Installing Operating Systems
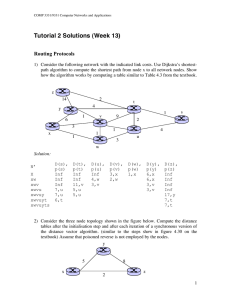
... The unattended operating system installation function helps you install the Microsoft Windows and RedHat Linux operating systems. UCS-SCU has integrated device drivers including RAID drivers to seamlessly install operating systems on supported RAID logical arrays without additional load driver steps ...
... The unattended operating system installation function helps you install the Microsoft Windows and RedHat Linux operating systems. UCS-SCU has integrated device drivers including RAID drivers to seamlessly install operating systems on supported RAID logical arrays without additional load driver steps ...
- Networked Robotics Corporation
... The incubator must have the capability of RS485 data communications. Many units come shipped with this option from the factory however if you don’t have this option the capability may be added by purchasing the RS485 option for these units (Part number 190523) from Thermo or you can purchase this pa ...
... The incubator must have the capability of RS485 data communications. Many units come shipped with this option from the factory however if you don’t have this option the capability may be added by purchasing the RS485 option for these units (Part number 190523) from Thermo or you can purchase this pa ...
Final Review Report - Cardiff Physics and Astronomy
... with/without nanocrystal quantum dots as active optical medium. His research was part of a larger study on quantum optical properties of solid-state microcavities in the so-called “badcavity limit” in our group to which Dr. Vasily Temnov, Dr. Yuri Fedutik and Dipl. Phys. Oliver Schöps contributed. A ...
... with/without nanocrystal quantum dots as active optical medium. His research was part of a larger study on quantum optical properties of solid-state microcavities in the so-called “badcavity limit” in our group to which Dr. Vasily Temnov, Dr. Yuri Fedutik and Dipl. Phys. Oliver Schöps contributed. A ...
Social Network Effects on Performance and Layoffs
... network are still greater than what is provided in a redundant network. In this paper, I focus on the information benefits and examine how they affect performance independent of whether individuals control the information flow to their advantage. Thus, I hypothesize that a structurally diverse netwo ...
... network are still greater than what is provided in a redundant network. In this paper, I focus on the information benefits and examine how they affect performance independent of whether individuals control the information flow to their advantage. Thus, I hypothesize that a structurally diverse netwo ...
Tuesday, April 10, 2007 (QoS)
... • Isolates well-behaved from misbehaving sources Sharing • Mixing of different sources in a way beneficial to all FIFO: sharing • each traffic source impacts other connections directly • e.g. malicious user can grab extra bandwidth • the simplest and most common queueing discipline • averages out th ...
... • Isolates well-behaved from misbehaving sources Sharing • Mixing of different sources in a way beneficial to all FIFO: sharing • each traffic source impacts other connections directly • e.g. malicious user can grab extra bandwidth • the simplest and most common queueing discipline • averages out th ...
802.11g Wireless PCI Adapter Model # AWLH3026T
... supports data transfer speeds of up to 54 Mbps. The adapter can be integrated into a network in either Ad-Hoc mode (without an Access Point) or Infrastructure mode (with an Access Point). This Adapter supports 64/128-bit WEP data encryption that protects your wireless network from eavesdropping. It ...
... supports data transfer speeds of up to 54 Mbps. The adapter can be integrated into a network in either Ad-Hoc mode (without an Access Point) or Infrastructure mode (with an Access Point). This Adapter supports 64/128-bit WEP data encryption that protects your wireless network from eavesdropping. It ...
Tutorial 2 Solutions (Week 13)
... H3 via a 300m cable and so on upto computer H10, which is connected via a 1000m cable (ignore the requirement of repeater due to signal degradation). Assume that the hub introduces a delay of 2.5 microseconds. Calculate the shortest packet length Lmin of this network in order to ensure that the CSMA ...
... H3 via a 300m cable and so on upto computer H10, which is connected via a 1000m cable (ignore the requirement of repeater due to signal degradation). Assume that the hub introduces a delay of 2.5 microseconds. Calculate the shortest packet length Lmin of this network in order to ensure that the CSMA ...
Sustainable Logistics Networks in Sparsely Populated Areas
... municipalities. This resettlement of young people from peripheral areas to the built-up ones resulted in a dichotomy between the sparsely and densely populated areas which further accentuated by the distortion of population structure and gender ratio. According to Neto et al. [11], the increasing fo ...
... municipalities. This resettlement of young people from peripheral areas to the built-up ones resulted in a dichotomy between the sparsely and densely populated areas which further accentuated by the distortion of population structure and gender ratio. According to Neto et al. [11], the increasing fo ...
11g WLAN USB Adapter 3054UB5
... way to let you put a desktop or a notebook computer almost anywhere without the hassle of running network cables. Now there will be no more drilling holes and eyesore exposed cables. Once you are connected, you can do anything, just like the wired network. This USB client adapter operates seamlessly ...
... way to let you put a desktop or a notebook computer almost anywhere without the hassle of running network cables. Now there will be no more drilling holes and eyesore exposed cables. Once you are connected, you can do anything, just like the wired network. This USB client adapter operates seamlessly ...
802.11g Wireless USB Adapter
... device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses and can radiate radio frequency energy and, if not installed and used in accordance with the instruction ...
... device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses and can radiate radio frequency energy and, if not installed and used in accordance with the instruction ...
TL-WPA4230P KIT_V1_QIG_EU - TP-Link
... Q4. What can I do if my computer can’t access the Internet after it is connected to a powerline adapter/extender? Check the following: 1. Connect your computer to the modem or router to test the Internet connection. 2. Make sure the hardware connection is correct. 3. Make sure the Powerline LEDs lig ...
... Q4. What can I do if my computer can’t access the Internet after it is connected to a powerline adapter/extender? Check the following: 1. Connect your computer to the modem or router to test the Internet connection. 2. Make sure the hardware connection is correct. 3. Make sure the Powerline LEDs lig ...
Network Connections and Wireless Security
... Understanding the Smart Wizard These instructions explain how to use the NETGEAR WG111v2 Smart Wizard to change the WG111v2 wireless settings. When you have installed the software from the NETGEAR CD, the icon appears on your desktop and in the Windows System Tray. The Windows System Tray is located ...
... Understanding the Smart Wizard These instructions explain how to use the NETGEAR WG111v2 Smart Wizard to change the WG111v2 wireless settings. When you have installed the software from the NETGEAR CD, the icon appears on your desktop and in the Windows System Tray. The Windows System Tray is located ...
DEVICES ARE PLUG AND PLAY READY.
... network with the default Private Network Name is as easy as plugging the device into the power outlet. If you wish to have a unique Private Network Name, simply follow the instructions below. This Easy Start Guide, the User Manual, and the HomePlug AV Utility software is included in the Resource CD. ...
... network with the default Private Network Name is as easy as plugging the device into the power outlet. If you wish to have a unique Private Network Name, simply follow the instructions below. This Easy Start Guide, the User Manual, and the HomePlug AV Utility software is included in the Resource CD. ...
SpeedTouch™121g
... A caution warns you about potential problems or specific precautions that need to be taken. ...
... A caution warns you about potential problems or specific precautions that need to be taken. ...
PM-130 Modbus Data Logger UM 20130107
... is “empty”(don’t type anything). However, it is not recommended to leave it empty in field operation. If you could not login, it means you have to key in the password. If you do not know the password you can turn off the power and then use any point tip to push “Reset” button and hold it to turn on ...
... is “empty”(don’t type anything). However, it is not recommended to leave it empty in field operation. If you could not login, it means you have to key in the password. If you do not know the password you can turn off the power and then use any point tip to push “Reset” button and hold it to turn on ...
Difficulty printing from your PC can occur for various reasons
... HL2170W Windows Network Connection Repair Instructions ...
... HL2170W Windows Network Connection Repair Instructions ...
Chapter 8 8 Slutsky Equation
... The pure substitution effect is as for a normal good. But, the income effect is in the opposite direction. Good 1 is ( 1’’’,x (x ’’’ 2’’’) income-inferior f because an x 2’ i increase to income i x2’’ causes demand to f ll fall. x2 ...
... The pure substitution effect is as for a normal good. But, the income effect is in the opposite direction. Good 1 is ( 1’’’,x (x ’’’ 2’’’) income-inferior f because an x 2’ i increase to income i x2’’ causes demand to f ll fall. x2 ...
x 2
... rare cases of extreme incomeinferiority, the income effect may be larger in size than the substitution effect, causing quantity demanded to fall as own-price rises. Such goods are Giffen goods. ...
... rare cases of extreme incomeinferiority, the income effect may be larger in size than the substitution effect, causing quantity demanded to fall as own-price rises. Such goods are Giffen goods. ...
Quick User Guide - Axis AV Solutions
... Network Connection / AP Client mode. If WiD510-ENT needs to be on existing network infrastructure via Ethernet connection for accessing internet or network resources, connect a network cable from switch or router to the RJ-45 connector. If WiD510-ENT needs to be on existing Wireless Access point (no ...
... Network Connection / AP Client mode. If WiD510-ENT needs to be on existing network infrastructure via Ethernet connection for accessing internet or network resources, connect a network cable from switch or router to the RJ-45 connector. If WiD510-ENT needs to be on existing Wireless Access point (no ...
CONTRA MANUALES
... to check your configuration. 2. Check your router or access point configuration. ...
... to check your configuration. 2. Check your router or access point configuration. ...
Uninstalling and Reinstalling on a Server Computer
... This guide describes the process for uninstalling and then reinstalling Medical Director, PracSoft, and/or SQL Instances on a computer that has been designated the Medical Director and/or PraSoft Server. Note that these instructions are not relevant to computers where Medical Director and/or PracSof ...
... This guide describes the process for uninstalling and then reinstalling Medical Director, PracSoft, and/or SQL Instances on a computer that has been designated the Medical Director and/or PraSoft Server. Note that these instructions are not relevant to computers where Medical Director and/or PracSof ...
Replacing Complex Internet VPN Networks
... static public IP addresses. Moving from a DHCP based service to a static IP service immediately changes the price of the broadband service, as it moves the customer from a residential pricing plan to a business pricing plan. These cost increases can range from $20.00 a month to over $150.00 per mont ...
... static public IP addresses. Moving from a DHCP based service to a static IP service immediately changes the price of the broadband service, as it moves the customer from a residential pricing plan to a business pricing plan. These cost increases can range from $20.00 a month to over $150.00 per mont ...
ISS DTN experiment support
... • Experiment was performed using CGBA as a proxy onboard to route traffic to the METERON laptop • Cu-Boulder’s ground site was also used to proxy DTN traffic to ESA – No ACS was used for this experiment – Custody Transfer was not used for this experiment ...
... • Experiment was performed using CGBA as a proxy onboard to route traffic to the METERON laptop • Cu-Boulder’s ground site was also used to proxy DTN traffic to ESA – No ACS was used for this experiment – Custody Transfer was not used for this experiment ...
Chapter Eight
... increase demand when own-price falls, a normal good’s ordinary demand curve slopes down. ...
... increase demand when own-price falls, a normal good’s ordinary demand curve slopes down. ...
Network effect

In economics and business, a network effect (also called network externality or demand-side economies of scale) is the effect that one user of a good or service has on the value of that product to other people. When a network effect is present, the value of a product or service is dependent on the number of others using it.The classic example is the telephone. The more people who own telephones, the more valuable the telephone is to each owner. This creates a positive externality because a user may purchase a telephone without intending to create value for other users, but does so in any case. Online social networks work in the same way, with sites like Twitter and Facebook becoming more attractive as more users join.The expression ""network effect"" is applied most commonly to positive network externalities as in the case of the telephone. Negative network externalities can also occur, where more users make a product less valuable, but are more commonly referred to as ""congestion"" (as in traffic congestion or network congestion).Over time, positive network effects can create a bandwagon effect as the network becomes more valuable and more people join, in a positive feedback loop.