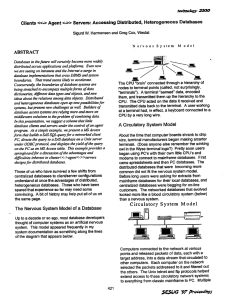
Clients <<-> Agent <->> Servers: Accessing Distributed, Heterogeneous Databases
... program on the server that manages setting up clients so they can display the query form; public use query form objects for the clients to download; a mechanism for managing update, insert, and delete transactions; a method for handling queries to more than one database and combining the answers; an ...
... program on the server that manages setting up clients so they can display the query form; public use query form objects for the clients to download; a mechanism for managing update, insert, and delete transactions; a method for handling queries to more than one database and combining the answers; an ...
dg.o Slides - Columbia University
... What’s an Employee? An appointed officer or employee of USDA including special Government employees (collaborators, consultants and panel members). The term excludes independent contractors. ...
... What’s an Employee? An appointed officer or employee of USDA including special Government employees (collaborators, consultants and panel members). The term excludes independent contractors. ...
ppt slides
... For a given set of keywords, the search component provides interfaces to (1) retrieve matching databases from a set of published databases, and (2) selectively identify tables, columns/rows that need to be searched within each database identified in step (1). ...
... For a given set of keywords, the search component provides interfaces to (1) retrieve matching databases from a set of published databases, and (2) selectively identify tables, columns/rows that need to be searched within each database identified in step (1). ...
Chapter 20: Database System Architectures
... The interface between the front-end and the back-end is through SQL ...
... The interface between the front-end and the back-end is through SQL ...
Chapter 6 Study Tool
... – The data dictionary is transformed into a physical data repository, which also contains the schema and subschemas – The physical repository might be centralized, or distributed at several locations – ODBC – open database connectivity – JDBC – Java database connectivity ...
... – The data dictionary is transformed into a physical data repository, which also contains the schema and subschemas – The physical repository might be centralized, or distributed at several locations – ODBC – open database connectivity – JDBC – Java database connectivity ...
Chapter 1
... Database Models • Collection of logical constructs used to represent data structure and relationships within the database – Conceptual models: logical nature of data representation – Implementation models: emphasis on how the data are represented in the database ...
... Database Models • Collection of logical constructs used to represent data structure and relationships within the database – Conceptual models: logical nature of data representation – Implementation models: emphasis on how the data are represented in the database ...
Autonomics and Data Management
... • Data integration involves assembling information about the relationships between sources: – What sources there are. – The services provided by the source. – The concepts represented in each source. – How the data represented. – What relationships there are between extents. – What mappings exist be ...
... • Data integration involves assembling information about the relationships between sources: – What sources there are. – The services provided by the source. – The concepts represented in each source. – How the data represented. – What relationships there are between extents. – What mappings exist be ...
Empress Offers an Effective Embedded Database Solution
... of applications can benefit from an "embedded database" solution. But what is an embedded database system? An embedded database system is one that can be linked with a client application, so that the application and the DBMS run in a single address space. By embedding the database into the applicati ...
... of applications can benefit from an "embedded database" solution. But what is an embedded database system? An embedded database system is one that can be linked with a client application, so that the application and the DBMS run in a single address space. By embedding the database into the applicati ...
Slide 1
... Private Content Based Image Retrieval Shashank J, Kowshik P, Kannan Srinathan and C.V. Jawahar ...
... Private Content Based Image Retrieval Shashank J, Kowshik P, Kannan Srinathan and C.V. Jawahar ...
Chapter 23: Advanced Data Types and New Applications
... Deletion of an entry in an R-tree done much like a B+-tree deletion. ...
... Deletion of an entry in an R-tree done much like a B+-tree deletion. ...
Oracle Database Security
... Authoritative security studies have documented that more than 80% of information system data losses and attacks have been perpetrated by 'insiders' — those authorized with some level of access to the system and its data. • 80% of threats come from insiders. • 65% of internal threats are undetected. ...
... Authoritative security studies have documented that more than 80% of information system data losses and attacks have been perpetrated by 'insiders' — those authorized with some level of access to the system and its data. • 80% of threats come from insiders. • 65% of internal threats are undetected. ...
Building Mission Critical Applications
... Integrated management Relational Database, Analysis ...
... Integrated management Relational Database, Analysis ...
Database Tables and Normalization
... • Normalized (decomposed) tables require additional processing, reducing system speed. • Normalization purity is often difficult to sustain in the modern database environment. The conflict between design efficiency, information requirements, and processing speed are often resolved through compromise ...
... • Normalized (decomposed) tables require additional processing, reducing system speed. • Normalization purity is often difficult to sustain in the modern database environment. The conflict between design efficiency, information requirements, and processing speed are often resolved through compromise ...
Data Abstraction
... A data model is a collection of concepts for describing data properties and domain knowledge: Data relationships Data semantics Data constraints ...
... A data model is a collection of concepts for describing data properties and domain knowledge: Data relationships Data semantics Data constraints ...
Here> Oracle Database 11g for Data Warehousing
... • Retail customer data (~50 GB) • Concurrent users submitting queries randomly • Executive dashboard with 12 heavy analytical queries • Cache results only at in-line view level • 12 queries run in random, different order – 4 queries cached ...
... • Retail customer data (~50 GB) • Concurrent users submitting queries randomly • Executive dashboard with 12 heavy analytical queries • Cache results only at in-line view level • 12 queries run in random, different order – 4 queries cached ...
database security - S2010
... SQL injection may be possible if input is not filtered for escape characters and is then passed into a SQL statement. This result in the potential manipulation of the statements performed on the database by the end user of the application. The following line of code illustrates this vulnerability: s ...
... SQL injection may be possible if input is not filtered for escape characters and is then passed into a SQL statement. This result in the potential manipulation of the statements performed on the database by the end user of the application. The following line of code illustrates this vulnerability: s ...
eSupport HD Practice
... Ensuring Quality Support by Measuring Quality of Responses Mike Myers Director – Help Desk Operations Robin Rea Process Services Project Manager CompuCom Systems ...
... Ensuring Quality Support by Measuring Quality of Responses Mike Myers Director – Help Desk Operations Robin Rea Process Services Project Manager CompuCom Systems ...
Training Workshop on Advanced Diagnosis and Surveillance
... and beyond those measures provided by the design of the system. •Training for staff who will have access to the system. •Comprehensive user manual. •Specify standards, especially where these are not incorporated into the system, e.g. as pick lists. •One person enters data; another person checks that ...
... and beyond those measures provided by the design of the system. •Training for staff who will have access to the system. •Comprehensive user manual. •Specify standards, especially where these are not incorporated into the system, e.g. as pick lists. •One person enters data; another person checks that ...
Using SQL Queries to Insert, Update, Delete and View Data
... Inserting LOB Column Locators Oracle stores LOB data in separate (alternate) physical location from other types of data LOB locator needs to be created to – Hold information that identifies LOB data type, and – Point to alternate memory location ...
... Inserting LOB Column Locators Oracle stores LOB data in separate (alternate) physical location from other types of data LOB locator needs to be created to – Hold information that identifies LOB data type, and – Point to alternate memory location ...
Overview of SQL Server
... Additionally, backing up and restoring databases is useful for other purposes, such as copying a database from one server to another. By backing up a database from one computer and restoring the database to another, a copy of a database can be made quickly and easily. ...
... Additionally, backing up and restoring databases is useful for other purposes, such as copying a database from one server to another. By backing up a database from one computer and restoring the database to another, a copy of a database can be made quickly and easily. ...