* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Configuration - Quest Software
Computer network wikipedia , lookup
Network tap wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Dynamic Host Configuration Protocol wikipedia , lookup
Deep packet inspection wikipedia , lookup
Remote Desktop Services wikipedia , lookup
Wireless security wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Distributed firewall wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
SonicWALL Global Management System
Configuration Guide
Standard Edition
Version 2.9.4
Copyright Information
© 2005 SonicWALL, Inc. All rights reserved.
Under copyright laws, this manual or the software described within may not be copied, in whole or part, without the
written consent of the manufacturer, except in the normal use of the software to make a backup copy. The same proprietary and copyright notices must be affixed to any permitted copies as were affixed to the original. Under the
law, copying includes translating into another language or format.
SonicWALL is a registered trademark of SonicWALL, Inc.
Other product and company names mentioned herein may be trademarks and/or registered trademarks of their
respective companies.
Specifications and descriptions are subject to change without notice.
Part Number: 232-000673-01
Rev A 09/2005
Software License Agreement for
SonicWALL Global Management System
To review the SonicWALL Global Management System Software License Agreement, see the SonicWALL Global Management System Introduction Guide.
CONTENTS
Section I
Initial Configuration of SonicWALL GMS and SonicWALL Appliances
Chapter 1 Introduction
Chapter 2 Configuring SonicWALL Appliances for Management
Manually Configuring SonicWALL Appliances
Updating Firmware
Enabling Remote Management
Configuring SonicWALL Appliances Using the Wizard
Enabling Remote Management
Modifying Remote Management Settings
PortShield Support for the SonicWALL PRO 1260
Chapter 3 Creating Groups and Adding SonicWALL Appliances
Creating SonicWALL Fields and Views
Creating Custom Fields
SonicWALL Fields
Setting Up Views
Changing Views
Adding SonicWALL Appliances to SonicWALL GMS
Modifying SonicWALL Appliance Management Options
Changing Agents or Management Methods
Importing SonicWALL Appliances
Registering SonicWALL Appliances
Moving SonicWALL Appliances Between Groups
Inheriting Group Settings
Embedded Login Support
Chapter 4 SonicWALL GMS User Management
Overview
Creating User Groups
Configuring Screen Access
Configuring Unit, View, and CLI Actions
Adding Users
Configuring Screen Access
Configuring Appliance Access
Configuring Unit, View, and CLI Actions
Chapter 5 Locating Devices
Left-Pane Navigational Tree
Find
3
5
6
6
6
8
8
20
21
25
25
25
27
27
29
30
33
35
36
38
39
40
40
41
41
42
42
43
45
46
47
48
49
49
50
Section II
SonicWALL Appliances
iii
Chapter 6 Configuring and Maintaining SonicWALL Appliances
53
Chapter 7 Configuring System Settings
55
Configuring Time Settings
Configuring Administrator Settings
Configuring Contact Information
Saving and Applying SonicWALL Settings
Viewing Diagnostic Information
Viewing Connections Monitor
Viewing CPU Monitor
Viewing Process Monitor
Configuring Simple Network Management Protocol
Viewing CA Certificates
Chapter 8 Using SonicWALL Tools
Restarting SonicWALL Appliances
Requesting Diagnostics for SonicWALL
Inheriting Group Settings
Clearing the ARP Cache
Synchronizing Now
Synchronizing with mysonicwall.com
Chapter 9 Configuring Network Settings
Configuring Network Settings
Transparent or Standard Mode
NAT-Enabled Mode
NAT with DHCP Client Mode
NAT With PPPoE Client
NAT With L2TP Client
NAT With PPTP Client
Configuring Web Proxy Settings
Configuration
Configuring Intranet Settings
Configuration
Configuring Routes
Configuring Routing Information Protocol
Configuring DMZ (HomePort) Addresses
Configuration
Configuring One-to-One Network Address Translation
Configuration
Configuring Ethernet Settings
Configuring ARP
Chapter 10 Configuring Network Settings for SonicOS Enhanced
Configuring Interface Network Settings
Virtual Interfaces (VLAN)
Configure Interface Settings
Configuring VLAN Sub-Interfaces
WAN Failover and Load Balancing
Configuring Zones
Configuring DNS
Configuring Dynamic DNS
Configuring Address Objects
Creating an Address Object
Network Address Object Deletion
iv
SonicWALL Global Management System Configuration Guide
55
57
58
59
61
63
65
66
67
68
69
69
70
71
72
73
74
75
75
76
77
78
79
80
81
83
83
84
84
85
86
87
87
88
89
90
91
93
94
94
95
99
101
103
104
105
107
107
109
Creating an Address Object Group
Configuring Network Address Translation
Common Types of Mapping
SonicWALL NAT Policy Fields
Common Configuration Types
Configuring NAT Policies
Configuring Web Proxy Forwarding Settings
Configuring Policy-Based Routing
Configuring Routing Information Protocol
Configuring Advanced Routing Services
Configuring RIP
Configuring OSPF
Configuring Global RIP Configuration
Configuring Global OSPF Configuration
Configuring IP Helper
Configuring ARP
Static ARP Entries
Secondary Subnets with Static ARP
Flushing the ARP Cache
Navigating and Sorting the ARP Cache Table Entries
Chapter 11 Configuring Firewall Settings
Understanding the Network Access Rules Hierarchy
Defining Firewall Rules
SonicOS Enhanced
SonicOS Standard
Configuring Advanced Access Settings
Configuring Voice over IP Settings
Configuring Multicast Settings
Chapter 12 Configuring Log Settings
Heartbeat Settings on the Enhanced Log Settings Page
Chapter 13 Configuring SonicWALL QoS
Working with Classification
Working with Marking
Working with Conditioning
Working with 802.1p and DSCP QoS
Enabling 802.1P
Working with DSCP Marking
DSCP Marking and Mixed VPN Traffic
Configuring QoS
Enabling 802.1p Tagging
Creating a QoS Rule
Configuring QoS Settings
Chapter 14 Configuring Website Blocking
Configuring General Website Blocking Options
Selecting the Content to Block
Content Filter List
Content Filter Service
Controlling Access to Specific Domains
Deleting Domains from the Domain Lists
Blocking Access to Domains by Keywords
Blocking Web Features
109
110
111
111
111
112
113
114
116
118
119
120
122
122
123
124
125
125
125
126
127
128
128
128
135
139
140
141
143
145
147
147
148
148
149
149
150
151
151
151
152
154
155
156
157
157
159
165
166
167
168
v
Consent
Websense and N2H2 Content Filtering
N2H2
Websense
Chapter 15 Configuring Dynamic Host Configuration Protocol
Configuring DHCP Over VPN
Configuring Dynamic DHCP IP Address Ranges
Configuring Static IP Addresses
Chapter 16 Configuring User Settings
Configuring Users
SonicOS Enhanced
SonicOS Standard
SonicOS Enhanced
Authentication Method
Configuring User Level Authentication Settings
Configuring RADIUS Authentication
Active Directory / LDAP Authentication
Global User Settings
Acceptable Use Policy
Chapter 17 Configuring Virtual Private Networking
Configuring VPN
Enabling VPN
Configuring Security Associations
Internet Key Exchange Using SonicWALL Certificates
Internet Key Exchange Using Third-Party Certificates
Internet Key Exchange Using Pre-Shared Secret
Manual Keying
Configuring VPN to Receive L2TP Connections
Monitor VPN Connections
Management of VPN Client Users
Enabling the VPN Client
Downloading VPN Client Software
Basic Terms and Concepts
173
173
175
177
179
179
179
183
185
185
185
186
187
195
195
197
198
198
200
200
206
212
217
221
222
223
223
223
224
Chapter 18 Configuring Virtual Private Networking 2.0
229
Configuring VPN
Interconnected Mode
Non-Interconnected Mode
Configuring VPN to Receive L2TP Connections
Monitoring VPN Connections
Managing VPN Client Users
Enabling the VPN Client
Downloading VPN Client Software
229
229
232
235
236
237
237
237
Chapter 19 Configuring Security Services
Overview of Anti-Virus Protection
Configuring Anti-Virus Settings
Changing Anti-Virus Password
Configuring Anti-Virus Settings
Configuring Anti-Virus Email Filter Settings
Overview of IPS
SonicWALL IPS Features
vi
169
171
171
172
SonicWALL Global Management System Configuration Guide
239
240
241
241
242
243
245
245
SonicWALL Deep Packet Inspection
246
How SonicWALL’s Deep Packet Inspection Architecture Works246
SonicWALL IPS Terminology
247
Configuring Intrusion Prevention Services
248
Enabling Intrusion Prevention Services
248
Manual Upload of Keyset and Signature Files
250
Configuring Global Security Client Security Settings
252
Accessing the Policy Editor
252
Configuring the Policy Editor
253
SonicWALL Anti-Spyware Overview
258
SonicWALL Anti-Spyware Service
258
SonicWALL Gateway Anti-Virus, Anti-Spyware and
Intrusion Prevention Security Services
259
Activating the SonicWALL Anti-Spyware License
260
Setting Up SonicWALL Anti-Spyware Protection
261
Enabling SonicWALL Anti-Spyware
263
Specifying Spyware Danger Level Protection
263
Applying SonicWALL Anti-Spyware Protection to Zones (Enhanced)263
Configuring Signature Settings
266
Licenses and Subscription Search Capability
268
Licenses and Subscription Search Capability
271
Chapter 20 Configuring Hardware Failover Settings
275
Chapter 21 Configuring Web Filters
(Content Security Manager 2100 CF)277
Configuring Web Filters (Content Security Manager 2100 CF)
Configuring Settings
Settings
IP Address Exclusion List
URL Rating Review
Configuring Policy Groups
Policy Groups Table
Modifying the *Default Policy Group
Configuring Policies
Policies Table
Configuring Custom Categories
Untrusted URLs
Untrusted Keywords
Trusted URLs
Configuring Privacy Prevention
Privacy Threats
Untrusted File Types
Privacy Threat Exclusion List
Configuring Custom Block Page
Message to Display when Blocking
Chapter 22 Configuring SonicPoints
Managing SonicPoints
Before Managing SonicPoints
SonicPoint Provisioning Profiles
Configuring a SonicPoint Profile
SonicPoint G Support
Updating SonicPoint Settings
SonicPoint G Support
277
278
279
279
279
279
280
280
281
281
281
282
282
282
283
283
283
284
284
284
287
287
287
288
288
292
294
295
vii
SonicPoint WLAN Scheduling
Updating SonicPoint Firmware
Automatic Provisioning (SDP & SSPP)
Viewing Station Status
Event and Statistics Reporting
Using and Configuring SonicPoint IDS
Detecting SonicPoint Access Points
Wireless Intrusion Detection Services
Chapter 23 Configuring Wireless Options
Configuring General Wireless Settings
Wireless Radio Operating Schedule
Configuring WEP Encryption Settings
Configuring Advanced Wireless Settings
Configuring MAC Filter List Settings
Configuring Intrusion Detection Settings
Configuring Wireless Guest Services
Configuring General Wireless Guest Services Settings
Configuring the URL Allow List
Denying Access to Networks
Configuring the Custom Login Screen
Chapter 24 Configuring Dialup Options
297
297
297
298
298
299
299
299
301
301
302
302
303
305
306
307
307
308
308
309
311
Configuring the Dialup Profile
Configuring Dialup
311
313
Chapter 25 Upgrading SonicWALL Appliances
315
Upgrading Firmware
Firmware File Naming Convention
Upgrading SonicWALL Appliances
Purchasing Upgrades
Activating the Upgrades
Applying the Upgrades
Creating License Sharing Groups
Creating VPN Client License Sharing Groups
Creating Anti-Virus License Sharing Groups
Viewing Used Activation Codes
315
316
317
317
317
318
319
319
322
327
Section III
SonicWALL GMS Configuration and Maintenance
Chapter 26 Configuring and Working with SonicWALL GMS
Configure SonicWALL GMS User Settings
Configuring SonicWALL GMS Report Settings
Deleting the SonicWALL GMS Logs
Viewing the SonicWALL GMS Log
Working with SonicWALL GMS Tasks
Scheduling Tasks at the Time of Task Configuration
Managing SonicWALL GMS
Configuring GMS Management Settings
Configuring Alert Notification Settings
Managing Sessions
Managing Agent Configurations
Configuring SNMP Settings
viii
SonicWALL Global Management System Configuration Guide
331
331
332
334
335
336
337
338
338
339
340
341
342
Configuring Inheritance Settings
Configuring the Message of the Day Settings
Upgrading SonicWALL GMS
Upgrading a Demo License to a Retail License
Upgrading the Node License
Activating SonicWALL GMS Support
Synchronize with mysonicwall.com
Log into Mysonicwall.com
Configuring Debug Log Settings
Performing a System Snapshot
Performing the Snapshot
Viewing the Snapshot or Diagnostics
Applying SonicWALL GMS Updates
Running Patches from the GUI
Updating SonicWALL GMS Registration
Working with Capacity Planning
Chapter 27 Configuring and Working with SonicWALL GMS
GMS Navigation Tool
VPN Monitor
Net Monitor
Configuring the Net Monitor
Adding Devices to the Net Monitor
Managing Realtime Monitors
Managing Severity and Thresholds
Adding Custom Icons to the Net Monitor
Real-Time Syslog
Drive Mapping Problems
Windows Processes
Starting or Stopping Processes
UNIX Processes
Starting or Stopping Processes
Using an Existing VPN Tunnel
Using a Proxy Server
Using a Multihomed SonicWALL GMS Server
SQL Server Error Messages
Oracle Error Messages
343
344
346
346
347
348
349
350
351
352
352
353
355
356
357
357
359
360
361
363
363
366
371
374
378
378
382
383
383
383
383
385
385
386
389
389
ix
x
SonicWALL Global Management System Configuration Guide
Section I
Initial Configuration of SonicWALL GMS and
SonicWALL Appliances
CHAPTER 1
Introduction
This guide is designed to help you configure the SonicWALL Global Management System (SonicWALL GMS). If
you have not used SonicWALL GMS before, you may want to familiarize yourself with some of the
SonicWALL GMS concepts and features. For more information, see the SonicWALL Global Management System
Introduction Guide.
Before configuring SonicWALL GMS, it must be properly installed. For more information, see the SonicWALL
Global Management System Installation Guide.
Introduction
3
4
SonicWALL Global Management System Configuration Guide
CHAPTER 2
Configuring SonicWALL Appliances for Management
Before managing SonicWALL appliances from SonicWALL Global Management System (SonicWALL GMS), you
must configure them for SonicWALL GMS management and add them to SonicWALL GMS user interface.
This chapter describes how to set up new or currently configured SonicWALL appliances for SonicWALL GMS
management. Select from the following:
•
•
To configure existing SonicWALL appliances for management by SonicWALL GMS, see “Manually Configuring SonicWALL Appliances” on page 6.
To prepare new SonicWALL appliances for SonicWALL GMS, see “Configuring SonicWALL Appliances
Using the Wizard” on page 8.
Configuring SonicWALL Appliances for Management
5
Manually Configuring SonicWALL Appliances
Before an existing SonicWALL appliance can be administered from the SonicWALL GMS user interface (UI), the
following must occur:
The firmware must be updated to a version that is compatible with SonicWALL GMS. For more information,
see “Updating Firmware,” below.
• Remote management must be enabled on the SonicWALL appliance. For more information, see “Enabling
Remote Management” on page 6.
•
After you have completed these steps, add the SonicWALL appliance to the SonicWALL GMS UI as outlined in
“Adding SonicWALL Appliances to SonicWALL GMS” on page 30.
Updating Firmware
SonicWALL appliances that are managed by SonicWALL GMS must be running firmware version 6.1.1.0 or later
or SonicOS firmware version 2.0.1.3 or later. For information on updating firmware, refer to the SonicWALL appliance’s documentation.
Enabling Remote Management
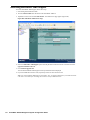
To configure the SonicWALL appliance to be remotely managed by SonicWALL GMS, follow these steps:
1. Log into the SonicWALL appliance.
2. Click System in the left pane.
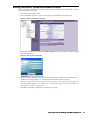
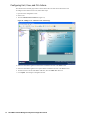
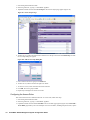
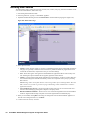
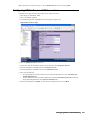
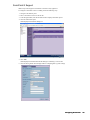
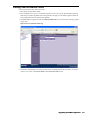
3. Select the Administration folder. The Administration page appears (Figure 1).
4. Scroll down to the Advanced Management section.
Figure 1: Administration Page
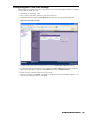
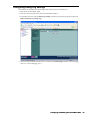
5. Select The Enable Management using GMS check box.
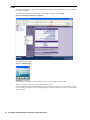
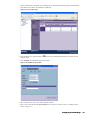
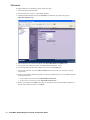
6. Click Configure. The Configure GMS Settings dialog box appears (Figure 2).
6
SonicWALL Global Management System Configuration Guide
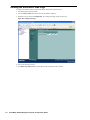
Figure 2: Configure GMS Settings Dialog Box
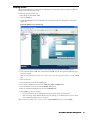
7. Configure the following options:
•
•
•
GMS Host Name or IP Address—IP address or host name of the SonicWALL GMS server.
GMS Syslog Server Port—syslog server port (default: 514).
GMS behind NAT Device—specifies whether the SonicWALL GMS server is behind a NAT device. If so,
enter the IP address in the NAT Device IP Address field.
8. Select one of the following from the Management Mode list box:
IPSec Management—if the SonicWALL appliance will be managed through a VPN management tunnel
(default), configure the following fields:
• Encryption Algorithm—select Encrypt and Authenticate (DES MD5).
• Encryption Key—16-character encryption key. The key must be exactly 16 characters long and composed of hexadecimal characters. Valid hexadecimal characters are “0” to “9”, and “a” to “f” (i.e., 0, 1,
2, 3, 4, 5, 6, 7, 8, 9, a, b, c, d, e, f). For example, a valid key would be “1234567890abcdef.”
• VPN Policy Bound to—select Interface WAN.
• Authentication Key—32-character authentication key. The key must be exactly 32 characters long and
composed of hexadecimal characters. For example, a valid key would be
“1234567890abcdef1234567890abcdef.”
• Management through Existing VPN Tunnel—if the SonicWALL appliance will be managed through an
existing tunnel or is on the same network as the SonicWALL GMS server, no further configuration is necessary. Continue to the next step.
• HTTPS Management—if the SonicWALL appliance will be managed using HTTPS, specify whether the
SonicWALL GMS uses a separate GMS Reporting server that collects syslog data.
•
If so, select the Send Syslog Messages to a Distributed GMS Reporting Server check box and enter the
IP address and port of the server in the GMS Reporting Server IP Address and GMS Reporting Server
Port fields.
Note: To use HTTPS management, the SonicWALL appliance must be using Firmware 6.6 or later.
Note: If there is a firewall between the SonicWALL appliance and the SonicWALL GMS agent, make sure
the firewall is configured to allow port 514.
9. When you are finished, click Update. The SonicWALL appliance is now configured for management by
SonicWALL GMS. To clear the settings and start over, click Reset. To add the unit to SonicWALL GMS, see
“Adding SonicWALL Appliances to SonicWALL GMS” on page 30.
10. To add the SonicWALL appliance to SonicWALL GMS UI using the import option, save the SonicWALL
appliance's configuration (prefs) file.
Configuring SonicWALL Appliances for Management
7
Configuring SonicWALL Appliances Using the Wizard
This section describes how to configure SonicWALL appliances for SonicWALL GMS management using the Configuration Wizard. For information on adding existing SonicWALL appliances, see “Manually Configuring SonicWALL Appliances” on page 6.
Enabling Remote Management
This section describes how to enable remote management on the following SonicWALL appliances:
•
•
•
•
•
•
•
TELE3 SP/SPi/TZ/TZX
SOHO3
SOHO TZW
PRO 100
PRO 200/230
PRO 300/330
GX 250/650
Note: Ensure the SonicWALL appliance is running firmware version 6.1.1.0 or later.
To configure a new SonicWALL appliance for remote management, follow these steps:
Note: For information on migrating existing SonicWALL appliances, see “Manually Configuring SonicWALL
Appliances” on page 6.
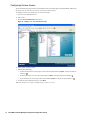
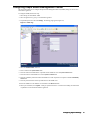
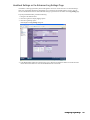
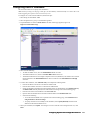
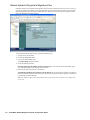
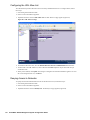
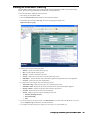
1. Start the SonicWALL installation Wizard. The Welcome screen appears (Figure 3).
Figure 3: Installation Welcome Screen
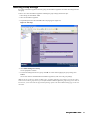
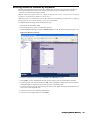
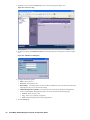
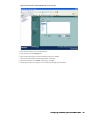
2. Click Next. The Set Password screen appears (Figure 4).
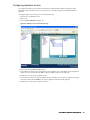
8
SonicWALL Global Management System Configuration Guide
Figure 4: Set Password Screen
3. Enter the password for the SonicWALL appliance, select the Use Global Management System check box, and
click Next.
Note: In order for SonicWALL GMS to manage a SonicWALL appliance, it must have the password. For more
information, see “Adding SonicWALL Appliances to SonicWALL GMS” on page 30.
The Set Global Management System Information screen appears (Figure 5).
Figure 5: Set Global Management System Information Screen
4. Enter the IP address of the SonicWALL GMS server in the Host Name or IP Address field.
5. Enter a 16-character encryption key in the Encryption Key field. The key must be exactly 16 characters long
and composed of hexadecimal characters. Valid hexadecimal characters are “0” to “9”, and “a” to “f” (i.e., 0, 1,
2, 3, 4, 5, 6, 7, 8, 9, a, b, c, d, e, f). For example, a valid key would be “1234567890abcdef.”
6. Enter a 32-character authentication key in the Authentication Key field. The key must be exactly 32 characters
long and composed of hexadecimal characters. For example, a valid key would be
“1234567890abcdef1234567890abcdef.”
7. If a NAT device is between the SonicWALL appliance and SonicWALL GMS, select the Interposed NAT
Device check box and enter the IP address of the SGMS gateway in the NAT Device IP Address field.
Configuring SonicWALL Appliances for Management
9
8. When you are finished configuring this page, click Next. The Time Zone screen appears (Figure 6).
Figure 6: Time Zone Screen
9. Select the time zone.
10. Make sure you have all required network information and click Next. The Connecting to the Internet screen
appears (Figure 7).
Figure 7: Connecting to the Internet Screen
11. Select how the device will connect to the Internet:
If the device uses a single IP address provided by the Internet Service Provider (ISP), select Assigned you
a single static IP address and click Next. Continue to “Single IP Address” on page 11.
• If the device uses two or more IP addresses provided by the ISP, select Assigned you two or more IP
addresses and click Next. Continue to “Two or More IP Addresses” on page 13.
• If the device will use point-to-point protocol over Ethernet (PPPoE), select Provided you with desktop
software, a username, and password and click Next. Continue to “PPPoE” on page 16.
• If the device will automatically be assigned a dynamic IP address, select Automatically assigns you a
dynamic IP address and click Next. Continue to “DHCP” on page 18.
•
10
SonicWALL Global Management System Configuration Guide
Single IP Address
If the ISP provided a single IP address, follow these steps:
1. From the Use Network Address Translation screen, click Next.
Figure 8: Use Network Address Translation Screen
The Getting to the Internet screen appears (Figure 9).
Figure 9: Getting to the Internet Screen
2. Enter the WAN IP address of the SonicWALL appliance.
3. Enter the WAN subnet mask of the SonicWALL appliance.
4. Enter the IP address of the gateway or router that provides Internet access to the SonicWALL appliance.
5. Enter the IP addresses of the DNS servers (maximum of three IP addresses). SonicWALL appliances require the
IP address of at least one DNS server to function properly.
6. When you are finished configuring this page, click Next. The LAN Information screen appears (Figure 10).
Configuring SonicWALL Appliances for Management
11
Figure 10: LAN Information Screen
7. Enter an IP address for the SonicWALL LAN interface in the SonicWALL LAN IP Address field. This
address is also used for configuration and monitoring.
Although you can enter any IP address, we highly recommend using a private IP address. The following IP
address ranges are reserved for private IP networks and are not routed on the Internet:
10.0.0.0 - 10.255.255.255
172.16.0.0 - 172.31.255.255
192.168.0.0 - 192.168.255.255
Note: If your network uses IP addresses that are not registered to your organization and are not within the private IP address ranges, the servers on the Internet to which those IP addresses belong will not be accessible
from your network. For example, if an IP address on your network is 185.5.20.105 and it is not registered to
your organization, the server that uses that IP address on the Internet will not be accessible from your network.
8. Enter the subnet to which the LAN IP address belongs in the LAN Subnet Mask field.
9. When you are finished configuring this page, click Next. The DHCP Server screen appears (Figure 11).
Figure 11: DHCP Server Screen
12
SonicWALL Global Management System Configuration Guide
10. If the SonicWALL appliance will act as the Dynamic Host Configuration Protocol (DHCP) server on the network, select the Enable DHCP Server check box and enter the beginning and end of the address range.
11. When you are finished configuring this page, click Next. The Restart screen appears (Figure 12).
Figure 12: Restart Screen
12. To restart the SonicWALL appliance, click Restart. The SonicWALL device is configured and ready to be
managed by SonicWALL GMS. To add the unit to SonicWALL GMS, see “Adding SonicWALL Appliances to
SonicWALL GMS” on page 30.
Two or More IP Addresses
If the ISP provided two or more IP address, follow these steps:
1. From the Network Address Translation screen, select whether the device will provide NAT for the network.
Figure 13: Use Network Address Translation Screen
Configuring SonicWALL Appliances for Management
13
NAT provides anonymity to machines on the LAN by connecting the entire network to the Internet using a single IP address. This provides security to the internal machines by hiding them from the outside world and conserves IP addresses.
When using NAT, we recommend using internal network IP addresses from a special range. The following IP
address ranges are reserved for private IP networks and are not routed on the Internet:
10.0.0.0 - 10.255.255.255
172.16.0.0 - 172.31.255.255
192.168.0.0 - 192.168.255.255
Note: If your network uses IP addresses that are not registered to your organization and are not within the private IP address ranges, the servers on the Internet to which those IP addresses belong will not be accessible
from your network. For example, if an IP address on your network is 185.5.20.105 and it is not registered to
your organization, the server that uses that IP address on the Internet will not be accessible from your network.
After selecting whether the SonicWALL device will use NAT, click Next. The Getting to the Internet screen
appears (Figure 14).
Figure 14: Getting to the Internet Screen
2. Enter the WAN IP address of the SonicWALL appliance.
3. Enter the WAN subnet mask of the SonicWALL appliance.
4. Enter the IP address of the gateway or router that provides Internet access to the SonicWALL appliance.
5. Enter the IP addresses of the DNS servers (maximum of three IP addresses). SonicWALL appliances require the
IP address of at least one DNS server to function properly.
6. When you are finished configuring this page, click Next. The LAN Information screen appears (Figure 15).
14
SonicWALL Global Management System Configuration Guide
Figure 15: LAN Information Screen
7. Enter an IP address for the SonicWALL LAN interface in the SonicWALL LAN IP Address field. Although
you can enter any IP address, we highly recommend using a private IP address.
Note: This address is also used for configuration and monitoring.
8. Enter the appropriate subnet in the LAN Subnet Mask field.
9. When you are finished configuring this page, click Next. The DHCP Server screen appears (Figure 16).
Figure 16: DHCP Server Screen
10. If the SonicWALL appliance will act as the DHCP server on the network, select the Enable DHCP Server
check box and enter the beginning and end of the address range.
11. When you are finished configuring this page, click Next. The Restart screen appears (Figure 17).
Configuring SonicWALL Appliances for Management
15
Figure 17: Restart Screen
12. To restart the SonicWALL appliance, click Restart. The SonicWALL device is configured and ready to be
managed by SonicWALL GMS. To add the unit to SonicWALL GMS, see “Adding SonicWALL Appliances to
SonicWALL GMS” on page 30.
PPPoE
If the device connects to the Internet using Point-to-Point over Ethernet (PPPoE), follow these steps:
1. From the PPPoE screen, enter the account user name and password.
Figure 18: PPPoE Screen
2. Click Next. The LAN Information screen appears (Figure 19).
16
SonicWALL Global Management System Configuration Guide
Figure 19: LAN Information Screen
3. Enter an IP address for the SonicWALL LAN interface in the SonicWALL LAN IP Address field. Although
you can enter any IP address, we highly recommend using a private IP address.
Note: This address is also used for configuration and monitoring.
4. Enter the appropriate subnet in the LAN Subnet Mask field.
5. When you are finished configuring this page, click Next. The DHCP Server screen appears (Figure 20).
Figure 20: DHCP Server Screen
6. If the SonicWALL appliance will act as the DHCP server on the network, select the Enable DHCP Server
check box and enter the beginning and end of the address range.
7. When you are finished configuring this page, click Next. The Restart screen appears (Figure 21).
Configuring SonicWALL Appliances for Management
17
Figure 21: Restart Screen
8. To restart the SonicWALL appliance, click Restart. The SonicWALL device is configured and ready to be
managed by SonicWALL GMS. To add the unit to SonicWALL GMS, see “Adding SonicWALL Appliances to
SonicWALL GMS” on page 30.
DHCP
If the device is dynamically assigned an IP address, follow these steps:
1. From the Obtain an IP Address Automatically Screen, click Next.
Figure 22: Obtain an IP Address Automatically Screen
The LAN Information screen appears (Figure 23).
18
SonicWALL Global Management System Configuration Guide
Figure 23: LAN Information Screen
2. Enter an IP address for the SonicWALL LAN interface in the SonicWALL LAN IP Address field. Although
you can enter any IP address, we highly recommend using a private IP address.
Note: This address is also used for configuration and monitoring.
3. Enter the appropriate subnet in the LAN Subnet Mask field.
4. When you are finished configuring this page, click Next. The DHCP Server screen appears (Figure 24).
Figure 24: DHCP Server Screen
5. If the SonicWALL appliance will act as the DHCP server on the network, select the Enable DHCP Server
check box and enter the beginning and end of the address range.
6. When you are finished configuring this page, click Next. The Restart screen appears (Figure 25).
Configuring SonicWALL Appliances for Management
19
Figure 25: Restart Screen
7. To restart the SonicWALL appliance, click Restart. The SonicWALL device is configured and ready to be
managed by SonicWALL GMS. To add the unit to SonicWALL GMS, see “Adding SonicWALL Appliances to
SonicWALL GMS” on page 30.
8. To add the SonicWALL appliance to SonicWALL GMS UI using the import option, save the SonicWALL
appliance's configuration (prefs) file.
Modifying Remote Management Settings
After a SonicWALL appliance is configured for SonicWALL GMS management, you can modify its management
settings through SonicWALL GMS.
To change the management options for a SonicWALL appliance, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the Network tree and click Management. The Management page appears (Figure 26).
20
SonicWALL Global Management System Configuration Guide
Figure 26: Management Page
4. Enter the port used to manage the SonicWALL appliance in the HTTP Port field.
5. To allow HTTPS management of this SonicWALL appliance, the Enable HTTPS Access to the unit check
box and specify the management port and common certificate name.
6. Select The Enable Management using check box and select SGMS.
7. Configure the following options:
•
•
GMS Host Name or IP Address—IP address or host name of the SonicWALL GMS server.
GMS Syslog Server Port—syslog server port (default: 514).
8. If the SonicWALL GMS server is behind a NAT device, select the GMS behind NAT Device check box and
enter the IP address in the NAT Device IP Address field.
9. If the SonicWALL GMS server and SonicWALL appliance are on the same network or communicating through
a VPN select the SGMS on VPN check box.
10. When you are finished, click Update. The SonicWALL appliance is now configured for management by
SonicWALL GMS. To clear the settings and start over, click Reset. To add the unit to SonicWALL GMS, see
“Adding SonicWALL Appliances to SonicWALL GMS” on page 30.
PortShield Support for the SonicWALL PRO 1260
GMS now supports the PortShield feature for the SonicWALL PRO 1260 security appliance. SonicWALL PortShieldTM is a feature of the SonicWALL PRO 1260 security appliance running SonicOS Enhanced 3.1 or newer.
PortShield architecture enables you to configure some or all of the 24 LAN switch ports on the PRO 1260 into separate security contexts, providing protection not only from the WAN and DMZ, but between devices inside your
network as well. In effect, each context has its own wire-speed switch ports that enjoy the protection of a dedicated,
deep packet inspection firewall.
You can assign any combination of ports into a PortShield interface. All ports you do not assign to a PortShield
interface are assigned to the LAN interface. For example, if you assign ports 4 through 12 to a PortShield interface,
ports 1 through 3, ports 13 through 24, and the uplink port are all assigned to the LAN interface.
To configure a port shield interface, perform the following steps:
1. Navigate to the Policies Panel.
2. Click on the Networks Menu.
Configuring SonicWALL Appliances for Management
21
3. Click on the Switch Ports Menu.
GMS displays a table detailing the ports of the SonicWALL PRO 1260.
4. Select a port to which you want to include in a Port Shield Interface and click the Configure icon for that port.
GMS displays the port configuration dialog box.
5. Note that the name of the PortShield interface group will be assigned by default.
6. Click on the Port Enable list box and click on either the Enable or Disable option to either activate or deactivate
the interfaces in the PortShield interface group.
7. Click on the PortShield interface list box and click on the PortShield interface you created in the previous procedure.
22
SonicWALL Global Management System Configuration Guide
8. Click on the Link Speed list box and click on a throughput speed you want to assign the interface. The choices
are:
•
•
•
•
•
Auto negotiate
100Mbps Full Duplex
100 Mbps Half Duplex
10 Mbps Full Duplex
10 Mbps Half Duplex
Note: Do not change this setting from the default of Auto negotiate unless your system requires you to do so.
Also, note that for any setting involving the Full Duplex feature to work properly, be sure to configure Full
Duplex on both ends of the link. By not having Full Duplex configured on both ends, a duplex mismatch occurs,
causing throughput loss.
9. Click on the Rate Limit option and click on a value. The rate limit value enables you to throttle traffic coming
into the switch. Remember, these values apply to inbound traffic only. The rate limit choices are
10. 64 Kbps
•
•
•
•
•
•
•
128 Kbps
256 Kbps
512 Kbps
1 Mbps
4 Mbps
10 Mbps
20 Mbps
11. Click Ok. Wait for a few seconds. The system then will incorporate the changes you made to the PortShield
interface Group and add it back to the switch ports list.
Configuring SonicWALL Appliances for Management
23
24
SonicWALL Global Management System Configuration Guide
CHAPTER 3
Creating Groups and Adding SonicWALL Appliances
After you configure the SonicWALL appliances for SonicWALL GMS management, you can create SonicWALL
fields that will be used to organize SonicWALL appliances. For more information, see “Creating SonicWALL
Fields and Views” on page 25.
After you determine how you will organize SonicWALL GMS, you can use the following methods to add SonicWALL appliances to the SonicWALL GMS UI:
To add SonicWALL appliances one at a time through the SonicWALL GMS UI, see “Adding SonicWALL
Appliances to SonicWALL GMS” on page 30.
• To add the SonicWALL appliances using the import option, see “Adding SonicWALL Appliances to
SonicWALL GMS” on page 30.
• To add multiple SonicWALL appliances using the SonicWALL GMS Command Line Interface, see the
SonicWALL GMS Command Line Interface User Guide.
•
After you have added the SonicWALL appliances, you must register them. See “Registering SonicWALL Appliances” on page 38.
Note: If you need to move SonicWALL appliances to different groups, see “Moving SonicWALL Appliances Between
Groups” on page 39.
Creating SonicWALL Fields and Views
The SonicWALL GMS uses an innovative method for organizing SonicWALL appliances.
SonicWALL appliances are not forced into specific, limited, rigid hierarchies. Simply create a set of fields that
define criteria (e.g., country, city, state) which separate SonicWALL appliances. Then, create and use views to display and sort appliances on the fly.
To organize SonicWALL appliances, follow these steps:
• Create custom fields that will be useful to your organization. See “Creating Custom Fields” on page 25.
• Review the standard SonicWALL fields. See “SonicWALL Fields” on page 27.
• Create views that will make your job easier. See “Setting Up Views” on page 27.
Creating Custom Fields
When first configuring SonicWALL GMS, you will create custom fields that will be entered for each SonicWALL
appliance. SonicWALL GMS supports up to ten custom fields.
Note: Although SonicWALL GMS supports up to ten custom fields, only seven fields can be used to sort SonicWALL
appliances at any given time.
Creating Groups and Adding SonicWALL Appliances
25
The following are examples of custom fields that you can use:
• Geographic—useful for organizing SonicWALL appliances geographically. Especially useful when used in
combination with other grouping methods. Geographic fields may include:
• Country
• Time Zone
• Region
• State
• City
• Customer-based—useful for organizations that are providing managed security services for multiple customers.
Customer-based fields may include:
• Company
• Division
• Department
• Configuration-based—useful when SonicWALL appliances will have very different configurations. (e.g., Filtering, No Filtering, Pornography Filtering, Violence Filtering, or VPN).
• User-type—different service offerings can be made available to different user types. For example, engineering,
sales, and customer service users can have very different configuration requirements. Or, if offered as a service
to end users, you can allow or disallow network address translation (NAT) depending on the number of IP
addresses that you want to make available.
SonicWALL GMS is pre-configured with four custom fields: Country, Company, Department, and State. These
fields can be modified or deleted. To add fields, follow these steps:
1. Start and log into SonicWALL GMS.
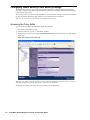
2. Click the Console tab.
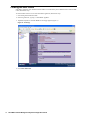
3. Expand the Management tree and click Custom Groups (Figure 27).
Figure 27: Custom Group
4. Right-click Custom Groupings in the right pane.
5. Select Add Group from the pop-up menu.
6. Enter the name of the first field.
7. Select the newly created field and select Add Group from the pop-up menu.
8. Enter the name of the new field.
9. Repeat Steps 6 through 8 for each field that you want to create. You can create up to ten fields.
Note: Although the fields appear to be in a hierarchical form, this has no effect on how the fields will appear within
a view. To define views, see “Setting Up Views” on page 27.
To modify or delete fields, right-click any of the existing fields and select Modify or Delete from the pop-up menu.
26
SonicWALL Global Management System Configuration Guide
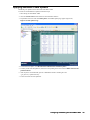
SonicWALL Fields
SonicWALL GMS includes standard fields that can be used to sort SonicWALL appliances based on their model,
their firmware version, and other criteria. SonicWALL GMS fields include the following:
•
•
•
•
•
•
•
•
•
•
•
•
•
AV Enabled—places the SonicWALL appliances into two groups: appliances that have anti-virus (AV) subscriptions and appliances that do not.
AV Status—places the SonicWALL appliances into different groups based on their status.
CFL Status—places the SonicWALL appliances into two groups: appliances that have content filter list (CFL)
subscriptions and appliances that do not.
Firmware—creates a group for each Firmware version and places each SonicWALL appliance into its corresponding group.
Model—creates a group for each SonicWALL model and places each SonicWALL appliance into its corresponding group.
Network Type—creates a group for each network type and places each SonicWALL appliance into its corresponding group. These include:
• Standard
• NAT with DHCP Client
• NAT with PPPoE Client
• NAT with L2TP Client
• NAT with PPTP Client
• NAT Enabled
• Unknown
Nodes—creates a group for each node range and places each SonicWALL appliance into its corresponding
group.
PKI Status—places the SonicWALL appliances into two groups: appliances that have Public Key Infrastructure
(PKI) certificates and appliances that do not.
Registered—places the SonicWALL appliances into two groups: appliances that are registered and appliances
that are not.
Scheduler—creates a group for each scheduler agent and places each SonicWALL appliance into its corresponding group.
State—creates a group for each type of state and places each SonicWALL appliance into its corresponding
group.
VPN Present—places the SonicWALL appliances into two groups: appliances that have VPN and appliances
that do not.
Warranty Status—places the SonicWALL appliances into two groups: appliances that have current warranties
and appliances that do not.
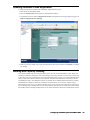
Setting Up Views
After creating custom fields and reviewing SonicWALL GMS fields, SonicWALL GMS administrators can set up
views to perform different functions.
Note: Each view can show a maximum of seven fields.
Some views can include the following:
•
Standard Geographic Views
When the number of SonicWALL appliances managed by SonicWALL GMS becomes large, you can divide the
appliances geographically among SonicWALL administrators.
For example, if one administrator will be responsible for each time zone in the United States, you can choose
the following grouping methods:
•
• Administrator 1: Country: USA, Time Zone: Pacific, State, City.
• Administrator 2: Country: USA, Time Zone: Mountain, State, City.
• Administrator 3: Country: USA, Time Zone: Central, State, City.
• Administrator 4: Country: USA, Time Zone: Eastern, State, City.
Firmware Views
Creating Groups and Adding SonicWALL Appliances
27
To ensure that all SonicWALL appliances are using the current firmware, you can create a view to check and
update firmware versions and batch process firmware upgrades when network activity is low.
For example, if you want to update all SonicWALL appliances to the latest firmware at 2:00 A.M., you can use
the following grouping method:
•
Firmware Version, Time Zone
If you want to update SonicWALL appliances only for companies that have agreed to the upgrade and you want
the upgrades to take place at 2:00 A.M., you can use the following grouping method:
• Company, Firmware Version, Time Zone
• Registration Views
To ensure that all SonicWALL appliances are registered, you can create a registration view and check it periodically. To create a registration view, you can use the following grouping method:
• Registration Status, any other grouping fields
• Upgrade View
You can create views that contain information on which upgrades customers do not have and forward this information to the Sales Department.
For example, you can choose the following grouping methods:
•
•
•
28
Content Filter List, Company, Division, Department
Anti-Virus, Company, Division, Department
Warranty Status, Company, Division, Department
SonicWALL Global Management System Configuration Guide
Creating Views
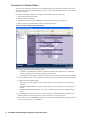
To create a view, follow these steps:
1. Start and log into SonicWALL GMS.
2. Right-click anywhere in the left pane of the SonicWALL GMS window and select Add/Delete/Modify View
from the pop-up menu. The Add/Delete/Modify View page appears (Figure 28).
Figure 28: Edit View Page
3. Enter the name of the new view in the View Name field. Save the view by clicking Add View.
4. To add a view category, click Add Level. These categories will be used to sort SonicWALL appliances in your
view. The categories are a combination of custom fields and SonicWALL GMS fields. To change a field, type
the name of the field in the Group Category field or select one by clicking the Group Category field. For a
list of SonicWALL GMS fields and their meanings, see “SonicWALL Fields” on page 27.
5. You can add up to seven categories. Repeat Step 4 for each category that you would like to add.
6. To delete a view category, select the level and click Delete Level.
7. When you are finished configuring this view, click Modify View.
8. To add another view, repeat Steps 3 through 7.
9. When you are finished, click Done.
Changing Views
To change views from within the SonicWALL GMS UI, follow these steps:
1. Start and log into SonicWALL GMS.
2. Right-click anywhere in the left pane of the SonicWALL GMS window and select Change View from the popup menu. The Change View dialog box appears (Figure 29).
Figure 29: Change View Dialog Box
3. Select a view and click OK. The new view is displayed.
Creating Groups and Adding SonicWALL Appliances
29
Adding SonicWALL Appliances to SonicWALL GMS
SonicWALL GMS can communicate with SonicWALL appliances through VPN tunnels, HTTPS, or directly over
VPN tunnels that already exist between the SonicWALL appliances and the SGMS gateway.
This section describes how to add SonicWALL appliances from the SonicWALL GMS UI. To add a SonicWALL
appliance using its preferences file to pre-populate fields, see “Importing SonicWALL Appliances” on page 36. To
add SonicWALL appliances using the command-line interface, refer to the SonicWALL Global Management System
Command Line Interface Guide. To add a SonicWALL appliance using the SonicWALL GMS UI, follow these
steps:
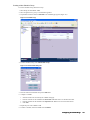
1. Start and log into SonicWALL GMS.The Status page appears (Figure 30).
Figure 30: Adding a SonicWALL Appliance
2. Expand the SonicWALL GMS tree and select the group to which you will add the SonicWALL appliance.
Then, right-click the group and select Add Unit from the pop-up menu. To not specify a group, right-click an
open area in the left pane of the SonicWALL GMS UI and select Add Unit. The Add Unit dialog box appears
(Figure 31).
Note: The group to which you add the SonicWALL appliance must be comprised of custom attributes. For
example, if SonicWALL appliances are grouped by model number, you cannot add a SOHO to a PRO group.
Figure 31: Add Unit Dialog Box
3. Enter a descriptive name for the SonicWALL appliance in the SonicWALL Name field.
30
SonicWALL Global Management System Configuration Guide
Note: Do not enter the single quote character (‘) in the SonicWALL Name field.
4. Enter the administrator login name for the SonicWALL appliance in the SonicWALL Login Name field.
5. Enter the password used to access the SonicWALL appliance in the SonicWALL Password field.
6. Enter the serial number of the SonicWALL appliance in the Serial Number field.
7. Select from the following management modes:
•
•
•
If the SonicWALL appliance will be managed through an existing VPN tunnel or over a private network,
select Using Exiting Tunnel or LAN.
If the SonicWALL appliance will be managed through a dedicated management VPN tunnel, select Using
Management VPN Tunnel (default).
If the SonicWALL appliance will be managed over HTTPS, select Using HTTPS.
Note: HTTPS management requires additional configuration. For more information, see “Enabling
Remote Management” on page 8.
8. Enter the port used to administer the SonicWALL appliance in the SonicWALL HTTP Port field (standard:
80; HTTPS: 443).
9. For VPN tunnel management, enter a 16-character encryption key in the SA Encryption Key field. The key
must be exactly 16 characters long and composed of hexadecimal characters. Valid hexadecimal characters are
“0” to “9”, and “a” to “f” (i.e., 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, a, b, c, d, e, f). For example, a valid key would be
“1234567890abcdef.”
Note: This key must match the encryption key of the SonicWALL appliance.
10. For VPN tunnel management, enter a 32-character authentication key in the SA Authentication Key field. The
key must be exactly 32 characters long and composed of hexadecimal characters. For example, a valid key
would be “1234567890abcdef1234567890abcdef.”
Note: This key must match the authentication key of the SonicWALL appliance.
11. If the SonicWALL appliance uses the Anti-Virus feature, enter the Anti-Virus password. Otherwise, leave the
field blank.
12. Select the IP address of the SonicWALL GMS agent server that will manage the SonicWALL appliance from
the Agent IP Address list box:
If SonicWALL GMS is configured in a multi-tier distributed environment, you must select the
SonicWALL GMS Agent whose IP address matches the IP address that you specified when configuring the
SonicWALL appliance for SonicWALL GMS management.
• If SonicWALL GMS is in a single-server environment, the IP address of the SonicWALL GMS agent
server already appears in the field.
•
13. If SonicWALL GMS is configured in a multi-tier distributed environment, enter the IP address of the backup
SonicWALL GMS server in the Standby Agent IP field. The backup server will automatically manage the
SonicWALL appliance in the event of a primary failure. Any Agent can be configured as the backup.
Note: If SonicWALL GMS is in a single server environment, leave this field blank.
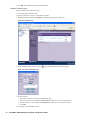
14. Click Properties. The Unit Properties dialog box appears (Figure 32).
Figure 32: Unit Properties Dialog Box
15. This dialog box displays fields to which the SonicWALL appliance belongs. To change any of the values, enter
a new value. When you are finished, click OK. You are returned to the Add Unit dialog box.
16. Click OK. The new SonicWALL appliance appears in the SonicWALL GMS UI. It will have a yellow icon that
indicates it has not yet been successfully acquired.
Creating Groups and Adding SonicWALL Appliances
31
The SonicWALL GMS will then attempt to establish a management VPN tunnel, set up an HTTPS connection,
or use the existing site-to-site VPN tunnel to access the appliance. It then read its configuration and acquires the
SonicWALL appliance for management. This will take a few minutes.
After the SonicWALL appliance is successfully acquired, its icon will turn blue, its configuration settings will
be displayed at the unit level, and its settings will be saved to the database. A text version of this configuration
file is also saved in <gms_directory>/etc/Prefs.
Note: In multi-tier distributed environment, both the primary and secondary SonicWALL GMS Agents must be configured to use the same management method.
Note: If you need to change the SonicWALL appliance settings, see “Modifying SonicWALL Appliance Management Options,” next.
32
SonicWALL Global Management System Configuration Guide
Modifying SonicWALL Appliance Management Options
If you make a mistake or need to change the settings of an added SonicWALL appliances, you can manually modify
its settings or how it is managed.
Note: If a unit has not been acquired (yellow icon), you can change its management mode using this procedure.
After it has been acquired (red or blue icon), you cannot change its management mode using this procedure and
must reassign it. For more information, see “Changing Agents or Management Methods” on page 35.
To modify a SonicWALL appliance, follow these steps:
1. Start and log into SonicWALL GMS.The Status page appears (Figure 33).
Figure 33: Modifying a SonicWALL Appliance
2. Right-click in the left pane of the SonicWALL GMS UI and select Modify Unit from the pop-up menu. The
Modify Unit dialog box appears (Figure 34).
Figure 34: Modify Unit Dialog Box
3. Enter a descriptive name for the SonicWALL appliance in the SonicWALL Name field.
Note: Do not enter the single quote character (‘) in the SonicWALL Name field.
4. Enter the administrator login name for the SonicWALL appliance in the SonicWALL Login field.
5. Enter the password used to access the SonicWALL appliance in the SonicWALL Password field.
6. Enter the serial number of the SonicWALL appliance in the Serial Number field.
Creating Groups and Adding SonicWALL Appliances
33
7. Select from the following management modes:
If the SonicWALL appliance will be managed through an existing VPN tunnel or over a private network,
select Using Exiting Tunnel or LAN.
• If the SonicWALL appliance will be managed through a dedicated management VPN tunnel, select Using
Management VPN Tunnel (default).
• If the SonicWALL appliance will be managed over HTTPS, select Using HTTPS.
•
Note: HTTPS management requires additional configuration. For more information, see “Enabling
Remote Management” on page 6.
8. Enter the port used to administer the SonicWALL appliance in the SonicWALL HTTP Port field (default: 80).
9. Enter a 16-character encryption key in the SA Encryption Key field. The key must be exactly 16 characters
long and composed of hexadecimal characters. Valid hexadecimal characters are “0” to “9”, and “a” to “f” (i.e.,
0, 1, 2, 3, 4, 5, 6, 7, 8, 9, a, b, c, d, e, f). For example, a valid key would be “1234567890abcdef.”
Note: This key must match the encryption key of the SonicWALL appliance.
10. Enter a 32-character authentication key in the SA Authentication Key field. The key must be exactly 32 characters long and composed of hexadecimal characters. For example, a valid key would be
“1234567890abcdef1234567890abcdef.”
Note: This key must match the authentication key of the SonicWALL appliance.
11. If the SonicWALL appliance uses the Anti-Virus feature, enter the Anti-Virus password. Otherwise, leave the
field blank.
12. Select the IP address of the SonicWALL GMS agent server that will manage the SonicWALL appliance from
the Agent IP Address list box:
If SonicWALL GMS is configured in a two-tier distributed environment, you must select the
SonicWALL GMS Agent whose IP address matches the IP address that you specified when configuring the
SonicWALL appliance for SonicWALL GMS management.
• If SonicWALL GMS is in a single-server environment, the IP address of the SonicWALL GMS agent
server already appears in the field.
•
13. If SonicWALL GMS is configured in a two-tier distributed environment, enter the IP address of the backup
SonicWALL GMS server in the Standby Agent IP field. The backup server will automatically manage the
SonicWALL appliance in the event of a primary failure. Any Agent can be configured as the backup.
Note: If SonicWALL GMS is in a single server environment, leave this field blank.
14. Click OK. The SonicWALL appliance settings are modified.
34
SonicWALL Global Management System Configuration Guide
Changing Agents or Management Methods
To provide increased flexibility when managing SonicWALL appliances, SonicWALL GMS enables you to change
the Agents that manage SonicWALL appliances, as well as their management methods.
To change how a SonicWALL appliance is managed, follow these steps:
1. Start and log into SonicWALL GMS. The Status page appears (Figure 35).
2. Select the global icon, a group, or a SonicWALL appliance.
Figure 35: Re-Assigning Agents
3. Right-click in the left pane of the SonicWALL GMS UI and select Re-assign Agents from the pop-up menu.
The Re-assign Agents dialog box appears (Figure 36).
Figure 36: Re-assign Agents Dialog Box
4. Select the IP address of the SonicWALL GMS agent server that will manage the SonicWALL appliance from
the Scheduler IP Address list box.
5. If SonicWALL GMS is configured in a multi-tier distributed environment, enter the IP address of the backup
SonicWALL GMS server in the Standby Agent IP field. The backup server will automatically manage the
SonicWALL appliance in the event of a primary failure. Any Agent can be configured as the backup.
Note: If SonicWALL GMS is in a single server environment, leave this field blank.
6. Select from the following management modes:
• If the SonicWALL appliance will be managed through an existing VPN tunnel or over a private network,
select Using Exiting Tunnel or LAN.
• If the SonicWALL appliance will be managed through a dedicated management VPN tunnel, select Using
Management VPN Tunnel (default).
• If the SonicWALL appliance will be managed over HTTPS, select Using HTTPS.
Note: HTTPS management requires additional configuration. For more information, see “Enabling
Remote Management” on page 6.
Creating Groups and Adding SonicWALL Appliances
35
7. Enter the port used to administer the SonicWALL appliance in the SonicWALL HTTP Port field (standard:
80; HTTPS: 443).
8. When you are finished, click OK. A task is created for each selected SonicWALL appliance.
Importing SonicWALL Appliances
To add a SonicWALL appliance to the SonicWALL GMS UI using the import option, follow these steps:
1. Start and log into SonicWALL GMS. The Status page appears (Figure 37).
Figure 37: Adding a SonicWALL Appliance
2. Right-click in the left pane of the SonicWALL GMS UI and select Add Unit from the pop-up menu. The Add
Unit dialog box appears (Figure 38).
Figure 38: Add Unit Dialog Box
3. Enter a descriptive name for the SonicWALL appliance in the SonicWALL Name field.
Note: Do not enter the single quote character (') in the SonicWALL Name field.
4. Enter the password to access the SonicWALL appliance in the SonicWALL Password field.
5. Click Import. The Import dialog box appears (Figure 39).
36
SonicWALL Global Management System Configuration Guide
Figure 39: Import Dialog Box
Note: If the above Import Dialog Box does not appear, you need to edit the java.policy file on your system. See
“Using the Import Feature from Applet” on page 381.
6. Find and select the saved prefs file of the SonicWALL appliance. Click Import. You are returned to the Add
Unit dialog box.
7. Click Properties. The Unit Properties dialog box appears (Figure 43).
Figure 40: Unit Properties Dialog Box
8. This dialog box displays fields to which the SonicWALL appliance belongs. To change any of the values, enter
a new value. When you are finished, click OK. You are returned to the Add Unit dialog box.
9. Click OK. The new SonicWALL appliance appears in the SonicWALL GMS UI. It will have a yellow icon that
indicates it has not yet been successfully acquired.
The SonicWALL GMS will then attempt to establish a management VPN tunnel to the appliance, read its configuration, and acquire it for management. This will take a few minutes.
After the SonicWALL appliance is successfully acquired, its icon will turn blue, its configuration settings will
be displayed at the unit level, and its settings will be saved to the database. A text version of this configuration
file is also saved in <gms_directory>/etc/Prefs.
Creating Groups and Adding SonicWALL Appliances
37
Registering SonicWALL Appliances
After successfully adding one or more SonicWALL appliances to the SonicWALL GMS UI, the next step is to register them. Registration is required for firmware upgrades, technical support, and more.
To register one or more SonicWALL appliances, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Register/Upgrades tree and click Register SonicWALLs. The Register SonicWALLs page appears
(Figure 41).
Figure 41: Register SonicWALLs Page
4. Click Register. SonicWALL GMS creates a task for each SonicWALL appliance registration.
By default, SonicWALL GMS executes the tasks immediately. However, they can also be scheduled for another
time and will remain in the schedule queue until they are executed. To view the status of these tasks, click the
Console tab. Then, expand the Tasks tree and click Scheduled Tasks.
During the task execution, SonicWALL GMS registers each selected SonicWALL appliance using the information that you used to register with the SonicWALL registration site. After registration is complete, the task will
be removed from the Scheduled Tasks page and the status of the task execution will be logged. To view these
logs, click the Console tab. Then, expand the Log tree and click View Log.
38
SonicWALL Global Management System Configuration Guide
Moving SonicWALL Appliances Between Groups
To move SonicWALL appliances between groups, simply change the properties of their custom fields. To change
these properties, follow these steps.
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance or group in the left pane of the SonicWALL GMS UI (Figure 42).
Figure 42: Moving a SonicWALL Appliance
3. Right-click the appliance or group and select Modify Properties from the pop-up menu. The Properties dialog
box appears (Figure 43).
Figure 43: Unit Properties Dialog Box
4. Make any changes to the categories to which the SonicWALL appliance or group of appliances belongs. For
information on creating categories, see “Creating SonicWALL Fields and Views” on page 25.
Note: If you are performing this procedure at the group or global level, all parameters will be changed for all
selected SonicWALL appliances. For example, if you were attempting to only change the Country attribute, all
other parameters would be changed as well.
5. Click OK. The SonicWALL appliance(s) are moved to the new group.
Creating Groups and Adding SonicWALL Appliances
39
Inheriting Group Settings
If you move SonicWALL appliances between groups, the SonicWALL appliances can inherit the settings from the
new group.
To move one or more SonicWALL appliances inheriting the group settings, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the SonicWALL appliance.
3. Expand the System tree and click Tools. The Tools page appears (Figure 44).
Figure 44: Tools Page
4. Click Inherit Settings from Group.
You are prompted to continue.
5. To inherit the settings from the new group, click OK. To cancel without applying the group settings, click
Cancel.
One or more tasks are scheduled and the SonicWALL appliance(s) will receive the group settings.
Note: For the Access/Services and Access/Rules pages, by default, inheriting group settings overwrites the values
at the unit level with the group values. If you wish for SonicWALL GMS to append the group settings to the values at
the unit level, you need to enable the Append Group Settings option on the General/GMS Settings page on the Console Panel.
Embedded Login Support
You can now set up your system so when a user logs into their organization portal, and selects a link, the customer
automatically logs into GMS. This feature occurs through embedded login support, sometimes known as singlesignon. The user has all the privileges that the organization has set for them. This is useful for providing users
access to reports for an individual secure appliance.
The encryption types are as follows:
•
•
encType of 0 means clear-text
encType of 1 means base64
More encryption types may be available if necessary, but for now, GMS will remain supporting only these two simple encryption types. Adding complicated encryption types can complicate development for the portal developer.
SonicWALL recommends that users of this feature use HTTPS on their GMS Webserver when implementing
embedded login support so that the data portion of the URL is encrypted. HTTP is not recommended.
40
SonicWALL Global Management System Configuration Guide
CHAPTER 4
SonicWALL GMS User Management
Overview
To operate in complex environments, the SonicWALL Global Management System (SonicWALL GMS) is
designed to support multiple users, each with his or her own set of permissions and access rights. To add a new user,
follow these steps:
Select the group to which the new user will belong. If an appropriate group does not exist, you can create one.
See “Creating User Groups” on page 42.
• Add the user and configure general settings. See “Adding Users” on page 45.
• Configure the screens to which the new user has access if they are different from the group settings. See “Configuring Screen Access” on page 46.
• Configure the SonicWALL appliances to which the new user has access if they are different from the group settings. See “Configuring Appliance Access” on page 47.
•
Note: If you do not want to restrict access to SonicWALL appliances or SonicWALL GMS functions, but want to
divide SonicWALL GMS responsibility among multiple users, you can use views. Views use specific criteria to display groups of SonicWALL appliances. Depending on the type of task they are trying to perform, users can switch
between these views as often as necessary. For more information, see “Setting Up Views” on page 27.
Note: All of the user configuration options are available through the command-line interface. For more information, refer to the SonicWALL Global Management System Command-Line Interface Guide.
SonicWALL GMS User Management
41
Creating User Groups
A user group is a group of SonicWALL GMS users who perform similar tasks and have similar permissions.
SonicWALL GMS provides three pre-configured groups:
•
•
•
Administrators—full view and update privileges.
Operators—view privileges only.
End Users—no privileges.
To create a new group, follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Console tab.
3. Expand the Management tree and click Users. The General Page of the User screen appears (Figure 45).
Figure 45: Adding a User Group: General Page
4. Right-click All Users and select Add User Types from the pop-up menu. A new user group appears.
5. Enter the name of the new user group.
6. Enter any comments regarding the new user group in the Comments field.
7. Select a default view for the new user group from the Default View pull-down menu. This view will be displayed for members of the user group when they first log in to SonicWALL GMS.
8. Click Update. The new user group is added. By default, the new group has no privileges. To configure screen
access settings, see “Configuring Screen Access” on page 42.
Configuring Screen Access
The Screen Permissions page contains a hierarchical list of all screens that appear within SonicWALL GMS. From
this screen, you can control access to sections or individual screens.
To configure screen access settings for a user group, follow these steps:
1. Open the Users configuration screen.
2. Select the new user group.
3. Click the Screen Permissions tab (Figure 46).
42
SonicWALL Global Management System Configuration Guide
Figure 46: Adding a User Group: Screen Permissions Page
4. Select a panel, section, or screen.
5. Select from the following:
•
To allow unrestricted access to the object, select View and Update and click Update. The object will be preceded by a .
• To allow view only access, select View Only and click Update. The object will be preceded by a
•
To prevent any access to the object, select None and click Update. The object will be preceded by a
.
.
Note: By default, a new user group has no privileges.
6. To clear all screen settings and start over, click Reset.
Note: : You can allow access rights to multiple panels, sections, or screens.
Configuring Unit, View, and CLI Actions
The Unit/Views/CLI Actions page contains a list of actions and views that can are allowed for a group.
To configure actions and views for a group, follow these steps:
1. Open the Users configuration screen.
2. Select the user group.
3. Click the Unit/Views/CLI Actions tab (Figure 47).
SonicWALL GMS User Management
43
Figure 47: Adding a User Group: Units/Views/CLI Actions Page
4. Select the SonicWALL appliance actions that are available for the group in the Units section.
5. Select the SonicWALL appliance view options that are available for the group in the Views section.
6. To allow members of the group to use the SonicWALL GMS CLI, select the Allow CLI check box.
7. Click Update. The settings are changed for the group.
44
SonicWALL Global Management System Configuration Guide
Adding Users
This section describes how to create a new user. Although the user will inherit all group settings, individual user
settings will override the group settings.
To add a new user, follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Console tab.
3. Expand the Management tree and click Users. The General Page of the User configuration screen appears
(Figure 48).
Figure 48: Adding a User: General Page
4. Right-click a user group and select Add User from the pop-up menu. The Add User window appears.
5. Enter a username and click OK; enter a password and click OK. The new user appears beneath the group to
which it is assigned.
Note: The username and password are case-sensitive. Do not enter the single quote character (‘) in the User ID
field.
6. Select the new user.
7. Enter the full name of the user in the Name field.
8. Enter contact information for the user in the Phone, Fax, Pager, and Email fields.
9. Select the default view for the user from the Default View list box.
10. Enter any comments regarding the new user in the Comments field.
11. Click Update. The new user is added.
•
•
If the user will inherit the user permissions from the group user settings, you are finished.
If the user settings will be different than the group user settings, see “Configuring Screen Access,” below
and “Configuring Appliance Access” on page 47.
Note: To temporarily disable a user account, select the Account Disabled check box and click Update.
SonicWALL GMS User Management
45
Configuring Screen Access
The Screen Permissions page contains a hierarchical list of all screens that appear within SonicWALL GMS. From
this screen, you can control access to screens or all screens within a section.
To configure screen access settings for a user, follow these steps:
1. Open the User configuration screen.
2. Select a user.
3. Click the Screen Permissions tab (Figure 49).
Figure 49: Adding a User: Screen Permissions Page
4. Select a panel, section, or screen.
5. Select from the following:
•
To allow unrestricted access to the object, select View and Update and click Update. The object will be preceded by a .
•
To allow view only access, select View Only and click Update. The object will be preceded by a
• To prevent any access to the object, select None and click Update. The object will be preceded by a
6. To clear all screen settings and start over, click Reset.
Note: You can allow access rights to multiple panels, sections, or screens.
46
SonicWALL Global Management System Configuration Guide
.
.
Configuring Appliance Access
The Appliance Permissions page contains a hierarchical list of all SonicWALL appliances that appear within
SonicWALL GMS. From this screen, you can control access to SonicWALL groups or individual SonicWALL
appliances.
To configure appliance access settings for a user, follow these steps:
1. Open the Users configuration screen.
2. Select a user.
3. Click the Unit Permissions tab (Figure 50).
Figure 50: Adding a User: Unit Permissions Page
4. Select a View from the Views pull-down menu.
5. To provide the user with access to a SonicWALL group or appliance, select a SonicWALL group or appliance in
the left pane of the window and click Add. The group or appliance appears in the right pane.
6. Repeat Step 5 for each group or appliance to add.
7. To prevent the user from accessing a SonicWALL group or appliance, select the group or appliance in the right
pane of the window and click Remove. The group or appliance is deleted from the right pane.
8. Repeat Step 7 for each group or appliance to remove.
SonicWALL GMS User Management
47
Configuring Unit, View, and CLI Actions
The Unit/Views/CLI Actions page contains a list of actions and views that can are allowed for a user.
To configure actions and views for a user, follow these steps:
1. Open the Users configuration screen.
2. Select a user.
3. Click the Unit/Views/CLI Actions tab (Figure 51).
Figure 51: Adding a User: Units/Views/CLI Actions Page
4. Select the SonicWALL appliance actions that are available for the user in the Units section.
5. Select the SonicWALL appliance view options that are available for the user in the Views section.
6. To allow the user to use the SonicWALL GMS CLI, select the Allow CLI check box.
7. Click Update. The settings are changed for the user.
48
SonicWALL Global Management System Configuration Guide
CHAPTER 5
Locating Devices
As the GMS network grows, it can become more difficult to locate SonicWALL appliances. This chapter describes
how to find SonicWALL appliances within the GMS network.
SonicWALL Global Management System (SonicWALL GMS) provides three methods for locating SonicWALL
appliances:
• Left-pane navigational tree—see “Left-Pane Navigational Tree” on page 49.
• Find—see “Find” on page 50.
Left-Pane Navigational Tree
The easiest way to locate SonicWALL appliances in small- to medium-size networks is by using the left-pane navigational tree.
The left-pane navigational tree can sort SonicWALL appliances by custom categories that you specify, anti-virus
settings, content filter list settings, firmware versions, models, and more. To locate a SonicWALL appliance, simply
select a view and navigate through the navigational tree until you find the SonicWALL appliance for which you are
looking.
The following figure shows a GMS network with each SonicWALL appliance grouped by model (Figure 52).
Figure 52: SonicWALL Appliances Sorted by Model
For more information about setting up views, see “Creating SonicWALL Fields and Views” on page 25.
Locating Devices
49
Find
SonicWALL GMS includes a find tool that enables you to search for SonicWALL appliances by name, serial number, or WAN IP Address.
To use the find tool, right-click in the left pane of the SonicWALL GMS UI and click Find.
Figure 53: Searching for SonicWALL Appliances
The Find dialog box appears.
Figure 54: Find Dialog Box
Enter the name, serial number, or WAN IP address of the SonicWALL appliance and click OK.
Note: To search for an exact match, select the Whole Name check box.
The first SonicWALL appliances that matches the search criteria appears. If there is more than one match, a dialog
box will prompt you to search for the next matching appliance. To view this appliance, select No. To search for next
match, select Yes.
50
SonicWALL Global Management System Configuration Guide
Section II
SonicWALL Appliances
CHAPTER 6
Configuring and Maintaining SonicWALL Appliances
The SonicWALL Global Management System (SonicWALL GMS) user interface (UI) is similar to the standard
SonicWALL appliance UI. However, SonicWALL GMS offers the ability to push configuration settings to a single
SonicWALL appliance, a group of SonicWALL appliances, or all SonicWALL appliances being managed by the
SonicWALL GMS.
For example, to change the time for all SonicWALL appliances within a group, select the group, expand the General
tree, and click Time. The Time page appears (Figure 55).
Figure 55: Time Page
When you have finished making changes, click Update. The changes become tasks and are applied to all
SonicWALL units within the group.
Note: For detailed information on making changes to the Time page and other pages in the Policies Panel, refer to
the other chapters of this section.
To view the status of these tasks, click the Console tab. Then expand the SonicWALL GMS Tasks tree and click
Scheduled Tasks. The Scheduled Tasks page appears (Figure 56).
Configuring and Maintaining SonicWALL Appliances
53
Figure 56: Scheduled Tasks Page
The task appears in the Scheduled Tasks page. After a task is successfully applied to a SonicWALL appliance, the
task is removed from the page.
Note: The status of task execution is logged on the View Log page. For more information, see Chapter 12, “Configuring Log Settings.”
SonicWALL GMS provides a scheduling engine. Once a configuration policy is defined for a SonicWALL appliance or a group of SonicWALL appliances, SonicWALL GMS schedules a task for this policy for each SonicWALL
appliance.
By default, SonicWALL GMS queues and executes tasks immediately. To configure SonicWALL GMS to execute
tasks when network activity is low, you can schedule them for a specific window of operation. To do this, configure
the default task execution schedule. For more information, see “Managing Agent Configurations” on page 341.
If you configure tasks to execute at a specific time, but need to execute one or more tasks now, you can execute the
tasks immediately from the Scheduled Tasks page. You can also reschedule the tasks for a specific time outside of
the scheduled window of operation. For more information, see “Working with SonicWALL GMS Tasks” on
page 336.
54
SonicWALL Global Management System Configuration Guide
CHAPTER 7
Configuring System Settings
When configuring new or existing SonicWALL appliances, it is important to make sure that the network and general settings are correct.
This chapter describes how to use the SonicWALL Global Management System (SonicWALL GMS) to configure
general SonicWALL settings. Select from the following:
Time—describes how to change the time and time options for one or more SonicWALL appliances. See “Configuring Time Settings” on page 55.
• Administrator—describes how to change the administrator and password options for one or more SonicWALL
appliances. See “Configuring Administrator Settings” on page 57.
• Info—describes how to change contact information for one or more SonicWALL appliances. See “Configuring
Contact Information” on page 58.
• Settings—describes how to backup and save SonicWALL appliance settings as well as restore them from preferences files. See “Saving and Applying SonicWALL Settings” on page 59.
• Diagnostics—describes how to perform diagnostics on a SonicWALL appliance. See “Viewing Diagnostic
Information” on page 61.
•
Configuring Time Settings
To change time settings on one or more SonicWALL appliances, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the System tree and click Time. The Time page appears (Figure 57).
Configuring System Settings
55
Figure 57: Time Page
4. Select the Time Zone of the appliance(s) from the Time Zone field.
5. To configure the SonicWALL(s) to automatically adjust their clocks for Daylight Savings Time, select the
Automatically Adjust Clock for Daylight Savings Changes check box.
6. To configure the SonicWALL(s) to use Universal Time Coordinated (UTC) or Greenwich Mean Time (GMT)
instead of local time, select the Display UTC in Logs Instead of Local Time check box.
7. To configure the SonicWALL(s) to display the time in the international time format, select the Display Time in
International Format check box.
8. Select from the following:
•
•
To manually configure the time and date, make sure the Use NTP to set time automatically check box is
deselected. The SonicWALL appliance(s) will automatically use the time settings of the SonicWALL GMS
agent.
To configure the SonicWALL(s) to automatically set the local time using Network Time Protocol (NTP),
select the Use NTP to set time automatically check box.
9. When you are finished, click Update. A task gets scheduled to apply the new settings for each selected appliance.
10. If you don't want to use the SonicWALL appliance's internal NTP list, you can add your own NTP list. To add
an NTP server, enter the IP address of an NTP server in the Add NTP Server field.
A task gets scheduled to add the NTP server to each selected SonicWALL appliance.
Note: To add additional NTP servers, click Add and enter another NTP server.
11. To clear all screen settings and start over, click Reset.
56
SonicWALL Global Management System Configuration Guide
Configuring Administrator Settings
The Administrator page configures administrator settings for the SonicWALL appliance. These settings affect both
SonicWALL GMS and other administrators. To change administrator settings on one or more SonicWALL appliances, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the System tree and click Administrator. The Administrator page appears (Figure 58).
Figure 58: Administrator Page
4. Enter the login name for the administrator in the Administrator Login Name field. To use the default administrator name “admin,” leave this field blank.
5. Specify how long the SonicWALL appliance(s) wait (in minutes) before logging out inactive administrators in
the Log out the Administrator after inactivity of field.
6. To lockout the SonicWALL appliance after user login failure, select the Enable user lockout on login failure
check box. Then, specify the number of login failure attempts that must occur before the user is locked out in
the Failed login attempts per minute before lockout field and how long the user will be locked out in the
Lockout Period field.
7. Select from the following options to change the SonicWALL appliance password(s):
• If you are configuring a SonicWALL appliance at the unit level, enter and reenter the new SonicWALL
password. Then, enter the SonicWALL GMS password and click Change Password. The password is
changed.
• If you are configuring a SonicWALL appliance at the group or global level, enter the SonicWALL GMS
password and click Change Password. Each SonicWALL appliance will receive a unique randomly generated password. This unique password is encrypted and recorded in the SonicWALL GMS database.
Note: The unique encrypted password is also written into a file in <gms_directory>/etc/Prefs. The filename
format is <serialnumber>.pwd; each file contains the old and the new password for the SonicWALL appliance.
The file gets overwritten every time the password for the SonicWALL appliance is changed. The encryption is
base64.
8. When you are finished, click Update. A task gets spooled and once it is executed successfully, the settings are
updated for the selected SonicWALL appliances.
9. To clear all screen settings and start over, click Reset.
Configuring System Settings
57
Configuring Contact Information
The Info page contains contact information for the SonicWALL appliance. These settings are for informational purposes only and do not affect the operation of SonicWALL appliances. To change informational settings on one or
more SonicWALL appliances, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the System tree and click Info. The Info page appears (Figure 59).
Figure 59: Info Page
4. Enter contact information for the SonicWALL appliance(s).
Note: The Email Address 1 field is used to send event notifications to the local SonicWALL Appliance administrator. For more information, see “Configuring Alert Notification Settings” on page 339.
The name and other contact information on this page appears when you mouse over the device in the
SonicWALL GMS UI.
5. To configure firewall alerts to be sent to the email address specified in the Email Address 1 field, select the
Firewall Alerts to be sent to Email Address1 check box.
6. When you are finished, click Update. A task gets spooled and once it is executed successfully, the information
is updated for the selected SonicWALL appliances.
7. To clear all screen settings and start over, click Reset.
58
SonicWALL Global Management System Configuration Guide
Saving and Applying SonicWALL Settings
SonicWALL GMS enables you to save SonicWALL appliance settings to the SonicWALL GMS database or a file
which can be used for restoration purposes. To save or apply SonicWALL appliance settings, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance
3. Expand the System tree and click Settings. The Settings page appears (Figure 60).
Figure 60: Settings Page
4. To save the settings of a SonicWALL appliance to the SonicWALL GMS database, enter a name for the settings
in the Name field and click Store settings read from unit. Then, if you want to save these settings to a local
file, click Save the settings to a local file. You can save multiple version of settings for each SonicWALL
appliance to the SonicWALL GMS database and to different local files.
5. To apply settings to the SonicWALL appliance directly from SonicWALL GMS database, select the saved settings and click Restore the settings to the unit.
Note: The Restore the settings to the unit option is available only at the unit level, and not at the group and global
levels. This option previously was available at the group and global levels. GMS now does not display the option at
both the group and global levels to minimize risk of you writing a non-compatible prefs file to an incorrect firmware
version running on a SonicWALL appliance.
6. To restore settings from a file to the SonicWALL appliance, enter the path to the file and click Store settings
from local file. The Store settings from local file button is used to store the prefs file from the local hard disk
into the GMS database so that it displays in the list box of the Settings page, ensuring that the settings from the
local file are not written to the SonicWALL appliance. Once stored in the database (when it will display in the
list box), you can then click the Restore the settings to the unit button.
7. To automatically backup the preferences for the selected SonicWALL appliance, select the Enable Prefs File
Backup check box and click Update.
Note: The backed up prefs file contains the configuration settings and the firmware version of the security
appliance you are backing up.
8. Go to the System > Management > GMS Settings page and update the values in the Automatically save prefs
file section. This enables you to specify when and how frequently GMS backs up the prefs files.
9. If you want to automatically purge older backups, select the number of newer backup files you want to keep in
the Number of newest Prefs Files to be preserved field. Enter 0 to prevent purging of older backups.
Configuring System Settings
59
10. To configure how many reporting intervals SonicWALL GMS waits before reporting a SonicWALL appliance
as down, enter the value in the Missed Reports Threshold field. To configure SonicWALL GMS to never
report a SonicWALL appliance as down, enter ‘0’.
11. To delete settings from the SonicWALL GMS database, select the saved settings and click Delete the settings.
60
SonicWALL Global Management System Configuration Guide
Viewing Diagnostic Information
SonicWALL appliances store information about all devices with which they have communicated.
When you generate diagnostic information, only one report can be generated at a time and the information is only
maintained during the current session. For example, if you run a firewall log report and then log off or generate
another report, the firewall log report data will be lost until you run the report again.
To view diagnostic data, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Diagnostics tree and click Network. The Network page appears (Figure 61) and (Figure 62).
Figure 61: Network Page (Top)
Configuring System Settings
61
Figure 62: Network Page (Bottom)
4. To refresh the diagnostic data, click Refresh Diagnostic Data display.
5. To delete the diagnostic data, click Delete Diagnostic Data display.
6. To view the log file for the selected SonicWALL appliance(s), click Request Log file display from unit(s).
7. To test the RADIUS server, enter the username and password of a valid user and click RADIUS Client Test.
8. To perform a DNS lookup from the SonicWALL appliance(s), enter a hostname or IP address and click DNS
Lookup.
9. To find a network path from the SonicWALL appliance(s), enter an IP address and click Find Network Path.
10. To ping a host from the SonicWALL appliance(s), enter a hostname or IP address and click Ping.
11. To perform a Traceroute from the SonicWALL appliance(s), enter a hostname or IP address and click
TraceRoute Lookup.
12. To view dynamic routing information, click Fetch Default Route Policies (SonicOS 2.5 Enhanced or later)
13. .To perform a reverse name resolution, enter an IP address in the Reverse Lookup the IP Address field and
click Reverse Name Resolution.
14. To perform a real-time black list lookup, enter an IP address in the IP Address field, a FQDN for the RBL in
the RBL Domain field, and DNS server information in the DNS Server field. Click Real-time Black List
Lookup.
15. To generate a Tech Support Report, select any of the following four report options and click Fetch Tech Support Report.
• VPN Keys - saves shared secrets, encryption, and authentication keys to the report.
• ARP Cache - saves a table relating IP addresses to the corresponding MAC or physical addresses.
• DHCP Bindings - saves entries from the SonicWALL security appliance DHCP server.
• IKE Info - saves current information about active IKE configurations.
16. To request a packet trace, enter the IP address of the remote host in the Trace on IP address field, and click
Start. You must enter an IP address in the Trace on IP address field; do not enter a host name, such as
“www.yahoo.com”. Click Stop to terminate the packet trace, and Reset to clear the results.
62
SonicWALL Global Management System Configuration Guide
Viewing Connections Monitor
The Active Connections Monitor displays real-time filterable views of all connections to and through the
SonicWALL security appliance.
To view diagnostic data, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Diagnostics tree and click Connections Monitor. The Connections Monitor page appears
(Figure 63)
Figure 63: Connections Monitor Page
You can filter the results to display only connections matching certain criteria. You can filter by Source IP,
Destination IP, Destination Port, Protocol, Source Interface, and Destination Interface. Enter your filter criteria in the Active Connections Monitor Settings table.
The fields you enter values into are combined into a search string with a logical AND. For example, if you enter
values for Source IP and Destination IP, the search string will look for connections matching:
Source IP AND Destination IP
Check the Group Filters box next to any two or more criteria to combine them with a logical OR. For example, if
you enter values for Source IP, Destination IP, and Protocol, and check Group Filter next to Source IP and Destination IP, the search string will look for connections matching:
(Source IP OR Destination IP) AND Protocol
Click Fetch Active Connections Monitor to apply the filter immediately to the Active Connections Monitor
table (Figure 64). Click Reset Filter to clear the filter and display the unfiltered results again.
Configuring System Settings
63
Figure 64: Connections Monitor Page with Data
64
SonicWALL Global Management System Configuration Guide
Viewing CPU Monitor
The CPU Monitor displays real-time CPU utilization in second, minute, hour, and day intervals.
To view diagnostic data, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Diagnostics tree and click CPU Monitor. The CPU Monitor page appears (Figure 65)
Figure 65: CPU Monitor Page
4. Click Fetch CPU Information to display CPU information from the SonicWALL appliance.
Configuring System Settings
65
Viewing Process Monitor
The Process Monitor displays individual system processes, their CPU utilization, and their system time.
To view diagnostic data, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Diagnostics tree and click CPU Monitor. The Process Monitor page appears (Figure 63)
Figure 66: Process Monitor Page
4. Click Fetch CPU Information to display Process Monitor information.
66
SonicWALL Global Management System Configuration Guide
Configuring Simple Network Management Protocol
This section describes how to configure Simple Network Management Protocol (SNMP) settings for one or more
SonicWALL appliances.
To configure SNMP, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the System tree and click Settings. The Settings page appears (Figure 67).
Figure 67: SNMP Page
4. Select the Enable SNMP check box.
5. Enter a name for the System Name field.
6. Enter the name of the administrator responsible for the SNMP server in the System Contact field.
7. Enter the location of the SNMP server in the System Location field.
8. Enter the community name from which the SNMP server will respond to Get requests in the Get Community
Name field.
9. Enter the password used to send trap notifications to the SNMP server.
10. Enter the SNMP server IP addresses or hostnames in the Hosts 1-4 fields.
11. When you are finished, click Update. A task gets spooled and once it is executed successfully, the information
is updated for each selected SonicWALL appliances.
Configuring System Settings
67
Viewing CA Certificates
The CA Certificates dialog box displays details for Certificate Authority (CA) Certificates that you have imported
on your device. To perform tasks related to CA Certificates in this dialog box, perform the following steps.
1. From the Name list box, click on a certificate.
2. Note the details, including the certificate name and subject in the Details region.
3. Specify a URL of the location of the Certificate Revocation List (CRL) in the CRL URL field. Then click the
CRL URL button to launch the CRL.
4. Provide a CRL name in the Import CRL field by clicking the Browse button and navigating to the CRL you
want. Then click the Import CRL button to import the CRL.
5. Click on the Invalidate Certificates and Security Association if CRL import or processing fails checkbox to
ensure safe cleanup of half-imported certificates if when trying to import a CRL, the process is interrupted.
6. Click on the Email Certificate button if you want to send the certificate to a location by email.
7. Click the Delete Certificate button if you want to remove the certificate.
8. Provide a certificate name in the Import Cert field by clicking the Browse button and navigating to the certificate you want. Then click the Import Cert button to import the certificate.
68
SonicWALL Global Management System Configuration Guide
CHAPTER 8
Using SonicWALL Tools
This chapter describes how to use SonicWALL tools to restart SonicWALL appliances, request diagnostics, inherit
settings from the group, and more.
Restarting SonicWALL Appliances
Some SonicWALL GMS changes require the SonicWALL appliance(s) to automatically be restarted after changes
are applied. However, there may be instances when you want to restart the SonicWALL appliance(s) manually.
Note: We recommend restarting the SonicWALL appliance(s) when network activity is low.
To restart one or more SonicWALL appliances, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the System tree and click Tools. The Tools page appears (Figure 68).
Figure 68: Tools Page
4. To restart the selected SonicWALL appliance(s), click Restart SonicWALL.
Using SonicWALL Tools
69
Requesting Diagnostics for SonicWALL
To request diagnostics for one or more SonicWALL appliances, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the System tree and click Tools. The Tools page appears (Figure 69).
Figure 69: Tools Page
4. To request diagnostics for the selected SonicWALL appliance(s), click Request Diagnostics.
SonicWALL GMS schedules a task to immediately request diagnostics for the selected SonicWALL appliances.
5. To view the diagnostics, see “Viewing the Snapshot or Diagnostics” on page 353.
70
SonicWALL Global Management System Configuration Guide
Inheriting Group Settings
If you move SonicWALL appliances between groups, the SonicWALL appliances can inherit the settings from the
new group.
To move one or more SonicWALL appliances inheriting the group settings, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the SonicWALL appliance.
3. Expand the System tree and click Tools. The Tools page appears (Figure 70).
Figure 70: Tools Page
4. Click Inherit Settings from Group.
You are prompted to continue.
5. To inherit the settings from the new group, click OK. To cancel without applying the group settings, click
Cancel.
One or more tasks are scheduled and the SonicWALL appliance(s) will receive the group settings.
Note: For the Access/Services and Access/Rules pages, by default, inheriting group settings overwrites the values
at the unit level with the group values. If you wish for SonicWALL GMS to append the group settings to the values at
the unit level, you need to enable the Append Group Settings option on the General/GMS Settings page on the Console Panel.
Using SonicWALL Tools
71
Clearing the ARP Cache
SonicWALL appliances store information about all devices with which they have communicated. To clear the ARP
Cache, follow these steps:
To clear the ARP Cache for one or more SonicWALL appliances, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the System tree and click Tools. The Tools page appears (Figure 71).
Figure 71: Tools Page
4. Click Clear ARP Cache.
72
SonicWALL Global Management System Configuration Guide
Synchronizing Now
If a change is made to the SonicWALL appliance from the local interface, SonicWALL GMS will be notified of the
change through the syslog data stream. After this notification is received, SonicWALL GMS will schedule a task to
synchronize its database with the local change. After the task successfully executes, the current configuration
(prefs) file is read from the SonicWALL appliance and loaded into the database.
Note: After receiving and processing the localsync status message from syslog, SonicWALL GMS drops the status
message and does not store it in the ViewPoint database. Also if syslog is forwarded from SonicWALL GMS to
another syslog server, SonicWALL GMS will still not retain the localsync status message.
Auto synchronization automatically occurs whenever SonicWALL GMS receives a local change notification status
syslog message from a SonicWALL appliance.
You can also force an auto synchronization at any time for a SonicWALL appliance or a group of SonicWALL
appliances. To do this, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the System tree and click Tools. The Tools page appears (Figure 72).
Figure 72: Tools Page
4. To synchronize the selected SonicWALL appliance(s), click Synchronize Now.SonicWALL GMS schedules a
task to synchronize the selected SonicWALL appliances.
Note: The auto synchronization feature can be disabled on the Login/GMS Settings page.
Using SonicWALL Tools
73
Synchronizing with mysonicwall.com
If a new service is added to a SonicWALL appliance and it is upgraded manually, the information will not appear in
SonicWALL GMS. To force the SonicWALL to synchronize with mysonicwall.com now, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the System tree and click Tools. The Tools page appears (Figure 73).
Figure 73: Tools Page
4. To synchronize the selected SonicWALL appliance(s), click Synchronize with mysonicwall.com
Now.SonicWALL GMS schedules a task to synchronize the selected SonicWALL appliances.
74
SonicWALL Global Management System Configuration Guide
CHAPTER 9
Configuring Network Settings
When configuring new or existing SonicWALL appliances, it is important to make sure that the network and general settings are correct. This section describes how to configure the network settings for SonicWALL appliances
running SonicOS Standard. To configure network settings for SonicWALL appliance running SonicOS Enhanced,
see Chapter 10, “Configuring Network Settings for SonicOS Enhanced.”
This chapter describes how to use the SonicWALL Global Management System (SonicWALL GMS) to configure
SonicWALL network settings. Select from the following:
•
•
•
•
•
•
•
•
Network Settings—describes how to configure the network settings of the SonicWALL appliance(s). See
““Configuring Network Settings” on page 75.
Proxy Settings—describes how to configure the SonicWALL appliance(s) when a proxy server is installed
between the SonicWALL appliance(s) and the Internet. See “Configuring Web Proxy Settings” on page 83.
Intranet Settings—describes how to configure the SonicWALL appliance(s) when installed between two intranet segments. See “Configuring Intranet Settings” on page 84.
Routes Settings—describes how to configure static routes. See “Configuring Routes” on page 85.
RIP Settings—describes how to configure the SonicWALL appliance(s) when using Routing Information Protocol (RIP). See “Configuring Routing Information Protocol” on page 86.
DMZ Settings—describes how to configure the settings of the SonicWALL appliance(s) when servers will be
installed on the DMZ port. See “Configuring DMZ (HomePort) Addresses” on page 87.
One-to-One NAT Settings—describes how to configure one-to-one NAT settings. See “Configuring One-toOne Network Address Translation” on page 88.
Ethernet Settings—describes how to configure the Ethernet port settings of the SonicWALL appliance(s). See
“Configuring Ethernet Settings” on page 90.
Configuring Network Settings
Note: In order for changes on this page to take effect, the SonicWALL appliance will automatically restart. We recommend scheduling the tasks to run when network activity is low.
The Network settings page is used to configure the network addressing mode, LAN (WorkPort) settings, WAN settings, DMZ (HomePort) settings, and the DNS server address(es).
Note: The Network settings page cannot be used at the Global and Group levels, except for configuring the DNS
server address(es).
Before configuring any settings, it is important to determine the network addressing mode. These options include:
Standard—see “Transparent or Standard Mode,” below.
NAT Enabled—see “NAT-Enabled Mode” on page 77.
NAT with Dynamic Host Configuration Protocol (DHCP) Client—see “NAT with DHCP Client Mode” on
page 78.
• NAT with PPP over Ethernet (PPPoE) Client—see “NAT With PPPoE Client” on page 79.
• NAT with L2TP Client—see “NAT With L2TP Client” on page 80.
• NAT with PPTP Client—see “NAT With PPTP Client” on page 81.
•
•
•
Configuring Network Settings
75
Transparent or Standard Mode
When you select Transparent Mode (also known as Standard Mode), Network Address Translation (NAT) is disabled. All nodes on the LAN or WorkPort that will access or be accessed from the Internet must use valid, Internetaccessible IP addresses.
To configure a SonicWALL appliance for transparent network addressing, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the Network tree and click Settings. The Network Settings page appears (Figure 74).
4. Select Transparent or Standard from the Network Addressing Mode area.
Figure 74: Network Settings Page: Standard Mode
5. Configure the following LAN (WorkPort) Settings:
•
•
SonicWALL LAN (WorkPort) IP Address—IP address assigned to the SonicWALL LAN or WorkPort
interface. This address is also used for configuration and monitoring.
LAN (WorkPort) Subnet Mask—Determines the subnet to which the LAN or WorkPort IP address belongs.
6. To add an additional subnet, enter the IP address and subnet in the Network Gateway and Subnet Mask fields.
7. Configure the following WAN Settings:
WAN Gateway (Router) Address—Address of the router that provides Internet access to SonicWALL
appliances.
• SonicWALL WAN IP Address—This value is automatically set to the SonicWALL LAN (WorkPort) IP
Address.
• WAN/DMZ (HomePort) Subnet Mask—This value is automatically set to the LAN (WorkPort) Subnet
Mask.
•
8. Enter the IP addresses of the DNS servers in the Other Settings area (maximum of three IP addresses). SonicWALL appliances require the IP address of at least one DNS server to function properly.
9. When you are finished, click Update. The settings are changed for the selected SonicWALL appliance. To clear
all screen settings and start over, click Reset.
76
SonicWALL Global Management System Configuration Guide
NAT-Enabled Mode
NAT provides anonymity to machines on the LAN or WorkPort by connecting the entire network to the Internet
using a single IP address. This provides security to the internal machines by hiding them from the outside world and
conserves IP addresses.
When using NAT, we recommend using internal network IP addresses from a special range. The following IP
address ranges are reserved for private IP networks and are not routed on the Internet:
10.0.0.0 - 10.255.255.255
172.16.0.0 - 172.31.255.255
192.168.0.0 - 192.168.255.255
If your network uses IP addresses that are not registered to your organization and are not within the private IP
address ranges, the servers on the Internet to which those IP addresses belong will not be accessible from your network. For example, if an IP address on your network is 185.5.20.105 and it is not registered to your organization,
the server that uses that IP address on the Internet will not be accessible from your network.
Note: If you choose to use NAT, but need to make some machines available to the outside world, use One-to-One
NAT. One-to-One NAT maps external IP addresses to private IP addresses. For more information, see “Configuring One-to-One Network Address Translation” on page 88.
To configure a SonicWALL appliance for NAT, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the Network tree and click Settings. The Network Settings page appears (Figure 75).
4. Select NAT Enabled from the Network Addressing Mode area.
Figure 75: Network Settings Page: NAT Enabled Mode
5. Configure the following LAN (WorkPort) Settings:
• SonicWALL LAN (WorkPort) IP Address—IP address assigned to the SonicWALL LAN or WorkPort
interface. This address is also used for configuration and monitoring.
• LAN (WorkPort) Subnet Mask—Determines the subnet to which the LAN or WorkPort IP address belongs.
6. To add an additional subnet, enter the IP address and subnet in the Network Gateway and Subnet Mask fields.
Configuring Network Settings
77
7. Configure the following WAN Settings:
• WAN Gateway (Router) Address—Address of the router that attaches the LAN or WorkPort to the Internet.
• SonicWALL WAN IP (NAT Public) Address—Public IP address used to access the Internet. All activity on
the Internet will appear to originate from this address. This IP address must be valid and is generally supplied by your Internet Service Provider (ISP).
• WAN/DMZ (HomePort) Subnet Mask—Determines the subnet to which the public IP address belongs.
This is generally supplied by your ISP.
8. Enter the IP addresses of the DNS servers in the Other Settings section (maximum of three IP addresses).
Note: SonicWALL appliances require the IP address of at least one DNS server to function properly.
9. When you are finished, click Update. The settings are changed for the selected SonicWALL appliance. To clear
all screen settings and start over, click Reset.
NAT with DHCP Client Mode
When you select the NAT with DHCP Client mode, the SonicWALL appliance uses DHCP to obtain a dynamic IP
address from the ISP and NAT. For more information on NAT, see “NAT-Enabled Mode” on page 77. For more
information on configuring DHCP, see Chapter 15, “Configuring Network Settings.”
To configure a SonicWALL appliance for NAT with a DHCP client, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the Network tree and click Settings. The Network Settings page appears (Figure 76).
4. Select NAT with DHCP Client from the Network Addressing Mode area.
Figure 76: Network Settings Page: NAT with DHCP Client Mode
5. Configure the following LAN (WorkPort) Settings:
• SonicWALL LAN (WorkPort) IP Address—IP address assigned to the SonicWALL LAN (WorkPort) interface. This address is also used for configuration and monitoring.
• LAN (WorkPort) Subnet Mask—Determines the subnet to which the LAN or WorkPort IP address belongs.
6. To add an additional subnet, enter the IP address and subnet in the Network Gateway and Subnet Mask fields.
7. The WAN settings and the DNS server IP addresses are automatically provided by the DHCP server of the service provider. You do not need to configure any parameters in the WAN Settings area.
78
SonicWALL Global Management System Configuration Guide
8. In the Other Settings area, enter the name of the DHCP server in the Host Name field.
9. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
NAT With PPPoE Client
When you select the NAT with PPPoE Client mode, the SonicWALL appliance uses PPP over Ethernet (PPPoE) to
connect to the Internet. PPPoE is required by some ISPs to authenticate users over broadband Internet access
devices (e.g., DSL, cable modems, wireless). Note that when using NAT for the PPPoE client, the password appears
in clear text.
Note: When this mode is selected, the SonicWALL LAN (WorkPort) IP Address is used as the gateway address for
computers on the LAN or WorkPort.
To configure a SonicWALL appliance for NAT with PPPoE, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the Network tree and click Settings.The Network Settings page appears (Figure 77).
4. Select NAT with PPPoE Client from the Network Addressing Mode area.
Figure 77: Network Settings Page: NAT With PPPoE Client Mode
5. Configure the following LAN (WorkPort) Settings:
•
•
SonicWALL LAN (WorkPort) IP Address—IP address assigned to the SonicWALL LAN or WorkPort
interface. This address is also used for configuration and monitoring.
LAN (WorkPort) Subnet Mask—Determines the subnet to which the LAN or WorkPort IP address belongs.
6. To add an additional subnet, enter the IP address and subnet in the Network Gateway and Subnet Mask fields.
7. Configure the following ISP Settings:
•
•
User Name—username provided by the ISP.
Password—password used to authenticate the username with the ISP. This field is case-sensitive.
8. To specify how long the SonicWALL appliance waits before disconnecting from the Internet, enter the amount
of time in the inactivity field.
Configuring Network Settings
79
9. Select from the following:
To configure the SonicWALL appliance(s) to dynamically obtain an IP address, select Obtain an IP Address
automatically.
• To configure the SonicWALL appliance(s) to use a fixed IP address, select Use the following IP Address
and enter the IP address.
•
10. When you are finished, click Update. The settings are changed for the selected SonicWALL appliance. To clear
all screen settings and start over, click Reset.
NAT With L2TP Client
When you select the NAT with L2TP Client mode, the SonicWALL appliance uses Layer Two Tunneling Protocol
(L2TP) to connect to the Internet.
Note: When this mode is selected, the SonicWALL LAN (WorkPort) IP Address is used as the gateway address for
computers on the LAN or WorkPort.
To configure a SonicWALL appliance for NAT with L2TP, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the Network tree and click Settings.The Network Settings page appears (Figure 78).
4. Select NAT with L2TP Client from the Network Addressing Mode area.
Figure 78: Network Settings Page: NAT With L2TP Client Mode
5. Configure the following LAN (WorkPort) Settings:
• SonicWALL LAN (WorkPort) IP Address—IP address assigned to the SonicWALL LAN or WorkPort
interface. This address is also used for configuration and monitoring.
• LAN (WorkPort) Subnet Mask—Determines the subnet to which the LAN or WorkPort IP address belongs.
6. To add an additional subnet, enter the IP address and subnet in the Network Gateway and Subnet Mask fields.
80
SonicWALL Global Management System Configuration Guide
7. Select from the following WAN settings:
To configure the SonicWALL appliance to dynamically obtain an IP address, select Obtain an IP address
using DHCP.
• To configure the SonicWALL appliance to use fixed settings, select Use the specified IP address and enter
the following:
• SonicWALL WAN IP (NAT Public) Address—Public IP address used to access the Internet. All activity on the Internet will appear to originate from this address. This IP address must be valid and is generally supplied by your Internet Service Provider (ISP).
• WAN Gateway (Router) Address—Address of the router that attaches the LAN (WorkPort) to the Internet.
• WAN/DMZ (HomePort) Subnet Mask—Determines the subnet to which the public IP address belongs.
This is generally supplied by your ISP.
•
8. Enter the IP address of the DNS server in the DNS Server 1 field.
9. Configure the following ISP L2TP Settings:
•
•
•
•
L2TP Host Name—this information is provided by your ISP.
L2TP Server IP Address—this information is provided by your ISP.
User Name—username provided by the ISP.
Password—password used to authenticate the username with the ISP. This field is case-sensitive.
10. To specify how long the SonicWALL appliance(s) wait before disconnecting from the Internet, select the Disconnect after check box and enter the amount of time.
11. When you are finished, click Update. The settings are changed for the selected SonicWALL appliance. To clear
all screen settings and start over, click Reset.
NAT With PPTP Client
When you select the NAT with PPTP Client mode, the SonicWALL appliance uses Point-to-Point Tunneling Protocol (PPTP) to connect to the Internet.
When this mode is selected, the SonicWALL LAN (WorkPort) IP Address is used as the gateway address for computers on the LAN or WorkPort.
To configure a SonicWALL appliance for NAT with PPTP, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the Network tree and click Settings.The Network Settings page appears (Figure 79).
4. Select NAT with PPTP Client from the Network Addressing Mode area.
Configuring Network Settings
81
Figure 79: Network Settings Page: NAT With PPTP Client Mode
5. Configure the following LAN (WorkPort) Settings:
SonicWALL LAN (WorkPort) IP Address—IP address assigned to the SonicWALL LAN or WorkPort
interface. This address is also used for configuration and monitoring.
• LAN (WorkPort) Subnet Mask—Determines the subnet to which the LAN or WorkPort IP address belongs.
•
6. To add an additional subnet, enter the IP address and subnet in the Network Gateway and Subnet Mask fields.
7. Select from the following WAN settings:
To configure the SonicWALL appliance to dynamically obtain an IP address, select Obtain an IP address
using DHCP.
• To configure the SonicWALL appliance to use fixed settings, select Use the specified IP address and enter
the following:
• SonicWALL WAN IP (NAT Public) Address—Public IP address used to access the Internet. All activity on the Internet will appear to originate from this address. This IP address must be valid and is generally supplied by your Internet Service Provider (ISP).
• WAN Gateway (Router) Address—Address of the router that attaches the LAN (WorkPort) to the Internet.
• WAN/DMZ (HomePort) Subnet Mask—Determines the subnet to which the public IP address belongs.
This is generally supplied by your ISP.
•
8. Enter the IP address of the DNS server in the DNS Server 1 field. Configure the following ISP PPTP Settings:
• PPTP Host Name—this information is provided by your ISP.
• PPTP Server IP Address—this information is provided by your ISP.
• User Name—username provided by the ISP.
• User Password—password used to authenticate the username with the ISP. This field is case-sensitive.
9. To specify how long the SonicWALL appliance(s) wait before disconnecting from the Internet, select the Disconnect after check box and enter the amount of time.
10. When you are finished, click Update. The settings are changed for the selected SonicWALL appliance. To clear
all screen settings and start over, click Reset.
82
SonicWALL Global Management System Configuration Guide
Configuring Web Proxy Settings
A proxy server intercepts all requests to web servers on the Internet. As users access websites, the data is cached on
the proxy server. This improves Internet response and lessens the load on the Internet link. For example, suppose a
school is using the Internet for a research project. A student requests a certain Web page, and then sometime later, a
second student requests the same page. Instead of forwarding the request to the Web server where the page resides,
the proxy server returns the local copy of the page that was cached when the first student accessed the page.
The problem with a proxy server is that each client must be configured to support the proxy, creating unnecessary
administrative problems. If a proxy server is already installed on the LAN (WorkPort), instead of configuring each
client to point to the proxy server, move it to the WAN and enable automatic proxy forwarding. SonicWALLs can
automatically forward all Web proxy requests to proxy servers without client configuration.
Note: The proxy server must be located on the WAN; it may not be located on the LAN (WorkPort).
Configuration
To configure web proxy settings, follow these steps:
Note: In order for changes on this page to take effect, the SonicWALL(s) will automatically be restarted. We recommend configuring these options when network activity is low.
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Network tree and click Web Proxy. The Web Proxy page appears (Figure 80).
Figure 80: Web Proxy Page
4. Enter the IP address of the proxy server in the Proxy Web Server field.
5. Enter the web server port of the proxy server in the Proxy Web Server Port field.
6. Normally, if a proxy server fails, clients behind the SonicWALL appliance will not be able to access the Internet. To allow clients to bypass the proxy server in the event that it fails or becomes unavailable, select the
Bypass Proxy Servers Upon Proxy Server Failure check box.
7. If you have clients configured on the DMZ, select Forward DMZ Client Requests to Proxy Server.
8. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
Configuring Network Settings
83
Configuring Intranet Settings
SonicWALLs can be installed between LAN segments of intranets to prevent unauthorized access to certain
resources. For example, if the administrative offices of a school are on the same network as the student computer
lab, they can be separated by a SonicWALL.
Figure 81 shows how a SonicWALL appliance can be installed between two network segments on an Intranet.
Figure 81: SonicWALL Intranet Configuration
Note: Devices connected to the WAN port do not have firewall or content filter protection. To protect these units,
install another SonicWALL appliance between the Internet and devices connected to the WAN port of the other SonicWALL appliance.
Configuration
Although the systems on the WAN and LAN links are separated, they are still on the same subnet. Consequentially,
you must make the systems on the larger network aware of the systems on the smaller network. To do this, follow
these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Advanced tree and click Intranet. The Intranet page appears (Figure 82).
Figure 82: Intranet Page
84
SonicWALL Global Management System Configuration Guide
4. Select from the following:
If the SonicWALL is not used to separate LAN segments on the intranet, select SonicWALL’s WAN link is
connected to the Internet Router.
• If the smaller network is connected to the LAN, select Specified addresses are attached to the LAN (WorkPort) link.
• If the smaller network is connected to the WAN, select Specified addresses are attached to the WAN link.
•
5. Enter the IP address or IP address range of a system or group of systems on the smaller network:
• To enter a single IP address, enter the IP address in the Addr Range Begin field.
• To enter a range of IP addresses, enter the starting IP address in the Addr Range Begin field and the ending
IP address in the Addr Range End field.
• Click Add Range.
6. Repeat Step 5 for each IP address or IP address range on the smaller network.
7. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
8. To define which services can be accessed from outside the restricted network segment, see Chapter 11, “Configuring Firewall Settings.”
Configuring Routes
If the LAN(s) have internal routers, their addresses and network information must be entered into the SonicWALL(s). To add an internal router, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Advanced tree and click Routes. The Routes page appears (Figure 83).
Figure 83: Routes Page
4. Select whether the router is connected to the LAN (WorkPort), WAN, or DMZ (HomePort) interface from the
the Link list box.
5. Enter the destination network IP addresses in the Destination Network and Subnet Mask fields.
6. Enter the IP address of the router in the Gateway field.
7. Click Add Route. Repeat Step 4 through 6 for each route that you want to add.
Configuring Network Settings
85
8. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
Configuring Routing Information Protocol
RIP is a distance-vector routing protocol that is commonly used in small homogeneous networks. Using RIP, a
router will periodically send its entire routing table to its closest neighbor, which passes the information to its next
neighbor, and so on. Eventually, all routers within the network will have the information about the routing paths.
When attempting to route packets, a router will check the routing table and select the path that requires the fewest
hops.
RIP is not supported by all SonicWALL appliances.
To configure RIP, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Advanced tree and click RIP. The Routes page appears (Figure 84).
Figure 84: RIP Page
86
SonicWALL Global Management System Configuration Guide
4. Select from the following RIP options on the LAN interface:
•
•
•
•
•
•
•
Select the RIP version from the RIP Advertisements list box:
• RIPv1 Enabled—first version of RIP.
• RIPv2 Enabled (multicast)—sends route advertisements using multicasting (a single data packet to specific nodes on the network).
• RIPv2 Enabled (broadcast)—sends route advertisements using broadcasting (a single data packet to all
nodes on the network).
To advertise static routes that you specified on the Routes page, select the Advertise Static Routes check
box.
To set the amount of time between a VPN tunnel state change and the time the change is advertised, enter a
value in the Route Change Damp Time field (default: 30 seconds).
To specify the number of advertisements that are sent after a route is deleted, enter a value in the Deleted
Route Advertisements field (default: 5 advertisements).
By default, the connection between this router and its neighbor counts as one hop. However, there are cases
where you want to discourage or reduce the use of this route by adding additional hops. To change the hop
count of this route, enter the number of hops in the Route Metric field.
Optional. If RIPv2 is selected from the Route Advertisements list box, you can enter a value for the Route
Tag. This value is implementation-dependent and provides a mechanism for routers to classify the originators of RIPv2 advertisements.
Optional. Select from the following RIPv2 Authentication options:
• User Defined—Enter 4 hex digits in the Authentication Type field and 32 hex digits in the Authentication Data field.
• Cleartext Password—Enter a password (16 characters or less) in the Authentication Password field.
• MD5 Digest—Enter a numerical value from 0-255 in the Authentication Key-Id field. Enter a 32 hex
digit value for the Authentication Key field, or use the generated key.
5. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
Configuring DMZ (HomePort) Addresses
SonicWALL appliances protect users by preventing Internet users from accessing systems within the LAN (WorkPort). However, this security also prevents users from reaching servers intended for public access, such as web and
mail servers.
To allow these services, many SonicWALL models have a special Demilitarized Zone (DMZ) port (also known as
the HomePort) which is used for public servers. The DMZ sits between the LAN (WorkPort) and the Internet. Servers on the DMZ are publicly accessible, but are protected from denial of service attacks such as SYN Flood and
Ping of Death.
Although the DMZ port is optional, it is strongly recommended for public servers or when connecting the servers
directly to the Internet where they are not protected.
Note: Some newer SonicWALL appliances have one or more OPT ports that can be configured as a DMZ port. For
more information, see “Configuring Interface Network Settings” on page 94.
Configuration
Each server on the DMZ port or HomePort requires a unique, publishable Internet IP address. The ISP that provides
your Internet connection should be able to provide these addresses.
To add DMZ (HomePort) IP addresses, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Advanced tree and click DMZ Addresses. or HomePort Addresses.
4. The DMZ/HomePort Addresses page appears (Figure 85).
Configuring Network Settings
87
Figure 85: DMZ Addresses Page
5. Select from the following:
If the devices on the DMZ will use fixed IP addresses, select DMZ (HomePort) in Standard Mode. Then,
enter the starting IP address in the Addr Range Begin field, the ending IP address in the Addr Range End
field, and click Add Range. Repeat this step for each range of IP addresses.
• To enter a single IP address, enter the IP address in the Addr Range Begin field.
• If the devices on the DMZ or HomePort will use NAT, select DMZ (HomePort) in NAT Mode and do the
following:
• Enter the private internal IP address assigned to the DMZ or HomePort interface in the DMZ (HomePort) Private Address field.
• Assign a subnet mask in the DMZ or HomePort Subnet Mask field. The LAN (WorkPort) and DMZ
(HomePort) can have the same subnet mask, but the subnets must be different. For instance, the LAN
subnet can be 192.168.0.1 with a subnet mask of 255.255.255.0, and the DMZ subnet can be
172.16.18.1 with a subnet mask of 255.255.255.0.
• To define a DMZ or HomePort public IP address that will be used to access devices on the DMZ interface, enter an IP address in the DMZ (HomePort) NAT Many to One Public Address field (Optional).
•
6. Select from the following:
• To enter a single IP address, enter the IP address in the Addr Range Begin field.
• To enter a range of IP addresses, enter the starting IP address in the Addr Range Begin field and the ending
IP address in the Addr Range End field.
7. Click Add Range.
8. To enter additional IP addresses and IP address ranges, repeat Steps 6 and 7.
9. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
Configuring One-to-One Network Address Translation
One-to-One NAT maps valid external IP addresses to internal addresses hidden by NAT. This enables you to hide
most of your network by using internal IP addresses. However, some machines may require access. This enables
you to allow direct access when necessary.
88
SonicWALL Global Management System Configuration Guide
To do this, assign a range of internal IP addresses to a range of external IP addresses of equal size. The first internal
IP address will correspond to the first external IP address, the second internal IP address to the second external IP
address, and so on.
For example, if an ISP has assigned IP addresses 209.19.28.16 through 209.19.28.31 with 209.19.28.16 as the NAT
public address and the address range 192.168.168.1 through 192.168.168.255 is used on the LAN (WorkPort), the
following table shows how the IP addresses will be assigned.
Table 1: One-to-One NAT Example
LAN Address
WAN Address
Accessed Via
192.168.168.1
209.19.28.16
Inaccessible, NAT
public IP address
192.168.168.2
209.19.28.17
209.19.28.17
192.168.168.3
209.19.28.18
209.19.28.18
[...]
[...]
[...]
192.168.168.16
209.19.28.31
209.19.28.31
192.168.168.16
No corresponding
IP address
No corresponding
IP address
[...]
[...]
[...]
192.168.168.16
No corresponding
IP address
No corresponding
IP address
Configuration
To configure One-to-One NAT, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Advanced tree and click One-to-One NAT. The One-to-One NAT page appears (Figure 86).
Figure 86: One-to-One NAT Page
4. Select the Enable One-to-One NAT check box.
Configuring Network Settings
89
5. Enter the first IP address of the internal IP address range in the Private Range Begin field.
6. Enter the first corresponding external IP address in the Public Range Begin field.
Note: Do not include the NAT Public IP Address in a range.
7. Enter the number of IP addresses in the range in the Range Length field.
8. Click Add Range.
9. To add additional IP address ranges, repeat Step 5 through 8 for each range. When you are finished, click
Update. The settings are changed for each selected SonicWALL appliance. To clear all screen settings and start
over, click Reset.
Configuring Ethernet Settings
This section describes how to configure Ethernet settings on each port of the SonicWALL appliance(s). To configure Ethernet settings, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Advanced tree and click Ethernet.
4. The Ethernet page appears (Figure 87).
Figure 87: Ethernet Page
5. Select from the following WAN Link settings:
•
•
To configure the WAN link to automatically negotiate Ethernet settings, select Auto Negotiate.
To specify WAN link settings, select Force and select the speed and duplex settings.
6. Select from the following DMZ (HomePort) Link settings:
•
•
To configure the DMZ (HomePort) to automatically negotiate Ethernet settings, select Auto Negotiate.
To specify DMZ (HomePort) link settings, select Force and select the speed and duplex settings.
7. Select from the following LAN (WorkPort) Link settings:
• To configure the LAN link to automatically negotiate Ethernet settings, select Auto Negotiate.
• To specify LAN link settings, select Force and select the speed and duplex settings.
8. If you are managing the Ethernet connection from the LAN (WorkPort) side of your network, select the Proxy
Management Workstation Ethernet Address on WAN check box. The SonicWALL appliance will take the
90
SonicWALL Global Management System Configuration Guide
Ethernet address of the computer that is managing the SonicWALL appliance and will proxy the address on the
WAN port of the SonicWALL. If you are not managing the SonicWALL appliance from the LAN side of your
network, the firmware looks for a random computer on the LAN which can be a lengthy search process.
9. To limit the size of packets sent over the Ethernet WAN interface, select the Fragment Outbound Packets Larger
than the WAN MTU check box and enter the maximum size in the WAN MTU field.
If the maximum transmission unit (MTU) size is too large for a remote router, it may require more transmissions. If the packet size is too small, this could result in more packet header overhead and more acknowledgements that have to be processed. The default size is 1,500 MTU.
10. To enable bandwidth management, select the Enable check box and enter the bandwidth of the connection in
the Available Bandwidth field.
11. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
Configuring ARP
ARP (Address Resolution Protocol) maps layer 3 (IP addresses) to layer 2 (physical or MAC addresses) to enable
communications between hosts residing on the same subnet. ARP is a broadcast protocol that can create excessive
amounts of network traffic on your network. To minimize the broadcast traffic, an ARP cache is maintained to store
and reuse previously learned ARP information.
To configure ARP, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the Network tree and click ARP. The ARP page appears (Figure 88).
Figure 88: ARP Page
4. To configure a specific length of time for the entry to time out, enter a value in minutes in the ARP Cache entry
time out field.
5. To view ARP cache information, click Request ARP Cache display from unit(s).
Configuring Network Settings
91
92
SonicWALL Global Management System Configuration Guide
CHAPTER 10
Configuring Network Settings for SonicOS Enhanced
This section describes how to configure network settings for SonicWALL appliances using SonicOS Enhanced.
SonicOS Enhanced introduces a large number of new concepts that simplify network management while adding
new levels of complexity and control.
This section describes how to configure the network settings for SonicWALL appliances running SonicOS
Enhanced. To configure network settings for SonicWALL appliance running SonicOS Standard, see Chapter 9,
“Configuring Network Settings.”
To configure network settings for a SonicWALL appliance using SonicOS, configure the following:
•
Interfaces
Required. Defines the networks associated with the LAN, WAN, and optional interfaces. This includes protocols, gateways, DNS servers, Virtual LANs, and management settings. For more information, see “Configuring
Interface Network Settings” on page 94.
•
WAN Failover & Load Balancing
Optional. WAN Failover enables you to configure one of the user-defined interfaces as a secondary WAN port.
For more information, see “WAN Failover and Load Balancing” on page 101.
•
Zones
Optional. Zones are logical groupings of one or more interfaces.
There is one pre-defined Zone associated with each interface as well as a VPN and Multicast Zone. These are
pre-defined with default settings that you may want to check before proceeding. For more information, see
“Configuring Zones” on page 103.
•
DNS
Optional. Defines the DNS servers. By default, the SonicWALL appliance will obtain inherit its DNS settings
from the WAN Zone. To manually specify servers, see “Configuring DNS” on page 104.
•
Dynamic DNS
Optional. Enables the SonicWALL appliance to use a DDNS service to automatically change DNS records for
dynamic changing IP addresses without manual intervention. This service allows for network access using
domain names rather than IP addresses, even when the target IP addresses change. To specify a DDNS service,
see “Configuring Dynamic DNS” on page 105.
•
Address Objects and Groups
Optional. An Address Object is a host, network, or IP address range. An Address Object Group is a group of
Address Objects or Address Object Groups. Once defined, you can quickly establish NAT Policies VPN Security Associations (SAs), firewall rules, and DHCP settings between Address Objects and Address Object
Groups with no manual configuration.
By default, Address Objects are defined for each interface, the network associated with each interface, gateways, the GMS server, and more. For information on creating custom Address Objects and Address Object
Groups, see “Configuring Address Objects” on page 107.
•
NAT Policies
Optional. Defines NAT Policies between Address Objects and Groups. For example, you could configure NAT
for all traffic that originated from the DMZ and was destined for the LAN. For more information, see “Configuring Network Address Translation” on page 110.
Configuring Network Settings for SonicOS Enhanced
93
• Web Proxy
Optional. Specifies the IP address and port of the proxy server if one is installed between the SonicWALL
appliance and the WAN network. For more information, see “Configuring Web Proxy Forwarding Settings” on
page 113.
• Routing (ENH)
Optional. Defines the gateway associated with static network routes. For more information, see “Configuring
Policy-Based Routing” on page 114.
• RIP (ENH)
Optional. Defines RIP settings for each network interface. For more information, see “Configuring Routing
Information Protocol” on page 116.
• Advanced Routing Services
Optional. SonicOS Enhanced 3.0 running on the PRO4060 and PRO5060 offers the option of enabling
Advanced Routing Services (ARS). Advanced Routing Services provides full advertising and listening support
for the Routing Information Protocol (RIPv1 - RFC1058) and (RIPv2 - RFC2453), and Open Shortest Path First
(OSPFv2 – RFC2328). For more information, see “Configuring Advanced Routing Services” on page 118
•
IP Helper
Optional. Defines DHCP and NetBIOS policies between Address Objects and Address Object Groups. For
example, you can configure all devices on VPNs to obtain their IP addresses from the LAN. For more information, see “Configuring IP Helper” on page 123.
• ARP
Optional. Defines the ARP Cache timeout settings. For more information, see “Configuring ARP” on page 124.
Configuring Interface Network Settings
This section describes how to configure each interface to communicate properly with the network to which it
attaches.
Figure 89 shows the basic interfaces for a SonicWALL appliance. The LAN interface uses a static IP address and
acts as a gateway for devices on the LAN Network. The WAN interface can use a static or dynamic IP address and
can connect to the Internet via Transmission Control Protocol (TCP), Point-to-Point Protocol over Ethernet
(PPPoE), Level 2 Tunneling Protocol (L2TP), or Point-to-Point Tunneling Protocol (PPTP). A SonicWALL appliance might have one, many, or no optional interfaces. Optional interfaces can be configured for LAN, WAN, DMZ,
WLAN, or Multicast connections, or they can be disabled.
Figure 89: Interfaces
W
A
NInterface:
S
taticorD
ynam
icIP
TC
P
,P
P
P
oE
, L2TP
, or
P
P
TP
LA
NInterface:
S
taticIP
O
P
TInterface:
S
taticorD
ynam
icIP
R
outer
LA
N
O
ptional Interface
LA
N
,W
A
N
,D
M
Z, orM
ulticast
W
A
N
Virtual Interfaces (VLAN)
On the SonicWALL PRO 4060 and SonicWALL PRO 5060 security appliances, virtual Interfaces are sub-interfaces
assigned to a physical interface. Virtual interfaces allow you to have more than one interface on one physical connection.
94
SonicWALL Global Management System Configuration Guide
Virtual interfaces provide many of the same features as physical interfaces, including Zone assignment, DHCP
Server, and NAT and Access Rule controls.
Sub-Interfaces
VLAN support on SonicOS Enhanced is achieved by means of sub-interfaces, which are logical interfaces nested
beneath a physical interface. Every unique VLAN ID requires its own sub-interface. For reasons of security and
control, SonicOS does not participate in any VLAN trunking protocols, but instead requires that each VLAN that is
to be supported be configured and assigned appropriate security characteristics.
Configure Interface Settings
To configure the network interfaces for a SonicWALL appliance, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the Network tree and click Interfaces. The Interfaces page appears (Figure 90).
Figure 90: Interfaces Page
4. Click the Edit Icon (
) of the LAN, WAN, or Optional interface. The Edit Interface property sheet appears.
5. Configure the interface settings:
Configuring Network Settings for SonicOS Enhanced
95
Edit Interface Settings
Figure 91: Edit Interface
For LAN, DMZ, or Multicast interfaces, configure the following settings:
• IP Address—Enter the IP address of the LAN interface.
• Subnet Mask—Enter the subnet mask for the network.
• Comment—Enter any comments regarding the interface.
• Management—Select from the following management options:
• HTTP—When selected, allows HTTP management from the interface.
• HTTPS—When selected, allows HTTPS management from the interface.
• Ping—When selected, the interface will respond to ping requests.
• SNMP—When selected, the interface will support Simple Network Management Protocol (SNMP).
• User Login—Select from the following user login options:
• HTTP—When selected, users will be able to login using HTTP.
• HTTPS—When selected, users will be able to login using HTTPS.
96
SonicWALL Global Management System Configuration Guide
WAN Settings
Figure 92: WAN Settings
For WAN interfaces, select how the WAN connects to the Internet from the IP Assignment list box and configure those settings:
Static—If the WAN IP address will be static, configure the following settings:
• IP Address—Enter the IP address of the interface.
• Subnet Mask—Enter the subnet mask for the network.
• Default Gateway—IP address of the WAN gateway.
• DNS Server 1-3—IP addresses of the DNS Servers.
• Comment—Enter any comments regarding the interface.
• Management—Select from the following management options:
• HTTP—When selected, allows HTTP management from the interface.
• HTTPS—When selected, allows HTTPS management from the interface.
• Ping—When selected, the interface will respond to ping requests.
• SNMP—When selected, the interface will support Simple Network Management Protocol
(SNMP).
• User Login—Select from the following user login options:
• HTTP—When selected, users will be able to login using HTTP.
• HTTPS—When selected, users will be able to login using HTTPS.
• DHCP—If the WAN IP address will use a dynamic IP address to connect to the Internet, configure the following settings:
• Host Name—Specifies the host name of the SonicWALL device on the WAN interface.
• Comment—Enter any comments regarding the interface.
• Management—Select from the following management options:
• HTTP—When selected, allows HTTP management from the interface.
• HTTPS—When selected, allows HTTPS management from the interface.
• Ping—When selected, the interface will respond to ping requests.
• SNMP—When selected, the interface will support Simple Network Management Protocol
(SNMP).
• User Login—Select from the following user login options:
• HTTP—When selected, users will be able to login using HTTP.
• HTTPS—When selected, users will be able to login using HTTPS.
•
Configuring Network Settings for SonicOS Enhanced
97
• IP Address, Subnet Mask, Gateway (Router) Address, and DNS Server 1-3—automatically filledin.
• Renew—Renews the IP address.
• Release—Releases the current IP address.
• PPPoE—If the WAN IP address will use PPPoE to connect to the Internet, configure the following settings:
• User Name—Enter username provided by the ISP.
• Password—Enter the password used to authenticate the username with the ISP. This field is case-sensitive.
• Comment—Enter any comments regarding the interface.
• Management—Select from the following management options:
• HTTP—When selected, allows HTTP management from the interface.
• HTTPS—When selected, allows HTTPS management from the interface.
• Ping—When selected, the interface will respond to ping requests.
• SNMP—When selected, the interface will support Simple Network Management Protocol
(SNMP).
• User Login—Select from the following user login options:
• HTTP—When selected, users will be able to login using HTTP.
• HTTPS—When selected, users will be able to login using HTTPS.
• Inactivity Disconnect—Specify how long (in minutes) the SonicWALL appliance waits before disconnecting from the Internet.
• Select from the following:
• To configure the SonicWALL appliance(s) to dynamically obtain an IP address, select Obtain an
IP Address automatically.
• To configure the SonicWALL appliance(s) to use a fixed IP address, select Use the following IP
Address and enter the IP address.
• Select from the following:
• To configure the SonicWALL appliance(s) to obtain the DNS server information automatically,
select Obtain DNS Server Address Automatically.
• To specify DNS servers, select Specify DNS Servers and enter the DNS Server IP addresses.
• PPTP—If the WAN IP address will use PPTP to connect to the Internet, configure the following settings:
• User Name—Enter username provided by the ISP.
• User Password—Enter the password used to authenticate the username with the ISP. This field is casesensitive.
• PPTP Server IP Address—this information is provided by your ISP.
• PPTP (Client) Host Name—this information is provided by your ISP.
• Comment—Enter any comments regarding the interface.
• Management—Select from the following management options:
• HTTP—When selected, allows HTTP management from the interface.
• HTTPS—When selected, allows HTTPS management from the interface.
• Ping—When selected, the interface will respond to ping requests.
• SNMP—When selected, the interface will support Simple Network Management Protocol
(SNMP).
• User Login—Select from the following user login options:
• HTTP—When selected, users will be able to login using HTTP.
• HTTPS—When selected, users will be able to login using HTTPS.
• Inactivity Disconnect—Specify how long (in minutes) the SonicWALL appliance waits before disconnecting from the Internet.
• Select from the following from the PPTP IP Assignment list box:
• To configure the SonicWALL appliance(s) to dynamically obtain an IP address, select DHCP.
• To configure the SonicWALL appliance(s) to use a fixed IP address, select Static and enter the IP
address, subnet mask, and gateway IP address.
• L2TP——If the WAN IP address will use L2TP to connect to the Internet, configure the following settings:
• User Name—Enter username provided by the ISP.
98
SonicWALL Global Management System Configuration Guide
•
•
•
•
•
•
•
•
User Password—Enter the password used to authenticate the username with the ISP. This field is casesensitive.
L2TP Server IP Address—this information is provided by your ISP.
L2TP (Client) Host Name—this information is provided by your ISP.
Comment—Enter any comments regarding the interface.
Management—Select from the following management options:
• HTTP—When selected, allows HTTP management from the interface.
• HTTPS—When selected, allows HTTPS management from the interface.
• Ping—When selected, the interface will respond to ping requests.
• SNMP—When selected, the interface will support Simple Network Management Protocol
(SNMP).
User Login—Select from the following user login options:
• HTTP—When selected, users will be able to login using HTTP.
• HTTPS—When selected, users will be able to login using HTTPS.
Inactivity Disconnect—Specify how long (in minutes) the SonicWALL appliance waits before disconnecting from the Internet.
Select from the following from the L2TP IP Assignment list box:
• To configure the SonicWALL appliance(s) to dynamically obtain an IP address, select DHCP.
• To configure the SonicWALL appliance(s) to use a fixed IP address, select Static and enter the IP
address, subnet mask, and gateway IP address.
6. Click Update. The settings are saved. To clear any changes and start over, click Reset.
7. Click the Ethernet tab and configure the following settings:
Communication Settings—Specify the following settings:
• To configure the interface to automatically negotiate Ethernet settings, select Auto Negotiate.
• To specify ethernet settings, select Force and select the speed and duplex settings.
• WAN Only. Interface MTU—Specify the size of the Maximum Transmission Unit (MTU) in octets
(default: 1500).
• To fragment packets that are larger than this MTU, select the Fragment non-VPN outbound packets
larger than this Interface's MTU check box.
•
Note: If the maximum transmission unit (MTU) size is too large for a remote router, it may require more
transmissions. If the packet size is too small, this could result in more packet header overhead and more
acknowledgements that have to be processed.
• To ignore Don’t Fragment (DF) bits from routers connected to the SonicWALL appliance, select the
Ignore Don't Fragment (DF) Bit check box.
• WAN Only. Bandwidth Management—To enable bandwidth management on this interface, select the
Enable check box and enter the bandwidth of the connection in the Available Interface Bandwidth field
in kilobytes per second (Kbps).
8. Click Update. The settings are saved. To clear any changes and start over, click Reset.
Configuring VLAN Sub-Interfaces
When you add a VLAN sub-interface, you need to assign it to a Zone, assign it a VLAN Tag, and assign it to a
physical interface. Based on your zone assignment, you configure the VLAN sub-interface the same way you configure a physical interface for the same zone.
Adding a virtual interface
1. In the left-navigation menu click on Network and then Interfaces to display the Network > Interfaces page.
2. At the bottom of the Interface Settings table, click Add Interface. The Edit Interface window displays.
Configuring Network Settings for SonicOS Enhanced
99
Figure 93: Add Interface
3. Select a Zone to assign to the interface. You can select LAN, WAN, DMZ, WLAN, or a custom zone. The zone
assignment does not have to be the same as the parent (physical) interface. In fact, the parent interface can even
remain Unassigned.
Your configuration choices for the network settings of the sub-interface depend on the zone you select.
• LAN, DMZ, or a custom zone of Trusted type: Static or Transparent
• WAN or a custom zone of Untrusted type: DHCP, Static, PPPoE, PPTP, or L2TP
• WLAN or a custom Wireless zone: static IP only (no IP Assignment list)
4. Assign a VLAN tag (ID) to the sub-interface. Valid VLAN ID’s are 1 to 4095, although some switches reserve
VLAN 1 for native VLAN designation. You will need to create a VLAN sub-interface with a corresponding
VLAN ID for each VLAN you wish to secure with your security appliance.
5. Declare the parent (physical) interface to which this sub-interface will belong. There is no per-interface limit to
the number of sub-interfaces you can assign – you may assign sub-interfaces up to the system limit (200 for the
PRO 4060, 400 for the PRO 5060).
6. Configure the sub-interface network settings based on the zone you selected. Select the management and userlogin methods for the sub-interface.
7. Click OK.
The Virtual interface displays in the VLAN Interfaces table below the Interfaces table
100
SonicWALL Global Management System Configuration Guide
Figure 94: Interfaces Page with VLAN Sub-interfaces
Click the Edit Icon (
) of the VLAN sub-interface to edit its settings.
WAN Failover and Load Balancing
WAN Failover enables you to configure one of the user-defined interfaces as a secondary WAN port. The secondary
WAN port can be used in a simple “active/passive” setup to allow traffic to be only routed through the secondary
WAN port if the Primary WAN port is unavailable. This allows the SonicWALL to maintain a persistent connection
for WAN port traffic by “failing over” to the secondary WAN port.
This feature also allows you to perform simple load balancing for the WAN traffic on the SonicWALL. You can
select a method of dividing the outbound WAN traffic between the two WAN ports and balance network traffic.
The SonicWALL can monitor WAN traffic using Physical Monitoring which detects if the link is unplugged or disconnected, or Physical and Logical Monitoring, which monitors traffic at a higher level, such as upstream connectivity interruptions.
Note: Before you begin, be sure you have configured a user-defined interface to mirror the WAN port settings.
To configure the WAN Failover for a SonicWALL appliance, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the Network tree and click WAN Failover & LB. The WAN Failover & LB page appears (Figure 95).
Configuring Network Settings for SonicOS Enhanced
101
Figure 95: WAN Failover & LB Page
4. Select the Enable Load Balancing check box.
5. Select the secondary interface from the Secondary WAN Interface list box.
Note: If this is not configured, you will need to configure a WAN interface from the Network | Interfaces page.
6. Specify how often the SonicWALL appliance will check the interface (5-300 seconds) in the Check interface
every field (default: 5 seconds).
7. Specify the number of times the SonicWALL appliance tests the interface as inactive before failing over
(default: 3). For example, if the SonicWALL appliance tests the interface every 5 seconds and finds the interface inactive after 3 successive attempts, it will fail over to the secondary interface after 15 seconds.
8. Specify the number of times the SonicWALL appliance tests the interface as active before failing back to the
primary interface (default: 3). For example, if the SonicWALL appliance tests the interface every 5 seconds and
finds the interface active after 3 successive attempts, it will fail back to the primary interface after 15 seconds.
9. To configure outbound load balancing, select from the following:
Basic Active/Passive Failover—The SonicWALL appliance will not load-balance outbound traffic and
will only use the secondary interface when the primary fails. To configure the SonicWALL appliance to fail
back to the primary interface when it becomes available, select the Preempt and failback to Primary
WAN when possible check box.
• Per Connection Round-Robin—The SonicWALL appliance will load-balance outbound traffic using an
alternating or round-robin method.
• Spillover-Based—The SonicWALL appliance will load-balance outbound traffic when the primary WAN
exceeds the bandwidth setting that you specify in the Send traffic to Secondary WAN when bandwidth
exceeds: field.
• Percentage-Based—The SonicWALL appliance will load-balance outbound traffic according to the percentages that you specify in the Primary WAN Percentage and the Secondary WAN Percentage fields.
•
10. The SonicWALL appliance can monitor the WAN by detecting whether the link is unplugged or disconnected
or by sending probes to a target IP address of an “always available” target upstream device on the WAN net-
102
SonicWALL Global Management System Configuration Guide
work, such as an ISP side router. To enable probe monitoring, select the Enable Probe Monitoring check box
and configure the following settings:
Primary WAN Probe Settings—Select the protocol used for monitoring and enter the IP address and port
(TCP only) of the probe target. If there will be an optional probe target, specify these settings also and
select whether the SonicWALL appliance must test both targets or either target.
• Secondary WAN Probe Settings—Select the protocol used for monitoring and enter the IP address and
port (TCP only) of the secondary probe target. If there will be an optional secondary probe target, specify
these settings also and select whether the SonicWALL appliance must test both targets or either target.
•
11. When you are finished, click Update. The settings are changed for the selected SonicWALL appliance. To clear
all screen settings and start over, click Reset.
Configuring Zones
A Zone is a logical grouping of one or more interfaces designed to make management, such as the definition and
application of Access Rules, a simpler and more intuitive process than following a strict physical interface scheme.
There are four fixed Zone types: Trusted, Untrusted, Public, and Encrypted. Trusted is associated with LAN Zones.
These fixed Zone types cannot be modified or deleted. A Zone instance is created from a Zone type and named
accordingly, i.e Sales, Finance, etc.
Only the number of interfaces limits the number of Zone instances for Trusted and Untrusted Zone types. The
Untrusted Zone type (i.e. the WAN) is restricted to two Zone instances. The Encrypted Zone type is a special system Zone comprising all VPN traffic and doesn’t have any associated interfaces.
Trusted and Public Zone types offer an option, Interface Trust, to automate the creation of Access Rules to allow
traffic to flow between the Interfaces of a Zone instance. For example, if the LAN Zone has interfaces X0, X3, and
X5 assigned to it, checking Allow Interface Trust on the LAN Zone creates the necessary Access Rules to allow
hosts on these Interfaces to communicate with each other.
To add or edit a Zone, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the Network tree and click Zones. The Zones page appears (Figure 96).
Figure 96: Zones Page
4. Click the Edit Icon (
) for a Zone or click Add New Zone. The Edit Zone or Add Zone dialog box appears.
Configuring Network Settings for SonicOS Enhanced
103
Figure 97: Adding or Editing a Zone
5. If this is a new Zone, enter a name for the Zone.
6. Select the Security Type.
7. To configure the SonicWALL appliance to automatically create the rules that allow data to freely flow between
interfaces in the same Zone, select the Allow Interface Trust check box.
8. To enforce content filtering on multiple interfaces in the same Trusted or Public Zones, select the Enforce
Content Filtering Service check box.
9. To enforce network anti-virus protection on multiple interfaces in the same Trusted or Public Zones, select the
Enforce Network Anti-Virus Service check box.
10. To enforce gateway anti-virus protection on multiple interfaces in the same Trusted or Public Zones, select the
Enable Gateway Anti-Virus Service.
11. To enforce Intrusion Prevention Services (IPS) on multiple interfaces in the same Trusted or Public Zones,
select the Enable IPS check box.
12. To enforce security policies for Global Security Clients on multiple interfaces in the same Trusted or Public
Zones, select Enforce Global Security Clients.
13. To automatically create a GroupVPN policy for this zone, select Create Group VPN.
14. When you are finished, click Update. The Zone is modified or added for selected SonicWALL appliance. To
clear all settings and start over, click Reset.
Configuring DNS
Domain Name System (DNS) is the Internet standard for locating domain names and translating them into IP
addresses. To configure DNS, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the Network tree and click DNS. The DNS page appears (Figure 98).
104
SonicWALL Global Management System Configuration Guide
Figure 98: DNS Page
4. Select from the following:
To specific IP addresses manually, select Specify DNS Servers Manually and enter the IP addresses of two
or three DNS servers.
• To inherit the DNS settings from the WAN Zone configuration, select Inherit DNS Settings Dynamically
from WAN Zone.
•
5. When you are finished, click Update. The settings are changed for the selected SonicWALL appliance. To clear
all screen settings and start over, click Reset.
Configuring Dynamic DNS
Dynamic DNS (DDNS) is a service provided by various companies and organizations that allows for dynamic
changing IP addresses to automatically update DNS records without manual intervention. This service allows for
network access using domain names rather than IP addresses, even when the target’s IP addresses change.
To configure Dynamic DNS on the SonicWALL security appliance, perform these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the Network tree and click Dynamic DNS. The Dynamic DNS page appears (Figure 99).
Configuring Network Settings for SonicOS Enhanced
105
Figure 99: Dynamic DNS Page
4. Click Add Dynamic DNS Profile. The Add Dynamic DNS Profile window is displayed (Figure 100)
Figure 100: Add Dynamic DNS Profile
5. Select the Provider from the drop-down list at the top of the page. This example uses DynDNS.org. Dyndns.org
requires the selection of a service. This example assumes you have created a dynamic service record with
dyndns.org.
6. Enter a name to assign to the DDNS entry in the Profile Name field. This can be any value used to identify the
entry in the Dynamic DNS Settings table.
7. If Enable this profile is checked, the profile is administratively enabled, and the SonicWALL security appliance takes the actions defined in the Online Settings section on the Advanced tab.
8. If Use Online Settings is checked, the profile is administratively online.
9. Enter your dyndns.org username and password in the User Name and Password fields.
10. Enter the fully qualified domain name (FQDN) of the hostname you registered with dyndns.org in the Domain
Name field. Make sure you provide the same hostname and domain as you configured.
11. You may optionally select Enable Wildcard and/or configure an MX entry in the Mail Exchanger field.
Check Backup MX if your DDNS provider allows for the specification of an alternative IP address for the MX
record.
12. Click the Advanced tab. You can typically leave the default settings on this page (Figure 101).
106
SonicWALL Global Management System Configuration Guide
Figure 101: Advanced Tab
13. The On-line Settings section provides control over what address is registered with the dynamic DNS provider.
The options are:
Let the server detect IP Address - The dynamic DNS provider determines the IP address based upon
the source address of the connection. This is the most common setting.
• Automatically set IP Address to the Primary WAN Interface IP Address - This will cause the SonicWALL device to assert its WAN IP address as the registered IP address, overriding auto-detection by
the dynamic DNS server. Useful if detection is not working correctly.
• Specify IP Address manually - Allows for the IP address to be registered to be manually specified and
asserted.
•
14. The Off-line Settings section controls what IP Address is registered with the dynamic DNS service provider if
the dynamic DNS entry is taken off-line locally (disabled) on the SonicWALL. The options are:
Do nothing - the default setting. This allows the previously registered address to remain current with
the dynamic DNS provider.
• Use the Off-Line IP Address previously configured at Providers site - if your provider supports
manual configuration of Off-Line Settings, you can select this option to use those settings when this
profile is taken administratively offline.
• Make Host Unknown - Unregisters the entry.
• Specify IP Address manually •
15. When you are finished, click Update. The settings are changed for the selected SonicWALL appliance. To clear
all screen settings and start over, click Reset.
Configuring Address Objects
An Address Object is a host, network, or IP address range. An Address Object Group is a group of Address Objects
or other Address Object Groups. Once defined, you can quickly establish NAT Policies, VPN Security Associations
(SAs), firewall rules, and DHCP settings between Address Objects and Address Object Groups without individual
configuration.
All SonicWALL appliances come with a group of pre-defined default network objects. These include subnets for
each interface, interface IP addresses for each interface, management IP addresses, and more.
Creating an Address Object
To create an address object, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the Network tree and click Address Objects. The Address Objects page appears (Figure 102).
Configuring Network Settings for SonicOS Enhanced
107
Figure 102: Address Objects Page
4. Scroll to the bottom of the page and click Add New Address Object.
Figure 103: Adding an Address Object
5. Enter a name for the Address Object in the Name field.
6. Select from the following:
• To specify an individual IP address, select Host from the Type field and enter the IP address.
• To specify an IP address range, select Range from the Type field and enter the starting and ending IP
addresses.
• To specify a network, select Network from the Type field and enter the IP address and subnet mask.
7. Select the zone to which this Address Object will be assigned from the Zone Assignment list box.
8. When you are finished, click OK.
9. Repeat this procedure for each Address Object to add.
108
SonicWALL Global Management System Configuration Guide
Network Address Object Deletion
GMS now enables you to delete a single address object more conveniently. To delete network address objects, perform the following steps:
1. Navigate to the Policies Panel.
2. Go to the Network > Settings page.
3. Click on the Trashcan icon of the selected address object.
Creating an Address Object Group
To create an Address Object Group, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the Network tree and click Address Objects. The Address Objects page appears (Figure 104).
Configuring Network Settings for SonicOS Enhanced
109
Figure 104: Address Objects Page
4. Scroll down and click Add New Group.
Figure 105: Adding an Address Object Group
5. Enter a name for the Address Object Group in the Name field.
6. Select an object or group that will be a part of the Address Object Group and click the right arrow.
7. Repeat Step 6 for each object or group to add.
8. When you are finished, click OK.
9. Repeat this procedure for each Address Object Group to add.
Configuring Network Address Translation
SonicWALL appliances support Network Address Translation (NAT). NAT is the automated translation of IP
addresses between different networks. For example, a company might use private IP addresses on a LAN that are
represented by a single IP address on the WAN side of the SonicWALL appliance.
SonicWALL appliances support two types of NAT:
Address-to-Address Translation—local addresses are matched to public IP addresses. For example, the private IP address 10.50.42.112 might be mapped to the public IP address 132.22.3.2.
• Port Translation or Network Address Port Translation (NAPT)—local addresses are dynamically matched
to public IP address/port combinations (standard TCP ports). For example, the private IP address
192.168.102.12 might be mapped to the public IP address 48.12.11.1 using port 2302.
•
Note: IP address/port combinations are dynamic and not preserved for new connections. For example, the first
connection for IP address might use port 2302, but the second connection might use 2832.
110
SonicWALL Global Management System Configuration Guide
Common Types of Mapping
SonicWALL supports several types of address mapping. These include
One-to-One Mapping—one local IP address is mapped to one public IP address using Address-to-Address
translation.
• Many-to-One Mapping—many local IP addresses are mapped to a single public IP address using NAPT.
• Many-to-Many Mapping—many local IP addresses are mapped to many public IP addresses. If the number of
public IP addresses are greater than or equal to the number of local IP addresses, the SonicWALL appliance
uses Address-to-Address translation. If the number of public IP addresses is less than the number of local IP
addresses, the SonicWALL appliance uses NAPT. For example. If there are 10 private IP addresses and 5 public
IP addresses, two private IP addresses will be assigned to each public IP address using NAPT.
•
SonicWALL NAT Policy Fields
When configuring a NAT Policy, you will configure a group of settings that specify how the IP address originates
and how it will be translated. Additionally, you can apply a group of filters that allow you to apply different policies
to specific services and interfaces.
•
Original Source—used to remap IP addresses based on the source address, this field specifies an Address
Object that can consist of an IP address or IP address range.
Note: This field can also be used as a filter.
• Translated Source—specifies the IP address or IP address range to which the original source will be mapped.
• Original Destination—used to remap IP addresses based on the destination address, this field specifies an
Address Object that can consist of an IP address or IP address range.
•
•
•
•
•
Note: This field can also be used as a filter.
Translated Destination—specifies the IP address or IP address range to which the original source will be
mapped.
Original Service—used to filter destination addresses by service, this field specifies a Service Object that can
be a single service or group of services.
Translated Service—.specifies the service or port to which the original service will be remapped.
Source Interface—filters source addresses by interface.
Destination Interface—filters destination addresses by interface.
Common Configuration Types
One-to-One Mapping
To configure one-to-one mapping from the private network to the public network, select the Address Object that
corresponds to the private network IP address in the Original Source field and the public IP address that it will
used to reach the Internet in the Translated Source field. Leave the other fields alone, unless you want to filter by
service or interface.
Note: If you map more than one private IP address to the same public IP address, the private IP addresses will
automatically be configured for port mapping or NAPT.
To configure one-to-one mapping from the public network to the private network, select the Address Object that
corresponds to the public network IP address in the Original Destination field and the private IP address that it will
used to reach the server in the Translated Destination field. Leave the other fields alone, unless you want to filter
by service or interface.
Note: If you map one public IP address to more than one private IP address, the public IP addresses will be mapped
to the first private IP address. Load balancing is not supported. Additionally, you must set the Original Source to
Any.
Many-to-One Mapping
To configure many-to-one mapping from the private network to the pubic network, select the select the Address
Object that corresponds to the private network IP addresses in the Original Source field and the public IP address
that it will used to reach the Internet in the Translated Source field. Leave the other fields alone, unless you want
to filter by service or interface.
Configuring Network Settings for SonicOS Enhanced
111
Note: You can also specify Any in the Original Source field and the Address Object of the LAN interface in the
Translated Source field.
Many-to-Many Mapping
To configure many-to-many mapping from the private network to the pubic network, select the select the Address
Object that corresponds to the private network IP addresses in the Original Source field and the public IP
addresses to which they will be mapped in the Translated Source field. Leave the other fields alone, unless you
want to filter by service or interface.
Note: If the IP address range specified in the Original Source is larger than the Translated Source, the SonicWALL
appliance will use port mapping or NAPT. If the Translated Source is equal to or larger than the Original Source,
addresses will be individually mapped.
To configure many-to-many mapping from the public network to the private network, select the Address Object that
corresponds to the public network IP addresses in the Original Destination field and the IP addresses on the private network in the Translated Destination field. Leave the other fields alone, unless you want to filter by service
or interface.
Note: If the IP address range specified in the Original Destination is smaller than the Translated Destination, the
SonicWALL appliance will be individually mapped to the first translated IP addresses in the translated range. If the
Translated Destination is equal to or smaller than the Original Destination, addresses will be individually mapped.
Configuring NAT Policies
To configure NAT Policies, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the Network tree and click NAT Policies. The NAT Policies page appears (Figure 106).
Figure 106: NAT Policies Page
4. To edit an existing policy, click its Edit Icon (
112
). To add a new policy, click Add NAT Policy.
SonicWALL Global Management System Configuration Guide
Figure 107: NAT Policies Page
5. Configure the following:
•
•
•
•
•
•
•
•
Original Source—used to remap IP addresses based on the source address, this field specifies an Address
Object that can consist of an IP address or IP address range.
Translated Source—specifies the IP address or IP address range to which the original source will be
mapped.
Original Destination—used to remap IP addresses based on the destination address, this field specifies an
Address Object that can consist of an IP address or IP address range.
Translated Destination—specifies the IP address or IP address range to which the original source will be
mapped.
Original Service—used to filter source addresses by service, this field specifies a Service Object that can
be a single service or group of services.
Translated Service—used to filter destination addresses by service, this field specifies a Service Object
that can be a single service or group of services.
Source Interface—filters source addresses by interface.
Destination Interface—filters destination addresses by interface.
6. To enable the NAT policy, select the Enable check box.
7. Add any comments to the Comments field.
8. When you are finished, click Update. The policy is added and you are returned to the NAT Policies screen.
9. Repeat Steps 4 through 8 for each policy to add.
Configuring Web Proxy Forwarding Settings
A Web proxy server intercepts HTTP requests and determines if it has stored copies of the requested Web pages. If
it does not, the proxy completes the request to the server on the Internet, returning the requested information to the
user and also saving it locally for future requests.
Setting up a Web proxy server on a network can be cumbersome, because each computer on the network must be
configured to direct Web requests to the server.
If there is a proxy server on the SonicWALL appliance’s network, you can move the SonicWALL appliance
between the network and enable Web Proxy Forwarding. This will forward all WAN requests to the proxy server
without requiring the computers to be individually configured.
To configure Web Proxy Forwarding settings, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the Network tree and click Web Proxy. The Web Proxy page appears (Figure 108).
Configuring Network Settings for SonicOS Enhanced
113
Figure 108: Web Proxy Page
4. Enter the name or IP address of the proxy server in the Proxy Web Server field.
5. Enter the proxy IP port in the Proxy Web Server Port field.
6. To bypass the Proxy Server if a failure occurs, select the Bypass Proxy Servers Upon Proxy Server Failure
check box.
7. If you have clients configured on the DMZ, select the Forward DMZ Client Requests to Proxy Server check
box.
8. When you are finished, click Update. The settings are changed for the selected SonicWALL appliance. To clear
all screen settings and start over, click Reset.
Configuring Policy-Based Routing
If you have routers on your interfaces, you can configure the SonicWALL appliance to route network traffic to specific predefined destinations.
Static routes must be defined if the network connected to an interface is segmented into subnets, either for size or
practical considerations. For example, a subnet can be created to isolate a section of a company, such as finance,
from network traffic on the rest of the LAN, DMZ, or WAN.
To add static routes, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the Network tree and click Routing. The Routing page appears (Figure 109).
114
SonicWALL Global Management System Configuration Guide
Figure 109: Routing Page
4. Click Add Route Policy.
Figure 110: Routing Page
5. Select the source address object from the Source list box.
6. Select the destination address object from the Destination list box.
7. Specify the type of service that will be routed from the Service list box.
8. Select the address object that will act as a gateway for packets matching these settings.
9. Select the interface through which these packets will be routed from the Interface list box.
10. Specify the RIP metric in the Metric field.
11. When you are finished, click Update. The route settings are configured for the selected SonicWALL appliance(s). To clear all screen settings and start over, click Reset.
12. Repeat Steps 4 through 11 for each route to add.
13. When you are finished, click Update. The settings are saved.
Configuring Network Settings for SonicOS Enhanced
115
Configuring Routing Information Protocol
Routing Information Protocol (RIP) is a distance-vector routing protocol that is commonly used in small homogeneous networks. Using RIP, a router will periodically send its entire routing table to its closest neighbor, which
passes the information to its next neighbor, and so on. Eventually, all routers within the network will have the information about the routing paths. When attempting to route packets, a router will check the routing table and select
the path that requires the fewest hops.
SonicWALL appliances support RIPv1 or RIPv2 to advertise its static and dynamic routes to other routers on the
network. Changes in the status of VPN tunnels between the SonicWALL and remote VPN gateways are also
reflected in the RIPv2 advertisements. Choose between RIPv1 or RIPv2 based on your router’s capabilities or configuration. RIPv1 is an earlier version of the protocol that has fewer features, and it also sends packets via broadcast
instead of multicast. RIPv2 packets are backwards-compatible and can be accepted by some RIPv1 implementations that provide an option of listening for multicast packets. The RIPv2 Enabled (broadcast) selection broadcasts
packets instead of multicasting packets is for heterogeneous networks with a mixture of RIPv1 and RIPv2 routers.
To configure RIP, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the Network tree and click RIP (ENH). The RIP (ENH) page appears (Figure 111).
Figure 111: RIP Page
4. Click the Edit Icon (
116
) for an interface. The Edit Route Advertising Settings dialog box appears.
SonicWALL Global Management System Configuration Guide
Figure 112: Edit Route Advertising Settings Dialog Box
5. Select the RIP version from the RIP Advertisements list box:
RIPv1 Enabled—first version of RIP.
RIPv2 Enabled (multicast)—sends route advertisements using multicasting (a single data packet to
specific nodes on the network).
• RIPv2 Enabled (broadcast)—sends route advertisements using broadcasting (a single data packet to
all nodes on the network).
•
•
6. To advertise static routes that you specified on the Routes page, select the Advertise Static Routes check box.
7. To advertise remote VPN networks that you specified on the Routes page, select the Advertise Remote VPN
Networks check box.
8. To set the amount of time between a VPN tunnel state change and the time the change is advertised, enter a
value in the Route Change Damp Time field (default: 30 seconds).
9. To specify the number of advertisements that are sent after a route is deleted, enter a value in the Deleted Route
Advertisements field (default: 5 advertisements).
10. By default, the connection between this router and its neighbor counts as one hop. However, there are cases
where you want to discourage or reduce the use of this route by adding additional hops. To change the hop
count of this route, enter the number of hops in the Route Metric field.
11. Optional. If RIPv2 is selected from the Route Advertisements list box, you can enter a value for the Route
Tag. This value is implementation-dependent and provides a mechanism for routers to classify the originators
of RIPv2 advertisements.
12. Optional. Select from the following RIPv2 Authentication options:
User Defined—Enter 4 hex digits in the Authentication Type field and 32 hex digits in the Authentication Data field.
• Cleartext Password—Enter a password (16 characters or less) in the Authentication Password field.
• MD5 Digest—Enter a numerical value from 0-255 in the Authentication Key-Id field. Enter a 32 hex digit
value for the Authentication Key field, or use the generated key.
•
13. When you are finished, click Update. The settings are changed for the SonicWALL appliance. To clear all
screen settings and start over, click Reset.
14. Repeat this procedure for each interface to configure.
Configuring Network Settings for SonicOS Enhanced
117
Configuring Advanced Routing Services
SonicOS Enhanced 3.0 running on the PRO4060 and PRO5060 offers the option of enabling Advanced Routing
Services (ARS). Advanced Routing Services provides full advertising and listening support for the Routing
Information Protocol (RIPv1 - RFC1058) and (RIPv2 - RFC2453), and Open Shortest Path First (OSPFv2 –
RFC2328). Advanced Routing Service should only be enabled by those environments requiring support for either
or both of these dynamic routing protocols.
This section provides configuration procedures to enable Advanced Routing services.
To configure Advanced Routing, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the Network tree and click RIP (ENH). The RIP (ENH) page appears (Figure 113).
Figure 113: RIP Page
4. Select Use Advanced Routing and click update. The RIP (ENH) page displays the advanced routing settings.
118
SonicWALL Global Management System Configuration Guide
Figure 114: RIP Page
Configuring RIP
1. Click the Edit Icon ( ) for an interface in the Edit column for RIP. The Edit RIP Route Advertisement dialog
box appears (Figure 115).
Figure 115: Edit RIP Route Advertisement Dialog Box
Configuring Network Settings for SonicOS Enhanced
119
2. Select the RIP mode from the RIP list box:
• Disabled – RIP is disabled on this interface
• Send and Receive – The RIP router on this interface will send updates and process received updates.
• Send Only – The RIP router on this interface will only send updates, and will not process received
updates. This is similar to the basic routing implementation.
• Receive Only – The RIP router on this interface will only process received updates.
• Passive – The RIP router on this interface will not process received updates, and will only send updates
to neighboring RIP routers specified with the CLI ‘neighbor’ command. This mode should only be used
when configuring advanced RIP options from the ars-rip CLI.
3. If you selected Send and Receive or Receive Only modes, select one of the following options from the
Receive list box:
• RIPv1 – Receive only broadcast RIPv1 packets.
• RIPv2 – Receive only multicast RIPv2 packets. RIPv2 packets are sent by multicast, although some
implementations of RIP routers (including basic routing on SonicWALL devices) have the ability to
send RIPv2 in either broadcast or multicast formats.
4. If you selected Send and Receive or Send Only, select one of the following options from the Send list box.
• RIPv1 – Send only broadcast RIPv1 packets.
• RIPv2 - v1 compatible – Send only broadcast RIPv2 packets.
• RIPv2 – send only multicast RIPv2 packets. RIPv2 packets are sent by multicast, although some implementations of RIP routers (including basic routing on SonicWALL devices) have the ability to send
RIPv2 in either broadcast or multicast formats.
5. To suppress the inclusion of routes sent in updates to routers from which they were learned, select
Split Horizon. This is a common RIP mechanism for preventing routing loops.
6. Select Poison Reverse as an optional mode of Split Horizon operation. Rather than suppressing the inclusion
of learned routes, the routes are sent with a metric of infinity (16) thus indicating that they are unreachable.
7. To enable the use of a plain-text password on this interface, select Use Password and enter up to a 16 alphanumeric character password in the Password (Max 16 chars.) field.
8. When you are finished, click Update. The settings are changed for the SonicWALL appliance. To clear all
screen settings and start over, click Reset.
9. Repeat this procedure for each interface to configure.
Configuring OSPF
1. Click the Edit Icon ( ) for an interface in the Edit column for OSPF. The Edit OSPF Route Advertisement
dialog box appears (Figure 116).
Figure 116: Edit OSPF Route Advertisement Dialog Box
2. Select one of the following options from the OSPFv2 list box:
• Disabled – OSPF Router is disabled on this interface
• Enabled – OSPF Router is enabled on this interface
• Passive – The OSPF router is enabled on this interface, but only advertises connected networks using
type 1 LSA’s (Router Link Advertisements) into the local area. This is different from the ‘Redistribute
120
SonicWALL Global Management System Configuration Guide
Connected Networks’ options, which would cause the OSPF router to behave as an ASBR, and to use
type 5 LSA’s (AS External Link Advertisement) to flood the advertisements into all non-stub areas. See
the ‘OSPF Terms’ section for more information.
3. Specify the OSPF area represented in either IP or decimal notation in the OSPF Area field.
4. Select one of the following options from the OSPFv2 Area Type list box:
•
•
•
•
Normal
Stub Area
Totally Stubby Area
Not-So-Stubby Area
5. In the Dead Interval field, specify the period after an entry in the LSDB is removed if not Hello is received.
The default is 40 seconds, with a minimum of 1 and a maximum on 65,535. Be sure this value agrees with the
other OSPF routers on the segment for successful neighbor establishment.
6. In the Hello Interval field, specify the period of time between Hello packets. The default is 10 seconds, with a
minimum of 1 and a maximum on 65,535. Be sure this value agrees with the other OSPF routers on the segment
for successful neighbor establishment.
7. In the Interface Cost field, specify the overhead of sending packets across this interface. The default value is
10, generally used to indicate an Ethernet interface. The minimum value is 1 (e.g. Fast Ethernet) and the maximum value is 65,535.
8. In the Router Priority field, specify the router priority value used in determining the Designated Router (DR)
for a segment. The higher the value, the higher the priority. In the event of a priority tie, the Router ID will act
as the tie-breaker. Setting a value of 0 makes the OSPF router on this interface ineligible for DR status. The
default value is 1, and the maximum value is 255.
9. Specify one of the following authentication methods from the Authentication list box. Be sure this setting
agrees with the other OSPF routers on the segment for successful neighbor establishment.
• Disabled – No authentication is used on this interface.
• Simple Password – A plain-text password is used for identification purposes by the OSPF router on
this interface.
• Message Digest – An MD5 hash is used to securely identify the OSPF router on this interface.
10. If you selected Simple Password in the Authentication list box, enter up to a 16 alpha-numeric character
password in the Password (Max 16 chars.) field.
11. When you are finished, click Update. The settings are changed for the SonicWALL appliance. To clear all
screen settings and start over, click Reset.
12. Repeat this procedure for each interface to configure.
Configuring Network Settings for SonicOS Enhanced
121
Configuring Global RIP Configuration
•
•
•
•
•
•
•
Default Metric – Used to specify the metric that will be used when redistributing routes from other (Default,
Static, Connected, OSPF, or VPN) routing information sources. The default value (undefined) is 1 and the maximum is 15.
Administrative Distance – The administrative distance value is used by routers in selecting a path when there
is more than one route to a destination, with the smaller distance being preferred. The default value is 120, minimum is 1, and maximum is 255.
Originate Default Route – This checkbox enables or disables the advertising of the SonicWALL’s default
route into the RIP system.
Redistribute Static Routes – Enables or disables the advertising of static (Policy Based Routing) routes into
the RIP system. The metric can be explicitly set for this redistribution, or it can use the value (default) specified
in the ‘Default Metric’ setting.
Redistribute Connected Networks - Enables or disables the advertising of locally connected networks into the
RIP system. The metric can be explicitly set for this redistribution, or it can use the value (default) specified in
the ‘Default Metric’ setting.
Redistribute OSPF Routes - Enables or disables the advertising of routes learned via OSPF into the RIP system. The metric can be explicitly set for this redistribution, or it can use the value (default) specified in the
‘Default Metric’ setting.
Redistribute Remote VPN Networks - Enables or disables the advertising of static (Policy Based Routing)
routes into the RIP system. The metric can be explicitly set for this redistribution, or it can use the value
(default) specified in the ‘Default Metric’ setting.
Configuring Global OSPF Configuration
OSPF Router ID – The Router ID can be any value, represented in IP address notation. It is unrelated to the
any of the IP addresses on the SonicWALL, and can be set to any unique value within your OSPF network.
• Default Metric – Used to specify the metric that will be used when redistributing routes from other (Default,
Static, Connected, RIP, or VPN) routing information sources. The default value (undefined) is 1 and the maximum is 16,777,214.
• ABR Type – Allows for the specification of the topology with which this OSPF router will be participating, for
the sake of compatibility. The options are:
• Standard – Full RFC2328 compliant ABR OSPF operation.
• Cisco – For interoperating with Cisco’s ABR behavior, which expects the backbone to be configured and
active before setting the ABR flag.
• IBM – For interoperating with IBM’s ABR behavior, which expects the backbone to be configured before
settings the ABR flag.
• Shortcut – A ‘shortcut area’ enables traffic to go through the non-backbone area with a lower metric
whether or not the ABR router is attached to area 0.
• Originate Default Route – This checkbox enables or disables the advertising of the SonicWALL’s default
route into the OSPF system on this interface. The Default Route is always advertised as an External Type 2
using LSA Type 5.
•
122
SonicWALL Global Management System Configuration Guide
Note: The following applies to all Redistributed routes: The metric can be explicitly set for this redistribution, or it
can use the value (default) specified in the ‘Default Metric’ setting. An optional route tag value can be added to
help other routers identify this redistributed route (the default tag value is 0). The redistributed route advertisement
will be an LSA Type 5, and the type may be selected as either Type 1 (adds the internal link cost) or Type 2 (only
uses the external link cost).
• Redistribute Static Routes – Enables or disables the advertising of static (Policy Based Routing) routes into
the OSPF system.
• Redistribute Connected Networks - Enables or disables the advertising of locally connected networks into the
OSPF system.
• Redistribute RIP Routes - Enables or disables the advertising of routes learned via RIP into the OSPF system.
• Redistribute Remote VPN Networks - Enables or disables the advertising of static (Policy Based Routing)
routes into the RIP system.
Configuring IP Helper
The IP Helper allows the SonicWALL to forward DHCP requests originating from the interfaces on a SonicWALL
to a centralized DHCP server on the behalf of the requesting client. IP Helper is used extensively in routed VLAN
environments where a DHCP server is not available for each interface, or where the layer 3 routing mechanism is
not capable of acting as a DHCP server itself. The IP Helper also allows NetBIOS broadcasts to be forwarded with
DHCP client requests.
To enable IP Helper and add an IP Helper policy, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the Network tree and click IP Helper. The IP Helper page appears (Figure 117).
Figure 117: IP Helper Page
4. Select the Enable IP Helper check box.
5. To enable DHCP support, select Enable DHCP Support.
6. To enable NetBIOS support, select Enable NetBIOS Support.
7. To add an IP Helper Policy, click Add IP Helper Policy. The Add IP Helper dialog box appears.
Configuring Network Settings for SonicOS Enhanced
123
Figure 118: Add IP Helper Dialog Box
8. The policy is enabled by default. To configure the policy without enabling it, clear the Enabled check box.
9. Select DHCP or NetBIOS from the Protocol menu.
10. Select a source Interface or Zone from the From menu.
11. Select a destination IP address or subnet from the To menu.
12. Enter an optional comment in the Comment field.
13. Click OK to add the policy to the IP Helper Policies table.
14. Repeat this procedure for each policy to add.
15. When you are finished, click Update. The settings are changed for the selected SonicWALL appliance. To clear
all screen settings and start over, click Reset.
Configuring ARP
ARP (Address Resolution Protocol) maps layer 3 (IP addresses) to layer 2 (physical or MAC addresses) to enable
communications between hosts residing on the same subnet. ARP is a broadcast protocol that can create excessive
amounts of network traffic on your network. To minimize the broadcast traffic, an ARP cache is maintained to store
and reuse previously learned ARP information.
To configure ARP, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the Network tree and click ARP. The ARP page appears (Figure 119).
Figure 119: ARP Page
124
SonicWALL Global Management System Configuration Guide
Static ARP Entries
The Static ARP feature allows for static mappings to be created between layer 2 MAC addresses and layer 3 IP
addresses, but also provides the following capabilities:
Figure 120: Static ARP Entry
Publish Entry - Enabling the Publish Entry option in the Add Static ARP window causes the SonicWALL device to respond to ARP queries for the specified IP address with the specified MAC address.
This can be used, for example, to have the SonicWALL device reply for a secondary IP address on a particular interface by adding the MAC address of the SonicWALL. See the Secondary Subnet section that follows.
• Bind MAC Address - Enabling the Bind MAC Address option in the Add Static ARP window binds the
MAC address specified to the designated IP address and interface. This can be used to ensure that a particular workstation (as recognized by the network card's unique MAC address) can only the used on a specified interface on the SonicWALL. Once the MAC address is bound to an interface, the SonicWALL will not
respond to that MAC address on any other interface. It will also remove any dynamically cached references
to that MAC address that might have been present, and it will prohibit additional (non-unique) static mappings of that MAC address.
• Update IP Address Dynamically - The Update IP Address Dynamically setting in the Add Static ARP
window is a sub-feature of the Bind MAC Address option. This allows for a MAC address to be bound to
an interface when DHCP is being used to dynamically allocate IP addressing. Enabling this option will blur
the IP Address field, and will populate the ARP Cache with the IP Address allocated by the SonicWALL's
internal DHCP server, or by the external DHCP server if IP Helper is in use.
•
Secondary Subnets with Static ARP
The Static ARP feature allows for secondary subnets to be added on other interfaces, and without the addition
of automatic NAT rules.
Adding a Secondary Subnet using the Static ARP Method
1. Add a 'published' static ARP entry for the gateway address that will be used for the secondary subnet, assigning
it the MAC address of the SonicWALL interface to which it will be connected.
2. Add a static route for that subnet, so that the SonicWALL regards it as valid traffic, and knows to which interface to route that subnet's traffic.
3. Add Access Rules to allow traffic destined for that subnet to traverse the correct network interface.
4. Optional: Add a static route on upstream device(s) so that they know which gateway IP to use to reach the secondary subnet.
Flushing the ARP Cache
It is sometimes necessary to flush the ARP cache if the IP address has changed for a device on the network. Since
the IP address is linked to a physical address, the IP address can change but still be associated with the physical
address in the ARP Cache. Flushing the ARP Cache allows new information to be gathered and stored in the ARP
Cache. Click Flush ARP Cache to clear the information.
To configure a specific length of time for the entry to time out, enter a value in minutes in the ARP Cache entry
time out (minutes) field.
Configuring Network Settings for SonicOS Enhanced
125
Navigating and Sorting the ARP Cache Table Entries
To view ARP cache information, click Request ARP Cache display from unit(s).
The ARP Cache table provides easy pagination for viewing a large number of ARP entries. You can navigate a
large number of ARP entries listed in the ARP Cache table by using the navigation control bar located at the top
right of the ARP Cache table. Navigation control bar includes four buttons. The far left button displays the first
page of the table. The far right button displays the last page. The inside left and right arrow buttons moved the previous or next page respectively.
You can enter the policy number (the number listed before the policy name in the # Name column) in the Items
field to move to a specific ARP entry. The default table configuration displays 50 entries per page. You can change
this default number of entries for tables on the System > Administration page.
You can sort the entries in the table by clicking on the column header. The entries are sorted by ascending or
descending order. The arrow to the right of the column entry indicates the sorting status. A down arrow means
ascending order. An up arrow indicates a descending order.
126
SonicWALL Global Management System Configuration Guide
C H A P T E R 11
Configuring Firewall Settings
To determine whether packets are allowed through the firewall, each SonicWALL checks the destination IP address,
source IP address, and port against the firewall rules.
Note: Firewall rules take precedence over the default firewall functions. Because it is possible to disable all firewall
protection or block all access to the Internet, use caution when creating or deleting network access rules.
Network access rules do not disable protection from Denial of Service attacks such as SYN Flood, Ping of Death,
LAND, and so on. However, it is possible to create vulnerabilities to attacks that exploit application weaknesses.
It is important to consider the purpose and ramifications of a rule before adding it to the firewall rule list. Use the
following guidelines to determine the rule logic:
•
•
•
•
•
•
What is the purpose of the rule? For example, “This rule will restrict all Internet Relay Chat (IRC) access from
the LAN (WorkPort) to the Internet.” Or, “This rule will allow a remote Lotus Notes server to synchronize with
our internal Notes server via the Internet.
Will the rule allow or deny traffic?
What is the flow of the traffic: LAN (WorkPort) to Internet or Internet to LAN (WorkPort)?
Which IP services will be affected?
Which computers on the LAN (WorkPort) will be affected?
Which computers on the Internet will be affected? Be as specific as possible. For example, if traffic is being
allowed from the Internet to the LAN (WorkPort), it is better to only allow specific computers to access the
LAN or WorkPort.
After determining the logic of the rule, consider the ramifications:
Will this rule stop LAN (WorkPort) users from accessing important resources on the Internet? For example, if
IRC is blocked, are there users who require this service?
• Can the rule be modified to be more specific? For example, if IRC is blocked for all users, will a rule that only
blocks certain users be more effective?
• Will this rule allow Internet users to access LAN or WorkPort resources in a way that makes the LAN vulnerable? For example, if NetBIOS ports (UDP 137,138, 139) are allowed from the Internet to the LAN, Internet
users may be able to connect to PCs that have file sharing enabled.
• Does this rule conflict with other rules?
•
Configuring Firewall Settings
127
Understanding the Network Access Rules Hierarchy
The rule hierarchy uses two basic concepts:
•
•
Specific rules override general rules.
Equally specific Deny rules override Allow rules.
For example: a rule defining a specific service is more specific than the Default rule; a defined Ethernet link, such
as LAN (WorkPort), or WAN, is more specific than * (all); and a single IP address is more specific than an IP
address range.
Rules are listed in the LAN (WorkPort) Interface window from most specific to the least specific, and rules at the
top override rules listed below.
To illustrate this, consider the Rules shown below.
Table 2: Sample Rules
#
Action
Service
Source
Destination
1
Deny
Chat (IRC)
206.18.25.4 (LAN)
148.178.90.55 (WAN)
2
Allow
Ping
199.2.23.0 - 199.2.23.255 (WAN)
206.18.25.4 (WAN)
3
Deny
Web (HTTP)
216.37.125.0 - 216.37.125.255 (WAN)
*
4
Allow
Lotus Notes
WAN
LAN (WorkPort)
5
Deny
News (NNTP)
LAN (WorkPort)
*
6
Deny
Default
*
LAN (WorkPort)
7
Allow
Default
LAN (WorkPort)
*
The Default Allow Rule (#7) at the bottom of the page allows all traffic from the LAN (WorkPort) out to the WAN.
However, Rule #5 blocks all NNTP traffic from the LAN (WorkPort).
The Default Deny Rule (#6) blocks traffic from the WAN to the LAN (WorkPort). However, Rule #4 overrides part
of this rule by allowing Lotus Notes into the LAN (WorkPort) from the WAN.
Defining Firewall Rules
After defining rules and understanding their ramifications, select from the following:
• SonicOS Enhanced—see “SonicOS Enhanced” on page 128.
• SonicOS Standard—see “SonicOS Standard” on page 135.
SonicOS Enhanced
To configure rules for SonicOS Standard, follow these steps:
1. Schedules are pre-defined periods of time that enable you to quickly define when rules are applied. To add a
schedule, see “Adding a Service” on page 136.
2. Determine whether the service for which you want to create a rule is defined. If not, define the service or Service Group. See “Adding a Service Object” on page 131 and “Adding a Service Object Group” on page 131.
3. Create one or more rules for the service. See “Creating Rules” on page 136.
4. Repeat this procedure for each service for which you would like to define rules.
Configuring Schedule Groups and Schedules
Schedule Groups are groups of schedules to which you can apply firewall rules. For example, you might want to
block access to auction sites during business hours, but allow employees to access the sites after hours.
You can apply rules to specific schedule times or all schedules within a Schedule Group. For example, you might
create an Engineering Work Hours group that runs from 11:00 AM to 9:00 PM, Monday through Friday and 12:00
PM to 5:00 PM, Saturday and Sunday. Once configured, you can apply specific firewall rules to the entire Engineering Work Hours Schedule Group or only to the weekday schedule.
128
SonicWALL Global Management System Configuration Guide
Creating a New Schedule Group
To create a Schedule Group, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Firewall tree and click Schedules. The Schedules page appears (Figure 121).
Figure 121: Schedules Page
4. To add a Schedule Group, click Add Schedule Group.
Figure 122: Add Schedule Dialog Box
5. Enter the name of the Schedule Group in the Name field.
6. Configure a schedule:
• Select the check boxes for each day the schedule will apply.
• Enter the start time for the schedule in the Start Time field. Make sure to use the 24-hour format.
• Enter the end time for the schedule in the Stop Time field. Make sure to use the 24-hour format.
• Click Add.
7. Repeat Step 6 for each schedule to add.
8. To delete a schedule, select the schedule and click Delete.
Configuring Firewall Settings
129
9. Click OK. The Schedule Group is added and configured.
Editing a Schedule Group
To edit a Schedule Group, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Firewall tree and click Schedules. The Schedules page appears (Figure 123).
Figure 123: Schedules Page
4. To add a Schedule Group, click its Edit Icon (
). The Edit Schedule Group dialog box appears.
Figure 124: Edit Schedule Dialog Box
5. To add a schedule:
•
•
•
•
Select the check boxes for each day the schedule will apply.
Enter the start time for the schedule in the Start Time field. Make sure to use the 24-hour format.
Enter the end time for the schedule in the Stop Time field. Make sure to use the 24-hour format.
Click Add.
6. Repeat Step 5 for each schedule to add.
130
SonicWALL Global Management System Configuration Guide
7. To delete a schedule, select the schedule and click Delete.
8. Click OK. The settings for the Schedule Group are changed.
Adding a Service Object
A Service Object is a protocol/port range combination that defines a service. A Service Group is a group of services
that, once defined, enable you to quickly establish firewall rules without manually configuring each service.
By default, a large number of services are pre-defined. To add a service, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Firewall tree and click Service Objects. The Service Objects page appears (Figure 125).
Figure 125: Service Objects Page
4. To add a service, scroll to the bottom of the Custom Services section and click Add Service.
Figure 126: Add Service Dialog Box
5. Enter the name of the service in the Name field.
6. Enter the starting and ending port for the service in the Port Range fields.
7. Select the type of protocol from the Protocol field.
8. Click OK. The service is added.
9. Repeat Steps 4 through 8 for each service to add.
Adding a Service Object Group
A Service Group is a group of services that can be used to quickly apply rules to large numbers of services without
individually configuring each service. By default, many Service Groups are pre-defined. To add a new Service
Group, follow these steps:
Configuring Firewall Settings
131
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Firewall tree and click Service Objects. The Service Objects page appears (Figure 127).
Figure 127: Service Objects Page
4. To add a service, scroll to the bottom of the Custom Service Groups section and click Add Group. The Add
Service Group dialog box appears.
Figure 128: Add Service Group Dialog Box
5. Enter a name for the service group in the Name field.
6. To add a service, select it and click the right arrow button.
7. To remove a service, select it and click the left arrow button.
8. Click OK. The service group is added.
9. Repeat Steps 4 through 8 for each service to add.
Configuring the Access Rules
This section describes how to define firewall rules. To create a rule, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Firewall tree and click Access Rules. The Access Rules page appears (Figure 129).The Firewall >
Access Rules page enables you to select multiple views of Access Rules, including Drop-down boxes, Option
132
SonicWALL Global Management System Configuration Guide
Buttons, and All Rules. The default view is the Matrix View which provides a matrix of source and destination
nodes between LAN, WAN, VPN, Multicast, and WLAN.
Figure 129: Access Rules Page
4. From the Matrix View, click the Edit Icon (
configure a rule.
). for the source and destination interfaces for which you will
5. Click Add Rule. The Add Rule Property Sheet appears.
Figure 130: Add Rule Property Sheet
6. Select whether access to this service will be allowed or denied.
7. Select a service from the from the Service Name list box. If the service does not exist, see “Adding a Service
Object” on page 131.
Configuring Firewall Settings
133
8. Select the source Address Object from the Source list box.
9. Select the destination Address Object from the Destination list box.
10. Specify when the rule will be applied by selecting a schedule or Schedule Group from the Schedule list box. If
the rule will always be applied, select Always on. If the schedule does not exist, see “Configuring Schedule
Groups and Schedules” on page 128.
11. To enable logging for this rule, select the Logging check box.
12. Add any comments to the Comment field.
13. Click the Advanced tab. The Advanced properties page appears.
Figure 131: Add Rule Property Sheet: Advanced Page
14. Fragmented packets are used in certain types of Denial of Service attacks and, by default, are blocked. You
should only enable the Allow Fragmented Packets check box if users are experiencing problems accessing certain applications and the SonicWALL logs show many dropped fragmented packets.
15. Specify how long (in minutes) the connection may remain idle before the connection is terminated in the Inactivity Timeout field.
16. Click the Bandwidth tab. The Bandwidth page appears.
134
SonicWALL Global Management System Configuration Guide
Figure 132: Add Rule Property Sheet: Bandwidth Page
17. SonicWALL appliances can manage outbound traffic using bandwidth management. To enable bandwidth management for this service, select the Enable Bandwidth Management check box.
Enter the amount of bandwidth that will always be available to this service in the Guaranteed Bandwidth
field. Keep in mind that this bandwidth will be permanently assigned to this service and not available to other
services, regardless of the amount of bandwidth this service does or does not use.
Enter the maximum amount of bandwidth that will be available to this service in the Maximum Bandwidth
field.
Select the priority of this service from the Bandwidth Priority list box. Select a priority from 0 (highest) to 7
(lowest).
Note: In order to configure bandwidth management for this service, bandwidth management must be enabled
on the SonicWALL appliance. For more information, see “Configuring Interface Network Settings” on page 94.
18. To add this rule to the rule list, click OK. You are returned to that Access Rules page.
19. Repeat Steps 4 through 18 for each rule that you will to add.
20. If the network access rules have been modified or deleted, you can restore the Default Rules. The Default Rules
prevent malicious intrusions and attacks, block all inbound IP traffic and allow all outbound IP traffic. To
restore the network access rules to their default settings, click Restore Rules to Defaults and click Update. A
task is scheduled to update the rules page for each selected SonicWALL appliance.
21. To modify a rule, click its Edit Icon ( ). The Add/Modify Rule dialog box appears. When you are finished
making changes, click OK. SonicWALL GMS creates a task that modifies the rule for each selected SonicWALL appliance.
22. To enable logging for a rule, select its Logging check box.
23. To disable a rule without deleting it, deselect its Enable check box.
24. To delete a rule, click its trash can icon. SonicWALL GMS creates a task that deletes the rule for each selected
SonicWALL appliance.
SonicOS Standard
To configure rules for SonicOS Standard, follow these steps:
1. Determine whether the service for which you want to create a rule is defined. If not, define the service. See
“Adding a Service” on page 136.
2. Create one or more rules for the service. See “Creating Rules” on page 136.
3. Repeat this procedure for each service for which you would like to define rules.
Configuring Firewall Settings
135
Adding a Service
By default, a large number of services are pre-defined. This section describes how to add a new or custom service.
To add a service, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Firewall tree and click Services. The Services page appears (Figure 133).
Figure 133: Access Services Page
4. To add a known service (e.g., HTTP, FTP, News), select the service from the Service Name list box and click
Add Known Service. Repeat this step for each service that you would like to add. A task is scheduled for each
service for each selected SonicWALL appliance.
5. To add a custom service, enter its name in the Service Name field, enter the port range it uses in the Port Begin
and Port End fields, select the appropriate protocol check boxes, and click Add Custom Service. Repeat this
step for each service that you would like to add. A task gets scheduled for each service for each selected SonicWALL appliance.
6. To remove a service from the list, select its trash can check box and click Update. A task gets scheduled to
update the services page for each selected SonicWALL appliance.
7. To clear all screen settings and start over, click Reset.
Creating Rules
This section describes how to define rules for defined services.
To create a rule, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Firewall tree and click Rules. The Rules page appears (Figure 134).
136
SonicWALL Global Management System Configuration Guide
Figure 134: Access Rules Page
4. Click Add Rule. The Add Rule dialog box appears.
Figure 135: Add Rule Dialog Box
5. Select a service from the from the Service Name list box. If the service does not exist, see “Adding a Service”
on page 136.
6. Select whether access to this service will be allowed or denied.
7. Select the SonicWALL interface to which this rule applies. Select whether this rule will apply to packets coming from the LAN (WorkPort), WAN, DMZ (HomePort), or all interfaces (*).
Configuring Firewall Settings
137
8. Specify the source IP address range. The rule will apply to requests originating from IP addresses within this
range. For all IP addresses, enter an asterisk (*).
9. Specify the destination IP address range. The rule will apply to requests sent to IP addresses within this range.
For all IP addresses, enter an asterisk (*).
10. Specify when the rule will be applied. By default, it is Always. To specify a time, enter the time of day (in 24hour format) to begin and end enforcement. Then, enter the days of the week to begin and end rule enforcement.
11. Specify how long (in minutes) the connection may remain idle before the connection is terminated in the Inactivity Timeout field.
12. Fragmented packets are used in certain types of Denial of Service attacks and, by default, are blocked. You
should only enable the Allow Fragmented Packets check box if users are experiencing problems accessing certain applications and the SonicWALL logs show many dropped fragmented packets.
13. SonicWALL appliances can manage outbound traffic using bandwidth management. To enable bandwidth management for this service, select the Enable Bandwidth Management check box.
Enter the amount of bandwidth that will always be available to this service in the Guaranteed Bandwidth
field. Keep in mind that this bandwidth will be permanently assigned to this service and not available to other
services, regardless of the amount of bandwidth this service does or does not use.
Enter the maximum amount of bandwidth that will be available to this service in the Maximum Bandwidth
field.
Select the priority of this service from the Bandwidth Priority list box. Select a priority from 0 (highest) to 7
(lowest).
Note: In order to configure bandwidth management for this service, bandwidth management must be enabled
on the SonicWALL appliance. For more information, see “Configuring Ethernet Settings” on page 119.
14. To add this rule to the rule list, click Update. Repeat Step 4 through Step 14 for each rule that you will to add.
15. If the network access rules have been modified or deleted, you can restore the Default Rules. The Default Rules
prevent malicious intrusions and attacks, block all inbound IP traffic and allow all outbound IP traffic. To
restore the network access rules to their default settings, click Restore Rules to Defaults and click Update. A
task is scheduled to update the rules page for each selected SonicWALL appliance.
16. If the network access rules for a SonicWALL appliance need to be uniform with access rules for other
SonicWALL appliances in the same group, you can restore the group rules.
To do this, click Restore Rules to Group Settings and click Update. A task is scheduled to overwrite the rules
page for each selected SonicWALL appliance.
If you want to append the group rules to the current rules, make sure the Append Services and Rules inherited
from group check box is selected on the GMS Settings page of the Console Panel.
Note: This option is not available at the group or global level.
17. To modify a rule, select its notepad icon. The Add/Modify Rule dialog box appears. When you are finished
making changes, click Update. SonicWALL GMS creates a task that modifies the rule for each selected SonicWALL appliance.
18. To disable a rule without deleting it, deselect its Enable Rule check box.
19. To delete a rule, select its trash can icon and click Update. SonicWALL GMS creates a task that deletes the rule
for each selected SonicWALL appliance.
138
SonicWALL Global Management System Configuration Guide
Configuring Advanced Access Settings
To configure advanced access settings, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Firewall tree and click Advanced. The Advanced page appears (Figure 136).
Figure 136: Advanced Page
4. Computers running Microsoft Windows communicate with each other through NetBIOS broadcast packets. By
default, SonicWALL appliances block these broadcasts. Select from the following:
To configure the SonicWALL appliance(s) to allow NetBIOS packets to pass from the LAN (WorkPort) to
the DMZ (HomePort), select the From LAN to DMZ or From WorkPort to HomePort check box.
• To configure the SonicWALL appliance(s) to allow NetBIOS packets to pass from the LAN (WorkPort) to
the WAN, select the From LAN to WAN or From WorkPort to WAN check box.
•
5. Detection prevention helps hide SonicWALL appliances from potential hackers. Select from the following
Detection Prevention options:
To enable stealth mode, select the Enable Stealth Mode check box. During normal operation, SonicWALL
appliances respond to incoming connection requests as either “blocked” or “open.” During stealth operation, SonicWALL appliances do not respond to inbound requests, making the appliances “invisible” to
potential hackers.
• Hackers can use various detection tools to “fingerprint” IP IDs and detect the presence of a SonicWALL
appliance. To configure the SonicWALL appliance(s) to generate random IP IDs, select the Randomize IP
ID check box.
•
6. Select the dynamic ports that will be supported from the Dynamic Ports area:
•
•
Enable support for Oracle (SQLNet)—Select if you have Oracle applications on your network.
Enable support for Windows Messenger—Select this option to support special SIP messaging used in
Windows Messenger on the Windows XP.
Configuring Firewall Settings
139
Enable support for H.323—Select this option to enable support for H.323. H.323 is a standard that was
designed to provide consistency for audio, video, and data transmissions over the Internet and is most commonly used for VoIP.
• Enable RTSP Transformations—Select this option to support on-demand delivery of real-time data, such
as audio and video. Real Time Streaming Protocol (RTSP) is an application-level protocol for control over
delivery of data with real-time properties.
7. The Drop Source Routed Packets check box is selected by default. Clear the check box if you are testing traffic between two specific hosts and you are using source routing.
8. The Connection Inactivity Timeout option disables connections outside the LAN if they are idle for a specified
period of time. Without this timeout, connections can stay open indefinitely and create potential security holes.
To specify how long the SonicWALL appliance(s) wait before closing inactive connections outside the LAN,
enter the amount of time in the Default Connection Timeout field (default: 25 minutes).
9. By default, FTP connections from port 20 are allowed, but remapped to outbound traffic ports such as 1024. If
you select the Force inbound and outbound FTP data connections to use default port 20 check box, any
FTP data connection through the SonicWALL must come from port 20 or the connection will be dropped and
logged.
10. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
Configuring Voice over IP Settings
To configure Voice over IP (VoIP) settings, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Firewall tree and click VoIP. The VoIP page appears (Figure 137).
Figure 137: VoIP Page
4. To enable secure NAT, select the Use secure NAT check box.
5. Select from the following Session Initiation Protocol (SIP) configuration options:
•
Enable SIP Transformations—Select this option to support translation of SIP messages.
By default, NAT translates Layer 3 addresses, but does not translate Layer 5 SIP/SDP addresses. Unless
there is another NAT traversal solution that requires this feature to be turned off, it is highly recommended
to enable SIP transformations.
140
SonicWALL Global Management System Configuration Guide
After enabling SIP transformations, configure the following options:
•
•
SIP Signaling inactivity time out (seconds)—Specifies the period of time that must elapse before timing out an inactive SIP session if no SIP signaling occurs (default: 1800 seconds or 30 minutes).
SIP Media inactivity time out (seconds)—Specifies the period of time that must elapse before timing
out an inactive SIP session if no media transfer activity occurs (default: 120 seconds or 2 minutes).
6. Select from the following H.323 configuration options:
• Enable H.323 Transformation—Select this option to allow stateful H.323 protocol-aware packet content
inspection and modification by the SonicWALL. The SonicWALL performs any dynamic IP address and
transport port mapping within the H.323 packets, which is necessary for communication between H.323
parties in trusted and untrusted networks/zones. Clear this check box to bypass the H.323 specific processing performed by the SonicWALL.
After enabling H.323 transformations, configure the following options:
Only accept incoming calls from Gatekeeper—when selected, only incoming calls from specified
Gatekeeper IP address will be accepted.
• Enable LDAP ILS Support— when selected, the SonicWALL appliance will support Lightweight
Directory Access Protocol (LDAP) and Microsoft Netmeeting’s Internet Locator Service (ILS)
• H.323 Signaling/Media inactivity time out (seconds)—specifies how long the SonicWALL appliance
waits before closing a connection when no activity is occurring.
• Default WAN/DMZ Gatekeeper IP Address—specifies the IP address of the H.323 Gatekeeper that
acts as a proxy server between clients on the private network and the Internet.
•
7. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
Configuring Multicast Settings
To configure multicast settings, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Firewall tree and click Multicast. The Multicast page appears (Figure 138).
Figure 138: Multicast Page
4. To enable multicast, select the Enable Multicast check box.
Configuring Firewall Settings
141
5. Configure the following options:
Require IGMP Membership reports for multicast data forwarding—This checkbox is enabled by
default. Select this checkbox to improve performance by regulating muliticast data to be forwarded to only
interfaces belonging to an enabled multicast group address.
• Multicast state table entry timeout (minutes)—This field has a default of 5. The value range for this field
is 5 to 60 (minutes). Increase the value if you have a client that is not sending reports periodically.
•
6. Select from the following:
To receive all (class D) multicast addresses, select Enable reception of all multicast addresses. Receiving
all multicast addresses may cause your network to experience performance degradation.
• Default. To enable reception for the following multicast addresses, select Enable reception for the following multicast addresses and select Create a new multicast object or Create new multicast group from
the list box.
•
7. To view the IGMP State Information, click Request IGMP State Information. The following information
appears:
• Multicast Group Address—Provides the multicast group address the interface is joined to.
• Interface / VPN Tunnel—Provides the interface (such as X0) or the VPN policy.
• IGMP Version—Provides the IGMP version (such as V2 or V3).
• Time Remaining—Provides the remaining time left for the multicast session. This is calculated by subtracting the “Multicast state table entry timeout (minutes)” value, which has the default value of 5 minutes,
and the elapsed time since the multicast address was added.
8. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
142
SonicWALL Global Management System Configuration Guide
CHAPTER 12
Configuring Log Settings
This chapter describes how to use the SonicWALL Global Management System (SonicWALL GMS) to configure
where the SonicWALL appliance(s) send their logs, how often the logs are sent, and what information is included.
To configure log settings, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Log tree and click Log Settings. The Log Settings page appears (Figure 139).
Figure 139: Log Settings Page
4. Enter the IP address of the mail server in the Mail Server IP Address field.
5. Enter the name of the SonicWALL appliance in the Firewall Name field. The firewall name appears in the subject of email sent by the SonicWALL appliance. By default, the firewall name is the same as the SonicWALL
appliance serial number.
Note: The name of the SonicWALL appliance cannot be configured at the group or global level.
6. Select a syslog format:
•
•
Default—standard SonicWALL syslog format.
WebTrends—reporting software that analyzed traffic activity, protocol usage, security problems, resource
usage, bandwidth consumption, and more. For more information, visit http://www.webtrends.com.
7. The Syslog Event Rate prevents repetitive events from being logged to the syslog. If duplicate events occur during the period, they will be logged as a single event that specifies the number of times that the event occurred.
Configuring Log Settings
143
To specify how often SonicWALL GMS logs repetitive events, enter the period in the Syslog Event Rate field
(default: 60 seconds). The minimum is 0 seconds and the maximum is 86,400 seconds (24 hours). If you specify
0, all events are logged.
Note: If you are using ViewPoint reporting, make sure the Syslog Event Rate is set to 0. Otherwise, ViewPoint
reports will not be accurate.
8. Specify how often the SonicWALL appliance(s) send heartbeats to SonicWALL GMS in the Heartbeat Rate
field (default: 60 seconds). If SonicWALL GMS does not receive a heartbeat message within three intervals,
SonicWALL GMS will consider the SonicWALL appliances offline or unavailable and its icon will turn red.
Note: It is highly recommended to leave the Heartbeat Rate at the default setting of 60 seconds. Values close to
zero will generate a large number of status messages. The maximum value is 86400 seconds (24 hours).
9. Enter the complete email address (for example, [email protected]) where the log will be sent in the
Email Log to field. If this field is left blank, the log will not be sent.
Note: This address will also be used as the return address.
10. Some events, such as an attack, may require immediate attention. Enter the complete email address or email
pager address in the Email Alerts to field. If this field is left blank, alerts will not be sent.
Note: This address will also be used as the return address.
11. Select when the log file will be sent from the Send Log list box. Options include daily, weekly, or when log is
full. If the log will be sent daily, select the time that the log will be sent (24 hour format). If the log will be sent
weekly, select the time and day of the week.
12. In some cases, the log buffer may fill up. This may occur if there is a problem with the mail server and the log
cannot be successfully e-mailed. By default, SonicWALL appliances will overwrite the log and discard its contents. To prevent further traffic from not being logged, select Shutdown SonicWALL.
13. Select information to log from the Categories section.
Note: If you are using SonicWALL GMS ViewPoint, make sure that it can generate all reports for each SonicWALL appliance by selecting all log category check boxes.
14. To immediately send the log to the specified email address now, click Email Log Now.
15. To delete the contents of the log, click Clear Log Now.
16. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
144
SonicWALL Global Management System Configuration Guide
Heartbeat Settings on the Enhanced Log Settings Page
A heartbeat is a message generated by the firewall appliance sent out at various intervals to a connected management server to determine whether the management server connected to the firewall appliance is active. You can
now set a threshold value for how often a heartbeat message is generated. You can do this on the Log Settings page.
To specify the Heartbeat Rate, perform the following:
1. Navigate to the Policies Panel.
2. Click the Log menu to display logging options.
3. Click the Log Settings option.
GMS displays the Log Settings dialog box.
4. In the Heartbeat Rate field in the General region, type a value that represents the number of seconds that is the
interval between heartbeat tests. Note that the default interval is 60 seconds.
Configuring Log Settings
145
146
SonicWALL Global Management System Configuration Guide
CHAPTER 13
Configuring SonicWALL QoS
Quality of Service (QoS) adds the ability to recognize, map, modify, and generate the industry-standard 802.1p and
Differentiated Services Code Points (DSCP) Class of Service (CoS) designators. When used in combination with a
QoS capable network infrastructure, SonicOS QoS features provide predictability that is vital for certain types of
applications, such as Voice over IP (VoIP), multimedia content, or business-critical applications such as credit card
processing. To centrally manage the 802.1p-DSCP Mappings Table, GMS now provides a new configuration found
under the path Policies > Firewalls > QoS Mapping.
Even the highest amounts of bandwidth ultimately are used to capacity at some point by users on the network.
Being able to manage bandwidth to obtain the most efficient use from it is essential. Only QoS, when configured
and implemented correctly, properly manages traffic and guarantees the desired levels of network service. Three
concepts are central to the traffic management provided by QoS:
•
•
•
Classification
Marking
Conditioning
Each is described in the following sections.
Working with Classification
Classification is necessary as a first step to identify traffic that needs to be prioritized for optimal use. GMS uses
access rules as the interface to classification of traffic. This provides fine control using combination of Address
Object, Service Object, and Schedule Object elements, allowing for classification criteria as general as all HTTP
traffic and as specific as SSH traffic from HostA to ServerB on Wednesdays at 2:12am.
GMS provides the ability to recognize, map, modify, and generate the industry-standard external CoS designators,
DSCP and 802.1p protocols.
Once identified, or classified, it can be managed. Management can be performed internally by SonicWALL BWM,
which is effective as long as the network is a fully contained autonomous system. Once external or intermediate elements are introduced, for example, foreign network infrastructures with unknown configurations, or other hosts
contending for bandwidth (for example, the endpoints of the network and all entities in between are within your
management. BWM works exactly as configured. Once external entities are introduced, the precision and efficacy
of BWM configurations can begin to degrade.
Once GMS classifies the traffic, it then tags it to communicate this classification to certain external systems that are
capable of abiding by CoS tags. The external systems then can participate in providing QoS to traffic passing
through them.
Note: Many service providers do not support CoS tags such as 802.1p or DSCP. Also, most network equipment with
standard configurations will not be able to recognize 802.1p tags, and could drop tagged traffic.
Note: If you wish to use 802.1p or DSCP marking on your network or your service provider’s network, you must
first establish that these methods are supported. Verify that your internal network equipment can support CoS priority marking, and that it is correctly configured to do so. Check with your service provider - some offer fee-based
support for QoS using these CoS methods.
Configuring SonicWALL QoS
147
Working with Marking
Once the traffic has been classified, if it is to be handled by QoS capable external systems, it must be tagged to
enable external systems to make use of the classification, and provide correct handling and Per Hop Behaviors
(PHB). An example of a QoS capable external system is a CoS-aware switch or router that might be available on a
premium service provider’s infrastructure, or on a private WAN.
Originally, this was attempted at the IP layer (layer 3) with RFC 791’s three precedence bits and RFC 1394 ToS
(type of service) field, but this was not widely used. Its successor, RFC 2474, introduced the more widely used
DSCP (Differentiated Services Code Point) which offers up to 64 classifications, in addition to user-definable
classes. DSCP was further enhanced by RFC 2598 (Expedited Forwarding, intended to provide leased-line behaviors) and RFC 2697 (Assured Forwarding levels within classes, also known as Gold, Silver, and Bronze levels).
DSCP is a safe marking method for traffic that traverses public networks because there is no risk of incompatibility.
At the very worst, a hop along the path might disregard or strip the DSCP tag, but it will rarely mistreat or discard
the packet.
The other prevalent method of CoS marking is IEEE 802.1p occurs at the MAC layer (layer 3) and is closely related
to IEEE 802.1Q VLAN marking, sharing the same 16-bit field, although it is actually defined in the IEEE 802.1D
standard. Unlike DSCP, 802.1p will only work with 802.1p capable equipment, and is not universally interoperable.
Additionally, 802.1p, because of its different packet structure, can rarely traverse wide area networks, even private
WANs. Nonetheless, 802.1p is gaining wide support among Voice and Video over IP vendors, so a solution for supporting 802.1p across network boundaries (i.e., WAN links) was introduced in the form of 802.1p to DSCP mapping.
802.1p to DSCP mapping allows 802.1p tags from one LAN to be mapped to DSCP values by GMS, allowing the
packets to safely traverse WAN links. When the packets arrive on the other side of the WAN or VPN, the receiving
GMS appliance can then map the DSCP tags back to 802.1p tags for use on that LAN.
Working with Conditioning
Finally, the traffic can be conditioned or managed using any of the many policing, queueing, and shaping methods
available. GMS provides internal conditioning capabilities with its Egress and Ingress Bandwidth Management
(BWM). SonicWALL BWM is a perfectly effective solution for fully autonomous private networks with sufficient
bandwidth, but can become somewhat less effective as more unknown external network elements and bandwidth,
but can become somewhat less effective as more unknown external network elements and bandwidth contention are
introduced.
To provide end-to-end QoS, business-class service providers are increasingly offering traffic conditioning services
on their IP networks. These services typically depend on the customer premise equipment to classify and tag the
traffic, generally using a standard marking method such as DSCP. GMS has the ability to DSCP mark traffic after
classification, as well as the ability to map 802.1p tags to DSCP tags for external network traversal and CoS preservation. For VPN traffic, GMS can DSCP mark not only the internal (payload) packets, but the external (encapsulating) packets as well so that QoS capable service providers can offer QoS even on encrypted VPN traffic.
The actual conditioning method employed by service providers varies from one to the next, but it generally
involves a class-based queueing method such as Weighted Fair Queuing for prioritizing traffic, in addition to a congestion avoidance method, such as tail-drop or Random Early Detection.
148
SonicWALL Global Management System Configuration Guide
Working with 802.1p and DSCP QoS
The following sections detail the 802.1p standards and DSCP QoS.
Enabling 802.1P
GMS supports layer 2 and layer 3 CoS methods for broad interoperability with external systems participating in
QoS enabled environments. The layer 2 method is the IEEE 802.1p standard wherein 3 bits of an additional 16 bits.
inserted into the header of the Ethernet frame can be used to designate the priority of the fame, as illustrated in the
following figure.
TPID: Tag Protocol Identifier begins at byte 12 (after the 6-byte destination and source fields), is 2 bytes long,
and has an Ethertype of 0x8100 for tagged traffic.
• 802.1p: The first three bits of the TCI (Tag Control Information - beginning at byte 14, and spanning 2 bytes)
define user priority, giving eight (2^3) priority levels. IEEE 802.1p defines the operation for these 3 user priority bits.
• CFI: Canonical Format Indicator is a single-bit flag, always set to zero for Ethernet switches. CFI is used for
compatibility reasons between Ethernet networks and Token Ring networks. If a frame received at an Ethernet
port has a CFI set to 1, then that frame should not be forwarded as it is to an untagged port.
• VLAN ID: VLAN ID (starts at bit 5 of byte 14) is the identification of the VLAN. It has 12 bits and allows for
the identification of 4,096 (2^12) unique VLAN IDs. Of the 4,096 possible IDs, an ID of 0 is used to identify
priority frames, and an ID of 4,095 (FFF) is reserved, so the maximum possible VLAN configurations are
4,094.
•
802.1p support begins by enabling 802.1p marking on the interfaces which you wish to have process 802.1p tags.
802.1p can be enabled on any Ethernet interface on any SonicWALL appliance including the TZ 170 Series, PRO
2040, PRO 3060, PRO 4060, and PRO 5060.
Note: 802.1p tagging is not currently supported on the PRO 1260.
Although Enable 802.1p tagging does not appear as an option on VLAN sub-interfaces on the PRO 4060 and PRO
5060, the 802.1q tags of VLAN subinterfaces. The behavior of the 802.1p field within these tags can be controlled
by access rules. The default 802.1p capable network Access Rule action of None resets existing 802.1p tags to 0,
unless otherwise configured.
Enabling 802.1p marking allows the target interface to recognize incoming 802.1p tags generated by 802.1p capable network devices, and will also allow the target interface to generate 802.1p tags, as controlled by Access Rules.
Frames that have 802.1p tags inserted by GMS will bear VLAN ID 0.
802.1p tags will only be inserted according to access rules, so enabling 802.1p marking on an interface will not, at
its default setting, disrupt communications with 802.1p-incapable devices.
802.1p requires the specific support by the networking devices with which you wish to use this method of prioritization. Many voice and video over IP devices provide support for 802.1p, but the feature must be enabled. Check
your equipment’s documentation for information on 802.1p support if you are unsure. Similarly, many server and
host network cards (NICs) have the ability to support 802.1p, but the feature is usually disabled by default.
Configuring SonicWALL QoS
149
Working with DSCP Marking
DSCP (Differentiated Services Code Point) marking uses six bits of the eight bit ToS field in the IP header to provide up to 64 classes (or code points) for traffic. Since DSCP is a layer 3 marking method, there is no concern about
compatibility as there is with 802.1p marking. Devices that do not support DSCP will simply ignore the tags, or at
worst, they reset the tag value to 0.
The above diagram depicts an IP packet, with a close-up on the ToS portion of the header. The ToS bits were originally used for Precedence and ToS (delay, throughput, reliability, and cost) settings, but were later reused by the
RFC 2474 for the more versatile DSCP settings. The following table shows the commonly used code point as well
as their mapping to the legacy Precedence and ToS settings.
DSCP
0
8
10
12
14
16
18
20
22
24
26
27
30
32
34
36
38
40
46
48
56
150
Legacy IP
Precedence
0 (Routine - 000)
1 (Priority - 001)
1 (Priority - 001)
1 (Priority - 001)
1 (Priority - 001)
2 (Immediate - 010)
2 (Immediate - 010)
2 (Immediate - 010)
2 (Immediate - 010)
3 (Flash - 011)
3 (Flash - 011)
3 (Flash - 011)
3 (Flash - 011)
4 (Flash Override 100)
Class 4, Gold AF41
4 (Flash Override 100)
Class 4, Silver AF42 4 (Flash Override 100)
Class 4, Bronze AF43 4 (Flash Override 100)
Express Forwarding 5 (CRITIC/ECP 101)
Expedited
5 (CRITIC/ECP Forwarding (EF)
101)
Control
6 (Internet Control 110)
Control
7 (Internet Control 111)
DSCP Description
Best Effort
Class 1
Class 1, Gold AF11
Class 1, Silver AF12
Class 1, Bronze AF13
Class 2
Class 2, Gold AF21
Class 2, Silver AF22
Class 2, Bronze AF23
Class 3
Class 3, Gold AF31
Class 3, Silver AF32
Class 3, Bronze AF33
Class 4
Legacy IP ToS (D,
T, R)
T
D
D, T
T
D
D, T
T
D
D, T
T
D
D, T
D, T
-
SonicWALL Global Management System Configuration Guide
DSCP marking can be performed on traffic to and from any interface and to and from any zone type, without exception. DSCP marking is controlled by Access Rules, from the QoS tab, and can be used in conjunction with 802.1p
marking, as well as with SonicOS internal bandwidth management.
DSCP Marking and Mixed VPN Traffic
Among the security measures and characteristics pertaining to them, IPSec VPNs employ anti-replay mechanisms
based upon monotonically incrementing sequence numbers added to the ESP header. Packets with duplicate
sequence numbers are dropped, as are packets that do not adhere to sequence criteria. One criterion governs the
handling of out-of-order packets. GMS provides a replay window of 64 packets, i.e., if an ESP packet for a Security
Association (SA) is delayed by more than 64 packets, the packet will be dropped.
This should be considered when using DSCP marking to provide layer 3 QoS to traffic traversing a VPN. If you
have a VPN tunnel transporting a variety of traffic, some that is being DSCP tagged high priority (for example,
VoIP), and some that is DSCP tagged low-priority, or untagged/best-effort packets over the best-effort ESP packets.
Under certain traffic conditions, this can result in the best-effort packets being delayed for more than 64 packets,
causing them to be dropped by the receiving SonicWALL’s anti-replay defenses.
If symptoms of such a scenario emerge (for example, excessive retransmissions of low-priority traffic), it is recommended that you create a separate VPN policy for the high-priority and low-priority classes of traffic. This is most
easily accomplished by placing the high-priority hosts (for example, the VoIP network) on their own subnet.
Configuring QoS
You need to perform the following tasks to configure QoS:
•
•
•
Enable 802.1p tagging.
Create a QoS rule.
Configure QoS settings.
Enabling 802.1p Tagging
Before you begin to perform any QoS configuration tasks, you first need to enable your device to accept QoS values. To do that you have to enable the IEEE 802.1p tagging protocol. You enable protocols at the WAN interface
level. To enable 802.1p tagging, perform the following steps:
1. Click on the Interfaces option in the Network menu. GMS displays the Interfaces list.
2. Click on the Configuration icon for the WAN interface. GMS displays the Edit Interface dialog box.
Configuring SonicWALL QoS
151
3. Click on the Advanced Tab. GMS displays the Advanced Tab.
4. Click on the Enable 802.1p tagging checkbox to place a check mark in the checkbox.
5. Click Update. GMS updates the WAN interface, allowing it to accept 802.1p tagging.
Creating a QoS Rule
The next step you must perform is you need to create a QoS rule for the WAN interface in the Access Rules dialog
box. To configure a QoS rule, perform the following steps:
1. From the Firewall menu, click on the Access Rules option. GMS displays the Access Rules dialog box that contains various interfaces for which you can create an access rule.
2. Note the LAN > WAN rule bar.
3. Click Add Rule. GMS displays the Add Rule dialog box.
152
SonicWALL Global Management System Configuration Guide
4. Click the QoS Tab.
5. In the DSCP Marking Settings region, click the DSCP Marking Action list box and select the Map option.
6. In the 802.1p Marking Settings region, click the 802.1p Marking Action list box and select the Map option.
7. Click Ok. GMS configures your WAN interface to accept traffic shaping values.
Configuring SonicWALL QoS
153
Configuring QoS Settings
Now that you have enabled the 802.1p protocol and created a specific QoS rule, you can create your QoS settings.
To create QoS settings, perform the following steps:
1. Click on the QoS Settings option in the Firewall menu. GMS displays the QoS Mapping dialog box:
2. Click on the Configuration icon for any of the 802.1p Class of Service objects. GMS displays the class of service Edit QoS Mapping dialog box.
3. Select the following values from each list box in the dialog box.
List Box
L2 CoS
Description
Layer 2 Class of Service. If there’s a packet with a QoS bit set to 0,
then you need to map it to the value in the To DSCP list box. The
CoS
To DSCP
Indicates the value of the DSCP marking value that indicates the
priority of the traffic.
From DSCP
The lower limit of the range of values for marking that indicates the
Begin
priority assigned to a packet traveling across the network.
From DSCP End The upper limit of the range of values for marking that indicates the
priority assigned to a packet traveling across the network.
154
SonicWALL Global Management System Configuration Guide
CHAPTER 14
Configuring Website Blocking
This chapter describes how to use SonicWALL Global Management System (SonicWALL GMS) to configure one
or more SonicWALL appliances’ website blocking options. This functionality can be used to deny access to material supplied by the active content filtering subscription, specific domains, domains by keyword, and web features
such as ActiveX, Java, and cookies.
To configure website blocking features, select from the following:
•
•
General Options—configure when SonicWALL blocks access to the selected content and whether access is
blocked or only logged. See “Configuring General Website Blocking Options” on page 156.
Content Subscription Material—select which material will be blocked when you sign up for an active content
filtering subscription. See “Selecting the Content to Block” on page 157.
Note: SonicWALL appliances are entitled to a one-month content filter trial subscription. To enable the trial
subscription, see Chapter 25, “Upgrading SonicWALL Appliances.”
• Domain Blocking—block access to specific domains. See “Controlling Access to Specific Domains” on
page 165.
• Domains Keyword Blocking—block access to domains by keyword. See “Blocking Access to Domains by
Keywords” on page 167.
• Feature Blocking—block access to web features such as ActiveX, Java, and cookies. See “Blocking Web Features” on page 168.
Configuring Website Blocking
155
Configuring General Website Blocking Options
The General page is used to configure whether access to restricted content, sites, and features is blocked or logged,
when users can access blocked material (if ever), and the message that will be displayed when users attempt to
access blocked material.
SonicWALL offers two types of content filtering and supports two third-party content filtering packages: N2H2 and
Websense Enterprise. To configure filtering options for N2H2 or Websense, view the documentation that came with
the software package.
To configure general blocking options, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Website Blocking tree and click General. The Website Blocking General page appears
(Figure 140).
Figure 140: Website Blocking General Page
4. Select the content filtering package that you will use:
SonicWALL CFL/CFS—enables either the CFL or CFS SonicWALL filtering package based on the firmware version of the SonicWALL appliance. To configure SonicWALL content filtering, see “Selecting the
Content to Block” on page 157.
• N2H2—To use N2H2, you must have the N2H2 software package running on a server in your network. For
more information, visit www.n2h2.com.
• Websense—To use Websense, you must have the Websense Enterprise software package running on a
server in your network. For more information, visit www.websense.com.
•
Note: If you select N2H2 or Websense, make sure to configure their filtering options. For more information, see
“Websense and N2H2 Content Filtering” on page 171.
5. To apply content filtering to and web feature restrictions to the LAN port (WorkPort), select LAN/WorkPort.
6. To apply content filtering to and web feature restrictions to the DMZ port (HomePort), select DMZ/HomePort.
7. A trusted domain is a domain that is allowed to use web features such as Java, ActiveX, and Cookies. To create
a list of trusted domains, select the Don't block Java/ActiveX/Cookies to Trusted Domains check box.
Then, enter a domain name in the Trusted Domains field and click Add. Repeat this step for each domain you
would like to add.
156
SonicWALL Global Management System Configuration Guide
Note: Enter the domain name only. For example, “yahoo.com.” Do not include “http://.”
Entering “yahoo.com” will also allow access to www.yahoo.com, my.yahoo.com, sports.yahoo.com, and so on.
Note: This feature will only enable web features for the selected domains. To make the domain available for
unrestricted browsing, add it to the Allowed Domains list. For more information, see “Controlling Access to
Specific Domains” on page 165.
8. Enter the message that will be displayed when users attempt to access restricted content, sites, and features. For
example, “This material is restricted. Get back to work.”
9. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
10. Continue to the next section, “Selecting the Content to Block.”
Selecting the Content to Block
Depending on the version of the firmware, you will use either the CFL Filter List or the CFS Filter List page. If a
SonicWALL appliance uses CFL, it will periodically download a filter list that will be used to block objectionable
sites. If a SonicWALL appliance uses CFS, it will send a request to the SonicWALL site each time a request for
potentially objectionable material is made.
Content Filter List
The CFL Filter List page defines categories of website content that will be blocked and when the SonicWALL
appliance(s) will download the content filter list.
Note: This page does not affect N2H2 or Websense content filtering. For information on configuring filtering
options for these software packages, refer to their documentation.
To configure the filter list, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Website Blocking tree and click CFL Filter List. The CFL Filter List page appears (Figure 141).
Figure 141: CFL Filter List Page
Configuring Website Blocking
157
4. Select the content to block:
•
•
•
•
•
•
•
•
•
•
•
•
Violence/Profanity—Includes pictures or text exposing extreme cruelty, or physical or emotional acts
against any animal or person that are primarily intended to hurt or inflict pain. Obscene words, phrases, and
profanity are defined as text that uses, but is not limited to, George Carlin’s seven censored words more
often than once every 50 messages (Newsgroups) or once a page (Web sites).
Partial Nudity—Pictures exposing the female breast or full exposure of either male or female buttocks,
except when exposing genitalia. Excludes all swimsuits, including thongs.
Full Nudity—Pictures exposing any or all portions of the human genitalia. Excludes sites containing
nudity or partial nudity of a wholesome nature. For example, web sites hosted by publications such as
National Geographic or Smithsonian Magazine and museums such as the Guggenheim, the Louvre, or the
Museum of Modern Art are not blocked.
Sexual Acts (graphics or text)—Pictures or text exposing anyone or anything involved in explicit sexual
acts and or lewd and lascivious behavior, including masturbation, copulation, pedophilia, and intimacy
involving nude or partially nude people in heterosexual, bisexual, lesbian or homosexual encounters. This
also includes phone sex ads, dating services, adult personals, CD-ROMs, and videos.
Gross Depictions (graphics or text)—Pictures or descriptive text of anyone or anything that are crudely
vulgar or grossly deficient in civility or behavior, or that show scatological impropriety. For example,
maiming, bloody figures, or indecent depiction of bodily functions.
Intolerance (graphics or text)—Pictures or text advocating prejudice or discrimination against any race,
color, national origin, religion, disability or handicap, gender, or sexual orientation. Includes any picture or
text that elevates one group over another. Also includes intolerant jokes or slurs.
Satanic/Cult (graphics or text)—Pictures or text advocating devil worship, an affinity for evil or wickedness, or the advocacy to join a cult. A cult is defined as a closed society headed by a single individual where
loyalty is demanded and leaving is punishable.
Drugs/Drug Culture (graphics or text)—Pictures or text advocating the illegal use of drugs for entertainment. Includes substances used for other than their primary purpose to alter the individual’s state of mind,
such as glue sniffing. Excludes currently illegal drugs legally prescribed for medicinal purposes (e.g., drugs
used to treat glaucoma or cancer).
Militant/Extremist (graphics or text)—Pictures or text advocating extremely aggressive and combative
behaviors, or unlawful political measures. Topics include groups that advocate violence as a means to
achieve their goals. Includes “how to” information on weapons making, ammunition making, or the making
or use of pyrotechnic materials. Also includes the use of weapons for unlawful reasons.
Sex Education (graphics or text)—Pictures or text advocating the proper use of contraceptives. This topic
includes condom use, the correct way to wear a condom and how to put a condom in place. Also included
are sites relating to discussion about the use of the Pill, IUDs, and other types of contraceptives. In addition
to the above, this includes discussion sites on discussing diseases with a partner, pregnancy, and respecting
boundaries. Excluded from this category are commercial sites selling sexual paraphernalia.
Questionable/Illegal Gambling (graphics or text)—Pictures or text advocating materials or activities of a
dubious nature which that be illegal in any or all jurisdictions, such as illegal business schemes, chain letters, copyright infringement, computer hacking, phreaking (using someone’s phone lines without permission), and software piracy. Also includes text advocating gambling relating to lotteries, casinos, betting,
numbers games, on-line sports, and financial betting, including non-monetary dares.
Alcohol & Tobacco (graphics or text)—Pictures or text advocating the sale, consumption, or production
of alcoholic beverages and tobacco products.
5. To configure the SonicWALL appliance(s) to download the content list weekly, select the Automatically
Download List Every check box and select the day of the week and time when the download will occur.
If you select this option, configure the SonicWALL appliance(s) to download the list at a time when network
activity is low.
Note: This option requires a subscription to the Content Filter List updates.
6. To download a new content filter list now, click the Download Filter List Now button.
7. Select one of the following Timing options:
•
•
158
Always Block—Always blocks access to all restricted content, sites, and features.
Block From—Blocks access to restricted content, sites, and features between the selected hours.
SonicWALL Global Management System Configuration Guide
8. Select one of the following Logging options:
•
•
Log and Block Access—Blocks access to restricted content, sites, and features and logs access attempts.
Log Only—Does not block access to restricted content, sites, and features, but logs access. This enables
organizations to monitor appropriate usage without restricting access.
9. Select from the following filter list expiration options:
•
•
To block access to all web sites except trusted domains thirty days after the filter list expires, select Block
traffic to all websites except for trusted domains.
To allow access to all web sites thirty days after the filter list expires, select Allow traffic access to all
websites.
10. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
11. Continue to the next section, “Controlling Access to Specific Domains.”
Content Filter Service
To configure the Content Filter Service, follow these steps:
•
•
•
Configure the general CFS Filter List settings. For more information, see “Configuring the General CFS Filter
List Settings” on page 159.
If this is a standard CFS subscription, configure the CFS Standard options. For more information, see “Configuring the CFS Standard Page” on page 160.
If this is a premium CFS subscription, configure the CFS Premium options. For more information, see “Configuring the CFS Premium Page” on page 162.
Configuring the General CFS Filter List Settings
The CFS Filter List page defines categories of web site content that will be blocked in real time.
Note: This page does not affect N2H2 or Websense content filtering. For information on configuring filtering
options for these software packages, refer to their documentation.
To configure the filter list, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Website Blocking tree and click CFS Filter List. The CFS Filter List page appears (Figure 143).
Configuring Website Blocking
159
Figure 142: CFS Filter List Page
4. Specify how long the SonicWALL appliance will wait if the CFS server is unavailable before blocking web
traffic in the If Server is unavailable for field.
5. Specify the action the SonicWALL appliance will take if the server is unavailable. To block access to all web
sites, select Block traffic to all Web sites. To allow access to all web sites, select Allow traffic to all Web
sites.
6. Specify how the SonicWALL appliance will respond to blocked URLs:
•
•
Block Access to URL—Blocks access to restricted content, sites, and features.
Log Access to URL—Does not block access to restricted content, sites, and features, but logs access. This
enables organizations to monitor appropriate usage without restricting access.
7. Specify the size of the URL cache in the Cache Size field (default: 3072 KB).
8. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
Configuring the CFS Standard Page
The CFS Standard page defines categories of web site content that will be blocked in real time.
Note: This page does not affect N2H2 or Websense content filtering. For information on configuring filtering
options for these software packages, refer to their documentation.
To configure the filter list, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Website Blocking tree and click CFS Standard. The CFS Standard page appears (Figure 143).
160
SonicWALL Global Management System Configuration Guide
Figure 143: CFS Standard Page
4. To enable content filtering, select the Enable Allowed/Forbidden Domains check box.
5. To enable keyword blocking, select the Enable Keyword Blocking check box.
6. To disable all web traffic except for specifically allowed domains, select the Disable all web traffic except for
allowed domains check box.
7. Select the content to block:
• Violence/Hate/Racism—Includes pictures or text exposing extreme cruelty, or physical or emotional acts
against any animal or person that are primarily intended to hurt or inflict pain. Includes pictures or text
advocating prejudice or discrimination against any race, color, national origin, religion, disability or handicap, gender, or sexual orientation. Includes any picture or text that elevates one group over another. Also
includes intolerant jokes or slurs.
• Intimate Apparel/Swimsuit —Partial Nudity—Pictures exposing males or females in lingerie, swimsuits, or other intimate apparel.
• Nudism (graphics or text)—Pictures or text advocating nudism, providing information, or advertising
related resorts or services.
• Pornography (graphics or text)—Pictures of any or all portions of the human genitalia and pictures or
text exposing anyone or anything involved in explicit sexual acts and or lewd and lascivious behavior,
including masturbation, copulation, pedophilia, and intimacy involving nude or partially nude people in
heterosexual, bisexual, lesbian or homosexual encounters. Excludes sites containing nudity or partial nudity
of a wholesome nature and all swimsuits, including thongs.
• Weapons (graphics or text)—Pictures or text advocating the legal or illegal use of weapons, providing
weapons for sale, or advocating extremely aggressive and combative behaviors, or unlawful political measures.
• Adult/Mature Content (graphics or text)—Pictures or text such as phone sex ads, dating services, adult
personals, CD-ROMs, and videos. Excludes sites containing nudity or partial nudity of a wholesome nature
and all swimsuits, including thongs.
• Cult/Occult (graphics or text)—Pictures or text advocating devil worship, an affinity for evil or wickedness, or the advocacy to join a cult. A cult is defined as a closed society headed by a single individual where
loyalty is demanded and leaving is punishable.
• Drugs/Illegal Drugs (graphics or text)—Pictures or text advocating the illegal use of drugs for entertainment. Includes substances used for other than their primary purpose to alter the individual’s state of mind,
Configuring Website Blocking
161
•
•
•
•
such as glue sniffing. Excludes currently illegal drugs legally prescribed for medicinal purposes (e.g., drugs
used to treat glaucoma or cancer).
Illegal Skills/Questionable Skills (graphics or text)—Pictures or text advocating materials or activities of
a dubious nature which that be illegal in any or all jurisdictions, such as illegal business schemes, chain letters, copyright infringement, computer hacking, phreaking (using someone’s phone lines without permission), and software piracy.
Sex Education (graphics or text)—Pictures or text advocating the proper use of contraceptives. This topic
includes condom use, the correct way to wear a condom and how to put a condom in place. Also included
are sites relating to discussion about the use of the Pill, IUDs, and other types of contraceptives. In addition
to the above, this includes discussion sites on discussing diseases with a partner, pregnancy, and respecting
boundaries. Excluded from this category are commercial sites selling sexual paraphernalia.
Gambling (graphics or text)—Pictures or text providing or advocating gambling services relating to lotteries, casinos, betting, numbers games, on-line sports, and financial betting, including non-monetary dares.
Alcohol & Tobacco (graphics or text)—Pictures or text advocating the sale, consumption, or production
of alcoholic beverages and tobacco products.
8. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
Configuring the CFS Premium Page
The CFS Premium service enables you to add advanced content filtering functionality to one or more SonicWALL
appliances by choosing specific content to filter from 64 different content categories. This section describes how to
configure the CFS Premium service.
Note: This page does not affect N2H2 or Websense content filtering. For information on configuring filtering
options for these software packages, refer to their documentation.
To configure the CFS Premium service, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Website Blocking tree and click CFS Premium. The CFS Premium page appears (Figure 144).
Figure 144: CFS Premium Page
4. Click Add CFS Policy. The Add CFS Policy page appears.
162
SonicWALL Global Management System Configuration Guide
Figure 145: Policy Page
5. Enter a name for the policy.
6. Click the URL List tab.
Figure 146: URL List Page
7. Select the check boxes of the categories to block.
8. Click the Settings tab.
Configuring Website Blocking
163
Figure 147: CFS Settings Page
9. To disable the allowed domains list, select the Disable Allowed Domains check box.
10. To prevent access to domains specified in the Forbidden Domain list, select the Enable Forbidden Domains
check box.
11. To enable the keyword blocking feature, select the Enable Keyword Blocking check box.
12. Select when the forbidden URLs will be blocked.
13. When you are finished, click OK. The settings are changed for each selected SonicWALL appliance. To clear
all screen settings and start over, click Cancel.
14. Repeat this procedure for each filter that you would like to add.
164
SonicWALL Global Management System Configuration Guide
Controlling Access to Specific Domains
The Customization page is used to block or allow access to specific domain names. This enables an organization to
block access to domains that are not in the content filter list, allow access to domains in the content filter list, or
only allow access to specific domains.
Allowed domains are domains that users can access, regardless of whether they appear in the content filter list.
Allowed domains are particularly useful for dedicated systems that are only allowed to access specific websites. Up
to 256 entries are supported in the Allowed Domains list.
Forbidden domains are domains that users will not be allowed to access. This is useful when a website disrupts a
corporate or educational environment. To find out which websites are most frequently accessed, refer to the Top
Web Site Hits section of the log report. Up to 256 entries are supported in the Allowed Domains list.
Note: This feature is not available if you select N2H2 or Websense content filtering. For information on configuring
filtering options for these software packages, refer to their documentation.
To configure list customization options, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Website Blocking tree and click Customization. The Customization page appears (Figure 148).
Figure 148: Customization Page
4. Enable list customization by selecting the Enable Filter List Customization check box.
5. To add an allowed domain, enter a domain name in the Allowed Domains field and click Add. Repeat this step
for each domain you would like to add.
Note: Enter the domain name only. For example, “yahoo.com.” Do not include “http://.”
Entering “yahoo.com” will also allow access to www.yahoo.com, my.yahoo.com, sports.yahoo.com, and so on.
6. To add a forbidden domain, enter a domain name in the Forbidden Domains field and click Add. Repeat this
step for each forbidden domain you would like to add.
Note: Enter the domain name only. For example, “bad-site.com.” Do not include “http://.”
Entering “bad-site.com” will also block access to www.bad-site.com, really.bad-site.com, amazingly.badsite.com, and so on.
Configuring Website Blocking
165
7. Select one of the following Timing options:
• Always Block—Always blocks access to all restricted content, sites, and features.
• Block From—Blocks access to restricted content, sites, and features between the selected hours.
8. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
9. Continue to the next section, “Blocking Access to Domains by Keywords.”
Deleting Domains from the Domain Lists
To delete one or more domains from the Allowed Domain or Forbidden Domain lists, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Website Blocking tree and click Customization.
4. Select an item to delete and click its check box below the trash can icon. Repeat this step for each domain that
you want to remove from the domain lists.
5. When you are finished, click Update. The selected items are deleted.
166
SonicWALL Global Management System Configuration Guide
Blocking Access to Domains by Keywords
The URL Keywords page is used to block access to domain names by keyword. This provides a second line of
defense against objectionable material. For example, if the keyword “xxx” was included in the list, the site
“www.new-site.com/xxx.html” would be blocked.
Note: Be careful when using this feature. For example, blocking the word “breast” can prevent access to both pornographic or objectionable sites and those on breast cancer.
Note: This feature is not available if you select N2H2 or Websense content filtering. For information on configuring
filtering options for these software packages, refer to their documentation.
To configure domain blocking by keyword, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Website Blocking tree and click URL Keywords. The URL Keywords page appears (Figure 149).
Figure 149: URL Keywords Page
4. Enable keyword blocking by selecting the Enable Keyword Blocking check box.
5. Click Update. A task is scheduled that will apply the new setting to each selected SonicWALL appliance.
6. To add a keyword, enter the keyword and click Add. A task is scheduled to add the keyword to each selected
SonicWALL appliance. Repeat this step for each keyword you would like to add.
7. To remove a keyword, select its check box below the trash can icon. Repeat this step for each domain that you
want to remove from the domain lists.
8. Continue to the next section, “Blocking Web Features.”
9. To clear all screen settings and start over, click Reset.
Configuring Website Blocking
167
Blocking Web Features
The Web Features page is used to block ActiveX Controls, Java, cookies, web proxy, and known fraudulent certificates. To block these features, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Website Blocking tree and click Web Features. The Web Features page appears (Figure 150).
Figure 150: Web Features Page
4. Select objects to block:
ActiveX—blocks ActiveX controls. ActiveX is a programming language used to imbed small programs in
web pages. It is generally considered insecure because it is possible for malicious programmers to write
controls that can delete files, compromise security, or cause other damage.
• Java—blocks Java applets. Java applets are downloadable web applications that are used on many websites. Selecting this option will block all Java applets, regardless of their function.
• Cookies—prevents websites from placing information on user hard drives. Cookies are used by Web servers to track Web usage and remember user identity. Cookies can compromise users' privacy by tracking
Web activities.
•
Note: Blocking cookies on the public Internet creates a large number of accessibility problems. Most sites
make extensive use of cookies to generate web pages and blocking cookies will make most e-commerce
applications unusable.
• Access to HTTP Proxy Servers—blocks users from accessing web proxy servers on the Internet to circumvent content filtering by pointing their computers to the proxy servers.
• Known Fraudulent Certificates—blocks access to web content that originated from a known fraudulent
certificate. Digital certificates help verify that web content originated from an authorized party.
5. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
6. Continue to the next section, “Consent.”
168
SonicWALL Global Management System Configuration Guide
Consent
The consent feature allows organizations to specify computers that are always filtered and computers that are filtered by user request. This feature is popular in libraries, Internet cafes, and other public Internet systems.
The following is an example of a consent web page (Figure 151).
Figure 151: Sample Consent Page
Note: This feature is not available if you select N2H2 or Websense content filtering. For information on configuring
filtering options for these software packages, refer to their documentation.
To configure the consent feature, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Website Blocking tree and click Consent. The Consent page appears (Figure 152).
Configuring Website Blocking
169
Figure 152: Filtering Consent Page
4. Select the Require Consent check box.
5. Enter the maximum time a user can access the Internet in the Maximum Web Usage field.
6. Specify the maximum amount of time (in minutes) a connection may remain idle before the user is logged out
and must agree to the consent agreement again in the User Idle Timeout field.
7. When the consent feature is enabled, users must choose whether they want filtering. Configure the following:
Enter the URL of the web page from which users choose to enable filtering. This page appears when users
first attempt to access the Internet and must contain a link for choosing unfiltered access and a link for
choosing filtered access. The link for unfiltered access is IPaddress/iAccept.html. The link for filtered
access is IPaddress/iAcceptFilter.html. IPaddress is the LAN (WorkPort) IP address of the SonicWALL
appliance.
• Enter the URL of the page that appears when users choose to access the Internet without content filtering in
the Consent Accepted URL (Filtering Off) field. This page must be accessible on the LAN (WorkPort).
• Enter the URL of the page that appears when users access the Internet with content filtering enabled in the
Consent Accepted URL (Filtering On) field. This page must be accessible on the LAN (WorkPort).
•
8. When a user opens a web browser on a computer with mandatory content filtering they will be shown a consent
page. You will need to create this Web page. It usually contains an Acceptable Use Policy and a notification that
violations will be logged or blocked.
This web page must reside on a web server that is accessible as a URL by LAN (WorkPort) users. This page
must also contain a link that tells the SonicWALL appliance that the user agrees to having filtering enabled. To
do this, create the following link:
IPaddress/iAcceptFilter.html
where IPaddress is the LAN (WorkPort) IP address of the SonicWALL appliance.
Enter the URL of this page in the Consent page URL (Mandatory Filtering) field.
Enter the IP address of a system that will be subject to mandatory filtering and click Add. Repeat this step for
each system that will use mandatory filtering. Up to 128 IP addresses can be entered.
To remove a system from the mandatory filtering list, highlight its IP address and click Delete Address.
9. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
170
SonicWALL Global Management System Configuration Guide
Websense and N2H2 Content Filtering
This section describes additional filtering configuration options for N2H2 and Websense content filtering.
N2H2
To configure N2H2 content filtering options, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Website Blocking tree and click N2H2. The N2H2 page appears (Figure 153).
Figure 153: N2H2 Page
4. Enter the N2H2 server name or IP address in the Server Host Name or IP Address field.
5. Enter the port that the N2H2 server listens for N2H2 requests in the Listen Port field (default: 4005).
6. Enter the port that the N2H2 server uses to send packets to the SonicWALL appliances in the Reply Port field
(default: 4005).
7. Enter the username associated with the N2H2 account in the User Name field.
8. Enter the size of the URL cache in the URL Cache Size field. A larger URL cache can improve browser
response times.
9. Select the action that the SonicWALL appliance(s) will take if the N2H2 server is unavailable beyond the specified period of time:
• To block traffic to all web sites, select Block traffic to all web sites.
• To allow access to all web sites, select Allow traffic to all web sites.
10. Select one of the following:
•
•
Block Access to URL—Blocks access to restricted sites and logs access attempts.
Log Access to URL—Does not block access to restricted sites, but logs access. This enables organizations
to monitor appropriate usage without restricting access.
11. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
Configuring Website Blocking
171
Websense
To configure Websense content filtering options, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Website Blocking tree and click Websense. The Websense page appears (Figure 154).
Figure 154: Websense Page
4. Enter the Websense server name or IP address in the Server Host Name or IP Address field.
5. Enter the port used for Websense packets in the Server Port field (default: 15666).
6. Enter the username associated with the Websense account in the User Name field.
7. Enter the size of the URL cache in the URL Cache Size field. A larger URL cache can improve browser
response times.
8. Select the action that the SonicWALL appliance(s) will take if the Websense server is unavailable beyond the
specified period of time:
• To block traffic to all web sites, select Block traffic to all web sites.
• To allow access to all web sites, select Allow traffic to all web sites.
9. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
172
SonicWALL Global Management System Configuration Guide
CHAPTER 15
Configuring Dynamic Host Configuration Protocol
Dynamic Host Configuration Protocol (DHCP) enables network administrators to automate the assignment of IP
addresses from a centralized DHCP server. This conserves IP addresses and make is easy for mobile users to move
among different segments of the network without having to manually enter new IP addresses.
This chapter describes how to use the SonicWALL Global Management System (SonicWALL GMS) to configure
SonicWALL appliances as DHCP servers.
Select from the following:
To configure clients to obtain their IP addresses from a DHCP server at the other end of a VPN tunnel, see
“Configuring DHCP Over VPN” on page 173.
• To specify DHCP IP address ranges, see “Configuring Dynamic DHCP IP Address Ranges” on page 175.
• To specify static IP addresses, see “Configuring Dynamic DHCP IP Address Ranges” on page 175.
•
Configuring DHCP Over VPN
DHCP over VPN enables clients of the SonicWALL appliance to obtain IP addresses from a DHCP server at the
other end of the VPN tunnel or a local DHCP server.
To configure DHCP over VPN, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the DHCP tree and click DHCP over VPN. The DHCP over VPN page appears (Figure 155).
Configuring Dynamic Host Configuration Protocol
173
Figure 155: DHCP Over VPN Page
4. Select from the following:
•
174
To configure the SonicWALL appliance to forward DHCP requests through a VPN tunnel, select Remote
Gateway from the DHCP Relay Mode list box and do the following:
• Select the security association (SA) through which the DHCP server resides from the Obtain using
DHCP through this SA list box.
• Enter the IP address that will be inserted by the SonicWALL appliance as the IP address of the DHCP
Relay Agent in the Relay IP Address field.
• To manage this SonicWALL appliance remotely through the VPN tunnel from behind the Central Gateway, enter the management IP address in the Remote Management IP Address field.
• If you enable Block traffic through tunnel when IP spoof detected, the SonicWALL blocks any traffic across the VPN tunnel that is spoofing an authenticated user’s IP address. If you have any static
devices, however, you must ensure that the correct Ethernet address is entered for the device.
• If the VPN tunnel is disrupted, temporary DHCP leases can be obtained from the local SonicWALL
appliance. Once the tunnel is active, it will stop issuing leases. To enable this option, select the Obtain
temporary lease from local DHCP server if tunnel is down check box.
When you enable this option, clients will be able to obtain IP addresses if the tunnel is unavailable. To
ensure that clients use the remote DHCP server shortly after it becomes available, enter a short lease
time in the Temporary Lease Time field. The default value is two minutes.
SonicWALL Global Management System Configuration Guide
Make sure to enable DHCP and enter an IP address range on the DHCP Setup page. Otherwise, the
SonicWALL appliance will be unable to act as a DHCP server.
• To specify static IP addresses on the LAN (WorkPort), enter the IP address and MAC address and click
Add. Repeat this step for each device that uses a static IP address.
• To specify a device that is not allowed to obtain an IP address through the SA, enter its MAC address
and click Add. Repeat this step for each device that will not be allowed to obtain an IP address through
the SA.
• To configure the SonicWALL appliance to forward DHCP requests to local servers, select Central Gateway from the DHCP Relay Mode list box and do the following:
• To configure the SonicWALL appliance to send DHCP requests to specific DHCP servers, select the
Send DHCP requests to the server addresses listed below check box. Then, enter the IP address of a
DHCP server and click Add. Repeat this step for DHCP server that you want to add.
• To configure the SonicWALL appliance to broadcast DHCP requests, deselect the Send DHCP
requests to the server addresses listed below check box and leave the DHCP Servers field blank.
• To use the DHCP server built into the SonicWALL appliance for some clients, select the Use Internal
DHCP Server check box.
To use the internal DHCP server for Global VPN clients, select the For Global VPN Client check box.
To use the internal DHCP server for remote firewalls, select the For Remote Firewalls check box.
5. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
Configuring Dynamic DHCP IP Address Ranges
This section describes how to configure dynamic IP address ranges.
Note: In order for changes on this page to take effect, the SonicWALL(s) will automatically be restarted. We recommend configuring these options when network activity is low.
To configure one or more dynamic IP address ranges, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the DHCP tree and click Dynamic Ranges. The Dynamic Ranges page appears (Figure 156).
Figure 156: Dynamic Ranges Page
Configuring Dynamic Host Configuration Protocol
175
4. Select from the following:
• To enable the DHCP server, select the Enable DHCP Server check box.
• To disable the DHCP server, deselect the Enable DHCP Server check box.
• To disable the DHCP server and configure computers on the LAN (WorkPort) to use a DHCP server outside
the firewall, deselect the Enable DHCP Server check box and select the Allow DHCP Pass Through
check box.
5. To add a dynamic range, click Add Dynamic Range and complete the following fields:
• Enter the start of the range in the Range Start field.
• Enter the end of the range in the Range End field.
• To allow BootP clients to use this range, select the Allow BootP clients to use range check box.
• Specify the IP address and subnet mask of the default gateway for this IP address range in the Default
Gateway and Subnet Mask fields. By default, these fields will use the settings on the Network Settings
page.
• Enter the lease time for this range in the Lease Time field.
• Optional. Enter the domain name associated with this IP address range in the Domain Name field.
• Select from the following:
• To use the DNS and WINS servers specified on the Network Settings page, select Set DNS Servers
using SonicWALLs Network settings.
• To specify the DNS servers manually for this IP address range, select Specify Manually and enter the
IP addresses of the DNS and WINS servers.
6. When you are finished, click Update. The settings are saved. To clear all screen settings and start over, click
Reset.
176
SonicWALL Global Management System Configuration Guide
Configuring Static IP Addresses
This section describes how to specify static IP addresses.
Note: In order for changes on this page to take effect, the SonicWALL(s) will automatically be restarted. We recommend configuring these options when network activity is low.
To configure one or more static IP addresses, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the DHCP tree and click Static Entries. The Static Entries page appears (Figure 156).
Figure 157: Static Entries Page
4. Select from the following:
• To enable the DHCP server, select the Enable DHCP Server check box.
• To disable the DHCP server, deselect the Enable DHCP Server check box.
• To disable the DHCP server and configure computers on the LAN (WorkPort) to use a DHCP server outside
the firewall, deselect the Enable DHCP Server check box and select the Allow DHCP Pass Through
check box.
5. To add a static IP address, click Add Static Entry and complete the following fields:
• Enter the IP address of the device in the Static IP Address field.
• Enter the MAC address of the device in the Static IP Address field.
• Specify the IP address and subnet mask of the default gateway for this IP address in the Default Gateway
and Subnet Mask fields. By default, these fields will use the settings on the Network Settings page.
• Enter the lease time for this IP address in the Lease Time field.
• Optional. Enter the domain name associated with this IP address in the Domain Name field.
• Select from the following:
• To use the DNS and WINS servers specified on the Network Settings page, select Set DNS Servers
using SonicWALLs Network settings.
• To specify the DNS servers manually for this IP address, select Specify Manually and enter the IP
addresses of the DNS and WINS servers.
6. When you are finished, click Update. The settings are saved. To clear all screen settings and start over, click
Reset.
Configuring Dynamic Host Configuration Protocol
177
178
SonicWALL Global Management System Configuration Guide
CHAPTER 16
Configuring User Settings
This chapter describes how to use the SonicWALL Global Management System (SonicWALL GMS) to configure
user and user access settings.
Configuring Users
Select from the following:
• Configuring users for SonicOS Enhanced. See “SonicOS Enhanced” on page 179.
• Configuring users for SonicOS Standard. See “SonicOS Standard” on page 183.
SonicOS Enhanced
SonicOS Enhanced uses a Group/User hierarchy for organizing users. This section describes how to configure new
users and groups.
Configuring Local Groups
By default, SonicOS Enhanced has five groups. These include:
•
•
•
•
•
Everyone
Guest Services
Trusted Users
Content Filtering Bypass
Limited Administrators
The permissions of these groups will automatically be applied to its members unless you manually modify a users
settings. To add or edit a group, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Users tree and click Local Groups. The Local Groups page appears (Figure 158).
Configuring User Settings
179
Figure 158: Local Groups Page
4. To add a local group, click Add New Local Group. To edit the settings of an existing group, click its Configure
icon.
Figure 159: Add/Edit Group Dialog Box
5. Configure the following options:
Bypass Filters—select Bypass Filters if the users within the group will have unlimited access to the Internet from the LAN, bypassing Web, News, Java, and ActiveX blocking.
• Limited Management Capabilities—select this option to provide users within the group limited local
management access to the SonicWALL Management interface. The access is limited to the following
pages:
• General—Status, Network, Time
• Log—View Log, Log Settings, Log Reports
• Tools—Restart, Diagnostics minus Tech Support Report
•
6. Click the Members tab.
180
SonicWALL Global Management System Configuration Guide
Figure 160: Add/Edit Group Dialog Box
7. Select the members or groups that will belong to this group and click the right arrow button (->).
8. Click the VPN Access tab.
Figure 161: Add/Edit Group Dialog Box
9. Select the networks to which users within this group will be able to access through their VPN client software
and click the right arrow button (->).
10. Click the CFS Policy tab.
Figure 162: Add/Edit Group Dialog Box
11. Select the content that will be restricted to users within this group.
12. When you are finished, click OK. The settings are saved.
13. Repeat this procedure for each group to add or modify.
Configuring Local Users
To add or edit a user, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
Configuring User Settings
181
3. Expand the Users tree and click Local Users. The Local Users page appears (Figure 163).
Figure 163: Local Users Page
4. To add a local group, click Add New Local User. To edit the settings of an existing user, click its Configure
icon.
Figure 164: Add/Edit User Dialog Box
5. Configure the following options:
Name—name of the user.
Password—password of the user.
Bypass Filters—select Bypass Filters if the user will have unlimited access to the Internet from the LAN,
bypassing Web, News, Java, and ActiveX blocking.
• Limited Management Capabilities—select this option to provide the user limited local management
access to the SonicWALL Management interface. The access is limited to the following pages:
• General—Status, Network, Time
• Log—View Log, Log Settings, Log Reports
• Tools—Restart, Diagnostics minus Tech Support Report
•
•
•
6. Click the Groups tab.
182
SonicWALL Global Management System Configuration Guide
Figure 165: Add/Edit User Dialog Box
7. Select a user group to which this user will be a member and click the right arrow button (->). Repeat this step
for each group to add.
8. Click the VPN Access tab.
Figure 166: Add/Edit Group Dialog Box
9. Select a network to which this user will be able to access through the VPN client software and click the right
arrow button (->). Repeat this step for each network to add.
10. When you are finished, click OK. The settings are saved.
11. Repeat this procedure for each user to add or modify.
SonicOS Standard
SonicWALL appliances can be configured to authenticate users through a Remote Authentication Dial-In User Service (RADIUS) server, a local user list, or a combination of both. If authenticated locally or a combination of
locally and through RADIUS, SonicWALL appliances can also control user access privileges.
Note: In order for changes on this page to take effect, the SonicWALL(s) will automatically be restarted. We recommend configuring these options when network activity is low.
To add a user, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Users tree and click Settings. The User Settings page appears (Figure 168).
Configuring User Settings
183
Figure 167: Users Settings Page
4. Specify the maximum amount of time (in minutes) a connection may remain idle before users are required to
reestablish an authenticated session in the User Idle Timeout field. The timeout applies to both Remote Access
and Bypass Filters. This value may range from 5 to 99 minutes.
5. Enter the maximum amount of time a user may remain logged in through the SonicWALL appliance in the
Maximum user login time field. To allow indefinite access, enter 0.
6. To allow only authenticated users access to the Internet, select the Allow only authenticated users to access
the Internet check box.
7. Select from the following:
• To use RADIUS for all user authentication, select Use RADIUS.
• To use RADIUS for all user authentication but only allow specific listed users, select Use RADIUS and
select the Allow only users listed below check box.
• To bypass RADIUS and authenticate the listed users locally, select Authenticate users in list below.
8. When you are finished, click Update. SonicWALL GMS creates a task that changes these settings for each
selected SonicWALL appliance.
9. To add a user, do the following:
• Enter the user name in the User Name field.
• Enter the password in the New Password field and reenter it in the Confirm Password field.
•
184
Note: Passwords are case-sensitive.
Select from the following user privileges:
• Remote Access—enables the users to access LAN resources from the Internet. This option is only
available in Standard mode.
• Bypass Filters—enables Bypass Filters if the user can bypass Content Filtering settings.
• Access to VPNs—enables the users to send information over the VPN Security Associations.
• Access from VPN Client with XAUTH—use if a VPN client is using XAUTH for authentication.
• Access Internet Access—enables the users to access the Internet.
• Limited Management—allows authorized users limited local management access to the SonicWALL
interface. Access is limited to the General page (Status, Network, Time), the Log page (View Log, Log
Settings, Log Reports), and the Tools page (Restart, Diagnostics minus Tech Support).
SonicWALL Global Management System Configuration Guide
When you are finished, click Add. SonicWALL GMS creates a task that adds these users for each selected
SonicWALL appliance. Repeat this step for each user that you want to add (up to 100 users).
10. To clear all screen settings and start over, click Reset.
SonicOS Enhanced
In addition to the authentication methods available in SonicOS Standard, SonicOS Enhanced allows you to use
Lightweight Directory Access Protocol (LDAP) to authenticate users. LDAP is compatible with Microsoft’s Active
Directory.
Figure 168: User Settings Page, SonicOS Enhanced
Authentication Method
•
•
•
•
•
Select Local Users to configure users in the local database using the
Users > Local Users and Users > Local Groups pages.
Select RADIUS if you have more than 1,000 users or want to add an extra layer of security for authenticating
the user to the SonicWALL. If you select Use RADIUS for user authentication, users must log into the SonicWALL using HTTPS in order to encrypt the password sent to the SonicWALL. If a user attempts to log into
the SonicWALL using HTTP, the browser is automatically redirected to HTTPS.
Select RADIUS + Local Users if you want to use both RADIUS and the SonicWALL local user database for
authentication.
Select LDAP if you use a Lightweight Directory Access Protocol (LDAP) server or Microsoft Active Directory
(AD) server to maintain all your user account data.
Select LDAP + Local Users if you want to use both LDAP and the SonicWALL local user database for authentication.
Configuring User Level Authentication Settings
This section describes how to configure User Level Authentication (ULA) settings. To configure ULA settings, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Users tree and click User ULA Settings. The User ULA Settings page appears (Figure 169).
Configuring User Settings
185
Figure 169: User ULA Settings Page
4. To only allow authenticated users to access the Internet, select the Allow only authenticated users to access
the Internet check box.
5. To allow unauthenticated users to access a service, select the service in the Always allow these services area
and click Add. Repeat this step for each service to add.
6. To specify a range of IP addresses that will always be allowed to access the Internet, enter the IP address in the
Begin field and the size of the range in the Length field. Repeat this step for each range to add.
7. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
Configuring RADIUS Authentication
If you selected Use RADIUS for user authentication or Use RADIUS but also allow locally configured users,
the Configure button becomes available.
1. Click Configure to set up your RADIUS server settings on the SonicWALL. The RADIUS Configuration
window is displayed.
2. Define the RADIUS Server Timeout in Seconds. The allowable range is 1-60 seconds with a default value of
5.
3. Define the number of times the SonicWALL attempts to contact the RADIUS server in the Retries field. If the
RADIUS server does not respond within the specified number of retries, the connection is dropped. This field
can range between 0 and 10, however 3 RADIUS server retries is recommended.
RADIUS Servers
4. Specify the settings of the primary RADIUS server in the RADIUS servers section. An optional secondary
RADIUS server can be defined if a backup RADIUS server exists on the network.
5. Type the IP address of the RADIUS server in the IP Address field.
6. Type the Port Number for the RADIUS server.
7. Type the RADIUS server administrative password or “shared secret” in the Shared Secret field. The alphanumeric Shared Secret can range from 1 to 31 characters in length. The shared secret is case sensitive.
8. If there is a secondary RADIUS server, type the appropriate information in the Secondary Server section.
186
SonicWALL Global Management System Configuration Guide
9. Type the RADIUS server administrative password or “shared secret” in the Shared Secret field. The alphanumeric Shared Secret can range from 1 to 31 characters in length. The shared secret is case sensitive.
RADIUS Users
Click the RADIUS Users tab
RADIUS Users Settings
Select Allow only users listed locally if only the users listed in the SonicWALL database are authenticated using
RADIUS.
Select the mechanism used for setting user group memberships for RADIUS users from the following list:
•
•
•
Use SonicWALL vendor-specific attribute on RADIUS server: select to apply specific attributes from the
RADIUS server.
Use RADIUS Filter-ID attribute on RADIUS server
Do not use any RADIUS attributes for user groups
For a shortcut for managing RADIUS user groups, check Memberships can be set locally by duplicating
RADIUS user names. When you create users with the same name locally on the security appliance and manage
their group memberships, the memberships in the RADIUS database will automatically change to mirror your local
changes.
If you have previously configured User Groups on the SonicWALL, select the group from the Default user group
to which all RADIUS user belong menu.
You can create a new group by choosing Create a new user group... from the list:
1. Select Create a new user group... The Add Group window displays.
2. In the Settings tab, enter a name for the group. You may enter a descriptive comment as well.
3. In the Members tab, select the members of the group. Select the users or groups you want to add in the left column and click the -> button. Click Add All to add all users and groups.
Note: You can add any group as a member of another group except Everybody and All RADIUS Users. Be
aware of the membership of the groups you add as members of another group.
4. In the VPN Access tab, select the network resources this group will have VPN Access to by default.
5. If you have Content Filtering Service (CFS) on your security appliance, you can configure the content filtering
policy for this group in the CFS Policy tab. See Chapter 51, Configuring SonicWALL Content Filter for
instructions on registering for and managing the SonicWALL Content Filtering Service.
RADIUS Client Test
You can test your RADIUS Client user name and password by typing in a valid user name in the User field, and the
password in the Password field.
If the validation is successful, the Status messages changes to Success. If the validation fails, the Status message
changes to Failure. Once the SonicWALL has been configured, a VPN Security Association requiring RADIUS
authentication prompts incoming VPN clients to type a User Name and Password into a dialogue box.
Active Directory / LDAP Authentication
In addition to RADIUS and the local user database, SonicOS Enhanced can support LDAP and Microsoft Active
Directory (AD) directory services for user authentication. Active Directory support on SonicOS Enhanced is not a
single-sign on mechanism, but rather the ability for SonicOS Enhanced to act as an LDAP client against an Active
Directory’s LDAP interface using Microsoft’s implementation of an LDAP schema. SonicOS Enhanced provides
extremely flexible schema interoperability, with support for the Microsoft AD schema, the LDAP core schema, the
Configuring User Settings
187
RFC2798 inetOrgPerson schema, and even user-defined schemas. Connectivity to LDAP servers is also flexible,
with support for following protocols:
•
•
•
•
•
LDAPv2 (RFC3494)
LDAPv3 (RFC2251-2256, RFC3377)
LDAPv3 over TLS (RFC2830)
LDAPv3 with STARTTLS (RFC2830)
LDAP Referrals (RFC2251)
LDAP Terms
The following terms are useful when working with LDAP and its variants:
•
•
•
•
•
•
•
•
•
•
•
Schema – The schema is the set of rules or the structure that defines the types of data that can be stored in a
directory, and how that data can be stored. Data is stored in the form of ‘entries’.
Entry – The data that is stored in the LDAP directory. Entries are stored in ‘attribute’/value (or name/value)
pairs, where the attributes are defined by ‘object classes’. A sample entry would be ‘cn=john’ where ‘cn’ (common name) is the attribute, and ‘john’ is the value.
Object class – Object classes define the type of entries that an LDAP directory may contain. A sample object
class, as used by AD, would be ‘user’ or ‘group’.
Microsoft Active Directory’s Classes can be browsed at <http://msdn.microsoft.com/library/default.asp?url=/
library/en-us/adschema/adschema/classes_all.asp>
Object - In LDAP terminology, the entries in a directory are referred to as objects. For the purposes of the SonicOS implementation of the LDAP client, the critical objects are ‘User’ and ‘Group’ objects. Different implementations of LDAP can refer to these object classes in different fashions, for example, Active Directory refers
to the user object as ‘user’ and the group object as ‘group’, while RFC2798 refers to the user object as ‘inetOrgPerson’ and the group object as ‘groupOfNames’.
Attribute - A data item stored in an object in an LDAP directory. Object can have required attributes or allowed
attributes. For example, the ‘dc’ attribute is a required attribute of the ‘dcObject’ (domain component) object.
dn - A ‘distinguished name’, which is a globally unique name for a user or other object. It is made up of a number of components, usually starting with a common name (cn) component and ending with a domain specified
as two or more domain components (dc). For example, ‘cn=john,cn=users,dc=domain,dc=com’
cn – The ‘common name’ attribute is a required component of many object classes throughout LDAP.
ou – The ‘organizational unit’ attribute is a required component of most LDAP schema implementations.
dc – The ‘domain component’ attribute is commonly found at the root of a distinguished name, and is commonly a required attribute.
TLS – Transport Layer Security is the IETF standardized version of SSL (Secure Sockets Layer). TLS 1.0 is the
successor to SSL 3.0.
LDAP / AD Configuration is performed from the ‘User > Settings’ page.
Selecting either LDAP or LDAP+Local Users and clicking Apply at the top of the page will enable LDAP support, the former using an LDAP directory server exclusively, and the latter using a combination of the LDAP server
and the local user database. Upon applying these settings, an informational alert will be presented. Because the
SonicWALL will be receiving sensitive username and password information from authenticating clients, HTTPS
logins will automatically be enabled to secure the credential exchanges.
Before you begin
Before beginning your LDAP configuration, you should prepare your LDAP server and your SonicWALL for
LDAP over TLS support. This will involve installing a server certificate and your LDAP server, and a CA (Certificate Authority) certificate for the issuing CA on your SonicWALL. Assuming this has not already been done, the
steps for performing these tasks in an Active Directory environment follow:
1. Configuring the CA on the Active Directory server (skip steps a. through e. if Certificate Services are already
installed):
a. Start>Settings>Control Panel>Add/Remove Programs’
b. Select ‘Add/Remove Windows Components’
c. Select ‘Certificate Services’
d. Select ‘Enterprise Root CA’ when prompted.
188
SonicWALL Global Management System Configuration Guide
e. Enter the requested information. For detailed information on CA setup, see http://www.microsoft.com/
windows2000/techinfo/planning/security/casetupsteps.asp
a. Launch the ‘Domain Security Policy’ application:
b. ‘Start>Run>dompol.msc’
c. Open ‘Security Settings > Public Key Policies’
d. Right click on ‘Automatic Certificate Request Settings’
e. Select ‘New > Automatic Certificate Request’
f. Step through the wizard, and select ‘Domain Controller’ from the list.
2. Exporting the CA certificate from the AD server:
a. Launch the ‘Certification Authority’ application: Start>Run>certsrv.msc
b. Right click on the CA you created, select ‘properties’
c. On the ‘General’ tab, click the ‘View Certificate’ button
d. From the ‘Details’ tab, select ‘Copy to File’
e. Step through the wizard, select the ‘Base-64 Encoded X.509 (.cer)’ format.
f. Specify a path and filename to which to save the certificate.
3. Importing the CA certificate onto the SonicWALL:
a. Browse to ‘System > CA Certificates’
b. Select ‘Add new CA certificate’. Browse to and select the certificate file you just exported
c. Click the ‘Import certificate’ button.
4. Continue LDAP configuration:
a. Browse to the ‘User > Settings’ page.
Note: Should installation of Certificate Services on the Active Directory server be undesirable for some
reason, secure operation can be achieved without TLS by using LDAP with RADIUS – see RADIUS with
LDAP for user groups section later.
The ‘Configure’ button will bring up the tabbed LDAP Configuration window:
Figure 170: LDAP Configuration Window
•
Name or IP Address – Enter the FQDN or the IP address of the LDAP server against which you
wish to authenticate. If using a name, be certain it can be resolved by your DNS server. Also, if
using TLS with the ‘Require valid certificate from server’ option, the name provided here must
Configuring User Settings
189
•
•
•
•
•
•
•
•
•
•
match the name to which the server certificate was issued (i.e. the CN) or the TLS exchange
will fail.
Port Number – The default LDAP over TLS port number is TCP 636. The default LDAP (unencrypted) port
number is TCP 389. If you are using a custom listening port on your LDAP server, specify it here.
Server timeout – The amount of time, in seconds, that the SonicWALL will wait for a response from the
LDAP server before timing out. Allowable ranges are 1 to 99999 (in case you’re running your LDAP server
on a VIC-20 located on the moon), with a default of 10 seconds.
Anonymous Login – Some LDAP servers allow for the tree to be accessed anonymously. If your server
supports this (MS AS generally does not), then you may select this option.
Login name – Specify a user name which has rights to log in to the LDAP directory. The login name will
automatically be presented to the LDAP server in full ‘dn’ notation. This can be any account with LDAP
read privileges (essentially any user account) – Administrative privileges are not required. Note that this is
the user’s name, not their login ID (e.g. John Smith rather than jsmith).
Login password – The password for the user account specified above.
Protocol version – Select either LDAPv3 or LDAPv2. Most modern implementations of LDAP, including
AD, employ LDAPv3.
Use TLS – Use Transport Layer Security (SSL) to log in to the LDAP server. It is strongly recommended
that TLS be used to protected the username and password information that will be sent across the network.
Most modern implementations of LDAP server, including AD, support TLS. Deselecting this default setting will provide an alert which must be accepted to proceed.
Send LDAP ‘Start TLS’ Request – Some LDAP server implementations support the Start TLS directive
rather than using native LDAP over TLS. This allows the LDAP server to listen on one port (normally 389)
for LDAP connections, and to switch to TLS as directed by the client. AD does not use this option, and it
should only be selected if required by your LDAP server.
Require valid certificate from server – Validates the certificate presented by the server during the TLS
exchange, matching the name specified above to the name on the certificate. Deselecting this default option
will present an alert, but exchanges between the SonicWALL and the LDAP server will still use TLS – only
without issuance validation.
Local certificate for TLS – Optional, to be used only if the LDAP server requires a client certificate for connections. Useful for LDAP server implementations that return passwords to ensure the identity of the
LDAP client (AD does not return passwords). This setting is not required for AD.
If multiple LDAP/AD servers are to be used with referrals, then one should be chosen as the primary server
(probably the one that holds the bulk of the users) and the above settings should be set for that server. It will
then refer the SonicWALL on to the other servers for users in domains other than its own. For the SonicWALL
to be able to log in to those other servers, each server must have a user configured with the same credentials
(user name, password and location in the directory) as per the login to primary server. This may entail creating
a special user in the directory for the SonicWALL login. Note that only read access to the directory is required.
190
SonicWALL Global Management System Configuration Guide
Figure 171: LDAP Schema
• LDAP Schema – select ‘Microsoft Active Directory’, ‘RFC2798 inetOrgPerson’, or ‘user-defined’. Selecting either of the first two will automatically and immutably populate the User and User Group Object fields
with their correct values. Selecting ‘user-defined’ will allow you to specify your own values – use this only
if you have a specific or proprietary LDAP schema configuration.
• Framed IP address attribute – this attribute can be used to retrieve a static IP address that is assigned to a
user in the directory. Currently it is only used for a user connecting via L2TP with the SonicWALL’s L2TP
server.
Figure 172: User Directory Information
• Primary Domain – specify the user domain used by your LDAP implementation. For AD, this will be the
Active Directory domain name, e.g. yourADdomain.com. Changes to this field will, optionally, automatically update the tree information in the rest of the page.
• User tree for login to server – The tree in which the user specified in the ‘Settings’ tab resides. For example,
in AD the ‘administrator’ account’s default tree is the same as the user tree.
• Trees containing users – The trees where users commonly reside in the LDAP directory. One default value
is provided which can be edited, an up to a total of 64 DN values may be provided, and the SonicWALL
Configuring User Settings
191
•
search the directory using them all until a match is found, or the list is exhausted. If you have created other
user containers within your LDAP or AD directory, you should specify them here.
Trees containing user groups – Same as above, only with regard to user group containers, and a maximum
of 32 DN values may be provided. These are only applicable when there is no user group membership
attribute in the schema's user object, and are not used with AD.
All the above trees are normally given in URL format but can alternatively be specified as distinguished names
(e.g. “myDom.com/Sales/Users” could alternatively be given as the
DN “ou=Users,ou=Sales,dc=myDom,dc=com”).
Ordering is not critical, but since they are searched in the given order it is most efficient to place the most commonly used trees first in each list. If referrals between multiple LDAP servers are to be used, then the trees are
best ordered with those on the primary server first, and the rest in the same order that they will be referred.
Note that with AD, to locate the location of a user in the directory for the ‘User tree for login to server’ field,
the directory can be searched manually from the Active Directory Users and Settings control panel applet on
the server, or a directory search utility such as queryad.vbs in the Windows NT/2000/XP Resource Kit can be
run from any PC in the domain.
• Auto-configure – This causes the SonicWALL to auto-configure the ‘Trees containing users’ and ‘Trees
containing user groups’ fields by scanning through the directory/directories looking for all trees that contain user objects. The ‘User tree for login to server’ must first be set, and clicking the Auto-configure button
then brings up the following dialog:
Figure 173: Domain for Auto-configure
Select whether to append new located trees to the current configuration, or to start from scratch removing all
currently configured trees first, and then click OK. Note that it will quite likely locate trees that are not needed
for user login and some tidying up afterwards, manually removing such entries, is worth while.
If using multiple LDAP/AD servers with referrals, this process can be repeated for each, replacing the ‘Domain
to search’ accordingly and selecting ‘Append to existing trees’ on each subsequent run.
192
SonicWALL Global Management System Configuration Guide
Figure 174: LDAP Users
• Allow only users listed locally – Requires that LDAP users also be present in the SonicWALL local user
database for logins to be allowed.
• User group membership can be set locally by duplicating LDAP user names – Allows for group membership (and privileges) to be determined by the intersection of local user and LDAP user configurations.
• Default LDAP User Group – A default group on the SonicWALL to which LDAP users will belong in addition to group memberships configured on the LDAP server.
Group memberships (and privileges) can also be assigned simply with LDAP. By creating user groups on the
LDAP/AD server with the same name as SonicWALL built-in groups (such as ‘Guest Services’, ‘Content Filtering Bypass’, ‘Limited Administrators’) and assigning users to these groups in the directory, or creating user
groups on the SonicWALL with the same name as existing LDAP/AD user groups, SonicWALL group memberships will be granted upon successful LDAP authentication.
The SonicWALL can retrieve group memberships more efficiently in the case of Active Directory by taking
advantage of its unique trait of returning a ‘memberOf’ attribute for a user.
Figure 175: RADIUS to LDAP Relay Settings
The RADIUS to LDAP Relay feature is designed for use in a topology where there is a central site with an
LDAP/AD server and a central SonicWALL, with remote satellite sites connected into it via low-end SonicWALL security appliances that may not support LDAP. In that case the central SonicWALL can operate as a
Configuring User Settings
193
RADIUS server for the remote SonicWALLs, acting as a gateway between RADIUS and LDAP, and relaying
authentication requests from them to the LDAP server.
Additionally, for remote SonicWALLs running non-enhanced firmware, with this feature the central SonicWALL can return legacy user privilege information to them based on user group memberships learned via
LDAP. This avoids what can be very complex configuration of an external RADIUS server such as IAS for
those SonicWALLs.
Enable RADIUS to LDAP Relay – Enables this feature.
Allow RADIUS clients to connect via - Check the relevant checkboxes and policy rules will be added to
allow incoming Radius requests accordingly.
• RADIUS shared secret - This is a shared secret common to all remote SonicWALLs.
• User groups for legacy users – These define the user groups that correspond to the legacy ‘Access to
VPNs’, ‘Access from VPN client with XAUTH’, ‘Access from L2TP VPN client’ and ‘Allow Internet
access (when access is restricted)’ privileges respectively. When a user in one of the given user groups is
authenticated, the remote SonicWALL will be informed that the user is to be given the relevant privilege.
•
•
Figure 176: Test LDAP Settings
The ‘Test’ page allows for the configured LDAP settings to be tested by attempting authentication with specified user and password credentials. Any user group memberships and/or framed IP address configured on the
LDAP/AD server for the user will be displayed.
194
SonicWALL Global Management System Configuration Guide
Global User Settings
The settings listed below apply to all users when authenticated through the SonicWALL.
•
•
•
•
•
•
•
•
•
Inactivity timeout (minutes): users can be logged out of the SonicWALL after a preconfigured inactivity time.
Enter the number of minutes in this field. The default value is 5 minutes.
Enable login session limit: you can limit the time a user is logged into the SonicWALL by selecting the check
box and typing the amount of time, in minutes, in the Login session limit (minutes) field. The default value is
30 minutes.
Login page timeout (minutes): defines how much time a user has to log in before the login page times out. If
it times out, a message displays saying they must click before attempting to log in again.
Show user login status window with logout button: causes a status window to display with a Log Out button
during the user’s session. The user can click the Log Out button to log out of their session.
User's login status window refreshes every (minutes): determines how often the users’ status display is
updated.
Enable disconnected user detection: causes the SonicWALL to detect when a user’s connection is no longer
valid and end the session.
User's login status window sends heartbeat every (seconds): sets the frequency of the heartbeat signal used
to detect whether the user still has a valid connection
Timeout on heartbeat from user's login status window (minutes): sets the time needed without a reply from
the heartbeat before ending the user session.
Allow these HTTP URLs to bypass users authentication access rules: Define a list of URLs users can connect to without authenticating. To add a URL to the list:
a. Click Add below the URL list.
b. In the Enter URL window, enter the top level URL you are adding, for example, www.sonicwall.com.
All sub directories of that URL are included, such as
www.sonicwall.com/services/documentation.html. Click on OK to add the URL to the list.
Acceptable Use Policy
An acceptable use policy (AUP) is a policy users must agree to follow in order to access a network or the Internet.
It is common practice for many businesses and educational facilities to require that employees or students agree to
an acceptable use policy before accessing the network or Internet through the SonicWALL.
The Acceptable Use Policy section allows you to create the AUP message window for users. You can use HTML
formatting in the body of your message. Clicking the Example Template button creates a preformatted HTML
template for your AUP window.
Display on login from - select the network interface(s) you want to display the Acceptable Use Policy page
when users login. You can choose Trusted Zones, WAN Zone, Public Zones, Wireless Zones, and VPN Zone
in any combination.
• Window size (pixels) - allows you to specify the size of the AUP window defined in pixels. Checking the
Enable scroll bars on the window allows the user to scroll through the AUP window contents.
• Acceptable use policy page content - enter your Acceptable Use Policy text in the text box. You can include
HTML formatting. The page that is displayed to the user includes an I Accept button or Cancel button for user
confirmation. Click the Preview button to display your AUP message as it will appear for the user. The Example Template button creates a preformatted template for your AUP window.
•
Configuring User Settings
195
196
SonicWALL Global Management System Configuration Guide
CHAPTER 17
Configuring Virtual Private Networking
A Virtual Private Network (VPN) is a private data network that uses encryption technologies to operate over public
networks. Each node in a network can exchange data by establishing a VPN tunnel or a Security Association (SA)
with one or more other nodes. Once a tunnel is established, the SA uses encryption and authentication keys to
ensure data security and integrity.
A security key string is an encryption key that is used to encrypt and decrypt secure data. Both nodes must have the
key to exchange data. For example, the announcer of the Little Orphan Show used the same key to encode the secret
messages that the kids used to decode the messages.
Although an encrypted message cannot be read, it can be tampered with externally. Using an authentication key prevents external tampering. An authentication key is a hash function that is applied to the message content and is
checked by the message recipient to verify the message was not modified in transit.
In order to ensure message security, it is very important that the security and authentication keys are not discovered
by outside parties. Otherwise, the messages could be read in transit.
SonicWALL appliances can use the following methods to exchange security and authentication keys:
•
SonicWALL certificates—each SonicWALL appliance obtains a certificate from the SonicWALL Certificate
Authority (CA). Security and authentication keys are exchanged using public-key cryptography and authenticity of each node is verified by the SonicWALL CA.
After the SA expires, the SonicWALL appliances will reestablish an SA using the same public keys, but the
security and authentication keys will be different. If one set of security and authentication keys is compromised
by an outside party, that party will be unable to compromise the next set of keys.
•
Third-party certificates—the SonicWALL appliance and peer device obtain certificates from the third-party
certificate authorities. Security and authentication keys are exchanged using public-key cryptography and
authenticity of each node is verified by the third-party CA.
After the SA expires, the peers will reestablish an SA using the same public keys, but will not use the same
security and authentication keys.
•
Pre-shared secret—each SonicWALL appliance has a shared secret that is used to establish an SA.
After the SA expires, the SonicWALL appliances will reestablish an SA using the same public keys, but will not
use the same security and authentication keys.
•
Pre-exchanged security and authentication keys—keys are exchanged in advance.
The SA will always use the same encryption and authentication keys. If the keys are compromised by an outside party, they will remain compromised until the keys are changed.
Note: For an explanation of VPN terms, see “Basic Terms and Concepts” on page 224.
Note: Some SonicWALL appliances include VPN and others require a VPN upgrade that must be purchased separately. For example, the SonicWALL TELE2 includes VPN and the SonicWALL SOHO2 does not.
Configuring Virtual Private Networking
197
Configuring VPN
This chapter describes how to configure VPN version 1.0 for SonicOS Standard. To configure VPN for SonicOS
Enhanced, see Chapter 18, “Configuring Virtual Private Networking 2.0.”
To configure VPN for SonicWALL appliances using SonicOS Standard, follow these procedures:
•
•
•
•
•
Obtain and activate a VPN upgrade for each device—see Chapter 25, “Upgrading SonicWALL Appliances.”
Enable VPN for each SonicWALL appliance—see “Enabling VPN” on page 198.
Configure security associations—see “Configuring Security Associations” on page 200.
Configure Remote L2TP Connections—see “Configuring VPN to Receive L2TP Connections” on page 221.
Configure VPN Client License Sharing Groups—see “Creating License Sharing Groups” on page 319.
Note: To monitor VPN connections, see “Monitor VPN Connections” on page 222.
Enabling VPN
After applying a VPN upgrade, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the VPN tree and click Summary. The VPN Summary page appears (Figure 178).
Note: If VPN is already configured for the SonicWALL appliance, a list of current SAs appears.
The unique firewall identifier also appears.
4. Note the improved navigation for managing VPNs through use of page navigation arrows within the Current
IPSec Security Associations. To navigate through the pages, click on the navigation arrow buttons in the upper
right corner of the VPN Summary Page as shown in the figure here.
Figure 177: VPN Summary Page with Page Navigation Arrows for SAs
Page Navigation
Arrows
When managing VPNs, the VPN Summary Window sometimes can have too many VPNs listed for you to easily
find the VPN entry you want to view. To make VPN searching and viewing more easy, GMS now provides a pagination feature in the VPN Summary screen which breaks the list of VPNs into multiple pages. Each page can display up to 50 VPNs. To display the next page of VPNs, simply click the Next button. GMS displays the succeeding
page of the VPN Summary Window.
198
SonicWALL Global Management System Configuration Guide
Figure 178: VPN Summary Page
5. Select the Enable VPN check box.
6. To enable remote VPN access to the SonicWALL appliance through VPN Software Clients, select the Enable
GroupVPN check box.
7. To disable all NetBIOS broadcasts, select the Disable all VPN Windows Networking (NetBIOS) broadcast
check box.
8. To improve interoperability with other VPN gateways and applications that use a large data packet size, select
the Enable Fragmented Packet Handling check box. Packet fragmentation overburdens a network router by
resending data packets and causes network traffic to slow down between networks.
The Enable Fragmented Packet Handling option configures the SonicWALL appliance to listen to the intermediate router and, if necessary, send Internet Control Message Protocol (ICMP) messages to the router to
decrease the size of the data packets. Enabling this option is recommended if the VPN tunnel logs contain many
“Fragmented IPSec packets dropped” messages.
9. To ignore Don’t Fragment (DF) bits from routers connected to the SonicWALL appliance, select the Ignore DF
Bit check box.
10. NAT Traversal is an Internet Engineering Task Force (IETF) draft standard that wraps an IPsec packet into a
UDP/IP header, allowing NAT devices to change IP addresses without affecting the integrity of the IPsec
packet. To enable NAT traversal, select the Enable NAT Traversal check box.
11. To enable detection of a dead peer, select the Enable IKE Dead peer detection. Then, specify how often the
SonicWALL appliance attempt to detect a peer in the Dead peer detection Interval field and specify the number of failed attempts that must occur before closing the VPN tunnel in the Failure Trigger Level field.
12. SonicWALL appliances can manage outbound traffic using bandwidth management. To enable bandwidth management for VPN tunnels, select the Enable Bandwidth Management check box.
Enter the amount of bandwidth that will always be available to VPN tunnels in the VPN Guaranteed Bandwidth field. Keep in mind that this bandwidth will be permanently assigned to VPN services and not available
to other services, regardless of the amount of bandwidth that VPN uses.
Enter the maximum amount of bandwidth that will be available for VPN services in the VPN Maximum Bandwidth field.
Select the priority of VPN services in relation to other services from the VPN Bandwidth Priority list box.
Select a priority from 0 (highest) to 7 (lowest).
Note: In order to configure bandwidth management, bandwidth management must be enabled on the
SonicWALL appliance. For more information, see “Configuring Ethernet Settings” on page 119.
Configuring Virtual Private Networking
199
13. VPN Clients use RCF files to import data used to communicate with SonicWALL appliances. To send an RCF
File to an email address, enter the following information:
• Enter the email address in the Email Address field.
• Enter and reenter the RCF File password in the RCF File Export Password and Confirm Password
fields.
• Select whether the file will be used for WAN or wireless connections.
• Select from the following:
• To email the file, click Email RCF File.
• To email the file with the Global VPN Client software, click Email RCF File and Global VPN Client.
14. When you are finished, click Update. To clear all screen settings and start over, click Reset.
Configuring Security Associations
SonicWALL GMS supports several methods for establishing and maintaining security associations (SAs). These
include:
• Internet Key Exchange (IKE) using SonicWALL certificates. See “Internet Key Exchange Using SonicWALL
Certificates” on page 200.
• IKE using third-party certificates. See “Internet Key Exchange Using Third-Party Certificates” on page 206.
• IKE using a pre-shared secret. See “Internet Key Exchange Using Pre-Shared Secret” on page 212.
• Manual keying. See “Manual Keying” on page 217.
Internet Key Exchange Using SonicWALL Certificates
Note: This section assumes that you are familiar with Public Key Infrastructure (PKI) and the implementation of
digital certificates with VPN.
A digital certificate is an electronic means to verify identity by using a trusted third party known as a Certificate
Authority (CA). SonicWALL certificates are the easiest certificate solution for establishing the identity of peer
VPN devices and users.
Internet Key Exchange (IKE) is an important part of IPSec VPN solutions, and it can use digital signatures to
authenticate peer devices before setting up security associations. Without digital signatures, VPN users must
authenticate by manually exchanging shared secrets or symmetric keys. Devices using digital signatures do not
require configuration changes every time a new device is added to the network.
Note: Although SAs can be established with most IPSec-compliant devices, SonicWALL Certificates can only be
used between SonicWALL appliances.
This section describes how to establish SAs between SonicWALL appliances that are managed by
SonicWALL GMS and SonicWALL appliances that are not managed by SonicWALL GMS.
Note: Before establishing SAs using SonicWALL certificates, you must obtain a Public Key Infrastructure (PKI)
administrator certificate and apply it to each SonicWALL appliance. For more information, see Chapter 25,
“Upgrading SonicWALL Appliances.”
When All Appliances are Managed by SonicWALL GMS
To enable VPN using certificates, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the VPN tree and click Configure. The VPN Configure page appears (Figure 179).
200
SonicWALL Global Management System Configuration Guide
Figure 179: VPN Configure Page
4. Select the Use Interconnected Mode check box.
5. Select IKE using SonicWALL Certificates.
6. Select from the following:
• To add a new SA, select Add a new Security Association.
• To delete an existing SA, select Delete an existing Security Association.
• To edit an existing SA, select Modify an existing Security Association.
7. Click Select Destination.
A dialog box that contains all SonicWALL appliances managed by this SonicWALL GMS appears.
8. Select the SonicWALL appliance or group to which you will establish SAs and click the Select button. The
name of the target appears in the Target SonicWALL Group/Node field.
9. Aggressive mode improves the performance of IKE SA negotiation by only requiring three packet exchanges.
However, it provides no identity protection. To enable aggressive mode, select Aggressive Mode from the
Exchange list box. Otherwise, select Main Mode.
10. Select the Diffie-Hellman (DH) group that will be used when the VPN devices are negotiating encryption and
authentication keys from the Phase 1 DH Group list box.
Note: Group 1 specifies a 768-bit Diffie-Hellman value, Group 2 specifies a more secure 1024-bit Diffie-Hellman value, and Group 5 specifies the currently most secure 1536-bit Diffie-Hellman value.
11. Select the Diffie-Hellman group that will be used when the VPN devices have established an SA from the
Phase 2 DH Group list box.
12. Select the type of encryption and authentication keys used when the VPN devices are negotiating encryption
and authentication keys from the Phase 1 Encryption/Authentication list box.
13. Select the type of encryption and authentication keys used for the SAs from the Phase 2 Encryption/Authentication list box.
14. To specify the default LAN (WorkPort) gateway, enter the IP address of the gateway in the Default LAN
(WorkPort) Gateway field.
A Default LAN (WorkPort) Gateway is used at a central site in conjunction with a remote site using the Route
all Internet traffic through this destination unit check box. The Default LAN (WorkPort) Gateway field
allows the network administrator to specify the IP address of the default LAN route for incoming Internet Protocol Security (IPSec) packets for this SA.
Configuring Virtual Private Networking
201
Incoming packets are decoded by the SonicWALL and compared to static routes configured in the
SonicWALL. Since packets can have any IP address destination, it is impossible to configure enough static
routes to handle the traffic. For packets received via an IPSec tunnel, the SonicWALL looks up a route for the
LAN (WorkPort). If no route is found, the SonicWALL checks for a Default LAN Gateway. If a Default LAN
Gateway is detected, the packet is routed through the gateway. Otherwise, the packet is dropped.
15. To specify how long the tunnel is active before being renegotiated, enter a value in the SA Lifetime field. We
recommend a value of 28,800 seconds (8 hours).
16. To prevent repeated compromises of the same security key when reestablishing a tunnel, select the Enable Perfect Forward Secrecy check box.
17. To configure the VPN tunnel to remain open as long as there is network traffic on the SA, select the Enable
Keep Alive check box.
18. To configure the SonicWALL appliance to establish the VPN tunnel before users generate any VPN traffic,
select the Try to bring up all possible SAs check box.
19. To enable NetBIOS broadcasts across the SA, select the Enable Windows Networking Broadcast check box.
20. To allow the remote VPN tunnel to be included in the routing table, select the Forward Packets to Remote
VPNs check box.
Normally, inbound traffic is decrypted and only forwarded to the local LAN (WorkPort) or a manually specified
route (see “Configuring Routes” on page 113). This option enables you to create a “hub and spoke” network
configuration where all traffic is routed among branch offices via the corporate office.
Note: To create a “hub and spoke” network, make sure to select the Forward Packets to Remote VPNs check
box for each SA.
21. To force all network traffic to the WAN through a VPN to a central site, select the Route all Internet traffic
through destination unit check box.
When this option is selected, all traffic that is not destined for another SA is forwarded through this VPN tunnel. If this option is not specified and the destination does not match any SA, the packet is forwarded unencrypted to the WAN.
Note: Only one SA can have this option enabled.
22. Select one the following VPN termination options:
To configure the VPN tunnel to terminate at the LAN or WorkPort, select LAN (WorkPort). Users on the
other side of the SA will be able to access the LAN, but not the DMZ (HomePort).
• To configure the VPN tunnel to terminate at the DMZ or HomePort, select DMZ (HomePort). Users on the
other side of the SA will be able to access the DMZ, but not the LAN (WorkPort).
• To allow users on the other side of the SA to access both the LAN and DMZ, select LAN/DMZ or WorkPort/HomePort.
•
23. Select from the following NAT and Firewall Rules:
To disable NAT and not apply firewall rules to traffic coming through this SA, select Disabled.
To enable NAT and firewall rules for the selected SonicWALL appliance, select Source. If NAT is enabled,
all traffic originating from this appliance will appear to originate from a single IP address and network firewall rules will be applied to all traffic on this SA.
• To enable NAT and firewall rules for the selected SonicWALL appliance and its peer, select Source and
Destination. If NAT is enabled, all traffic originating from this appliance will appear to originate from a
single IP address and all traffic originating from its peer will appear to originate from a single IP address.
Network firewall rules will be applied to all traffic on this SA.
•
•
Note: Applying firewall rules can dramatically affect services that run between the networks. For more information, see Chapter 11, “Configuring Firewall Settings.”
24. Select how local users are authenticated:
• To disable authentication for local users, select Disabled.
• To configure local users to be authenticated locally, either through the SonicWALL device or the RADIUS
server, select Source.
• To configure local users to be authenticated on the destination network, either through the SonicWALL
device or the RADIUS server, select Destination.
• To authenticate local users both locally and on the destination network, select Source and Destination.
202
SonicWALL Global Management System Configuration Guide
25. Select how remote users are authenticated:
• To disable authentication for remote users, select Disabled.
• To configure remote users to be authenticated locally, either through the SonicWALL device or the
RADIUS server, select Source.
• To configure remote users to be authenticated on the destination network, either through the SonicWALL
device or the RADIUS server, select Destination.
• To authenticate remote users both locally and on the destination network, select Source and Destination.
26. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
Note: To disable this SA, select the Disable this SA check box and click Update.
When One Appliance Is Not Managed by SonicWALL GMS
Although SAs can be established with most Internet Protocol Security (IPSec)-compliant devices, Certificates can
only be used between SonicWALL appliances.
This section describes how to establish SonicWALL certificate-based SAs between SonicWALL appliances that are
managed by SonicWALL GMS and SonicWALL appliances that are not managed by SonicWALL GMS.
To create SAs using certificates, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the VPN tree and click Configure. The VPN Configure page appears (Figure 180).
Figure 180: VPN Configure Page
4. Deselect the Use Interconnected Mode check box.
5. Select IKE using SonicWALL Certificates.
6. Select from the following:
• To add a new SA, select Add a new Security Association.
• To delete an existing SA, select Delete an existing Security Association.
• To edit an existing SA, select Modify an existing Security Association.
7. Enter the name of the remote firewall/VPN gateway in the Security Association Name field. This name must
match exactly if the device has a dynamic IP address.
Configuring Virtual Private Networking
203
8. Enter the IP address of the remote firewall/VPN gateway in the IPSec Gateway Address field. This address
must be valid and will be the public IP address if the remote LAN has NAT enabled. If the remote VPN gateway has a dynamic IP address, this field can be left blank if the name matches.
9. To specify how long the tunnel is active before being renegotiated, enter a value in the SA Lifetime field. We
recommend a value of 28,800 seconds (8 hours).
10. To specify the default LAN (WorkPort) gateway, enter the IP address of the gateway in the Default LAN
(WorkPort) Gateway field.
A Default LAN (WorkPort) Gateway is used at a central site in conjunction with a remote site using the Route
all internet traffic through destination unit check box. The Default LAN (WorkPort) Gateway field allows
the network administrator to specify the IP address of the default LAN route for incoming IPSec packets for
this SA.
Incoming packets are decoded by the SonicWALL and compared to static routes configured in the
SonicWALL. Since packets can have any IP address destination, it is impossible to configure enough static
routes to handle the traffic. For packets received via an IPSec tunnel, the SonicWALL looks up a route for the
LAN. If no route is found, the SonicWALL checks for a Default LAN Gateway. If a Default LAN Gateway is
detected, the packet is routed through the gateway. Otherwise, the packet is dropped.
11. To prevent repeated compromises of the same security key when reestablishing a tunnel, select the Enable Perfect Forward Secrecy check box.
12. To enable NetBIOS broadcasts across the SA, select the Enable Windows Networking Broadcast check box.
13. To apply NAT and firewall rules to all traffic coming through this SA, select the Apply NAT and firewall rules
check box.
This feature is useful for hiding the LAN subnet from the corporate site. All traffic will appear to originate from
a single IP address.
14. To allow the remote VPN tunnel to be included in the routing table, select the Forward Packets to Remote
VPNs check box.
This will enable the SonicWALL appliance to receive VPN traffic, decrypt it, and forward it to another VPN
tunnel. This feature can be used to create a “hub and spoke” network configuration by routing traffic among
SAs. To do this, make sure to enable this option for all SAs.
15. To configure the VPN tunnel to remain open as long as there is network traffic on the SA, select the Enable
Keep Alive check box.
16. To configure the SonicWALL appliance to establish the VPN tunnel before users generate any VPN traffic,
select the Try to bring up all possible SAs check box.
17. To require local users to authenticate locally before accessing the SA, select the Require authentication of
local users check box.
18. To require remote users to authenticate with this SonicWALL appliance or the local RADIUS server before
accessing resources, select the Require authentication of remote users check box.
19. Enter the serial number of the target SonicWALL appliance in the Peer SonicWALL Serial # field.
20. Aggressive mode improves the performance of IKE SA negotiation by only requiring three packet exchanges.
However, it provides no identity protection. To enable aggressive mode, select Aggressive Mode from the
Exchange list box. Otherwise, select Main Mode.
21. Select the Diffie-Hellman group that will be used when the VPN devices are negotiating encryption and authentication keys from the Phase 1 DH Group list box.
Note: Group 1 specifies a 768-bit Diffie-Hellman value, Group 2 specifies a more secure 1024-bit DiffieHellman value, and Group 5 specifies the currently most secure 1536-bit Diffie-Hellman value.
22. Select the Diffie-Hellman group that will be used when the VPN devices have established an SA from the
Phase 2 DH Group list box.
23. Select the type of encryption and authentication keys used when the VPN devices are negotiating encryption
and authentication keys from the Phase 1 Encryption/Authentication list box.
24. Select the type of encryption and authentication keys used for the SAs from the Phase 2 Encryption/Authentication list box.
204
SonicWALL Global Management System Configuration Guide
25. Select from the following:
To allow this SA to be used as the default route for all Internet traffic, select Use this SA as default route
for all Internet traffic.
• If the destination network will receive its IP addresses on this network using DHCP, select Destination network obtains IP addresses using DHCP.
• To specify destination networks, select Specify destination networks below. Then, click Modify and enter
the destination network IP addresses and subnet masks.
•
26. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
Note: To disable this SA without deleting it, select the Disable this SA check box and click Update.
Configuring Virtual Private Networking
205
Internet Key Exchange Using Third-Party Certificates
Note: This section assumes that you are familiar with Public Key Infrastructure (PKI) and the implementation of
digital certificates with VPN.
A digital certificate is an electronic means to verify identity by using a trusted third party known as a Certificate
Authority (CA). SonicWALL now supports third party certificates in addition to the existing Authentication Service. The difference between third party certificates and the SonicWALL Authentication Service is the ability to
select the source for your CA certificate. Using Certificate Authority Certificates and Local Certificates is a more
manual process than using the SonicWALL Authentication Service; therefore, experience with implementing Public Key Infrastructure (PKI) is necessary to understand the key components of digital certificates.
Internet Key Exchange (IKE) is an important part of IPSec VPN solutions, and it can use digital signatures to
authenticate peer devices before setting up security associations. Without digital signatures, VPN users must
authenticate by manually exchanging shared secrets or symmetric keys. Devices using digital signatures do not
require configuration changes every time a new device is added to the network.
SonicWALL has implemented X.509v3 as its certificate form and CRLv2 for its certificate revocation list.
SonicWALL supports the following two vendors of Certificate Authority Certificates:
• VeriSign
• Entrust
Obtaining a Certificate
To obtain a certificate, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the VPN tree and click Local Certs. The Local Certs page appears (Figure 181).
Figure 181: Local Certs Page
4. Complete the information in the Generate Certificate Request section and click Generate Request.
The request appears in the Current Certificate Requests section.
5. Click Export.
You are prompted to save the file. It will be saved in the PKCS 10 format.
6. Obtain a certificate from one of the approved certificate authorities using the PKCS 10 file.
206
SonicWALL Global Management System Configuration Guide
7. After you receive the certificate file, locate and import the file by clicking Browse in the Import Certificate
With Private Key section. Then click Import.
The certificate will appear in the Current Local Certificates section.
Note: After you have obtained certificates for both devices, continue to “When All Appliances are Managed by
SonicWALL GMS” on page 207 or “When One Appliance Is Not Managed by SonicWALL GMS” on page 209.
When All Appliances are Managed by SonicWALL GMS
Setting up a VPN tunnel between appliances requires you to configure several parameters on both appliances.
When setting up VPN tunnels between SonicWALL appliances managed by SonicWALL GMS, all selected appliances are automatically configured based on the settings that you entered.
To enable VPN using third-party certificates when both devices are managed by SonicWALL GMS, follow these
steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the VPN tree and click Configure. The VPN Configure page appears (Figure 179).
Figure 182: VPN Configure Page
4. Select the Use Interconnected Mode check box.
5. Select IKE using 3rd Party Certificates.
6. Select from the following:
• To add a new SA, select Add a new Security Association.
• To delete an existing SA, select Delete an existing Security Association.
• To edit an existing SA, select Modify an existing Security Association.
7. Click Select Destination.
A dialog box that contains all SonicWALL appliances managed by this SonicWALL GMS appears.
8. Select the SonicWALL appliance or group to which you will establish SAs and click the Select button. The
name of the target appears in the Target SonicWALL Group/Node field.
9. Aggressive mode improves the performance of IKE SA negotiation by only requiring three packet exchanges.
However, it provides no identity protection. To enable aggressive mode, select Aggressive Mode from the
Exchange list box. Otherwise, select Main Mode.
Configuring Virtual Private Networking
207
10. Select the Diffie-Hellman (DH) group that will be used when the VPN devices are negotiating encryption and
authentication keys from the Phase 1 DH Group list box.
Note: Group 1 specifies a 768-bit Diffie-Hellman value, Group 2 specifies a more secure 1024-bit Diffie-Hellman value, and Group 5 specifies the currently most secure 1536-bit Diffie-Hellman value.
11. Select the Diffie-Hellman group that will be used when the VPN devices have established an SA from the
Phase 2 DH Group list box.
12. Select the type of encryption and authentication keys used when the VPN devices are negotiating encryption
and authentication keys from the Phase 1 Encryption/Authentication list box.
13. Select the type of encryption and authentication keys used for the SAs from the Phase 2 Encryption/Authentication list box.
14. To specify the default LAN (WorkPort) gateway, enter the IP address of the gateway in the Default LAN
(WorkPort) Gateway field.
A Default LAN (WorkPort) Gateway is used at a central site in conjunction with a remote site using the Route
all Internet traffic through this destination unit check box. The Default LAN (WorkPort) Gateway field
allows the network administrator to specify the IP address of the default LAN route for incoming Internet Protocol Security (IPSec) packets for this SA.
Incoming packets are decoded by the SonicWALL and compared to static routes configured in the
SonicWALL. Since packets can have any IP address destination, it is impossible to configure enough static
routes to handle the traffic. For packets received via an IPSec tunnel, the SonicWALL looks up a route for the
LAN. If no route is found, the SonicWALL checks for a Default LAN Gateway. If a Default LAN Gateway is
detected, the packet is routed through the gateway. Otherwise, the packet is dropped.
15. To specify how long the tunnel is active before being renegotiated, enter a value in the SA Lifetime field. We
recommend a value of 28,800 seconds (8 hours).
16. To prevent repeated compromises of the same security key when reestablishing a tunnel, select the Enable Perfect Forward Secrecy check box.
17. To configure the VPN tunnel to remain open as long as there is network traffic on the SA, select the Enable
Keep Alive check box.
18. To configure the SonicWALL appliance to establish the VPN tunnel before users generate any VPN traffic,
select the Try to bring up all possible SAs check box.
19. To enable NetBIOS broadcasts across the SA, select the Enable Windows Networking Broadcast check box.
20. To allow the remote VPN tunnel to be included in the routing table, select the Forward Packets to Remote
VPNs check box.
Normally, inbound traffic is decrypted and only forwarded to the local LAN (WorkPort) or a manually specified
route (see “Configuring Routes” on page 113). This option enables you to create a “hub and spoke” network
configuration where all traffic is routed among branch offices via the corporate office.
Note: To create a “hub and spoke” network, make sure to select the Forward Packets to Remote VPNs check
box for each SA.
21. To force all network traffic to the WAN through a VPN to a central site, select the Route all Internet traffic
through destination unit check box.
When this option is selected, all traffic that is not destined for another SA is forwarded through this VPN tunnel. If this option is not specified and the destination does not match any SA, the packet is forwarded unencrypted to the WAN.
Note: Only one SA can have this option enabled.
22. Select one the following VPN termination options:
To configure the VPN tunnel to terminate at the LAN or WorkPort, select LAN (WorkPort). Users on the
other side of the SA will be able to access the LAN, but not the DMZ (HomePort).
• To configure the VPN tunnel to terminate at the DMZ or HomePort, select DMZ (HomePort). Users on the
other side of the SA will be able to access the DMZ, but not the LAN (WorkPort).
• To allow users on the other side of the SA to access both the LAN and DMZ, select LAN/DMZ or WorkPort/HomePort.
•
208
SonicWALL Global Management System Configuration Guide
23. Select from the following NAT and Firewall Rules:
To disable NAT and not apply firewall rules to traffic coming through this SA, select Disabled.
To enable NAT and firewall rules for the selected SonicWALL appliance, select Source. If NAT is enabled,
all traffic originating from this appliance will appear to originate from a single IP address and network firewall rules will be applied to all traffic on this SA.
• To enable NAT and firewall rules for the selected SonicWALL appliance and its peer, select Source and
Destination. If NAT is enabled, all traffic originating from this appliance will appear to originate from a
single IP address and all traffic originating from its peer will appear to originate from a single IP address.
Network firewall rules will be applied to all traffic on this SA.
•
•
Note: Applying firewall rules can dramatically affect services that run between the networks. For more information, see Chapter 11, “Configuring Firewall Settings.”
24. Select how local users are authenticated:
To disable authentication for local users, select Disabled.
To configure local users to be authenticated locally, either through the SonicWALL device or the RADIUS
server, select Source.
• To configure local users to be authenticated on the destination network, either through the SonicWALL
device or the RADIUS server, select Destination.
• To authenticate local users both locally and on the destination network, select Source and Destination.
•
•
25. Select how remote users are authenticated:
• To disable authentication for remote users, select Disabled.
• To configure remote users to be authenticated locally, either through the SonicWALL device or the
RADIUS server, select Source.
• To configure remote users to be authenticated on the destination network, either through the SonicWALL
device or the RADIUS server, select Destination.
• To authenticate remote users both locally and on the destination network, select Source and Destination.
26. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
Note: To disable this SA, select the Disable this SA check box and click Update.
When One Appliance Is Not Managed by SonicWALL GMS
This section describes how to configure VPN when the target appliance is not managed by SonicWALL GMS.
To create SAs using third-party certificates, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the VPN tree and click Configure. The VPN Configure page appears (Figure 180).
Configuring Virtual Private Networking
209
Figure 183: VPN Configure Page
4. Deselect the Use Interconnected Mode check box.
5. Select IKE using 3rd Party Certificates.
6. Select from the following:
• To add a new SA, select Add a new Security Association.
• To delete an existing SA, select Delete an existing Security Association.
• To edit an existing SA, select Modify an existing Security Association.
7. Enter the name of the remote firewall/VPN gateway in the Security Association Name field. This name must
match exactly if the device has a dynamic IP address.
8. Select the certificate to use from the Select Certificate list box.
9. Enter the IP address of the remote firewall/VPN gateway in the IPSec Gateway Address field. This address
must be valid and will be the public IP address if the remote LAN has NAT enabled. If the remote VPN gateway has a dynamic IP address, this field can be left blank if the name matches.
10. To specify how long the tunnel is active before being renegotiated, enter a value in the SA Lifetime field. We
recommend a value of 28,800 seconds (8 hours).
11. To specify the default LAN (WorkPort) gateway, enter the IP address of the gateway in the Default LAN
(WorkPort) Gateway field.
A Default LAN (WorkPort) Gateway is used at a central site in conjunction with a remote site using the Route
all internet traffic through destination unit check box. The Default LAN (WorkPort) Gateway field allows
the network administrator to specify the IP address of the default LAN route for incoming IPSec packets for
this SA.
Incoming packets are decoded by the SonicWALL and compared to static routes configured in the
SonicWALL. Since packets can have any IP address destination, it is impossible to configure enough static
routes to handle the traffic. For packets received via an IPSec tunnel, the SonicWALL looks up a route for the
LAN. If no route is found, the SonicWALL checks for a Default LAN Gateway. If a Default LAN Gateway is
detected, the packet is routed through the gateway. Otherwise, the packet is dropped.
12. To prevent repeated compromises of the same security key when reestablishing a tunnel, select the Enable Perfect Forward Secrecy check box.
13. To enable NetBIOS broadcasts across the SA, select the Enable Windows Networking Broadcast check box.
14. To apply NAT and firewall rules to all traffic coming through this SA, select the Apply NAT and firewall rules
check box.
210
SonicWALL Global Management System Configuration Guide
This feature is useful for hiding the LAN subnet from the corporate site. All traffic will appear to originate from
a single IP address.
15. To allow the remote VPN tunnel to be included in the routing table, select the Forward Packets to Remote
VPNs check box.
This will enable the SonicWALL appliance to receive VPN traffic, decrypt it, and forward it to another VPN
tunnel.This feature can be used to create a “hub and spoke” network configuration by routing traffic among
SAs. To do this, make sure to enable this option for all SAs.
16. To configure the VPN tunnel to remain open as long as there is network traffic on the SA, select the Enable
Keep Alive check box.
17. To configure the SonicWALL appliance to establish the VPN tunnel before users generate any VPN traffic,
select the Try to bring up all possible SAs check box.
18. To require local users to authenticate locally before accessing the SA, select the Require authentication of
local users check box.
19. To require remote users to authenticate with this SonicWALL appliance or the local RADIUS server before
accessing resources, select the Require authentication of remote users check box.
20. Select one the following VPN termination options:
To configure the VPN tunnel to terminate at the LAN or WorkPort, select LAN (WorkPort). Users on the
other side of the SA will be able to access the LAN, but not the DMZ (HomePort).
• To configure the VPN tunnel to terminate at the DMZ or HomePort, select DMZ (HomePort). Users on the
other side of the SA will be able to access the DMZ, but not the LAN (WorkPort).
• To allow users on the other side of the SA to access both the LAN and DMZ, select LAN/DMZ or WorkPort/HomePort.
•
21. Aggressive mode improves the performance of IKE SA negotiation by only requiring three packet exchanges.
However, it provides no identity protection. To enable aggressive mode, select Aggressive Mode from the
Exchange list box. Otherwise, select Main Mode.
22. Select the Diffie-Hellman group that will be used when the VPN devices are negotiating encryption and authentication keys from the Phase 1 DH Group list box.
Note: Group 1 specifies a 768-bit Diffie-Hellman value, Group 2 specifies a more secure 1024-bit DiffieHellman value, and Group 5 specifies the currently most secure 1536-bit Diffie-Hellman value.
23. Select the Diffie-Hellman group that will be used when the VPN devices have established an SA from the
Phase 2 DH Group list box.
24. Select the type of encryption and authentication keys used when the VPN devices are negotiating encryption
and authentication keys from the Phase 1 Encryption/Authentication list box.
25. Select the type of encryption and authentication keys used for the SAs from the Phase 2 Encryption/Authentication list box.
26. Select whether the peer device uses a distinguished name, e-mail ID, or domain name as its certificate ID from
the Peer Certificate’s ID list box.
27. Enter the peer device’s certificate ID in the Peer Certificate’s ID field.
28. Select from the following:
To allow this SA to be used as the default route for all Internet traffic, select Use this SA as default route
for all Internet traffic.
• If the destination network will receive its IP addresses on this network using DHCP, select Destination network obtains IP addresses using DHCP.
• To specify destination networks, select Specify destination networks below. Then, click Modify and enter
the destination network IP addresses and subnet masks.
•
29. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
Note: To disable this SA without deleting it, select the Disable this SA check box and click Update.
Configuring Virtual Private Networking
211
Internet Key Exchange Using Pre-Shared Secret
When using IKE with a pre-shared secret, two VPN devices establish encryption and authentication keys using a
shared secret. After the SA expires, the SonicWALL appliances will reestablish an SA using the same shared secret,
but will not use the same security and authentication keys.
When All Appliances are Managed by SonicWALL GMS
Setting up a VPN tunnel between appliances requires you to configure several parameters on both appliances.
When setting up VPN tunnels between SonicWALL appliances managed by SonicWALL GMS, all selected appliances are automatically configured based on the settings that you entered.
To configure an SA using IKE with pre-shared secrets, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the VPN tree and click Configure. The VPN Configure page appears (Figure 184).
Figure 184: VPN Configure Page
4. Select the Use Interconnected Mode check box.
5. Select IKE using Pre-shared Secret.
6. Select from the following:
• To add a new SA, select Add a new Security Association.
• To delete an existing SA, select Delete an existing Security Association.
• To edit an existing SA, select Modify an existing Security Association.
7. Click Select Destination.
A dialog box that contains all SonicWALL appliances managed by this SonicWALL GMS appears.
8. Select the SonicWALL appliance or group to which you will establish SAs and click the Select button. The
name of the target appears in the Target SonicWALL Group/Node field.
9. Aggressive mode improves the performance of IKE SA negotiation by only requiring three packet exchanges.
However, it provides no identity protection. To enable aggressive mode, select Aggressive Mode from the
Exchange list box. Otherwise, select Main Mode.
10. Select the Diffie-Hellman group that will be used when the VPN devices are negotiating encryption and authentication keys from the Phase 1 DH Group list box.
212
SonicWALL Global Management System Configuration Guide
Note: Group 1 specifies a 768-bit Diffie-Hellman value, Group 2 specifies a more secure 1024-bit DiffieHellman value, and Group 5 specifies the currently most secure 1536-bit Diffie-Hellman value.
11. Select the Diffie-Hellman group that will be used when the VPN devices have established an SA from the
Phase 2 DH Group list box.
12. Select the type of encryption and authentication keys used when the VPN devices are negotiating encryption
and authentication keys from the Phase 1 Encryption/Authentication list box.
13. Select the type of encryption and authentication keys used for the SAs from the Phase 2 Encryption/Authentication list box.
14. To specify the default LAN (WorkPort) gateway, enter the IP address of the gateway in the Default LAN
(WorkPort) Gateway field.
A Default LAN (WorkPort) Gateway is used at a central site in conjunction with a remote site using the Route
all internet traffic through destination unit check box. The Default LAN (WorkPort) Gateway field allows
the network administrator to specify the IP address of the default LAN route for incoming IPSec packets for
this SA.
Incoming packets are decoded by the SonicWALL and compared to static routes configured in the
SonicWALL. Since packets can have any IP address destination, it is impossible to configure enough static
routes to handle the traffic. For packets received via an IPSec tunnel, the SonicWALL looks up a route for the
LAN. If no route is found, the SonicWALL checks for a Default LAN Gateway. If a Default LAN Gateway is
detected, the packet is routed through the gateway. Otherwise, the packet is dropped.
15. To specify how long the tunnel is active before being renegotiated, enter a value in the SA Lifetime field. We
recommend a value of 28,800 seconds (8 hours).
16. To prevent repeated compromises of the same security key when reestablishing a tunnel, select the Enable Perfect Forward Secrecy check box.
17. To configure the VPN tunnel to remain open as long as there is network traffic on the SA, select the Enable
Keep Alive check box.
18. To configure the SonicWALL appliance to establish the VPN tunnel before users generate any VPN traffic,
select the Try to bring up all possible SAs check box.
19. To enable NetBIOS broadcasts across the SA, select the Enable Windows Networking Broadcast check box.
20. To allow the remote VPN tunnel to be included in the routing table, select the Forward Packets to Remote
VPNs check box.
Normally, inbound traffic is decrypted and only forwarded to the local LAN or a manually specified route (see
“Configuring Routes” on page 113). This option enables you to create a “hub and spoke” network configuration
where all traffic is routed among branch offices via the corporate office.
Note: To create a “hub and spoke” network, make sure to select the Forward Packets to Remote VPNs check
box for each SA.
21. To force all network traffic to the WAN through a VPN to a central site, select the Route all internet traffic
through destination unit check box.
When this option is selected, all traffic that is not destined for another SA is forwarded through this VPN tunnel. If this option is not specified and the destination does not match any SA, the packet is forwarded unencrypted to the WAN.
Note: Only one SA can have this option enabled.
22. Select one the following VPN termination options:
• To configure the VPN tunnel to terminate at the LAN or WorkPort, select LAN (WorkPort). Users on the
other side of the SA will be able to access the LAN, but not the DMZ (HomePort).
• To configure the VPN tunnel to terminate at the DMZ or HomePort, select DMZ (HomePort). Users on the
other side of the SA will be able to access the DMZ, but not the LAN (WorkPort).
• To allow users on the other side of the SA to access both the LAN and DMZ, select LAN/DMZ or WorkPort/HomePort.
Configuring Virtual Private Networking
213
23. Select from the following NAT and Firewall Rules:
• To disable NAT and not apply firewall rules to traffic coming through this SA, select Disabled.
• To enable NAT and firewall rules for the selected SonicWALL appliance, select Source. If NAT is enabled,
all traffic originating from this appliance will appear to originate from a single IP address and network firewall rules will be applied to all traffic on this SA.
• To enable NAT and firewall rules for the selected SonicWALL appliance and its peer, select Source and
Destination. If NAT is enabled, all traffic originating from this appliance will appear to originate from a
single IP address and all traffic originating from its peer will appear to originate from a single IP address.
Network firewall rules will be applied to all traffic on this SA.
Note: Applying firewall rules can dramatically affect services that run between the networks. For more information, see Chapter 11, “Configuring Firewall Settings.”
24. Select how local users are authenticated:
• To disable authentication for local users, select Disabled.
• To configure local users to be authenticated locally, either through the SonicWALL device or the RADIUS
server, select Source.
• To configure local users to be authenticated on the destination network, either through the SonicWALL
device or the RADIUS server, select Destination.
• To authenticate local users both locally and on the destination network, select Source and Destination.
25. Select how remote users are authenticated:
• To disable authentication for remote users, select Disabled.
• To configure remote users to be authenticated locally, either through the SonicWALL device or the
RADIUS server, select Source.
• To configure remote users to be authenticated on the destination network, either through the SonicWALL
device or the RADIUS server, select Destination.
• To authenticate remote users both locally and on the destination network, select Source and Destination.
26. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
Note: To disable this SA, select the Disable this SA check box and click Update.
When One Appliance Is Not Managed by SonicWALL GMS
This section describes how to configure VPN when the target appliance is not managed by SonicWALL GMS.
To enable VPN using IKE with a pre-shared secret, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the VPN tree and click Configure. The VPN Configure page appears (Figure 185).
214
SonicWALL Global Management System Configuration Guide
Figure 185: VPN Configure Page
4. Deselect the Use Interconnected Mode check box.
5. Select IKE using Pre-Shared Secret in the IPSec Keying mode section.
6. Select from the following:
• To add a new SA, select Add a new Security Association.
• To delete an existing SA, select Delete an existing Security Association.
• To edit an existing SA, select Modify an existing Security Association.
7. Enter the name of the remote firewall/VPN gateway in the Security Association Name field. This name must
match exactly if the device has a dynamic IP address.
8. Enter the IP address of the remote firewall/VPN gateway in the IPSec Gateway Address field. This address
must be valid and will be the public IP address if the remote LAN has NAT enabled. If the remote VPN gateway has a dynamic IP address, this field can be left blank if the name matches.
9. Enter the amount of time before an IKE SA will automatically negotiate (120 to 2,499,999 seconds).
10. To specify the default LAN (WorkPort) gateway, enter the IP address of the gateway in the Default LAN
(WorkPort) Gateway field.
A Default LAN (WorkPort) Gateway is used at a central site in conjunction with a remote site using the Route
all Internet traffic through destination unit check box. The Default LAN (WorkPort) Gateway field allows
the network administrator to specify the IP address of the default LAN route for incoming IPSec packets for
this SA.
Incoming packets are decoded by the SonicWALL and compared to static routes configured in the
SonicWALL. Since packets can have any IP address destination, it is impossible to configure enough static
routes to handle the traffic. For packets received via an IPSec tunnel, the SonicWALL looks up a route for the
LAN. If no route is found, the SonicWALL checks for a Default LAN Gateway. If a Default LAN Gateway is
detected, the packet is routed through the gateway. Otherwise, the packet is dropped.
11. To prevent repeated compromises of the same security key when reestablishing a tunnel, select the Enable Perfect Forward Secrecy check box.
12. To access remote resources within the Windows Network Neighborhood, select the Enable Windows Networking (NetBIOS) Broadcast check box.
13. To apply NAT and firewall rules to all traffic coming through this SA, select the Apply NAT and firewall rules
check box.
This feature is useful for hiding the LAN subnet from the corporate site. All traffic will appear to originate from
a single IP address.
Configuring Virtual Private Networking
215
14. To allow the remote VPN tunnel to be included in the routing table, select the Forward Packets to Remote
VPNs check box.
This will enable the SonicWALL appliance to receive VPN traffic, decrypt it, and forward it to another VPN
tunnel. This feature can be used to create a “hub and spoke” network configuration by routing traffic among
SAs. To do this, make sure to enable this option for all SAs.
15. To configure the VPN tunnel to remain open as long as there is network traffic on the SA, select the Enable
Keep Alive check box.
16. To configure the SonicWALL appliance to establish the VPN tunnel before users generate any VPN traffic,
select the Try to bring up all possible SAs check box.
17. To require local users to authenticate locally before accessing the SA, select the Require authentication of
local users check box.
18. To require remote users to authenticate with this SonicWALL appliance or the local RADIUS server before
accessing resources, select the Require authentication of remote users check box.
19. Select one the following VPN termination options:
To configure the VPN tunnel to terminate at the LAN or WorkPort, select LAN (WorkPort). Users on the
other side of the SA will be able to access the LAN, but not the DMZ (HomePort).
• To configure the VPN tunnel to terminate at the DMZ or HomePort, select DMZ (HomePort). Users on the
other side of the SA will be able to access the DMZ, but not the LAN (WorkPort).
• To allow users on the other side of the SA to access both the LAN and DMZ, select LAN/DMZ or WorkPort/HomePort.
• To force inbound VPN clients to authenticate with the RADIUS server, select Require VPN Clients with
XAUTH (only allows VPN Clients). Otherwise, select Remote users behind VPN gateway.
•
Note: Only SonicWALL VPN clients can authenticate to a RADIUS server. Users tunneling from another VPN
gateway will not be able to complete the VPN tunnel if this check box is selected.
20. Enter the shared secret in the Shared Secret field.
21. Aggressive mode improves the performance of IKE SA negotiation by only requiring three packet exchanges.
However, it provides no identity protection. To enable aggressive mode, select Aggressive Mode from the
Exchange list box. Otherwise, select Main Mode.
22. Select the Diffie-Hellman group that will be used when the VPN devices are negotiating encryption and authentication keys from the Phase 1 DH Group list box.
Note: Group 1 specifies a 768-bit Diffie-Hellman value, Group 2 specifies a more secure 1024-bit Diffie-Hellman value, and Group 5 specifies the currently most secure 1536-bit Diffie-Hellman value.
23. Select the Diffie-Hellman group that will be used when the VPN devices have established an SA from the
Phase 2 DH Group list box.
24. Select the type of encryption and authentication keys used when the VPN devices are negotiating encryption
and authentication keys from the Phase 1 Encryption/Authentication list box.
25. Select the type of encryption and authentication keys used for the SAs from the Phase 2 Encryption/Authentication list box.
26. Select from the following:
To allow this SA to be used as the default route for all Internet traffic, select Use this SA as default route
for all Internet traffic.
• If the destination network will receive its IP addresses on this network using DHCP, select Destination network obtains IP addresses using DHCP.
• To specify destination networks, select Specify destination networks below. Then, click Modify and enter
the destination network IP addresses and subnet masks.
•
27. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
28. Create an SA in the remote VPN device for each SonicWALL appliance that you have configured.
Note: To disable this SA without deleting it, select the Disable this SA check box and click Update.
216
SonicWALL Global Management System Configuration Guide
Manual Keying
Manual keying involves exchanging keys in encryption and authentication keys in advance. Although this is the
simplest method of establishing an SA between two VPN devices, the SA will always use the same encryption and
authentication keys. If the keys are compromised by an outside party, they will remain compromised until the keys
are changed.
When All Appliances are Managed by SonicWALL GMS
Setting up a VPN tunnel between appliances requires you to configure several parameters on both appliances.
When setting up VPN tunnels between SonicWALL appliances managed by SonicWALL GMS, all selected appliances are automatically configured based on the settings that you entered.
To enable VPN using manual keying, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the VPN tree and click Configure. The VPN Configure page appears (Figure 186).
Figure 186: VPN Configure Page
4. Select the Use Interconnected Mode check box.
5. Select Manual Key.
6. Select from the following:
• To add a new SA, select Add a new Security Association.
• To delete an existing SA, select Delete an existing Security Association.
• To edit an existing SA, select Modify an existing Security Association.
7. Click Select Destination.
A dialog box that contains all SonicWALL appliances managed by this SonicWALL GMS appears.
8. Select the SonicWALL appliance or group to which you will establish SAs and click the Select button. The
name of the target appears in the Target SonicWALL Group/Node field.
9. Select one of the encryption methods from the Encryption Method list box.
10. To specify the default LAN (WorkPort) gateway, enter the IP address of the gateway in the Default LAN
(WorkPort) Gateway field.
A Default LAN (WorkPort) Gateway is used at a central site in conjunction with a remote site using the Route
all Internet traffic through destination unit check box. The Default LAN (WorkPort) Gateway field allows
Configuring Virtual Private Networking
217
the network administrator to specify the IP address of the default LAN route for incoming IPSec packets for
this SA.
Incoming packets are decoded by the SonicWALL and compared to static routes configured in the
SonicWALL. Since packets can have any IP address destination, it is impossible to configure enough static
routes to handle the traffic. For packets received via an IPSec tunnel, the SonicWALL looks up a route for the
LAN. If no route is found, the SonicWALL checks for a Default LAN Gateway. If a Default LAN Gateway is
detected, the packet is routed through the gateway. Otherwise, the packet is dropped.
11. To enable NetBIOS broadcasts across the SA, select the Enable Windows Networking (NetBIOS) Broadcast
check box.
12. To allow the remote VPN tunnel to be included in the routing table, select the Forward Packets to Remote
VPNs check box.
Normally, inbound traffic is decrypted and only forwarded to the local LAN or a manually specified route (see
“Configuring Routes” on page 113). This option enables you to create a “hub and spoke” network configuration
where all traffic is routed among branch offices via the corporate office.
Note: To create a “hub and spoke” network, make sure to select the Forward Packets to Remote VPNs check
box for each SA.
13. To force all network traffic to the WAN through a VPN to a central site, select the Route all Internet traffic
through destination unit check box.
When this option is selected, all traffic that is not destined for another SA is forwarded through this VPN tunnel. If this option is not specified and the destination does not match any SA, the packet is forwarded unencrypted to the WAN.
14. Select from the following NAT and Firewall Rules:
• To disable NAT and not apply firewall rules to traffic coming through this SA, select Disabled.
• To enable NAT and firewall rules for the selected SonicWALL appliance, select Source. If NAT is enabled,
all traffic originating from this appliance will appear to originate from a single IP address and network firewall rules will be applied to all traffic on this SA.
• To enable NAT and firewall rules for the selected SonicWALL appliance and its peer, select Source and
Destination. If NAT is enabled, all traffic originating from this appliance will appear to originate from a
single IP address and all traffic originating from its peer will appear to originate from a single IP address.
Network firewall rules will be applied to all traffic on this SA.
Note: Applying firewall rules can dramatically affect services that run between the networks. For more information, see Chapter 11, “Configuring Firewall Settings.”
15. Select how local users are authenticated:
• To disable authentication for local users, select Disabled.
• To configure local users to be authenticated locally, either through the SonicWALL device or the RADIUS
server, select Source.
• To configure local users to be authenticated on the destination network, either through the SonicWALL
device or the RADIUS server, select Destination.
• To authenticate local users both locally and on the destination network, select Source and Destination.
16. Select how remote users are authenticated:
• To disable authentication for remote users, select Disabled.
• To configure remote users to be authenticated locally, either through the SonicWALL device or the
RADIUS server, select Source.
• To configure remote users to be authenticated on the destination network, either through the SonicWALL
device or the RADIUS server, select Destination.
• To authenticate remote users both locally and on the destination network, select Source and Destination.
17. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
Note: To disable this SA, select the Disable this SA check box and click Update.
218
SonicWALL Global Management System Configuration Guide
When One Appliance Is Not Managed by SonicWALL GMS
This section describes how to configure VPN when the target appliance is not managed by SonicWALL GMS.
To enable VPN using manual keying, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the VPN tree and click Configure. The VPN Configure page appears (Figure 187).
Figure 187: VPN Configure Page
4. Deselect the Use Interconnected Mode check box.
5. Select Manual Key in the IPSec Keying mode section.
6. Select from the following:
• To add a new SA, select Add a new Security Association.
• To delete an existing SA, select Delete an existing Security Association.
• To edit an existing SA, select Modify an existing Security Association.
7. Enter a descriptive name for the SA in the Security Association Name field.
8. Enter the IP address of the remote firewall in the IPSec Gateway Address field. This address must be valid and
will be the public IP address if the remote LAN has NAT enabled.
9. To specify the default LAN (WorkPort) gateway, enter the IP address of the gateway in the Default LAN
(WorkPort) Gateway field.
A Default LAN (WorkPort) Gateway is used at a central site in conjunction with a remote site using the Route
all Internet traffic through destination unit check box. The Default LAN (WorkPort) Gateway field allows
the network administrator to specify the IP address of the default LAN route for incoming IPSec packets for
this SA.
Incoming packets are decoded by the SonicWALL and compared to static routes configured in the
SonicWALL. Since packets can have any IP address destination, it is impossible to configure enough static
routes to handle the traffic. For packets received via an IPSec tunnel, the SonicWALL looks up a route for the
LAN. If no route is found, the SonicWALL checks for a Default LAN Gateway. If a Default LAN Gateway is
detected, the packet is routed through the gateway. Otherwise, the packet is dropped.
10. To access remote resources within the Windows Network Neighborhood, select the Enable Windows Networking (NetBIOS) Broadcast check box.
11. To apply NAT and firewall rules to all traffic coming through this SA, select the Apply NAT and firewall rules
check box.
Configuring Virtual Private Networking
219
This feature is useful for hiding the LAN subnet from the corporate site. All traffic will appear to originate from
a single IP address.
12. To allow the remote VPN tunnel to be included in the routing table, select the Forward Packets to Remote
VPNs check box.
This will enable the SonicWALL appliance to receive VPN traffic, decrypt it, and forward it to another VPN
tunnel. This feature can be used to create a “hub and spoke” network configuration by routing traffic among
SAs. To do this, make sure to enable this option for all SAs.
13. Select one of the encryption methods from the Encryption Method list box.
14. Enter the key used for encryption in the Encryption Key field. The DES and ARCFour Keys must be exactly
16 characters long and be composed of hexadecimal characters. Encryption keys less than 16 characters will not
be accepted; keys longer than 16 characters will be truncated.
Note: Valid hexadecimal characters are “0” to “9”, and “a” to “f” (i.e., 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, a, b, c, d, e,
f). For example, a valid key would be “1234567890abcdef.”
This key must match the encryption key of the remote VPN gateway or client. If encryption is not used, this
field is ignored.
15. Enter the key used for authentication in the Authentication Key field. The authentication key must be exactly
32 characters long and be composed of hexadecimal characters. Authentication keys less than 32 characters will
not be accepted; keys longer than 32 characters will be truncated.
Note: Valid hexadecimal characters are “0” to “9”, and “a” to “f” (i.e., 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, a, b, c, d, e,
f). For example, a valid key would be “1234567890abcdef1234567890abcdef.”
This key must match the authentication key of the remote VPN gateway or client. If authentication is not used,
this field is ignored.
16. Enter the Security Parameter Index (SPI) that the remote location will send to identify the Security Association
used for the VPN Tunnel in the Incoming SPI field.
Note: The SPI may be up to eight characters long and be composed of hexadecimal characters. Valid hexadecimal characters are “0” to “9”, and “a” to “f” (e.g., 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, a, b, c, d, e, f).
The hexadecimal characters “0” to “ff” inclusive are reserved by the Internet Engineering Task Force (IETF)
and are not allowed for use as an SPI. For example, a valid SPI would be “1234abcd.”
Note: The SPI for an SA must be unique when compared to SPIs for other SAs. However, the Incoming SPI can
be the same as the Outgoing SPI on the same SA.
17. Enter the Security Parameter Index (SPI) that the local SonicWALL VPN will transmit to identify the Security
Association used for the VPN Tunnel in the Outgoing SPI field.
18. Select from the following:
To allow this SA to be used as the default route for all Internet traffic, select Use this SA as default route
for all Internet traffic.
• To specify destination networks, select Specify destination networks below. Then, click Modify and enter
the destination network IP addresses and subnet masks.
•
19. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
20. Create an SA in the remote VPN device for each SonicWALL appliance that you have configured.
220
SonicWALL Global Management System Configuration Guide
Note: To disable this SA without deleting it, select the Disable this SA check box and click Update.
Configuring VPN to Receive L2TP Connections
To support secure LT2P connections from remote clients, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the VPN tree and click L2TP. The L2TP page appears (Figure 188).
Figure 188: L2TP Server Page
4. Select the Enable L2TP Server check box.
5. Specify how often the SonicWALL appliance issues a Keepalive in the Keep alive time field.
6. Enter the IP addresses of the DNS Servers in the DNS Server fields.
7. Enter the IP addresses of the WINS Servers in the WINS Server fields.
8. Select from the following:
To assign IP addresses to L2TP clients that are provided by the RADIUS server, select IP address provided by RADIUS Server.
• To use IP addresses from a local L2TP IP address pool, select Use the Local L2TP IP pool and enter the
starting and ending IP addresses in the Start IP and End IP fields.
•
9. When you are finished, click Update. To clear all screen settings and start over, click Reset.
Configuring Virtual Private Networking
221
Monitor VPN Connections
To monitor VPN connections, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the VPN tree and click Monitor. The Monitor page appears (Figure 189).
Figure 189: Monitor Page
4. To show VPN tunnels that are up, select the Show Up Tunnels check box and click Refresh.
5. To show VPN tunnels that are down, select the Show Down Tunnels check box and click Refresh.
6. To show all VPN tunnels, select the Show All Tunnels check box and click Refresh.
7. To synchronize the tunnel status information, click Synchronize Tunnel Status Information.
8. To refresh the statistics, click Refresh Selected Tunnel Statistics.
9. To view the tunnel statistics, select one or more tunnels and click View Selected Tunnel Statistics.
10. To renegotiate selected tunnels, select one or more tunnels and click Renegotiate Selected Tunnels.
222
SonicWALL Global Management System Configuration Guide
Management of VPN Client Users
To configure VPN Clients on SonicWALL appliances, follow these procedures:
Obtain and activate VPN Client licenses for each SonicWALL appliance—see Chapter 25, “Upgrading SonicWALL Appliances.”
• Enable VPN Clients for each SonicWALL appliance—see “Enabling the VPN Client” on page 223.
•
Enabling the VPN Client
After applying a VPN Client license to one or more SonicWALL appliances, follow these steps:
1. Ensure that the Group VPN is enabled (Figure 190).
Figure 190: VPN Summary Page
2. To email the SPD file to the SonicWALL GMS administrator or the VPN Client user, click Email SPD file. The
file is attached to the email. A task is scheduled for each email.
Note: A copy of the SPD file is also stored in the SonicWALL Agent's <gms_directory\etc directory.
3. Once the SPD file is received, it can be loaded by the VPN Client software on the VPN Client user's computer.
4. If the user does not have the VPN Client software, you can send both the SPD file and the email the client software by clicking Email SPD File and VPN Client.
Note: Before the VPN client can be emailed to users, it must be downloaded to the <gms_directory>\etc directory
from Mysonicwall.com.
Downloading VPN Client Software
To download the VPN Client software from Mysonicwall.com, follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Console Panel tab at the bottom of the SonicWALL GMS UI.
3. Expand the Licenses tree and click GMS License.
4. Click Login in a new window. This will open a new browser into the GMS account on Mysonicwall.com.
5. Download the VPN Client software from Mysonicwall.com to a local directory.
6. Copy the VPN Client software to SonicWALL Agent's <gms_directory>\etc directory.
7. Rename the file to SWVpnClient.zip.
Configuring Virtual Private Networking
223
Basic Terms and Concepts
Before installing and configuring SonicWALL VPN, it is important to understand the following basic terms and
concepts.
• VPN Tunnel
Tunneling is the encapsulation of point-to-point transmissions inside IP packets. A VPN Tunnel is a term that is
used to describe a connection between two or more private nodes or LANs over a public network, typically the
Internet. Encryption is often used to maintain the confidentiality of private data when traveling over the Internet.
•
Encryption
Encryption is a mathematical operation that transforms data from “clear text” (something that a human or a program can interpret) to “cipher text” (something that cannot be interpreted). Usually the mathematical operation
requires that an alphanumeric “key” be supplied along with the clear text. The key and clear text are processed
by the encryption operation, which leads to the data scrambling that makes encryption secure. Decryption is the
opposite of encryption: it is a mathematical operation that transforms cipher text to clear text. Decryption also
requires a key.
•
Key
A key is an alphanumeric string that is used by the encryption operation to transform clear text into cipher text.
A key is composed of hexadecimal characters (0, 1, 2, 3, 4, 5, 6, 7, 8, 9, a, b, c, d, e, f). A valid key would be
1234567890abcdef. Keys used in VPN communications can vary in length, but are typically 16 or 32 characters. The longer the key, the more difficult it is to break the encryption. The reason for this is that most methods
used to break encryption involve trying every possible combination of characters, similar to trying to find
someone’s telephone number by dialing every possible combination of phone numbers.
• Asymmetric vs. Symmetric Cryptography
Asymmetric and symmetric cryptography refer to the keys used to authenticate, or encrypt and decrypt the data.
Asymmetric cryptography, or public key cryptography, uses two keys for verification. Organizations such as
RSA Data Security and VeriSign support asymmetric cryptography.
With symmetric cryptography, the same key is used to authenticate on both ends of the VPN. Symmetric cryptography, or secret key cryptography, is usually faster than asymmetric cryptography. Therefore symmetric
algorithms are often used when large quantities of data need to be exchanged.
SonicWALL VPN uses symmetric cryptography. As a result, the key on both ends of the VPN tunnel must
match exactly.
•
Security Association (SA)
An SA is the group of security settings needed to create a VPN tunnel. All SAs require an encryption method,
an IPSec gateway address, and a destination network address. IKE includes a shared secret. manual keying
includes two SPIs and an encryption and authentication key.
SonicWALL PRO appliances supports up to 100 SAs. SonicWALL SOHO2 and SonicWALL XPRS2 appliances support 10 and 25 SAs, respectively. Different SAs may be created to connect branch offices, allow
secure remote management, and pass unsupported traffic.
•
Internet Key Exchange (IKE)
IKE is a negotiation and key exchange protocol specified by the Internet Engineering Task Force (IETF). An
IKE SA automatically negotiates encryption and authentication keys. With IKE, an initial exchange authenticates the VPN session and automatically negotiates keys that will be used to pass IP traffic.
•
Manual Key
Manual keying allows the SonicWALL administrator to specify the encryption and authentication keys.
SonicWALL VPN supports the ability to manually set up a security association as well as the ability to automatically negotiate an SA using IKE.
•
Shared Secret
A shared secret is a predefined field that the two endpoints of a VPN tunnel use to set up an IKE SA. This field
can be any combination of alphanumeric characters with a minimum length of 4 characters and a maximum of
224
SonicWALL Global Management System Configuration Guide
128 characters. Precautions should be taken when delivering/exchanging this shared secret to assure that a third
party cannot compromise the security of a VPN tunnel.
•
Encapsulating Security Payload (ESP)
ESP provides confidentiality and integrity of data by encrypting the data and encapsulating it into IP packets.
Encryption may be in the form of ARCFour (similar to the popular RC4 encryption method), DES, etc.
The use of ESP typically increases the processing requirements and communications latency. The increased
latency is primarily due to the encryption and decryption required for each IP packet containing an ESP.
ESP typically involves encryption of the packet payload using standard encryption mechanisms, such as RC4,
ARCFour, DES, or 3DES.
ESP has no mechanism for providing strong integrity and authentication of the data.
• Authentication Header (AH)
The authentication header is a mechanism for providing strong integrity and authentication for IP packets. The
Authentication Header does not offer confidentiality and protection from traffic analysis.
The IP authentication header provides security by adding authentication information to an IP packet. This
authentication information is calculated using all header and payload data in the IP packet. This provides significantly more security than is currently present in IP.
Use of an AH will increase the processing requirements of SonicWALL VPN and will also increase the communications latency. The increased latency is primarily due to the calculation of the authentication data by the
sender and the calculation and comparison of the authentication data by the receiver for each IP packet.
•
Data Encryption Standard (DES)
When DES is used for data communications, both sender and receiver must know the same secret key, which
can be used to encrypt and decrypt the message, or to generate and verify a message authentication code. The
SonicWALL DES encryption algorithm uses a 56-bit key.
The DES Key must be exactly 16 characters long and is composed of hexadecimal characters. Valid hexadecimal characters are “0” to “9”, and “a” to “f” inclusive (0, 1, 2, 3, 4, 5, 6, 7, 8, 9, a, b, c, d, e, f). For example, a
valid key would be “1234567890abcdef.”
•
Triple Data Encryption Standard (3DES)
3DES is the same as DES, except that it applies three DES keys in succession and is significantly more secure.
However, 3DES has significantly more processing requirements than DES.
The 3DES Key must be exactly 16 characters long and is composed of hexadecimal characters. Valid hexadecimal characters are “0” to “9”, and “a” to “f” inclusive (0, 1, 2, 3, 4, 5, 6, 7, 8, 9, a, b, c, d, e, f). For example, a
valid key would be “1234567890abcdef.”
•
ARCFour
ARCFour is used for communications with secure Web sites using the SSL protocol. Many banks use a 40-bit
key ARCFour for online banking, while others use a 128-bit key. SonicWALL VPN uses a 56-bit key for ARCFour.
The ARCFour key must be exactly 16 characters long and is composed of hexadecimal characters. Valid hexadecimal characters are “0” to “9”, and “a” to “f” (i.e., 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, a, b, c, d, e, f). For example, a
valid key would be “1234567890abcdef.”
•
Security Parameter Index (SPI)
The SPI is used to establish a VPN tunnel. The SPI is transmitted from the remote VPN gateway to the local
VPN gateway. The local VPN gateway then uses the network, encryption, and key values that the administrator
associated with the SPI to establish the tunnel.
The SPI must be unique, is from one to eight characters long, and is composed of hexadecimal characters. Valid
hexadecimal characters are “0” to “9”, and “a” to “f” (i.e., 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, a, b, c, d, e, f). For example,
valid SPIs would be 999 or “1234abcd.”
Configuring Virtual Private Networking
225
Using OCSP with SonicWALL Security Appliances
Online Certificate Status Protocol (OCSP) allows you to check VPN certificate status without CRLs. This allows timely
updates regarding the status of the certificates used on your SonicWALL.
About OCSP
OCSP is designed to augment or replace Certificate Revocation Lists (CRL) in your Public Key Infrastructure (PKI) or digital
certificate system. The CRL is used to validate the digital certificates comprised by the PKI. This allows the Certificate
Authority (CA) to revoke certificates before their scheduled expiration date and is useful in protecting the PKI system against
stolen or invalid certificates.
Certificate Revocation Lists main disadvantage is the need for frequent updates to keep the CRL of every client current.
These frequent updates greatly increase network traffic when the complete CRL is downloaded by every client. Depending on
the frequency of the CRL updates, a period of time can exist when a certificate is revoked by the CRL but the client has not
received the CRL update and permits the certificate to be used.
Online Certificate Status Protocol determines the current status of a digital certificate without using a CRL. OCSP enables the
client or application to directly determine the status of an identified digital certificate. This provides more timely information
about the certificate than is possible with CRLs. In addition, each client typically only checks a few certificates and does not
incur the overhead of downloading an entire CRL for only a few entries. This greatly reduces the network traffic associated
with certificate validation.
OCSP transports messages over HTTP for maximum compatibility with existing networks. This requires careful
configuration of any caching servers in the network to avoid receiving a cached copy of an OCSP response that might be out
of date.
The OCSP client communicates an OCSP responder. The OCSP responder can be a CA server or another server that
communicates with the CA server to determine the certificate status. The OCSP client issues a status request to an OCSP
responder and suspends the acceptance of the certificate until the responder provides a response. The client request includes
data such as protocol version, service request, target certificate identification and optional extensions. These optional
extensions may or may not be acknowledged by the OCSP responder.
The OCSP responder receives the request from the client and checks that the message is properly formed and if the responder
is able to respond to the service request. Then it checks if the request contains the correct information needed for the service
desired. If all conditions are satisfied, the responder returns a definitive response to the OCSP client. The OCSP responder is
required to provide a basic response of GOOD, REVOKED, or UNKNOWN. If both the OCSP client and responder support
the optional extensions, other responses are possible. The GOOD state is the desired response as it indicates the certificate has
not been revoked. The REVOKED state indicates that the certificate has been revoked. The UNKNOWN state indicates the
responder does not have information about the certificate in question.
OCSP servers typically work with a CA server in push or pull setup. The CA server can be configured to push a CRL list
(revocation list) to the OCSP server. Additionally the OCSP server can be configured to periodically download (pull) the
CRL from the CA server. The OCSP server must also be configured with an OCSP response signing certificate issued by the
CA server. The signing certificate must be properly formatted or the OCSP client will not accept the response from the OSCP
server.
226
SonicWALL Global Management System Configuration Guide
OpenCA OCSP Responder
Using OCSP requires the OpenCA (OpenSource Certificate Authority) OpenCA OCSP Responder as it is the only supported
OCSP responder. OpenCA OCSP Responder is available at <http://www.openca.org/ocspd/>. The OpenCA OCSP
Responder is an rfc2560 compliant OCSP responder that runs on a default port of 2560 in homage to being based on rfc2560.
For SonicOS to act as an OCSP client to a responder, the CA certificate must be loaded onto the SonicWALL.
Using OCSP with VPN Policies
The SonicWALL OCSP settings can be configured on a policy level or globally. To configure OCSP checking for individual
VPN policies. Then click on the VPNs page.
1 Select the radio button next to Enable OCSP Check
2 Specify the OCSP Responder URL of the OCSP server, for example http://192.168.168.220:2560 where
192.168.168.220 is the IP address of your OCSP server and 2560 is the default port of operation for the OpenCA OCSP
responder service.
Configuring Virtual Private Networking
227
228
SonicWALL Global Management System Configuration Guide
CHAPTER 18
Configuring Virtual Private Networking 2.0
This chapter describes how to configure VPN settings for SonicWALL appliances running SonicOS Enhanced. To
configure VPN for SonicOS Standard, see Chapter 17, “Configuring Virtual Private Networking.”
To configure VPN for SonicWALL appliances using SonicOS Enhanced, follow these procedures:
•
•
•
•
•
To configure VPNs, see “Configuring VPN” on page 229.
To configure L2TP VPNs, see “Configuring VPN to Receive L2TP Connections” on page 235.
To monitor VPNs, see “Monitoring VPN Connections” on page 236.
To manage VPN client users, see “Managing VPN Client Users” on page 237.
To create VPN client license sharing groups, “Creating License Sharing Groups” on page 319.
Configuring VPN
SonicOS uses Address Objects and Address Object Groups to simplify network configuration and interconnection.
Address objects are network addresses or hosts. Address object groups are groups of address objects and/or address
object groups.
When you configure VPN between Address Object Groups on two SonicWALL appliances, SonicWALL GMS will
automatically establish VPN connections between every network within those groups. This saves a lot of configuration time and dramatically simplifies VPN configuration.
Select from the following:
• To configure VPNs between two SonicWALL appliances, see “Interconnected Mode” on page 229.
• To configure a VPN between a SonicWALL appliance and another device, see “Non-Interconnected Mode” on
page 232.
Interconnected Mode
Establishing a VPN between two SonicWALL appliances that are being managed by SonicWALL GMS is easy.
Because SonicWALL GMS is aware of the configuration settings, it will automatically configure most of the VPN
settings without any user intervention. To establish VPNs between two SonicWALL appliances that are being managed by SonicWALL GMS, follow these steps:
Note: To quickly establish a VPN tunnel using the default settings, complete Steps 1 through 12 and click OK.
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the VPN tree and click Configure 2.0. The VPN Configure page appears with the General tab selected
(Figure 191).
Configuring Virtual Private Networking 2.0
229
Figure 191: VPN Configure 2.0 Page
4. To establish a new SA, select Add New SA from the Security Association list box.
5. Select the Interconnected check box.
6. To configure SonicWALL GMS to convert the SAs to non-interconnected mode VPN tunnels, select the Make
SAs viewable in Non-Interconnected Mode check box.
Note: This is not reversible.
7. Select the destination SonicWALL appliance by clicking Select Destination Node and selecting the node from
the dialog box that appears.
8. Select from the following keying modes from the IPSec Keying Mode list box:
•
Manual Key—keys are exchanged in advance.
The SA will always use the same encryption and authentication keys. If the keys are compromised by an
outside party, they will remain compromised until the keys are changed.
•
IKE Using 3rd Party Certificates—the SonicWALL appliance and peer device obtain certificates from
the third-party certificate authorities. Security and authentication keys are exchanged using public-key
cryptography and authenticity of each node is verified by the third-party CA.
After the SA expires, the peers will reestablish an SA using the same public keys, but will not use the same
security and authentication keys.
• IKE Using Pre-Shared Secret—each SonicWALL appliance has a shared secret that is used to establish an
SA.
After the SA expires, the SonicWALL appliances will reestablish an SA using the same public keys, but
will not use the same security and authentication keys.
If you select this option, configure the following:
Local IKE ID—specifies the whether the IP address or SonicWALL Identifier will be used as the IKE
ID for the local SonicWALL appliance.
• Peer IKE ID—specifies the whether the IP address or SonicWALL Identifier will be used as the IKE
ID for the peer SonicWALL appliance.
•
9. Specify the FQDN of the gateway in the Destination Gateway field (optional).
10. Click the Network tab.
230
SonicWALL Global Management System Configuration Guide
11. Select which local networks will be establishing VPN connections with the destination networks:
Choose local network from list—specifies an Address Object that contains one or more networks. For
information on creating address objects, refer to the documentation that accompanied the SonicWALL
appliance.
• Local network obtains IP addresses using DHCP through this VPN Tunnel—indicates that the computers on the local network will obtain their IP addresses from the destination network.
• Any address—configures all networks to establish VPN connections with the specified destination networks.
•
12. Select the destination networks with which the local networks will connect:
Use this VPN Tunnel as default route for all Internet traffic—configures all networks on the destination
network to use this VPN for all Internet traffic.
• Destination network obtains IP addresses using DHCP through this VPN Tunnel—indicates that the
computers on the destination network will obtain their IP addresses from the local network.
• Choose destination network from list—specifies an Address Object that contains one or more networks.
For information on creating address objects, refer to the documentation that accompanied the SonicWALL
appliance.
•
13. Click the Proposals tab.
14. Select the IKE Phase 1 Proposal Options (Certificates and Pre-Shared Secret only):
Exchange—select the exchange mode from the Exchange list box. Aggressive mode improves the performance of IKE SA negotiation by only requiring three packet exchanges. However, it provides no identity
protection. Otherwise, select Main Mode.
• DH Group—specifies the Diffie-Hellman group to use when the VPN devices are negotiating encryption
and authentication keys.
•
•
•
•
Note: Group 1 specifies a 768-bit Diffie-Hellman value, Group 2 specifies a more secure 1024-bit DiffieHellman value, and Group 5 specifies the currently most secure 1536-bit Diffie-Hellman value.
Encryption—specifies the type of encryption key to use when the VPN devices are negotiating encryption
keys.
Authentication—specifies the type of authentication key to use when the VPN devices are negotiating
authentication keys.
Life Time (seconds)—specifies how long a tunnel will remain active before being renegotiated. We recommend a value of 28,800 seconds (8 hours).
15. Select the IKE Phase 2 Proposal Options:
• Protocol—specifies the type of protocol to use for VPN communications (AH or ESP).
• Encryption—specifies the type of encryption key to use when the VPN devices after negotiating encryption keys.
• Authentication—specifies the type of authentication key to use when the VPN devices after negotiating
authentication keys.
• Enable Perfect Forward Secrecy—when selected, this option prevents repeated compromises of the same
security key when reestablishing a tunnel.
• DH Group—specifies the Diffie-Hellman group to use when the VPN devices after negotiating encryption
and authentication keys.
•
Note: Group 1 specifies a 768-bit Diffie-Hellman value, Group 2 specifies a more secure 1024-bit DiffieHellman value, and Group 5 specifies the currently most secure 1536-bit Diffie-Hellman value.
Life Time (seconds)—specifies how long a tunnel will remain active before being renegotiated. We recommend a value of 28,800 seconds (8 hours).
16. Click the Advanced tab.
Configuring Virtual Private Networking 2.0
231
17. Configure the following Advanced settings:
•
•
•
•
•
•
Enable Keep Alive—configures the VPN tunnel to remain open as long as there is network traffic on the
SA.
Enable Windows Networking Broadcast—enables NetBIOS broadcasts across the SA.
Management via this SA—specifies which protocols can be used to manage the SonicWALL appliance
through this SA.
User login via this SA—specifies the protocols that users can use to login to the SonicWALL appliance
through this SA.
Default LAN Gateway—specifies the default gateway when routing all traffic through this tunnel.
VPN Policy bound to—specifies the zone or interface to which the VPN tunnel will terminate.
18. When you are finished, click OK. SonicWALL GMS begins establishing VPN tunnels between all specified
networks.
Non-Interconnected Mode
To establish VPNs between two SonicWALL appliances that are being managed by SonicWALL GMS, follow
these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the VPN tree and click Configure 2.0. The VPN Configure page appears with the General tab selected
(Figure 192).
Figure 192: VPN Configure 2.0 Page
4. To establish a new SA, select Add New SA from the Security Association list box.
5. Deselect the Interconnected check box.
6. Select from the following keying modes from the IPSec Keying Mode list box:
•
Manual Key—keys are exchanged in advance.
The SA will always use the same encryption and authentication keys. If the keys are compromised by an
outside party, they will remain compromised until the keys are changed.
232
SonicWALL Global Management System Configuration Guide
If you select this option, configure the following:
• Name—specifies the name of the SA.
• IPSec Gateway Name or Address—specifies the name or IP address of the gateway.
• IKE Using 3rd Party Certificates—the SonicWALL appliance and peer device obtain certificates from
the third-party certificate authorities. Security and authentication keys are exchanged using public-key
cryptography and authenticity of each node is verified by the third-party CA.
After the SA expires, the peers will reestablish an SA using the same public keys, but will not use the same
security and authentication keys.
If you select this option, configure the following:
• Name—specifies the name of the SA.
• IPSec Primary Gateway Name or Address—specifies the name or IP address of the primary gateway.
• IPSec Secondary Gateway Name or Address—specifies the name or IP address of the secondary
gateway.
• Third Party Certificate—specifies the certificate used to establish the SAs.
• Peer Certificate's ID Type—specifies the ID type of the peer certificate.
• ID string to match—specifies the string used to establish the SAs.
• IKE Using Pre-Shared Secret—each SonicWALL appliance has a shared secret that is used to establish an
SA.
After the SA expires, the SonicWALL appliances will reestablish an SA using the same public keys, but
will not use the same security and authentication keys.
If you select this option, configure the following:
• Name—specifies the name of the SA.
• IPSec Primary Gateway Name or Address—specifies the name or IP address of the primary gateway.
• IPSec Secondary Gateway Name or Address—specifies the name or IP address of the secondary
gateway.
• Shared Secret—specifies the shared secret used to negotiate the VPN tunnel.
• Local IKE ID—specifies the whether the IP address or SonicWALL Identifier will be used as the IKE
ID for the local SonicWALL appliance.
• Peer IKE ID—specifies the whether the IP address or SonicWALL Identifier will be used as the IKE
ID for the peer SonicWALL appliance.
7. Specify the FQDN of the gateway in the Destination Gateway field (optional).
8. Click the Network tab.
9. Select which local networks will be establishing VPN connections with the destination networks:
• Choose local network from list—specifies an Address Object that contains one or more networks. For
information on creating address objects, refer to the documentation that accompanied the SonicWALL
appliance.
• Local network obtains IP addresses using DHCP through this VPN Tunnel—indicates that the computers on the local network will obtain their IP addresses from the destination network.
• Any address—configures all networks to establish VPN connections with the specified destination networks.
10. Select the destination networks with which the local networks will connect:
Use this VPN Tunnel as default route for all Internet traffic—configures all networks on the destination
network to use this VPN for all Internet traffic.
• Destination network obtains IP addresses using DHCP through this VPN Tunnel—indicates that the
computers on the destination network will obtain their IP addresses from the local network.
• Choose destination network from list—specifies an Address Object that contains one or more networks.
For information on creating address objects, refer to the documentation that accompanied the SonicWALL
appliance.
•
11. Click the Proposals tab.
Configuring Virtual Private Networking 2.0
233
12. Select the IKE Phase 1 Proposal Options (Certificates and Pre-Shared Secret only):
Exchange—Select the exchange mode from the Exchange list box. Aggressive mode improves the performance of IKE SA negotiation by only requiring three packet exchanges. However, it provides no identity
protection. Otherwise, select Main Mode.
• DH Group—specifies the Diffie-Hellman group to use when the VPN devices are negotiating encryption
and authentication keys.
•
Note: Group 1 specifies a 768-bit Diffie-Hellman value, Group 2 specifies a more secure 1024-bit DiffieHellman value, and Group 5 specifies the currently most secure 1536-bit Diffie-Hellman value.
• Encryption—specifies the type of encryption key to use when the VPN devices are negotiating encryption
keys.
• Authentication—specifies the type of authentication key to use when the VPN devices are negotiating
authentication keys.
• Life Time (seconds)—specifies how long a tunnel will remain active before being renegotiated. We recommend a value of 28,800 seconds (8 hours).
13. Select the IKE Phase 2 Proposal Options:
• Protocol—specifies the type of protocol to use for VPN communications (AH or ESP).
• Encryption—specifies the type of encryption key to use when the VPN devices after negotiating encryption keys.
• Authentication—specifies the type of authentication key to use when the VPN devices after negotiating
authentication keys.
• Enable Perfect Forward Secrecy—when selected, this option prevents repeated compromises of the same
security key when reestablishing a tunnel.
• DH Group—specifies the Diffie-Hellman group to use when the VPN devices after negotiating encryption
and authentication keys.
Note: Group 1 specifies a 768-bit Diffie-Hellman value, Group 2 specifies a more secure 1024-bit DiffieHellman value, and Group 5 specifies the currently most secure 1536-bit Diffie-Hellman value.
• Life Time (seconds)—specifies how long a tunnel will remain active before being renegotiated. We recommend a value of 28,800 seconds (8 hours).
14. Click the Proposals tab.
15. Configure the following Advanced settings:
•
•
•
•
•
•
•
•
Enable Keep Alive—configures the VPN tunnel to remain open as long as there is network traffic on the
SA.
Enable Windows Networking Broadcast—enables NetBIOS broadcasts across the SA.
Apply NAT Policies—enables NAT for the selected networks.
Management via this SA—specifies which protocols can be used to manage the SonicWALL appliance
through this SA.
User login via this SA—specifies the protocols that users can use to login to the SonicWALL appliance
through this SA.
Default LAN Gateway—specifies the default gateway when routing all traffic through this tunnel
(required for Enhanced-to-Standard configuration, optional for Enhanced-to-Enhanced).
VPN Policy bound to—specifies the zone or interface to which the VPN tunnel will terminate.
Enable Windows Networking Broadcast—enables NetBIOS broadcasts across the SA.
16. When you are finished, click OK. SonicWALL GMS begins establishing VPN tunnels between all specified
networks.
234
SonicWALL Global Management System Configuration Guide
Configuring VPN to Receive L2TP Connections
Layer 2 Tunneling Protocol (L2TP) can be used to create VPN over public networks such as the Internet. Although
L2TP is an extension of PPTP and L2F, it provides interoperability between different VPN vendors that the PPTP
and L2F protocols do not.
L2TP supports several of the authentication options supported by PPP, including Password Authentication Protocol
(PAP), Challenge Handshake Authentication Protocol (CHAP), and Microsoft Challenge Handshake Authentication Protocol (MS-CHAP). You can use L2TP to authenticate the endpoints of a VPN tunnel to provide additional
security, and you can implement it with IPSec to provide a secure, encrypted VPN solution.
To support secure LT2P connections from remote clients, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the VPN tree and click L2TP. The L2TP page appears (Figure 193).
Figure 193: L2TP Server Page
4. Select the Enable L2TP Server check box.
5. Specify how often the SonicWALL appliance issues a Keepalive in the Keep alive time field.
6. Enter the IP addresses of the DNS Servers in the DNS Server fields.
7. Enter the IP addresses of the WINS Servers in the WINS Server fields.
8. Select from the following:
To assign IP addresses to L2TP clients that are provided by the RADIUS server, select IP address provided by RADIUS Server.
• To use IP addresses from a local L2TP IP address pool, select Use the Local L2TP IP pool and enter the
starting and ending IP addresses in the Start IP and End IP fields.
•
9. When you are finished, click Update. To clear all screen settings and start over, click Reset.
Configuring Virtual Private Networking 2.0
235
Monitoring VPN Connections
To monitor VPN connections, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the VPN tree and click Monitor. The Monitor page appears (Figure 194).
Figure 194: Monitor Page
4. To show VPN tunnels that are up, select the Show Up Tunnels check box and click Refresh.
5. To show VPN tunnels that are down, select the Show Down Tunnels check box and click Refresh.
6. To show all VPN tunnels, select the Show All Tunnels check box and click Refresh.
7. To synchronize the tunnel status information, click Synchronize Tunnel Status Information.
8. To refresh the statistics, click Refresh Selected Tunnel Statistics.
9. To view the tunnel statistics, select one or more tunnels and click View Selected Tunnel Statistics.
10. To renegotiate selected tunnels, select one or more tunnels and click Renegotiate Selected Tunnels.
236
SonicWALL Global Management System Configuration Guide
Managing VPN Client Users
Remote clients can use the SonicWALL VPN Client Software to securely access a SonicWALL appliance. To configure VPN Clients on SonicWALL appliances, follow these procedures:
Obtain and activate VPN Client licenses for each SonicWALL appliance—see Chapter 25, “Upgrading SonicWALL Appliances.”
• Enable VPN Clients for each SonicWALL appliance—see “Enabling the VPN Client” on page 237.
• Instruct the VPN Client users to download and install the SonicWALL VPN Client Software—see “Enabling
the VPN Client” on page 237.
•
Enabling the VPN Client
After applying a VPN Client license to one or more SonicWALL appliances, follow these steps:
1. Ensure that the Group VPN is enabled (Figure 195).
Figure 195: VPN Summary Page
2. To email the SPD file to the SonicWALL GMS administrator or the VPN Client user, click Email SPD file. The
file is attached to the email. A task is scheduled for each email.
Note: A copy of the SPD file is also stored in the SonicWALL Agent's <gms_directory\etc directory.
3. Once the SPD file is received, it can be loaded by the VPN Client software on the VPN Client user's computer.
4. If the user does not have the VPN Client software, you can send both the SPD file and the email the client software by clicking Email SPD File and VPN Client.
Note: Before the VPN client can be emailed to users, it must be downloaded to the <gms_directory>\etc directory
from Mysonicwall.com.
Downloading VPN Client Software
To download the VPN Client software from Mysonicwall.com, follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Console Panel tab at the bottom of the SonicWALL GMS UI.
3. Expand the Licenses tree and click GMS License.
4. Click Login in a new window. This will open a new browser into the GMS account on Mysonicwall.com.
5. Download the VPN Client software from Mysonicwall.com to a local directory.
Configuring Virtual Private Networking 2.0
237
6. Copy the VPN Client software to SonicWALL Agent's <gms_directory>\etc directory.
7. Rename the file to SWVpnClient.zip.
238
SonicWALL Global Management System Configuration Guide
CHAPTER 19
Configuring Security Services
SonicWALL security appliances offer several services for protecting networks against viruses and attacks. This
chapter provides concept overviews and configuration tasks for deploying these services.
This chapter contains the following sections:
Overview of Anti-Virus Protection—see “Configuring Anti-Virus Settings” on page 241
Anti-Virus Protection—see “Configuring Anti-Virus Settings” on page 241.
Overview of Intrusion Prevention Services—see “Overview of IPS” on page 245
Configuring Intrusion Prevention—see “Configuring Intrusion Prevention Services” on page 248.
Configuring Global Security Client Access Settings—see “Configuring Global Security Client Security Settings” on page 252.
• SonicWALL Anti-Spyware Overview—see “SonicWALL Anti-Spyware Overview” on page 258.
• Setting Up SonicWALL Anti-Spyware Protection—see “Setting Up SonicWALL Anti-Spyware Protection”
on page 261.
•
•
•
•
•
Configuring Security Services
239
Overview of Anti-Virus Protection
The widespread outbreaks of viruses, such as NIMDA and Code Red, illustrate the problematic nature of virus
defense for small and medium businesses. Users without the most current virus definition files allow these viruses
to multiply and infect many other users and networks. SonicWALL Network Anti-Virus prevents occurrences like
these and offers a new approach to virus protection. SonicWALL security appliances constantly monitor the version
of the virus definition file and automatically triggers download and installation of new virus definition files to each
user’s computer. In addition, SonicWALL security appliances restrict each user’s access to the Internet until they
are protected, therefore acting as an enforcer of the company’s virus protection policy. This new approach ensures
the most current version of the virus definition file is installed and active on each PC on the network, preventing a
rogue user from disabling the virus protection and potentially exposing the entire organization to an outbreak.
Anti-virus products typically require regular, active maintenance on every PC. When a new virus is discovered, all
anti-virus software deployed within an organization must be updated with the latest virus definition files. Failure to
do so severely limits the effectiveness of anti-virus software and disrupts productive work time. With more than
50,000 known viruses and new virus outbreaks occurring regularly, the task of maintaining and updating virus protection can become unwieldy. Unfortunately, many small to medium businesses do not have adequate IT staff to
maintain their anti-virus software. The resulting gaps in virus defenses may lead to data loss and decreased
employee productivity.
p
Note: You must purchase an Anti-Virus subscription to enforce Anti-Virus through the SonicWALL security appliance’s Management Interface.
240
SonicWALL Global Management System Configuration Guide
Configuring Anti-Virus Settings
SonicWALL Global Management System (SonicWALL GMS) offers anti-virus protection on a subscription-basis
through a partnership with McAfee.
Note: SonicWALL appliances are entitled to a one-month anti-virus trial subscription. To enable the trial subscription, see Chapter 25, “Upgrading SonicWALL Appliances.”
Select from the following:
•
•
•
•
To change the anti-virus password, see “Changing Anti-Virus Password” on page 241.
To change standard anti-virus settings, see “Configuring Anti-Virus Settings” on page 242.
To configure the anti-virus email filter, see “Configuring Anti-Virus Email Filter Settings” on page 243.
To create a License Sharing Group that can be used to share anti-virus licenses among multiple SonicWALL
appliances, see “Creating License Sharing Groups” on page 319.
Changing Anti-Virus Password
This section describes how to configure the Anti-Virus password for SonicWALL appliances.
To configure the Anti-Virus password for one or more SonicWALL appliances, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Security Services tree and click AV Password. The AV Password page appears (Figure 196).
Figure 196: AV Password Page
4. Select from the following:
•
•
If a single SonicWALL appliance is selected, enter a new password and click Change Anti-Virus Password. The password is changed.
Note: This option can also be used to correct a password that was incorrectly entered during configuration.
If the global or group view is selected, click Change Anti-Virus Password(s) Randomly. The password(s)
are changed.
Configuring Security Services
241
Configuring Anti-Virus Settings
This section describes how to configure Anti-Virus settings for SonicWALL appliances.
To configure Anti-Virus settings for one or more SonicWALL appliances, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Security Services tree and click AV Configure. The AV Configure page appears (Figure 197).
Figure 197: AV Configure Page
4. Select the Enable Anti-Virus Client Automated Installation, Updates and Enforcement check box.
5. To enforce Anti-Virus protection on the DMZ port or HomePort (if available), select the Enable DMZ/HomePort/WLAN/OPT Policing check box.
6. To disable policing from the LAN to the DMZ, select the Disable policing from LAN/WorkPort to DMZ/
HomePort/WLAN/OPT check box.
7. To reduce the anti-virus traffic over ISDN connections, select the Reduce AV Traffic for ISDN Connections
check box.
8. SonicWALL GMS automatically downloads the latest virus definition files. To configure the maximum number
of days that can pass before SonicWALL GMS downloads the latest files, select the number of days from the
Maximum Days Allowed Before Forcing Update list box.
9. Significant virus events can occur without warning (e.g., Melissa, ILOVEYOU, and others). When these occur,
SonicWALL GMS can be configured to block network traffic until the latest virus definition files are downloaded. To configure this feature, determine which types of events will require updating. Then, select the Low
Risk, Medium Risk, or High Risk check boxes.
10. To configure the SonicWALL appliance(s) to only check for updates once a day, select the Reduce AV Traffic
for ISDN connections check box. This is useful for low bandwidth connections or connections that are not
“always on.”
11. To enable infected email attachment blocking on inbound SMTP and POP3 e-mail protocols, select the Enable
E-mail Attachment Filtering Alert Service check box. The SonicWALL appliance will block viruses that are
discovered by the virus signature files and filenames that are known to be infected during an outbreak even
before Anti-Virus signature (DAT) files are available.
This feature also provides full filename blocking of virus files. The full filename attachment filtering allows
SonicWALL to block only malicious attachments, while enabling all other attachments through. For example,
242
SonicWALL Global Management System Configuration Guide
during a virus outbreak, only the virus file is blocked while other productive files (such as Word documents and
Excel spreadsheets) are allowed through.
Note: Only files that were discovered to be infected will be blocked. If a message contains uninfected attachments, those will be forwarded to the recipient.
12. Select from the following:
• To configure the SonicWALL appliance(s) to provide Anti-Virus enforcement for all computers on the network, select Enforce Anti-Virus policies for all computers.
• To configure the SonicWALL appliance(s) to provide Anti-Virus enforcement for a specific list of computers, select Include specific address ranges in the Anti-Virus enforcement and enter ranges of IP
addresses in the Addr Range Begin and Addr Range End fields.
• To configure the SonicWALL appliance(s) to provide Anti-Virus enforcement for all computers except
those listed, select Exclude specific address ranges in the Anti-Virus enforcement and enter ranges of IP
addresses in the Addr Range Begin and Addr Range End fields.
13. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
Configuring Anti-Virus Email Filter Settings
This section describes how to configure SonicWALL appliances to automatically scan email messages for viruses.
To configure email filter settings for one or more SonicWALL appliances, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Security Services tree and click EMail Filter. The EMail Filter page appears (Figure 198).
Figure 198: Email Filter Page
4. Select the Enable Email Attachment Filtering check box.
5. To add an extension to scan for viruses, enter the extension in the Extensions field and click Add. Hackers commonly spread viruses through Visual Basic and Windows Executable files, therefore “vbs” and “exe” are provided as default extensions for this feature.
6. To configure the SonicWALL appliance(s) to disable infected attachment files as they pass through the SonicWALL by changing their extensions, select Disable forbidden file by altering the file extension. The Son-
Configuring Security Services
243
icWALL appliance replaces the third character of file extensions with “_”. If the email attachment is a valid file,
the message recipient may return the attachment to its original file extension without damaging the file.
7. To configure the SonicWALL appliance(s) to delete infected files, select Delete forbidden file.
8. Enter warning text that will be attached to the message and forwarded to the message recipient (maximum 256
characters).
9. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
The SonicWALL appliance will block viruses that are discovered by the virus signature files and filenames that
are known to be infected during an outbreak.
Note: Only infected files will be blocked. If a message contains uninfected attachments, those will be forwarded
to the recipient.
244
SonicWALL Global Management System Configuration Guide
Overview of IPS
SonicWALL Intrusion Prevention Service (SonicWALL IPS) delivers a configurable, high performance Deep
Packet Inspection engine for extended protection of key network services such as Web, e-mail, file transfer, Windows services and DNS. SonicWALL IPS is designed to protect against application vulnerabilities as well as
worms, Trojans, and peer-to-peer, spyware and backdoor exploits. The extensible signature language used in SonicWALL’s Deep Packet Inspection engine also provides proactive defense against newly discovered application and
protocol vulnerabilities. SonicWALL IPS offloads the costly and time-consuming burden of maintaining and updating signatures for new hacker attacks through SonicWALL’s industry-leading Distributed Enforcement Architecture
(DEA). Signature granularity allows SonicWALL IPS to detect and prevent attacks based on a global, attack group,
or per-signature basis to provide maximum flexibility and control false positives.
SonicWALL IPS is managed directly from the SonicWALL Security Appliance. Alternatively, SonicWALL Global
Management System (SonicWALL GMS) provides global management capabilities that enabled administrators to
manage SonicWALL IPS across multiple SonicWALL Security Appliances from a central location. SonicWALL
GMS and SonicWALL ViewPoint solutions allow administrator’s to create detailed reports based on attack source,
destination and type of intrusion, such as “Top Intrusions,” “Destinations Over Time” and “Intrusions Over Time.”
SonicWALL IPS Features
•
•
•
•
•
•
•
•
•
High Performance Deep Packet Inspection Technology - SonicWALL’s Intrusion Prevention Service features a configurable, high-performance Deep Packet Inspection engine that uses parallel searching algorithms
on incoming packets through the application layer to deliver increased attack prevention capabilities over those
supplied by traditional stateful packet inspection firewall. By performing all of the matching on packets, SonicWALL IPS eliminates the overhead of having to reassemble the data stream. Parallel processing reduces the
impact on the processor and maximizes available memory for exceptional performance on SonicWALL appliances.
Inter-Zone Intrusion Prevention - SonicWALL IPS provides an additional layer of protection against malicious threats by allowing administrator’s to enforce intrusion prevention not only between each network zone
and the Internet, but also between internal network zones. This is performed by enabling intrusion prevention
on inbound and outbound traffic between trusted zones (SonicOS Enhanced).
Extensive Signature Database - SonicWALL IPS utilizes an extensive database of over 1,700 attack and vulnerability signatures written to detect and prevent intrusions, worms, application exploits, as well as peer-topeer and instant messaging traffic. The SonicWALL Deep Packet Inspection engine can also read signatures
written in the popular Snort format, allowing SonicWALL to easily incorporate new signatures as they are published by third parties. SonicWALL maintains a current and robust signature database by incorporating the latest available signatures from thousands of open source developers and by continually developing new
signatures for application vulnerabilities that are not immediately available or provided by open source.
Dynamically Updated Signature Database - SonicWALL IPS includes automatic signature updates delivered
through SonicWALL’s Distributed Enforcement Architecture (DEA), providing protection from emerging
threats and lowering total cost of ownership. Updates to the signature database are dynamic for SonicWALL
firewalls under an active subscription.
Scalable - SonicWALL IPS is a scalable solution for SonicWALL TZ 170 and PRO Series Appliances that
secures small, medium and large networks with complete protection from application exploits, worms and malicious traffic.
Application Control - SonicWALL IPS provides the ability to prevent Instant Messaging and Peer-to-Peer file
sharing programs from operating through the firewall, closing a potential backdoor that can be used to compromise the network while also improving employee productivity and conserving Internet bandwidth.
Simplified Deployment and Management - SonicWALL IPS allows network administrators to quickly and
easily manage the service within minutes. Administrator’s can create global policies between security zones
and interfaces as well as group attacks by priority, simplifying deployment and management across a distributed network.
Granular Policy Management - SonicWALL IPS provides administrators with a range of granular policy
tools to enforce IPS on a global, group, or individual signature level to enable more control and reduce the number of false policies. SonicWALL IPS allows also allows administrators to choose between detection, prevention, or both to tailor policies for their specific network environment.
Logging and Reporting - SonicWALL IPS offers comprehensive logging of all intrusion attempts with the
ability to filter logs based on priority level, enabling administrator’s to highlight high priority attacks. Granular
reporting based on attack source, destination and type of intrusion is available through SonicWALL ViewPoint
Configuring Security Services
245
and Global Management System. A hyperlink of the intrusion brings up the signature window for further information from the SonicWALL appliance log.
• Management by Risk Category - SonicWALL IPS allows you to enable/disable detection or prevention based
on the priority level of attack through High, Medium, or Low predefined priority groups.
• Detection Accuracy - SonicWALL IPS detection and prevention accuracy is achieved minimizing both false
positives and false negatives. Signatures are written around applications, such as Internet Explorer or SQL
Server rather than ports or protocols to ensure that malicious code targeting them are correctly identified and
prevented.
SonicWALL Deep Packet Inspection
Deep Packet Inspection looks at the data portion of the packet. The Deep Packet Inspection technology includes
intrusion detection and intrusion prevention. Intrusion detection finds anomalies in the traffic and alerts the administrator. Intrusion prevention finds the anomalies in the traffic and reacts to it, preventing the traffic from passing
through.
Deep Packet Inspection is a technology that allows a SonicWALL Security Appliance to classify passing traffic
based on rules. These rules include information about layer 3 and layer 4 content of the packet as well as the information that describes the contents of the packet’s payload, including the application data (for example, an FTP session, an HTTP Web browser session, or even a middleware database connection). This technology allows the
administrator to detect and log intrusions that pass through the SonicWALL Security Appliance, as well as prevent
them (i.e. dropping the packet or resetting the TCP connection). SonicWALL’s Deep Packet Inspection technology
also correctly handles TCP fragmented byte stream inspection as if no TCP fragmentation has occurred.
How SonicWALL’s Deep Packet Inspection Architecture Works
Deep Packet Inspection technology enables the firewall to investigate farther into the protocol to examine information at the application layer and defend against attacks targeting application vulnerabilities. This is the technology
behind SonicWALL Intrusion Prevention Service. SonicWALL’s Deep Packet Inspection technology enables
dynamic signature updates pushed from the SonicWALL Distributed Enforcement Architecture.
The following steps describe how the SonicWALL Deep Packet Inspection Architecture works:
1. Pattern Definition Language Interpreter uses signatures that can be written to detect and prevent against known
and unknown protocols, applications and exploits.
2. TCP packets arriving out-of-order are reassembled by the Deep Packet Inspection framework.
3. Deep Packet Inspection engine preprocessing involves normalization of the packet’s payload. For example, a
HTTP request may be URL encoded and thus the request is URL decoded in order to perform correct pattern
matching on the payload.
4. Deep Packet Inspection engine postprocessors perform actions which may either simply pass the packet without modification, or could drop a packet or could even reset a TCP connection.
5. SonicWALL’s Deep Packet Inspection framework supports complete signature matching across the TCP fragments without performing any reassembly (unless the packets are out of order). This results in more efficient
use of processor and memory for greater performance.
246
SonicWALL Global Management System Configuration Guide
If TCP packets arrive out of order, the SonicWALL IPS engine reassembles them before inspection. However, SonicWALL’s IPS framework supports complete signature matching across the TCP fragments without having to perform complete reassembly. SonicWALL’s unique reassembly-free matching solution dramatically reduces CPU and
memory resource requirements.
SonicWALL IPS Terminology
•
•
•
•
•
•
•
Stateful Packet Inspection - looking at the header of the packet to control access based on port, protocol and
IP address.
Deep Packet Inspection - looking at the data portion of the packet. Enables the firewall to investigate farther
into the protocol to examine information at the application layer and defend against attacks targeting application vulnerabilities.
Intrusion Detection - a process of identifying and flagging malicious activity aimed at information technology.
False Positive - a falsely identified attack traffic pattern.
Intrusion Prevention - finding anomalies and malicious activity in traffic and reacting to it.
Snort - an open source network intrusion detection system. SonicWALL IPS includes open-source Snort signatures, as well as signatures from other signature databases, and SonicWALL created signatures. SonicWALL
does not use the Snort engine.
Signature - code written to detect and prevent intrusions, worms, application exploits, and Peer-to-Peer and
Instant Messaging traffic.
Configuring Security Services
247
Configuring Intrusion Prevention Services
The Intrusion Prevention Service (IPS) is a subscription-based service that is frequently updated to protect your networks from new attacks and undesired uses that expose your network to potential risks such as Instant Messaging
(IM) or Peer-to-Peer (P2P) applications.
For information on adding the IPS to SonicWALL appliances, see Chapter 25, “Upgrading SonicWALL Appliances.”
Enabling Intrusion Prevention Services
To configure IPS settings for one or more SonicWALL appliances, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Security Services tree and click Intrusion Prevention. The Intrusion Prevention page appears
(Figure 199).
Figure 199: Intrusion Prevention Page
4. Select the check boxes of the ports to monitor in the IPS Settings area.
5. Configure the following settings for High Priority Attacks in the IPS Settings area:
• To to detect, log, and prevent all high priority attacks, select the Prevent All check box.
• To detect and log all high priority attacks, select the Detect All check box.
• To prevent the log from becoming overloaded with entries for the same attack, enter a value in the Log
Redundancy Filter field. For example, if you entered a value of 30 seconds and there were 100 SubSeven
attacks during that period of time, only one attack would be logged during that 30 second period.
6. Repeat Step 5 for each Medium Priority Attacks, Low Priority Attacks, IM Applications, and P2P Applications.
7. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
8. To configure settings for individual attacks, scroll down to the bottom of the IPS Policies section.
248
SonicWALL Global Management System Configuration Guide
Figure 200: IPS Policy Screen
9. Locate the type of attack that you would like to view. To sort by category, select a category from the Categories
list box. To sort by priority, select a priority level from the Priority list box.
10. After locating a type of attack to configure, click its Configure Icon (
appears.
). The Configure IPS dialog box
Figure 201: Configure IPS Dialog Box
11. Select whether attack detection for this type of attack is enabled, disabled, or uses the default global settings for
the attack category from the Detection list box.
12. Select whether attack prevention for this type of attack is enabled, disabled, or uses the default global settings
for the attack category from the Prevention list box.
13. When you are finished, click Update. You are returned to the Intrusion Prevention page.
14. Repeat Steps 10 through 13 for each attack to edit.
15. To reset all attacks to their default settings, click Reset ALL IPS Settings and Policies.
Configuring Security Services
249
Manual Upload of Keyset and Signature Files
GMS now enables you to manually upload signature files in instances when the Internet is not active on your system. This is useful for SonicWALL security appliances that do not have direct Internet connectivity such as those
deployed in high-security environments. In these situations, GMS retrieves the new signatures and then uploads
them to the SonicWALL security appliance.
To enable manual upload signature files, perform the following steps:
1. Navigate to the Console Panel.
2. Click on the Management menu.
3. Click on the GMS Settings option.
The GMS Settings dialog box displays.
4. Check the following checkbox:
Firewalls managed by this GMS do not have Internet Access - This indicates that the SonicWALL appliances managed by GMS cannot directly reach the Internet.
5. Make sure the following checkbox is not checked:
Automatically upload the latest signatures onto the firewall - By not checking this checkbox, this indicates
that the SonicWALL appliance will not attempt to upload the latest signatures onto the appliance, enabling you
to perform this operation manually.
Note: Note that keyset files will be uploaded at the time of registering a unit or when there is a change in the
user license.
250
SonicWALL Global Management System Configuration Guide
6. Navigate to the System > Tools page to upload keyset and signature files.
7. Click the Upload Signatures Now button.
Configuring Security Services
251
Configuring Global Security Client Security Settings
The Policy Editor and Policy Server architecture introduces the ability to configure client policies through the
SonicWALL GMS. The SonicWALL GMS Administrator defines the remote Distributed Security Client security
policies from the Policy Editor.
These security policies are enforced by the SonicWALL to ensure the remote desktop is secured by the Distributed
Security Client before allowing the VPN connection via the Global VPN Client Enterprise.
Note: You can only create one security policy for all Global Security Clients.
Accessing the Policy Editor
To access the Policy Editor in the SonicWALL Management Interface:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Security Services tree and click Global Security Client. The Global Security Client page appears
(Figure 202).
Figure 202: Global Security Client Page
Note: The Policy Editor button appears only if you have activated your Global Security Client licenses. See the
SonicWALL Global Security Client Administrator’s Guide for more information.
To view the Active policy or the policy that your are editing, click its View button.
252
SonicWALL Global Management System Configuration Guide
Figure 203: Global Security Client Page
Editing a Security Policy
Clicking the Edit button in the Policy Being Edited section of the Global Security Client > Summary page
access the settings for configuring a policy.
Deploying a Security Policy
Once you have configured the security policy for the Distributed Security Clients, you can deploy the policy by
clicking Deploy.
Getting Help
Clicking the ? on the top right of the SonicWALL Management Interface page displays online help for the page.
Configuring the Policy Editor
Defining Basic Settings
To define basic settings, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Security Services tree and click Global Security Client. The Global Security Client page appears
(Figure 204).
Configuring Security Services
253
Figure 204: Global Security Client Page
4. Click Edit.
Figure 205: Global Security Client Page
5. Define how often the SonicWALL appliance will check the policy on all clients in the Policy Polling Frequency field (default: 60 minutes).
6. To configure services settings, click the Configure button in the Services area.
254
SonicWALL Global Management System Configuration Guide
Figure 206: Global Security Client Page
7. Configure the following Security settings:
•
Anti-IP (Anti-IP Spoofing)
IP Spoofing is a process used by hackers to hijack a communication session between two computers. A
hacker can send a data packet that causes Computer A to drop the communication. Then, pretending to be
Computer A, the hacker can communicate with Computer B, thus hijacking a communication session and
attempting to attack Computer B. Anti-IP spoofing foils most IP spoofing attempts by randomizing the
sequence numbers of each communication packet, preventing a hacker from anticipating a packet and intercepting it.
• Anti-MAC (Anti-MAC Spoofing)
Anti-MAC Spoofing is like IP spoofing, hackers can use MAC spoofing to attempt to hijack a communication session between two computers in order to hack one of the machines. MAC (media access control)
addresses are hardware addresses that identify computers, servers, routers, etc. When Computer A wishes
to communicate with Computer B, it may send an ARP (Address Resolution Protocol) packet to the computer. The anti-MAC spoofing feature blocks any ARP packets sent to your computer. This way, hackers
attempting to determine your MAC address will be blocked from doing so. If you request an ARP packet,
SonicWALL Global Security Client will allow it.
•
Port Scanner (Port Scan Detection)
Port scanning is a popular method that hackers use to determine which of your computer’s ports are open to
communication. Ports are dynamically blocked in Global Security Client, and are protected from hacking
attempts. This feature detects if someone is scanning your ports, and notifies you. If disabled, Global Security Client will not detect scans or notify you of them but will still protect your ports from hacking attempts.
•
Stealth (Stealth Mode Browsing)
Stealth mode is a term used to describe a computer that is hidden from other computers while on a network.
A computer on the Internet, for example, if in stealth mode cannot be detected by port scans or communication attempts, such as ping. If you enable this feature, the computer will be invisible to other computer on
any network to which it is connected.
•
Pre-Start
Pre-Start prevents any traffic from entering or leaving your computer during the precious seconds between
the time that you machine turns on and the Distributed Security Client is launched. This time frame is a
small security hole that can allow unauthorized communication. Enabling this feature prevents possible
Trojan Horses or other unauthorized applications from communicating with other computers.
•
NetBIOS Protection
Configuring Security Services
255
NetBIOS Protection blocks all communication from computers located outside of your subnet range. A
subnet is a group of computers that connect to the same gateway. If your computer is located on an office
network, then other computers in your office are most likely on your subnet. If you connect to the Internet
using and ISP, your subnet may be very large. NetBIOS traffic is blocked on UDP ports 88, 137, and TCP
ports 135, 139, 445, and 1026.
Note: Because this option can interfere with the functioning of Windows applications, it is recommended
that only users who have a firm understanding of Windows and DLLs enable this feature.
8. To add an access rule, click the Add button in the Advanced Rules area.
Figure 207: Global Security Client Page
9. Do the following:
• Enter the new rule name in the Name field.
• Select the Protocol option (TCP, UDP, or ICMP) from the Protocol menu.
• Specify the local and/or remote port number or range in the Port/Type field. Separate the beginning and
ending port numbers in a range with a comma.
• Enter the IP address or IP address range in the IP field.
• Select Inbound, Outbound or Both from the Direction menu.
• Select Allow or Block from the Action menu to specify the traffic direction of the filter action.
• Click Apply. The new rule is displayed in the Advanced Rules table in the Global Security Client page
• Repeat this step for each rule to add.
Note: The Advanced Rules table displays all your added rules by Name, Protocol, Port/Type, IP, Direction,
and Action.
10. To block use of specific applications through the VPN connection, scroll down to the application list and select
whether to allow or block each application in the list.
11. To add a new application, enter the executable filename for the application in the Executable Name field, an
optional description of the application in the Description field, and click Add Application. The application is
added to the Applications table.
12. When you are finished, click Apply. The settings are changed for the SonicWALL appliance. To clear all screen
settings and start over, click Cancel.
Creating Groups
To create new groups, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Security Services tree and click Global Security Client. The Global Security Client page appears.
4. Click Edit.
5. Click Add in the Groups area.
256
SonicWALL Global Management System Configuration Guide
Figure 208: Global Security Client Page
6. Enter a name for the group in the Name field.
7. Click Add.
Figure 209: Global Security Client Page
8. Define the criteria that will include or exclude users, hostnames, or IP addresses from the group and click
Apply. You are returned to the previous page and the new criteria appears.
9. Select whether users of this group will be included or excluded from the Distributed Security Client rules.
10. When you are finished, click Apply. The settings are changed for the SonicWALL appliance. To clear all screen
settings and start over, click Cancel.
Configuring Security Services
257
SonicWALL Anti-Spyware Overview
SonicWALL Anti-Spyware is included within the SonicWALL Gateway Anti-Virus (GAV), Anti-Spyware and
Intrusion Prevention Service (IPS) unified threat management solution. SonicWALL GAV,
Anti-Spyware and IPS delivers a comprehensive, real-time gateway security solution for your entire network.
Note: For complete instructions on setting up SonicWALL Anti-Spyware Service, refer to the SonicWALL Anti-Spyware Service Administrator’s Guide available on the SonicWALL Web site
<http://www.sonicwall.com/support/documentation.html>
SonicWALL Anti-Spyware Service
The SonicWALL Anti-Spyware Service protects networks from intrusive spyware by cutting off spyware installations and delivery at the gateway and denying previously installed spyware from communicating collected information outbound. SonicWALL Anti-Spyware works with other anti-spyware program, such as programs that remove
existing spyware applications from hosts. You are encouraged to use or install host-based anti-spyware software as
an added measure of defense against spyware.
SonicWALL Anti-Spyware analyzes inbound connections for the most common method of spyware delivery,
ActiveX-based component installations. It also examines inbound setup executables and cabinet files crossing the
gateway, and resets the connections that are streaming spyware setup files to the LAN. These file packages may be
freeware bundled with adware, keyloggers, or other spyware. If spyware has been installed on a LAN workstation
prior to the SonicWALL Anti-Spyware solution install, the service will examine outbound traffic for streams originating at spyware infected clients and reset those connections. For example, when spyware has been profiling a
user's browsing habits and attempts to send the profile information home, the SonicWALL security appliance identifies that traffic and resets the connection.
The SonicWALL Anti-Spyware Service provides the following protection:
•
•
•
•
•
258
Blocks spyware delivered through auto-installed ActiveX components, the most common vehicle for distributing malicious spyware programs.
Scans and logs spyware threats that are transmitted through the network and alerts administrators when new
spyware is detected and/or blocked.
Stops existing spyware programs from communicating in the background with hackers and servers on the Internet, preventing the transfer of confidential information.
Provides granular control over networked applications by enabling administrators to selectively permit or deny
the installation of spyware programs.
Prevents e-mailed spyware threats by scanning and then blocking infected e-mails transmitted either through
SMTP, IMAP or Web-based e-mail.
SonicWALL Global Management System Configuration Guide
SonicWALL Gateway Anti-Virus, Anti-Spyware and
Intrusion Prevention Security Services
•
•
•
•
•
•
•
•
•
•
•
•
•
•
•
Integrated Deep Packet Inspection Technology - features a configurable, high-performance Deep Packet
Inspection architecture that uses parallel searching algorithms up through the application layer to deliver complete application layer, Web and e-mail attack prevention. Parallel processing reduces the impact on the processor and maximizes available memory for exceptional performance on SonicWALL appliances.
Spyware Protection - prevents malicious spyware from infecting networks by blocking spyware installations
at the gateway and disrupts background communications from existing spyware programs that transmit confidential data.
Real-Time AV Gateway Scanning - delivers intelligent file-based virus and malicious code prevention by
scanning in real-time for decompressed and compressed files containing viruses, Trojans, worms and other
Internet threats over the corporate network.
Powerful Intrusion Prevention - delivers complete protection from a comprehensive array of network-based
application layer threats by scanning packet payloads for worms, Trojans, software vulnerabilities such as
buffer overflows, peer-to-peer and instant messenger applications, backdoor exploits, and other malicious code.
Scalability and Performance - utilitizes a per packet scanning engine, allowing the SonicWALL unified threat
management solution to handle unlimited file size and virtually unlimited concurrent downloads.
Day Zero Protection - ensures fast time-to-protection by employing a dynamically updated database of signatures created by a combination of SonicWALL’s SonicAlert Team and third-party sources.
Extensive Signature List - utilizes an extensive database of thousands of attack and vulnerability signatures
written to detect and prevent intrusions, viruses, spyware, worms, Trojans, application exploits, and malicious
applications.
Distributed Enforcement Architecture - utilizes a distributed enforcement architecture to deliver automated
signature updates, providing real-time protection from emerging threats and lowering total cost of ownership.
Inter-zone Protection - provides application layer attack protection against malicious code and other threats
originating from the Internet or from internal sources. Administrators have the ability to enforce intrusion prevention and anti-virus scanning not only between each network zone and the Internet, but also between internal
network zones for added security (Requires SonicOS Enhanced).
Advanced File Decompression Technology - includes advanced decompression technology that can automatically decompress and scan files on a per packet basis to search for viruses, Trojans, worms and malware. Supported compression formats include: ZIP, Deflate and GZIP.
File-Based Scanning Protocol Support - delivers protection for high threat viruses and malware by inspecting
the most common protocols used in today’s networked environments, including SMTP, POP3, IMAP, HTTP,
FTP, NETBIOS, instant messaging and peer-to-peer applications, and dozens of other stream-based protocols.
This closes potential back doors that can be used to compromise the network while also improving employee
productivity and conserving Internet bandwidth.
Application Control - provides the ability to prevent instant messaging and peer-to-peer file sharing programs
from operating through the firewall, closing a potential back door that can be used to compromise the network
while also improving employee productivity and conserving Internet bandwidth.
Simplified Deployment and Management - allows network administrators to create global policies between
security zones and group attacks by priority, simplifying deployment and management across a distributed network.
Granular Management - provides an intuitive user interface and granular policy tools, allowing network
administrators to configure a custom set of detection or prevention policies for their specific network environment and reduce the number of false policies while identifying immediate threats.
Logging and Reporting - offers comprehensive logging of all intrusion attempts with the ability to filter logs
based on priority level, enabling administrators to highlight high priority attacks. Granular reporting based on
attack source, destination and type of intrusion is available through SonicWALL ViewPoint and Global Management System.
Configuring Security Services
259
Activating the SonicWALL Anti-Spyware License
If you do not have SonicWALL Gateway Anti-Virus, Anti-Spyware, and Intrusion Prevention Service installed on
your SonicWALL security appliance, the Security Services > Anti-Spyware page indicates an upgrade is required
and includes a link to activate it from your SonicWALL security appliance management interface.
SonicWALL Anti-Spyware is part of the unified SonicWALL Gateway Anti-Virus, Anti-Spyware, and Intrusion
Prevention Service, so you use a single parent License Key to activate all three services on your SonicWALL security appliance. You activate the SonicWALL Gateway Anti-Virus, Anti-Spyware, and Intrusion Prevention Service
parent license for SonicWALL Intrusion Prevention Service first from the Security Services > Intrusion Prevention page. Once you have activated Intrusion Prevention Service, you can then activate SonicWALL Gateway AntiVirus and SonicWALL Anti-Spyware.
To activate a SonicWALL Gateway Anti-Virus, Anti-Spyware, and Intrusion Prevention Service on your SonicWALL security appliance, you need the following:
SonicOS Standard 3.1 or SonicOS Enhanced 3.1. Your SonicWALL security appliance must be running
SonicOS Standard 3.1 or SonicOS Enhanced 3.1 for SonicWALL Gateway Anti-Virus,
Anti-Spyware, and Intrusion Prevention Service. If you do not have SonicOS 3.1 installed on your SonicWALL
security appliance, refer to the SonicOS Standard or Enhanced Administrator’s Guide available on the SonicWALL Web site <http://www.sonicwall.com/support/documentation.html> for SonicOS upgrade instructions.
• mySonicWALL.com account. A mySonicWALL.com account allows you to manage your SonicWALL products. You need to register your SonicWALL security appliance to activate SonicWALL security services. Creating a mySonicWALL.com is fast, simple, and FREE. Simply complete an online registration form directly from
your SonicWALL security appliance management interface. Your mySonicWALL.com account is also accessible at
<https://www.mysonicwall.com> from any Internet connection with a Web browser.
• Registered SonicWALL Security Appliance with Active Internet Connection. Registering your SonicWALL security appliance is a simple procedure done directly from the management interface. Once your
SonicWALL security appliance is registered, you can activate your SonicWALL security service using an activation key.
• SonicWALL Gateway Anti-Virus, Anti-Spyware, and Intrusion Prevention Service License. You need to
purchase a SonicWALL Gateway Anti-Virus, Anti-Spyware, and Intrusion Prevention Service license from a
SonicWALL reseller or through your mySonicWALL.com account (limited to customers in the USA and Canada). After purchasing the license, you are provided with an Activation Key. You use this Activation Key to
activate the service on your SonicWALL security appliance.
•
Tip: If your SonicWALL security appliance is connected to the Internet and registered at mySonicWALL.com, you
can activate a 30-day FREE TRIAL of SonicWALL Gateway Anti-Virus, SonicWALl Anti-Virus, and SonicWALL
Intrusion Prevention Service separately from the Security Services > Gateway Anti-Virus, Security Services >
Anti-Spyware, and Security Services > Intrusion Prevention pages in the management interface.
260
SonicWALL Global Management System Configuration Guide
Setting Up SonicWALL Anti-Spyware Protection
Activating the SonicWALL Anti-Spyware license on your SonicWALL security appliance does not automatically
enable the protection. To configure SonicWALL Anti-Spyware to begin protecting your network, you need to perform the following steps:
1. Enable SonicWALL Anti-Spyware
2. Specify Spyware Danger Level Protection
3. Apply SonicWALL Anti-Spyware Protection to Zones
Note: For complete instructions on setting up SonicWALL Anti-Spyware Service, refer to the SonicWALL Anti-Spyware Service Administrator’s Guide available on the SonicWALL Web site
<http://www.sonicwall.com/support/documentation.html>
Once you configured these basic anti-spyware protection settings, you can perform additional configuration options
to tailor SonicWALL Spyware protection for your network environment.
Selecting Security Services > Anti-Spyware displays the configuration settings for SonicWALL Anti-Spyware on
your SonicWALL security appliance. The Anti-Spyware page for the SonicOS Enhanced is divided into three sections:
Configuring Security Services
261
The Anti-Spyware page for the SonicOS Standard contains extra checkboxes.
•
Anti-Spyware Status - displays status information on the state of the signature database, your SonicWALL
Anti-Spyware license, and other information.
• Anti-Spyware Global Settings - provides the key settings for enabling SonicWALL Anti-Spyware on your
SonicWALL security appliance, specifying global SonicWALL Anti-Spyware protection based on three classes
of spyware, and other configuration options.
• Anti-Spyware Signatures - shows the status and contents of your signature database.
Warning: After activating your SonicWALL Anti-Spyware license, you must enable and configure SonicWALL Anti-Spyware on the SonicWALL management interface to before anti-spyware policies are applied
to your network traffic.
262
SonicWALL Global Management System Configuration Guide
Enabling SonicWALL Anti-Spyware
SonicWALL Anti-Spyware must be globally enabled on your SonicWALL security appliance. Select the Enable
Anti-Spyware check box (a checkmark is displayed), and then click Configure Anti-Spyware Settings to apply
the settings.
Checking the Enable Anti-Spyware check box does not automatically start SonicWALL Anti-Spyware protection.
You must also specify a Prevent All action in the Signature Groups table to activate anti-spyware on the SonicWALL security appliance, and then specify the zones you want to protect on the Network > Zones page. You can
also select Detect All for spyware event logging and alerting.
Specifying Spyware Danger Level Protection
SonicWALL Anti-Spyware allows you to globally manage your network protection against attacks by simply
selecting the class of attacks: High Danger Level Spyware, Medium Danger Level Spyware and Low Danger
Level Spyware.
Selecting the Prevent All and Detect All check boxes for High Danger Level Spyware and Medium Danger
Level Spyware in the Signature Groups table, and then clicking Apply protects your network against the most
dangerous spyware.
Warning: SonicWALL recommends enabling Prevent All for High Danger Level Spyware and Medium Danger
Level Spyware signature groups to provide anti-spyware protection against the most damaging and disruptive spyware applications. You can also enable Detect All for spyware logging and alerting.
SonicWALL Anti-Spyware also allows you to configure anti-spyware policies at the category and signature level to
provide flexible granularity for tailoring SonicWALL Anti-Spyware protection based on your network environment
requirements. If you’re running SonicOS Enhanced, you can apply these custom SonicWALL Anti-Spyware policies to Address Objects, Address Groups, and User Groups, as well as create enforcement schedules. For more
information, refer to the SonicWALL Anti-Spyware Administrator’s Guide available on the SonicWALL Web site
<http://www.sonicwall.com/support/documentation>
Applying SonicWALL Anti-Spyware Protection to Zones (Enhanced)
For SonicWALL security appliances running SonicOS Enhanced 3.0, you apply SonicWALL Anti-Spyware to
Zones on the Network > Zones page to enforce SonicWALL Anti-Spyware not only between each network zone
and the WAN, but also between internal zones. For example, enabling SonicWALL Anti-Spyware on the LAN zone
enforces SonicWALL Anti-Spyware on all incoming and outgoing LAN traffic.
In the Anti-Spyware Status section of the Security Services > Anti-Spyware page, click the Network > Zones
link to access the Network > Zones page or select the Network > Zones page. You apply SonicWALL Anti-Spyware policies to a zone listed on the Network > Zones page.
To enable SonicWALL Anti-Spyware on a zone, perform these steps:
Configuring Security Services
263
1. In the SonicWALL security appliance management interface, select Network > Zones or from the Anti-Spyware Status section, on the Security Services > Anti-Spyware page, click the Network > Zones link. The
Network > Zones page is displayed.
2. In the Configure column in the Zone Settings table, click the edit icon
for the zone you want to apply
SonicWALL IPS. The Edit Zone window is displayed.
3. Click the Enable Anti-Spyware Service checkbox. A checkmark appears. To disable SonicWALL Anti-Spyware Service, uncheck the box.
4. Click OK.
You also enable SonicWALL IPS protection for new zones you create on the Network > Zones page. Clicking the
Add button displays the Add Zone window, which includes the same settings as the Edit Zone window.
Configuring the Anti-Spyware Category
SonicWALL Anti-Spyware also allows you to configure anti-spyware policies at the category and signature level to
provide flexible granularity for tailoring SonicWALL Anti-Spyware protection based on your network environment
requirements. If you are using GMS to configure a device that runs SonicOS Enhanced, you can apply these custom
SonicWALL Anti-Spyware policies to Address Objects, Address Groups, and User Groups, as well as create
264
SonicWALL Global Management System Configuration Guide
enforcement schedules. For more information, refer to the SonicWALL Anti-Spyware Administrator’s Guide available on the SonicWALL Web site http://www.sonicwall.com/support/documentation.
Configure the fields in the Anti-Spyware Product Settings dialog box as described in the following
table.
Field
Description
Prevention
Allows you to enable and disable intrusion prevention for the device.
Detection
Allows you to enable and disable intrusion detection for the device.
Included Users/Groups
Applies the anti-spyware settings to members of the following group
types: All, Administrators, Everyone, Guest Services, Trusted Users,
Content Filtering Bypass, and Limited Administrators.
Excluded Users/Groups
Does not apply the anti-spyware settings to members of the following
group types: All, Administrators, Everyone, Guest Services, Trusted
Users, Content Filtering Bypass, and Limited Administrators.
Included IP Address Range Allows you to apply the anti-spyware settings to all users that fall within
a specified IP address range of a specified category. For more details on
the categories, see the table below.
Configuring Security Services
265
For a bird’s eye view of the categories, refer to the following figure.
Configuring Signature Settings
Additionally, you can configure signature settings for Anti-Spyware. SonicWALL Gateway Anti-Virus, Anti-Spyware and Intrusion Service are applied to both inbound and outbound traffic, because signatures are written directionally. That is, the direction of the attack is considered when applying protection on a SonicWALL security
appliance.
For example, the Sasser worm. SonicWALL signatures were written to examine different stages and directions of
this complex attack. One signature looked for a NetBIOS buffer overflow attack that uses the common NetBIOS
ports as an exploit. This SonicWALL signature is applied inbound between zones (SonicOS Enhanced) and interfaces (SonicOS Standard) from the Internet, effectively stopping the proliferation of the exploit from the external
network. After the initial exploit, the Sasser worm attempts to download the main part of its program through an
FTP session out to the Internet.
Another SonicWALL signature automatically prevents Sasser from establishing an outbound FTP session to the
Internet, and it may be applied to each zone or interface.
SonicWALL Gateway Anti-Virus, Anti-Spyware and Instrusion Prevention Service does not require you to understand what signatures are applied in what directions. You simply select predefined groups based on the severity of
the attacks or the danger level of the spyware.
To configure Anti-Spyware Signature Settings, perform the following steps:
1. Click on the Configure icon in a product row (for example, the 123 Search row) in the signature list of the AntiSpyware dialog box.GMS displays the Edit Anti-Spyware Signature dialog box.
266
SonicWALL Global Management System Configuration Guide
2. Provide settings for the fields in the dialog box as described in the following table:
Field
Description
Prevention
Allows you to enable and disable intrusion prevention for signatures to
the device.
Detection
Allows you to enable and disable intrusion detection for signatures for the
device.
Included Users/Groups
Applies the anti-spyware settings to members of the following group
types: All, Administrators, Everyone, Guest Services, Trusted Users,
Content Filtering Bypass, and Limited Administrators for signatures to
the device.
Excluded Users/Groups
Does not apply the anti-spyware settings to members of the following
group types: All, Administrators, Everyone, Guest Services, Trusted
Users, Content Filtering Bypass, and Limited Administrators for
signatures to the device.
Included IP Address Range Allows you to apply the anti-spyware settings to all users that fall within
a specified IP address range of a specified category. For more details on
the categories, see the table above.
Configuring Security Services
267
Licenses and Subscription Search Capability
The GMS now offers administrators a single search function for conducting a wide range of searches, such as lists
of users with no subscriptions or expiring subscriptions. Such searches provide a strong source for pinpointing
users who would be interested in purchasing new licenses and subscriptions.
The user can enter any string, and GMS will search the entire database and provide links to the firewall, and the
specific screens within GMS that has that information. The output can create a list of firewalls in their GMS that are
registered or have a subscription expiring in a variable number of days. A user can narrow down the search to the
node that is selected in the leftmost listbox.
There are three types of criteria entries a user can select in the left-most listbox.
Registration Status - When this is selected, the user can further narrow down the search so that only the Registered
or Not Registered firewalls list is displayed.
Subscription Services - These are the security services that can be renewed once the subscription has expired, such
as Anti-Spyware, etc. A special entry, “Any Subscription Service” allows the user to search against any such service. When a subscription service is selected, then the user can search against services with the following attributes:
•
•
•
•
•
Current subscription
Free-trial subscription
Expired subscription
Services that were never subscribed for
Any subscription status
Upgrade Services - These are non-subscription based services, such as Node Upgrade, etc. A special entry, Any
Upgrade, lets the user search against any upgrade. The upgrade status that a user can search against includes services that fall into one of the following upgrade categories:
•
•
•
Upgraded
Not upgraded
Any upgrade status
Depending on the kind of upgrade service, the user can optionally search against the number of nodes or users that
the service has been upgraded for (for example, VPN SA, etc.) When the search results in one or more firewalls,
then a number of useful columns are displayed in the search section in the same screen. The user can then click on
the header columns of the table display to sort the data in ascending or descending order.
A print button is available that prints an administrative report from GMS displaying all managed devices and their
current licenses with expiration dates.
To access this search tool, perform the following steps:
1. Navigate to the Policies Panel.
2. Click on the Register/Upgrades menu.
3. Click the Search option.
GMS displays the Search dialog box.
268
SonicWALL Global Management System Configuration Guide
4. Click on the Registration listbox and select a registration type.
5. Click the Subscription Status list box and select a subscription type.
6. Specify an expiration date for the subscription in the format MM/DD/YY.
7. Click Search.
Example: As an example, if you chose CFS Premium Service in the Subscription listbox and selected with any
Subscription Status in the Subscription Status listbox, you might see output that resembles the following.
Note the columns:
Column
Description
#
The number of the appliance that contains the specified
subscription service.
Security Service
The name of the subscription service.
Appliance Name
The name of the appliance.
Serial
The serial number of the appliance.
Configuring Security Services
269
270
Column
Description
Subscription Status
The type of subscription that exists. Subscriptions
can be one of the following types:
Expiry Date
The date the subscription runs out.
Nodes/Users
The nodes or users that are members of the
subscription.
SonicWALL Global Management System Configuration Guide
Licenses and Subscription Search Capability
The GMS now offers administrators a single search function for conducting a wide range of searches, such as lists
of users with no subscriptions or expiring subscriptions. Such searches provide a strong source for pinpointing
users who would be interested in purchasing new licenses and subscriptions.
The user can enter any string, and GMS will search the entire database and provide links to the firewall, and the
specific screens within GMS that has that information. The output can create a list of firewalls in their GMS that are
registered or have a subscription expiring in a variable number of days. A user can narrow down the search to the
node that is selected in the leftmost listbox.
There are three types of criteria entries a user can select in the left-most listbox.
Registration Status - When this is selected, the user can further narrow down the search so that only the Registered
or Not Registered firewalls list is displayed.
Subscription Services - These are the security services that can be renewed once the subscription has expired, such
as Anti-Spyware, etc. A special entry, “Any Subscription Service” allows the user to search against any such service. When a subscription service is selected, then the user can search against services with the following attributes:
•
•
•
•
•
Current subscription
Free-trial subscription
Expired subscription
Services that were never subscribed for
Any subscription status
Upgrade Services - These are non-subscription based services, such as Node Upgrade, etc. A special entry, Any
Upgrade, lets the user search against any upgrade. The upgrade status that a user can search against includes services that fall into one of the following upgrade categories:
•
•
•
Upgraded
Not upgraded
Any upgrade status
Depending on the kind of upgrade service, the user can optionally search against the number of nodes or users that
the service has been upgraded for (for example, VPN SA, etc.) When the search results in one or more firewalls,
then a number of useful columns are displayed in the search section in the same screen. The user can then click on
the header columns of the table display to sort the data in ascending or descending order.
A print button is available that prints an administrative report from GMS displaying all managed devices and their
current licenses with expiration dates.
To access this search tool, perform the following steps:
1. Navigate to the Policies Panel.
2. Click on the Register/Upgrades menu.
3. Click the Search option.
GMS displays the Search dialog box.
Configuring Security Services
271
4. Click on the Registration listbox and select a registration type.
5. Click the Subscription Status list box and select a subscription type.
6. Specify an expiration date for the subscription in the format MM/DD/YY.
7. Click Search.
Example: As an example, if you chose CFS Premium Service in the Subscription listbox and selected with any
Subscription Status in the Subscription Status listbox, you might see output that resembles the following.
Note the columns:
272
Column
Description
#
The number of the appliance that contains the specified
subscription service.
Security Service
The name of the subscription service.
Appliance Name
The name of the appliance.
Serial
The serial number of the appliance.
SonicWALL Global Management System Configuration Guide
Column
Description
Subscription Status
The type of subscription that exists. Subscriptions
can be one of the following types:
Expiry Date
The date the subscription runs out.
Nodes/Users
The nodes or users that are members of the
subscription.
Configuring Security Services
273
274
SonicWALL Global Management System Configuration Guide
CHAPTER 20
Configuring Hardware Failover Settings
The hardware failover feature configures a pair of SonicWALL PRO or PRO-VX appliances as a primary and
backup. The backup monitors the primary through a series of heartbeats. If the backup detects that the primary is
unavailable or has failed, it will replace the primary.
This chapter describes how to use the SonicWALL Global Management System (SonicWALL GMS) to configure
hardware failover.
To configure hardware failover, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Hardware Failover tree and click Configure. The Configure page appears (Figure 210).
Figure 210: Configure Page
4. Enter the LAN (WorkPort) and WAN IP addresses of the primary.
5. Select the Enable Hardware Failover check box.
6. Enter the serial number of the backup.
7. Enter the LAN (WorkPort) and WAN IP addresses of the backup SonicWALL appliance.
8. To configure the primary SonicWALL appliance to take over from the backup SonicWALL appliance when it
becomes available, select the Preempt Mode check box. Otherwise, the backup SonicWALL appliance will
remain active.
9. Enter the heartbeat interval (in seconds) in the Heartbeat Interval field.
Configuring Hardware Failover Settings
275
10. When a SonicWALL appliance becomes active after startup, it looks for an active SonicWALL appliance that is
configured for hardware failover. If the other appliance is active, it transitions to Idle mode. Sometimes, due to
network latency and other issues, it may take a while to find the other SonicWALL appliance.
To specify how long the SonicWALL appliance will look, enter the number of seconds in the Detection Delay
Time field. You can enter a value between 0 and 300 seconds, but the default value of 0 seconds is sufficient in
most cases.
11. Specify how long the backup waits before replacing the primary (in seconds) in the Failover Trigger Level
field.
12. When changes are made to the Primary or Backup firewall, the changes are automatically synchronized
between the two firewalls. To cause the synchronization to occur now, click Synchronize Now. The Backup
SonicWALL will restart and become temporarily unavailable while it updates its settings.
Note: If you change the IP address of either SonicWALL appliance, synchronization cannot occur between the
two SonicWALL appliances without updating the changes manually on the Hardware Failover page.
13. When you are finished, click Update. The settings are changed for each selected SonicWALL appliance. To
clear all screen settings and start over, click Reset.
276
SonicWALL Global Management System Configuration Guide
CHAPTER 21
Configuring Web Filters
(Content Security Manager 2100 CF)
SonicWALL Content Security Manager 2100 CF provides appliance-based Internet filtering that enhances security
and employee productivity, optimizes network utilization, and mitigates legal liabilities by managing access to
objectionable and unproductive Web content. This chapter provides configuration tasks for deploying these
services.
This chapter contains the following sections:
•
•
•
•
•
•
Configuring Settings—see “Configuring Settings” on page 278.
Configuring Policy Groups—see “Configuring Policy Groups” on page 279.
Configuring Policies—see “Configuring Policies” on page 281.
Configuring Custom Policies—see “Configuring Custom Categories” on page 281.
Configuring Privacy Prevention—see “Configuring Privacy Prevention” on page 283.
Configuring a Custom Block Page—see “Configuring Custom Block Page” on page 284.
Configuring Web Filters (Content Security Manager 2100 CF)
Web Filters includes settings for configuring Internet filtering on the SonicWALL Content Security Manager
2100 CF.
To configure Web Filters, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL Content Security Manager 2100 CF appliance.
3. Expand the Web Filters tree.
Configuring Web Filters (Content Security Manager 2100 CF)
277
Figure 211: Web Filters
Configuring Settings
The Settings page provides information on the status of filtering subscription service updates, settings for enabling
filtering, managing the behavior of the Dynamic Rating engine, adding IP addresses to exclude from filtering, and
access to URL ratings with the SonicWALL Content Filtering Service database.
Figure 212: Settings
278
SonicWALL Global Management System Configuration Guide
Settings
• Enable Web Filtering - enables Web Filtering on the SonicWALL Content Security Manager.
• URL Cache Size (KBs) - specifies the URL Cache size on the SonicWALL Content Security Manager. The
default value is 5120 KBs. A larger URL Cache size can provide noticeable improvements in Internet browsing
response times.
• Use Dynamic Rating - enables the use of the Content Security Manager’s integrated dynamic rating engine
that allows an unrated URL to be dynamically rated in real-time.
• Dynamic Rating Settings - the Optimize for speed setting instructs the dynamic rating engine to process less
information for faster ratings with the trade off of less accuracy. The Optimize for accuracy setting instructs
the dynamic rating engine to process more information resulting in slower ratings with the trade off of more
accuracy.
• Suppress Compressed Server Responses - selecting this setting blocks URLs from Web sites that compressed
content.
IP Address Exclusion List
The IP Address Exclusion List allows you specify an IP address or IP address range on your network that are
excluded from any SonicWALL Content Security Manager filtering.
To add an IP address or IP address range:
1. To specify a single IP address, enter the IP address in the IP Address Begin and in the IP Address End fields.
2. To specify an IP address range, enter the starting IP address in the IP Address Begin field and the ending IP
address in the IP Address End field.
3. Click the Add.
4. If you selected other settings for the IP Address Exclusion List, click Update.
URL Rating Review
Clicking the here link displays the same CFS URL Rating Review Request page that displays when you click the
URL Rating Review button.
Configuring Policy Groups
The Policy Groups page is where you define policy groups by assembling default content filter and custom categories into unique policies that are applied to users and groups. The *Default policy group is the baseline policy that
cannot be removed but you can modify the policies it includes. You define what default categories are included in a
policy group on the Policies page. Once you create policies in the Policies page, you can assemble them into policy
groups in the Policy Groups page.
Configuring Web Filters (Content Security Manager 2100 CF)
279
Figure 213: Policy Groups
Policy Groups Table
The Policy Group table displays the following information about the *Default policy group and your custom policy
groups:
Name - The name of the policy group.
Type - Displays Policy Group or Policy. Clicking the + button expands the policy group to display the policies included in the group.
• Comment - Displays a caption icon. When you move the pointer over the icon, the comment text is displayed. The comment text is entered in the Add Policy Group window.
• Schedule - Displays the Schedule icon for policies and custom policy groups indicating the policy has a
schedule activation time.
• Configure - Includes the edit icon, which displays the Edit Policy Group window, and the Delete icon for
removing the policy group. The Delete icon is dimmed for the *Default policy group only.
•
•
Clicking the + button expands the policy group to display the policies included in the group.
Clicking the Restore Defaults button removes all custom policies and any policies you added to the *Default
policy group.
Clicking Add Policy Group window displays the Add Web Filter Policy Group window for adding new policies.
Modifying the *Default Policy Group
1. Click the edit (notepad) icon under Configure in the *Default policy group row of the Policy Groups table.
The Edit Web Filter Policy Group window is displayed.
2. The Name field displays the *Default entry, which can be renamed. You must add descriptive text up to 63
characters in length in the Comment field. The Comment field cannot be left blank.
3. Click the Policies tab.
4. Select the policy categories you want to add to the *Default policy group. Select the Name column to select all
the categories. If you want to remove any policies, uncheck the policy. Uncheck the Name column to unselect
all the policies.
5. Click OK.
280
SonicWALL Global Management System Configuration Guide
Configuring Policies
The Policies page allows you create and edit policies that are used to create policy groups, which in turn are applied
to user groups.
Figure 214: Policies
Policies Table
The Policies table initially lists the default 12 predefined policy groups. Clicking the + button expands the list to
display every policy under the policy group.
As you create custom policies, they are displayed in the table. The Policies table displays the following information
about each policy:
Name - The name of the policy.
Type - Displays Policy or Default Category. Clicking the + button expands the policy group to display the
policies included in the group.
• Comment - Displays a caption icon. When you move the pointer over the icon, the comment text is displayed. The comment text is entered in the Add Policy or Edit Policy window.
• Schedule - Displays the Schedule icon for policies and custom policy groups indicating the policy has a
schedule activation time.
• Configure - Includes the edit icon that displays the Edit Policy window, and the delete icon. The Delete
icon is dimmed for the *Default policy and for the pre-defined policy groups.
•
•
Clicking the + button expands the policy group to display the policies included in the group.
Clicking the Restore Defaults button removes all custom policies and any policies you added to the *Default
policy.
Clicking Add Policy button displays the Add Web Filter Policy window for adding new policies.
Configuring Custom Categories
The Custom Categories page allows you to create custom policies that can incorporate untrusted urls and domains,
untrusted keywords, and trusted urls and domains.
Configuring Web Filters (Content Security Manager 2100 CF)
281
Figure 215: Custom Categories
Untrusted URLs
Untrusted URLs allows you to specify URLs that you want to selectively block or allow with logging of the action
by the Content Security Manager. You add Untrusted URLs to policies in the Web Filters > Policies page.
The Untrusted URLs table displays the names of the Untrusted URLs categories you create, any optional comments added when you create the category are displayed in the Comment column, and the Configure column with
the Edit icon for accessing the Edit Untrusted URLs window and the Delete icon.
You have two available actions for Untrusted URLs categories in policies: Block and Log Only, which you specify in the Web Filters > Policies page. Log Only allows users to access the URLs in the Untrusted URLs category
but logs each access event in the Content Security Manager log.
Untrusted Keywords
Untrusted Keywords allows you to specify keywords that are substrings of URLs, which allows you to employ
stricter filtering, blocking sites whose URLs contain specific words.
The Untrusted Keywords table displays the names of the Untrusted Keywords categories you create, any
optional comments added when you create the category are displayed in the Comments column, and the Configure
column with the Edit icon for accessing the Edit Untrusted Keywords window and the Delete icon.
You have two available actions for Untrusted Keywords categories in policies: Block and Log Only, which you
specify in the Web Filters > Policies page. Log Only allows users to access the URLs in the URLs category but
logs each access event in the Content Security Manager log.
Trusted URLs
Trusted URLs allows you to specify URLs that are always allowed.
The Trusted URLs table displays the names of the Trusted URLs categories you create, any optional comments
added when you create the category is displayed in the Comment column, and the Configure column with the Edit
icon for accessing the Edit Trusted URLs window and the Delete icon.
You have one available action for Trusted URLs categories in policies: Allow, which is specified in the
Web Filters > Policies page.
282
SonicWALL Global Management System Configuration Guide
Configuring Privacy Prevention
The Privacy Prevention page allows you to enhance your network security by blocking potentially harmful
applications from entering your network.
Figure 216: Privacy Protection
Privacy Threats
Privacy Threats compromises Block Cookies, Block ActiveX, Block HTTP Proxy Server, and Block
Fraudulent Certificates. These settings are always activated as Block and cannot be deleted or modified.
Block Cookies - Cookies are used by Web servers to track Web usage and remember user identity. Cookies
can also compromise users' privacy by tracking Web activities.
• Block ActiveX - ActiveX is a programming language that embeds scripts in Web pages. Malicious programmers can use ActiveX to delete files or compromise security.
• Block HTTP Proxy Servers - When a proxy server is located on the external interface, users can circumvent content filtering by pointing their computer to the proxy server.
• Block Fraudulent Certificates - Digital certificates help verify that Web content and files originated from
an authorized party. Enabling this feature protects users on the LAN from downloading malicious programs
warranted by these fraudulent certificates. If digital certificates are proven fraudulent, then the SonicWALL
Content Security Manager blocks the Web content and the files that use these fraudulent certificates.
Known fraudulent certificates blocked by SonicWALL Content Security Manager include two certificates
issued on January 29 and 30, 2001 by VeriSign to an impostor masquerading as a Microsoft employee.
•
Untrusted File Types
These are groupings of file extensions used for similar purposes. SonicWALL Content Security Manager allows
you to filter Internet content based on file extension. For example, you can restrict access to particular types of files
from sites within an otherwise permitted. File type filtering is activated via policies. SonicWALL provides several
predefined file types for use in filtering. You can modify these, or create new file types to suit your needs.
Untrusted File Types compromises of Java Applets, Executable Files, Video Files, Audio Files, and user specified file types by extension. You have two available actions for Untrusted File Type categories in policies: Block
and Log Only, which you specify in the Web Filters > Policies page. Log Only allows users to access the file types
in the Untrusted File Types category but logs each access event in the Content Security Manager log.
Configuring Web Filters (Content Security Manager 2100 CF)
283
The Untrusted File Types table displays the names of the default Untrusted File Types categories and the ones
you create, any optional comments added when you create the category are displayed in the Comment column, and
the Configure column with the Edit icon for accessing the Edit Untrusted File Types window and the Delete icon.
Privacy Threat Exclusion List
The Privacy Threat Exclusion List is a list of domains that act as an exclusion list for Privacy Threats. Domains
specified in the Privacy Threat Exclusion List cannot act upon any other class.
Only a single Privacy Threat Exclusion List can be specified, but it can be shared among multiple policies.
The Trusted Domains includes Web sites your trust, which are sites that you believe users can access without damaging your network or data. Cookies, ActiveX, Java and all other file types specified in the Untrusted File Types
categories are not blocked for these sites.
The Privacy Threat Exclusion List table displays only the Privacy Threat Exclusion List category, any optional
comments added when you create the Edit Privacy Threat Exclusion List window is displayed in the Comment
column, and the Configure column with the Edit icon for accessing the Edit Privacy Threat Exclusion List window and the Delete icon.
You have one available action for the Privacy Threat Exclusion List in policies: Trusted, which is specified in the
Web Filters > Policies page.
Configuring Custom Block Page
The Custom Block Page allows you to enter your customized text to display to the user when access to a blocked
site is attempted. Any message, including embedded HTML, can be entered in this field.
Figure 217: Custom Block Page
Message to Display when Blocking
Enter your customized text to display to the user when access to a blocked site is attempted. The default message is
This site is blocked by the SonicWALL Content Filter Service. Any message, including embedded HTML, up to
255 characters long, can be entered in this field.
You can select a background color for the pop-up window from the Background Color menu.
284
SonicWALL Global Management System Configuration Guide
Click Preview to display your pop-up window. A Web page is displayed in your browser with your blocked site
text. Clicking the Click here to bookmark URL link saves the URL of your page. Click the Go Back button to
return to the management interface.
Configuring Web Filters (Content Security Manager 2100 CF)
285
286
SonicWALL Global Management System Configuration Guide
CHAPTER 22
Configuring SonicPoints
This chapter describes how to configure SonicPoint managed secure wireless access points.
1. Start and log into SonicWALL GMS.
2. Select a wireless SonicWALL appliance.
3. Expand the SonicPoints tree and click Settings. The Settings page appears (Figure 218).
Managing SonicPoints
SonicWALL SonicPoints are wireless access points specially engineered to work with SonicWALL security appliances running SonicOS Enhanced 2.5 or greater to provide wireless access throughout your enterprise.
The SonicPoint section of GMS lets you manage the SonicPoints connected to your system.
Figure 218: SonicPoints > Settings Page
Before Managing SonicPoints
Before you can manage SonicPoints in GMS, you must first:
•
•
•
•
Configure your SonicPoint Provisioning Profiles
Configure a Wireless zone.
Assign profiles to wireless zones. This step is optional. If you do not assign a default profile for a zone, SonicPoints in that zone will use the first profile in the list.
Assign an interface to the Wireless zone.
Configuring SonicPoints
287
• Attach the SonicPoints to the interfaces in the Wireless zone.
• Test SonicPoints
SonicPoint Provisioning Profiles
SonicPoint Provisioning Profiles provide a scalable and highly automated method of configuring and provisioning
multiple SonicPoints across a Distributed Wireless Architecture. SonicPoint Profile definitions include all of the
settings that can be configured on a SonicPoint, such as radio settings for the 2.4GHz and 5GHz radios, SSID’s, and
channels of operation.
Once you have defined a SonicPoint profile, you can apply it to a Wireless zone. Each Wireless zone can be configured with one SonicPoint profile. Any profile can apply to any number of zones. Then, when a SonicPoint is connected to a zone, it is automatically provisioned with the profile assigned to that zone.
SonicOS includes a default SonicPoint profile, named SonicPoint. You can modify this profile or create a new one.
The default SonicPoint profile has the following settings:
802.11a Radio
Enable 802.11a
Radio
SSID
Radio Mode
Channel
ACL Enforcement
Authentication
Type
Schedule IDS Scan
Data Rate
Antenna Diversity
802.11g Radio
Yes - Always on
SonicWALL
54Mbps - 802.11a
AutoChannel
Disabled
Enable 802.11g
Radio
Yes - Always on
SonicWALL
SSID
2.4 GHz 54Mbps - 802.11g
Radio Mode
AutoChannel
Channel
ACL Enforcement
Disabled
WEP - Both
Authentication
Open System & Shared Key Type
WEP - Both
Open System & Shared Key
Disabled
Disabled
Best
Best
Schedule IDS Scan
Best
Data Rate
Antenna Diversity
Best
Configuring a SonicPoint Profile
You can add any number of SonicPoint profiles. To configure a SonicPoint provisioning profile:
1. To add a new profile click Add below the list of SonicPoint provisioning profiles
To edit an existing profile, select the profile and click the edit icon
editing.
in the same line as the profile you are
2. In the General tab of the Add Profile window, specify:
Enable SonicPoint: Check this to automatically enable each SonicPoint when it is provisioned with this
profile.
• Name Prefix: Enter a prefix for the names of all SonicPoints connected to this zone. When each SonicPoint
is provisioned it is given a name that consists of the name prefix and a unique number, for example: “SonicPoint 126008.“
• Country Code: Select the country where you are operating the SonicPoints. The country code determines
which regulatory domain the radio operation falls under.
•
3. In the 802.11a tab, Configure the radio settings for the 802.11a (5GHz band) radio:
Enable 802.11a Radio: Check this to automatically enable the 802.11a radio bands on all SonicPoints provisioned with this profile.
• Select a schedule to determine when the radio is enabled. The default is Always on. you can create and
manage Schedule objects in the System > Schedules page of GMS.
•
288
SonicWALL Global Management System Configuration Guide
•
SSID: Enter a recognizable string for the SSID of each SonicPoint using this profile. This is the name that
will appear in clients’ lists of available wireless connections.
!
Note: If all SonicPoints in your organization share the same SSID, it is easier for users to maintain their wireless connection when roaming from one SonicPoint to another.
• Radio Mode: Select the speed of the wireless connection. You can choose 54 Mbps or 108 Mbps (Turbo)
mode. If you choose Turbo mode, all users in your company must use wireless access cards from the same
manufacturer.
• Channel: Select the channel the radio will operate on. The default is AutoChannel, which automatically
selects the channel with the least interference. Use AutoChannel unless you have a specific reason to use or
avoid specific channels.
• ACL Enforcement: Select this to enforce Access Control by allowing or denying traffic from specific
devices. Select an address object from the list of
• Authentication Type: Select the method of authentication for your wireless network. You can select WEP
- Both (Open System & Shared Key), WEP - Open System, WEP - Shared Key, WPA - PSK, or WPA
- EAP.
• WEP Key Mode: Select the size of the encryption key.
• Default Key: Select which key in the list below is the default key, which will be tried first when trying to
authenticate a user.
• Key Entry: Select whether the key is alphanumeric or hexadecimal.
• Key 1 - Key 4: Enter the encryptions keys for WEP encryption. Enter the most likely to be used in the field
you selected as the default key.
4. In the 802.11a Advanced tab, configure the performance settings for the 802.11a radio. For most 802.11a
advanced options, the default settings give optimum performance.
Figure 219: 802.11a Advanced Settings
• Hide SSID in Beacon: Check this option to have the SSID broadcast as part of the wireless beacon, rather
than as a separate broadcast.
• Schedule IDS Scan: Select a time when there are fewer demands on the wireless network to schedule an
Intrusion Detection Service (IDS) scan to minimize the inconvenience of dropped wireless connections.
• Data Rate: Select the speed at which the data is transmitted and received. Best automatically selects the
best rate available in your area given interference and other factors. You can select: Best, 6 Mbps, 9 Mbps,
12 Mbps, 18 Mbps, 24 Mbps, 36 Mbps, 48 Mbps, or 54 Mbps.
• Transmit Power: Select the transmission power. Transmission power effects the range of the SonicPoint.
You can select: Full Power, Half (-3 dB), Quarter (-6 dB), Eighth (-9 dB), or Minimum.
Configuring SonicPoints
289
•
•
•
•
•
•
Antenna Diversity: The Antenna Diversity setting determines which antenna the SonicPoint uses to send
and receive data. You can select:
• Best: This is the default setting. When Best is selected, the SonicPoint automatically selects the
antenna with the strongest, clearest signal. In most cases, Best is the optimal setting.
• 1: Select 1 to restrict the SonicPoint to use antenna 1 only. Facing the rear of the SonicPoint, antenna 1
is on the left, closest to the power supply.
• 2: Select 2 to restrict the SonicPoint to use antenna 2 only. Facing the rear of the SonicPoint, antenna 2
is on the right, closest to the console port.
Beacon Interval (milliseconds): Enter the number of milliseconds between sending out a wireless beacon.
DTIM Interval: Enter the interval in milliseconds.
Fragmentation Threshold (bytes): Enter the number of bytes of fragmented data you want the network to
allow.
RTS Threshold (bytes): Enter the number of bytes.
Maximum Client Associations: Enter the maximum number of clients you want the SonicPoint to support
on this radio at one time.
Figure 220: 802.11g Advanced Settings
The settings in the 802.11g Radio and 802.11g Advanced tabs are similar to the settings in the 802.11a Radio
and 802.11a Advanced tabs. Follow the instructions in step 3 and step 4 in this procedure to configure the
802.11g radio.
When a SonicPoint unit is first connected and powered up, it will have a factory default configuration (IP Address
192.168.1.20, username: admin, password: password). Upon initializing, it will attempt to find a SonicOS device
with which to peer. If it is unable to find a peer SonicOS device, it will enter into a stand-alone mode of operation
with a separate stand-alone configuration allowing it to operate as a standard Access Point.
If the SonicPoint does locate, or is located by a peer SonicOS device, via the SonicWALL Discovery Protocol, an
encrypted exchange between the two units will ensue wherein the profile assigned to the relevant Wireless Zone
will be used to automatically configure (provision) the newly added SonicPoint unit.
As part of the provisioning process, SonicOS will assign the discovered SonicPoint device a unique name, and it
will record its MAC address and the interface and Zone on which it was discovered. It can also automatically assign
the SonicPoint an IP address, if so configured, so that the SonicPoint can communicate with an authentication
server for WPA-EAP support. SonicOS will then use the profile associated with the relevant Zone to configure the
2.4GHz and 5GHz radio settings.
Modifications to profiles will not affect units that have already been provisioned and are in an operational state.
Configuration changes to operational SonicPoint devices can occur in two ways:
290
SonicWALL Global Management System Configuration Guide
• Via manual configuration changes – Appropriate when a single, or a small set of changes are to be affected, particularly when that individual SonicPoint requires settings that are different from the profile assigned to its
Zone.
• Via un-provisioning – Deleting a SonicPoint unit effectively un-provisions the unit, or clears its configuration
and places it into a state where it will automatically engage the provisioning process anew with its peer SonicOS device. This technique is useful when the profile for a Zone is updated or changed, and the change is set
for propagation. It can be used to update firmware on SonicPoints, or to simply and automatically update multiple SonicPoint units in a controlled fashion, rather than changing all peered SonicPoints at once, which can
cause service disruptions.
Configuring SonicPoints
291
SonicPoint G Support
GMS now provides support for SonicPoint G wireless security appliances.
To configure a SonicPoint G device in GMS, perform the following steps.
1. Navigate to the Policies panel.
2. Select a SonicPoint G device in the unit list.
3. In the Navigation Bar, click the SonicPoint menu to display SonicPoint options.
4. Click the SonicPoints option.
GMS displays the SonicPoints dialog box.
5. Click Add.
GMS displays the Add SonicPoint Profile dialog box containing a series of tabs.
6. Click the 802.11g Radio Tab to display fields for configuring 802.11g radio settings.
Note: The SonicPoint has two separate radios built in. Therefore, it can send and receive on both the 802.11a
and 802.11g bands at the same time.
292
SonicWALL Global Management System Configuration Guide
7. Click the 802.11g Adv to display 802.11g advanced settings fields.
Hide SSID in Beacon: Check this option to have the SSID broadcast as part of the wireless beacon, rather
than as a separate broadcast.
• Data Rate: Select the speed at which the data is transmitted and received. Best automatically selects the
best rate available in your area given interference and other factors. You can select: Best, 6 Mbps, 9 Mbps,
12 Mbps, 18 Mbps, 24 Mbps, 36 Mbps, 48 Mbps, or 54 Mbps.
• Transmit Power: Select the transmission power. Transmission power effects the range of the SonicPoint.
You can select: Full Power, Half (-3 dB), Quarter (-6 dB), Eighth (-9 dB), or Minimum.
• Antenna Diversity: The Antenna Diversity setting determines which antenna the SonicPoint uses to send
and receive data. You can select:
• Best: This is the default setting. When Best is selected, the SonicPoint automatically selects the antenna
with the strongest, clearest signal. In most cases, Best is the optimal setting.
•
1: Select 1 to restrict the SonicPoint to use antenna 1 only. Facing the rear of the SonicPoint, antenna 1 is on
the left, closest to the power supply.
2: Select 2 to restrict the SonicPoint to use antenna 2 only. Facing the rear of the SonicPoint, antenna 2 is on
the right, closest to the console port.
• Beacon Interval (milliseconds): Enter the number of milliseconds between sending out a wireless beacon.
• DTIM Interval: Enter the interval in milliseconds.
• Fragmentation Threshold (bytes): Enter the number of bytes of fragmented data you want the network to
allow.
• RTS Threshold (bytes): Enter the number of bytes.
• Maximum Client Associations: Enter the maximum number of clients you want the SonicPoint to support
on this radio at one time.
These settings affect the operation of the 802.11g radio bands. The SonicPoint has two separate radios built in.
Therefore, it can send and receive on both the 802.11a and 802.11g bands at the same time.
Configuring SonicPoints
293
Updating SonicPoint Settings
You can change the settings of any individual SonicPoint list on the Wireless > SonicPoints page.
Edit SonicPoint settings
To edit the settings of an individual SonicPoint:
1. Under SonicPoint Settings, click the Edit icon
in the same line as the SonicPoint you want to edit.
2. In Edit SonicPoint screen, make the changes you want. The Edit SonicPoint screen has the following tabs:
•
•
•
•
•
General
802.11a Radio
802.11a Advanced
802.11g Radio
802.11g Advanced
The options on these tabs are the same as the Add SonicPoint Profile screen. See “Configuring a SonicPoint
Profile” for instructions on configuring these settings.
3. Click OK to apply these settings.
Synchronize SonicPoints
Click Synchronize SonicPoints at the top of the SonicPoint > SonicPoints page to update the settings for each
SonicPoint reported on the page. When you click Synchronize SonicPoints, SonicOS polls all connected SonicPoints and displays updated settings on the page.
Enable and Disable Individual SonicPoints
You can enable or disable individual SonicPoints on the SonicPoint > SonicPoints page:
1. Check the box under Enable to enable the SonicPoint, uncheck the box to disable it.
2. Click Apply at the top of the SonicPoint > SonicPoints page to apply this setting to the SonicPoint.
294
SonicWALL Global Management System Configuration Guide
SonicPoint G Support
GMS now provides support for SonicPoint G wireless security appliances.
To configure a SonicPoint G device in GMS, perform the following steps.
1. Navigate to the Policies panel.
2. Select a SonicPoint G device in the unit list.
3. In the Navigation Bar, click the SonicPoint menu to display SonicPoint options.
4. Click the SonicPoints option.
GMS displays the SonicPoints dialog box.
5. Click Add.
GMS displays the Add SonicPoint Profile dialog box containing a series of tabs.
6. Click the 802.11g Radio Tab to display fields for configuring 802.11g radio settings.
Configuring SonicPoints
295
7. Click the 802.11a Adv to display 802.11a advanced settings fields.
Hide SSID in Beacon: Check this option to have the SSID broadcast as part of the wireless beacon, rather
than as a separate broadcast.
• Data Rate: Select the speed at which the data is transmitted and received. Best automatically selects the
best rate available in your area given interference and other factors. You can select: Best, 6 Mbps, 9 Mbps,
12 Mbps, 18 Mbps, 24 Mbps, 36 Mbps, 48 Mbps, or 54 Mbps.
• Transmit Power: Select the transmission power. Transmission power effects the range of the SonicPoint.
You can select: Full Power, Half (-3 dB), Quarter (-6 dB), Eighth (-9 dB), or Minimum.
• Antenna Diversity: The Antenna Diversity setting determines which antenna the SonicPoint uses to send
and receive data. You can select:
• Best: This is the default setting. When Best is selected, the SonicPoint automatically selects the antenna
with the strongest, clearest signal. In most cases, Best is the optimal setting.
•
1: Select 1 to restrict the SonicPoint to use antenna 1 only. Facing the rear of the SonicPoint, antenna 1 is on
the left, closest to the power supply.
2: Select 2 to restrict the SonicPoint to use antenna 2 only. Facing the rear of the SonicPoint, antenna 2 is on
the right, closest to the console port.
• Beacon Interval (milliseconds): Enter the number of milliseconds between sending out a wireless beacon.
• DTIM Interval: Enter the interval in milliseconds.
• Fragmentation Threshold (bytes): Enter the number of bytes of fragmented data you want the network to
allow.
• RTS Threshold (bytes): Enter the number of bytes.
• Maximum Client Associations: Enter the maximum number of clients you want the SonicPoint to support
on this radio at one time.
These settings affect the operation of the 802.11g radio bands. The SonicPoint has two separate radios built in.
Therefore, it can send and receive on both the 802.11a and 802.11g bands at the same time.
Note that the settings in the 802.11g Radio and 802.11g Advanced tabs are similar to the settings in the 802.11a
Radio and 802.11a Advanced tabs.
296
SonicWALL Global Management System Configuration Guide
SonicPoint WLAN Scheduling
GMS now supports scheduling activation of both 802.11a Radio and 802.11g Radio devices. To schedule these
devices, perform the following steps:
1. Navigate to the Policies Panel.
2. Select either a SonicPoint G or SonicPoint A device in the unit list.
3. In the Navigation Bar, click the SonicPoint menu to display SonicPoint options.
4. Click the SonicPoints option.
GMS displays the SonicPoints dialog box.
5. Click on an existing SonicPoint device in the device list or click Add.
GMS displays the SonicPoint Profile dialog box containing a series of tabs.
6. Click either the 802.11g Radio or 802.11a Radio Tab, depending on which device you want to schedule.
7. Click on the Schedule list box at the top of the screen to the right of the Enable checkbox.
The following figure is an example of a scheduling list box (for 802.11g).
Updating SonicPoint Firmware
SonicOS Enhanced 2.5 (or greater) contains an image of the SonicPoint firmware. When you connect a SonicPoint
to a security appliance running SonicOS Enhanced 2.5 (or greater), the appliance checks the version of the SonicPoint’s firmware, and automatically updates it, if necessary.
Automatic Provisioning (SDP & SSPP)
The SonicWALL Discovery Protocol (SDP) is a layer 2 protocol employed by SonicPoints and devices running
SonicOS Enhanced 2.5 and higher. SDP is the foundation for the automatic provisioning of SonicPoint units via the
following messages:
•
•
•
•
•
Advertisement – SonicPoint devices without a peer will periodically and on startup announce or advertise
themselves via a broadcast. The advertisement will include information that will be used by the receiving SonicOS device to ascertain the state of the SonicPoint. The SonicOS device will then report the state of all peered
SonicPoints, and will take configuration actions as needed.
Discovery – SonicOS devices will periodically send discovery request broadcasts to elicit responses from L2
connected SonicPoint units.
Configure Directive – A unicast message from a SonicOS device to a specific SonicPoint unit to establish
encryption keys for provisioning, and to set the parameters for and to engage configuration mode.
Configure Acknowledgement – A unicast message from a SonicPoint to its peered SonicOS device acknowledging a Configure Directive.
Keepalive – A unicast message from a SonicPoint to its peered SonicOS device used to validate the state of the
SonicPoint.
If via the SDP exchange the SonicOS device ascertains that the SonicPoint requires provisioning or a configuration
update (e.g. on calculating a checksum mismatch, or when a firmware update is available), the Configure directive
will engage a 3DES encrypted, reliable TCP based SonicWALL Simple Provisioning Protocol (SSPP) channel. The
SonicOS device will then send the update to the SonicPoint via this channel, and the SonicPoint will restart with the
updated configuration. State information will be provided by the SonicPoint, and will be viewable on the SonicOS
device throughout the entire discovery and provisioning process.
Configuring SonicPoints
297
Viewing Station Status
Event and Statistics Reporting
The SonicPoint > Station Status page reports on the statistics of each SonicPoint.
The table lists entries for each wireless client connected to each SonicPoint. The sections of the table are divided by
SonicPoint. Under each SonicPoint, is the list of all clients currently connected to it.
Click the Refresh button in the top right corner to refresh the list.
By default, the page displays the first 50 entries found. Click the First Page
Last Page
, Previous Page , Next Page , and
icons to navigate if you need to view more than 50 entries.
Each SonicPoint device reports for both radios, and for each station, the following information to its SonicOS peer:
• MAC Address – The client’s (Station’s) hardware address
• Station State – The state of the station. States can include:
• None – No state information yet exists for the station
• Authenticated – The station has successfully authenticated.
• Associated – The station is associated.
• Joined – The station has joined the ESSID.
• Connected – The station is connected (joined, authenticated or associated).
• Up – An Access Point state, indicating that the Access Point is up and running.
• Down – An Access Point state, indicating that the Access Point is not running.
• Associations – Total number of Associations since power up.
• Dis-Associations – Total number of Dis-Associations.
• Re-Associations – Total number of Re-Associations.
• Authentications – Number of Authentications.
• De-Authentications – Number of De-Authentications.
• Good Frames Received – Total number of good frames received.
• Good Frames Transmitted – Total number of good frames transmitted.
• Error in Receive Frames – Total number of error frames received.
• Error in Transmit Frames – Total number of error frames transmitted.
• Discarded Frames – Total number of frames discarded. Discarded frames are generally a sign of network congestion.
• Total Bytes received – Total number of bytes received.
• Total Bytes Transmitted – Total number of bytes transmitted.
• Management Frames Received – Total number of Management frames received. Management Frames include:
• Association request
• Association response
• Re-association request
• Re-association response
• Probe request
• Probe response
• Beacon frame
• ATIM message
• Disassociation
• Authentication
• De-authentication
• Management Frames Transmitted – Total number of Management frames transmitted.
• Control Frames Received – Total number of Control frames received. Control frames include:
• RTS – Request to Send
• CTS – Clear to Send
• ACK – Positive Acknowledgement
• Control Frames Transmitted – Total number of Control frames transmitted.
298
SonicWALL Global Management System Configuration Guide
• Data Frames Received – Total number of Data frames received.
• Data Frames Transmitted – Total number of Data frames transmitted.
Using and Configuring SonicPoint IDS
Detecting SonicPoint Access Points
You can have many wireless access points within reach of the signal of the SonicPoints on your network. The SonicPoint > IDS page reports on all access points the TZ 170 Wireless can find by scanning the 802.11a and 802.11g
radio bands.
Wireless Intrusion Detection Services
Intrusion Detection Services (IDS) greatly increase the security capabilities of the TZ 170 with SonicOS Enhanced
by enabling it to recognize and even take countermeasures against the most common types of illicit wireless activity. IDS consists of three types of services, namely, Sequence Number Analysis, Association Flood Detection, and
Rogue Access Point Detection. IDS logging and notification can be enabled under Log > Categories by selecting
the IDS checkbox under Log Categories and Alerts.
Intrusion Detection Settings
Rogue Access Points have emerged as one of the most serious and insidious threats to wireless security. In general
terms, an access point is considered rogue when it has not been authorized for use on a network. The convenience,
affordability and availability of non-secure access points, and the ease with which they can be added to a network
creates a easy environment for introducing rogue access points. Specifically, the real threat emerges in a number of
different ways, including unintentional and unwitting connections to the rogue device, transmission of sensitive
data over non-secure channels, and unwanted access to LAN resources. So while this doesn't represent a deficiency
in the security of a specific wireless device, it is a weakness to the overall security of wireless networks.
The security appliance can alleviate this weakness by recognizing rogue access points potentially attempting to gain
access to your network. It accomplishes this in two ways: active scanning for access points on all 802.11a and
802.11g channels, and passive scanning (while in Access Point mode) for beaconing access points on a single channel of operation.
Intrusion Detection Settings
Check Enable Rogue Access Point Detection to enable the security appliance to search for rogue access points.
The Authorized Access Points list determines which access points the security appliance will considered authorized when it performs a scan. You can select All Authorized Access Points to allow all SonicPoints, or you can
select an address object group containing a group of MAC address to limit the list to only those SonicPoints whose
MAC addresses are contained in the address object group.
Select Create Address Object Group to add a new group of MAC address objects to the list.
Note: See Chapter 10, Configuring Network Settings for SonicOS Enhanced for instructions on creating address
objects and address object groups.
Scanning for Access Points
Active scanning occurs when the security appliance starts up, and at any time Scan All is clicked on the SonicPoint
> IDS page. When the security appliance performs a scan, a temporary interruption of wireless clients occurs for no
more than a few seconds. This interruption manifests itself as follows:
• Non-persistent, stateless protocols (such as HTTP) should not exhibit any ill-effects.
• Persistent connections (protocols such as FTP) are impaired or severed.
• WiFiSec connections should automatically re-establish and resume with no noticeable interruption to the client.
Warning: If service disruption is a concern, it is recommended that the Scan Now feature not be used while the TZ
170 Wireless is in Access Point mode until such a time that no clients are active, or the potential for disruption
becomes acceptable.
Configuring SonicPoints
299
Discovered Access Points
The Discovered Access points displays information on every access point that can be detected by the SonicPoint
radio:
SonicPoint: The SonicPoint that detected the access point.
MAC Address (BSSID): The MAC address of the radio interface of the detected access point.
SSID: The radio SSID of the access point.
Type: The range of radio bands used by the access point, 2.4 GHz or 5 GHz.
Channel: The radio channel used by the access point.
Manufacturer: The manufacturer of the access point. SonicPoints will show a manufacturer of either SonicWALL or Senao.
• Signal Strength: The strength of the detected radio signal
• Max Rate: The fastest allowable data rate for the access point radio, typically 54 Mbps.
• Authorize: Click the Authorize icon to add the access point to the address object group of authorized access
points.
•
•
•
•
•
•
View Style
If you have more than one SonicPoint, you can select an individual device from the SonicPoint list to limit the Discovered Access Points table to display only scan results from that SonicPoint. Select All SonicPoints to display
scan results from all SonicPoints.
Authorizing Access Points on Your Network
Access Points detected by the security appliance are regarded as rogues until they are identified to the security
appliance as authorized for operation. To authorize an access point, it can be manually added to the Authorized
Access Points list by clicking edit icon in the Authorize column and specifying its MAC address (BSSID) along
with an optional comment. Alternatively, if an access point is discovered by the security appliance scanning feature,
it can be added to the list by clicking the Authorize icon.
300
SonicWALL Global Management System Configuration Guide
CHAPTER 23
Configuring Wireless Options
This chapter describes how to configure wireless connectivity options for wireless SonicWALL appliances.
Configuring General Wireless Settings
This section describes how to configure general wireless settings. To do this, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a wireless SonicWALL appliance.
3. Expand the Wireless tree and click Settings. The Settings page appears (Figure 221).
Figure 221: Settings Page
4. Select whether the SonicWALL appliance will act as an Access Point or a Wireless Bridge from the Radio Role
list box.
5. To enable Wireless networking on this device, select the Enable WLAN check box.
6. Enter the IP address and subnet mask of the Wireless LAN port in the WLAN IP Address and WLAN Subnet
Mask fields.
7. Enter the Service Set Identifier (SSID) or wireless network name in the SSID field (maximum: 32 characters).
8. Select a wireless channel to use from the Channel list box.
Configuring Wireless Options
301
9. When you are finished, click Update. The settings are changed for the selected SonicWALL appliance. To clear
all screen settings and start over, click Reset.
Wireless Radio Operating Schedule
Wireless Schedule allows you to specify time periods of operation for the WLAN. This feature is available in the
Wireless > Settings screen. In SonicOS Standard, it is available under the section Use Time Constraints, and in
SonicOS Enhanced, it is available as Schedule drop-down list and at unit Level this section is displayed depending
on whether it is SonicOS Standard or Enhanced. At group level, both options are shown with text in italics indicating which section applies to SonicOS Standard and SonicOS Enhanced.
Configuring WEP Encryption Settings
This section describes how to configure Wireless Equivalent Privacy (WEP) security settings. To do this, follow
these steps:
1. Start and log into SonicWALL GMS.
2. Select a wireless SonicWALL appliance.
3. Expand the Wireless tree and click WEP Encryption. The WEP Encryption page appears (Figure 222).
Figure 222: WEP Encryption Page
4. Select whether wireless devices that attempt to connect to the SonicWALL appliance must first authenticate:
• If all devices must authenticate, select Shared Key from the Authentication Type list box.
• If no authentication is required, select Open System from the Authentication Type list box.
• To support both authenticated and non-authenticated connections, select Both from the Authentication
Type list box.
5. Select the size of the authentication key used to authenticate devices that connect to the SonicWALL appliance
from the WEP Key Mode field.
302
SonicWALL Global Management System Configuration Guide
6. If you selected the Shared Key authentication type, do the following:
Select the default key from the Default Key list box. This is the first key that will be used to send challenges to wireless devices attempting to communicate with the SonicWALL appliance.
• Select whether the encryption keys will be Alphanumeric or Hexadecimal.
• Enter up to four keys in the Key fields.
•
7. To specify a client that will have wireless access without additional authentication, enter its information in the
MAC Address and Comment fields and click Add. Repeat this step for each client to add.
8. When you are finished, click Update. The settings are changed for the selected SonicWALL appliance. To clear
all screen settings and start over, click Reset.
Configuring Advanced Wireless Settings
This section describes how to configure advanced wireless settings. To do this, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a wireless SonicWALL appliance.
3. Expand the Wireless tree and click Advanced. The Advanced page appears (Figure 223).
Figure 223: Advanced Page
4. SSIDs are used to logically segment wireless networks. At an interval that you set, the wireless SonicWALL
appliance will send out beacon frames that identify the SSID. Select the following beacon options:
•
To hide the SSID in beacons, select the Hide SSID in Beacon check box.
Note: This provides marginal security as Probe Responses and other 802.11 frames contain the SSID.
To block responses when a device does not specify and SSID, select the Block Response to Unspecified
SSID check box.
• Enter how often (in milliseconds) a beacon will be sent in the Beacon Interval field.
•
Configuring Wireless Options
303
5. Wireless clients are devices that attempt to access the wireless SonicWALL appliance. Select the following
wireless client options:
To specify the maximum number of wireless clients, enter the limit in the Maximum Client Associations
field.
• Select whether wireless clients will be able to communicate with each other from the Interclient Communications list box.
• Enter the URL to the VPN Client software from the VPN Client Download URL field.
•
6. Select the following Advanced Radio Settings:
• Enable Antenna Diversity -- XXXX
• Select the transmit power of the wireless SonicWALL appliance from the Transmit Power list box.
• Select whether wireless clients will be able to communicate with each other from the Interclient Communications list box.
• Enter the URL to the VPN Client software from the VPN Client Download URL field.
• Most current wireless equipment supports orthogonal frequency-division multiplexing (OFDM) which uses
a short preamble to improve network performance. A preamble is the initial information sent in a frame that
announces to other devices in the network the beginning of data transmission.
Using a short preamble improves network performance and is recommended unless your wireless network
consists of older equipment.
Specify the level (in bytes) that the SonicWALL appliance will begin fragmenting packets in the Fragmentation Threshold field.
• In environments with high rates of collision, the Request to Send/Clear to Send (RTS/CTS) feature reduces
collision rates. The RTS/CTS option is invoked when a wireless device sends wishes to send a large packet.
First, the wireless device sends an RTS/CTS request which is answered by an RTS/CTS response. All other
wireless devices receive this response and cease transmitting for the specified period of time.
•
To activate RTS/CTS, specify the size a packet must reach before the RTS/CTS feature is invoked in the
RTS Threshold field. A threshold around 500 to 600 kilobytes is generally recommended. Using a threshold larger than the Fragmentation Threshold will essentially disable this feature (default: 2432 or disabled).
•
The delivery traffic indication message (DTIM) is a message that informs power-save devices that a packet
is waiting for them. This message is sent with a beacon.
To configure this interval, enter a value in the DTIM Interval field (default: 3).
For example, if you specify a value of 4 and the Beacon Interval is set to 100 milliseconds, DTIMs will be
sent every 400 milliseconds.
• Specify the amount of time in which an authentication must take place in the authentication field (default:
10 seconds).
• Specify the amount of time (in seconds) within which an authenticated device must establish an association
in the Association Timeout field (default: 300 seconds).
7. Select the broadcast rate from the Broadcast Rate field.
8. When you are finished, click Update. The settings are changed for the selected SonicWALL appliance. To clear
all screen settings and start over, click Reset.
304
SonicWALL Global Management System Configuration Guide
Configuring MAC Filter List Settings
Wireless SonicWALL appliances can allow or block wireless devices based on their MAC addresses. To configure
the MAC filter list, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a wireless SonicWALL appliance, a group, or the global icon.
3. Expand the Wireless tree and click MAC Filter List. The MAC Filter List page appears (Figure 224).
Figure 224: MAC Filter List Page
4. To enable the MAC filter list for the selected device(s), select the Enable MAC Filter List check box.
5. To add a MAC address to the filter list, enter the address in the MAC Address List field, select whether it is
allowed or blocked, add any comments to the Comment field, and click Add MAC Address.
6. Repeat this step for each MAC address that you want to add.
7. When you are finished, click Update. The settings are changed for the selected SonicWALL appliance(s). To
clear all screen settings and start over, click Reset.
Configuring Wireless Options
305
Configuring Intrusion Detection Settings
This section describes how to configure intrusion detection settings (IDS) for wireless SonicWALL appliances. To
configure the IDS, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a wireless SonicWALL appliance, a group, or the global icon.
3. Expand the Wireless tree and click IDS. The IDS page appears (Figure 225).
Figure 225: IDS Page
4. Sequence number analysis is used to detect MAC address spoofing. To enable this feature, select the Enable
Sequence Number Analysis check box.
5. Hackers can cause a Denial-of-Service (DoS) attack by flooding a wireless network with association requests.
To combat this, select the Enable Association Flood Detection check box.
The default association flood threshold is 10 association attempts within 5 seconds. To change this setting, enter
new flood threshold values.
To block the MAC address of a computer or device attempting this attack, select the Block station's MAC
address in response to an association flood field.
6. To access a network, hackers can set up a rogue access point that will intercept communications with legitimate
users attempting to access a legitimate access point. This “man-in-the-middle” attack can expose passwords and
other network resources. To enable detection of rogue access points, select the Enable Rogue Access Point
Detection check box.
7. To prevent rogue access points, you must specify each authorized access point within the network. To do so,
enter the MAC address of an access point in the MAC Address field and click Add. Repeat this step for each
authorized access point within the network.
8. When you are finished, click Update. The settings are changed for the selected SonicWALL appliance(s). To
clear all screen settings and start over, click Reset.
306
SonicWALL Global Management System Configuration Guide
Configuring Wireless Guest Services
This section describes how to configure Wireless Guest Services (WGS).
Configuring General Wireless Guest Services Settings
This section describes how to configure general wireless settings. To do this, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a wireless SonicWALL appliance.
3. Expand the WGS tree and click Settings. The Settings page appears (Figure 226).
Figure 226: Settings Page
4. To enable Wireless Guest Services on this device, select the Enable Wireless Guest Services check box.
5. To disable filtering for guest accounts, select the Bypass Filters for Guest Accounts check box.
6. To limit the number of concurrent guests, enter the maximum number in the Maximum Concurrent Guests
field.
7. Dynamic Address Translation (DAT) saves wireless clients the hassle of reconfiguring their IP address and network settings. To enable DAT, select the Dynamic Address Translation (DAT) check box.
8. To add a new guest, click Add New Wireless Guest and enter the following information:
•
•
•
•
•
•
User Name—enter the username of the guest account.
User Password—enter the password of the guest account.
Confirm Password—reenter the password of the guest account.
Account Lifetime—select the maximum lifetime of the guest account.
Session Timeout—select the session timeout for the guest account.
Comment—add any comments.
When you are finished, click Update.
9. When you are finished, click Update. The settings are changed for the selected SonicWALL appliance. To clear
all screen settings and start over, click Reset.
Configuring Wireless Options
307
Configuring the URL Allow List
The URL allow list specifies URLs that can be accessed by unauthenticated users. To configure this list, follow
these steps:
1. Start and log into SonicWALL GMS.
2. Select a wireless SonicWALL appliance.
3. Expand the WGS tree and click URL Allow List. The URL Allow List page appears (Figure 227).
Figure 227: URL Allow List Page
4. To enable the URL Allow List, select the Enable URL Allow List for Unauthenticated Users check box.
5. To add a URL to the URL Allow List, enter a URL and click Add. Repeat this step for each URL that you
would like to add.
6. When you are finished, click Update. The settings are changed for the selected SonicWALL appliance. To clear
all screen settings and start over, click Reset.
Denying Access to Networks
To specify networks that authenticated users will not be allowed to access, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a wireless SonicWALL appliance.
3. Expand the WGS tree and click IP Deny List. The IP Deny List page appears (Figure 228).
308
SonicWALL Global Management System Configuration Guide
Figure 228: IP Deny List Page
4. To enable the IP Deny List, select the Enable IP Address Deny List for Authenticated Users check box.
5. To add a URL to the IP Deny List, enter an IP address and subnet mask and click Add IP Deny Entry. Repeat
this step for each URL that you would like to add.
6. When you are finished, click Update. The settings are changed for the selected SonicWALL appliance. To clear
all screen settings and start over, click Reset.
Configuring the Custom Login Screen
The Custom Login page is used to configure the login page that will be accessed by guest users attempting to connect to the wireless SonicWALL appliance.
To configure the Custom Login page, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a wireless SonicWALL appliance.
3. Expand the WGS tree and click Custom Login. The Custom Login page appears (Figure 229).
Configuring Wireless Options
309
Figure 229: Custom Login Page
4. To customize the login page, select the Customize Login Page check box.
5. The body of the login page will contain the username and password fields that the user must access to authenticate with the SonicWALL appliance. To configure the header and footer text, select from the following:
•
•
To display custom header and footer URLs, enter the URLs in the Custom Header URL and Custom
Footer URL fields.
To enter custom text for the header and footer, enter the text in the Custom Header Text and Custom
Footer Text fields.
6. When you are finished, click Update. The settings are changed for the selected SonicWALL appliance. To clear
all screen settings and start over, click Reset.
310
SonicWALL Global Management System Configuration Guide
CHAPTER 24
Configuring Dialup Options
This chapter describes how to configure the dialup settings for SonicWALL SmartPath (SP) and SmartPath ISDN
(SPi) appliances.
SonicWALL SP appliances have a WAN Failover feature. When the primary broadband connection becomes
unavailable, SonicWALL SP appliances automatically use built-in modems to establish Internet connectivity. This
is ideal when the SonicWALL appliance must remain connected to the Internet, regardless of network speed.
Configuring the Dialup Profile
A profile is a list of dialup connection settings that can be used by a SonicWALL SP appliance.
To configure a profile, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the SonicWALL appliance.
3. Expand the Dialup tree and click Profile. The Profile page appears (Figure 230).
Figure 230: Profile Page
4. To edit an existing profile or use an existing profile as a template, select a profile from the Current Profile list
box.
5. Select from the following:
•
•
If this will be a new profile, enter the name of the profile in the Name field.
If you are editing an existing profile, make sure the entry in the Name field matches the profile that you are
editing.
Configuring Dialup Options
311
6. Enter the primary phone number of the ISP in the Primary phone number field.
7. Enter the backup phone number in the Secondary phone number field.
8. Enter the username associated with the account in the User field.
9. Enter the password associated with the account in the Password and Confirm Password fields.
10. Select from the following IP address options:
• If the account obtains an IP address dynamically, select Obtain automatically.
• If the account uses a fixed IP address, select Specify and enter the IP address.
11. Select from the following DNS server options:
•
•
If the account obtains DNS server information from the ISP, select Obtain automatically.
If the account uses a specific DNS servers, select Specify and enter the DNS server IP addresses.
12. Enter a chat script (optional).
13. MSN/EAZ - XXXX
14. Select from the following connection options:
If the SonicWALL appliance(s) will remain connected to the Internet until the broadband connection is
restored, select Persistent Connection.
• If the SonicWALL appliance(s) will only connect to the Internet when data is being sent, select Dial On
Data.
• If the SonicWALL appliance(s) will connect to the Internet manually, select Manual Dial.
•
15. To specify how long the modem waits before disconnecting from the Internet, enter the amount of time in the
Inactivity Timeout field. To disable the Inactivity Timeout option, enter ‘0’.
16. To specify a maximum connection speed, select the speed from the Max connection speed list box. Otherwise,
make sure Auto is selected.
17. To specify the maximum connection time, enter the amount of time in the Max Connection Time field. To configure the SonicWALL device to allow indefinite connections, enter ‘0’.
18. Delay before reconnect - XXXX
19. Network modem mode - XXXX
20. Disable VPN when dialed - XXXX
21. To disable call waiting, select Disable Call Waiting and select the touch tone disabling code.
22. If the modem is unable to connect to the ISP, specify the number of retries in the Dial Retries per phone number field.
23. To specify how long the modem waits between retries, specify how long in the Delay between Retries field.
24. When you are finished, click Update. The profile is added. To clear all screen settings and start over, click
Reset.
312
SonicWALL Global Management System Configuration Guide
Configuring Dialup
To configure the WAN Failover feature for one or more SonicWALL SP appliances, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the SonicWALL appliance.
3. Expand the Dialup tree and click Configure. The Configure page appears (Figure 231).
Figure 231: Configure Page
4. Select the first profile that the SonicWALL appliance will attempt to use when the broadband connection is not
available from the Primary Profile list box.
5. Select the second profile that the SonicWALL appliance will attempt to use when the broadband connection is
not available from the Secondary Profile list box.
6. Select the volume of the speaker from the Speaker volume list box.
7. Enter any AT commands that the modem will need to use to establish a connection in the AT Commands field.
8. ISDN Protocol-- XXXX
9. Enable the WAN Failover feature by selecting the Enable WAN Failover check box.
10. Preempt mode-- XXXX
11. Enter the IP address that the SonicWALL appliance will use to test Internet connectivity in the Probe Target
field. We recommend using the IP address of the WAN Gateway.
12. Specify how often the IP address will be tested in the Probe Interval field.
13. Specify how many times the probe target must be unavailable before the SonicWALL appliance fails over to the
modem in the Failover Trigger Level field.
14. Specify how many times the SonicWALL appliance must successfully reach the probe target to reactivate the
broadband connection in the Successful probes to reactivate Primary field.
15. When you are finished, click Update. WAN Failover is enabled for the selected SonicWALL SP appliances. To
clear all screen settings and start over, click Reset.
Configuring Dialup Options
313
314
SonicWALL Global Management System Configuration Guide
CHAPTER 25
Upgrading SonicWALL Appliances
This chapter describes how to upgrade SonicWALL appliances. Select from the following:
To upgrade SonicWALL firmware, see “Upgrading Firmware” on page 315.
To upgrade SonicWALL appliance nodes, subscription services, or add other services, see “Upgrading SonicWALL Appliances” on page 317.
• To share anti-virus and VPN client licenses among multiple SonicWALL appliances, see “Creating License
Sharing Groups” on page 319.
• To view used activation codes, see “Viewing Used Activation Codes” on page 327.
•
•
Upgrading Firmware
SonicWALL firmware is updated on a periodic basis to offer new functionality and address any known issues. After
a SonicWALL appliance is added to SonicWALL GMS management, its auto-update feature is disabled.
SonicWALL GMS periodically polls mysonicwall.com site for new firmware versions. Once a new version of firmware is detected and available, SonicWALL GMS sends an email notification to the SonicWALL GMS
administrator.
You need to go to your mysonicWALL.com account at <https://www.mysonicwall.com> and download the
firmware, save the firmware file to the GMS server, and then access the SonicWALL security appliance from GMS.
Note: If you are using GMS version 2.9, when you download a firmware file from mysonicwall.com, the back end
server inserts extra characters in the firmware file name. You must remove the extra characters in the firmware file
to ensure the file uses the firmware file name conventions before upgrading the SonicWALL security appliance.
Upgrading to GMS 2.9.1 resolves this issue. Refer to “Firmware File Naming Convention” on page 316 for more
information on firmware file name conventions.
Note: If you want to disable firmware notifications, see “Configuring SonicWALL GMS Report Settings” on
page 332.
To upgrade to the latest firmware, follow these steps:
Note: In order for changes on this page to take effect, the SonicWALL appliance(s) will automatically be restarted.
We recommend scheduling the firmware update to run when network activity is low.
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Register/Upgrades tree and click Firmware Upgrade.
Upgrading SonicWALL Appliances
315
Figure 232: Register/Upgrades Page
4. Select from the following:
• To upgrade the firmware of all selected SonicWALL appliances, click Upgrade Firmware.
• If you are upgrading from a firmware file on the local drive of your desktop system, enter the path to the file
or click Browse to locate a file. Then, click Upgrade firmware from local file.
Firmware File Naming Convention
The following is the naming convention standard for SonicWALL firmware files 2.1.0.0 and above:
sw_<product>_<os_type>_<locale>_<n>.<n>.<n>.<n>[_<label>].sig
Examples
sw_pro2040_e_eng_2.1.0.0.sig
sw_pro2040_s_eng_2.1.0.0.sig
sw_pro3060_s_eng_2.1.0.0.sig
sw_pro4060_s_eng_2.1.0.0.sig
316
SonicWALL Global Management System Configuration Guide
Upgrading SonicWALL Appliances
This section describes the procedures for upgrading SonicWALL appliances. This functionality includes adding
nodes, content filter subscriptions, VPN functionality, VPN clients, anti-virus licenses, and more.
When a SonicWALL GMS subscription service (i.e., warranty support, anti-virus, or content filtering) is about to
expire, the GMS administrator will receive expiration notifications via email prior to the expiration. The email notification is sent once a day (if applicable) and lists all managed SonicWALL appliances with expiring subscription
services.
To upgrade SonicWALL appliances, complete the following procedures:
1. Purchase the Upgrade Licenses—see “Purchasing Upgrades” on page 317.
2. Activate the Upgrade Licenses—see “Activating the Upgrades” on page 317.
3. Applying the Upgrade Licenses—see “Applying the Upgrades” on page 318.
Note: If you have the activation codes ready, you can bypass Step 2 and enter them during Step 3.
Purchasing Upgrades
To purchase upgrades, follow these steps:
1. Contact your SonicWALL sales representative.
You will receive an activation code for each upgrade that you purchase.
2. After receiving the activation codes for the SonicWALL upgrades, continue to the next section.
Activating the Upgrades
To license upgrades, follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Console Panel tab at the bottom of the SonicWALL GMS UI.
3. Expand the Licenses tree and click SonicWALL Upgrades. The SonicWALL Upgrades page appears
(Figure 233).
Figure 233: SonicWALL Upgrades Page
Upgrading SonicWALL Appliances
317
4. Select the category of upgrade from the Category list box. For example, if you are adding an anti-virus subscription, select Antivirus.
5. Select the type of upgrade from the Type list box. For example, if you are adding an anti-virus subscription,
select the number of nodes.
6. Enter the activation code in the Activation Code field.
7. Click Add Activation Code.
The license is added to SonicWALL GMS license pool.
8. Repeat Step 4 through 7 for each node upgrade that you want to add.
9. If you are adding a large number of activation codes through an activation code file, click Browse and select the
activation code file. Then, click Add Activation Code and follow the on-screen prompts.
10. To activate the node upgrade(s), continue to the next section.
Applying the Upgrades
To activate upgrades for SonicWALL appliances, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance. If you select a group, all SonicWALL appliances
within that group will be upgraded. If the node upgrade does not apply to a SonicWALL appliance within the
group, the upgrade will not be applied to that appliance.
3. Expand the Register/Upgrades tree and click Service Licenses. The Service Licenses page appears
(Figure 234).
Figure 234: Node Upgrade Page
4. Verify that this is the SonicWALL appliance or group of appliances that you want to upgrade by checking the
Current Status section.
5. To upgrade the appliance(s), select from the following:
• Click the Upgrade button for the license to add.
• Enter the activation code in the Activation Code field and click Subscribe.
318
SonicWALL Global Management System Configuration Guide
Creating License Sharing Groups
License Sharing allows you to share VPN or Anti-Virus Client Licenses license among multiple SonicWALL appliances. As a result, you can save money by purchasing licenses in quantity and not wasting licenses on SonicWALL
appliances that do not use them all.
License sharing assigns a License Sharing Group (LSG) to a SonicWALL appliance and activates this feature. You
can then add other SonicWALL appliances to the LSG and assign them licenses from the pool of remaining available licenses.
Select from the following:
•
•
To create a VPN Client License Sharing Group, see “Creating VPN Client License Sharing Groups” on
page 319.
To create an Anti-Virus Client License Sharing Group, see “Creating Anti-Virus License Sharing Groups” on
page 322.
Creating VPN Client License Sharing Groups
Select from the following:
•
•
To create an VPN LSG, see “Creating a License Sharing Group” on page 319.
To add SonicWALL appliances to an existing VPN LSG, see “Adding a SonicWALL Appliance to an Existing
Group” on page 320.
Creating a License Sharing Group
To create a VPN LSG, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance that has extra VPN Client Licenses. If no appliances have extra licenses, you
will need to them. For more information, see Chapter 25, “Upgrading SonicWALL Appliances.”
3. Expand the Register/Upgrades tree and click License Sharing. The License Sharing page appears (Figure 235).
Figure 235: License Sharing Page
4. Select VPN Client Enterprise from the List of Services list box and click Join a License Sharing Group. The
Join a License Sharing Group dialog box appears (Figure 236).
Upgrading SonicWALL Appliances
319
Figure 236: Join a License Sharing Group Dialog Box
5. Select Create a new License Sharing Group With and select another SonicWALL appliance that will belong
to the group. Then, enter a name for the group and click Accept. SonicWALL GMS initiates a task that creates
a new group which will use the licenses from this SonicWALL appliance.
Adding a SonicWALL Appliance to an Existing Group
To add a SonicWALL appliance to an existing LSG, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Register/Upgrades tree and click License Sharing. The License Sharing page appears (Figure 237).
Figure 237: License Sharing Page
4. Click Join a License Sharing Group. The Join a License Sharing Group dialog box appears (Figure 238).
320
SonicWALL Global Management System Configuration Guide
Figure 238: Join a License Sharing Group Dialog Box
5. Select Join Existing License Sharing Group and select an LSG from the list box.
6. Click Accept. SonicWALL GMS initiates a task that will assign this SonicWALL appliance to the group.
Changing the License Count
To change the number of licenses that a SonicWALL appliance uses, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the Register/Upgrades tree and click License Sharing. The License Sharing page appears (Figure 239).
Figure 239: License Sharing Page
4. Make sure VPN Client Enterprise is selected from the List of Services list box.
5. Enter a new license value and click Change License Count to.
6. To remove this SonicWALL appliance from the LSG, select Remove from License Sharing Group.
View the Properties of a License Sharing Group
To view the properties of an LSG, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the Register/Upgrades tree and click License Sharing. The License Sharing page appears (Figure 240).
Upgrading SonicWALL Appliances
321
Figure 240: License Sharing Page
4. Click the name of the LSG to view. The License Sharing Group Properties dialog box appears.
Figure 241: License Sharing Page
5. This dialog box contains detailed information about the total number of licenses, the expiration date of the
license, the number of licenses used by each member of the group, and other information.
6. To change the name of the LSG, enter a new name and click Accept.
Creating Anti-Virus License Sharing Groups
Select from the following:
• To create an Anti-Virus LSG, see “Creating a License Sharing Group” on page 319.
• To add SonicWALL appliances to an existing Anti-Virus LSG, see “Adding a SonicWALL Appliance to an
Existing Group” on page 320.
Creating a License Sharing Group
To create an LSG, follow these steps:
1. Start and log into SonicWALL GMS.
322
SonicWALL Global Management System Configuration Guide
2. Select a SonicWALL appliance that has extra Anti-Virus Licenses. If no appliances have extra licenses, you
will need to them. For more information, see Chapter 25, “Upgrading SonicWALL Appliances.”
3. Expand the Register/Upgrades tree and click License Sharing. The License Sharing page appears (Figure 235).
Figure 242: License Sharing Page
4. Select Anti-Virus from the List of Services list box and click Join a License Sharing Group. The Join a
License Sharing Group dialog box appears (Figure 236).
Figure 243: Join a License Sharing Group Dialog Box
5. Select Create a new License Sharing Group With and select another SonicWALL appliance that will belong
to the group. Then, enter a name for the group and click Accept. SonicWALL GMS initiates a task that creates
a new group which will use the licenses from this SonicWALL appliance.
Adding a SonicWALL Appliance to an Existing Group
To add a SonicWALL appliance to an existing LSG, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance.
3. Expand the Register/Upgrades tree and click License Sharing. The License Sharing page appears (Figure 237).
Upgrading SonicWALL Appliances
323
Figure 244: License Sharing Page
4. Click Join a License Sharing Group. The Join a License Sharing Group dialog box appears (Figure 238).
Figure 245: Join a License Sharing Group Dialog Box
5. Select Join Existing License Sharing Group and select an LSG from the list box.
6. Click Accept. SonicWALL GMS initiates a task that will assign this SonicWALL appliance to the group.
Changing the License Count
To change the number of licenses that a SonicWALL appliance uses, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the Register/Upgrades tree and click License Sharing. The License Sharing page appears (Figure 246).
324
SonicWALL Global Management System Configuration Guide
Figure 246: License Sharing Page
4. Make sure Anti-Virus is selected from the List of Services list box.
5. Enter a new license value and click Change License Count to.
6. To remove this SonicWALL appliance from the LSG, select Remove from License Sharing Group.
View the Properties of a License Sharing Group
To view the properties of an LSG, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select a SonicWALL appliance.
3. Expand the Register/Upgrades tree and click License Sharing. The License Sharing page appears (Figure 247).
Upgrading SonicWALL Appliances
325
Figure 247: License Sharing Page
4. Click the name of the LSG to view. The License Sharing Group Properties dialog box appears.
Figure 248: License Sharing Page
5. This dialog box contains detailed information about the total number of licenses, the expiration date of the
license, the number of licenses used by each member of the group, and other information.
6. To change the name of the LSG, enter a new name and click Accept.
326
SonicWALL Global Management System Configuration Guide
Viewing Used Activation Codes
To view used activation codes, follow these steps:
1. Start and log into SonicWALL GMS.
2. Select the global icon, a group, or a SonicWALL appliance. If you select a group, all SonicWALL appliances
within that group will be upgraded. If the node upgrade does not apply to a SonicWALL appliance within the
group, the upgrade will not be applied to that appliance.
3. Expand the Register/Upgrades tree and click Used Activation Codes. The Used Activation Codes page appears
(Figure 249).
Figure 249: Used Activation Codes Page
4. SonicWALL GMS displays a list of used activation codes, sorted alphabetically by code number. To sort the
codes by service name, select Service Name from the Select sort order list box.
Upgrading SonicWALL Appliances
327
328
SonicWALL Global Management System Configuration Guide
Section III
SonicWALL GMS Configuration and Maintenance
CHAPTER 26
Configuring and Working with SonicWALL GMS
The SonicWALL Global Management System (SonicWALL GMS) Console Panel is used for configuring
SonicWALL GMS settings, working with the SonicWALL GMS log, working with SonicWALL GMS tasks, and
upgrading SonicWALL GMS.
This chapter describes the following:
•
•
•
•
•
•
Changing the SonicWALL GMS password. See “Configure SonicWALL GMS User Settings” on page 331.
Setting the SonicWALL GMS user idle-logout period and e-mail address. See “Configuring SonicWALL GMS
Report Settings” on page 332.
Configuring and viewing the SonicWALL GMS log. See “Viewing the SonicWALL GMS Log” on page 335.
Configuring task settings and view pending tasks. See “Working with SonicWALL GMS Tasks” on page 336.
Managing SonicWALL GMS sessions and configuring Agents. See “Managing SonicWALL GMS” on
page 338.
Adding SonicWALL GMS licenses to support additional SonicWALL appliances. See “Upgrading
SonicWALL GMS” on page 346.
Configure SonicWALL GMS User Settings
To change the SonicWALL GMS password and other user settings, follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Console Panel tab at the bottom of the SonicWALL GMS user interface (UI).
3. Expand the Settings tree and click User Settings. The User Settings page appears (Figure 250).
Figure 250: Change Password Page
Configuring and Working with SonicWALL GMS
331
4. To change the password, do the following:
• Enter the old SonicWALL GMS password in the Old GMS Password field.
• Enter the new SonicWALL GMS password in the New GMS Password field.
• Reenter the new password in the Confirm New Password field.
5. The GMS Inactivity Timeout period specifies how long SonicWALL GMS waits before logging out an inactive
user. To prevent someone from accessing the SonicWALL GMS UI when SonicWALL GMS users are away
from their desks, enter an appropriate value in the GMS Inactivity Timeout field (default: 10 minutes).
Note: This field can be set to a maximum of 120 minutes.
6. To configure SonicWALL GMS to display an editable task description each time a task is generated, select the
Enable edit task description dialog when creating tasks check box.
7. To display the users that are logged into SonicWALL GMS during login, select the Enable Session Window
Pop-up Feature.
8. To view the message of the day now, click View Message of the Day.
9. When you are finished, click Update. The settings are changed. To clear all screen settings and start over, click
Reset.
Note: The maximum size of the SonicWALL GMS User ID is 24 alphanumeric characters. The password is one-way
hashed and any password of any length can be hashed into a fixed 32 character long internal password.
Configuring SonicWALL GMS Report Settings
The GMS Reporting module uses a default group of settings that specify the types of charts and the amount of data
that is displayed. This settings can be changed during a session, but will be cleared once you log out.
To change the default settings for your user ID, follow these steps:
1. Start and log into SonicWALL GMS as the user whose default settings you will modify.
2. Click the Console tab.
3. Expand the User Settings tree and click Report Settings. The Report Settings page appears (Figure 251).
Figure 251: Report Settings Page
4. Select whether the reports will contain a chart and table or table only.
5. Select whether Summary and Over Time charts will be displayed as bar graphs or plots from the Summary/
Over Time Charts list box (default: BAR).
332
SonicWALL Global Management System Configuration Guide
6. Select whether User charts will be displayed as pie charts, bar graphs, area charts, or plots from the User Based
Charts list box (default: PIE).
7. Select the number of sites to display in Top Sites reports (default: 10).
8. Select the number of users to display in Top Users reports (default: 10).
9. Select the number of sites to display in Sites by User and Time reports (default: 5).
10. Select the number of items to display in all other reports (default: 10).
11. Select the number of entries per item to display in all other reports (default: 10).
12. To only display data for a specified group of web sites, enter the URL of each site (separated by commas) in the
Site List field. Because this field uses pattern matching, entries such as “yahoo.com” will display data for
mail.yahoo.com, shopping.yahoo.com, and so on.
13. To only display data for a specified group of users, enter the username of each user (separated by commas) in
the User List field. Because this field uses pattern matching, entries such as “john” will display data for johnm,
123john, and so on.
14. To configure the default start and end times for hourly reports, select a start and end time from the Start and
End list boxes.
15. To specify a list of web sites that will be excluded from the reports, enter a string that specifies a URL or portion of a URL to exclude from the reports. For example:
www.yahoo.com
ebay.com
netscape
...
Click Add. Any web site that contains a portion of the string that you specified will be excluded from the
report.
Repeat this step for each web site to exclude.
Configuring and Working with SonicWALL GMS
333
Deleting the SonicWALL GMS Logs
To configure SonicWALL GMS to automatically delete old log files, follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Console Panel tab at the bottom of the SonicWALL GMS UI.
3. Expand the Log tree and click Configuration. The Configuration page appears (Figure 252).
Figure 252: Configuration Page
4. Select a date from the list boxes.
5. Click Delete Logs Older Than. Log files older than the selected date will be deleted.
334
SonicWALL Global Management System Configuration Guide
Viewing the SonicWALL GMS Log
The SonicWALL GMS log keeps track of changes made within the SonicWALL GMS UI, logins, failed logins,
logouts, password changes, scheduled tasks, failed tasks, and completed tasks.
To view the SonicWALL GMS log, follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Console Panel tab at the bottom of the SonicWALL GMS UI.
3. Expand the Log tree and click View Log. The View Log page appears (Figure 253).
Figure 253: View Log Page
4. Each log entry contains the following fields:
• Number—specifies the number of the log entry.
• Date—specifies the date of the log entry.
• Message—contains a description of the event.
• Severity—displays the severity of the event (Alert, Warning, or FYI).
• SonicWALL—specifies the name of the SonicWALL appliance that generated the event (if applicable).
• User@IP—specifies the user name and IP address.
5. To narrow the search, configure some of the following criteria:
• Select Time of logs—displays all log entries for a specified period of time.
• SonicWALL Node—displays all log entries associated with the specified SonicWALL appliance.
• Message contains—displays all log entries that contain the specified text.
• User@IP—displays all log entries with the specified user.
• Severity—displays log entries with the matching severity level:
• All (Alert, Warning, and FYI)
• Alert and Warning
• Alert
6. To view the results of your search criteria, click Start Search. To save the results as an HTML file on your system, click Export Logs and follow the on-screen instructions.
7. To configure how many messages are shown per screen, enter a new value (default: 10).
Configuring and Working with SonicWALL GMS
335
Working with SonicWALL GMS Tasks
As you perform multiple tasks through the SonicWALL GMS UI, SonicWALL GMS creates, queues, and applies
them to the SonicWALL appliances.
As SonicWALL GMS processes the tasks, some SonicWALL appliances may be down or offline. When this occurs,
SonicWALL GMS requeues the tasks and reattempts the changes.
To view and manage pending tasks, follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Console Panel tab at the bottom of the SonicWALL GMS UI.
3. Expand the Tasks tree and click Scheduled Tasks. The Scheduled Tasks page appears (Figure 254).
Figure 254: Scheduled Tasks Page
4. Each task entry contains the following fields:
• Number (#)—specifies the number of the task entry.
• SonicWALL—specifies the name of the SonicWALL appliance to which the task applies.
• Description—contains a description of the task.
• Last Error—if the task was not successfully executed, specifies the error.
• Creation Time—specifies the date and time the task was generated.
• Last Attempt—specifies the last time SonicWALL GMS attempted to execute the task.
• No. of Attempts—specifies the number of times SonicWALL GMS has attempted to execute the task.
• Owner—specifies the user who created the task.
5. To narrow the search, enter one or more of the following search criteria and click Start Search:
•
•
•
•
•
Calendar—select the period of time for which SonicWALL GMS will display tasks. Options include the
task creation time, the local scheduled time, and the agent scheduled time.
SonicWALL Node—displays all tasks associated with the specified SonicWALL appliance.
Description contains—displays all tasks that contain the specified text.
Owner—displays all tasks with the specified owner.
Task ID—displays the task with the specified task ID.
6. To execute one or more scheduled tasks immediately, select their check boxes and click Execute the tasks
selected now.
7. To reschedule one or more pending tasks for another time, select their check boxes and click Re-schedule the
tasks selected. The GMS Date Selector dialog box appears (Figure 255).
336
SonicWALL Global Management System Configuration Guide
Figure 255: GMS Date Selector Dialog Box
8. Select a new date when the task will execute and click OK. The dialog box closes and the task will execute at
the selected time.
Note: The task(s) will execute based on the time setting of the SonicWALL GMS agent server, UTC, or local
browser's time.
9. To delete one or more tasks from the list of pending tasks, select their check boxes and click Delete the tasks
selected. To delete all pending tasks, select the Select all Tasks check box and click Delete the tasks selected.
Scheduling Tasks at the Time of Task Configuration
GMS now enables you to schedule tasks to run at a future time or date when running the task. The way you
approach scheduling a future time is by running a task supported by future task scheduling and indicate the time and
date of when to run it in the Modify Task Description and Schedule dialog box.
As an example, if you are trying to obtain the status of a unit, you can indicate that you want the information displayed at a later time. To schedule a later time to display the status of a unit, perform the following steps:
1. Navigate to the Policies Panel.
2. In the unit list, select a unit,
3. Click Status, in the Navigation Bar.
4. In the Status Window, click the Fetch Information button.
GMS displays the Modify Task Description and Schedule dialog box.
Figure 256: Task Description and Schedule Dialog Box
5. Click the Plus (+) symbol in the Schedule area.
Three Schedule radio buttons appear. They are:
•
•
•
Default - By selecting this radio button, the task will run at the default time.
Immediate - By selecting this radio button, the task will run immediately.
At - By selecting this radio button, GMS displays a time region and a calendar.
6. To schedule a future time for running the task, click in the Hour listbox and select an hour time. Then click in
the Minute listbox and select a minute time. Then click in the Timezone listbox and select a timezone. The combination of these three values provides a time when the task will run.
7. To schedule a date for running the task, click on the Month list box and select a month. In the year listbox,
select a year. In the calendar, select a date. The combination of these three values provides a date when the task
will run.
8. Click Accept.
Configuring and Working with SonicWALL GMS
337
Managing SonicWALL GMS
This section describes how to perform SonicWALL GMS management functions.
Configuring GMS Management Settings
The GMS Settings page is used to configure SonicWALL GMS Management Settings.
To configure the GMS management settings, follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Console Panel tab at the bottom of the SonicWALL GMS user interface (UI).
3. Expand the Management tree and click GMS Settings. The GMS Settings page appears (Figure 257).
Figure 257: Management GMS Settings Page
4. Enter the IP address or hostname of the Simple Mail Transfer Protocol (SMTP) server in the SMTP Server
field.
5. Enter the sender’s e-mail address that will appear in messages sent from the SonicWALL GMS in the GMS
Sender's e-Mail Address field.
6. Select how often SonicWALL GMS will automatically save the preferences and addUnit.xml files.
7. To automatically save the VPN Gateway Preferences files for SonicWALL appliances, select the Automatically save VPN Gateway Prefs file check box.
Note: The Enable Prefs Backup option must also be selected. For more information, see “Saving and Applying
SonicWALL Settings” on page 59.
8. To append services and rules that are inherited from the group for all firmware version, select Append all settings inherited from group.
9. To append services and rules that are inherited from the group for only non-SonicOS Enhanced firmware, select
the Append Services and Rules inherited from group (only for non-SonicOS Enhanced firmware) check
box.
At the unit level, SonicWALL GMS allows a SonicWALL appliance to inherit group settings. By default,
SonicWALL GMS overwrites the parameters at the Unit level with the values set at the Group level. If you
select this check box, the rules (Access\Rules) and services (Access\Services) settings will be appended to the
current settings rather than replacing them.
338
SonicWALL Global Management System Configuration Guide
10. To enable reporting, select the Enable Reporting check box. For more information on ViewPoint, see the SonicWALL Global Management System ViewPoint Guide.
Note: ViewPoint reporting can consume a significant amount of bandwidth.
11. To enable firmware updates to occur from the local drive of the SonicWALL GMS server, select the Enable
Firmware Upgrade From Local Drive check box.
12. To configure SonicWALL GMS to automatically synchronize with the local changes made to the SonicWALL
appliances, select the Enable Auto Synchronization check box.
13. To create a copy of the AddUnit.xml file, including the entire SonicWALL GMS system TreeControl hierarchy,
click Create AddUnit XML File. A new browser will pop up displaying the content of the AddUnit.xml file.
You can save this file to a local directory and modify it at a later time. This will enable you to add new SonicWALL appliances to SonicWALL GMS using the command-line interface.
Note: If need to reinstall SonicWALL GMS, you can use this file to reacquire the SonicWALL appliances from
the newly installed SonicWALL GMS system.
14. When you are finished, click Update. The settings are changed. To clear the screen settings and start over, click
Reset.
Configuring Alert Notification Settings
The Alert Settings page specifies which email addresses receive email alerts and notifications during specific times.
To configure the alert notification settings, follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Console Panel tab at the bottom of the SonicWALL GMS user interface (UI).
3. Expand the Management tree and click Alert Settings. The Alert Settings page appears (Figure 258).
Figure 258: SonicWALL GMS Alert Settings Page
Configuring and Working with SonicWALL GMS
339
4. Configure the email address(es) that will receive notifications and the times that they will receive them:
•
•
•
•
•
Schedule 1—Specifies who will receive notifications during the first weekday schedule. Enter one or more
email addresses (separated by commas) and specify the start and end time for the shift.
Schedule 2—Specifies who will receive notifications during the second weekday schedule. Enter one or
more email addresses (separated by commas) and specify the start and end time for the shift.
Schedule 3—Specifies who will receive notifications during the third weekday schedule. Enter one or more
email addresses (separated by commas) and specify the start and end time for the shift.
Saturday—Specifies who will receive notifications on Saturday. Enter one or more email addresses (separated by commas) and specify the start and end time for the shift.
Sunday—Specifies who will receive notifications on Sunday. Enter one or more e-mail addresses (separated by commas) and specify the start and end time for the shift.
5. Select whether the e-mail alert will be sent as HTML or Plain Text.
6. SonicWALL GMS provides a subscription expiry notification e-mail that notifies the SonicWALL GMS
administrator before warranty support, anti-virus, and content filtering services expire. By default, the e-mail is
sent to the SonicWALL GMS administrator 30 days and 7 days in advance of the firewall subscription service
expiration dates. The e-mail lists all managed SonicWALL appliances with expiring subscription services.
In the E-Mail Alert Frequencies area, configure the notification and alert frequency settings:
Subscription Expiration 1st Notice—Specifies when the first subscription expiration notification is sent
(default: 30 days).
• Subscription Expiration 2nd Notice—Specifies when the second subscription expiration notification is
sent (default: 7 days).
• E-Mail Summary on Down Unit's Status Every—Specifies how often e-mail notifications are sent when
a SonicWALL appliance is down (default: 24 hours).
• E-Mail Alert on Task Failure Count—Specifies how many times a task must fail before an email notification is sent (default: 25).
•
7. The Alerts area contains a list of alert events and the types of notifications that can be configured for each
event. To configure alert settings for an event, select from the following.
• GMSLog—When selected, this alert event will be written to the SonicWALL GMS log.
• Email—When selected, this alert event will be emailed to the email address(es) specified above.
• Unit Email—When selected, this alert event will be emailed to the administrator email address(es) specified for the affected SonicWALL appliance(s).
• Trap—When selected, this alert event will generate an SNMP trap.
• Sysout—When selected, this alert event will be displayed in the DOS or UNIX command-line window.
• File—When a filename is entered, this alert event will be appended to the end of the specified file. Do not
specify a path, simply enter a filename.
8. When you are finished, click Update. The settings are saved.
Managing Sessions
On occasion, it may be necessary to log off other user sessions. To do this, follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Console Panel tab at the bottom of the SonicWALL GMS user interface (UI).
3. Expand the Management tree and click Sessions. The Sessions page appears (Figure 259).
340
SonicWALL Global Management System Configuration Guide
Figure 259: SonicWALL GMS Sessions Page
4. Select the check box of each user to log off and click End selected sessions.
The selected users are logged off.
Managing Agent Configurations
The Agents page provides information for the SonicWALL GMS primary and backup agent servers that are managing the SonicWALL appliances. This page lists the IP address and status of each agent server, the IP address and
password of the GMS gateway for each agent server, and the number of firewalls under SonicWALL GMS management. You can also schedule all the tasks for each agent server to be executed during a specified time period.
Note: You can also use this page to remove agents, but they cannot be managing any firewalls.
To configure the Agents page, follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Console Panel tab at the bottom of the SonicWALL GMS user interface (UI).
3. Expand the Management tree and click Agents. The Agents page appears (Figure 260).
Configuring and Working with SonicWALL GMS
341
Figure 260: SonicWALL GMS Agents Page
4. The summary section displays the number of installed and running agents.
5. Select the IP address of the Agent you want to view from the Agent IP list box. The Agent Name field displays
the name of the selected Agent.
Note: The agent name can be modified by editing this field.
6. To specify when tasks can run, select the start time from the Daily At list box. The time is based on the SonicWALL appliance’s local time.
Note: By default, SonicWALL GMS schedules tasks for immediate execution.
7. For each agent server, the GMS Gateway IP address and password is displayed. If you change the GMS gateway IP address or password, you must also change the settings on this page.
8. To change the name of the GMS Gateway administrator for selected firmware/models, enter the name in the
GMS Gateway Username field (default: admin).
9. To change the password used to log in as the GMS Gateway administrator, enter the name in the GMS Gateway Password field.
10. For each agent server, the Firewalls for Primary Management list box lists the SonicWALL appliances that
are assigned to the agent server for primary management. The total number is also displayed.
11. For each agent server, the Firewalls for Standby Management list box lists the SonicWALL appliances that
are assigned to the agent server for backup management. The total number is also displayed.
12. For each agent server, the Firewalls Under Active Management list box lists the SonicWALL appliances that
are actively being managed by the agent server. The total number is also displayed.
13. When you are finished, click Update. The settings are changed. To clear the settings and start over, click Reset.
Configuring SNMP Settings
The SNMP Managers page enables you to specify SNMP Managers to which SonicWALL GMS will send SNMP
Traps.
To configure the SNMP Managers page, follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Console Panel tab at the bottom of the SonicWALL GMS user interface (UI).
342
SonicWALL Global Management System Configuration Guide
3. Expand the Management tree and click SNMP Managers. The SNMP Managers page appears (Figure 261).
Figure 261: SonicWALL GMS SNMP Managers Page
4. Select the IP address and port of the SNMP Manager from the SNMP Manager IP/Port fields.
5. Specify the IP addresses of SNMP Hosts to which traps will be forwarded in the SNMP Host to forward traps
to fields.
6. To enable trap forwarding, select the Enable SNMP Trap Forwarding check box.
7. To enable trap email, select the Enable SNMP Trap Email check box.
8. When you are finished, click Update. The settings are changed. To clear the settings and start over, click Reset.
Configuring Inheritance Settings
The SNMP Inheritance Filter page specifies which settings are inherited from the group when adding a new SonicWALL appliance.
To configure the SNMP Inheritance Filter page, follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Console Panel tab at the bottom of the SonicWALL GMS user interface (UI).
3. Expand the Management tree and click Inheritance Filters. The Inheritance Filter page appears (Figure 262).
Configuring and Working with SonicWALL GMS
343
Figure 262: SonicWALL GMS SNMP Inheritance Page
4. To edit an existing filter, select the filter from the Select Filter list box. To specify a new filter, enter the filter
name in the Filter name field.
5. Select which page settings are inherited in the Inheritance Filter Detail section.
6. Select the type of access that is available to each SonicWALL GMS user group from the Access for each UserType section.
7. When you are finished, click Add. The settings are changed. To clear the settings and start over, click Reset.
Configuring the Message of the Day Settings
The Message of the Day page displays a message when SonicWALL GMS users log on to SonicWALL GMS.
To configure the Message of the Day page, follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Console Panel tab at the bottom of the SonicWALL GMS user interface (UI).
3. Expand the Management tree and click Message of the Day. The Message of the Day page appears
(Figure 263).
344
SonicWALL Global Management System Configuration Guide
Figure 263: SonicWALL GMS SNMP Message of the Day Page
4. Select all users, a user group, or an individual user.
5. Enter message text in the Message field.
6. Select whether the message text will be displayed in plain text or HTML.
7. Select the start and end date of the message (default: current day).
8. When you are finished, click Update. The settings are changed.
9. Repeat this procedure for each group or user for which this message will be displayed.
Configuring and Working with SonicWALL GMS
345
Upgrading SonicWALL GMS
This section describes how to upgrade a SonicWALL GMS demo license or add upgrade the SonicWALL GMS
license to support additional SonicWALL appliances.
•
•
To upgrade a demo license, see “Upgrading a Demo License to a Retail License” on page 346.
To upgrade SonicWALL GMS to support additional SonicWALL appliances, see “Upgrading the Node
License” on page 347.
Upgrading a Demo License to a Retail License
To upgrade a SonicWALL GMS demo license to a retail license, select from the following:
•
•
To upgrade within the demo period, see “Upgrading within the Demo Period” on page 346.
To upgrade after the demo period expires, see “Upgrading within the Demo Period” on page 346.
Upgrading within the Demo Period
To upgrade a SonicWALL GMS demo license to a retail license within the demo period, follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Console Panel tab at the bottom of the SonicWALL GMS user interface (UI).
3. Expand the Licenses tree and click GMS License. The GMS License page appears (Figure 264).
Figure 264: SonicWALL GMS License Page
4. Enter the activation code in the Upgrade Activation Code field and click Perform Upgrade Now.
The License Type will change to Retail License and the Current Noes Allowed will change from 10 to 25.
Upgrading Outside the Demo Period
To upgrade a SonicWALL GMS demo license to a retail license after the demo period expires, follow these steps:
1. Start SonicWALL GMS. The Registration page appears.
2. Enter the demo upgrade activation code and click Update. The Login appears and the license is upgraded.
346
SonicWALL Global Management System Configuration Guide
Upgrading the Node License
Depending on the number of licenses you have ordered, you may need to add SonicWALL GMS licenses to configure and support additional SonicWALL appliances. This section describes how to perform a node license upgrade.
Purchasing a SonicWALL GMS Node License Upgrade
To purchase a SonicWALL GMS node license upgrade, follow these steps:
1. Contact your SonicWALL sales representative.
You will receive the activation code(s) for the node license upgrade(s) that you purchased.
2. After receiving the activation codes, continue to the next section.
Upgrading the License
To upgrade SonicWALL GMS, follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Console Panel tab at the bottom of the SonicWALL GMS user interface (UI).
3. Expand the Licenses tree and click GMS License. The GMS License page appears (Figure 265).
Figure 265: SonicWALL GMS License Page
4. Select the Node License Upgrade option from the pull-down menu and enter the activation code in the
Upgrade Activation Code field.
5. Click Perform Upgrade Now.
The Current Nodes Allowed number will increase by the number of node license upgrades that you purchased.
6. If you have additional activation codes, repeat Steps 4 and 5 for each activation code.
Configuring and Working with SonicWALL GMS
347
Activating SonicWALL GMS Support
To activate SonicWALL GMS support, follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Console Panel tab at the bottom of the SonicWALL GMS UI.
3. Expand the Licenses tree and click GMS License. The GMS License page appears (Figure 266).
Figure 266: SonicWALL GMS License Page
4. Select the SonicWALL GMS Support option from the pull-down menu and enter the activation code in the
Upgrade Activation Code field.
5. Click Perform Upgrade Now.
The selected SonicWALL GMS support with its expiration date will be displayed.
6. If you have additional activation codes, repeat Steps 4 and 5 for each activation code.
Note: For each SonicWALL GMS support option (Base, 24x7, or Software Maintenance), the CERT activation
code must be activated before activating the activation codes for additional nodes.
348
SonicWALL Global Management System Configuration Guide
Synchronize with mysonicwall.com
To automatically synchronize SonicWALL GMS with the mysonicwall.com, follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Console Panel tab at the bottom of the SonicWALL GMS UI.
3. Expand the Licenses tree and click GMS License. The GMS License page appears (Figure 267).
Figure 267: SonicWALL GMS License Page
4. Click Send GMS data to mysonicwall.com now. SonicWALL GMS synchronizes with mysonicwall.com.
Configuring and Working with SonicWALL GMS
349
Log into Mysonicwall.com
You can now automatically log into the SonicWALL registration site, Mysonicwall.com, from SonicWALL GMS.
Follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Console Panel tab at the bottom of the SonicWALL GMS UI.
3. Expand the Licenses tree and click GMS License. The GMS License page appears (Figure 268).
Figure 268: SonicWALL GMS License Page
4. Click Login in new window. A new browser opens with the SonicWALL GMS account on Mysonicwall.com.
350
SonicWALL Global Management System Configuration Guide
Configuring Debug Log Settings
When instructed by SonicWALL Technical Support, follow these steps to set the debug level:
1. Start and log into SonicWALL GMS.
2. Click the Console Panel tab at the bottom of the SonicWALL GMS UI.
3. Expand the Licenses tree and click Debug Log Settings. The Debug Log Settings page appears (Figure 269).
Figure 269: Debug Log Settings Page
4. .Select the amount of debug information that is stored from the System Debug Level field. For no debugging,
enter 0. For verbose debugging, enter 3.
Configuring and Working with SonicWALL GMS
351
Performing a System Snapshot
In order for a technical support representative to troubleshoot a problem, you might be asked to take a snapshot of
SonicWALL GMS or you might want to view the configuration yourself.
A system snapshot provides a detailed information about SonicWALL GMS, the SonicWALL GMS database, the
system environment, licensing, and firewalls. This information includes:
•
•
•
•
•
•
Data from the sgmsConfig.xml file (Console or Agent only)
• Debug state
• Build number
• Version
• Product Code
• Database type
• Database driver string
• Database dbuser
• Database password
• Database URL
SQLServer or Oracle state (Console or Agent only)—whether a database connection could be established
Environment information
• CLASSPATH, PATH variables
• DISPLAY variable (for Solaris - Console only)
• Web server listening port (Console only)
• Country
• Language
• Operating System
• IP Address
• MAC Address
• Machine data (memory size, etc.)
Latte/Licensing (Console or Agent only)
• Connectivity to Latte backend
• Latte username/password
• MS license information (Console only)
Agent specific data
• Managed units
• Units states (active or standby)
• Gateway firmware version
• Gateway state
• Ports (syslog, syslog parsing, etc.)
Firewall data (Gateway or Unit only)
• IP address
• Data from status.xml
• VPNs present (Gateway only)
• Latte information (if registered)
Performing the Snapshot
To take a snapshot of the system, follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Console tab at the bottom of the SonicWALL GMS UI.
3. Expand the Diagnostics tree and click Request Snapshot. The Request Snapshot page appears (Figure 270).
352
SonicWALL Global Management System Configuration Guide
Figure 270: Request Snapshot Page
4. To take a snapshot of the SonicWALL GMS console, select GMS Console.
5. To take a snapshot of one or more SonicWALL GMS agents, select the Agent check box(es).
6. To take a snapshot of the SGMS Gateway, select Gateway.
7. Click Submit Snapshot Request. SonicWALL GMS takes the snapshot.
8. To view the snapshot, see “Viewing the Snapshot or Diagnostics.”
Viewing the Snapshot or Diagnostics
To view a snapshot or SonicWALL diagnostics, follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Console tab at the bottom of the SonicWALL GMS UI.
3. Expand the Diagnostics tree and click Snapshot Status. The Snapshot Status page appears (Figure 271).
Configuring and Working with SonicWALL GMS
353
Figure 271: Snapshot Status Page
4. Select the snapshot or diagnostics that you want to view from the Diagnostics requested list box.
5. To view the information, click View Snapshot Data.
6. To save the information to a file that you can send to technical support, click Save Snapshot Data.
7. To delete the information, click Delete Snapshot Data.
8. To refresh the information, click Refresh Snapshot Data.
354
SonicWALL Global Management System Configuration Guide
Applying SonicWALL GMS Updates
Periodically, new updates will be released for SonicWALL GMS.
To check for and download new updates, follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Console Panel tab at the bottom of the SonicWALL GMS UI.
3. Expand the Licenses tree and click GMS Updates. The SGMS Updates page appears (Figure 272).
Figure 272: GMS Updates Page
4. To download new updates, click Download New GMS Software and Patch Updates.
5. To delete patches from the update list, select their corresponding check boxes and click Delete Selected Components from List.
6. After the patches are downloaded, open the command-line interface and navigate to the
<gms_directory>\patches directory.
7. Locate and execute the new update file.
Configuring and Working with SonicWALL GMS
355
Running Patches from the GUI
GMS now provides an easy-to-use graphical user interface screen for applying patches.You can perform this by
using the GMS Updater tool by running one of the following commands:
• For Windows: update.bat
• For Solaris: update.sh
These commands can be found in the Patches folder under the [SGMS2] folder.
356
SonicWALL Global Management System Configuration Guide
Updating SonicWALL GMS Registration
To change the registration information for SonicWALL GMS, follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Console Panel tab at the bottom of the SonicWALL GMS UI.
3. Expand the Licenses tree and click Registered User Info. The Registered User Info page appears (Figure 273).
Figure 273: Registered User Info Page
4. Make any necessary changes to the registration information. When you are finished, click Update. The settings
are changed.
Working with Capacity Planning
The Capacity Planning feature provides performance metrics for your network administrator to plan, design, and
expand your GMS server deployment. One of the challenges of growing a network is to know when you may need
to add a new server into your deployment. The Capacity Planning feature provides a convenient lookup that details
when you may need to add new resources to your network. This feature has information on the Syslog Collector
and Summarizer metrics. The Summarizer metrics are available only for GMS deployments and that have Distributed Summarizer enabled. The metrics are available for the past 24 hours, past seven days, and past 30 days.
These metrics are reset (to 0), every 24-hours for daily metrics, every seven days for weekly metrics, and every 30
days for monthly metrics. Weekly metrics are not shown unless the data collection for weekly metrics started earlier
than the daily metrics. Similarly, monthly metrics are not shown unless data collection for monthly metrics started
Configuring and Working with SonicWALL GMS
357
earlier than for daily and weekly metrics. GMS will not display metrics for a component if the daily statistics collection started more than 26 hours earlier. This will generally indicate that the component is not active.
To reach the Capacity Planning screen, go to the Console portion of GMS and then navigate to Diagnostics >
Capacity Planning. In the above screen, the average syslogs summarized per minute on the 192.168.253.12 system
is 18,108. The average number of syslogs received on that system is 91 per firewall, per minute. This suggests that
if the Summarizer was to constantly summarize 24 hours (as in the case of a dedicated Summarizer), this system
can handle around 18,108 / 91, 198 firewalls in all, assuming that the current set of firewalls under management of
this GMS is a fair sample of the additional firewalls that will be brought under the management of this GMS.
Analyzing Syslog Collector and Summarizer Metrics for Capacity Planning
Metrics can be used to identify network problems, either in the GMS deployment itself, or in the networks that are
being managed by the GMS. For example, a sudden increase in the average number of syslogs collected per minute
may indicate a remote network that is infected with malware application. A steep decrease in the average number of
syslogs summarized per minutes may indicate database issues (such as indexes not being maintained at regular
intervals) or malware consuming resources on the Summarizer system unnecessarily.
How to Interpret the Data
Use the following algorithm to approximate the number of SonicWALL security appliances (firewalls) a single
agent can handle. This model only applies to generation 2 or distributed summarizers, where n equals the number of
hours that the summarizer can run per day.
(number of syslogs summarized per minute) x (n/24)/(number of syslogs per firewall per minute)
For example, the average number of syslogs summarized per minute on the 192.168.253.12 system is 18,108. The
average number of syslogs received on that system is 83 per firewall, per minute. The administrator does not want
to summarize for more than eight hours a day.
18,108 x (8/24)/83 = 72
Therefore, this summarizer system can process a maximum of 72 SonicWALL security appliances. This is assuming that the current set of SonicWALL security appliances under management from this GMS server is a homogeneous sample of the additional units that will be brought under the management of this GMS server.
358
SonicWALL Global Management System Configuration Guide
CHAPTER 27
Configuring and Working with SonicWALL GMS
The SonicWALL Global Management System (SonicWALL GMS) Monitor Panel is used for real time monitoring
of SonicWALL appliances, VPN Tunnels, network devices, and syslog information.
This chapter describes the following:
•
•
•
•
“GMS Navigation Tool” on page 360
“VPN Monitor” on page 361
“Net Monitor” on page 363
• “Configuring the Net Monitor” on page 363
• “Adding Devices to the Net Monitor” on page 366
• “Managing Realtime Monitors” on page 371
• “Finding Devices” on page 364
• “Adding Custom Icons to the Net Monitor” on page 378
“Real-Time Syslog” on page 378
Configuring and Working with SonicWALL GMS
359
GMS Navigation Tool
The GMS Navigation Tool is a tool that shows a graphical representation of the GMS network. All devices within
the network are displayed and color-coded according to their operational state.
To open the GMS Navigation Tool, follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Monitor tab.
3. Expand the Tools tree and click GMS Navigation. Then, click Show Navigation Tool Window. The GMS
Navigation Tool appears with the managed SonicWALL appliances displayed (Figure 274).
Figure 274: Navigation Tool Viewer
4. The Navigation Tool provides a quick way to locate failed devices within the GMS network. The following
describes the meaning of link and device colors:
Device Status
• Yellow Device—device is provisioned
• Blue Device—device is operational
• Red Device—device is down
• Link Status
• Dark Blue Link—link is up and managed by Primary Agent
• Light Blue Link—link is up and managed by Standby Agent
• Link Thickness
• 1x Thick—link is using management tunnel
• 2x Thick—link is using existing tunnel
• 3x Thick—link is using HTTPS
• Solid—primary management tunnel
• Dashed—standby management tunnel
•
5. To hide the devices that belong to an Agent, right-click the agent and select Collapse. To view the properties of
a SonicWALL appliance, right-click the device and select Properties.
6. To move a device, right-click a device and select Cut. Then, right-click the new agent and select Paste.
7. To open the configuration pages for a device, double-click its icon.
Note: Clicking within the Navigation Tool will modify the network view.
8. When you are finished viewing managed SonicWALL appliances, close the window.
360
SonicWALL Global Management System Configuration Guide
VPN Monitor
The VPN Monitor shows a graphical representation of the VPN network. All devices within the network are displayed and color-coded according to their operational state.
To open the VPN Monitor, follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Monitor tab.
3. Expand the Tools tree and click VPN Monitor.
4. Click Show Navigation Tool Window. The VPN Monitor appears with the configured VPN tunnels displayed
(Figure 275).
Figure 275: VPN Monitor
Configuring and Working with SonicWALL GMS
361
5. The VPN Monitor provides a quick way to view the status of VPN connections within the GMS network. The
following describes the meaning of link and device colors:
• Node Status
• Yellow Device—unit is provisioned
• Blue Device—node is operational
• Red Device—node is down
• Black Device—group node
• Dark Gray Device—VPN not enabled
• Purple Device—Non-GMS device
• White Device—expanded tunnel nodes
• Link Status
• Blue Link—tunnel is operational
• Red Link—tunnel is down
• Yellow Link—tunnel is pending
• Black Link—tunnel is disabled
• White Link—tunnel status unknown
• Link Thickness
• 1x Thick—link not selected
• 2x Thick—link is selected
• Solid—direct tunnel
• Dashed—indirect tunnel
6. To synchronize the status of a tunnel with the Agent, right-click the SonicWALL appliance and select Synchronize Tunnel Status.
7. To show the remote units that belong to a SonicWALL appliance, right-click the agent and select Expand. To
hide the remote units, right-click the SonicWALL appliance and select Collapse.
8. To center a SonicWALL appliance and remove all other devices from the display, right-click the SonicWALL
appliance and select Center this node.
9. When you are finished monitoring VPNs, close the window.
362
SonicWALL Global Management System Configuration Guide
Net Monitor
The SonicWALL GMS Net Monitor periodically tests the status of SonicWALL appliances and other network
devices. Once configured, it enables you to monitor the status of your network and immediately respond when SonicWALL appliances and other network devices become unavailable.
The Net Monitor enables you to categorize different groups of SonicWALL appliances or other network devices.
You can categorize them by device type, geography, or any other organizational scheme. Additionally, you can
assign devices within each category a high, medium, or low priority. The following graphic shows the main Net
Monitor Page.
Figure 276: Net Monitor
When you add a new device to monitor, you will be able to select a category, priority level, how often the device is
tested, and the type of test that is used. The Net Monitor currently supports five types of tests: Ping, TCP Probe,
HTTP, HTTPS and SNMP.
Configuring the Net Monitor
This section contains the following subsections:
•
•
•
•
“Navigating the Net Monitor UI” on page 363
“Finding Devices” on page 364
“Viewing Device Status” on page 364
“Configuring Preferences” on page 365
Navigating the Net Monitor UI
The above graphic (Figure 274) shows the main page of the Net Monitor in which the SNWL_SEC_DEV category
is displayed. There are High, Medium and Low priority devices. To switch between categories, click a category
tab. To reconfigure the settings for a device, right-click the device and select Properties.
The Status Display shows the status of all devices within the category. If all devices are reachable, all three displays
will be green.
To change the priority for a device, drag and drop its icon to a new Priority Category. To move a device between
categories, drag its icon to the tab of the new category and drop it in the appropriate Priority Category.
Configuring and Working with SonicWALL GMS
363
Finding Devices
GMS NetMonitor gives you the ability to search for devices using the Find feature:
1. In the menu bar, go to Tools > Find.
2. Type a search string in the Look For field.
3. You can optionally choose to Match case or to find only the Whole word in your search.
4. Click the Find button to search all views for your search term, results are displayed below.
5. Double click on the device you wish to display and it will be found highlighted in the NetMonitor window.
Note: After making an initial search, you can use F3 (find next) and Shift+F3 (find previous) to move easily
between found devices without having to keep the Find window open.
Viewing Device Status
GMS NetMonitor provides the ability to view device status for all monitored devices:
1. In the NetMonitor window, select the device(s) you wish to view device status for.
2. In the menu bar, go to Tools > Device Status.
3. The Device Status window displays device specific attributes.
Note: Multiple Device Status windows may be opened simultaneously.
364
SonicWALL Global Management System Configuration Guide
Configuring Preferences
To configure Net Monitor preferences, follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Monitor tab.
3. Expand the Tools tree and click Monitor Tool.
4. Click Show Net Monitor Window. The Net Monitor appears (Figure 277).
Figure 277: Net Monitor
5. Select Preferences from the Tools Menu:
Figure 278: Preferences Dialog Box
6. To view each category on its own page, select Each from the View Type list box. To view all categories on one
page, select All.
7. To configure the Net Monitor to automatically refresh the status of monitored devices, select the Enable auto
refresh while loading check box and specify the refresh interval.
8. In the Filters tab, select which devices will be displayed in the Show devices by status area. To view all
devices, select the Select All check box.
Configuring and Working with SonicWALL GMS
365
9. In the Table tab, To view the default table color, select Default. To pick a custom color, select Custom and
choose a color from the color selector.
10. When you are finished, click Apply. To cancel and start over, click Cancel.
Adding Devices to the Net Monitor
This section contains the following subsections:
•
•
•
“Defining Categories” on page 366
“Adding SonicWALL Appliances” on page 367
“Adding Other Devices” on page 369
Defining Categories
To create a new category, follow these steps:
1. From the Monitor Tool window, select Add Category from the Categories Menu:
Figure 279: Add Category Dialog Box
2. Enter the name of the new category in the Name field.
3. When you are finished, click Apply. To cancel and start over, click Cancel.
4. Repeat this procedure for each category to add.
366
SonicWALL Global Management System Configuration Guide
Adding SonicWALL Appliances
To add one or more SonicWALL appliances, follow these steps:
1. From the Monitor Tool window, select Add GMS Device from the File Menu.
2. Select a device or group to monitor and click Add. Repeat this step for each device or group to monitor.
Figure 280: Add GMS Device Wizard
3. Click Next. The second page of the Add GMS Device Wizard appears.
Figure 281: Add GMS Device Wizard
4. Select the category to which the SonicWALL appliance(s) will be added from the Use an Existing Category
list box. To add the SonicWALL appliance(s) to a new category, enter the category name in the Add a New
Category field.
5. Select the priority of the SonicWALL appliance(s) from the Category Priority list box.
6. Select how the SonicWALL appliance(s) will be monitored from the Monitoring Type list box and specify a
Port if applicable.
Configuring and Working with SonicWALL GMS
367
7. If choosing SNMP as the monitoring type, you must enter a Monitor Port, and have the option of configuring
the following advanced settings by clicking on the Advanced button:
Figure 282: SNMP Advanced Settings
Table 3: SNMP Advanced Settings
Community
The community name.
Retry
Time to retry, in seconds.
Timeout
Timeout length, in seconds.
SNMP Version
Choose the version of SNMP to be used.
MIB(s)*
Select the MIB(s) you wish to use for polling information.
User Name
Enter a user name (SNMP v3 only).
Authentication Protocol
Select an authentication protocol form the list (SNMP v3 only).
Authentication Password
Enter an authentication password (SNMP v3 only).
Privacy Password
Enter a privacy password (SNMP v3 only).
Context ID
Enter a context ID (SNMP v3 only).
Context Name
Enter a context name (SNMP v3 only).
8. Press the OK button to save SNMP advanced settings.
9. Specify how often the SonicWALL appliance(s) will be tested in the Polling Interval field.
10. Enter the ideal response time (IRT) in the Ideal Response Time field (default: 500 milliseconds). SonicWALL
appliances that take between 1 and 1.5 times the IRT will be marked as Slow. SonicWALL appliances that take
between 1.5 and 2 times the IRT will be marked as Very Slow.
11. Select the Agent that will perform the testing from the Assign to Monitor list box.
12. Optional. To disable monitoring of the SonicWALL appliance(s), select Disable.
13. To change the icon image that will represent the device(s), click the icon image button and select a new image.
To use custom icons, see “Real-Time Syslog” on page 378.
14. Click the Finish button to acquire the new device.
Note: The process of acquiring a new device may take several minutes. To force acquisition of the device, select the
device and go to SNMP > SNMP Re-acquire in the NetMonitor menu bar.
* Custom MIBs may be required for some devices. Custom MIBs allow polling Non-SonicWALL or Non-Standard
based SNMP enabled devices and to poll information specific to a certain device based on Manufacturer ID.These
MIBs have to be placed in the etc\mibs folder by the GMS Administrator on the Web Server and Monitoring Agent
machine(s) in order to use it for probing.
368
SonicWALL Global Management System Configuration Guide
Adding Other Devices
In addition to SonicWALL appliances, SonicWALL GMS can monitor any publicly accessible servers or devices on
the Internet. To add one or more non-SonicWALL devices, follow these steps:
1. From the Monitor Tool window, select Add GMS Device from the File Menu:
Figure 283: Add Non-GMS Device Wizard
2. Enter a name for the device in the Name field and its IP address or hostname in the Host field and click Add.
Repeat this step for each device to monitor.
3. Click Next. The second page of the Add Non-GMS Device Wizard appears.
Figure 284: Add Non-GMS Device Wizard
4. Select the category to which the device(s) will be added from the Use an Existing Category list box. To add
the device to a new category, enter the category name in the Add a New Category field.
5. Select the priority of the device(s) from the Category Priority list box.
6. Select how the device(s) will be monitored from the Monitoring Type list box.
Configuring and Working with SonicWALL GMS
369
7. If choosing SNMP as the monitoring type, you must enter a Monitor Port, and have the option of configuring
the following advanced settings by clicking on the Advanced button:
Figure 285: SNMP Advanced Settings
Table 4: SNMP Advanced Settings
Community
The community name.
Retry
Time to retry, in seconds.
Timeout
Timeout length, in seconds.
SNMP Version
Choose the version of SNMP to be used.
MIB(s)*
Select the MIB(s) you wish to use for polling information.
User Name
Enter a user name (SNMP v3 only).
Authentication Protocol
Select an authentication protocol form the list (SNMP v3 only).
Authentication Password
Enter an authentication password (SNMP v3 only).
Privacy Password
Enter a privacy password (SNMP v3 only).
Context ID
Enter a context ID (SNMP v3 only).
Context Name
Enter a context name (SNMP v3 only).
8. Press the OK button to save SNMP advanced settings.
9. Specify how often the device(s) will be tested in the Polling Interval field.
10. Enter the ideal response time (IRT) in the Ideal Response Time field (default: 500 milliseconds). Devices that
take between 1 and 1.5 times the IRT will be marked as Slow. Devices that take between 1.5 and 2 times the
IRT will be marked as Very Slow.
11. Select the Agent that will perform the testing from the Assign to Monitor list box.
12. Optional. To disable monitoring of the device(s), select Disable.
13. To change the icon image that will represent the device(s), click the icon image button and select a new image.
To use custom icons, see “Real-Time Syslog” on page 378.
14. Click the Finish button to acquire the new device.
15. The process of acquiring a new device may take several minutes. To force acquisition of the device, select the
device and go to SNMP > SNMP Re-acquire in the NetMonitor menu bar.
* Custom MIBs may be required for some devices. Custom MIBs allow polling Non-SonicWALL or Non-Standard
based SNMP enabled devices and to poll information specific to a certain device based on Manufacturer ID.These
MIBs have to be placed in the etc\mibs folder by the GMS Administrator on the Web Server and Monitoring Agent
machine(s) in order to use it for probing.
370
SonicWALL Global Management System Configuration Guide
Managing Realtime Monitors
When a device is configured for monitoring, the data retrieved form these devices are displayed in the form of a
realtime monitor. There are 2 ways to create realtime monitors:
• “Creating a Realtime Monitor or Realtime Monitor Template Using a Dialog”
• “Creating a Realtime Monitor From a Template”
Creating a Realtime Monitor or Realtime Monitor Template Using a Dialog
The Manage Realtime Monitor Dialog enables you to create custom realtime monitors.
1. Select the device(s) you wish to create a realtime monitor for.
2. In the menu bar, go to SNMP > SNMP Manage Realtime Monitors.
Figure 286: Manage Realtime Monitors
3. Click on the
button on the left side of the screen (under Realtime Monitors) to add a new realtime monitor.
4. In the Middle of the screen, select your preferences as follows:
Add selected OIDs*
Individually: Add OID(s) as individual elements.
As a group: Add multiple similar OIDs as one single element.
Add Type
Add To: Add OID(s) to an existing Element.
Insert At: Add OID(s) as a new element in the specified location.
Append: Append OID(s) to the end of the element list.
5. Add a friendly name for the new monitor in the Monitor Name field.
6. If you wish to save the new monitor as a template for future use, click the Save as template checkbox and add
a friendly name for the template.
* It is important that the elements present in a Realtime Monitor Template contain OIDs that are present in the
devices that the template is applied to. Applying a template which contains un-relevant OIDs can produce unexpected results.
Configuring and Working with SonicWALL GMS
371
7. Choose your display type and chart style as follows:
Display Type
Table: Data is displayed in a tabular format.
Graph: Data is displayed in a graphical format.
Chart Style
Used only when display
type is set to graph.
Plot: Generates graph in plot format.
Bar: Generates graph in bar format.
Area: Generates graph in area format.
Pie: Generates graph in pie format.
8. Navigate to the MIB Tree list and select the OIDs you wish to add.
9. Click the
button on the right side of the screen (under MIB Tree) to add the selected MIB(s) to the
Elements list.
Note: You may also drag and drop MIBs from the MIB Tree into the Elements list instead of clicking the add button.
10. Enter a friendly name for the element you just added by double-clicking the display name field corresponding
to the new element.
11. Specify a threshold value for the alert monitor in the Threshold field corresponding to the new element.
12. Click the Apply button to save changes and create the realtime monitor.
Creating a Realtime Monitor From a Template
Complete the following steps to set up a realtime monitor using one or more templates:
1. Select the device(s) you wish to create a realtime monitor for.
2. In the menu bar, go to SNMP > SNMP Apply Realtime Monitor Templates.
Figure 287: .SNMP Apply Realtime Monitor Templates
3. Select the templates (ctrl-click for multiple selections) you wish to use for monitoring the selected device(s).
4. Click the Apply button to create the Realtime Monitor.
372
SonicWALL Global Management System Configuration Guide
Viewing Realtime SNMP Monitoring Information
GMS NetMonitor allows you to view realtime monitoring data for one or multiple devices simultaneously. Data
represented in these charts will show the last hour of activity for the specified node. In order to view the realtime
monitoring information for one or more devices:
1. Select the device(s) you wish to monitor from the GMS NetMonitor main status screen (ctrl-click for multiple
devices).
2. In the menu bar, select SNMP > SNMP Realtime Monitor Status.
3. In the Realtime Monitors window, select one or more nodes to monitor. The appropriate graphs and or tables
will be loaded into the monitoring window on the right side of the screen.
Note: Data in the monitoring windows is refreshed automatically based on the auto-refresh interval specified in
NetMonitor Preferences. While you may do a manual refresh of the graphs and charts, it is not necessary to do so.
Figure 288: Realtime Monitor Status
4. To display historical charts (daily, weekly, monthly) for a node, double-click on the desired realtime graph in
the monitoring window on the right side of the screen
Figure 289: SNMP Realtime Monitor Status: Historical Charts.
Note: Only one history chart window may be opened at a time. It is possible, however, to display historical charts
for multiple nodes by selecting the charts you wish to view with ctrl-click and then clicking the
top right side of the screen.
button at the
Configuring and Working with SonicWALL GMS
373
Managing Severity and Thresholds
Configuring Severity and Thresholds allows you to be notified when the value of a monitored OID exceeds a set
level. These levels are set in the Manage Severity dialog and are then used to define your alerts by assigning a
level of severity to each threshold, set in the Manage Threshold dialog.
Managing Severity
To configure your Severity settings:
1. In the menu bar, select Tools > Manage Severity.
Figure 290: Manage Severity.
2. Add a new severity by clicking the
button and entering a name for the severity.
3. Move the new severity to a different priority level by having the severity selected in the list and using the
and
buttons.
4. Change the color of the severity by having the severity selected in the list and clicking the
5. To delete a severity, have the severity selected in the list and click the
button.
button.
Note: A severity can not be deleted if it is being used by one or more threshold elements. In order to delete a severity, you must make sure all corresponding threshold elements are first unassociated with that severity.
Managing Thresholds
Every element in a threshold is assigned an operator, value and severity. These thresholds are used to notify the user
when an element reaches a certain severity. To configure your thresholds:
1. In the menu bar, select Tools > Manage Thresholds.
Figure 291: Manage Thresholds.
374
SonicWALL Global Management System Configuration Guide
2. Click the
button under Threshold and enter a friendly name to add a new threshold.
3. Click the
button under Elements to add a new element to the threshold.
4. Configure the Operator, Value and Severity fields in the new element as follows:
Operator
Choose an operator as a modifier for your value.
Value
Enter an alpha or numeric value. Numeric values are entered in bytes.
Severity
Choose a severity from the list to correspond with the operator and value.
Figure 292: The following threshold triggers a Low-level Warning at a value of less than 100000 bytes.
5. Click the Apply button to save your changes.
Note: Thresholds are global settings and will be ran across all available nodes.
Viewing Threshold Alerts in the Dashboard
The Dashobard View is a screen where an alert about an SNMP Realtime Monitor satisfying user-defined threshold
conditions are displayed. When a threshold alert is triggered, information about the device, realtime monitor and
the element that triggered the alert is shown in this screen.
Figure 293: Threshold Alert Dashboard
Managing SMTP Scheduled Reports
You can schedule reports form realtime monitors to be sent by e-mail or archived to a location on disk. To create a
scheduled report:
1. In the menu bar, select SNMP > Manage Scheduled Reports.
2. Click the
button to add a new report.
3. Enter a friendly name for the report in the Report field.
4. Enter a description for the report in the Description field.
5. Optionally, you may check Disable this report to disable the current report and save it for future use.
Configuring and Working with SonicWALL GMS
375
6. Check the Email check box to enable e-mailing of this report.
7. Enter your SMTP server information in the SMTP server field.
8. Enter a To address, From address, Subject and Body for the e-mail in the appropriate fields.
9. Check the Archive checkbox and enter a location in the Save Directory* field in order to archive this report on
disk.
10. Choose a Report Type and Realtime Report Type as follows:
Report Type
Specifies how often the report will be sent out.
Daily: Sent ever day
Weekly: Sent every week
Monthly: Sent ever month
Realtime Report Type
(for charts only)
Specifies the time range a report will cover.
Realtime: Reports only the data at the time the report is sent
Hourly: Reports hourly data form the last 24 hours.
Daily: Reports daily data from the last 7 days.
Monthly: Reports Monthly data from the last 12 months.
Generate reports in
XML
Sends reports as an XML attachment
Include all data in a
Single report
Includes all reports in a single e-mail, with the option to send
reports inline instead of as an attachment.
Zip reports to single file
Will zip all reports into a single zip attachment, with the option to
password protect the zip file.
Template Folder Name
The local folder where your template will be saved**
*If the directory path entered is invalid, the archive will be saved to the default path of
[sgms_directory]/Viewpoint/reports
** This field only requires the folder name to be entered, not the complete path.
376
SonicWALL Global Management System Configuration Guide
11. Select the checkboxes for the realtime monitors you wish to include in this report.
12. Click the Apply button to save this Scheduled Report.
Dashboard and E-mail Threshold Alerts
GMS NetMonitor sends e-mail alerts for ever threshold severity you configure. In addition to e-mail alerts, you can
also set dashboard alerts by choosing a minimum severity for the alert to show. The dashboard will show only the
alerts as of the last refresh.
To set dashboard threshold alerts:
1. In the menu bar, select Tools > Preferences.
Figure 294: Preferences
2. In the Monitor tab of the Preferences window, select a Minimum Severity to Show Alert in Dashboard form
the drop-down menu.
3. Click the Apply button to save changes.
To set e-mail threshold alerts:
1. Select the device(s) you wish to configure alerts for from the GMS NetMonitor main status screen by clicking
(ctrl-click for multiple devices).
2. In the menu bar, select Tools > Alert Settings.
Figure 295: Alert Settings
3. Select the Notify by Email check box to send the SonicWALL GMS administrator(s) e-mail when the status of
a device changes.
4. Select the Notify by SNMP Trap check box to generate an SNMP trap when the status of a device changes,
5. Choose to apply settings to Selected Devices or to All Devices.
6. Click the Apply button to save changes.
Configuring and Working with SonicWALL GMS
377
Monitoring Devices Behind a SonicWALL Appliance
To monitor devices behind a SonicWALL appliance, do one of the following:
•
•
Create a VPN tunnel to the remote firewall that makes all LAN subnets accessible to the Net Monitor.
Create NAT Policies that allow specific types of traffic through.
For example, if TCP Probe is chosen as the monitor type, TCP connections must be allowed to the specified
port. If Ping is chosen as the monitor type, ICMP must be allowed.
Adding Custom Icons to the Net Monitor
The Net Monitor supports custom icons that it will display in the Net Monitor window. The icons must be 16 x 16
pixels and created in the .GIF format. To add new icons to the Net Monitor, copy them to the following directory:
<gms_directory>\Tomcat\webapps\sgms\images\monitor
Real-Time Syslog
The real-time syslog utility enables you to diagnose the system by viewing the syslog messages in real time.
Note: Only use this utility when needed for diagnostic purposes.
To open the real-time syslog utility, follow these steps:
1. Start and log into SonicWALL GMS.
2. Click the Monitor tab.
3. Expand the Tools tree and click Real-Time Syslog. The Real-Time Syslog page appears.
4. If the Syslog Reader is not already running, click Start Syslog Reader.
5. Click Show Syslog Tail Window. The Syslog Viewer appears showing the latest syslog entries (Figure 296).
Figure 296: Syslog Viewer
6. To change how many messages are displayed, select a number from the Number of Messages list box.
7. To change how often the Syslog Viewer is refreshed, select the time from the Refresh Time list box.
8. To start the syslog viewer, click the Start button. To stop the viewer, click the Stop button.
9. To search for text, use the browser’s Find utility.
10. When you are finished, close the Syslog Viewer.
378
SonicWALL Global Management System Configuration Guide
APPENDIX C
Troubleshooting Tips
This appendix describes troubleshooting tips and other technical information.
SonicWALL GMS Log Files
SonicWALL GMS provides a number of log files that can be used for troubleshooting. These files are located in the
SonicWALL GMS Logs directory and are:
•
•
•
•
•
•
•
•
•
•
phase2install.log—Phase 2 Installation log
schedulerDbg.txt—GMS Scheduler log in debug mode
schedulerLog.txt—GMS Scheduler log in non-debug mode
SGMSWebServerLog.txt—GMS Web Server log
tomcaterr.log—Tomcat log
tomcatout.log—Tomcat log
vpSchedulerDbg.txt—GMS ViewPoint Scheduler log in debug mode
vpSchedulerLog.txt—GMS ViewPoint Scheduler log in non-debug mode
vpSummarizerDbg.txt—GMS ViewPoint Summarizer log in debug mode
vpSummarizerLog.txt—GMS ViewPoint Summarizer log in non-debug mode
The following log files are also available:
• <gms_directory>\SonicWALL_GMS_2.3_installLog.log—Phase 1 Installation log
• C:\sgms23_uninstall.log—Uninstall log
Encrypting the sgmsConfig.xml File
To encrypt text for use in the sgmsConfig.xml and web.xml files, do the following:
1. Navigate to the <gms_directory>:\bin folder.
2. Enter the following command:
java -cp . TEAV text
where text is the text string to encrypt.
This command returns the encrypted string.
3. Add the encrypted string to the sgmsConfig.xml or web.xml file.
Note: This procedure only performs encryption.
SonicWALL Information that Remains in the Database
When a managed SonicWALL appliance is deleted from SonicWALL GMS management, all records pertaining to
the managed SonicWALL appliance are removed from the database except for the following:
•
•
SonicWALL GMS log for the managed SonicWALL appliance.
ViewPoint related logs/summaries.
379
Resetting the Admin Password
To reset the admin user’s password to default value of 'password', enter the following from the command-line
prompt:
osql -U DBuser -P DBpassword -q "exit(update sgmsdb.dbo.users set password =
'5f4dcc3b5aa765d61d8327deb882cf99' where id like 'admin')"
where DBuser is the SGMSDB username and DBpassword is the SGMSDB password.
Using Remote Management feature with SonicWALL GMS
If you are trying to enable the Remote Management feature in a SonicWALL appliance that is under
SonicWALL GMS management, ensure that you include the IP address of the machine from which you will
remotely access the managed SonicWALL. This remote machine cannot be the SonicWALL GMS server.
Copying/Pasting into SonicWALL GMS
Java Plug-in 1.3 and later does not allow applets to access the user clipboards. To circumvent this, you need to
explicitly allow applets to access your clipboard. To do this, follow these steps:
1. Open the java.policy file with a text editor. It is usually located in the following directory:
c:\Program Files\JavaSoft\JRE\1.3\lib\security
2. Add the following line to the top of the file after the “// “standard” properties that can be read by anyone”:
permission java.awt.AWTPermission “accessClipboard”, “write”;
3. Save the java.policy file and exit.
Renewing/Extending a SonicWALL GMS Demo License
The GMS demo license is valid for 30 days. To renew the demo license for another 30 to 60 days, contact SonicWALL Technical Support.
Transferring Appliances from Mysonicwall.com to SonicWALL GMS
During the initial registration of SonicWALL GMS, an account gets created for the SonicWALL GMS on the
Mysonicwall.com. If you have one or more SonicWALL appliances that are registered under another Mysonicwall.com account, any attempt to register those appliances will fail because they are already registered to another
user.
To manage the SonicWALL appliances with SonicWALL GMS, they need to be transferred from the old Mysonicwall.com account to the SonicWALL GMS account. To do this, follow these steps:
1. Login into your personal Mysonicwall.com account.
2. Select the registered SonicWALL appliance.
3. Choose the Transfer option.
4. Enter the SonicWALL GMS serial number (license) in the New User Name field, and the SonicWALL GMS
administrator's e-mail address in the E-mail ID field.
Note: The SonicWALL GMS e-mail address is the e-mail address that you entered in the SonicWALL GMS Registration page during the initial registration.
5. Schedule a task to automatically synchronize the SonicWALL GMS with the SonicWALL appliance's local settings.
380
SonicWALL Global Management System Configuration Guide
Encrypted Data
The sgmsConfig.xml and web.xml files contain encrypted data. The following information is encrypted using the
Tiny Encryption technology:
•
•
•
•
•
•
Database Password
Database Name
Database Username
Database Owner
SGMS Gateway Password
SGMS Gateway IP Address
Non-encrypted GMS account password
The password for the GMS account that was created on the SonicWALL registration site, Mysonicwall.com, is not
encrypted. It is a cleartext password and is saved in the SonicWALL GMS database, SGMSDB.
Changing Task Execution Retries
During the GMS Scheduler window of operation, some tasks may not get executed. These tasks are automatically
reattempted after a specified period of time.
By default, SonicWALL GMS attempts to execute a failed task every ten minutes within the window of operation.
To change this setting, open the sgmsConfig.xml with a text editor, change the schedulerTaskRetryWaitMinutes
parameter, save the file, and exit.
To specify how many times SonicWALL GMS attempts to execute a task within the window of operation (default:
5), open the sgmsConfig.xml with a text editor, change the schedulerTaskRetries parameter, save the file, and exit.
Reducing Missed Heartbeat Messages Frequency
By default, SonicWALL appliances send heartbeat messages every sixty seconds to SonicWALL GMS. If
SonicWALL GMS does not receive a heartbeat message within three minutes, the SonicWALL appliance will be
marked as “Down.”
To change how long SonicWALL GMS waits before marking a SonicWALL appliance as “Down,” follow these
steps:
1. Open the sgmsConfig.xml file with a text editor.
2. Add the following to the end of the file before the </Configuration> section.
Parameter name="scheduler.missedreportthreshold" value=""
3. Enter a new value for the missed report threshold.
4. Save the file and exit.
Using the Import Feature from Applet
To use the SonicWALL GMS Import option from a remote browser, follow these steps:
1. Open the java.policy file with a text editor. It is usually located in the following directory:
c:\Program Files\JavaSoft\JRE\1.3\lib\security
2. Add the following line to the end of the file:
// permission granted to all domains to use GMS' Import option
grant {
permission java.io.FilePermission "<<ALL FILES>>", "read, write, delete, execute";
permission java.util.PropertyPermission "user.home", "read, write";
permission java.lang.RuntimePermission "modifyThread";
};
grant {
permission java.lang.RuntimePermission "accessClassInPackage.sun.misc";
381
};
3. Save the file and exit.
Drive Mapping Problems
If you encounter SonicWALL GMS drive mapping issues, check the SonicWALL log files. If you find messages
such as “File cannot be saved to specified location,” follow these steps to ensure each SonicWALL GMS service
maps the drive properly:
1. Make sure that SonicWALL GMS has adequate write permissions on the target drive.
2. Create an empty file for the service that generated the error and copy it to the \etc folder of the
SonicWALL GMS installation directory:
Table 5:
File Name
Service Name
sgmsInitSyslogd.bat
Syslog Collector service
sgmsInitVpScheduler.bat
VP Scheduler service
sgmsInitVpSummarizer.bat
VP Summarizer service
3. Edit the file and add the following line:
net use drive_letter: \\system_name\directory
4. Save the changes.
5. Restart SonicWALL GMS.
382
SonicWALL Global Management System Configuration Guide
APPENDIX D
Starting and Stopping SonicWALL GMS Processes
Windows Processes
The following is the list of SonicWALL GMS Windows processes:
•
•
•
•
•
GMS Scheduler
GMS ViewPoint Scheduler
GMS ViewPoint Summarizer
GMS Web Server
GMS SNMP Manager
Starting or Stopping Processes
To start or stop a process, follow these steps:
1. Click Start and select Control Panel.
2. Double-click Administrative Tools.
3. Double-click Component Services. The Component Services window appears.
4. Select Services.
5. Scroll down and select the service that you would like to start or stop.
6. Select from the following:
• To start a service, right-click the service and select Start. The service starts.
• To stop a service, right-click the service and select Stop. The service stops.
UNIX Processes
The following is the list of SonicWALL GMS UNIX processes:
• Email Report Scheduler—sgmsvp1.sh
• Summarizer—sgmsvp2.sh
• Scheduler—sgmssched.sh
• Web Server—tomcat.sh (web server)
• SNMP Manager—sgmsnmpmgr.sh
• Syslog Collector—syslogd.sh
• Net Monitor—monitord.sh
Starting or Stopping Processes
To start or stop a process, follow enter one of the following commands:
<sgms_directory>/viewpoint/sgmsvp1.sh {start | stop}
<sgms_directory>/viewpoint/sgmsvp2.sh {start | stop}
<sgms_directory>/scheduler/sgmssched.sh {start | stop}
<sgms_directory>/tomcat/bin/tomcat.sh {start | stop}
<sgms_directory>/scheduler/sgmsnmpmgr.sh {start | stop}
383
<sgms_directory>/viewpoint/syslogd.sh {start | stop}
<sgms_directory>/scheduler/monitord.sh {start | stop}
384
SonicWALL Global Management System Configuration Guide
APPENDIX E
Remotely Accessing SonicWALL GMS
In some cases, you might want to access the SonicWALL Global Management System (SonicWALL GMS) Console from outside the network in which it resides. In these situations, you will need to select from one of the following three access methods:
•
•
•
Existing Tunnel
Proxy Server
Multihomed SonicWALL GMS Server
Using an Existing VPN Tunnel
Using an existing VPN Tunnel is the simplest method for remotely managing the SonicWALL appliance. However,
it is not scalable, requires LAN-to-LAN connectivity, and if you make any changes to the VPN Tunnel that it uses,
it will affect connectivity.
Figure 297:
12.12.12.1
63.201.142.225
SGMS
Workstation
SOHO3
PRO 300
Using a Proxy Server
Using a proxy server enables you to use out-of-band management (management outside the VPN) and it allows you
to restrict SonicWALL GMS management to a single IP address. However, it does require a third-party proxy
server.
385
Figure 298:
209.14.1.12
Proxy Server
12.12.12.1
63.201.142.225
SGMS 10.10.10.1
Workstation
SOHO3
PRO 300
Using a Multihomed SonicWALL GMS Server
Using a proxy server enables you to use out-of-band management and keeps traffic secure. However, it requires an
extra firewall and additional configuration.
In the following example, a LAN-to-LAN VPN Tunnel is created between the new firewall and the SGMS Gateway
firewall. Additionally, a connection is established between the workstation and the new SonicWALL appliance.
Figure 299:
The SonicWALL GMS server is provided with an additional NIC, which is used by users that are behind managed
firewalls. This NIC must be installed without a configured gateway and routes must be added to the GMS server.
You will also need to modify the sgms_config.xml file located in the root directory by adding the following line:
<Parameter name="scheduler.IPAddress" value="second_nic_ip_address" />
This ensures that SonicWALL GMS will not create an additional agent when detecting the second NIC.
386
SonicWALL Global Management System Configuration Guide
APPENDIX F
SonicWALL GMS File
SonicWALL Global Management System (SonicWALL GMS) stores its configuration information in the
sgmsConfig.xml file.
The following table contains the contents of the sgmsConfig.xml file. Each of these parameters was configured during installation or can be configured from the SonicWALL GMS UI.
Table 6: The sgmsConfig.xml File
LANGUAGE
COUNTRY
autoRegisterAddedUnits
debug
installDir
dbtype
dbhost
dbport
dbname
dbuser
dbowner
datasource
dbpassword
dbconnections
dbdriver
dburl
reportsOn
licensPath
licenseTimeout
GatewayVPNLimit
log.filePath
log.fileSize
maxLogFileSizeInBytes
scheduler.controlPort
scheduler.count
scheduler.scheduerPorts
Specifies the language used by SonicWALL GMS (default: en).
Specifies the country (default: US).
Specifies whether new SonicWALL appliances are automatically registered when added to SonicWALL GMS. The default setting is 1,
which automatically adds units. To configure SonicWALL GMS to
not register new appliances, enter 0.
Specifies the debugging level (Levels 0, 1, 2, or 3). The default setting
0, which specifies no debugging.
Specifies where SonicWALL GMS is installed.
Specifies the type of database used.
Specifies the IP address of the database server.
Specifies the database port.
Specifies the database name. This is encrypted using Tiny Encryption
technology.
Specifies the database username. This is encrypted using Tiny Encryption technology.
Specifies the database owner. This is encrypted using Tiny Encryption
technology.
Specifies the data source.
Specifies the database password. This is encrypted using Tiny Encryption technology.
Number of database connections (default:20).
Specifies the database driver.
Specifies the URL of the database.
Indicates whether ViewPoint reporting is enabled. The value 0 indicates ViewPoint is disabled; the default setting 1 indicates ViewPoint
is enabled.
Path to the SonicWALL GMS license file.
Internal use only.
Number of security associations supported by the SGMS Gateway.
Specifies the path to the scheduler log file.
Specifies the maximum log file size before truncation (in kilobytes).
Specifies the maximum log file size of the debug logs before truncation (in bytes).
Internal use only.
Internal use only.
Internal use only.
387
scheduler.dispplayNames
scheduler.startHour
scheduler.endHour
scheduler.terminate
Internal use only.
Specifies when the scheduler activity window begins.
Specifies when the scheduler activity window ends.
To disable the scheduler service, specify the value “true” (default:
false).
scheduler.vpnGatewayIP
Specifies the IP address for the SGMS Gateway. This is encrypted
using Tiny Encryption technology.
scheduler.vpmGatewayPassword
Specifies the SGMS gateway password. This is encrypted using Tiny
Encryption technology.
scheduler.prefsDir
Specifies where the firewall configuration files are saved.
scheduler.schedulerTaskRetries
Specifies the number of times the scheduler will attempt to execute a
failed task (default: 5).
scheduler.schedulerTaskRetryWaitMinutes Specifies how long the scheduler will wait before re-executing a task
(default: 10 minutes).
snmpmgr.terminate
To disable the SNMP Manager service, specify the value “true”
(default: false).
syslogHandlerThreadCount
Specifies the maximum number of threads spawned by the Summarizer. This value can be set from 1 to 4. Values greater than 4 will be
treated as a value of ‘1’.
syslog.syslogParserPort
Internal use only.
syslog.syslogServerPort
Internal use only.
syslog.launchSyslogServer
Internal use only.
syslog.forwardToHost
Specifies another host that will receive syslog messages.
syslog.forwardToHostPort
Specifies the port of the host that will receive syslog messages.
syslog.terminate
To disable the syslog service, specify the value “true” (default: false).
scheduler.missedreportthreshold
Specifies the number of missed reports or intervals before
SonicWALL GMS declares a managed SonicWALL appliance
“Down” (default: 3). If ‘0’ is specified, the SonicWALL appliance will
never be reported as down.
vpSchedulerHandlerThreadCount
Specifies the maximum number of threads spawned by the Scheduler.
This value can be set from 1 to 20 (default: 10).
vpnscheduler.terminate
To disable the VPN Scheduler service, specify the value “true”
(default: false).
vpnsummarizer.terminate
To disable the VPN Summarizer service, specify the value “true”
(default: false).
388
SonicWALL Global Management System Configuration Guide
APPENDIX G
SonicWALL GMS Error Messages
This appendix contains information on SQL and Oracle SonicWALL Global Management System
(SonicWALL GMS) error messages that will receive alert e-mails. To view or edit the complete list of
SonicWALL GMS error codes or add new error messages, open the ErrorCodes.txt file in the <gms_directory>\etc
folder.
SQL Server Error Messages
The following table contains SQL Server error messages.
.
ID
Message
701
708
913
921
922
927
1105
8624
8902
8901
8645
There is insufficient system memory to run this query.
Low on virtual memory. Increase virtual memory on server.
Could not find Database ID.
Database has not yet been recovered yet. Wait and try again.
Database is being recovered. Wait until recovery is finished.
Database cannot be opened. It is in the middle of a restore.
Could not allocate space for object.
Internal SQL Server Error.
Memory allocation error.
Deadlock detected.
A time out occurred while waiting for memory resources.
Oracle Error Messages
The following table contains Oracle error messages.
ID
Message
2396
1536
18
603
1000
1034
1033
Exceeded max Idle Time, please connect again.
Space quota exceeded for tablespace.
Maximum number of sessions exceeded.
ORACLE Server session terminated by fatal error.
Maximum open cursors exceeded.
ORACLE not available.
Oracle startup or shutdown in progress.
389
390
SonicWALL Global Management System Configuration Guide
Console_Help_AboutViewPoint_Snwls
Console_Help_AboutGMS_Snwls
Policies_System_Management_Snwls
Console_Management_CustomGroups_Snwls
Policies_Register/Upgrades_RegisterSonicWALLs_Snwls
Console_Management_Users_Snwls
Policies_System_Status_Snwls
Policies_System_Time_Snwls
Policies_System_Administrator_Snwls
Policies_System_Info_Snwls
Policies_System_Settings_Snwls
Policies_System_DiagnosticData_Snwls
Policies_System_SNMP_Snwls
Policies_System_Tools_Snwls
Policies_Network_Settings_Snwls
Policies_Network_WebProxy_Snwls
Policies_Network_Intranet_Snwls
Policies_Network_Routing_Snwls
Policies_Network_RIP_Snwls
Policies_Network_DMZAddresses_Snwls
Policies_Network_One-to-OneNAT_Snwls
Policies_Network_Ethernet_Snwls
Policies_Network_ARP_Snwls
Policies_Network_Interfaces_Snwls
Policies_Network_WANFailoverLB_Snwls
Policies_Network_Zones_Snwls
Policies_Network_DNS_Snwls
Policies_Network_AddressObjects_Snwls
Policies_Network_NATPolicies_Snwls
Policies_Network_IPHelper_Snwls
Policies_Network_ARP_Snwls
Policies_Firewall_Rules_Snwls
Policies_Firewall_Schedules_Snwls
Policies_Firewall_ServiceObjects_Snwls
Policies_Firewall_Services_Snwls
Policies_Firewall_AccessRules_Snwls
Policies_Firewall_Advanced_Snwls
Policies_Firewall_VoIP_Snwls
Policies_Firewall_Multicast_Snwls
Policies_Log_LogSettings_Snwls
Policies_WebsiteBlocking_General_Snwls
Policies_WebsiteBlocking_FilterList_Snwls
Policies_SecurityServices_ContentFilter_Snwls
Policies_WebsiteBlocking_CFLFilterList_Snwls
Policies_WebsiteBlocking_CFSFilterList_Snwls
Policies_WebsiteBlocking_CFSStandard_Snwls
Policies_WebsiteBlocking_CFSPremium_Snwls
Policies_WebsiteBlocking_Customization_Snwls
Policies_WebsiteBlocking_URLKeywords_Snwls
Policies_WebsiteBlocking_WebFeatures_Snwls
Policies_WebsiteBlocking_Consent_Snwls
Policies_WebsiteBlocking_N2H2_Snwls
Policies_WebsiteBlocking_Websense_Snwls
Policies_DHCP_Setup_Snwls
Policies_DHCP_DHCPoverVPN_Snwls
Policies_DHCP_DynamicRanges_Snwls
Policies_DHCP_StaticEntries_Snwls
Policies_Users_LocalGroups_Snwls
Policies_Users_LocalUsers_Snwls
Policies_Users_Settings_Snwls
Policies_Users_ULASettings_Snwls
Policies_VPN_Configure_Snwls
Policies_VPN_Summary_Snwls
Policies_VPN_CACerts_Snwls
Policies_VPN_LocalCerts_Snwls
Policies_VPN_L2TPServer_Snwls
Policies_VPN_Monitor_Snwls
Policies_VPN_CACerts_Snwls
Policies_VPN_LocalCerts_Snwls
Policies_VPN_Configure2.0_Snwls
Policies_VPN_L2TPServer_Snwls
Policies_VPN_Monitor_Snwls
Policies_SecurityServices_AVPassword_Snwls
Policies_SecurityServices_AVConfigure_Snwls
Policies_SecurityServices_EMailFilter_Snwls
Policies_SecurityServices_IntrusionPrevention_Snwls
Policies_SecurityServices_GlobalSecurityClient_Snwls
Policies_HardwareFailover_Configure_Snwls
Policies_Wireless_StationStatus_Snwls
Policies_Wireless_SonicPoints_Snwls
Policies_Wireless_Settings_Snwls
Policies_Wireless_WEPEncryption_Snwls
Policies_Wireless_Advanced_Snwls
Policies_Wireless_MACFilterList_Snwls
Policies_Wireless_IDS_Snwls
Policies_WGS_Settings_Snwls
Policies_WGS_Settings_Snwls
Policies_WGS_URLAllowList_Snwls
Policies_WGS_IPDenyList_Snwls
Policies_WGS_CustomLogin_Snwls
Policies_Dialup_Profile_Snwls
Policies_Dialup_Configure_Snwls
Policies_Register/Upgrades_FirmwareUpgrade_Snwls
Policies_Register/Upgrades_ServiceLicenses_Snwls
Policies_Register/Upgrades_LicenseSharing_Snwls
Policies_Register/Upgrades_UsedActivationCodes_Snwls
Console_UserSettings_General_Snwls
Console_Management_GMSSettings_Snwls
Console_Management_ViewPointSettings_Snwls
Console_Log_ViewLog_Snwls
Console_Log_Configuration_Snwls
Console_Tasks_ScheduledTasks_Snwls
Console_Management_Sessions_Snwls
Console_Management_AlertSettings_Snwls
Console_Management_eMail/AlertSettings_Snwls
management_MOTD
Console_Management_Agents_Snwls
management_agents
Console_Management_SNMPManagers_Snwls
management_snmp_managers
Console_Management_InheritanceFilters_Snwls
Console_Management_MessageoftheDay_Snwls
management_inheritance_settings
management_MOTD
Console_Licenses_GMSLicense_Snwls
Console_Diagnostics_DebugLogSettings_Snwls
Console_Diagnostics_RequestSnapshot_Snwls
Console_Diagnostics_SnapshotStatus_Snwls
Console_Licenses_GMSUpdates_Snwls
Console_Licenses_RegisteredUserInfo_Snwls
Console_Tools_GMSNavigation_Snwls
Console_Tools_VPN_Monitor
Console_Tools_Syslog_Tail