Document
... Generation of initialization key: A method similar to SAFER+ Block Cipher is used. The input to this method is the public address of the bluetooth unit, PIN, length of the pin and a ...
... Generation of initialization key: A method similar to SAFER+ Block Cipher is used. The input to this method is the public address of the bluetooth unit, PIN, length of the pin and a ...
10 March 2009 - Computer Science
... algorithm used and then together with the recovered session key to decrypt to plain text. Of course the algorithm used for encryption is dependant on the protocol used and the algorithms that were negotiated between client and server. Investigate sensible means to store symmetric keys for later use. ...
... algorithm used and then together with the recovered session key to decrypt to plain text. Of course the algorithm used for encryption is dependant on the protocol used and the algorithms that were negotiated between client and server. Investigate sensible means to store symmetric keys for later use. ...
Chapter 19
... of implementing security for VPNs. • Encryption and authentication algorithms and security protocols are well studied. • Users can be confident that IPSec provides strong security. • Can be implemented in firewalls and routers owned by the organization, giving network managers control over security. ...
... of implementing security for VPNs. • Encryption and authentication algorithms and security protocols are well studied. • Users can be confident that IPSec provides strong security. • Can be implemented in firewalls and routers owned by the organization, giving network managers control over security. ...
Java Security
... order of the providers in which providers are searched for requested services when no specific provider is requested. Implementation interoperability means that various implementations can work with each other, use each other's keys, or verify each other's signatures. ...
... order of the providers in which providers are searched for requested services when no specific provider is requested. Implementation interoperability means that various implementations can work with each other, use each other's keys, or verify each other's signatures. ...
Well-Tempered Clavier
... • New key-profile values – New problem: Repetitions of notes affect result ...
... • New key-profile values – New problem: Repetitions of notes affect result ...
Getting Security Right in Wireless Sensor Networks
... Fortunately, there are powerful tools for building secure, robust wireless communications networks. It takes diligence and attention to detail, but there is nothing fundamentally hard about it. Ciphers and Nonces The most basic cryptographic tool is the block cipher. As an example, AES-128 is a part ...
... Fortunately, there are powerful tools for building secure, robust wireless communications networks. It takes diligence and attention to detail, but there is nothing fundamentally hard about it. Ciphers and Nonces The most basic cryptographic tool is the block cipher. As an example, AES-128 is a part ...
Hybrid cryptography using symmetric key encryption
... the majority networks to acquire the required data. Because of the defect of only the single data encryption and the use of famous encryption algorithm, which was not improved in traditional methods of the registration process, a combined encryption algorithm is proposed in this thesis[1- 4]. This p ...
... the majority networks to acquire the required data. Because of the defect of only the single data encryption and the use of famous encryption algorithm, which was not improved in traditional methods of the registration process, a combined encryption algorithm is proposed in this thesis[1- 4]. This p ...
D`Amo - softfarm
... Federal Information Processing Standard (FIPS) is a set of standards required by the United States Federal Government for use in computer systems used by government agencies and contractors. • Well-known FIPS standards include the Data Encryption Standard (DES) and the Advanced Encryption Standard ( ...
... Federal Information Processing Standard (FIPS) is a set of standards required by the United States Federal Government for use in computer systems used by government agencies and contractors. • Well-known FIPS standards include the Data Encryption Standard (DES) and the Advanced Encryption Standard ( ...
Remote Access - York Technical College
... Process of encoding data using a mathematical algorithm that makes it difficult for unauthorized users to read the data if they intercept it. Encryption requires a key (math. Algorithm) to read the data. Two types of encryption ...
... Process of encoding data using a mathematical algorithm that makes it difficult for unauthorized users to read the data if they intercept it. Encryption requires a key (math. Algorithm) to read the data. Two types of encryption ...
Lecture 25: Introduction to Network Security
... Critical health care data Banking and financial information National security secrets ...
... Critical health care data Banking and financial information National security secrets ...
Wireless Networking & Security
... What to do on Unsecured Wireless • Setup VPN Tunnel to a secured machine • Setup an SSH Tunnel to a secured machine • Force HTTPS on all possible connections ...
... What to do on Unsecured Wireless • Setup VPN Tunnel to a secured machine • Setup an SSH Tunnel to a secured machine • Force HTTPS on all possible connections ...
Course Learning Objectives:
... 1. Identify computer and network security threats, classify the threats and develop a security model to prevent, detect and recover from the attacks. (ABET Outcomes: a, c, e, j, k) 2. Encrypt and decrypt messages using block ciphers, sign and verify messages using well known signature generation and ...
... 1. Identify computer and network security threats, classify the threats and develop a security model to prevent, detect and recover from the attacks. (ABET Outcomes: a, c, e, j, k) 2. Encrypt and decrypt messages using block ciphers, sign and verify messages using well known signature generation and ...
Presentation4 - University Of Worcester
... e.g. Windows SIGVER (file signing) » method of checking incoming files to ensure that they are from a Microsoft approved source ...
... e.g. Windows SIGVER (file signing) » method of checking incoming files to ensure that they are from a Microsoft approved source ...
Hidden Markov Model Cryptanalysis
... attack based on information gained from the physical implementation of a cryptosystem. For example, timing information, power consumption, electromagnetic leaks or even sound can provide an extra source of information which can be exploited to break the ...
... attack based on information gained from the physical implementation of a cryptosystem. For example, timing information, power consumption, electromagnetic leaks or even sound can provide an extra source of information which can be exploited to break the ...
notes
... might be replaced to new router which can support IP Multicast function. May incur cost to replace router 2. While a few recent works have considered issues with key dissemination using overlays, these works rely on analysis or simulations with synthetic workloads and don’t consider issues such as ...
... might be replaced to new router which can support IP Multicast function. May incur cost to replace router 2. While a few recent works have considered issues with key dissemination using overlays, these works rely on analysis or simulations with synthetic workloads and don’t consider issues such as ...
PPT - Purdue Computer Science
... shared secret key available to two or more parties; – key transport: one party creates, and securely transfers it to the other(s). – key agreement: key establishment technique in which a shared secret is derived by two (or more) parties ...
... shared secret key available to two or more parties; – key transport: one party creates, and securely transfers it to the other(s). – key agreement: key establishment technique in which a shared secret is derived by two (or more) parties ...
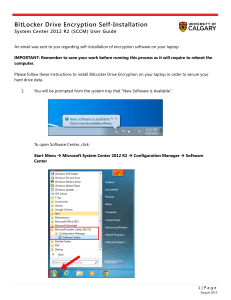
BitLocker Drive Encryption Self
... System Center 2012 R2 (SCCM) User Guide An email was sent to you regarding self-installation of encryption software on your laptop. IMPORTANT: Remember to save your work before running this process as it will require to reboot the computer. Please follow these instructions to install BitLocker Drive ...
... System Center 2012 R2 (SCCM) User Guide An email was sent to you regarding self-installation of encryption software on your laptop. IMPORTANT: Remember to save your work before running this process as it will require to reboot the computer. Please follow these instructions to install BitLocker Drive ...
CIT 016 Review for Final
... You must properly configure network equipment to resist attacks The primary method of resisting attacks is to filter data packets as they arrive at the perimeter of the network In addition to making sure the perimeter is secure, make sure the device itself is secure by using strong passwords and ...
... You must properly configure network equipment to resist attacks The primary method of resisting attacks is to filter data packets as they arrive at the perimeter of the network In addition to making sure the perimeter is secure, make sure the device itself is secure by using strong passwords and ...
Database Security
... – 56-bit key on 64-bit blocks of plaintext, producing 64-bit blocks of ciphertext – characters are substituted and rearranged according to the value of the key – Challenges with the DES system: key security and ease of cracking the code ...
... – 56-bit key on 64-bit blocks of plaintext, producing 64-bit blocks of ciphertext – characters are substituted and rearranged according to the value of the key – Challenges with the DES system: key security and ease of cracking the code ...
CN 2015 5 - SNGCE DIGITAL LIBRARY
... from masked data. It is the study of Encryption and Decryption methods. Encryption—Plain text to cipher text Decryption—Cipher text to Plain text ...
... from masked data. It is the study of Encryption and Decryption methods. Encryption—Plain text to cipher text Decryption—Cipher text to Plain text ...
Security
... install only shrink-wrapped software use antivirus software do not click on attachments to email ...
... install only shrink-wrapped software use antivirus software do not click on attachments to email ...
Kumar`s Security Slides
... * An attacker can flip a bit in the ciphertext, then upon decryption, the corresponding bit in the plaintext will be flipped. * Also, if an eavesdropper intercepts two ciphertexts encrypted with the same key stream, it is possible to obtain the XOR of the two plaintexts. * Knowledge of this XOR can ...
... * An attacker can flip a bit in the ciphertext, then upon decryption, the corresponding bit in the plaintext will be flipped. * Also, if an eavesdropper intercepts two ciphertexts encrypted with the same key stream, it is possible to obtain the XOR of the two plaintexts. * Knowledge of this XOR can ...
Single Photon Polarization
... 2. If it is head she decides to encode using a horizontal/verical basis. If it is a tail, she encodes in 45/135 basis. 3. Each bit is encoded as 0 or 1 in the chosen basis. 4. Bob receives each bit and does not know the basis used to encode. He also tosses a coin and decides to decode using the basi ...
... 2. If it is head she decides to encode using a horizontal/verical basis. If it is a tail, she encodes in 45/135 basis. 3. Each bit is encoded as 0 or 1 in the chosen basis. 4. Bob receives each bit and does not know the basis used to encode. He also tosses a coin and decides to decode using the basi ...
History of cryptography

Cryptography, the use of codes and ciphers to protect secrets, began thousands of years ago. Until recent decades, it has been the story of what might be called classic cryptography — that is, of methods of encryption that use pen and paper, or perhaps simple mechanical aids. In the early 20th century, the invention of complex mechanical and electromechanical machines, such as the Enigma rotor machine, provided more sophisticated and efficient means of encryption; and the subsequent introduction of electronics and computing has allowed elaborate schemes of still greater complexity, most of which are entirely unsuited to pen and paper.The development of cryptography has been paralleled by the development of cryptanalysis — the ""breaking"" of codes and ciphers. The discovery and application, early on, of frequency analysis to the reading of encrypted communications has, on occasion, altered the course of history. Thus the Zimmermann Telegram triggered the United States' entry into World War I; and Allied reading of Nazi Germany's ciphers shortened World War II, in some evaluations by as much as two years.Until the 1970s, secure cryptography was largely the preserve of governments. Two events have since brought it squarely into the public domain: the creation of a public encryption standard (DES), and the invention of public-key cryptography.