* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download CSCE 790: Computer Network Security
Deep packet inspection wikipedia , lookup
Remote Desktop Services wikipedia , lookup
Network tap wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Internet protocol suite wikipedia , lookup
Airborne Networking wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Zero-configuration networking wikipedia , lookup
DomainKeys Identified Mail wikipedia , lookup
Real-Time Messaging Protocol wikipedia , lookup
SIP extensions for the IP Multimedia Subsystem wikipedia , lookup
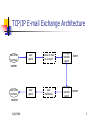
CSCE 515: Computer Network Programming Chin-Tser Huang [email protected] University of South Carolina Simple Mail Transfer Protocol (SMTP) Email is one of most popular applications In 1991 about ½ TCP connections are for SMTP Mail exchange is performed by a message transfer agent (MTA), for example Sendmail Users don’t interact with MTA but can choose their user agent 4/20/2004 2 TCP/IP E-mail Exchange Architecture user at a terminal user agent queue of mail to be sent message transfer agent client user agent user mailboxes message transfer agent server sender user at a terminal receiver 4/20/2004 3 SMTP Protocol Specified in RFC 821 Use NVT ASCII for communication between two MTAs Client sends commands to server Server responds with numeric reply codes with optional strings 4/20/2004 4 SMTP Commands Basic implementation includes eight commands HELO MAIL RCPT DATA QUIT RSET VRFY NOOP Additional commands include EXPN and TURN 4/20/2004 5 Envelopes, Headers, and Body Envelopes are used by MTAs for delivery Headers are used by user agents Specified by MAIL and RCPT commands RFC 822 specifies header format Each header field contains a name, a colon, and field value Body is content of message from sending user to receiving user When transferred using DATA command, headers are sent first, followed by a blank line, followed by body 4/20/2004 6 Transmission of a Mail User agent takes body, adds some headers, and passes to MTA MTA adds some headers, adds envelope, and sends to another MTA 4/20/2004 7 Relay Agents All individual systems send their mail to a relay system Two reasons of using relay system Simplify configuration of all MTAs other than relay system’s MTA Allow one system at an organization to act as mail hub Most organizations use relay system for Internet mail 4/20/2004 8 Improvements on SMTP Envelope changes: Extended SMTP Header changes: Non-ASCII characters Body changes: Multipurpose Internet Mail Extensions (MIME) 4/20/2004 9 Extended SMTP Framework for adding extensions to SMTP Client wishing to use new features can use EHLO, instead of HELO, to initiate session Server lists extended commands in the 250 reply to EHLO command 4/20/2004 10 Non-ASCII Characters Allow additional characters in sender and receiver names and in subject Header can contain encoded words =? charset ? encoding ? encoded-text ?= Charset can be us-ascii or iso-8859-1 Encoding can be quoted-printable or base-64 4/20/2004 Using base-64, three consecutive bytes are encoded as four 6-bit values 11 Multipurpose Internet Mail Extensions Allow structures in body Five new header fields Mime-Version: Content-Type: Content-Transfer-Encoding: Content-ID: Content-Description: Seven content types: text, multipart, message, application, image, audio, video Five encoding formats: 7bit, quoted-printable, base64, 8bit, binary 4/20/2004 12 Simple Network Management Protocol Need to manage systems within a coherent framework Network management consists of communication between managers and agents Number of networks within organization grows Heterogeneity of systems in network Managers are network management stations Agents are management software running on network elements, e.g. hosts, routers, X terminals Current version is SNMPv3 (RFC 2570) 4/20/2004 13 Components of Network Management Three components of SNMP Management Information Base (MIB): specifies what variables network elements maintain Structure of Management Information (SMI): a set of common structures and an identification scheme used to reference variables in MIB Simple Network Management Protocol (SNMP): protocol between manager and element 4/20/2004 14 SNMP Protocol Use UDP to send messages Seven types of messages are exchanged between managers and agents get-request allows manager to fetch value of variables get-next-request allows manager to fetch next variable after specified variables set-request allows manager to set value of variables get-response allows agent to return value of variables in response to get-request, get-next-request, and set-request trap allows agent to notify manager when something happens on agent get-bulk-request allows manager to retrieve large blocks of data inform-request allows one manager to send info to another manager 4/20/2004 15 SNMP Messages SNMP agent SNMP manager get-request UDP port 161 get-response get-next-request UDP port 161 get-response set-request UDP port 161 get-response UDP port 162 4/20/2004 trap 16 Structure of Management Info Data types used by SNMP INTEGER OCTET STRING DisplayString OBJECT IDENTIFIER NULL IpAddress PhysAddress Counter Gauge TimeTicks SEQUENCE SEQUENCE OF 4/20/2004 17 Object Identifiers A sequence of integers separated by decimal points These integers traverse a tree structure, similar to DNS Each node in the tree also has a textual name All variables in MIB start with the object identifier 1.3.6.1.2.1 4/20/2004 18 Instance Identification Every variable in MIB must be identified Simple variables are referenced by appending “.0” to variable’s object identifier Table entries are identified by combination of variables in table 4/20/2004 19 Traps Agent can send traps to manager to indicate that something has happened on agent Traps are sent to UDP port 162 on manager Seven types of traps coldStart warmStart linkDown linkUp authenticationFailure egpNeighborLoss enterpriseSpecific 4/20/2004 20 Next Class Peer-to-peer applications Read JNP Sec. 24.4 4/20/2004 21