* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download 08-Application File
Dynamic Host Configuration Protocol wikipedia , lookup
Extensible Authentication Protocol wikipedia , lookup
Server Message Block wikipedia , lookup
Deep packet inspection wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Cross-site scripting wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Remote Desktop Services wikipedia , lookup
SIP extensions for the IP Multimedia Subsystem wikipedia , lookup
Internet protocol suite wikipedia , lookup
Zero-configuration networking wikipedia , lookup
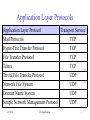
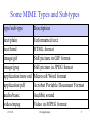
Application Layer Protocols Application Layer Protocol Transport Service Mail Protocols TCP Hyper-Text Transfer Protocol TCP File Transfer Protocol TCP Telnet TCP Trivial File Transfer Protocol UDP Network File System UDP Domain Name System UDP Simple Network Management Protocol UDP 2/11/10 08-Application 1 Mail Protocols • Simple Mail Transfer Protocol (SMTP) - for transmitting e-mails to a server and between servers • Post Office Protocol - Version 3 (POP3) – for retrieving emails from a server • Internet Mail Access Protocol (IMAP) – alternative improved protocol for retrieving e-mails • Multipurpose Internet Mail Extensions (MIME) – supports different formats for data attached to e-mails • ISO equivalent protocol is Message-Oriented Text Interchange Standard (MOTIS), also known as X.400 or Message Handling System (MHS) 2/11/10 08-Application 2 E-Mail Systems • E-mail systems involve user agents and message transfer agents (mail servers) • E-mail systems support 5 basic functions: – – – – – 2/11/10 Composition Transfer Reporting Displaying Disposition 08-Application 3 SMTP • Originally defined in RFC 822 in 1982 • Simple ASCII text based messaging protocol • Restricted to 7 bit ASCII code – binary data needs to be encoded in ASCII • Non-real time store and forward protocol • Messages comprise a header and a body • SMTP along with all other e-mail protocols requires a reliable transport service and runs over TCP 2/11/10 08-Application 4 RFC 822 Headers Fields related to Message Transfer © Tanenbaum, Prentice Hall International 2/11/10 08-Application 5 Other RFC 822 Headers Fields not related to Message Transfer © Tanenbaum, Prentice Hall International 2/11/10 08-Application 6 MIME • Multipurpose Internet Mail Extensions (MIME) – MIME is defined in RFC 2045 – It allows non-ASCII data, such as images, audio, video and 8 bit application data to be sent via e-mail – Data has to be encoded into ASCII and decoded at the receiving end – The type of data is indicated in a MIME header so that the user agent knows which application to use when asked to display/process the data – Mime data types are used by most other Internet applications 2/11/10 08-Application 7 RFC 822 Header Fields added by MIME © Tanenbaum, Prentice Hall International 2/11/10 08-Application 8 Some MIME Types and Sub-types type/sub-type Description text/plain text/html image/gif image/jpeg application/msword application/pdf audio/basic video/mpeg Unformatted text HTML format Still picture in GIF format Still picture in JPEG format Microsoft Word format Acrobat Portable Document Format Audible sound Video in MPEG format 2/11/10 08-Application 9 POP3 • Simple but limited mail access protocol • 3 phases – Authentication (username, password) – Transaction (user agent retrieves messages) – Update (server deletes messages, if required, after retrieval completed) • User Agent acts as a client to the Mail Server – 4 requests list, retr, dele, quit – 2 responses +OK, -ERR 2/11/10 08-Application 10 IMAP • Supports same functions as POP3, but has more features and is more complex • It allows mail folders to be stored on the server • IMAP is designed to support nomadic workers who want to access their e-mail from different machines • It allows users to retrieve headers, message bodies and individual parts of multipart MIME messages, thus conserving bandwidth on a low bandwidth connection 2/11/10 08-Application 11 Web-based E-mail • Introduced by Hotmail in the mid 1990s • User agent is a browser which retrieves messages from and sends messages to a Web Server using HTTP • Provides enormous convenience as all the user needs to access mail is a browser and an internet connection • Like IMAP messages can be organised into folders on the Server 2/11/10 08-Application 12 HTTP (Hyper-Text Transfer Protocol) • Client server protocol defined in RFC 1495 and RFC 2616 that allows a user agent (browser) to view web pages stored on Servers • A web page consists of a collection of objects stored in files on the server, such as HTML files, JPEG files, GIF files and Java applets. The main HTML file references the other objects to be displayed/processed using URLs • HTTP defines how the browser requests web pages from the server and how the server transfers web pages to the browser 2/11/10 08-Application 13 Uniform Resource Locators • URLs are used by browsers to reference web pages and other resources. They consist of three parts, usually of the form: protocol://hostname/resourcename:port number • In terms of web pages, the URL determines how the page can be accessed, where the page is located and what the page is called. Valid protocols are http, ftp, file, news, gopher, mailto or telnet. These are all supported in the address window of browsers 2/11/10 08-Application 14 HTTP Connections • HTTP requires a reliable transport service and runs over TCP connections. • Connections can be – Non-persistent (HTTP/1.0) • Only one object is transferred and the connection is then closed and a new transport connection opened to retrieve other referenced objects – Persistent (default, but configurable in HTTP/1.1) • Multiple objects can be transferred over the same transport connection which is closed after a timeout. This improves response times 2/11/10 08-Application 15 HTTP Pipelining • Persistent Connections can also support pipelining – Pipelining further improves response times by allowing the client to issue new requests before responses are received to earlier requests – Default mode of HTTP/1.1 is persistent with pipelining 2/11/10 08-Application 16 HTTP Requests • The HTTP Header has a Method field that indicates the type of request. • The most commonly used method is GET which requests the header and the body of the web page • If only the header is required the HEAD method is used 2/11/10 08-Application 17 HTTP Request Format © Kurose & Ross, McGraw Hill 2/11/10 08-Application 18 HTTP Responses • HTTP Responses include a status code and phrase – – – – – – 200 OK 301 Moved Permanently 400 Bad Request 401 Authorisation Required 404 Not Found 505 HTTP Version Not Supported • The server will generate header lines in the response appropriate to the version of HTTP indicated in the request 2/11/10 08-Application 19 HTTP Response Format © Kurose & Ross, McGraw Hill 2/11/10 08-Application 20 HTTP Authorisation • Web Servers do not normally store any state information about users (HTTP is said to be a stateless protocol) • Server responds with 401 Authorisation Required and specifies how to authenticate in a header field (E.g. username, password) • Browser prompts user for username and password • Browser resends the request and all subsequent requests to this server in an Authorisation header line 2/11/10 08-Application 21 HTTP Cookies • Web Servers do not normally store any information about their clients. • Web Servers can keep track of users by storing information, such as a user identifier on the client’s hard drive. This information is called a cookie • Web Servers store cookies with the Set-cookie header line • Clients transmit the cookie information whenever they make a subsequent request to the server using the Cookie header line 2/11/10 08-Application 22 HTTP Web Caching • Web pages can be cached locally by the browser and in proxy servers, to reduce response times and inefficiency of downloading recently accessed web pages • Browser can make sure it has the latest version of a page by using the If-modifiedsince header line with the time the page was cached 2/11/10 08-Application 23 File Transfer Protocol (FTP) • FTP is one of the original protocols designed for the Internet. It requires a reliable transport service and runs over TCP. It is used for uploading web pages • It has a command line interface and supports many complex functions • It sets up two TCP connections, one for commands and responses and the other for data transfer • Anonymous FTP uses anonymous as a username and by convention your e-mail address as the password • ISO equivalent protocol is File Transfer Access and Management (FTAM) 2/11/10 08-Application 24 Telnet • Telnet is a virtual terminal protocol that provides remote terminal access to a host. It runs over TCP • It is again one of the original protocols designed for the Internet • Telnet can translate between different character codes • It is extremely insecure. Usernames and passwords for remote login are transmitted without encryption • Firewall routers normally only forward telnet packets from known IP addresses • OSI equivalent protocol is Virtual Terminal (VT) 2/11/10 08-Application 25 Trivial File Transfer Protocol (TFTP) • TFTP is a lightweight simple file transfer protocol, designed for use over LANs with low error rates • It transmits one block of data and waits for an acknowledgement before sending any more data • It does not require a reliable transport protocol and runs over UDP 2/11/10 08-Application 26 Network File System • NFS was developed by Sun Microsystems for Unix but has been implemented for VMS, DOS, Windows and MVS. • It allows remote file systems (possibly using different operating systems) to be accessed as if they were local. • The physical location of directories and the remote operating system is hidden from the users • NFS makes use of Remote Procedure Calls (a simple client server request/response) which is best suited to running over UDP although it can be run over TCP in some implementations 2/11/10 08-Application 27 Domain Name System (DNS) • DNS is a Client Server Directory Service for translating between host names and IP addresses • The protocol consists of short request and response messages • DNS does not require a reliable transport service and runs over UDP • ISO equivalent protocol is Directory Access Protocol or X.500 2/11/10 08-Application 28 DNS Database • The DNS is a hierarchical distributed database reflecting the hierarchical structure of domains • Allocation of names is delegated to the Zones who are responsible for one or more domains who may delegate it further. Each Zone runs at least two DNS Servers • Top level domains are allocated by the Internet Corporation for Assigned Names and Numbers (ICANN) • Top level domains also exist for each country • ICANN coordinate 13 replicated root servers which know the authoritative servers for each top level domain 2/11/10 08-Application 29 The Domain Hierarchy © Tanenbaum, Prentice Hall International 2/11/10 08-Application 30 DNS Zones © Tanenbaum, Prentice Hall International 2/11/10 08-Application 31 DNS Name Resolution • The client (called the name resolver) will make a request to its local DNS server. If this has the name and address in cache it will return the IP address. Note: addresses will time out in cache at an interval determined by the administrator (typically 2 days) • Otherwise a request will be made to a higher level server or a root server which may have to refer the request down to its sub-domain servers. • The process will end either with an IP address being returned or an error message to say that the address could not be found 2/11/10 08-Application 32 Simple Network Management Protocol • SNMP is a simple protocol for managing network devices • SNMP is often implemented in simple network devices that cannot support a full and complex protocol stack. It therefore uses UDP as a transport service • SNMP uses ASN.1 encoding • The ISO equivalent protocol is the Common Management Information Protocol • SNMP will be studied in more detail in the second half of the course 2/11/10 08-Application 33