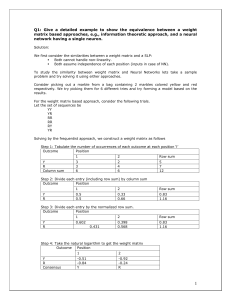
AI Approaches for Next Generation Telecommunication
... disruptive events. AntHocNet's innovative design, which sets it apart from other MANET routing algorithms, has been shown to give superior performance over a wide range of simulation scenarios with different characteristics in terms of mobility, data traffic, etc.. We believe that the good performan ...
... disruptive events. AntHocNet's innovative design, which sets it apart from other MANET routing algorithms, has been shown to give superior performance over a wide range of simulation scenarios with different characteristics in terms of mobility, data traffic, etc.. We believe that the good performan ...
CS 391L: Machine Learning Neural Networks Raymond J. Mooney
... • Multi-layer networks can represent arbitrary functions, but an effective learning algorithm for such networks was thought to be difficult. • A typical multi-layer network consists of an input, hidden and output layer, each fully connected to the next, with ...
... • Multi-layer networks can represent arbitrary functions, but an effective learning algorithm for such networks was thought to be difficult. • A typical multi-layer network consists of an input, hidden and output layer, each fully connected to the next, with ...
HTM304-9-BIKM
... Differences of reporting and data-mining tools Reporting tools use simple operations like sorting, group, and summing to provide description of existing data (mainly descriptive statistics) Data-mining tools use sophisticated techniques (including inferential statistics) ...
... Differences of reporting and data-mining tools Reporting tools use simple operations like sorting, group, and summing to provide description of existing data (mainly descriptive statistics) Data-mining tools use sophisticated techniques (including inferential statistics) ...
Learning Algorithms for Solving MDPs References: Barto, Bradtke
... Learning Algorithms for Solving MDPs References: Barto, Bradtke and Singh (1995) “Learning to Act Using Real-Time Dynamic Programming” in Machine Learning (also on WWW) 1. Q-Learning Given an MDP problem, define the ...
... Learning Algorithms for Solving MDPs References: Barto, Bradtke and Singh (1995) “Learning to Act Using Real-Time Dynamic Programming” in Machine Learning (also on WWW) 1. Q-Learning Given an MDP problem, define the ...
第頁共9頁 Machine Learning Final Exam. Student No.: Name: 104/6
... 1. (5%) Using principal components analysis, we can find a low-dimensional space such that when x is projected there, information loss is minimized. Let the projection of x on the direction of w is z = wTx. The PCA will find w such that Var(z) is maximized ...
... 1. (5%) Using principal components analysis, we can find a low-dimensional space such that when x is projected there, information loss is minimized. Let the projection of x on the direction of w is z = wTx. The PCA will find w such that Var(z) is maximized ...
Document
... Anomaly detection has been an important research topic in data mining and machine learning. Many real-world applications such as intrusion or credit card fraud detection require an effective and efficient framework to identify deviated data instances. However, most anomaly detection methods are typi ...
... Anomaly detection has been an important research topic in data mining and machine learning. Many real-world applications such as intrusion or credit card fraud detection require an effective and efficient framework to identify deviated data instances. However, most anomaly detection methods are typi ...
Intelligent data engineering
... of arriving requests with the blocking probability, leading to B = λp(Nc |λ, µ, Nc ). The expected value for the congestion timePis C = p(Nc |λ, µ, Nc ) and the expected value for c the number of channels in use is M = N n=0 np(n| λ, µ, Nc ). In [2], it was shown that the Erlang-B formula does not p ...
... of arriving requests with the blocking probability, leading to B = λp(Nc |λ, µ, Nc ). The expected value for the congestion timePis C = p(Nc |λ, µ, Nc ) and the expected value for c the number of channels in use is M = N n=0 np(n| λ, µ, Nc ). In [2], it was shown that the Erlang-B formula does not p ...
Applied Machine Learning for Engineering and Design
... http://www.jpo.umd.edu/ and http://www.studenthonorcouncil.umd.edu/code.html. Also note that no form of plagiarism will be tolerated. All work presented to the instructor is assumed to be the original work of the course participant(s). Words, diagrams, figures, or original contributions of anyone ot ...
... http://www.jpo.umd.edu/ and http://www.studenthonorcouncil.umd.edu/code.html. Also note that no form of plagiarism will be tolerated. All work presented to the instructor is assumed to be the original work of the course participant(s). Words, diagrams, figures, or original contributions of anyone ot ...
Logic and Learning - Foundations of Artificial Intelligence
... AI : hand coding NLP Dominant view 1960-1985 Cf. e.g. Steven Pinker’s The language instinct. (popular science book) ...
... AI : hand coding NLP Dominant view 1960-1985 Cf. e.g. Steven Pinker’s The language instinct. (popular science book) ...
PPT - UCLA Head and Neck Surgery
... • SD is a function of the squared differences of each observation from the mean • If the mean is influenced by a single extreme observation, the SD will overstate the actual variability • SEM: standard method of calculating the stability of the mean – SEM = SD - n ...
... • SD is a function of the squared differences of each observation from the mean • If the mean is influenced by a single extreme observation, the SD will overstate the actual variability • SEM: standard method of calculating the stability of the mean – SEM = SD - n ...