disks When the disk is in use, a drive motor spins it at high speed (typical, 60 – 200 times per second) Disk “time” (operation on the disk) has two parts Transfer time Positioning time • Seek time (move the disk arm to the desired cylinder) • Rotational latency (time for the desired sector to rotate to the disk head) Disk protection and head crash Lecture 2 1-18 Storage Hierarchy There are wide variety of storage systems in a computer system Main memory, magnetic disk, magnetic tapes and many more… Depending on three criteria, the storage systems are organized in hierarchy “The Factors” 1. 2. 3. Speed Cost Volatility Lecture 2 1-19 Storage-Device Hierarchy increasing speed cost decreasing volatility speed Lecture 2 cost volatility 1-20 Caching Important principle, performed at many levels in a computer (in hardware, operating system, software) Information in use copied from slower to faster storage Faster storage (cache) checked first to determine if information is there If it is, information used directly from the cache (fast) If not, data copied to cache and used there Cache smaller than storage being cached Cache management important design problem Cache size and replacement policy Lecture 2 1-21 Performance of Various Levels of Storage Lecture 2 1-22 Coherency and Consistency Problem First major issue in designing a secure and protected OS Multitasking environments must be careful to use most recent value, no matter where it is stored in the storage hierarchy Multiprocessor environment must provide cache coherency in hardware such that all CPUs have the most recent value in their cache Distributed environment situation even more complex Several copies of a datum can exist Lot of research conducted and various solutions achieved Lecture 2 1-23 Open-Source Operating Systems Operating systems made available in source-code format rather than just binary closed-source Counter to the copy protection and Digital Rights Management (DRM) movement Started by Free Software Foundation (FSF), which has “copyleft” GNU Public License (GPL) Examples include GNU/Linux, BSD UNIX (including core of Mac OS X), and Sun Solaris However, with increase in open-source OS popularity, increase in vulnerabilities Lecture 2 1-24 Networking increased the vulnerabilities even more 1960s Advanced Research Project Agency (ARPA) began to examine feasibility of redundant networked communications Larry Roberts developed ARPANET from its inception 1970s and 1980s ARPANET grew in popularity as did its potential for misuse No safety procedures for dial-up connections to ARPANET Nonexistent user identification and authorization to system Late 1970s and 1980s Information security began with Rand Report R-609 (paper that started the study of computer security) Scope of computer security grew from physical security to include: • Safety of data • Limiting unauthorized access to data • Involvement of distributed systems from multiple levels of organizations Lecture 2 1-25 MULTICS Early focus of computer security research was a system called Multiplexed Information and Computing Service (MULTICS) Initial planning started in 1964! First operating system created with security as its primary goal Mainframe, time-sharing OS developed in mid-1960s by General Electric (GE), Bell Labs, and Massachusetts Institute of Technology (MIT) Several MULTICS key players created UNIX Primary purpose of UNIX was text processing! Lecture 2 26 Protection and Security While MULTICS was commercially not a success it was able to teach us the correct lesson… Importance of protection and security When a program written by one user may be used by another user, misuse and unexpected behavior would occur Protection – any mechanism for controlling access of processes or users to resources defined by the OS Security – defense of the system against internal and external attacks Huge range including: denial-of-service, worms, viruses, identity theft, theft of service Lecture 2 1-27 Malware Trojan horse Hidden part of some otherwise useful software E.g., a text-editor program written by a user may include hidden code to search the file for certain keywords Another example may be a key-stroke logger Trojan horse often may open a “backdoor” and start a covert channel Covert channel is not a virus and thus not detected by antivirus Lecture 2 1-28 What is Covert Channel? A covert channel is a “parasitic communication channel” that is neither designed nor intended to transfer information at all [Lampson 1973] A covert channel refers to the mechanism of stealth information transfer using a legitimate communication channel visible to the rest of the world The main focus is to hide secret, valuable information through the usage of some other “normal, harmless” information Lecture 2 1-29 A simple illustration: “Harmless” Communication Hello Bob I am Adam Adam (Transmitter) Are Ed you(Eavesdropper) Bob (Receiver) There Listening? Lecture 2 1-30 Covert Channel Inter-arrival time Covert Bit Sequence Hello Adam (Transmitter) Bob 1s 0 I 2s 1 am 2s 1 Adam 2s 1 1s Bob (Receiver) 1s 0 There 2s 1 Listening? 2s 1 Are Ed you(Eavesdropper) Lecture 2 0 1-31 Other System Threats Worm: A process that uses spawn mechanism The processes “eat” system resources self- replicating: propagates to other hosts, users Do not even have to execute them to get started Virus infection by receiving object (e.g., e-mail attachment), actively executing Unlike worms, virus is a fragment of code Lecture 2 1-32 Denial of Service Attacks Denial of service (DoS): attackers make resources (CPU resources, bandwidth) unavailable to legitimate traffic by overwhelming resource with bogus traffic Lecture 2 1-33 Protection and Security Systems generally first distinguish among users, to determine who can do what User identities (user IDs, security IDs) include name and associated number, one per user User ID then associated with all files, processes of that user to determine access control Group identifier (group ID) allows set of users to be defined and controls managed, then also associated with each process, file Privilege escalation allows user to change to effective ID with more rights Lecture 2 1-34