Chapter 2 Data Representation on Bio
... The interesting question is to how to handle all these data types in Figure 2.1.1. Of course, the most efficient solution for the interesting question is to use a uniform representation of data. All data types from outside bio-molecular computing are transformed into this uniform representatio ...
... The interesting question is to how to handle all these data types in Figure 2.1.1. Of course, the most efficient solution for the interesting question is to use a uniform representation of data. All data types from outside bio-molecular computing are transformed into this uniform representatio ...
Solutions #1 - EECS: www
... (a) End hosts. Making the routers responsible for connection reliability would increase complexity and require too much memory. Furthermore, retransmission is not always necessary or desired (live video streaming, for instance). (b) End hosts. You shouldn’t rely on others for keeping your data secur ...
... (a) End hosts. Making the routers responsible for connection reliability would increase complexity and require too much memory. Furthermore, retransmission is not always necessary or desired (live video streaming, for instance). (b) End hosts. You shouldn’t rely on others for keeping your data secur ...
Understanding the Distribution of a Set of Data
... how the data points in the second group are close to the mean of 62 inches which results in a low standard deviation of 1.2. However, the data points in the first group are farther from the mean and the values in the third group are even more spread out from the mean, thus the higher standard deviat ...
... how the data points in the second group are close to the mean of 62 inches which results in a low standard deviation of 1.2. However, the data points in the first group are farther from the mean and the values in the third group are even more spread out from the mean, thus the higher standard deviat ...
No Slide Title
... Thumbprint technique (UC Davis) – allows limited traceback – thumbprint is a statistical digest of an interval of a communications channel – matching thumbprints can be used to reconstruct the path of an intruder ...
... Thumbprint technique (UC Davis) – allows limited traceback – thumbprint is a statistical digest of an interval of a communications channel – matching thumbprints can be used to reconstruct the path of an intruder ...
Double Interpolation
... be somewhat larger that 0.2 m3 /kg, and the volume for the second pair will be smaller. Our sought data point will therefore be bracketed by the four listed points. Now interpolate using the first pair of data points to get v for 1200 kPa and 323◦ C. The general formula is x − x1 ...
... be somewhat larger that 0.2 m3 /kg, and the volume for the second pair will be smaller. Our sought data point will therefore be bracketed by the four listed points. Now interpolate using the first pair of data points to get v for 1200 kPa and 323◦ C. The general formula is x − x1 ...
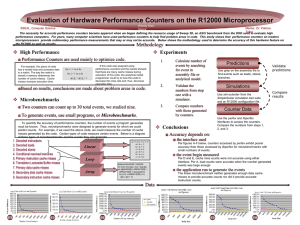
Evaluation of Hardware Performance Counters on the R12000
... The necessity for accurate performance counters became apparent when we began defining the resource usage of Sweep 3D, an ASCI benchmark from the DOD used to evaluate high performance computers. For years, many computer scientists have used performance counters to help find problem areas in code. Th ...
... The necessity for accurate performance counters became apparent when we began defining the resource usage of Sweep 3D, an ASCI benchmark from the DOD used to evaluate high performance computers. For years, many computer scientists have used performance counters to help find problem areas in code. Th ...
Normality distribution testing for levelling data obtained
... Case study showed that it is possible to accept opposite hypothesis about the distribution of the one set of data. As set of measured data was quite big it possible to state that all tests are reliable. This fact could open different questions about results of production measurements. For example du ...
... Case study showed that it is possible to accept opposite hypothesis about the distribution of the one set of data. As set of measured data was quite big it possible to state that all tests are reliable. This fact could open different questions about results of production measurements. For example du ...
Bridging work * gcse to as level sciences. standard defintions and
... These cause readings to differ from the true value by a consistent amount each time a measurement is made. Sources of systematic error can include the environment, methods of observation or instruments used. Systematic errors cannot be dealt with by simple repeats. If a systematic error is suspected ...
... These cause readings to differ from the true value by a consistent amount each time a measurement is made. Sources of systematic error can include the environment, methods of observation or instruments used. Systematic errors cannot be dealt with by simple repeats. If a systematic error is suspected ...
munich-2006
... U2F READOUT In poll mode must the computer react on the trigger. Large overhead in the USB calls for each channel to be read makes it slow. In push mode is all data sent from U2F as soon as it is available (in <=1024 byte bursts) => Computer do not need a trigger. Can have several events in the sam ...
... U2F READOUT In poll mode must the computer react on the trigger. Large overhead in the USB calls for each channel to be read makes it slow. In push mode is all data sent from U2F as soon as it is available (in <=1024 byte bursts) => Computer do not need a trigger. Can have several events in the sam ...
投影片 1 - National Cheng Kung University
... Flow statistics is a basic task of passive measurement and has been widely used to characterize the state of the network. Adaptive Non-Linear Sampling (ANLS) is one of the most accurate and memory-efficient flow statistics method proposed recently. This paper studies the parameter setting problem fo ...
... Flow statistics is a basic task of passive measurement and has been widely used to characterize the state of the network. Adaptive Non-Linear Sampling (ANLS) is one of the most accurate and memory-efficient flow statistics method proposed recently. This paper studies the parameter setting problem fo ...
HW2 - cs.Virginia
... According to the following materials: Capabilities: An ADSL circuit connects an ADSL modem on each end of a twistedpair telephone line, creating three information channels -- a high speed downstream channel, a medium speed duplex channel, depending on the implementation of the ADSL architecture, and ...
... According to the following materials: Capabilities: An ADSL circuit connects an ADSL modem on each end of a twistedpair telephone line, creating three information channels -- a high speed downstream channel, a medium speed duplex channel, depending on the implementation of the ADSL architecture, and ...
ppt
... Sometimes it is preferable to choose a course at random, rather than spend time working out which alternative is best. Main characteristic ...
... Sometimes it is preferable to choose a course at random, rather than spend time working out which alternative is best. Main characteristic ...
Physical Layer - Cloudfront.net
... • Classic problem — a lot of this is math, so we will gloss over. • In networks there are many choices: – don’t detect errors. Let higher layer deal with it end to end. – detect errors and retroactively correct it. – proactively correct errors. ...
... • Classic problem — a lot of this is math, so we will gloss over. • In networks there are many choices: – don’t detect errors. Let higher layer deal with it end to end. – detect errors and retroactively correct it. – proactively correct errors. ...
ber performance over fading channels diversity
... techniques to overcome the destructive effects of fading is Diversity. Diversity is an efficient technique to exploit the random nature of radio propagation by finding methods to generate and extract independent signal paths for communication. The concept behind diversity is relatively simple if one ...
... techniques to overcome the destructive effects of fading is Diversity. Diversity is an efficient technique to exploit the random nature of radio propagation by finding methods to generate and extract independent signal paths for communication. The concept behind diversity is relatively simple if one ...
Designing Parallel Programs
... – Understand the problem that you wish to solve in parallel (from serial program you need to understand the existing code) – Before spending time : determine whether or not the problem is one that can actually be parallelized – Identify the program’s hotspots (Know where of the real work is being do ...
... – Understand the problem that you wish to solve in parallel (from serial program you need to understand the existing code) – Before spending time : determine whether or not the problem is one that can actually be parallelized – Identify the program’s hotspots (Know where of the real work is being do ...
Lect 6 Estimation of authenticity of results of statistical research
... outcome data is a continuous variable such as weight. For example, one could estimate the effect of a diet on weight after adjusting for the effect of confounders such as smoking status. Logistic regression is used when the outcome data is binary such as cure or no cure. Logistic regression can be u ...
... outcome data is a continuous variable such as weight. For example, one could estimate the effect of a diet on weight after adjusting for the effect of confounders such as smoking status. Logistic regression is used when the outcome data is binary such as cure or no cure. Logistic regression can be u ...
Notes
... 3. We’ve been spending a lot of time talking about error analysis. It’s important to understand this stuff, because while Matlab gives you fast, robust linear solvers that you’re not likely to improve upon (for problems without special structure, at least), you can get into a lot of trouble using th ...
... 3. We’ve been spending a lot of time talking about error analysis. It’s important to understand this stuff, because while Matlab gives you fast, robust linear solvers that you’re not likely to improve upon (for problems without special structure, at least), you can get into a lot of trouble using th ...
voor dia serie SNS
... need only be calculated to within the given precision. The force due to a cluster of particles at some distance can be approximated with a single term. ...
... need only be calculated to within the given precision. The force due to a cluster of particles at some distance can be approximated with a single term. ...
Soc709 Lab 11
... sandwich estimator, which gives us unbiased estimates of the standard errors. If we have more information about the structure of the variance of the error term, such as its relationship to other variables in our analysis, then we can improve upon the HuberWhite approach. In lab we will learn how to ...
... sandwich estimator, which gives us unbiased estimates of the standard errors. If we have more information about the structure of the variance of the error term, such as its relationship to other variables in our analysis, then we can improve upon the HuberWhite approach. In lab we will learn how to ...
The BagTrack Project - An Overview 7/19/2012 Asif Iqbal Baba, Sari Haj Hussein, Tanvir Ahmed Supervisors: Torben Bach Pedersen and Hua Lu
... Research aims at reducing the errors that are inherent in RFIDbased indoor applications. Errors came from different sources including hardware limits and device deployment in a complicated indoor environments like airports. Data errors need to be minimized before any meaningful query/analysis can be ...
... Research aims at reducing the errors that are inherent in RFIDbased indoor applications. Errors came from different sources including hardware limits and device deployment in a complicated indoor environments like airports. Data errors need to be minimized before any meaningful query/analysis can be ...