Hidden Markov Model Cryptanalysis
... attack based on information gained from the physical implementation of a cryptosystem. For example, timing information, power consumption, electromagnetic leaks or even sound can provide an extra source of information which can be exploited to break the system. Timing attack, power monitoring attack ...
... attack based on information gained from the physical implementation of a cryptosystem. For example, timing information, power consumption, electromagnetic leaks or even sound can provide an extra source of information which can be exploited to break the system. Timing attack, power monitoring attack ...
procedure name - Siskiyou Central Credit Union
... or disparages an individual, Credit Union, or business. o They may not be used to conduct personal business. Solicitations, offers to buy and sell goods or services, and other personal messages to groups are not an appropriate use of these systems. o You must not make any copies of the Credit Union’ ...
... or disparages an individual, Credit Union, or business. o They may not be used to conduct personal business. Solicitations, offers to buy and sell goods or services, and other personal messages to groups are not an appropriate use of these systems. o You must not make any copies of the Credit Union’ ...
chap12
... Risks and Safeguards Single-User License vs Site License Single-User License • Install software on one computer • Sell software to someone, but only after removing software from ...
... Risks and Safeguards Single-User License vs Site License Single-User License • Install software on one computer • Sell software to someone, but only after removing software from ...
Introduction
... “IT security is the inherent technical features and functions that collectively contribute to an IT infrastructure achieving and sustaining confidentiality, integrity, availability, accountability, authenticity, and reliability.” “Operational security involves the implementation of standard operati ...
... “IT security is the inherent technical features and functions that collectively contribute to an IT infrastructure achieving and sustaining confidentiality, integrity, availability, accountability, authenticity, and reliability.” “Operational security involves the implementation of standard operati ...
answer-sheet-7540-040-7630-345-b_
... Virus – a virus is a type of programme that is designed to copy itself over, and over again, and it will attach itself to other programmes. Most of the time a virus can be annoying but harmless. The consequence of a virus is that it can cause a great amount of time wastage, financial loss for compa ...
... Virus – a virus is a type of programme that is designed to copy itself over, and over again, and it will attach itself to other programmes. Most of the time a virus can be annoying but harmless. The consequence of a virus is that it can cause a great amount of time wastage, financial loss for compa ...
Chapter 4
... • Over the years, attack tools have evolved. • Threats become more sophisticated as the technical expertise required to implement attacks diminishes. ...
... • Over the years, attack tools have evolved. • Threats become more sophisticated as the technical expertise required to implement attacks diminishes. ...
Professional Malware is a Pandemic
... Can detect illegal modifications to the system Is the only way to detect some of the latest threats ...
... Can detect illegal modifications to the system Is the only way to detect some of the latest threats ...
2012 Bond Planning Technology Project Update
... Minimum investment in most critical and high priority projects to provide additional devices for student use, additional software tools, and improved data analysis capabilities Significant investment in Computer & Devices Additional investment in educational technology innovation ...
... Minimum investment in most critical and high priority projects to provide additional devices for student use, additional software tools, and improved data analysis capabilities Significant investment in Computer & Devices Additional investment in educational technology innovation ...
Chapter11
... Right of individuals and companies to restrict collection and use of information about them Difficult to maintain today because data is stored online Employee monitoring is using computers to observe employee computer use ...
... Right of individuals and companies to restrict collection and use of information about them Difficult to maintain today because data is stored online Employee monitoring is using computers to observe employee computer use ...
WHAT IS EC SECURITY? - Joseph H. Schuessler, PhD
... occurs; each function in the business should have a valid recovery capability plan cybercrime Intentional crimes carried out on the Internet cybercriminal A person who intentionally carries out crimes over the Internet ...
... occurs; each function in the business should have a valid recovery capability plan cybercrime Intentional crimes carried out on the Internet cybercriminal A person who intentionally carries out crimes over the Internet ...
Port Scanning: Is it illegal
... Sequence Prediction tests to spoof packets. In addition to determining which ports are listening to the “public,” scans also reveal which platform the computer is using. Armed with this information, the cracker can conduct further research into exploits for that platform. “Normal” port scanning is s ...
... Sequence Prediction tests to spoof packets. In addition to determining which ports are listening to the “public,” scans also reveal which platform the computer is using. Armed with this information, the cracker can conduct further research into exploits for that platform. “Normal” port scanning is s ...
ITC_2013_13-02
... Unix/Linux and Mac OS X systems. Probing a target machine for susceptible entry points is often the starting point of an attack. Metasploit includes mechanisms to check a computer’s susceptibility to several known software exploits. An exploit is an amount of data or a sequence of commands a person( ...
... Unix/Linux and Mac OS X systems. Probing a target machine for susceptible entry points is often the starting point of an attack. Metasploit includes mechanisms to check a computer’s susceptibility to several known software exploits. An exploit is an amount of data or a sequence of commands a person( ...
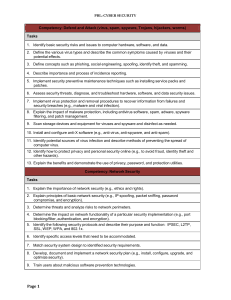
Competency: Defend and Attack (virus, spam, spyware - FBLA-PBL
... 16. Illustrate fundamental legal issues involved with security management. 17. Design an audit policy and incident response procedures. 18. Manage and distribute critical software updates that resolve known security vulnerabilities and other stability issues. 19. Explain the importance of educating ...
... 16. Illustrate fundamental legal issues involved with security management. 17. Design an audit policy and incident response procedures. 18. Manage and distribute critical software updates that resolve known security vulnerabilities and other stability issues. 19. Explain the importance of educating ...
Assessing Network Security for Northwind Traders What
... Denial-of-Service (DoS) attack: Any attempt by an attacker to deny his victim’s access to a resource DoS attacks can be divided into three categories: Flooding attacks Resource starvation attacks Disruption of service Note: Denial-of-service attacks should not be launched against your own live produ ...
... Denial-of-Service (DoS) attack: Any attempt by an attacker to deny his victim’s access to a resource DoS attacks can be divided into three categories: Flooding attacks Resource starvation attacks Disruption of service Note: Denial-of-service attacks should not be launched against your own live produ ...
The wild world of malware: Keeping your
... likely to have IT personnel whose sole focus is network security. This paper examines the current drivers of malware development, details the characteristics of each, discusses how they manifest themselves on the network, and points to how each can be remedied. While the names of many forms of malwa ...
... likely to have IT personnel whose sole focus is network security. This paper examines the current drivers of malware development, details the characteristics of each, discusses how they manifest themselves on the network, and points to how each can be remedied. While the names of many forms of malwa ...
Discovering Computers Fundamentals 3rd Edition
... Health Concerns of Computer Use What are some health concerns of computer use? Computer vision syndrome (CVS)—eye and vision ...
... Health Concerns of Computer Use What are some health concerns of computer use? Computer vision syndrome (CVS)—eye and vision ...
Chapter. 01
... A large measure of computer security is simply keeping the computer system's information secure. In broader terms, computer security can be thought of as the protection of the computer and its resources against accidental or intentional disclosure of confidential data, unlawful modification of data ...
... A large measure of computer security is simply keeping the computer system's information secure. In broader terms, computer security can be thought of as the protection of the computer and its resources against accidental or intentional disclosure of confidential data, unlawful modification of data ...
Computer Security and Penetration Testing Chapter 11 Denial
... • Exploit the existing software weaknesses • Effect is either degraded performance or crashes on the victim server • Hackers generate a small number of carefully malformed packets to exploit known software bugs – Bugs allow hackers to change or damage configuration files ...
... • Exploit the existing software weaknesses • Effect is either degraded performance or crashes on the victim server • Hackers generate a small number of carefully malformed packets to exploit known software bugs – Bugs allow hackers to change or damage configuration files ...
Introduction to Information Security Chapter N
... Identify and understand the threats posed to information security Identify and understand the more common attacks associated with those threats ...
... Identify and understand the threats posed to information security Identify and understand the more common attacks associated with those threats ...
Slide 1
... • Identity Theft – gaining access to someone’s personal information allowing them to imitate you (stolen laptop) • Denial of Service – attacks on websites using zombie computers that overwhelm the site and shut it down • Others: Spyware, Spam, Wireless Access, Viruses Security Technologies Companies ...
... • Identity Theft – gaining access to someone’s personal information allowing them to imitate you (stolen laptop) • Denial of Service – attacks on websites using zombie computers that overwhelm the site and shut it down • Others: Spyware, Spam, Wireless Access, Viruses Security Technologies Companies ...
Lecture 12
... failures, and other system events Application event logs record events that applications request be recorded Security event log records security-critical events such as logging in and out, system file accesses, and other events ...
... failures, and other system events Application event logs record events that applications request be recorded Security event log records security-critical events such as logging in and out, system file accesses, and other events ...
Presentation Title
... authorized recipients. This presentation may contain information that is confidential, proprietary or otherwise legally protected, and it may not be further copied, distributed or publicly displayed without the express written permission of Gartner, Inc. or its affiliates. © 2010 Gartner, Inc. and/o ...
... authorized recipients. This presentation may contain information that is confidential, proprietary or otherwise legally protected, and it may not be further copied, distributed or publicly displayed without the express written permission of Gartner, Inc. or its affiliates. © 2010 Gartner, Inc. and/o ...
Network Infrastructure Security
... people. LAN software and practices also need to provide for the security of these programs and data. ...
... people. LAN software and practices also need to provide for the security of these programs and data. ...