V290-19-B20B Technical Specifications
... Unitronics has been producing PLCs, automation software and accessory devices since 1989. Unitronics’ OPLC controllers combine full-function PLCs and HMI operating panels into single, compact units. These HMI + PLC devices are programmed in a single, user-friendly environment. Our clients save I/O p ...
... Unitronics has been producing PLCs, automation software and accessory devices since 1989. Unitronics’ OPLC controllers combine full-function PLCs and HMI operating panels into single, compact units. These HMI + PLC devices are programmed in a single, user-friendly environment. Our clients save I/O p ...
File
... smallest addressable piece of memory: typically, the CPU can load from or store into an individual byte. Possible integer values: 0..255 or -128..127 Can also represent a character ...
... smallest addressable piece of memory: typically, the CPU can load from or store into an individual byte. Possible integer values: 0..255 or -128..127 Can also represent a character ...
Teachware developed for students of UWB power engineering study
... The developed software for the short-circuit analysis is called TeNeCo (according to the names of its authors). The computer program is based on the principle of superposition and the method of symmetrical components [1], [3]. There are several approximations that have been used to simplify the faul ...
... The developed software for the short-circuit analysis is called TeNeCo (according to the names of its authors). The computer program is based on the principle of superposition and the method of symmetrical components [1], [3]. There are several approximations that have been used to simplify the faul ...
COMPUTER´S MEMORY Paula Michelle
... encoded in programs, the CPU can handle only one instruction and a few pieces of data at the time The computer divides each RAM chip into many equal-sized memory locations The central processing unit, is hardware component that executes the step on a software program ...
... encoded in programs, the CPU can handle only one instruction and a few pieces of data at the time The computer divides each RAM chip into many equal-sized memory locations The central processing unit, is hardware component that executes the step on a software program ...
open - WordPress.com
... system which can process or execute the input data and gives output. So, simply a microprocessor is nothing but a system which can execute small processes. 4004 was the first Microprocessor designed by Intel which was 4 bit. ...
... system which can process or execute the input data and gives output. So, simply a microprocessor is nothing but a system which can execute small processes. 4004 was the first Microprocessor designed by Intel which was 4 bit. ...
Inverter Error Messages
... drives. When troubleshooting these errors lease consult the manuals. For Magnetek or Yaskawa you can find the manuals on their web site, www.drivers.com, go to “Our Products” select the model number then look for the “Documentation: header. Baldor currently does not have the manuals on their web sit ...
... drives. When troubleshooting these errors lease consult the manuals. For Magnetek or Yaskawa you can find the manuals on their web site, www.drivers.com, go to “Our Products” select the model number then look for the “Documentation: header. Baldor currently does not have the manuals on their web sit ...
Measurements of tensions and current constant and to bake
... will cause, that the result will be systematically smaller or bigger than the actual value. Detecting the source of systematic errors is difficult and requires comparing used devices with the standard and the in-depth analysis of the method of measurement. At exercises performed in the student labor ...
... will cause, that the result will be systematically smaller or bigger than the actual value. Detecting the source of systematic errors is difficult and requires comparing used devices with the standard and the in-depth analysis of the method of measurement. At exercises performed in the student labor ...
8051 Notes - H Guy Williams
... The interrupt sources are associated with bit locations in registers. Each (or all) can be enabled by setting or clearing the appropriate bit in the IE register. If enabled, an interrupt will cause a call to one of the predefined locations in RAM. RETI = return from interrupt, pops last address befo ...
... The interrupt sources are associated with bit locations in registers. Each (or all) can be enabled by setting or clearing the appropriate bit in the IE register. If enabled, an interrupt will cause a call to one of the predefined locations in RAM. RETI = return from interrupt, pops last address befo ...
Embedded Multicores Example of Freescale solutions
... • Ensure threads don’t access critical section at same time ...
... • Ensure threads don’t access critical section at same time ...
Welcome to PHYS 276!!
... Usually estimated using information from the manufacturer of the measuring device or by making measurements of a calibrated standard. ...
... Usually estimated using information from the manufacturer of the measuring device or by making measurements of a calibrated standard. ...
NovaLynx Corporation 110-WS-16 Modular Weather Station
... two alarm outputs, & optional modem communications. The WS-16 is supplied with an attractive desktop data acquisition module with a memory capacity of 640KB RAM. The standard system includes a 120Vac power adaptor and RS232 serial port for connection to a personal computer. For outdoor or remote app ...
... two alarm outputs, & optional modem communications. The WS-16 is supplied with an attractive desktop data acquisition module with a memory capacity of 640KB RAM. The standard system includes a 120Vac power adaptor and RS232 serial port for connection to a personal computer. For outdoor or remote app ...
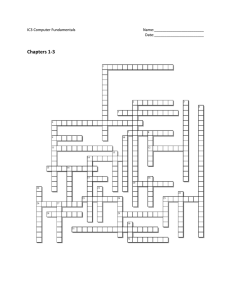
ch._1-3_crossword_puzzle
... 4 - prevents data loss due to power outages by continuing power 6 - This memory stores specific instructions; longterm 8 - Developed the microprocessor 10 - A circuit board that contains all of the computer system's main components 13 - Used to store data inside computer; can also be external 14 - G ...
... 4 - prevents data loss due to power outages by continuing power 6 - This memory stores specific instructions; longterm 8 - Developed the microprocessor 10 - A circuit board that contains all of the computer system's main components 13 - Used to store data inside computer; can also be external 14 - G ...
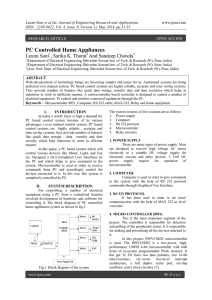
I45015153
... With advancement of technology things are becoming simpler and easier for us. Automated systems are being preferred over manual system. PC based control systems are highly reliable, accurate and time saving systems. They provide number of features like quick data storage, transfer data and data secu ...
... With advancement of technology things are becoming simpler and easier for us. Automated systems are being preferred over manual system. PC based control systems are highly reliable, accurate and time saving systems. They provide number of features like quick data storage, transfer data and data secu ...
15.5 Other Practical Considerations
... breadboard circuit, it is advisable to use duplicate components (where possible) for the soldered board (i.e., don’t cannibalize components from a working prototype circuit in case something goes wrong or gets damaged when soldering your board). ...
... breadboard circuit, it is advisable to use duplicate components (where possible) for the soldered board (i.e., don’t cannibalize components from a working prototype circuit in case something goes wrong or gets damaged when soldering your board). ...
A Switch is Pressed, So W hat??? Debouncing Light Dependent
... ADCx – ADC1 at 1x gain ADC{0,1} – ADC0 at 10x ADC{0,1} – ADC0 at 200x ADC{2,3} – ADC2 at 10x ADC{2,3} – ADC3 at 200x ADC{0,1,2,3,4,5} – ADC2 at 1x ...
... ADCx – ADC1 at 1x gain ADC{0,1} – ADC0 at 10x ADC{0,1} – ADC0 at 200x ADC{2,3} – ADC2 at 10x ADC{2,3} – ADC3 at 200x ADC{0,1,2,3,4,5} – ADC2 at 1x ...
The LIN (Local Interconnect Network) is a cost-effective
... Larger system distributed systems for telecommunications and computer networks typically employ a distributed power system which consists of an intermediate bus voltage, between 24 and 48 volts, which is then translated into the lower supply voltages where they are needed. This is typically done to ...
... Larger system distributed systems for telecommunications and computer networks typically employ a distributed power system which consists of an intermediate bus voltage, between 24 and 48 volts, which is then translated into the lower supply voltages where they are needed. This is typically done to ...