Poster PDF (1.5mb)
... processes: cavity blocking (κ>) and decoherence of the polarition by the cavity field (κ<). This second time constant can be changed experimentally by the control beam power. ...
... processes: cavity blocking (κ>) and decoherence of the polarition by the cavity field (κ<). This second time constant can be changed experimentally by the control beam power. ...
PPT - LSU Physics & Astronomy
... states, NOON, M&M, and Generalized Coherent. The conclusion from this plot is that The optimal states found by the computer code are N00N states for very low loss, M&M states for intermediate loss, and generalized coherent states for high loss. This graph supports the assertion that a Type-II sensor ...
... states, NOON, M&M, and Generalized Coherent. The conclusion from this plot is that The optimal states found by the computer code are N00N states for very low loss, M&M states for intermediate loss, and generalized coherent states for high loss. This graph supports the assertion that a Type-II sensor ...
Lecture 12
... Therefor, there are two possible states for every n, l, m (i.e. for every circle in the diagram above). ...
... Therefor, there are two possible states for every n, l, m (i.e. for every circle in the diagram above). ...
Presentazione di PowerPoint
... Cazzaniga took her pupils to a laboratory run by Milan University's physics department. There they took part in their first particle physics experiment to study the tracks left by alpha particles in a cloud chamber. A total of three scientists, six secondary school teachers and seven classes were in ...
... Cazzaniga took her pupils to a laboratory run by Milan University's physics department. There they took part in their first particle physics experiment to study the tracks left by alpha particles in a cloud chamber. A total of three scientists, six secondary school teachers and seven classes were in ...
Table of Contents
... introductory students, and a lack of ontological flexibility in their conceptions of light and matter. We have developed a framework for understanding and characterizing student perspectives ...
... introductory students, and a lack of ontological flexibility in their conceptions of light and matter. We have developed a framework for understanding and characterizing student perspectives ...
Quantum Interference Experiments
... for the fact that real experiments take place in interaction with the environment t in the form of air molecules or light radiation. It turns out that when you account for interaction with the environment the “mixtures” of various components of the quantum wave vanish very quickly. It turns out that ...
... for the fact that real experiments take place in interaction with the environment t in the form of air molecules or light radiation. It turns out that when you account for interaction with the environment the “mixtures” of various components of the quantum wave vanish very quickly. It turns out that ...
PHOTON AS A QUANTUM PARTICLE ∗
... 1.4. Photon is named Twenty years have passed after the publication of the Einstein paper and the term “photon” still had not been invented. It made its appearance in a letter to Nature [8] written by Gilbert N. Lewis, professor of theoretical chemistry in Berkeley. In this letter he wrote: “Had the ...
... 1.4. Photon is named Twenty years have passed after the publication of the Einstein paper and the term “photon” still had not been invented. It made its appearance in a letter to Nature [8] written by Gilbert N. Lewis, professor of theoretical chemistry in Berkeley. In this letter he wrote: “Had the ...
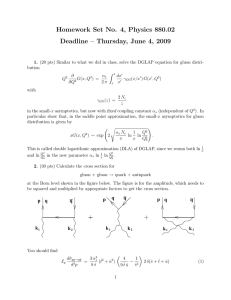
Homework Set No. 4, Physics 880.02
... with the Mandelstam variables ŝ = (k1 + k2 )2 , t̂ = (k1 − p)2 , û = (k2 − p)2 . The factor of 2 in front of the δ-function in Eq. (1) comes from the fact that either the quark or the antiquark can carry momentum p. (q and q̄ in the figure denote the quark and the antiquark. Time flows upward.) A ...
... with the Mandelstam variables ŝ = (k1 + k2 )2 , t̂ = (k1 − p)2 , û = (k2 − p)2 . The factor of 2 in front of the δ-function in Eq. (1) comes from the fact that either the quark or the antiquark can carry momentum p. (q and q̄ in the figure denote the quark and the antiquark. Time flows upward.) A ...
Spin supercurrents and torquing with majorana fermions
... Strong coupling can be realized when: Should be accessible with carbon nanotubes: J. C. Meyer, M. Paillet, and S. Roth, Science 309, 1539 (2005) ...
... Strong coupling can be realized when: Should be accessible with carbon nanotubes: J. C. Meyer, M. Paillet, and S. Roth, Science 309, 1539 (2005) ...
Quantum Information and Randomness - Max-Planck
... experiments disproved local realism and showed perfect agreement with the predictions from quantum theory. Up to the present, numerous experiments have been and are still being performed, achieving better and better accuracy and closing more and more of the loopholes of earlier experiments. In view ...
... experiments disproved local realism and showed perfect agreement with the predictions from quantum theory. Up to the present, numerous experiments have been and are still being performed, achieving better and better accuracy and closing more and more of the loopholes of earlier experiments. In view ...
QNSR
... encyclopedic. We are embarking here to provide a type of centenary revisiting of quantum and relativistic foundations and to create some perspective with which to understand and correlate different models and theories that have been introduced, many of which we find to have, after all, some powerful ...
... encyclopedic. We are embarking here to provide a type of centenary revisiting of quantum and relativistic foundations and to create some perspective with which to understand and correlate different models and theories that have been introduced, many of which we find to have, after all, some powerful ...
Quantum key distribution
Quantum key distribution (QKD) uses quantum mechanics to guarantee secure communication. It enables two parties to produce a shared random secret key known only to them, which can then be used to encrypt and decrypt messages. It is often incorrectly called quantum cryptography, as it is the most well known example of the group of quantum cryptographic tasks.An important and unique property of quantum key distribution is the ability of the two communicating users to detect the presence of any third party trying to gain knowledge of the key. This results from a fundamental aspect of quantum mechanics: the process of measuring a quantum system in general disturbs the system. A third party trying to eavesdrop on the key must in some way measure it, thus introducing detectable anomalies. By using quantum superpositions or quantum entanglement and transmitting information in quantum states, a communication system can be implemented which detects eavesdropping. If the level of eavesdropping is below a certain threshold, a key can be produced that is guaranteed to be secure (i.e. the eavesdropper has no information about it), otherwise no secure key is possible and communication is aborted.The security of encryption that uses quantum key distribution relies on the foundations of quantum mechanics, in contrast to traditional public key cryptography which relies on the computational difficulty of certain mathematical functions, and cannot provide any indication of eavesdropping at any point in the communication process, or any mathematical proof as to the actual complexity of reversing the one-way functions used. QKD has provable security based on information theory, and forward secrecy.Quantum key distribution is only used to produce and distribute a key, not to transmit any message data. This key can then be used with any chosen encryption algorithm to encrypt (and decrypt) a message, which can then be transmitted over a standard communication channel. The algorithm most commonly associated with QKD is the one-time pad, as it is provably secure when used with a secret, random key. In real world situations, it is often also used with encryption using symmetric key algorithms like the Advanced Encryption Standard algorithm. In the case of QKD this comparison is based on the assumption of perfect single-photon sources and detectors, that cannot be easily implemented.