Quantum correlations - Uniwersytet otwarty UG
... • instead a quantum state may be given for a system as a whole! • The entanglement was the subject of EinsteinPodolski-Rosen paper. • Correlations should be taken into account. ...
... • instead a quantum state may be given for a system as a whole! • The entanglement was the subject of EinsteinPodolski-Rosen paper. • Correlations should be taken into account. ...
Problem Set 1 - MIT OpenCourseWare
... the particle cannot have E = 0 while respecting the uncertainty principle. ASIDE: Quantum mechanically, then, there must be some minimum energy this system can have which cannot be predicted classically! For a particle on a table, this may not seem so important – but for Hydrogen, which you’ve just ...
... the particle cannot have E = 0 while respecting the uncertainty principle. ASIDE: Quantum mechanically, then, there must be some minimum energy this system can have which cannot be predicted classically! For a particle on a table, this may not seem so important – but for Hydrogen, which you’ve just ...
The Quantum Model of the Atom
... • Idea involved the detection of electrons, which are detected by their interactions with photons • Because photons have about the same energy as electrons, any attempt to locate a specific electron with a photon knocks the electron off its course • Results in uncertainty in trying to locate an el ...
... • Idea involved the detection of electrons, which are detected by their interactions with photons • Because photons have about the same energy as electrons, any attempt to locate a specific electron with a photon knocks the electron off its course • Results in uncertainty in trying to locate an el ...
A tutorial on non-Markovian quantum processes
... 2. Group (co-authors) 3. Dynamical maps (Complete Positivity) 4. Stinespring 5. Initial correlations/non-Markovianity 6. Pechucas theorem 7. Resolution (give up states) 8. Superchannel 9. Experiment 10. What is a process? 11. What is characterisation? ...
... 2. Group (co-authors) 3. Dynamical maps (Complete Positivity) 4. Stinespring 5. Initial correlations/non-Markovianity 6. Pechucas theorem 7. Resolution (give up states) 8. Superchannel 9. Experiment 10. What is a process? 11. What is characterisation? ...
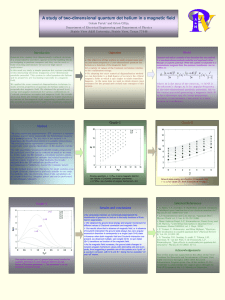
Exact diagonalization analysis of quantum dot helium for
... technique used to solve numerically the Schrödinger equation for a quantum system. The key idea of the method is to diagonalize the Hamiltonian matrix in a suitable chosen basis. The resulting matrix eigenvalues correspond to the numerically exact energy eigenvalues of the quantum system. The only u ...
... technique used to solve numerically the Schrödinger equation for a quantum system. The key idea of the method is to diagonalize the Hamiltonian matrix in a suitable chosen basis. The resulting matrix eigenvalues correspond to the numerically exact energy eigenvalues of the quantum system. The only u ...
Final Paper - The Oxbow School
... particles moves in any way the other is affected in the exact same way at the exact same time regardless of how far apart they are from each other. Also there have been cases where the particles revolve around one another around 10,000 times faster than light. Einstein disliked this and he called i ...
... particles moves in any way the other is affected in the exact same way at the exact same time regardless of how far apart they are from each other. Also there have been cases where the particles revolve around one another around 10,000 times faster than light. Einstein disliked this and he called i ...
Announcements
... smaller the wavelength of the EM radiation, the more likely the behavior is to be particle-like l The larger the wavelength, the more likely it is to be ...
... smaller the wavelength of the EM radiation, the more likely the behavior is to be particle-like l The larger the wavelength, the more likely it is to be ...
Another version - Scott Aaronson
... requirements and the evidence for classicalExperimental hardness, exact of algorithm demonstrations with 3-4 compared to simulation Shor’s factoring BosonSampling is possible, photons achieved (by Ourhierarchy proposal: then the polynomial groups in Oxford, Identical single Brisbane, Rome, Vienna) c ...
... requirements and the evidence for classicalExperimental hardness, exact of algorithm demonstrations with 3-4 compared to simulation Shor’s factoring BosonSampling is possible, photons achieved (by Ourhierarchy proposal: then the polynomial groups in Oxford, Identical single Brisbane, Rome, Vienna) c ...
Lecture Notes, Feb 29
... The idea of the position of an object seems so obvious that the concept of position is generally taken for granted in classical physics. Knowing the position of a particle means knowing the values of its coordinates in some coordinate system. The precision of those values, in classical physics, is l ...
... The idea of the position of an object seems so obvious that the concept of position is generally taken for granted in classical physics. Knowing the position of a particle means knowing the values of its coordinates in some coordinate system. The precision of those values, in classical physics, is l ...
Document
... Continuous quantum correlations in photon pairs can be used for key distribution Photons generated by PDC are correlated in lateral position and transverse wavevector If ...
... Continuous quantum correlations in photon pairs can be used for key distribution Photons generated by PDC are correlated in lateral position and transverse wavevector If ...
Lecture notes, part 2
... Since |ψ|2 is a probability density in space, how do we get information about quantities that depend on the particle momentum? We can get an expression for its expectation value by appealing to the Correspondence Principle, which says “Quantum mechanics must reduce to classical mechanics in some wa ...
... Since |ψ|2 is a probability density in space, how do we get information about quantities that depend on the particle momentum? We can get an expression for its expectation value by appealing to the Correspondence Principle, which says “Quantum mechanics must reduce to classical mechanics in some wa ...
a 1 - University of San Francisco
... There are a number of proposed schemes to overcome the decoherence problem. Research is ongoing. There are a very large number of quantum computing candidates. This large number is an indication that the topic is still in its infancy. At the same time, the large number is an indication of a vast amo ...
... There are a number of proposed schemes to overcome the decoherence problem. Research is ongoing. There are a very large number of quantum computing candidates. This large number is an indication that the topic is still in its infancy. At the same time, the large number is an indication of a vast amo ...
Madelung paper - Neo
... The form that the function U is to be given, insofar as it represents the interaction of the electrons with each other, as well as the “quantum term” of equation (3'), can first be determined from a successful calculation, at least in some particular cases. There is thus a chance of erecting the qua ...
... The form that the function U is to be given, insofar as it represents the interaction of the electrons with each other, as well as the “quantum term” of equation (3'), can first be determined from a successful calculation, at least in some particular cases. There is thus a chance of erecting the qua ...
From Billiard Balls to Quantum Computing: Geoff Sharman
... more complex circuits using an array of qubits The array must be initialised (pgm & data), and then allowed to “evolve” (zero energy computation) according the laws of QM There's no way of knowing how long this may last, or whether it will complete, but we can arrange for the QC to tell us via outpu ...
... more complex circuits using an array of qubits The array must be initialised (pgm & data), and then allowed to “evolve” (zero energy computation) according the laws of QM There's no way of knowing how long this may last, or whether it will complete, but we can arrange for the QC to tell us via outpu ...
Quantum key distribution
Quantum key distribution (QKD) uses quantum mechanics to guarantee secure communication. It enables two parties to produce a shared random secret key known only to them, which can then be used to encrypt and decrypt messages. It is often incorrectly called quantum cryptography, as it is the most well known example of the group of quantum cryptographic tasks.An important and unique property of quantum key distribution is the ability of the two communicating users to detect the presence of any third party trying to gain knowledge of the key. This results from a fundamental aspect of quantum mechanics: the process of measuring a quantum system in general disturbs the system. A third party trying to eavesdrop on the key must in some way measure it, thus introducing detectable anomalies. By using quantum superpositions or quantum entanglement and transmitting information in quantum states, a communication system can be implemented which detects eavesdropping. If the level of eavesdropping is below a certain threshold, a key can be produced that is guaranteed to be secure (i.e. the eavesdropper has no information about it), otherwise no secure key is possible and communication is aborted.The security of encryption that uses quantum key distribution relies on the foundations of quantum mechanics, in contrast to traditional public key cryptography which relies on the computational difficulty of certain mathematical functions, and cannot provide any indication of eavesdropping at any point in the communication process, or any mathematical proof as to the actual complexity of reversing the one-way functions used. QKD has provable security based on information theory, and forward secrecy.Quantum key distribution is only used to produce and distribute a key, not to transmit any message data. This key can then be used with any chosen encryption algorithm to encrypt (and decrypt) a message, which can then be transmitted over a standard communication channel. The algorithm most commonly associated with QKD is the one-time pad, as it is provably secure when used with a secret, random key. In real world situations, it is often also used with encryption using symmetric key algorithms like the Advanced Encryption Standard algorithm. In the case of QKD this comparison is based on the assumption of perfect single-photon sources and detectors, that cannot be easily implemented.