* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Computer Forensics and Investigations
Survey
Document related concepts
Transcript
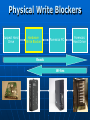
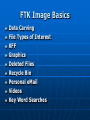
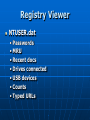
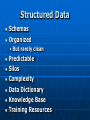
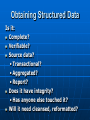
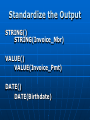
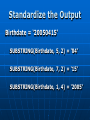
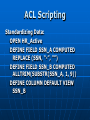
Digital Evidence Dean R. Beal CISA, CFE, ACE Allegation Anonymous Tip Ethics Line Risk Assessment Audit Continuous Auditing/Monitoring Allegation Fraud and/or Abuse: Breaches of Confidentiality Running a Personal Business Pornography Sharing Copyrighted Material Travel and Business Expenses Unlicensed Software Use Time and Attendance Harassment Bribery Theft Discrimination Assessing the Allegation Management: • Receives • Reviews • Assigns Guidelines: • Should exist for outlining the steps taken for obtaining digital evidence to support an investigation Assessing the Allegation Support a Non IT Investigation Complete an IT Investigation Obtaining Digital Evidence Identification of: • Person(s) Desktops/laptops Mobile devices External drives Network shares • Location(s) Network Segment • Ping • Doors accessed • Connectivity • Bandwidth Obtaining Digital Evidence Keep it Confidential • Only those with a “Need to Know” Physical Confiscation • Unplug, remove batteries • External storage devices • Digital camera • Chain of custody forms • Check in and under everything • Evidence bags • Document everything Unstructured Data No Schemas No Organization Unpredictable Make Note of: • Obvious • Not so obvious Piece the puzzle from the outside-in Start in the Forest • Don’t get lost in the trees… yet Searching Unstructured Data Internet eMail Instant Messenger Digital Forensics • Servers • Desktops • Laptops • Mobile Devices Searching the Internet Open Connection •No affiliation Use Alias: •eMail address •Profiles •User IDs Searching the Internet Web Reporting Google Hacking • “intext:” • “filetype:” Blogs Deep Web Public Records Social Media Searching eMail & IM Right to Privacy? • Warning banners Real-time Journaling Back-ups • .pst • .nsf “Fly Over” Items of potential importance Key words Searching eMail & IM Can See It All • Interesting differences between professional and personal personas Everything is Fair Game What’s Happening? • Substantiated? • More information needed? • Take notes Digital Forensics Network “Snapshot” Physical “Static” ProDiscover Can connect to any computer on the network • By IP address • By computer name Installs remote agent executable Runs in the background as a Service Captures image of hard drive over the network • Deleted files • Everything ProDiscover User does not know they are being imaged Connected external drives can be accessed Timing All or nothing Unix dd image format Slower processing time • Network location FTK Imager Physical drive dd Image E01 Image Format Segments Faster Processing • Physical device Physical Write Blockers http://www.forensicpc.com/products.asp?cat=38 Physical Write Blockers Suspect Hard Drive Hardware Write Blocker Forensics PC Reads Writes Forensics Hard Drive Hash Values Original MD5 Hash Value: 6f8e3290e1d4c2043b26552a40e5e038 Imaged MD5 Hash Value: 6f8e3290e1d4c2043b26552a40e5e038 :Verified MD5 Hashes • Image Level • File Level FTK Image Basics Data Carving File Types of Interest KFF Graphics Deleted Files Recycle Bin Personal eMail Videos Key Word Searches DTSearch Indexed • Faster searching And – both required Or – either required Not w/# - within number of words ? – any character * - any number of characters ~ - stems (good for tenses) % - fuzzy (good for misspellings) & - synonyms Regular Expressions Not Indexed • Slower Searching Social Security numbers Credit card numbers Phone numbers IP addresses Literal vs. operational • x vs.\x • d vs.\d \<\d\d\d\d(\-| )\d\d\d\d(\-| )\d\d\d\d(\-| )\d\d\d\d\> FTK Image Advanced Password Protected Files Encrypted Drives Data Wiping Missing File Headers index.dat Metadata Prefetch Link Files (LNK) Other Registry Artifacts Registry Viewer NTUSER.dat • Passwords • MRU • Recent docs • Drives connected • USB devices • Counts • Typed URLs Passwords/Encryption Password Recovery Toolkit (PRTK) • Dictionary • Decryption • Brute force • Export NTUSER.dat Distributed Network Attack (DNA) Full Disk Encryption • Decryption key needed Accountability Filter on: Username Relative Identifier (RID) • Security Identifier (SID) • Security Accounts Manager (SAM) Oxygen Forensic Suite Tool Capabilities are Device Specific Device Drivers Needed Chargers/Connectors Media Cards Passwords/PIN#s Remote Wiping Oxygen Forensic Suite eMail Text Messages Phonebook/Contact List Calendar Call History Pictures/Videos Social Network Messages Internet Sites Oxygen Forensic Suite Logical Analysis Physical Analysis Logical/Physical Analysis • SQLite, Plist, IPD file viewers Backup File Creation Mobile Device Storage Write Blockers Unstructured Data as Digital Evidence Actions Accountability Dates and Times Tie to Source Information • eMail & IM to image • Internet to image • Mobile device to image Structured Data Schemas Organized • But rarely clean Predictable Silos Complexity Data Dictionary Knowledge Base Training Resources Obtaining Structured Data Is it: Complete? Verifiable? Source data? • Transactional? • Aggregated? • Report? Does it have integrity? • Has anyone else touched it? Will it need cleansed, reformatted? Obtaining Structured Data Is it: • Hierarchal? • Relational? • Fixed length? • Variable length? • Delimited? • Mainframe? • HL7? • EDI? Obtaining Structured Data Learn Application and System Process and Data Flows Obtain Access to the Application Obtain Direct Access to the Source Data Learn the Query Language Admit You’re in Over Your Head Make Friends with IT • Ask for help • Without loss of confidentiality Involve IT • Legacy • Require confidentiality Obtaining Structured Data Source Systems: • • • • DB2 Oracle SQL Server Mainframe Querying Tools: • TOAD • QMF • Proprietary reporting tools No direct access available Obtaining Structured Data Structured Query Language (SQL) • Fairly standard across most platforms Some variations • PLSQL • TSQL Databases • Schemas Tables Normalization Fields/columns Primary keys Foreign keys Obtaining Structured Data Individual tables won’t always give you meaningful information Relating those tables by primary and foreign keys, provides meaningful information Obtaining Structured Data Tweak and Utilize Existing SQL Write Your Own • Can be time consuming Trial and Error Reconcile Back to Application Have Others Validate the Results • Back to source documentation if available Obtaining Structured Data Some Enterprise Databases contain 30,000+ Tables • Data dictionaries should exist • Determine the individual tables containing needed data • Determine the primary and foreign key(s) to create the join(s) Write the SQL statement(s) Obtaining Structured Data Joins are the Drivers • Inner Join All records in Table B that have a match in Table A • Outer Join (Left or Right) All records in Table A with or without a Match in Table B, and only those records in Table B that have a match in Table A • Cartesian Join Something is wrong Obtaining Structured Data When Querying Enterprise Databases: • Only what is necessary • Not all columns/records • No aggregating • Apply date parameters • Watch the processing time Something may be wrong with the SQL • Edit and repeat • Tie to source information Information to Evidence Microsoft Access & Excel ACL • Reformatting • Appending • Computed fields • Aggregating • Querying • Reporting Structured Data as Digital Evidence Append the Output • Like data from differing sources rarely matches Cleansing Re-formatting Reconcile to Source Data • Control totals • Record counts Create New Functionality • Computed fields • Get to the answer Standardize the Output Social Security Numbers Birthdates Addresses Names Phone Numbers Zip Codes Standardize the Output ACL creates its own “view” of the source data file with the .fil extension .fil is “read only” Source Data Remains Untouched Standardize the Output STRING() STRING(Invoice_Nbr) VALUE() VALUE(Invoice_Pmt) DATE() DATE(Birthdate) Standardize the Output Birthdate = ‘20050415’ SUBSTRING(Birthdate, 5, 2) = ‘04’ SUBSTRING(Birthdate, 7, 2) = ‘15’ SUBSTRING(Birthdate, 1, 4) = ‘2005’ Standardize the Output If you aren’t going to add, subtract, multiply, divide, or calculate the field, format it as Text If you are going to add, subtract, multiply, divide, or calculate the field, format it as Numeric or Date Structured Data as Digital Evidence Actions Accountability Dates and Times Tie to Source Information Control Weaknesses • Segregation of duties • Approval limits • Lack of oversight Presenting the Digital Evidence Report Preparation • Unstructured information • Structured information Support the Allegation(s) Refute the Allegation(s) Consult with Law Consult with Management Consult with Senior Executives CAATs Direct Access and the Right Tools Reactive • Ad-hoc Proactive • Automate • Take what’s been learned and apply to the entire population • 100% Testing • Exception based ACL Scripting Series of commands stored as a unit in an ACL project Executed repeatedly and automatically Any ACL command can be stored as a script 302|Advanced ACL Concepts & Techniques, SCRIPTS (CANADA: ACL Services Ltd, 2006), 2. ACL Scripting Standardizing Data: OPEN HR_Active DEFINE FIELD SSN_A COMPUTED REPLACE (SSN, “-”, “”) DEFINE FIELD SSN_B COMPUTED ALLTRIM(SUBSTR(SSN_A, 1, 9)) DEFINE COLUMN DEFAULT VIEW SSN_B ACL’s Audit Analytic Capability Model LEVEL 1 – BASIC • Audit specific • Classifications • Summarizations • Duplicates • Ad hoc The ACL Audit Analytic Capability Model: Navigating the journey from basic data analysis to continuous monitoring, WHITE PAPER (ACL Services Ltd, 2011), 3. ACL’s Audit Analytic Capability Model LEVEL 2 – APPLIED • Specific and repeatable tests • Start with “low hanging fruit” • Add additional and broader tests • Focus on data access • Efficient script design for repeatability The ACL Audit Analytic Capability Model: Navigating the journey from basic data analysis to continuous monitoring, WHITE PAPER (ACL Services Ltd, 2011), 5. ACL’s Audit Analytic Capability Model LEVEL 3 – MANAGED • Centralized, secure, controlled, efficient data analysis • Many people involved • Processes and technology in place • Server environment • Multiple locations The ACL Audit Analytic Capability Model: Navigating the journey from basic data analysis to continuous monitoring, WHITE PAPER (ACL Services Ltd, 2011), 7. ACL’s Audit Analytic Capability Model LEVEL 4 – AUTOMATED • Comprehensive suites of tests developed • Tests scheduled regularly • Concurrent, ongoing auditing of multiple areas • More efficient and effective audit process The ACL Audit Analytic Capability Model: Navigating the journey from basic data analysis to continuous monitoring, WHITE PAPER (ACL Services Ltd, 2011), 10. ACL’s Audit Analytic Capability Model LEVEL 5 – MONITORING • Progress from continuous auditing to continuous monitoring • Expanded to other business areas • Process owners notified immediately of exceptions The ACL Audit Analytic Capability Model: Navigating the journey from basic data analysis to continuous monitoring, WHITE PAPER (ACL Services Ltd, 2011), 12. Forensics Lab Physical Security Logical Security • SSNs • Credit card numbers Software Licensing • Updates, upgrades Hardware and Other Peripherals Storage • Short term, long term • Enough? Forensics Lab Forensic Workstation • Processing workhorse SSD Memory JBOD Forensic Desktop • Secondary processing • Image reviewing Forensics Laptops Open Internet Laptop • Don’t do this on the company network Forensics Lab Retention Inventory Back-ups and Recovery • On-site, off-site Chain of Custody • Physical • Image Data Wiping and Verification CIA COBIT Challenges Time Consuming Satellite Locations Emerging Technologies System Processing/Data Flows • Lack of documentation Cloud Computing Hard Drive Capacities Anti Forensics Challenges External Storage Devices Personal vs. Corporate • BYOD False Positives Data Silos Data Integrity Passwords Encryption Summary Mixture of Art and Science • Intuition • Common sense • Knowledge and use of tools • Persistence • Testing Theories • Research • Learning Conclusion No One Solution Expect the Unexpected Remain Fair and Objective Report Just the Facts Questions?