* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Chapter 1
Asynchronous Transfer Mode wikipedia , lookup
Distributed firewall wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Computer network wikipedia , lookup
Deep packet inspection wikipedia , lookup
Network tap wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Internet protocol suite wikipedia , lookup
Peer-to-peer wikipedia , lookup
Quality of service wikipedia , lookup
Airborne Networking wikipedia , lookup
UniPro protocol stack wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Computer Networks: A Systems Approach, 5e
Larry L. Peterson and Bruce S. Davie
Chapter 1
Foundation
Copyright © 2010, Elsevier Inc. All rights Reserved
1
Chapter 1
Problems
How to build a scalable network that will support
different applications?
What is a computer network?
How is a computer network different from other
types of networks?
What is a computer network architecture?
2
Chapter 1
Chapter Outline
Applications
Requirements
Network Architecture
Implementing Network Software
Performance
3
Chapter 1
Chapter Goal
Exploring the requirements that different
applications and different communities place on
the computer network
Introducing the idea of network architecture
Introducing some key elements in implementing
Network Software
Define key metrics that will be used to evaluate
the performance of computer network
4
Chapter 1
Applications
Most people know about the Internet (a
computer network) through applications
World Wide Web
Email
Online Social Network
Streaming Audio Video
File Sharing
Instant Messaging
…
5
Chapter 1
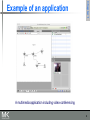
Example of an application
A multimedia application including video-conferencing
6
URL
Hyper Text Transfer Protocol
TCP
Uniform resource locater
http://www.cs.princeton.edu/~llp/index.html
HTTP
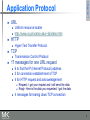
Chapter 1
Application Protocol
Transmission Control Protocol
17 messages for one URL request
6 to find the IP (Internet Protocol) address
3 for connection establishment of TCP
4 for HTTP request and acknowledgement
Request: I got your request and I will send the data
Reply: Here is the data you requested; I got the data
4 messages for tearing down TCP connection
7
Application Programmer
List the services that his application needs: delay
bounded delivery of data
Network Designer
Chapter 1
Requirements
Design a cost-effective network with sharable
resources
Network Provider
List the characteristics of a system that is easy to
manage
8
Need to understand the
following terminologies
Scale
Link
Nodes
Point-to-point
Multiple access
Switched Network
(a)
(b)
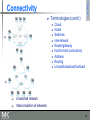
Chapter 1
Connectivity
Circuit Switched
Packet Switched
Packet, message
Store-and-forward
Point-to-point
Multiple access
9
Terminologies (contd.)
(a)
Chapter 1
Connectivity
Cloud
Hosts
Switches
internetwork
Router/gateway
Host-to-host connectivity
Address
Routing
Unicast/broadcast/multicast
(b)
(a)
(b)
A switched network
Interconnection of networks
10
Chapter 1
Section Summary
The main idea to take away from this discussion is that
we can define a network recursively as consisting of two
or more nodes connected by a physical link, or as two or
more networks connected by a node. In other words, a
network can be constructed from a nesting of networks,
where at the bottom level, the network is implemented by
some physical medium.
Among the key challenges in providing network
connectivity are the definition of an address for each
node that is reachable on the network (including support
for broadcast and multicast), and the use of such
addresses to forward messages toward the appropriate
destination node(s).
11
Resource: links and
nodes
How to share a link?
Multiplexing
De-multiplexing
Synchronous Time-division
Multiplexing
Multiplexing multiple logical flows
over a single physical link
Chapter 1
Cost-Effective Resource Sharing
Time slots/data
transmitted in
predetermined slots
12
FDM: Frequency Division
Multiplexing
Statistical Multiplexing
A switch multiplexing packets from
multiple sources onto one shared
link
Chapter 1
Cost-Effective Resource Sharing
Data is transmitted based
on demand of each flow.
What is a flow?
Packets vs. Messages
FIFO, Round-Robin,
Priorities (Quality-ofService (QoS))
Congested?
LAN, MAN, WAN
SAN (System Area
Networks
13
Chapter 1
Statistical multiplexing
The bottom line is that statistical multiplexing defines a
cost-effective way for multiple users (e.g., host-to-host
flows of data) to share network resources (links and
nodes) in a fine-grained manner.
It defines the packet as the granularity with which the
links of the network are allocated to different flows, with
each switch able to schedule the use of the physical links
it is connected to on a per-packet basis.
Fairly allocating link capacity to different flows and
dealing with congestion when it occurs are the key
challenges of statistical multiplexing.
14
Chapter 1
LAN, MAN, WAN
One way to characterize networks is according to their
size. Two well-known examples are local area networks
(LANs) and wide area networks (WANs); the former
typically extend less than 1 km, while the latter can be
worldwide. Other networks are classified as metropolitan
area networks (MANs), which usually span tens of
kilometers.
The reason such classifications are interesting is that
the size of a network often has implications for the
underlying technology that can be used, with a key factor
being the amount of time it takes for data to propagate
from one end of the network to the other; we discuss this
issue more in later chapters.
15
Chapter 1
LAN x WAN
An interesting historical note is that the term wide area
network was not applied to the first WANs because there
was no other sort of network to differentiate them from.
When computers were incredibly rare and expensive,
there was no point in thinking about how to connect all
the computers in the local area—there was only one
computer in that area.
Only as computers began to proliferate did LANs
become necessary, and the term “WAN” was then
introduced to describe the larger networks that
interconnected geographically distant computers.
16
Chapter 1
SAN
Another kind of network that we need to be aware of is
SANs (usually now expanded as storage area networks,
but formerly also known as system area networks). SANs
are usually confined to a single room and connect the
various components of a large computing system.
For example, Fibre Channel is a common SAN
technology used to connect high-performance computing
systems to storage servers and data vaults.
Although this book does not describe such networks in
detail, they are worth knowing about because they are
often at the leading edge in terms of performance, and
because it is increasingly common to connect such
networks into LANs and WANs.
17
Chapter 1
Support for Common Services
Logical Channels
Application-to-Application communication path or a
pipe
Process communicating over an
abstract channel
18
Chapter 1
Common Communication Patterns
Client/Server
Two types of communication channel
Request/Reply Channels
Message Stream Channels
19
Network should hide the errors
Bits are lost
Chapter 1
Reliability
Bit errors (1 to a 0, and vice versa)
Burst errors – several consecutive errors
Packets are lost (Congestion)
Links and Node failures
Messages are delayed
Messages are delivered out-of-order
Third parties eavesdrop
20
Chapter 1
Summary on channels
The key idea to take away from this
discussion is that defining useful channels
involves both understanding the
applications’ requirements and recognizing
the limitations of the underlying
technology.
The challenge is to fill in the gap between
what the application expects and what the
underlying technology can provide. This is
sometimes called the semantic gap.
21
Chapter 1
Network Architecture
Example of a layered network system
22
Chapter 1
Network Architecture
Layered system with alternative abstractions available at a given layer
23
Chapter 1
Protocols
Protocol defines the interfaces between the
layers in the same system and with the layers of
peer system
Building blocks of a network architecture
Each protocol object has two different interfaces
service interface: operations on this protocol
peer-to-peer interface: messages exchanged with
peer
Term “protocol” is overloaded
specification of peer-to-peer interface
module that implements this interface
24
Chapter 1
Interfaces
Service and Peer Interfaces
25
Chapter 1
Protocols
Protocol Specification: prose, pseudo-code, state
transition diagram
Interoperable: when two or more protocols that
implement the specification accurately
IETF: Internet Engineering Task Force
26
Chapter 1
Protocol Graph
Example of a protocol graph
nodes are the protocols and links the “depends-on” relation
27
Chapter 1
Encapsulation
High-level messages are encapsulated inside of low-level messages
28
Chapter 1
OSI Architecture
The OSI 7-layer Model
OSI – Open Systems Interconnection
29
Physical Layer
Handles the transmission of raw bits over a communication link
Data Link Layer
Chapter 1
Description of Layers
Collects a stream of bits into a larger aggregate called a frame
Network adaptor along with device driver in OS implement the
protocol in this layer
Frames are actually delivered to hosts
Network Layer
Handles routing among nodes within a packet-switched network
Unit of data exchanged between nodes in this layer is called a
packet
The lower three layers are implemented on all network nodes
30
Chapter 1
Description of Layers
Transport Layer
Session Layer
Provides a name space that is used to tie together the potentially
different transport streams that are part of a single application
Presentation Layer
Implements a process-to-process channel
Unit of data exchanges in this layer is called a message
Concerned about the format of data exchanged between peers
Application Layer
Standardize common type of exchanges
The transport layer and the higher layers typically run only on endhosts and not on the intermediate switches and routers
31
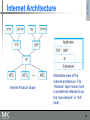
Internet Protocol Graph
Chapter 1
Internet Architecture
Alternative view of the
Internet architecture. The
“Network” layer shown here
is sometimes referred to as
the “sub-network” or “link”
layer.
32
Chapter 1
Internet Architecture
Defined by IETF
Three main features
Does not imply strict layering. The application is free to bypass
the defined transport layers and to directly use IP or other
underlying networks
An hour-glass shape – wide at the top, narrow in the middle and
wide at the bottom. IP serves as the focal point for the
architecture
In order for a new protocol to be officially included in the
architecture, there needs to be both a protocol specification and
at least one (and preferably two) representative implementations
of the specification
33
Chapter 1
Summary Internet architecture
Of these three attributes of the Internet architecture, the
hourglass design philosophy is important enough to bear
repeating.
The hourglass’s narrow waist represents a minimal and
carefully chosen set of global capabilities that allows both
higher-level applications and lower-level communication
technologies to coexist, share capabilities, and evolve
rapidly.
The narrow-waisted model is critical to the Internet’s
ability to adapt rapidly to new user demands and
changing technologies.
34
Chapter 1
Application Programming Interface
Interface exported by the network
Since most network protocols are implemented (those in
the high protocol stack) in software and nearly all
computer systems implement their network protocols as
part of the operating system, when we refer to the
interface “exported by the network”, we are generally
referring to the interface that the OS provides to its
networking subsystem
The interface is called the network Application
Programming Interface (API)
35
Socket Interface was originally provided by the
Berkeley distribution of Unix
- Now supported in virtually all operating systems
Each protocol provides a certain set of services,
and the API provides a syntax by which those
services can be invoked in this particular OS
Chapter 1
Application Programming Interface (Sockets)
36
What is a socket?
Chapter 1
Socket
The point where a local application process attaches
to the network
An interface between an application and the network
An application creates the socket
The interface defines operations for
Creating a socket
Attaching a socket to the network
Sending and receiving messages through the socket
Closing the socket
37
Socket Family
Chapter 1
Socket
PF_INET denotes the Internet family
PF_UNIX denotes the Unix pipe facility
PF_PACKET denotes direct access to the network
interface (i.e., it bypasses the TCP/IP protocol stack)
Socket Type
SOCK_STREAM is used to denote a byte stream
SOCK_DGRAM is an alternative that denotes a
message oriented service, such as that provided by
UDP
38
Chapter 1
Creating a Socket
int sockfd = socket(address_family, type, protocol);
The socket number returned is the socket descriptor for
the newly created socket
int sockfd = socket (PF_INET, SOCK_STREAM, 0);
int sockfd = socket (PF_INET, SOCK_DGRAM, 0);
The combination of PF_INET and SOCK_STREAM implies TCP
39
Chapter 1
Client-Serve Model with TCP
Server
Passive open
Prepares to accept connection, does not actually establish a
connection
Server invokes
int bind (int socket, struct sockaddr *address,
int addr_len)
int listen (int socket, int backlog)
int accept (int socket, struct sockaddr *address,
int *addr_len)
40
Chapter 1
Client-Serve Model with TCP
Bind
Binds the newly created socket to the specified address i.e. the
network address of the local participant (the server)
Address is a data structure which combines IP and port
Listen
Defines how many connections can be pending on the specified
socket
41
Chapter 1
Client-Serve Model with TCP
Accept
Carries out the passive open
Blocking operation
Does not return until a remote participant has established a
connection
When it does, it returns a new socket that corresponds to the
new established connection and the address argument
contains the remote participant’s address
42
Chapter 1
Client-Serve Model with TCP
Client
Application performs active open
It says who it wants to communicate with
Client invokes
int connect (int socket, struct sockaddr *address,
int addr_len)
Connect
Does not return until TCP has successfully established a
connection at which application is free to begin sending data
Address contains remote machine’s address
43
Chapter 1
Client-Serve Model with TCP
In practice
The client usually specifies only remote participant’s
address and let’s the system fill in the local
information
Whereas a server usually listens for messages on a
well-known port
A client does not care which port it uses for itself, the
OS simply selects an unused one
44
Chapter 1
Client-Serve Model with TCP
Once a connection is established, the application
process invokes two operation
int send (int socket, char *msg, int msg_len,
int flags)
int recv (int socket, char *buff, int buff_len,
int flags)
45
#include <stdio.h>
#include <sys/types.h>
#include <sys/socket.h>
#include <netinet/in.h>
#include <netdb.h>
Chapter 1
Example Application: Client
#define SERVER_PORT 5432
#define MAX_LINE 256
int main(int argc, char * argv[])
{
FILE *fp;
struct hostent *hp;
struct sockaddr_in sin;
char *host;
char buf[MAX_LINE];
int s;
int len;
if (argc==2) {
host = argv[1];
}
else {
fprintf(stderr, "usage: simplex-talk host\n");
exit(1);
}
46
/* translate host name into peer’s IP address */
hp = gethostbyname(host);
if (!hp) {
fprintf(stderr, "simplex-talk: unknown host: %s\n", host);
exit(1);
}
/* build address data structure */
bzero((char *)&sin, sizeof(sin));
sin.sin_family = AF_INET;
bcopy(hp->h_addr, (char *)&sin.sin_addr, hp->h_length);
sin.sin_port = htons(SERVER_PORT);
/* active open */
if ((s = socket(PF_INET, SOCK_STREAM, 0)) < 0) {
perror("simplex-talk: socket");
exit(1);
}
if (connect(s, (struct sockaddr *)&sin, sizeof(sin)) < 0) {
perror("simplex-talk: connect");
close(s);
exit(1);
}
/* main loop: get and send lines of text */
while (fgets(buf, sizeof(buf), stdin)) {
buf[MAX_LINE-1] = ’\0’;
len = strlen(buf) + 1;
send(s, buf, len, 0);
}
Chapter 1
Example Application: Client
}
47
#include <stdio.h>
#include <sys/types.h>
#include <sys/socket.h>
#include <netinet/in.h>
#include <netdb.h>
#define SERVER_PORT 5432
#define MAX_PENDING 5
#define MAX_LINE 256
Chapter 1
Example Application: Server
int main()
{
struct sockaddr_in sin;
char buf[MAX_LINE];
int len;
int s, new_s;
/* build address data structure */
bzero((char *)&sin, sizeof(sin));
sin.sin_family = AF_INET;
sin.sin_addr.s_addr = INADDR_ANY;
sin.sin_port = htons(SERVER_PORT);
/* setup passive open */
if ((s = socket(PF_INET, SOCK_STREAM, 0)) < 0) {
perror("simplex-talk: socket");
exit(1);
}
48
if ((bind(s, (struct sockaddr *)&sin, sizeof(sin))) < 0) {
perror("simplex-talk: bind");
exit(1);
}
listen(s, MAX_PENDING);
/* wait for connection, then receive and print text */
while(1) {
if ((new_s = accept(s, (struct sockaddr *)&sin, &len)) < 0) {
perror("simplex-talk: accept");
exit(1);
}
while (len = recv(new_s, buf, sizeof(buf), 0))
fputs(buf, stdout);
close(new_s);
}
Chapter 1
Example Application: Server
}
49
Chapter 1
Performance
Bandwidth
Width of the frequency band
Number of bits per second that can be transmitted over a
communication link
1 Mbps: 1 x 106 bits/second = 1x220 bits/sec
1 x 10-6 seconds to transmit each bit or imagine that a
timeline, now each bit occupies 1 micro second space.
On a 2 Mbps link the width is 0.5 micro second.
Smaller the width more will be transmission per unit time.
50
Chapter 1
Bandwidth
Bits transmitted at a particular bandwidth can be regarded as
having some width:
(a) bits transmitted at 1Mbps (each bit 1 μs wide);
(b) bits transmitted at 2Mbps (each bit 0.5 μs wide).
51
Chapter 1
Bandwidth x Throughput
Bandwidth and throughput are two of the most confusing
terms used in networking.
While we could try to give you a precise definition of
each term, it is important that you know how other people
might use them and for you to be aware that they are
often used interchangeably.
First of all, bandwidth is literally a measure of the width of
a frequency band. For example, a voice-grade telephone
line supports a frequency band ranging from 300 to 3300
Hz; it is said to have a bandwidth of 3300 Hz−300 Hz =
3000 Hz.
52
Chapter 1
Bandwidth x Throughput
If you see the word bandwidth used in a situation in which it
is being measured in hertz, then it probably refers to the
range of signals that can be accommodated.
When we talk about the bandwidth of a communication link,
we normally refer to the number of bits per second that can
be transmitted on the link. This is also sometimes called the
data rate.
We might say that the bandwidth of an Ethernet link is 10
Mbps. A useful distinction can also be made, however,
between the maximum data rate that is available on the link
and the number of bits per second that we can actually
transmit over the link in practice. We tend to use the word
throughput to refer to the measured performance of a
system.
53
Chapter 1
Bandwidth x Throughput
Thus, because of various inefficiencies of implementation, a
pair of nodes connected by a link with a bandwidth of 10
Mbps might achieve a throughput of only 2 Mbps. This
would mean that an application on one host could send
data to the other host at 2 Mbps.
Finally, we often talk about the bandwidth requirements of
an application. This is the number of bits per second that it
needs to transmit over the network to perform acceptably.
For some applications, this might be “whatever I can get”;
for others, it might be some fixed number (preferably no
more than the available link bandwidth); and for others, it
might be a number that varies with time. We will provide
more on this topic later in this section.
54
Chapter 1
Performance
Latency = Propagation + transmit + queue
Propagation = distance/speed of light
Transmit = size/bandwidth
One bit transmission => propagation is important
Large bytes transmission => bandwidth is important
55
Chapter 1
Delay X Bandwidth
We think the channel between a pair of processes as a
hollow pipe
Latency (delay) length of the pipe and bandwidth the
width of the pipe
Delay of 50 ms and bandwidth of 45 Mbps
50 x 10-3 seconds x 45 x 106 bits/second
2.25 x 106 bits = 280 KB data.
Network as a pipe
56
Chapter 1
Delay X Bandwidth
Relative importance of bandwidth and latency
depends on application
For large file transfer, bandwidth is critical
For small messages (HTTP, NFS, etc.), latency is
critical
Variance in latency (jitter) can also affect some
applications (e.g., audio/video conferencing)
57
Chapter 1
Delay X Bandwidth
How many bits the sender must transmit
before the first bit arrives at the receiver if the
sender keeps the pipe full
Takes another one-way latency to receive a
response from the receiver
If the sender does not fill the pipe—send a
whole delay × bandwidth product’s worth of
data before it stops to wait for a signal—the
sender will not fully utilize the network
58
Chapter 1
Delay-Bandwidth product
59
Infinite bandwidth
Chapter 1
Delay X Bandwidth
RTT dominates
Throughput = TransferSize / TransferTime
TransferTime = RTT + 1/Bandwidth x
TransferSize
Its all relative
1-MB file to 1-Gbps link looks like a 1-KB
packet to 1-Mbps link
60
Chapter 1
Relationship between bandwidth and latency
10 MB
10 MB
A 10MB file would fill the 1-Mbps link 80 times,
but only fill the 1-Gbps link 1/12 of one time
61
Chapter 1
Another view on high-speed nets
Another way to think about the situation is that more data
can be transmitted during each RTT on a high-speed
network, so much so that a single RTT becomes a
significant amount of time.
Thus, while you wouldn’t think twice about the difference
between a file transfer taking 101 RTTs rather than 100
RTTs (a relative difference of only 1%), suddenly the
difference between 1 RTT and 2 RTTs is significant—a
100% increase. In other words, latency, rather than
throughput, starts to dominate our thinking about network
design.
62
Chapter 1
Summary
We have identified what we expect from a computer
network
We have defined a layered architecture for computer
network that will serve as a blueprint for our design
We have discussed the socket interface which will be
used by applications for invoking the services of the
network subsystem
We have discussed two performance metrics using
which we can analyze the performance of computer
networks
63