mpi.h - ICTP
... – Function calls that can be made from any compiler, many languages – Just link to it – Wrappers: mpicc, mpif77 ...
... – Function calls that can be made from any compiler, many languages – Just link to it – Wrappers: mpicc, mpif77 ...
Parallel Programing with MPI
... a subroutine library with all MPI functions include files for the calling application program some startup script (usually called mpirun, but not standardized) ...
... a subroutine library with all MPI functions include files for the calling application program some startup script (usually called mpirun, but not standardized) ...
PDF - Complete Book (3.38 MB)
... meaning that once changed, every caller experiencing that element type is exposed to the same value. It is highly recommended to use only static final member variables, store any persistent data in the session (which the API provides access to), and keep all other variables local to the execution me ...
... meaning that once changed, every caller experiencing that element type is exposed to the same value. It is highly recommended to use only static final member variables, store any persistent data in the session (which the API provides access to), and keep all other variables local to the execution me ...
File - Computer Networks & Information Security
... layer also handles interactions between the profile and the JVM. The second layer is the profile layer, which consists of the minimum set of application programming interfaces (APIs) for the small computing device. The third layer is the Mobile Information Device Profile (MIDP). The MIDP layer conta ...
... layer also handles interactions between the profile and the JVM. The second layer is the profile layer, which consists of the minimum set of application programming interfaces (APIs) for the small computing device. The third layer is the Mobile Information Device Profile (MIDP). The MIDP layer conta ...
JBoss and Aspects for Middlware Components
... Users want “hooks” in different places of the application so that they can trigger things specific to their particular deployment If hooks are provided using OOP, it becomes tough to redesign or change API. By using pointcuts, the application designer provides logical names to pointcut express ...
... Users want “hooks” in different places of the application so that they can trigger things specific to their particular deployment If hooks are provided using OOP, it becomes tough to redesign or change API. By using pointcuts, the application designer provides logical names to pointcut express ...
Basic FPGA Configuration
... Does the application target a specific FPGA density or should it support migrating to other FPGA densities in the same package footprint? The package footprint and pinouts for some Xilinx families are designed to allow migration among different densities within a specific family This may require a l ...
... Does the application target a specific FPGA density or should it support migrating to other FPGA densities in the same package footprint? The package footprint and pinouts for some Xilinx families are designed to allow migration among different densities within a specific family This may require a l ...
PowerPoint
... Advantages of the DOM approach: 1. Good if any part of the document must be accessed more than once 2. If any rearrangement of the document must be done, it is facilitated by having a representation of the whole document in memory 3. Random access to any part of the document is ...
... Advantages of the DOM approach: 1. Good if any part of the document must be accessed more than once 2. If any rearrangement of the document must be done, it is facilitated by having a representation of the whole document in memory 3. Random access to any part of the document is ...
Comparison of Erlang Runtime System and Java Virtual Machine
... to the JVM as are Erlang processes. In order to really pull it off, Quasar needs to instrument your code to save the execution state and restore it when that lightweight thread starts running again[23]. Though instrumentation has many challenges that add complexity to the program instead of removing ...
... to the JVM as are Erlang processes. In order to really pull it off, Quasar needs to instrument your code to save the execution state and restore it when that lightweight thread starts running again[23]. Though instrumentation has many challenges that add complexity to the program instead of removing ...
Configuration Quick Start Guidelines Summary
... Xilinx CPLDs are generally non-volatile, utilizing EEPROM or FLASH Cell technology. Since they do not require an external memory device, the non-volatile nature of Xilinx CPLDs leads to different requirements in the programming process. ...
... Xilinx CPLDs are generally non-volatile, utilizing EEPROM or FLASH Cell technology. Since they do not require an external memory device, the non-volatile nature of Xilinx CPLDs leads to different requirements in the programming process. ...
Android
... - Usually run on top of other frameworks or external libraries - Are often open source - Can be domain specific (eg.: webshop) or generic (eg.:responsive website) - Have a learning curve… ...
... - Usually run on top of other frameworks or external libraries - Are often open source - Can be domain specific (eg.: webshop) or generic (eg.:responsive website) - Have a learning curve… ...
MIDP Application Security
... “MIDP Application Security 2: Understanding SSL and TLS”, http://wireless.java.sun.com/midp/articles/security2 “MIDP Application Security 3: Authentication in MIDP”, http://wireless.java.sun.com/midp/articles/security3 “Wireless Application Programming”, http://wireless.java.sun.com/midp/articles/ge ...
... “MIDP Application Security 2: Understanding SSL and TLS”, http://wireless.java.sun.com/midp/articles/security2 “MIDP Application Security 3: Authentication in MIDP”, http://wireless.java.sun.com/midp/articles/security3 “Wireless Application Programming”, http://wireless.java.sun.com/midp/articles/ge ...
client server computing
... client server computing represent the most important architectural change between traditional application programs and client server applications. • When using a remote procedure call approach, many functions or procedures communicate remotely with the server. • The interface between requesting and ...
... client server computing represent the most important architectural change between traditional application programs and client server applications. • When using a remote procedure call approach, many functions or procedures communicate remotely with the server. • The interface between requesting and ...
Exchange 2000 Server - Acronyms and Terminology
... A collection of Exchange 2000 servers than can be administered as a single unit. An administration group can include zero or more policies, routing groups, public folder trees, monitors, servers, conferencing services, and chat networks. When security settings (permissions) are applied to an adminis ...
... A collection of Exchange 2000 servers than can be administered as a single unit. An administration group can include zero or more policies, routing groups, public folder trees, monitors, servers, conferencing services, and chat networks. When security settings (permissions) are applied to an adminis ...
Applets in Java
... Applets are written in standard Java Applets are not “complete” applications – they plug into a browser Applets can be assumed to have graphics capability Applets run in a “sandbox” security environment, giving them extremely limited access to the resources of the local machine [usually a good t ...
... Applets are written in standard Java Applets are not “complete” applications – they plug into a browser Applets can be assumed to have graphics capability Applets run in a “sandbox” security environment, giving them extremely limited access to the resources of the local machine [usually a good t ...
OSC message
... using OSC protocol Manually send OSC messages to your Make Controller (ARM7) over Ethernet and USB Allow Flash (or other programs) communicate with ARM7 connected to the computer Open source. Written in C++, built with QT4 ...
... using OSC protocol Manually send OSC messages to your Make Controller (ARM7) over Ethernet and USB Allow Flash (or other programs) communicate with ARM7 connected to the computer Open source. Written in C++, built with QT4 ...
Combining Events And Threads For Scalable
... tens of thousands of simultaneous, mostly-idle client connections. Such massively-concurrent programs are difficult to implement, especially when other requirements, such as high performance and strong security, must also be met. Events vs. threads: Two implementation strategies for building such in ...
... tens of thousands of simultaneous, mostly-idle client connections. Such massively-concurrent programs are difficult to implement, especially when other requirements, such as high performance and strong security, must also be met. Events vs. threads: Two implementation strategies for building such in ...
Objectives
... because of the demand for more scalable and load-balanced systems to replace traditional two-tier client/server database systems. A centralized database system not only handles data access but also processes the business rules on data. Thus, a centralized database is usually heavily loaded because i ...
... because of the demand for more scalable and load-balanced systems to replace traditional two-tier client/server database systems. A centralized database system not only handles data access but also processes the business rules on data. Thus, a centralized database is usually heavily loaded because i ...
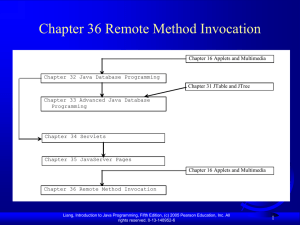
Chapter 18 Networking
... because of the demand for more scalable and load-balanced systems to replace traditional two-tier client/server database systems. A centralized database system not only handles data access but also processes the business rules on data. Thus, a centralized database is usually heavily loaded because i ...
... because of the demand for more scalable and load-balanced systems to replace traditional two-tier client/server database systems. A centralized database system not only handles data access but also processes the business rules on data. Thus, a centralized database is usually heavily loaded because i ...
Chapter 18 Networking
... because of the demand for more scalable and load-balanced systems to replace traditional two-tier client/server database systems. A centralized database system not only handles data access but also processes the business rules on data. Thus, a centralized database is usually heavily loaded because i ...
... because of the demand for more scalable and load-balanced systems to replace traditional two-tier client/server database systems. A centralized database system not only handles data access but also processes the business rules on data. Thus, a centralized database is usually heavily loaded because i ...
43slide - SIUE Computer Science
... because of the demand for more scalable and load-balanced systems to replace traditional two-tier client/server database systems. A centralized database system not only handles data access but also processes the business rules on data. Thus, a centralized database is usually heavily loaded because i ...
... because of the demand for more scalable and load-balanced systems to replace traditional two-tier client/server database systems. A centralized database system not only handles data access but also processes the business rules on data. Thus, a centralized database is usually heavily loaded because i ...
(.ppt)
... • Want to exploit Java’s “run everywhere” property, but - That requires 100% pure Java implementation, no single line of native code - Hard to use native communication (e.g. Myrinet) or native compiler/runtime system ...
... • Want to exploit Java’s “run everywhere” property, but - That requires 100% pure Java implementation, no single line of native code - Hard to use native communication (e.g. Myrinet) or native compiler/runtime system ...
Application Interface Specification
The Application Interface Specification (AIS) is a collection of open specifications that define the application programming interfaces (APIs) for high-availability application computer software. It is developed and published by the Service Availability Forum (SA Forum) and made freely available. Besides reducing the complexity of high-availability applications and shortening development time, the specifications intended to ease the portability of applications between different middleware implementations and to admit third party developers to a field that was highly proprietary in the past.