First, Second, and Third Generation Mesh Architectures
... bandwidth distribution are needed. Growing demands in video and voice data require a higher transfer rate with low latency and interference. This requires more node or hops ...
... bandwidth distribution are needed. Growing demands in video and voice data require a higher transfer rate with low latency and interference. This requires more node or hops ...
Remote Access
... Uses a standard PSTN voice line Standard established by the ITU ISDN service began in mid 1980’s Requires a Network Termination device(s) to process the data from the telephone company • Requires a Terminal Adapter (router) to convert the digital data to voice and distribute the communication. • Mus ...
... Uses a standard PSTN voice line Standard established by the ITU ISDN service began in mid 1980’s Requires a Network Termination device(s) to process the data from the telephone company • Requires a Terminal Adapter (router) to convert the digital data to voice and distribute the communication. • Mus ...
fm fluidity
... Our MPLS-based transmission protocol is built to overcome the limits of standard license-free protocols and to deliver a wireless network infrastructure with a higher level of reliability. Our innovative transmission protocol is based on a traffic optimization algorithm that allows every Fluidmesh r ...
... Our MPLS-based transmission protocol is built to overcome the limits of standard license-free protocols and to deliver a wireless network infrastructure with a higher level of reliability. Our innovative transmission protocol is based on a traffic optimization algorithm that allows every Fluidmesh r ...
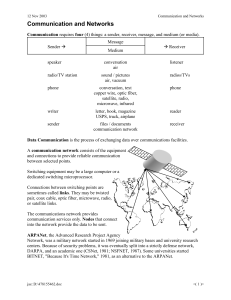
Communication and Networks
... Switching equipment may be a large computer or a dedicated switching microprocessor. Connections between switching points are sometimes called links. They may be twisted pair, coax cable, optic fiber, microwave, radio, or satellite links. The communications network provides communication services on ...
... Switching equipment may be a large computer or a dedicated switching microprocessor. Connections between switching points are sometimes called links. They may be twisted pair, coax cable, optic fiber, microwave, radio, or satellite links. The communications network provides communication services on ...
Federated Wireless Network Authentication
... Focused on 802.1x only? Concentrate group resources on single strategy Focus on standards-based solution that would provide a single interface for users Enables authn, encryption at edge If necessary, infrastructure could likely be used for non-802.1x ...
... Focused on 802.1x only? Concentrate group resources on single strategy Focus on standards-based solution that would provide a single interface for users Enables authn, encryption at edge If necessary, infrastructure could likely be used for non-802.1x ...
Alcatel-Lucent MDR-8000 Digital Microwave Radio Family
... video is increasing, as well as data – primarily IP traffic – to support departmental LANs and interdepartmental WANs; and the trend of sharing data across jurisdictions is accelerating the demand for more bandwidth. The MDR-8000 radio addresses all of these issues cost effectively, while providing ...
... video is increasing, as well as data – primarily IP traffic – to support departmental LANs and interdepartmental WANs; and the trend of sharing data across jurisdictions is accelerating the demand for more bandwidth. The MDR-8000 radio addresses all of these issues cost effectively, while providing ...
The CyberFence Difference
... environment. In evaluating options for securing vulnerable endpoints within an ICS, encryption and authentication should be thoroughly reviewed. This advanced security thwarts unauthorized devices and malicious interference to critical command and control processes in ICS. CyberFence offers a fully- ...
... environment. In evaluating options for securing vulnerable endpoints within an ICS, encryption and authentication should be thoroughly reviewed. This advanced security thwarts unauthorized devices and malicious interference to critical command and control processes in ICS. CyberFence offers a fully- ...
Exploration Comms and Computing Experiments and
... Protocol, based on older concepts for pushing large files from one planet to another. Trades interactivity for reliability UDP: Normal UDP/IP, use commercial technology and ...
... Protocol, based on older concepts for pushing large files from one planet to another. Trades interactivity for reliability UDP: Normal UDP/IP, use commercial technology and ...
DK1000 Smart Object
... This standards-based turnkey solution allows users, integrators, developers and OEMs to shorten the timeto-market of their IoT products. The Nivis DK1000 provides a complete development environment that helps engineers have our solution up and running in a matter of minutes and reduces R&D costs. ...
... This standards-based turnkey solution allows users, integrators, developers and OEMs to shorten the timeto-market of their IoT products. The Nivis DK1000 provides a complete development environment that helps engineers have our solution up and running in a matter of minutes and reduces R&D costs. ...
Basic Concepts
... Packets from many conversations are mixed (multiplexed) over each trunk line Only pay for the capacity used Dramatic trunk line cost savings The reason for packet switching ...
... Packets from many conversations are mixed (multiplexed) over each trunk line Only pay for the capacity used Dramatic trunk line cost savings The reason for packet switching ...
cable-replacement
... • A cable-replacement technology that can be used to connect almost any device to any other device • Radio interface enabling electronic devices to communicate wirelessly via short range (10 meters) ad-hoc radio connections • a standard for a small , cheap radio chip to be plugged into computers, pr ...
... • A cable-replacement technology that can be used to connect almost any device to any other device • Radio interface enabling electronic devices to communicate wirelessly via short range (10 meters) ad-hoc radio connections • a standard for a small , cheap radio chip to be plugged into computers, pr ...
PDF - This Chapter (47.0 KB)
... either be configured to continuously record, or be triggered to record by the presence of RTP packets. The recording system must manage the timestamp, datestamp, and duration information. Some recording systems are capable of detecting other external events, such as ring, off-hook, and contact closu ...
... either be configured to continuously record, or be triggered to record by the presence of RTP packets. The recording system must manage the timestamp, datestamp, and duration information. Some recording systems are capable of detecting other external events, such as ring, off-hook, and contact closu ...
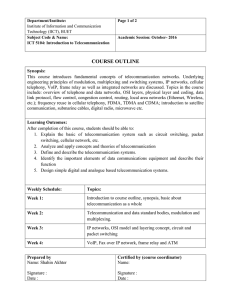
CO-ICT-5104_Edited
... This course introduces fundamental concepts of telecommunication networks. Underlying engineering principles of modulation, multiplexing and switching systems, IP networks, cellular telephony, VoIP, frame relay as well as integrated networks are discussed. Topics in the course include: overview of t ...
... This course introduces fundamental concepts of telecommunication networks. Underlying engineering principles of modulation, multiplexing and switching systems, IP networks, cellular telephony, VoIP, frame relay as well as integrated networks are discussed. Topics in the course include: overview of t ...
18-04-0003-00-0000-unlicensed-use-tv-bands
... • Some approaches to creating a database of unused or infrequently used channels: – Geolocation: use GPS or some other location technology along with a pre-programmed database. – Autonomous detection: scan all channels, identify any incumbent users based on signal characteristics, and create a datab ...
... • Some approaches to creating a database of unused or infrequently used channels: – Geolocation: use GPS or some other location technology along with a pre-programmed database. – Autonomous detection: scan all channels, identify any incumbent users based on signal characteristics, and create a datab ...
Document
... FDMA separates the spectrum into distinct voice channels by splitting it into uniform chunks of bandwidth like radio stations Each station sends its signal at a different frequency within the available band FDMA is used mainly for analog transmission. While it is certainly capable of carrying digita ...
... FDMA separates the spectrum into distinct voice channels by splitting it into uniform chunks of bandwidth like radio stations Each station sends its signal at a different frequency within the available band FDMA is used mainly for analog transmission. While it is certainly capable of carrying digita ...
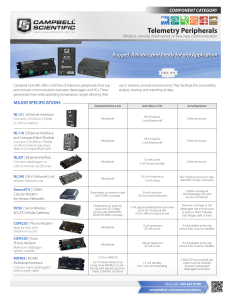
Telemetry Peripherals
... Campbell Scientific offers a full line of telemetry peripherals that support remote communications between dataloggers and PCs. These peripherals have wide operating temperature ranges allowing their ...
... Campbell Scientific offers a full line of telemetry peripherals that support remote communications between dataloggers and PCs. These peripherals have wide operating temperature ranges allowing their ...
Prevent Interference Between Co-Located, Wireless
... Slot Diagnostics is another tool in radios that engineers can use to analyze communication at the RF level between radios. Metrics about every single RF slot showed that radios that should have good signal levels were not even acknowledging RF packets. To resolve this issue, a 1 Pulse Per Second (1 ...
... Slot Diagnostics is another tool in radios that engineers can use to analyze communication at the RF level between radios. Metrics about every single RF slot showed that radios that should have good signal levels were not even acknowledging RF packets. To resolve this issue, a 1 Pulse Per Second (1 ...
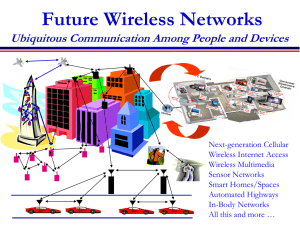
What is Wireless and Mobile Communication?
... by using the same radio channel for both transmission and reception. At any given time, the user can either transmit or receive information. ...
... by using the same radio channel for both transmission and reception. At any given time, the user can either transmit or receive information. ...
HIPERLAN: HIgh Performance Radio Local Area Networks
... Next generation of HiperLAN family: Proposed by ETSI BRAN (Broadband Radio Access Networks) in 1999, and is still under development. Goal: Providing high-speed (raw bit rate ~54Mbps) communications access to different broadband core networks and moving terminals Features: connection-oriented, QoS ...
... Next generation of HiperLAN family: Proposed by ETSI BRAN (Broadband Radio Access Networks) in 1999, and is still under development. Goal: Providing high-speed (raw bit rate ~54Mbps) communications access to different broadband core networks and moving terminals Features: connection-oriented, QoS ...
Spectrum sharing in infrastructure based Cognitive Radio networks
... region. Nowadays, the most actual issue now is reforming of the existing frequency range for LTE deployment. Nowadays, the most common band - 900/1800 MHz, which in usual licensed for the GSM networks. The main disadvantage of infrastructure-based CRn is that they allows to allocate LTE channels in ...
... region. Nowadays, the most actual issue now is reforming of the existing frequency range for LTE deployment. Nowadays, the most common band - 900/1800 MHz, which in usual licensed for the GSM networks. The main disadvantage of infrastructure-based CRn is that they allows to allocate LTE channels in ...
Document
... GPRS (General Packet Radio Service) To transmit and receive TCP/IP based data to and from GPRS mobile devices ...
... GPRS (General Packet Radio Service) To transmit and receive TCP/IP based data to and from GPRS mobile devices ...
Broadcast Channels
... Transmit energy minimized by maximizing bit time Circuit energy consumption increases with bit time Introduces a delay versus energy tradeoff for each bit ...
... Transmit energy minimized by maximizing bit time Circuit energy consumption increases with bit time Introduces a delay versus energy tradeoff for each bit ...
presentation
... – Each system design must trust the other one in order to fully work. If one system perceives that the other one is untrustworthy, the system may withhold levels of interoperability ...
... – Each system design must trust the other one in order to fully work. If one system perceives that the other one is untrustworthy, the system may withhold levels of interoperability ...
Physical Layer(September 20)
... Lower frequencies implies fewer bits can be transmitted per second. ...
... Lower frequencies implies fewer bits can be transmitted per second. ...