* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download of the Internet
Network tap wikipedia , lookup
Distributed firewall wikipedia , lookup
Net neutrality law wikipedia , lookup
Airborne Networking wikipedia , lookup
Policies promoting wireless broadband in the United States wikipedia , lookup
Computer network wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Deep packet inspection wikipedia , lookup
Wireless security wikipedia , lookup
Internet protocol suite wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
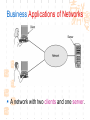
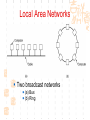
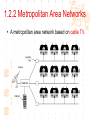
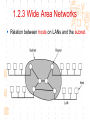
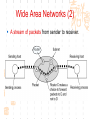
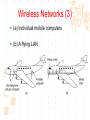
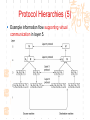
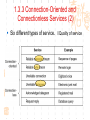
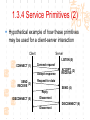
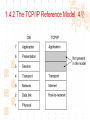
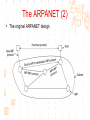
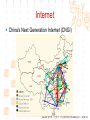
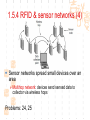
计算机网络与通信 授课班级: 软件工程111、112班 授课教师: 郑秋生 School of Computer Science Zhongyuan University of Technology http://www.cs.zzti.edu.cn [email protected] Sept. 2013 选用教材 计算机网络 Andrew S. Tanenbaum 第5版 严伟 潘爱民翻译 清华大学出版社 Computer Network Andrew S. Tanenbaum, 5th ,Prentice-Hall Inc. 影印版,清华大学出版社 参考资料 1、Andrew S. Tanenbaum, David J. Wetherall, “Computer Networks”, 5th Ed., 2010, AddisonWesley.该中文版的英文原版教材 2、James F. Kurose, Keith W. Ross, “Computer Networks: A Top-Down Approach”, 5th Ed., 2010, Addison-Wesley. 3、Larry L. Peterson, Bruce S. Davie, “Computer Networks: A System Approach”, 5th Ed., 2011, Elsevier. 4、 Computer Network and Internets, Douglas E. Comer, 5th, 2009. 参考资料 5、网络协议分析,寇晓蕤、罗君勇、蔡延荣 编著, 机械工业出版社,2009 6、计算机网络与因特网,第5版翻译,机械工业出 版社,2009 7、计算机网络,谢希仁,第6版,电子工业出版社 8、计算机网络课程设计,吴功宜等,机械工业出 版社,2005 9、Douglas Comer, “Internetworking With TCP/IP volume 1: Principles, Protocols, and Architecture”, 5th Ed., 2006, Pearson. The Most Important Journals IEEE-ACM Transaction on Networking: Bimonthly,ISSN: 1063-6692 IEEE NETWORK: Bimonthly,ISSN: 0890-8044 The Most Important Conferences ACM SIGCOMM: http://www.acm.org/sigcomm IEEE Infocom: http://www.ieee-infocom.org ACM SIGMETRICS: http://www.sigmetrics.org China Computer Federation CCF Evaluating academic achievement Class A is top important of journal and conference Class B is very important of journal and conference Class C is important of journal and conference http://www.ccf.org.cn/sites/ccf/paiming.jsp Websites and online courses http://www.computernetworks5e.org See: Video Lectures for CN5E Computer Networks MOOC Chapter 1 Introduction Chapter 1 Introduction Concepts: Computer Networks Distributed System World Wide Web Middleware Internet of Things 物联网 Uses of Computer Networks 1. Business Applications 2. Home Applications 3. Mobile Users 4. Social Issues Business Applications of Networks A network with two clients and one server. Business Applications of Networks (2) The client-server model involves requests and replies. Home Network Applications Access to remote information Digital Library: ACM,IEEE IM (Instant Message) Chat Room Person-to-person (P2P)communication Napster 电驴 Interactive entertainment Electronic commerce Home Network Applications (2) In peer-to-peer system there are no fixed clients and servers. Home Network Applications (3) Some forms of e-commerce. Mobile Network Users Combinations of wireless networks(无线 网络) and mobile computing.(移动计算) 1.2 Network Hardware Local Area Networks Metropolitan Area Networks Wide Area Networks Wireless Networks Home Networks Internetworks Broadcast (广播)Networks Types of transmission technology Broadcast links Point-to-point links Broadcast Networks (2) Classification of interconnected processors by scale. 1.2.1 Local Area Networks Three Characteristics: Size Transmission technology Topology Local Area Networks Two broadcast networks (a) Bus (b) Ring 1.2.2 Metropolitan Area Networks A metropolitan area network based on cable TV. 1.2.3 Wide Area Networks Relation between hosts on LANs and the subnet. Wide Area Networks (2) A stream of packets from sender to receiver. 1.2.4 Wireless Networks Categories of wireless networks: System interconnection Wireless LANs (802.11 a/b/g/n , Wi-Fi) Wireless WANs (802.16, Wi-Fi Max) GPRS、3G Wireless Networks (2) Bluetooth configuration (802.15) Wireless LAN (802.11) Wireless Networks (3) (a) Individual mobile computers (b) A flying LAN 1.2.5 Home Network Categories Computers (desktop PC, PDA, shared peripherals Entertainment (TV, DVD, VCR, camera, stereo, MP3) Telecomm (telephone, cell phone, intercom, fax) Appliances 家用电器 (microwave, fridge, clock, furnace, airco) Telemetry遥测设备 (utility meter 抄表, burglar alarm, babycam). 1.3 Network Software 从提出问题、解决问题的方法上理解、掌握 Protocol Hierarchies Design Issues for the Layers Connection-Oriented and Connectionless Services Service Primitives (服务原语) The Relationship of Services to Protocols 1.3.1 Protocol Hierarchies (1) The philosopher-translator-secretary architecture. • 复杂问题的 处理方法 • 分层思想 1.3.1 Protocol layers (2) Protocol layering is the main structuring method used to divide up network functionality. Physical communication – Each layer communicates only by using the one below – Lower layer services are accessed by an interface – At bottom, messages are carried by the medium – Each protocol instance talks virtually to its peer Layers, protocols, and interfaces. Virtual communication 1.3.1 Protocol layers (3) Each lower layer adds its own header (with control information) to the message to transmit and removes it on receiver Layers may also split and join messages, etc. 1.4.1 Protocol layers (4) Information transmission unit Protocol Hierarchies (5) Example information flow supporting virtual communication in layer 5. 1.3.2 Design Issues for the Layers 为什么会有这些问题?如何解决? Addressing Error Control Flow Control Multiplexing Routing 1.3.2 Design Issues for the Layers Each layer solves a particular problem but must include mechanisms to address a set of recurring design issues Issue Example mechanisms at different layers Reliability despite failures Codes for error detection/correction (§3.2, 3.3) Routing around failures (§5.2) Network growth and evolution Addressing (§5.6) and naming (§7.1) Protocol layering (§1.3) Allocation of resources Multiple access (§4.2) like bandwidth Congestion control (§5.3, 6.3) Security against various threats Confidentiality of messages (§8.6) Web security (§8.9) 1.3.3 Connection-Oriented and Connectionless Services (1) Connection-oriented must be set up for ongoing use (and torn down after use) e.g., phone call Connectionless messages are handled separately e.g., postal delivery 1.3.3 Connection-Oriented and Connectionless Services (2) Six different types of service. //Quality of service 1.3.3 Connection-Oriented vs. Connectionless (3) In connection-oriented service Establishes a connection, uses the connection, and then releases the connection. When a connection is established, negotiation has to do with getting both sides to agree on some parameters or values to be used during the communication. In the most cases the bits arrive to receiver in the order they were sent Message sequences vs. byte streams 1.3.3 Connection-Oriented vs. Connectionless (4) In connectionless service Store-and-forward switching vs. cut-through switching It is possible that the messages arrive to receiver out of order they were sent. Unreliable connectionless service is called datagram (数据报) Reliable service vs. unreliable service Must have acknowledgement (确认) or need not one 1.3.4 Service Primitives Five service primitives for implementing a simple connection-oriented service. 1.3.4 Service Primitives (2) Hypothetical example of how these primitives may be used for a client-server interaction Server Client LISTEN (0) CONNECT (1) Connect request Accept response SEND (3) RECEIVE ACCEPT (2) RECEIVE Request for data SEND (4) Reply DISCONNECT (5) Disconnect DISCONNECT (6) Disconnect 1.3.5 Services to Protocols Relationship The relationship between a service and a protocol. K层协议、K层服务 1.3.5 Services to Protocols Relationship A layer provides a service to the one above [vertical] A layer talks to its peer using a protocol [horizontal] 1.4 Reference Models 1. The OSI Reference Model 2. The TCP/IP Reference Model 3. A Comparison of OSI and TCP/IP 4. A Critique of the OSI Model and Protocols 5. A Critique of the TCP/IP Reference Model 自顶向下,自底向上的讨论、分析方法 1.4.1 The OSI Reference Model Provides functions needed by users Converts different representations Manages task dialogs Provides end-to-end delivery Sends packets over multiple links Sends frames of information Sends bits as signals 1.4.1 The OSI Reference Model A principled, international standard, seven layer model to connect different systems • The OSI reference model. • 理解:end to end 端到端 • 7层模型 1.4.2 The TCP/IP Reference Model 4层 1.4.2 The TCP/IP Reference Model A four layer model derived from experimentation omits some OSI layers and uses the IP as the IP is the “narrow waist network layer. 细腰” of the Internet Protocols are shown in their respective layers 1.4.3 Model used for this Course 5层 It is based on the TCP/IP model but we call out the physical layer and look beyond Internet protocols. 1.4.4 Critique of OSI & TCP/IP OSI + Very influential model with clear concepts Models, protocols and adoption all bogged down by politics and complexity TCP/IP + Very successful protocols that worked well and thrived (兴盛) Weak model derived after the fact from protocols A Critique 缺点 of the OSI Model and Protocols Why OSI did not take over the world Bad timing Bad technology Bad implementations Bad politics Bad Timing The apocalypse of the two elephants. A Critique(批评) of the TCP/IP Reference Model Problems: Service, interface, and protocol not distinguished Not a general model Host-to-network “layer” not really a layer No mention of physical and data link layers Minor protocols deeply entrenched, hard to replace 1.5 Example Networks The Internet 3G mobile phone networks Wireless LANs RFID and sensor networks The ARPANET (a) Structure of the telephone system. (b) Baran’s proposed distributed switching system. The ARPANET (2) The original ARPANET design. The ARPANET (3) Growth of the ARPANET (a) December 1969. (b) July 1970. (c) March 1971. (d) April 1972. (e) September 1972. NSFNET The NSFNET backbone in 1988. Internet Usage Traditional applications (1970 – 1990) E-mail News Remote login File transfer Architecture of the Internet Overview of the Internet architecture Internet Access network is the physical links that connect an end system to the edge router The technology includes ADSL Ethernet FTTH WiFi WiMAX Mobile communication … From KUROSE & ROSS, Computer Networking: A Top-Down Approach, 5th Edition Internet The modern Internet is more complex (1) ISP networks serve as the Internet backbone ISPs connect or peer to exchange traffic at IXPs Within each network routers switch packets Between networks, traffic exchange is set by business agreements Internet The modern Internet is more complex (2) Customers connect at the edge by many means Cable, DSL, Fiber-to-the-Home, 3G/4G wireless, dialup Data centers concentrate many servers (“the cloud”) Most traffic is content from data centers (esp. video) The architecture continues to evolve Internet ICANN (The Internet Corporation for Assigned Names and Numbers) announced ‘Available Pool of unallocated IPv4 Internet Addresses Now Completely Emptied’ in Feb. 3, 2011 US, EU (European Union), and Japan have scheduled for IPv4 to convert into IPv6 Internet Source: 邬贺铨, 《中国下一代互联网的研究和CNGI项目》, 2010.3.9 Internet China's Next Generation Internet (CNGI) Source: 邬贺铨, 《中国下一代互联网的研究和CNGI项目》, 2010.3.9 1.5.2 3G mobile phone(移动电话) networks (1) 3G network is based on spatial cells; each cell provides wireless service to mobiles within it via a base station 1.5.2 3G mobile phone networks (2) Base stations connect to the core network to find other mobiles and send data to the phone network and Internet Architecture of UMTS 3G network 1.5.2 3G mobile phone networks (3) As mobiles move, base stations hand them off from one cell to the next, and the network tracks their location Soft handover vs. hard handover (交接) Handover 1.5.2 3G mobile phone networks (4) Security SIM (Subscriber Identity Module) card Authentication Cryptographic keys on the chip are used to encrypt transmissions Encryption cell phone 3.5G 4G and WiMAX 1.5.3 Wireless LANs 8.2.11 Two different communication modes in 802.11 Infrastructure wireless LAN: Clients communicate via an AP (Access Point) that is wired to the rest of the network. Ad hoc (自组织)networks: clients can communicate directly in same radio rang. 1.5.3 Wireless LANs (2) Signals in the 2.4GHz ISM band vary in strength due to many effects, such as multipath fading (多经衰落) due to reflections requires complex transmission schemes, e.g., OFDM 1.5.3 Wireless LANs (3) Radio broadcasts interfere with each other, and radio ranges may incompletely overlap CSMA (Carrier Sense Multiple Access) designs are used 1.5.3 Wireless LANs (4) Mobility(移动性) Over a single 802.11 network Across different networks (IEEE 802.21) Security (802.11i) WEP (Wireless Equivalent Privacy 等效保密) was flawed and broken WPA2 (WiFi Protected Access 保护访问) WAPI (Wireless Authentication Privacy Infrastructure 认证与保密基础结构(): China standard (GB 15629) 通过互联网(百度百科、Wiki百科等), 了解以上技术 1.5.4 RFID & Sensor Networks (传感器网络)(1) networks everyday objectsPassive UHF(无源超高频) RFID Tags (stickers with not even a battery) are placed (or embedded) on objects Backscatter(反向散射体): readers send signals that the tags reflect to communicate 1.5.4 RFID & Sensor Networks (2) The Category of RFID Tags Passive (无源)RFID tags have neither an electric plug nor a battery. Active(有源) RFID has a power source in the tag. The Category Frequency of RFID UHF RFID (Ultra-High Frequency RFID) tags communicate at distance of several meters. It is used on shipping pallets and some drivers licenses. HF RFID (High Frequency RFID) is likely to be in the passports, credit cards, books, and noncontact payment systems. LF RFID (low Frequency RFID) is used for animal tracking. 1.5.4 RFID & Sensor Networks (3) The Problems in Using RFID Multiple tags in reading rage Like 802.11: wait for a short random interval Security Malware Virus 1.5.4 RFID & sensor networks (4) Sensor networks spread small devices over an area Multihop network: devices send sensed data to collector via wireless hops Problems: 24, 25 1.5.4 RFID & sensor networks (4) Sensor networks spread small devices over an area (2) The connections can be wired or wireless (Wireless) Mesh (网状) network The full mesh topology The partial mesh topology using self-healing(自愈 ) algorithms The figures from Wikipedia (Internet of Things)物联网 以物流为中心 不再是PC计算机节点 /IP编址,新的编址方法 比Internet的价值大30倍 中国的优势 起步早 参与标准的制定 物流环节完整 相关技术 无线网络、手机移动网、卫星网 GIS、WSN、RFID 系统的集成技术 物联网安全、物联网应用 通过互联网查资料,大家讨论IOT 1.6 Network Standardization Standards define what is needed for interoperability (互 操作性) Some of the many standards bodies Body Area Examples ITU Telecommunications G.992, ADSL H.264, MPEG4 IEEE Communications 802.3, Ethernet 802.11, WiFi IETF Internet RFC 2616, HTTP/1.1 RFC 1034/1035, DNS W3C Web HTML5 standard CSS standard IEEE 802 Standards The 802 working groups. The important ones are marked with *. The ones marked with are hibernating. The one marked with † gave up. 1.7 Metric Units The principal metric prefixes 1.8 The Future of Networks (1) Roadmap for the future of Web Source: 邬贺铨, 《中国下一代互联网的研究和CNGI项目》, 2010.3.9 1.8 The Future of Networks (2) Future Internet (1) There are different naming Future Internet Post IP network, etc. Design methods: clean slate vs. dirty slate Related national projects or programs (1) USA GENI (Global Environment for Network Innovations) FIND (Future Internet Design) FIA (Future Internet Architecture) 1.8 The Future of Networks (3) Future Internet (2) Related national projects or programs (2) EU FIRE (Future Internet Research and Experimentation) FIA (Future Internet Assembly) China CNGI 国家重点基础研究发展计划(973):面向服务的未来互 联网体系结构与机制研究 国家自然科学基金(NSFC):后IP网络体系结构及其机 理探索,未来网络体系结构与关键技术 1.8 The Future of Networks (4) Future Internet (3) Related International Standards ITU-T SG13 and FGFN (Focus Group on Future Networks) ISO JTC1/SC6 IETF ALTO WG (Application-Layer Traffic Optimization) LISP WG (Location-ID Separation Protocol) Multimob WG (Multicast Support for Proxy Mobile IPv6) LEDBAT WG (Low Extra Delay Background Transport) 1.8 The Future of Networks (5) Software Defined Networking (SDN) SDN separates the control plane from the data plane in network switches and routers OpenFlow is a leading SDN architecture Elastic(弹性) cloud architectures, dynamic resource allocation, mobile computing, and virtual machines need SDN 实验要求 教材 网络工程实训和实践应用教程 清华大学出版社 到学院资料室借阅 实验地点 计算机学院实验室 联系人:裴斐老师 实验时间 统一安排,再通知 实验要求 第1章 网络基础知识 第2章 综合布线 第3章 交换路由 第4章 Windows Server 2008操作系统 第5章 Linux操作系统管理及服务器配置 第6章 协议分析 第7章 网络测量 第8章 网络管理 第9章 网络安全 第10章 网络编程 第11章 故障排除 第12章 网络系统集成与规划设计 习题 课后习题 量大 有难度 先思考,自己做一下,再看习题答案 答疑 泛雅平台,网上答疑 课间





















































































![Introduction - start [kondor.etf.rs]](http://s1.studyres.com/store/data/000507900_1-4612cc6372b2ee158f9c52bcf8aea7c5-150x150.png)
![[slides] Introduction](http://s1.studyres.com/store/data/000071965_1-ad3bfbc03953cb954fa70b8bdbbdb4bb-150x150.png)





