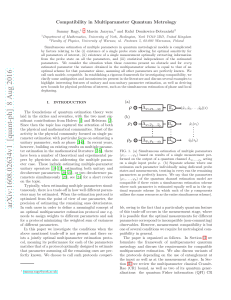
Design of Strongly Modulating Pulses to Implement Precise Effective
... to date have the disadvantage that low power implies long duration. This not only introduces errors due to relaxation, or decoherence, but also allows significant evolution under the action of the internal Hamiltonian. In the past, this evolution was rarely of concern because there was little import ...
... to date have the disadvantage that low power implies long duration. This not only introduces errors due to relaxation, or decoherence, but also allows significant evolution under the action of the internal Hamiltonian. In the past, this evolution was rarely of concern because there was little import ...
PDF only
... more and more introductory physics courses around the world. Because of the differences between the conceptual nature of quantum mechanics and classical physics, research on misconceptions, testing, and teaching strategies for introductory quantum mechanics is needed. For this review, 74 articles we ...
... more and more introductory physics courses around the world. Because of the differences between the conceptual nature of quantum mechanics and classical physics, research on misconceptions, testing, and teaching strategies for introductory quantum mechanics is needed. For this review, 74 articles we ...
Paper
... equivalently, by inducing tunneling through lattice modulation [37–39]. In the case of two different magnetic moments, one could also perform dynamic experiments, where laser parameters are modified in such a way that one switches either suddenly or adiabatically from the quantum Hall effect to the ...
... equivalently, by inducing tunneling through lattice modulation [37–39]. In the case of two different magnetic moments, one could also perform dynamic experiments, where laser parameters are modified in such a way that one switches either suddenly or adiabatically from the quantum Hall effect to the ...
I (x) - Boston University Physics Department.
... a) Scaling of AQ2 with L and : power-law exponents. Luttinger liquid physics in 1D, Kosterlitz-Thouless phase transition in 2D. b) Probability distribution W(AQ2): all order correlation functions. c) Fermions: cusp singularities in AQ2 ( ) corresponding to kf. ...
... a) Scaling of AQ2 with L and : power-law exponents. Luttinger liquid physics in 1D, Kosterlitz-Thouless phase transition in 2D. b) Probability distribution W(AQ2): all order correlation functions. c) Fermions: cusp singularities in AQ2 ( ) corresponding to kf. ...
- Nottingham ePrints
... We are operating in the classical regime, in that we observe quadrature variances that are several orders of magnitude larger than those in the quantum ground state. Therefore, we may estimate the particle’s momentum by simply taking the time differential of the position measurement. In passing we n ...
... We are operating in the classical regime, in that we observe quadrature variances that are several orders of magnitude larger than those in the quantum ground state. Therefore, we may estimate the particle’s momentum by simply taking the time differential of the position measurement. In passing we n ...
Quantum Computation, Quantum Theory and AI
... then we will obtain result 0 with probability 1/2, leaving the post-measurement state |β0 i = |00i, and 1 with probability 1/2, leaving the post-measurement state |β1 i = |11i. It is worth noting that after the measurement, the first and second qubits will always be in the same state. ...
... then we will obtain result 0 with probability 1/2, leaving the post-measurement state |β0 i = |00i, and 1 with probability 1/2, leaving the post-measurement state |β1 i = |11i. It is worth noting that after the measurement, the first and second qubits will always be in the same state. ...
Two interacting spin particles - Dipartimento di Matematica e Fisica
... that allow for a definition of quantum localization within the classical energy surface. These results, when extended to Hamiltonian systems, would impose severe quantum limitations on the behavior of classical ergodic systems. The important result is that room is left for quantum localization and t ...
... that allow for a definition of quantum localization within the classical energy surface. These results, when extended to Hamiltonian systems, would impose severe quantum limitations on the behavior of classical ergodic systems. The important result is that room is left for quantum localization and t ...
Quantum heating of a parametrically modulated oscillator: Spectral signatures M. Marthaler,
... This effect, quantum activation [10,11], has been now seen in the experiment [2]. Quantum heating also affects the dynamics of a resonantly driven oscillator coupled to a two-level system [12], and interesting spectral manifestations of the heating in such coupled system have been recently seen [13] ...
... This effect, quantum activation [10,11], has been now seen in the experiment [2]. Quantum heating also affects the dynamics of a resonantly driven oscillator coupled to a two-level system [12], and interesting spectral manifestations of the heating in such coupled system have been recently seen [13] ...
ןב תטיסרבינוא - בגנב ןוירוג
... 1.5 Qubit-specific measurement capability. Theoretically, we should be able to measure the state of each qubit independently of any other parameters of the system, including the state of the nearby qubits, without disturbing any other qubit, and to do so in a time interval “much shorter” then the de ...
... 1.5 Qubit-specific measurement capability. Theoretically, we should be able to measure the state of each qubit independently of any other parameters of the system, including the state of the nearby qubits, without disturbing any other qubit, and to do so in a time interval “much shorter” then the de ...
$doc.title
... effect, this leads to quantization of the transmitted charge, and is of metrological use [10]. Devices of this type are called ‘single-electron turnstiles’. Charge pumping is achieved by varying certain parameters of the system Hamiltonian periodically with time. When the change is carried out slowl ...
... effect, this leads to quantization of the transmitted charge, and is of metrological use [10]. Devices of this type are called ‘single-electron turnstiles’. Charge pumping is achieved by varying certain parameters of the system Hamiltonian periodically with time. When the change is carried out slowl ...
Superconducting Qubits and Circuits: Artificial Atoms Coupled to
... atoms) with electromagnetic fields. These lecture notes discuss the closely related problem of quantization of electrical circuits [1, 2]. Experimental progress over the last decade in creating and controlling quantum coherence in superconducting electrical circuits has been truly remarkable. The qua ...
... atoms) with electromagnetic fields. These lecture notes discuss the closely related problem of quantization of electrical circuits [1, 2]. Experimental progress over the last decade in creating and controlling quantum coherence in superconducting electrical circuits has been truly remarkable. The qua ...
Interacting Quantum Observables: Categorical Algebra and
... 1. Introduction Quantum theory is arguably the single most successful scientific theory. While it is now almost a century old, many new results have been discovered by approaching quantum theory from an computational and/or information theoretic perspective, signalling the potential for a quantum in ...
... 1. Introduction Quantum theory is arguably the single most successful scientific theory. While it is now almost a century old, many new results have been discovered by approaching quantum theory from an computational and/or information theoretic perspective, signalling the potential for a quantum in ...
DENSITY CONCEPT IN MOLECULES AND MATERIALS
... systems is the so called density functional theory (DFT) which essentially projects the many-particle picture to a single particle one. Selected illustrative applications through examples of the electron density based microscopic modeling of chemical binding as well as intermolecular interaction and ...
... systems is the so called density functional theory (DFT) which essentially projects the many-particle picture to a single particle one. Selected illustrative applications through examples of the electron density based microscopic modeling of chemical binding as well as intermolecular interaction and ...
Ab initio Quantum and ab initio Molecular Dynamics of the
... our study, belongs to this class. An initially decreasing sticking probability had usually been explained by a precursor mechanism.5 In this concept the molecules are temporarily trapped in a molecular physisorption state, the so-called precursor state, before they dissociatively adsorb. The energy ...
... our study, belongs to this class. An initially decreasing sticking probability had usually been explained by a precursor mechanism.5 In this concept the molecules are temporarily trapped in a molecular physisorption state, the so-called precursor state, before they dissociatively adsorb. The energy ...
Quantum key distribution
Quantum key distribution (QKD) uses quantum mechanics to guarantee secure communication. It enables two parties to produce a shared random secret key known only to them, which can then be used to encrypt and decrypt messages. It is often incorrectly called quantum cryptography, as it is the most well known example of the group of quantum cryptographic tasks.An important and unique property of quantum key distribution is the ability of the two communicating users to detect the presence of any third party trying to gain knowledge of the key. This results from a fundamental aspect of quantum mechanics: the process of measuring a quantum system in general disturbs the system. A third party trying to eavesdrop on the key must in some way measure it, thus introducing detectable anomalies. By using quantum superpositions or quantum entanglement and transmitting information in quantum states, a communication system can be implemented which detects eavesdropping. If the level of eavesdropping is below a certain threshold, a key can be produced that is guaranteed to be secure (i.e. the eavesdropper has no information about it), otherwise no secure key is possible and communication is aborted.The security of encryption that uses quantum key distribution relies on the foundations of quantum mechanics, in contrast to traditional public key cryptography which relies on the computational difficulty of certain mathematical functions, and cannot provide any indication of eavesdropping at any point in the communication process, or any mathematical proof as to the actual complexity of reversing the one-way functions used. QKD has provable security based on information theory, and forward secrecy.Quantum key distribution is only used to produce and distribute a key, not to transmit any message data. This key can then be used with any chosen encryption algorithm to encrypt (and decrypt) a message, which can then be transmitted over a standard communication channel. The algorithm most commonly associated with QKD is the one-time pad, as it is provably secure when used with a secret, random key. In real world situations, it is often also used with encryption using symmetric key algorithms like the Advanced Encryption Standard algorithm. In the case of QKD this comparison is based on the assumption of perfect single-photon sources and detectors, that cannot be easily implemented.