in PPT
... fundamental issues, these are the correlations achievable by classical resources. Bell inequalities define the limits on these correlations. For a finite number of measurements and results, these correlations define a polytope, a convex set with a finite number of extreme points. ...
... fundamental issues, these are the correlations achievable by classical resources. Bell inequalities define the limits on these correlations. For a finite number of measurements and results, these correlations define a polytope, a convex set with a finite number of extreme points. ...
Advanced Quantum Physics - Theory of Condensed Matter
... subjective exercise. Apart from the handout, I am not aware of a text that addresses all of the material covered in this course: Most are of course more dense and far-reaching, and others are simply more advanced or imbalanced towards specialist topics. At the same time, I would not recommend relyin ...
... subjective exercise. Apart from the handout, I am not aware of a text that addresses all of the material covered in this course: Most are of course more dense and far-reaching, and others are simply more advanced or imbalanced towards specialist topics. At the same time, I would not recommend relyin ...
The two-state vector description of a quantum system
... Strong measurement: The Aharonov-Bergmann-Lebowitz (ABL) formula: ...
... Strong measurement: The Aharonov-Bergmann-Lebowitz (ABL) formula: ...
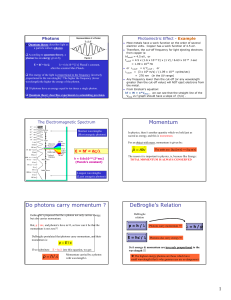
Momentum Do photons carry momentum ? DeBroglie`s Relation
... In physics, there’s another quantity which we hold just as sacred as energy, and this is momentum. For an object with mass, momentum is given by: ...
... In physics, there’s another quantity which we hold just as sacred as energy, and this is momentum. For an object with mass, momentum is given by: ...
$doc.title
... NB. Φ is not an observable, is single valued and can be normalised by ∫ φ *φ dq = 1 ...
... NB. Φ is not an observable, is single valued and can be normalised by ∫ φ *φ dq = 1 ...
Otto Stern and the discovery of space quantization
... The results of that experiment were astounding, although they were hinted at by quantum theory. The separation of the beam of silver atoms into two components occurred as if these moments pointed either one way or the opposite way. There was no mechanism that would orient them in one way or another ...
... The results of that experiment were astounding, although they were hinted at by quantum theory. The separation of the beam of silver atoms into two components occurred as if these moments pointed either one way or the opposite way. There was no mechanism that would orient them in one way or another ...
- Free Documents
... electrons excitons like a rock splashing water from a puddle. the environment frees up the exciton and allows it to get to where its going. which can then use it at maximum efficiency to convert carbon dioxide into sugars. All rights reserved . But is their path made up of random. though Robert Blan ...
... electrons excitons like a rock splashing water from a puddle. the environment frees up the exciton and allows it to get to where its going. which can then use it at maximum efficiency to convert carbon dioxide into sugars. All rights reserved . But is their path made up of random. though Robert Blan ...
Observable1 The term observable has become the - Philsci
... possibilities of assigning definite values to observables and to the possibilities of measurements in the quantum world. Indeed, observables A, B that do not commute do not share a complete system of eigenvectors, so that typically an eigenstate of (say) A will be a superposition of eigenstates of B ...
... possibilities of assigning definite values to observables and to the possibilities of measurements in the quantum world. Indeed, observables A, B that do not commute do not share a complete system of eigenvectors, so that typically an eigenstate of (say) A will be a superposition of eigenstates of B ...
“Can Quantum-Mechanical Description of Physical Reality Be
... we cannot verify its’ existence • Theories should be economical: Ptolemy vs Copernicus ...
... we cannot verify its’ existence • Theories should be economical: Ptolemy vs Copernicus ...
Chapter 7
... determined by the square of the wave function can give us a probability distribution. It is important in this regard that students distinguish the concept of orbital from an “orbit.” ...
... determined by the square of the wave function can give us a probability distribution. It is important in this regard that students distinguish the concept of orbital from an “orbit.” ...
Quantum Control
... The quantum-classical transition The process of measurement • Why is this “transition” between two very different theories so robust? – “we take this really small fuzzy globs that are evolving in an orderly fashion, and when we put enough of them together, for some reason everything crystallizes an ...
... The quantum-classical transition The process of measurement • Why is this “transition” between two very different theories so robust? – “we take this really small fuzzy globs that are evolving in an orderly fashion, and when we put enough of them together, for some reason everything crystallizes an ...
Quantum key distribution
Quantum key distribution (QKD) uses quantum mechanics to guarantee secure communication. It enables two parties to produce a shared random secret key known only to them, which can then be used to encrypt and decrypt messages. It is often incorrectly called quantum cryptography, as it is the most well known example of the group of quantum cryptographic tasks.An important and unique property of quantum key distribution is the ability of the two communicating users to detect the presence of any third party trying to gain knowledge of the key. This results from a fundamental aspect of quantum mechanics: the process of measuring a quantum system in general disturbs the system. A third party trying to eavesdrop on the key must in some way measure it, thus introducing detectable anomalies. By using quantum superpositions or quantum entanglement and transmitting information in quantum states, a communication system can be implemented which detects eavesdropping. If the level of eavesdropping is below a certain threshold, a key can be produced that is guaranteed to be secure (i.e. the eavesdropper has no information about it), otherwise no secure key is possible and communication is aborted.The security of encryption that uses quantum key distribution relies on the foundations of quantum mechanics, in contrast to traditional public key cryptography which relies on the computational difficulty of certain mathematical functions, and cannot provide any indication of eavesdropping at any point in the communication process, or any mathematical proof as to the actual complexity of reversing the one-way functions used. QKD has provable security based on information theory, and forward secrecy.Quantum key distribution is only used to produce and distribute a key, not to transmit any message data. This key can then be used with any chosen encryption algorithm to encrypt (and decrypt) a message, which can then be transmitted over a standard communication channel. The algorithm most commonly associated with QKD is the one-time pad, as it is provably secure when used with a secret, random key. In real world situations, it is often also used with encryption using symmetric key algorithms like the Advanced Encryption Standard algorithm. In the case of QKD this comparison is based on the assumption of perfect single-photon sources and detectors, that cannot be easily implemented.