* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download 01-Internet
Internet protocol suite wikipedia , lookup
Net neutrality law wikipedia , lookup
Computer network wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Airborne Networking wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
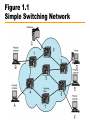
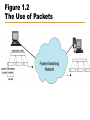
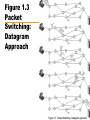
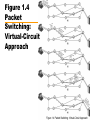
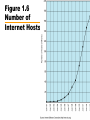
CIS 203 01 : Data Networks and The Internet Data Networks • Communication by transmitting data intermediate switching nodes • Switching nodes not concerned with content • End devices referred to as stations —Computers, terminals, telephones, etc. • Nodes connected in some topology by transmission links • Station attaches to node • Collection of nodes is a communications network Figure 1.1 Simple Switching Network Circuit Switching • Dedicated path between two stations —Connected sequence of links between nodes —E.g telephone network • Communication involves three phases —Circuit establishment —Data transfer —Circuit disconnect Circuit Establishment • • • • Station A to node 4 requesting connection to station E Circuit from A to 4 usually dedicated line Node 4 finds next leg to node 6 Based on routing information, availability, cost, node 4 selects circuit to node 5 • Allocates a free channel — TDM [time-division multiplexing] — FDM [frequency-division multiplexing] • Node 4 requests connection to E • And so on Data Transfer • Data may be digital (e.g., terminal to host) or analog (e.g., voice) • Signaling and transmission may each be digital or analog • Path is A-4 circuit, internal switching through 4, 4-5 channel, internal switching through 5, 5-6 channel, internal switching through 6, 6-E circuit • Generally, full duplex (data in both directions) Circuit Disconnect • Connection terminated —Usually by one of the stations • Signals to 4, 5, and 6 to de-allocate resources Circuit Switching - Notes • • • • Connection established before data transmission begins Channel capacity must be available and reserved. Nodes must have capacity to handle connection Switches must have intelligence to make allocations and devise route • Can be inefficient — Capacity dedicated for duration of connection • Even if no data are being transferred — For voice, utilization high, but still doesn’t approach 100% — For terminal connection, may be idle most of the time — Delay prior to data transfer for call establishment — Once circuit established, network transparent to users — Data transmitted at fixed rate • No delay other than propagation • Delay at node negligible Packet Switching • • • • • • • • 1970 Evolved substantially since Basic technology fundamentally the same today One of few effective technologies for long-distance data communications Frame relay and ATM (see later) variations Carries directly to Internet Advantages: flexibility, resource sharing, robustness, responsiveness Cost: elaborate algorithms to cope with time delay and overhead penalties of network operation Packet Switching – Circuit Switching Issues • Designed for voice • Resources dedicated to particular call • For voice, high utilization —Most of the time, someone is talking • For data —Line idle much of the time —Constant data rate • Limits interconnection of variety of host computers and terminals Packet Switching – Basic Operation • Data are transmitted in short blocks, called packets • Typical upper bound 1000 octets (bytes) • Longer messages broken up into series of packets — Each packet contains part (or all for short message) of user's data plus some control information — Control information includes network routing — At each node, packet is received, stored briefly, and passed on to the next node • • • • Transmitting computer sends message as sequence of packets Packet includes control information including destination station Packets sent to node to which sending station attaches Node stores packet briefly, determines next leg of route, and queues packet to go out on that link • When link is available, packet is transmitted to next node • All packets eventually work their way through network Figure 1.2 The Use of Packets Packet Switching – Advantages • Line efficiency greater — Node-to-node link dynamically shared by many packets • Data-rate conversion — Each station connects to its node at its proper data rate — Nodes act as buffers • Packets accepted, even under heavy traffic, but delivery delay increases — Circuit switching networks would block new connections • Priorities can be used Packet Switching – Disadvantages • Delay — Transmission delay equal to length of packet divided by incoming channel rate — Variable delay due to processing and queuing • Packets may vary in length — May take different routes — May be subject to varying delays — Overall packet delay can vary substantially (jitter) — Not good for real-time applications like voice and real-time video • Overheads including address of destination, sequencing information added to packet — Reduces capacity available for user data • More processing required at node Switching Technique – Datagram • Datagram: each packet treated independently — No reference to packets that have gone before — Each node chooses next node on path — Packets with same destination address do not follow same route — May arrive out of sequence — Exit node or destination restores packets to original order — Packet may be destroyed in transit — Either exit node or destination detects loss and recovers • Call setup avoided • For an exchange of a few packets, datagram quicker • More flexible. — E.g. Routing away from the congestion — Delivery is inherently more reliable • If a node fails, subsequent packets may be re-routed Figure 1.3 Packet Switching: Datagram Approach Switching Technique – Virtual Circuit • Preplanned route established before packets sent • All packets follow same route • Similar to circuit in circuit-switching network — Hence virtual circuit • Each packet has virtual circuit identifier — Nodes on route know where to direct packets — No routing decisions • Not dedicated path, as in circuit switching — Packet still buffered at node and queued for output — Routing decision made oncefor that virtual circuit • Network may provide services related to virtual circuit — Sequencing and error control • Packets should transit more rapidly • If node fails, all virtual circuits through node lost Figure 1.4 Packet Switching: Virtual-Circuit Approach Figure 1.5 Effect of Packet Size on Transmission Time Routing • Adaptive routing —Routing decisions change as conditions on network change • Failure of node or trunk • Congestion —Route around congestion • Requires exchange of network state information —Tradeoff between quality of information and overhead Frame Relay • Considerable overhead in packet-switching schemes to compensate for errors — Additional bits added to packet for redundancy — Additional processing at stations and nodes to detect and recover from errors • Modern systems more reliable — Any remaining errors caught in systems above packet-switching logic • • • • Original packet-switching networks data rate 64 kbps Frame relay networks up to 2 Mbps Strip out most error control overhead Uses variable-length packets (frames) Asynchronous Transfer Mode ATM or Cell Relay • • • • • Little overhead for error control Fixed-length packets (cells) Processing overhead reduced Designed to work at 10s, 100s of Mbps, and Gbps Small, fixed-size cells are efficient — Can offer constant-data-rate channel using packet-switching • Also evolution from circuit switching • Allows definition of multiple virtual channels — Data rates dynamically defined at virtual channel setup — Extends circuit switching to allow multiple channels with data rates set on demand Local Area Networks LAN • Small scope — Typically single building or a cluster of buildings — Leads to different technical solutions • Usually LAN owned by same organization that owns attached devices — For WANs, a significant fraction of the network assets are not owned. — May be a substantial capital investment for both purchase and maintenance. — Network management responsibility falls on owner • Data rates of LANs typically much greater than WANs • Most common are switched LANs and wireless LANs — E.g. Ethernet, ATM, Fibre Channel, WiFi (802.11) • More later Metropolitan Area Networks MAN • Between LANs and WANs • Traditional point-to-point and switched networks in WANs inadequate for growing needs of organizations • Requirement for high capacity private and public networks at low costs over a large area —E.g. Wireless networks, metropolitan extensions to Ethernet The Internet History (1) Background • Evolved from ARPANET, 1969 Advanced Research Projects Agency (ARPA),U.S. Department of Defense • First operational packet-switching network • Began in four locations: UCLA, University of Santa Barbara, the University of Utah, and SRI (Stanford Research Institute) • Today tens of millions of hosts • Hundreds of millions of users • Nearly 200 countries • Number of connections growing exponentially • Allowed devices from different manufacturers and with different data rates to communicate • Used adaptive routing Figure 1.6 Number of Internet Hosts The Internet History (2) Applications • Telnet provided common denominator terminal — Software written support “Telnet terminal,” — Any terminal could interact with any computer • File Transport Protocol (FTP) offered similar open functionality — Transparent transfer of files from one computer to another — Overcomes different word sizes, different bit orders and different word formats • First “killer app” was electronic mail — Previously all single computer systems — 1972, Ray Tomlinson of Bolt Beranek and Newman (BBN) — Distributed mail service across network using multiple computers — 1973 three quarters of all ARPANET traffic was e-mail The Internet History (3) – TCP/IP • Packet-switching applied to tactical radio communication (packet radio) and satellite communication (SATNET) — Different communication environments — Certain parameters, e.g. maximum packet size, different • Vint Cerf and Bob Kahn of ARPA developed protocols for communicating across arbitrary, multiple, packet-switched networks (internetting) • May 1974 Transmission Control Protocol • Refined by ARPANET community • Major contributions from participants from European Networks, such as Cyclades (France), and EIN • Leading to TCP and IP • Basis for TCP/IP protocol suite • 1982-1983, ARPANET switched from NCP to TCP/IP • Many networks connected using TCP/IP • Use of ARPANET restricted to ARPA contractors The Internet History (4) – National Science Foundation • Extended support to other computer research groups — CSNET in 1980-1981 • 1986, extended Internet support to general research community — NSFNET backbone — Originally designed to interconnect six NSF funded supercomputer centers across USA and to supercomputer users • Eventually, interconnection through NSF backbone to regional packet switched networks across USA • In 1990 ARPANET was shut down The Internet History (5) – Acceptable Use Policies • In many countries (including United States until 1995) national governments subsidized the Internet backbone • Acceptable use policies limited commercial activities —Research and educational (and of course government) use only —The “culture” of the Internet imposed additional informal limitations on commercial uses The Internet History (6) – Internet Interconnection Points • 1991 almost all commercial TCP/IP service in USA provided by: • General Atomics — Operated CERFnet (a California regional network) • Performance Systems International — PSINet (commercial spin-off from New York’s NYSERnet) • UUNET Technologies — Commercial Internet service provider that owned Alternet • Did not use NSF backbone on own networks — Not subject to Acceptable Use Policy • Communication between their networks did use NSF backbone — Under the policy The Internet History (7) – CIX • Commercial Information Interchange • Originally mechanism to interchange traffic at a West Coast router • Each network’s customers access customers on others’ networks at no extra charge • 1996, CIX had 147 member networks • No settlements — No traffic based fees for use • Similar interconnection point (1994) in England — London Internet Exchange (LINX) — 1996, it had 24 member networks • 1991, U.S. government said it would no longer subsidize Internet after 1995 • Mandated network access points • Now three, New York, Chicago, and San Francisco • Metropolitan area exchanges, MAE East and MAE West • U.S. part of Internet opened to commercial activity Figure 1.7 U.S. Internet Access Points The Internet History (8) – The World Wide Web • Spring 1989, at CERN (the European Laboratory for Particle Physics) • Englishman Tim Berners-Lee proposed a distributed hypermedia technology to exchange research findings over Internet • 1991 prototype World Wide Web (WWW or the Web) developed at CERN using NeXT computer as a platform • End of 1991, limited release of line-oriented browser or reader • Explosive growth came with first graphically oriented browser, Mosaic, 1993 — NCSA Center, University of Illinois — Mark Andreasson and others — Two million copies delivered over Internet — Now ubiquitous The Internet History (9) – What is the Web • Internationally distributed collection of multimedia files supported by clients (users) and servers (information providers) • Each file addressed in consistent manner using its Uniform Resource Locator (URL) • Viewed by clients using browsers — — — — E.g. Netscape Navigator, Microsoft’s Internet Explorer There are others! Usually graphical display and support for multimedia Move from file to file by clicking with mouse highlighted text or image (link) — Layout of display controlled by Hypertext Markup Language (HTML) — Embedded commands in text files — Specify fonts, colors, images and their placement and links • Hypertext Transfer Protocol (HTTP) — Protocol used in TCP/IP networks for fetching WWW files — More later The Internet History (10) – The Internet Today • Users connect through an Internet service provider (ISP) • Home users — Major online services such as America Online and Compuserve — Connect to ISPs over phone lines using modems at 56.6 kbps — OK for e-mail but marginal for graphics-intensive Web surfing — New alternatives include ISDN, ADSL, and cable modem • Work users — Workstations or PCs connected to LANs — LAN connects through trunks to ISP — T-1 or T-3 connection for large organizations — Smaller organizations may use 56 kbps or ISDN connections • ISPs connected by "wholesalers,“ — Network service providers • They interconnect using Internet connection points • T-3 rates or ATM connections The Internet History (11) – Commercial Use • Acceptable Use Policy limited early commercial use to research and educational — Some informational activities that could be considered marketing went on • First commercial applications were mainly informational — Sales, marketing, public relations • Electronic data interchange (EDI) — Intercompany invoices, billing, etc. — Designed for dedicated WAN • America Online, bulletin board type services dealing with technical and usage problems The Internet History (12) – Direct Sales • Initially Internet did not support online transactions well — No easy to use graphical user interface • World Wide Web not commonly available until 1993 • Initially little support for submitting information (forms) to server — No security — No effective payment systems — Credit card? — People uncomfortable sending credit card numbers over Internet — If information not encrypted it is easy to “listen in” — Several files of customer's credit card numbers on merchant’s computers have been compromised • Privacy concerns — “data mining,” • Collecting customer transaction information to improve targeting of marketing Figure 1.8 A Network Configuration Intranets • Implementation of Internet technologies within a corporate organization, rather than for external connection to the global Internet • Rapid prototyping and deployment of new services • Scales effectively • Virtually no user or developer training required — Services and user interfaces familiar from Internet • All platforms with complete interoperability • Open architecture — Lots of add-on applications available • Range of distributed computing architectures — Few central servers or many distributed servers • Support of "legacy" information sources — databases, word processing documents, groupware • Range of media types (audio, video, interactive applications) • Inexpensive to start Intranets and the Web • • • • Web has become universal information interface Management-employee communication Job-related information Departmental- and project-level information and services. — Set up Web pages to disseminate information and maintain project data • Easy to develop Web pages for specific needs • Connect Web service to database — Ease of administration — Deployment — Development speed — Flexible information presentation — Limited functionality — Stateless operation Figure 1.9 Web/Database Connectivity Other Intranet Technologies Electronic Mail • Electronic Mail —Most heavily used network application in corporate world —Attach documents multimedia to mail messages —Electronic mailing list • Alias with multiple destinations Other Intranet Technologies Network News or USENET • Collection of electronic bulletin boards • Work in similar way to Internet mailing lists • Subscribe to news group to you receive all messages posted to that group • May post message that available to all subscribers • Mechanics different from e-mail lists • Distributed network of sites that collect and broadcast news group entries • Need access to USENET node • Messages are archived at news sites — Organized by subject matter (thread) • Readily adapted to form an intranet news service Extranets • Makes use of TCP/IP protocols and applications — Especially the Web • Provides outside clients access to corporate resources — Suppliers and customers — Through the Internet or other networks • Security — Resources available to outside parties — Privacy and authentication concerns must be addressed • Access — Long-distance dial-up access — Internet access to intranet with security • Authentication of users and encryption of communications — Internet access to an external server • Duplicates some intranet data — Internet access to external server that originates database queries to internal servers — Virtual private network (VPN) Required Reading • Stallings, W. [2003], Computer Networks with Internet Technology, Prentice Hall, Upper Saddle River NJ. Chapter 1 • Web site for book: http://WilliamStallings.com/ • Any and all links from this site