* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download PPT Version of Presentation Slides
Survey
Document related concepts
Transcript
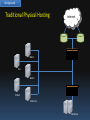
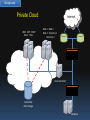
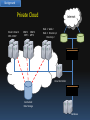
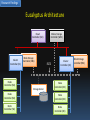
Investigating a Private Ubuntu Enterprise Cloud Suntisak Thammavongsa 28-11-2011 Bachelor of IT (Honours) Supervised by Dr Raymond Choo University of South Australia Outline Background Research Topic Research Method Research Findings Background Cloud Computing “A whole broad range of IT services as long as those IT services are delivered on demand and they’re delivered elastically in terms of being able scale out and scale in” defined by Dasmalchi (2010) Background Traditional Physical Hosting Internet Web 1 File Web 2 E-Mail Directory Database Background Private Cloud CRM APP DHCP Email DNS Internet Web 1 Web 2 Web 3 Directory 1 Directory 2 Cloud Controller Centralized Data Storage Database Background Private Cloud Email 1 Email 2 DNS DHCP CRM 1 CRM 2 APP 1 APP 2 Internet Web 1 Web 2 Web 3 Directory 1 Directory 2 Cloud Controller Centralized Data Storage Database Background Digital Forensics “The process of identifying, preserving, analysing and presenting digital evidence in a manner that is legally acceptable” defined by McKemmish (1999) Background Digital Forensics Primary questions • What happened? • When did it happen? • How did it happen? • Who was involved? Research Topic Investigate a private Ubuntu Enterprise Cloud v10.10 powered by Eucalyptus open source edition v2.0 SRQ1: What are the artefacts of interest? SRQ2: How to recover deleted artefacts? SRQ3: What are other sources of evidence? Research Method Desk-based • A more comprehensive literature review • To gain a deeper understanding of how the technology works Laboratory-based • Build a dual-node private cloud • Generate text files for a data recovery experiment Research Findings Eucalyptus Architecture Cloud Controller (CLC) Cluster Controller (CC) Block Storage Controller (EBS) Node Controller (NC) Storage Server Walrus Storage Controller (WS3) iSCSI Cluster Controller (CC) Node Controller (NC) Node Controller (NC) Node Controller (NC) Node Controller (NC) Node Controller (NC) Block Storage Controller (EBS) Research Findings SRQ1: What are the artefacts of interest? Linux system artefacts on Eucalyptus controllers • SWAP space under /proc • Linux logs under /var • Temporary files under /tmp Research Findings SRQ1: What are the artefacts of interest? Eucalyptus logs Cluster Controller (CC) cc.log, httpd-cc_error.log, registration.log Node Controller (NC) nc.log, httpd-nc_error.log, euca_test_nc.log Cloud Controller (CLC) cloud-debug.log, cloud-error.log, cloud-output.log, axis2c.log Elastic Block Storage Controller (EBS) sc-state.log, registration.log Walrus Storage Controller (WS3) walrus-state.log, registration.log Research Findings SRQ1: What are the artefacts of interest? Eucalyptus essential files Cloud Controller (CLC) $EUCALYPTUS/etc/eucalyptus.conf Cloud Controller (CLC) $EUCALYPTUS/var/lib/eucalyptus/db Cloud Controller (CLC) $EUCALYPTUS/var/lib/eucalyptus/keys Elastic Block Storage Controller (EBS) $EUCALYPTUS/var/lib/eucalyptus/bukkits Walrus Storage Controller (WS3) $EUCALYPTUS/var/lib/eucalyptus/volumes Research Findings SRQ1: What are the artefacts of interest? Virtual machine files • VM images & associated XML files on WS3 • Virtual hard disk files on NC User data files • User persistent data volumes on EBS • Snapshots of volumes on WS3 Research Findings SRQ2: How to recover deleted artefacts? • The process would be the same as the process in the traditional physical hosting • Each Eucalyptus controller is essentially a standard Linux server with Eucalyptus software • Data files are stored with EXT4 Research Findings SRQ2: How to recover deleted artefacts? If a forensic copy of the local storage of each Eucalyptus controller can be acquired, current forensic tools like EnCase can access and recover the following deleted files: • Linux system artefacts on Eucalyptus controllers • Eucalyptus logs • Eucalyptus essential files • VM images & associated XML files on WS3 • Virtual hard disk files on NC • Snapshots of volumes on WS3 Research Findings SRQ2: How to recover deleted artefacts? User data files on EBS volumes • Data files may be stored in different filesystems • The underlying hardware storage technology could be NAS, SAN, etc. Research Findings SRQ2: How to recover deleted artefacts? Artefacts inside virtual machines • Use VM ID to track down the NC • Recover virtual hard disk files • Recover deleted files on the virtual hard disk files Research Findings Summary of additional challenges Virtualization Dynamic nature of resource usage Increased number of nodes involved Centralised data storage Research Findings SRQ3: What are some other sources of evidence? Client side investigation • VNC, RDP, SSH, FireFox, etc. Live investigation • EnCase Enterprise • Virtual Introspection Network level monitoring • IDS, Firewall, WAF, etc. Thank you