The Object-Oriented Database System Manifesto
... A method is defined at the most general level (overriding) and can be redefined for subclasses (overloading). Which version of method to be used is determined at runtime (late binding). ...
... A method is defined at the most general level (overriding) and can be redefined for subclasses (overloading). Which version of method to be used is determined at runtime (late binding). ...
Storage-2017-1 - Lesmahagow High School
... 24/7 instant access is available where an internet connection does exist. Users can access their cloud storage space from numerous devices, often using apps or dedicated software. Local Using local storage it is usually necessary to be working on a client system within the network. Some systems do a ...
... 24/7 instant access is available where an internet connection does exist. Users can access their cloud storage space from numerous devices, often using apps or dedicated software. Local Using local storage it is usually necessary to be working on a client system within the network. Some systems do a ...
File
... e) Economic: AND Microprocessors offer a better price/performance than mainframes. Disadvantages of Distributed Systems over Centralized ones are: a) Security: As previously told you distributed systems will have an inherent security issue. b) Networking: If the network gets saturated then problems ...
... e) Economic: AND Microprocessors offer a better price/performance than mainframes. Disadvantages of Distributed Systems over Centralized ones are: a) Security: As previously told you distributed systems will have an inherent security issue. b) Networking: If the network gets saturated then problems ...
Spatio-Temporal Databases
... intersected during the time interval T,” or “find pairs of planes that will come closer than 1 mile in the next 5 minutes” similarity queries: “find objects that moved similarly to the movement of a given object o over an interval T” ...
... intersected during the time interval T,” or “find pairs of planes that will come closer than 1 mile in the next 5 minutes” similarity queries: “find objects that moved similarly to the movement of a given object o over an interval T” ...
The Microsoft Architecturefor the Internet of Things (IoT)
... Data Privacy Protection and Controls ...
... Data Privacy Protection and Controls ...
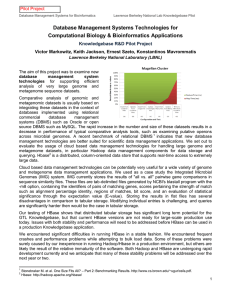
Database Management Systems Technologies for Computational
... Lawrence Berkeley National Lab Knowledgebase Pilot ...
... Lawrence Berkeley National Lab Knowledgebase Pilot ...
4/9/02 Oracle Objects
... An object has a name, a standard representation, and a standard collection of operations that affect it (methods) Abstract data types model classes of data within the database Abstract data types inherit the representation of their parents ...
... An object has a name, a standard representation, and a standard collection of operations that affect it (methods) Abstract data types model classes of data within the database Abstract data types inherit the representation of their parents ...
Disk Attachment
... NAS systems contain one or more hard disks, often arranged into logical, redundant storage containers or RAID arrays. ...
... NAS systems contain one or more hard disks, often arranged into logical, redundant storage containers or RAID arrays. ...
Chapter 13
... • Temporary storage of data as it moves between programs and secondary storage devices – Physical records are stored in the buffer as they are read from secondary storage – FMS extracts logical records from buffers and copies them to data area of the application program ...
... • Temporary storage of data as it moves between programs and secondary storage devices – Physical records are stored in the buffer as they are read from secondary storage – FMS extracts logical records from buffers and copies them to data area of the application program ...
Chapter 12
... • Temporary storage of data as it moves between programs and secondary storage devices – Physical records are stored in the buffer as they are read from secondary storage – FMS extracts logical records from buffers and copies them to data area of the application program ...
... • Temporary storage of data as it moves between programs and secondary storage devices – Physical records are stored in the buffer as they are read from secondary storage – FMS extracts logical records from buffers and copies them to data area of the application program ...
Underlying computer system = hardware + software
... z Processes can give up CPU when they don’t need it (e.g. waiting on I/O device) z ...
... z Processes can give up CPU when they don’t need it (e.g. waiting on I/O device) z ...
Risk-Free Storage for the VMware View Mobile
... the day, workloads spike as users simultaneously try to boot their desktops and login, creating a peak of data being read, or periodic virus scanning or updates triggers a wave of writes. Nimble Storage arrays, built on Nimble’s Cache Accelerated Sequential Layout (CASLTM) architecture, provide adap ...
... the day, workloads spike as users simultaneously try to boot their desktops and login, creating a peak of data being read, or periodic virus scanning or updates triggers a wave of writes. Nimble Storage arrays, built on Nimble’s Cache Accelerated Sequential Layout (CASLTM) architecture, provide adap ...
A Survey of Distributed Storage and Parallel I/O Technique
... such storage architectures and file systems were architecture-specific or aimed at applications in different fields; the effectiveness of the combined use of these architectures and systems remains to be seen. A variety of schemes may be envisioned depending on the types, volumes, and intended purpo ...
... such storage architectures and file systems were architecture-specific or aimed at applications in different fields; the effectiveness of the combined use of these architectures and systems remains to be seen. A variety of schemes may be envisioned depending on the types, volumes, and intended purpo ...
vGUARD - InfoGuard
... Secure infrastructure solution for virtualization The vGuard platform is based on reliable technologies and scalable technologies of leading security, network, server and storage manufacturers. These include secure connectivity from Juniper Networks, x86 servers from Fujitsu, storage systems from Ne ...
... Secure infrastructure solution for virtualization The vGuard platform is based on reliable technologies and scalable technologies of leading security, network, server and storage manufacturers. These include secure connectivity from Juniper Networks, x86 servers from Fujitsu, storage systems from Ne ...
Chapter 12 Representing Data Elements
... • Object is a tuple, and its instance variables are attributes. • Objects can have methods or special-purpose functions associated with them. • Objects may have an object identifier(OID), which is an address that refers uniquely to that object. Pointers are used to related objects with each other. ...
... • Object is a tuple, and its instance variables are attributes. • Objects can have methods or special-purpose functions associated with them. • Objects may have an object identifier(OID), which is an address that refers uniquely to that object. Pointers are used to related objects with each other. ...
ITS_3_Review of Storage, Display, and Input Devices
... Digital Video Disk which can be written to one time. It then becomes read only. DVD-RW Digital Video Disk which can be rewritten to. ...
... Digital Video Disk which can be written to one time. It then becomes read only. DVD-RW Digital Video Disk which can be rewritten to. ...
Video Surveillance at Scale
... Traditional video surveillance technology has included DVR or NVR-based appliances as well as analog cameras in an outdated architecture approach. With the growth of large-scale systems comprised of hundreds or thousands of cameras and increasing use of high-definition video, these traditional appro ...
... Traditional video surveillance technology has included DVR or NVR-based appliances as well as analog cameras in an outdated architecture approach. With the growth of large-scale systems comprised of hundreds or thousands of cameras and increasing use of high-definition video, these traditional appro ...
LiveBackup - 3CiME Technology Srl
... Supports mobile disconnected users Self-Serve easy recovery File, Bare-Metal and Disaster Recovery How valuable is your data? ...
... Supports mobile disconnected users Self-Serve easy recovery File, Bare-Metal and Disaster Recovery How valuable is your data? ...
Organizing Information Digitally
... characteristics from their corresponding generalizations. Inheritance can be defined as the process whereby one object acquires (gets, receives) characteristics from one or more other objects.” ...
... characteristics from their corresponding generalizations. Inheritance can be defined as the process whereby one object acquires (gets, receives) characteristics from one or more other objects.” ...
The Data Growth Problem
... The primary differentiator from business to business is the speed at which data progresses through its lifecycle ...
... The primary differentiator from business to business is the speed at which data progresses through its lifecycle ...
Assignment NoA6
... drives, tape drives, and other storage devices, like optical storage drives. The storage layer’s devices include some intelligence, such as RAID or other data-replication technologies to help protect data in the event of a failure. If you use an array of disks without any special connection between ...
... drives, tape drives, and other storage devices, like optical storage drives. The storage layer’s devices include some intelligence, such as RAID or other data-replication technologies to help protect data in the event of a failure. If you use an array of disks without any special connection between ...
Data warehousing with MySQL Flat Files MySQL MS-SQL
... • Supports MERGE table. • Support fulltext indexing • “INSERT DELAYED ...” option very useful when clients can't wait for the INSERT to complete. Many client bundled together and written in one block • Compress MyISAM tables with “myisampack” to take up much less space. • Benefit from higher perform ...
... • Supports MERGE table. • Support fulltext indexing • “INSERT DELAYED ...” option very useful when clients can't wait for the INSERT to complete. Many client bundled together and written in one block • Compress MyISAM tables with “myisampack” to take up much less space. • Benefit from higher perform ...
Computer Hardware
... access describe the same concept – An element of data or instructions can be directly stored and retrieved by selecting and using any of the locations on the storage media • Each storage position – Has a unique address – Can be individually accessed in approximately the same time ...
... access describe the same concept – An element of data or instructions can be directly stored and retrieved by selecting and using any of the locations on the storage media • Each storage position – Has a unique address – Can be individually accessed in approximately the same time ...